In today’s digital marketplace, there is hardly an organization that does not depend on software or “the internet”. This dependence brings with it a degree of vulnerability. Businesses today are far more likely to have their operations interrupted by cybercriminals than malicious actors in the real world.
Zero-day attacks are especially feared because they give hackers a unique opportunity to bypass typical cybersecurity defenses. In this article, learn what a zero-day vulnerability is and how you can protect against an attack.
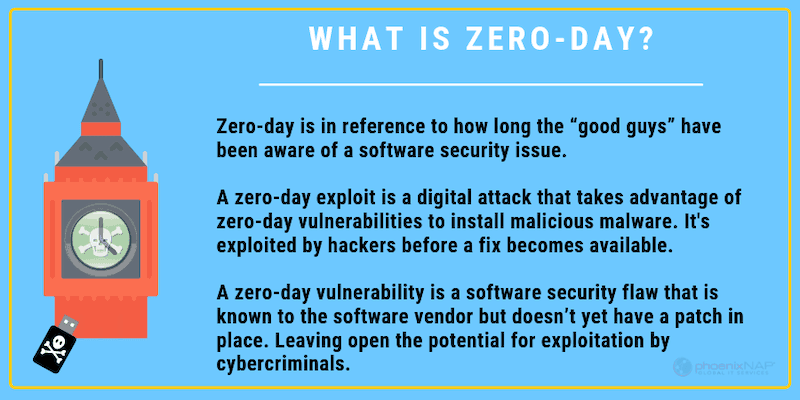
What Is a Zero-Day Vulnerability?
A zero-day attack is when hackers release malware before developers have an opportunity to release a fix for the vulnerability—hence zero-day.
Zero-day refers to a newly discovered vulnerability in the software. As developers are just finding out about the flaw, patches or security update to resolve the issue, have not been released. In zero-day attacks, software vendors are reactive, not proactive. They can only respond when problems emerge.
A zero-day attack happens when hackers exploit a window of vulnerability and then launch a direct attack using that vulnerability.
What makes zero-day exploits so dangerous is that the only people who know about them are the attackers themselves. Hackers can either attack immediatly or sit on their knowledge of weakness, waiting for the opportune moment to strike.
How Does A Zero-Day Attack Work?
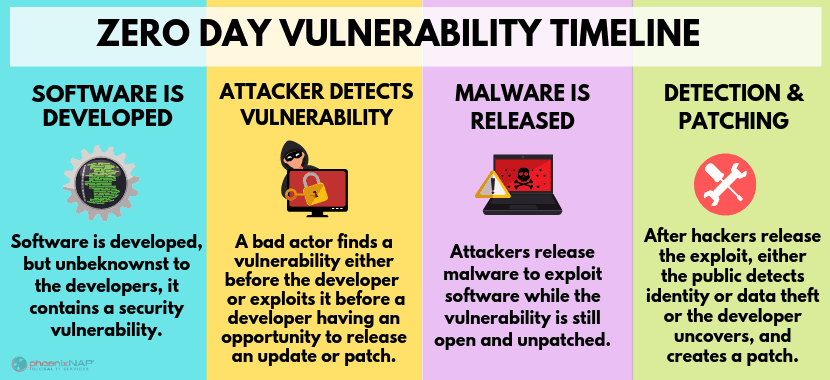
Zero-day exploits work by many mechanisms. Typically, they involve targeting a software system with malware. Malware integrates into an existing layer of software and prevents it from performing its normal function.
Infiltration with malware is surprisingly easy. Often hackers will disguise malware in the form of website links. All a user has to do is click a website link, and they will automatically begin downloading the problem software. Downloads like these often occur when a hacker has found a way to exploit unpatched vulnerabilities in a web browser.
For example, suppose that your browser has just updated its software to add more features. You log into a website that you trust on your browser and then click what you believe to be a valid link. The link, however, contains malicious code.
Before the patch, your browser would have prevented the link from automatically downloading software onto your computer. However, thanks to changes in the browser code after patching, the download begins. Your computer then becomes infected.
Hours later, the browser company releases a new patch to prevent other people from getting infected. However, for you, it’s already too late.
Who are the targets?
