Data breaches are occurring at an unprecedented rate, and there are no signs that they will slow down any time soon. If you’re one of the many organizations that store sensitive information online, then you’re at risk. Now is the time to learn more about the impending dangers businesses face and how to implement vital data protection practices.
What is a Data Breach?
In any instance, when information is accessed without authorization, it’s a data breach. The types of violations can vary and evolve as technology diversifies, but to put it simply, the information in the wrong hands constitutes a data breach. Information can become compromised in many ways now; a cyber-attack is only one. As the name implies, it’s a confirmed incident when an unauthorized entity has accessed confidential, sensitive, or protected information. Big data is now the norm, as more devices become connected. Those valuable connections also become points of weaknesses. Data breaches can wreak havoc on the reputations of businesses and induce a ripple of after-effects that can leave lasting repercussions.
For instance, a business may have to pay hefty fines due to a breach. Outside of regulatory penalties, they may have to compensate the victims whose data was compromised. Even a minor data breach could put an SMB out of business due to the financial constraints of fines, lawsuits, and loss of public trust. When someone steals secure data and publishes it on the web, it’s out there for the world to see. As more data becomes digitized, and we generate more original digital data, it’s logical that more data breaches will occur.
Recent History of Data Breaches
For the first time since 2013, this past year ransomware declined down 20 percent overall, but up 12 percent for enterprises according to Symantec. The most successful campaigns in 2019 involved ransomware that relies on open Remote Desktop Protocol (RDP) servers as the initial access point. Attackers more commonly use targeted, manual attacks instead of the one-two punch of malvertising exploits. The first quarter of 2019 saw the detection of several new ransomware families using innovative techniques to target businesses.
One of the most recent and significant data breaches occurred in September 2017 with the Equifax data breach, which exposed the personal data of 147 million people.
A few other prominent data breach examples include:
- Yahoo: Between 2013 and 2014, over three million user accounts affected.
- Marriott International: From 2014 to 2018, over 500 million of their user accounts were breached.
- Target Stores: In December of 2014, approximately 110 million of their user accounts got hacked.
- JP Morgan Chase: In July of 2014, around 76 million residential and seven million small business Chase customers had their financial records breached.
- A May 2019 ransomware attack on the City of Baltimore is expected to cost in excess of $18 Million to recover from.
The average cost per ransomware attack to businesses last year was $133,000. Attacks on Brittan’s National Health Service in 2017 cost nearly $100 Million in IT recovery services alone. Yet, the cost of customer confidence and company reputation can be unmeasurable.
Four Common Causes of Data Leaks
| Human error | Errors cannot be avoided, people make mistakes, and information may get distributed without mal intent. Proprietary data can get sent accidentally to the wrong person, and uploads to public folders or misconfigured servers can bleed sensitive information. |
| Theft or loss of devices | We all have devices. From smartphones to laptops, hard drives, USBs, and other data storage devices can easily get stolen, misplaced, lost, or disposed of incorrectly. Sensitive or protected information saved on those devices can end up in the wrong hands and lead to a more significant data breach. |
| Employee data leak or theft | When a company terminates an employee or ends a contract with notice, that person may deliberately access protected information without permission and copy it. They may use or distribute it with malicious intent. |
| Cyberattacks | Hacking is the most apparent form of a data breach. Hackers use malware, phishing, social engineering, skimming, and scams to get access to sensitive and encrypted information. |
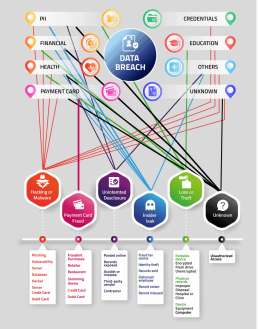
The Reality of Ransomware
Now that we know how data breaches and hacks can occur, we can look at why criminals are looking for a way to penetrate your firewalls. One major ploy cybercriminals use is Ransomware which is a form of extortion. It’s is a malware that infects, overtakes, and locks your data making it inaccessible unless a ransom is paid. The threat could be to publish a company’s data, erase it or perpetually block access to it, which can cripple a business.
The FBI warns not to pay a ransom, but many companies will be at a loss if they can’t access their sensitive data. Since ransomware is so profitable for hackers, attacks have skyrocketed. According to a Quickbridge study, over 4,000 separate ransomware attacks have occurred since 2016. Furthermore, they estimate the damages will reach around $11.9 billion globally.
It’s essential to know which types of information are the most valuable to cybercriminals. Cybercriminals may use programs that mine and lock your data, later using it for ransom. This attack is known as ransomware. Hackers can hold businesses hostage if vital information is leaked and user information exposed. Such an occurrence was the Ashley Madison hack of July 2015.
There are three main reasons a hacker wants your data:
- To sell it on the black market
- Identity theft
- Simply because they can
There’s no such thing as being ‘too safe’ in this digital era. One hundred percent secure may not exist as of yet, but you can take practical steps to mitigate the potential for massive data loss.
What to Do in Case of Ransomware Attack
Here are some ransomware response strategies:
| What you should do: |
|
| What you shouldn’t do: |
|
How to Prevent Security and Data Breaches
If you run a business, then it is likely you store personal information about your employees, customers, and others digitally or online. Since data breaches are on the rise, all organizations must start taking more detailed steps to prevent a data breach. By implementing protection best practices you will stay ahead of potential attacks and ensure the safety of your business.
Ransomware protection and response best practices were in focus of our recent webinar with Veeam. With October being National Cybersecurity Month, we thought it is the right time to revisit it.
