The latest numbers are in, and they aren’t pretty. In 2018, over 90% of cyber attacks and their resulting breaches stemmed from a spear phishing email.
According to SANS Institute’s Allen Paller, spear phishing emails caused 95% of all attacks on enterprise networks. So what is it that makes phishing emails in general and spear phishing emails in specific so dangerous? And how can individuals and enterprises protect themselves against such an invasive tactic?
The following article details what spear phishing attacks are and how to prevent them.
A Definition of Spear Phishing
Spear phishing is a much more targeted type of phishing attack. Here, the perpetrator doesn’t just send out a stock email to thousands or tens of thousands of recipients. Instead, they send out a personalized email to each of their targets. That email is sent out only after the perpetrator has done their research and knows specific details about their victim that will encourage the target to act. Those key details enable the perpetrator to draft the email in such a way as to instill trust in their victim and encourage them to do something that they might not otherwise do.
Spear phishing attacks usually appeal either to human greed or fear. This means they will either offer targets money, discounts, bargains, etc. or threaten targets into acting by saying their checking, PayPal, or eBay account has been frozen.
To encourage their victim to act, the perpetrator of a spear phishing attack will first find their victim and collect critical details to ensure whichever tactic will be believable. For example, they might search out an individual’s profile on a social networking site and from there glean their target’s email address, geographic location, workplace, friends list, and any new big items recently purchased and from where. Such details alone might seem innocuous but together enable the perpetrator to craft a dangerously effective email.
In their spear phishing email, the perpetrator will use the information to pose as a friend, colleague, boss, or other familiar entity to send out a highly convincing but ultimately fraudulent message. Hackers also employ a blend of email spoofing, and dynamic URLs to make emails appear more convincing.
91% of cyberattacks and the resulting data breach begin with a “spear phishing” email, according to research from security software firm Trend Micro.
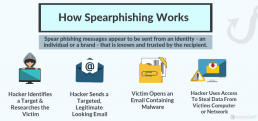
How Spear Phishing Works
Phishing schemes are any cyber or phone-based schemes designed to trick a victim into giving up personal details.
That information is then later used in some sort of scam. It’s a common hack, and most phishing scheme perpetrators target thousands of people with the goal of fooling a few. Take for example the famous “Nigerian Prince” scam. In this phishing scam, thousands of people receive emails offering a large sum of money on the condition the recipient transfers money for them. Most people will delete the email, but every year there continues to be those who don’t. Those victims who fall prey can lose thousands or even tens of thousands of dollars to the scam.
However, because more people have become aware of such scams and because business IT groups and email servers have tightened up security, the phishers have become more specialized. This is where the hacking technique of spear phishing developed.
Examples of Spear Phishing
Examples and scenarios for how spear phishing works and what it looks like include:
Spear Phishing An Individual: The perpetrator discovers the bank their target uses and using a spoofed email and copied website credentials, sends the target an email stating the account has been breached. That email will use fear-mongering to get the target to call a number or follow a link to provide confidential banking information (such as username and password) to confirm they are the real account holder. The perpetrator will then use that information to siphon out money.
Spear Phishing a business: A spear phishing attack against a company is similar to the one against an individual in that the perpetrator will first research and then use that research to draft a legitimate-looking scam. But the difference is the scale. Networking firm Ubiquiti Networks Inc. learned this the hard when cyber thieves uncovered key details about firm executives. The thieves then used those details to create spoof communications that appeared as though they were the firm executives and directed the firm’s finance department to initiate unauthorized international wire transfers to the tune of $46.7 million.
5 Protection Tactics To Avoid Spear Phishing Attacks
Spear phishing attacks look legitimate but are very dangerous. The following are a few tips both individuals and businesses can use to help prevent perpetrators of such attacks both from harvesting key data and using the data to get hold of critical accounts:
1. Avoid posting personal information online, such as a personal phone number. Every individual should avoid ever posting their phone number on their social media platform and avoid inputting their phone number with an unknown (and even most known) websites and mobile applications. Phone numbers are just as key to identifying a person and their complete financial background as a social security number. With techniques like SIM swapping and phishing scams, a person can essentially take over all of a person’s financial accounts.
2. Never click an unknown email link or attachment, especially from a financial or business institution. Use email security best practices. Perpetrators of spear phishing attacks will commonly send emails posing as a trusted institution their victim is known to frequent, such as Bank of America, Amazon, and eBay. Any emails an individual receives via personal business email should not be wholly trusted. Never click a link from such an organization, instead launch a separate browser window and go directly to the institution’s website to investigate claims and conduct business as usual. Any other emails, from friends, favorite blog writers, or nonprofit organizations, should be considered with care. Check the anchor text and never input personal details or otherwise confidential information on a link clicked from an email.
3. Be careful over-sharing on social media. Be mindful of personal details on their social media profiles and who they allow access to it. Keep privacy configurations high and avoid accepting unknown friend requests.
4. All organizations should implement a wholescale data protection program. Data protection programs are a combination of user education and security awareness training on best digital security practices and the implementation of a wholesale cyber protection solution designed to prevent potential data loss due to cyber attacks like spear phishing.
5. Keep confidential information out of emails. A favorite spear phishing tactic is to email employees from a reputable looking address and request sensitive information such as passwords or business banking details.ion.
Stay Alert & Stay Safe
No person and no organization is immune to becoming a target of cyber thieves.
If your information is on the internet or your smartphone has applications downloaded, then you are a potential target for this and other sophisticated cyber attacks. The best way to prevent falling victim is to stay aware at all time.
Keep information confidential, never trust outside sources and contact an experienced and professional security solutions team to ensure business assets are likewise protected.