Zero-day exploits target high-profile businesses and governments, but they can attack anyone. The zero-day exploit, Stuxnet, for instance, attempted to sabotage the Iranian Nuclear program in 2010. Many people believe that Israel and the United States were behind the attack. Stuxnet contained new forms of exploit that many people had not seen before.
New email software, for instance, may not be able to filter out fake addresses. This might expose people to various types of phishing attacks. Hackers may try to steal valuable information, like bank card details or passwords.
How Can Zero-Day Exploits be Prevented?
Many organizations and individuals believe that there’s not much that can be done to stop a zero-day attack. This is not entirely true. Take a look at these tips and learn prevention strategies.
Use Up-To-Date Advanced Security Software
The problem with many basic anti-virus software solutions is that they are only good at defending against known threats. When threats are unknown – as they are in zero-day attacks – then they can fail. Only the most advanced security software in the world can protect against hacking from as-yet-unknown origins. Keeping software up-to-date at all times is essential.
Ensure Security Software is Up-to-Date
Vendors may not always publicly disclose if they have been the victim of a zero-day attack. That’s why it’s essential to install new software updates as soon as they become available. They could protect your organization against threats software vendors have identified.
Teach Safe Online Security Habits
Many zero-day exploits harness human error. Malicious actors, for instance, may target employees with fake emails. These emails may contain documents infected with malware or encourage them to hand over sensitive information. Smart organizations, therefore, rigorously enforce security habits to help employees stay safe online.
Install Proactive Security Defenses
Smart security software can sometimes block as-yet-unknown threats using databases of past breaches. These data can be correlated with present attacks to detect threats. Look for software that can defend against attacks of both known and unknown origin.
Implement Network Access Control
Network access control is a tool that prevents unauthorized machines from accessing an organization’s network.
Use IPsec
IPsec encrypts and authenticates all network traffic. This allows the system to identify and isolate non-network traffic quickly.
Deploy a Web Application Firewall
Web application firewalls are a kind of firewall that helps to protect computers that link to a web server. The purpose of the firewall is to scan incoming packets of data for threats continually. The hope is that by using a web application firewall, companies can react in real-time. With a scanner, firms can immediately suppress suspicious activity on their platforms.
Use Content Threat Removal
Content threat removal is a type of detection technology that assumes all data is threatening. The system works by dismantling all data that comes through the network and discarding anything it thinks is malicious. The idea is to throw out anything potentially unsafe in the original data, based on a database of dangerous objects.
Develop Recovery Strategies
Even employing all of the above, it is unlikely that an organization will be able to eliminate the threat of zero-day exploits. Organizations, therefore, must prepare for the worse so that they can respond.
Having a disaster recovery strategy in place is essential. Disaster recovery strategies can mitigate damage from a breach. Most companies ensure that they have cloud backups for all their data. In the event of a breach, their data is safe, and they can continue with their operations as usual.
Detection of Zero Day Exploits
Organizations need to be able to detect attacks quick. Security professionals have four ways of identifying a zero-day attack.
- Statistical analysis can be deployed to analyze the likelihood and probable source of an attack.
- Signature-based. Previous data from past attacks can be examined and determine whether current data patterns signal a threat. If they do, then an attack may be underway.
- Behavioral analysis. By studying the behavior of malicious actors and see if it has changed. If the patterns from a suspected hacking entity differ from usual, then it could be a sign of an attack.
- Combination scoring system. By combining all methods into a single scoring system, the score determines the likelihood of a breach.
Recent Zero Day Attacks
Zero-day attacks are a common occurrence throughout recent history. Take a look at the following cases:
- Adobe Flash Player, 2016. In 2016, there was a zero-day attack on Adobe Flash. Hackers gained the ability to control read and write memory.
- Microsoft Office, 2017. In 2017, hackers discovered that documents in rich text format could open a visual basic script. The script could then be used to open PowerShell commands.
- Windows. A Google employee identified Windows as having zero-day vulnerabilities. The employee then went on the record to state the Microsoft’s flagship product had had flawed code for more than 20 years.
- Java. Java is a platform used by both Microsoft and Apple to create their products. Java recently released a fix designed to overcome some of the platform’s serious zero-day security vulnerabilities.