Take a look at the recording below and get insights from William Bell, EVP of Products from phoenixNAP, and Brandon McCoy, Cloud Sales Engineer from Veeam.
Here is a detailed checklist we recommend you go through to start consolidating your online security:
Don’t click on email attachments
Spammers and hackers are becoming more ingenious in their attempts to trick people into open email attachments. It’s no longer the Nigerian prince asking you to wire donations to his kingdom. Now you get emails from the IRS, Social Security Administration, and sometimes even someone that looks like one of your relatives. Spammers find relatives by searching your name from any number of person search sites, or social media which display the names of your relatives.
Before clicking on any email attachment, stop and ask yourself if you know the person or organization, and were you notified of an incoming attachment? If you answer no to any of those two questions, don’t open the attachment. In essence, you should delete the email immediately.
When in doubt, you can do a little investigative work to check if an email is legit. For example, check to see if info@paypal.com does originate from the official site. How? In your email client, display the email header information. There, it will be evident if the email did not come from paypal.com. If there are links in the email, hover over one of them, but don’t click it! You should see a popup or hint that displays the full URL. If it doesn’t start with a paypal.com domain, it’s a fake.
Implement and use 2FA
2FA or Two Factor Authentication is a security method that verifies you. You’re already familiar with website logins. 2FA takes logins a step further. It does this by checking if it’s genuinely you that is logging in with your credentials. 2FA does this by asking for additional information. After you enter your login info, the 2FA scheme will send a text code to your verified phone number. Which in turn, you must enter into the login screen to gain access.
There isn’t a field on the login screen to enter your device’s phone number. That would defeat the purpose of 2FA since a spammer would be able to enter their mobile number and hijack the auth code. Instead, the mobile number you saved in your account is used. By involving another device that only you have access to, 2FA provides more confidence that the person logging in is you.
A 2018 study by Carnegie Mellon University found that over 75 percent of study participants thought 2FA made their accounts more secure, but 50 percent thought the process was annoying. 2FA also helped to stop dangerous security practices, such as credential sharing.
Never share your social security number
Most job applications will ask for your social security number to perform a background check. Outside of job applications and government organizations, there is no need to provide your social security number. Some companies may ask for it to set up an account for you. You can decline, and ask that the company uses another identifying number. After all, you have no idea what sort of security practices go on at any company.
Lockdown physical assets
Keep physical locks on any devices which contain sensitive data and are vulnerable to hacking.
Restrict access
Limit access to sensitive data, to employees on a straightforward need-to-know basis.
Update all your operating systems
Through cloud computing, these should be updated consistently and automatically. It’s always safer to ensure you have the latest versions with the most recent security fixes and patches installed.
Schedule regular updates for applications
Some apps will have to be updated manually, where others will be updated automatically. This rule is critical since earlier versions will have loopholes that hackers can exploit.
Use SSL in your email client
When using a desktop email client, the client connects to your email provider’s servers to receive and send emails. With some providers, you have the option to use a non-SSL connection. This can prove risky.
A non-SSL connection will send your non-encrypted email login credentials over the Internet. When you connect to a public or unsecured WiFi network (i.e., coffee shop or hotel), your email credentials will be vulnerable. Always use SSL when connecting to your email provider.
Use machine-generated passwords
With the advent of keyword loggers and even cameras spying on networks and devices, it’s imperative to use a machine-generated password.
Furthermore, hackers often play the guessing game too. One of the most popular passwords are names of personal pets. Using social media, it’s not hard to discover your pet’s name. For example, a simple Facebook search can give any hacker that type of personal information.
Play it safe by using something generated for you, and it is also completely random. If storage and memory pose an issue, then use a password manager.
Use Strong Complex Passwords
Don’t use the same password across multiple logins, even if you have used a password generator. Each login should be different. If one login is compromised, at least your other logins are safe – for now. By diversifying with strong secure passwords, you are essentially creating a firewall between each login.
Use a Credit monitoring service
Credit monitoring services can alert you to suspicious activity within your financial accounts. Credit monitoring services are convenient because you can monitor activity within all of your financial accounts, and through all three credit bureaus.
If you don’t want to pay for a monitoring service, most credit cards and bank accounts have alerts that inform you of suspicious activity. It’s triggered when a transaction exceeds a specific dollar amount, or a questionable purchase has been made on the card.
Contact your financial institution immediately
If you see suspicious activity on one of your business accounts, contact your financial institution right away. Your institution has protocols in place for events like these.
Train and educate your employees
The Office of the Future survey, Canon USA reported that more than one-third of respondents consider malware and ransomware a priority threat. Yet, 25% of respondents say that employees have limited to no security awareness, nor do they understand their role in prevention.
For better overall security, it’s essential to train your employees on your most recent security protocols. Create written privacy and data security policies. Educate your employees on those policies, and make them aware of their responsibilities for keeping company data secure. Offer this type of training at least two or three times per year.
If you’re self-employed, use an EIN instead of your social security number
If you are self-employed and have to fill out W-9s and 1099s, use a federal EIN. Using the Employer Identification Number means you do not need to use your social security number. And this protects you from becoming a victim of identity theft.
Conclusion
Data breaches are an unfortunate part of doing business online and participating in digital activities. In this article, you can learn to arm yourself and your business with protective knowledge and strategies and best practices to avoid data breaches. You can drastically reduce the possibility of your private data ending up online, or in hands, you don’t want it to be.
If you are still unsure about how to secure your business online, contact phoenixNAP today to get more information on how to develop your own strategy.

