Protect Your Data Every Step of the Way
By 2025, the total amount of data in the cloud and on-prem will reach 181 zettabytes. To meet the growing challenge of protecting your organization’s distributed data, phoenixNAP offers state-of-the-art Confidential Computing solutions. Take advantage of next-gen technologies available as a service and encrypt data at rest, in transit, and in use for unmatched end-to-end security.
Data-at-Rest Encryption
Encrypting data at rest is a standard safeguard for data stored on drives or in the cloud.
Data-in-Transit Encryption
Encrypting data in transit between systems protects it from unauthorized access.
Data-in-Use Encryption
Confidential Computing shields data in a hardware-based CPU enclave while processing.
Testimonial
“Intel and phoenixNAP technologies are vital to ensuring efficient and secure data processing. We’ve had a great collaboration with both companies over the years and we are excited to continue exploring the potential of their technologies”
– Nik Schork, Ph.D., Deputy Director of Quantitative Science, TGen
What Is Confidential Computing?
Confidential Computing is a cloud computing technique that encrypts data in use. The technology behind it reduces the risk of cyber breaches by encrypting workloads while they are being processed. Complementing data at-rest and in-transit encryption, in-use encryption ensures comprehensive data protection.
Some of the key benefits of this approach include:
- End-to-end security
- Reduced attack surface
- Lower risk of outsider and insider threats
- Improved environment controls
- Greater transparency
- Increased confidence in cloud providers
Confidential Computing Explained in 2 Minutes
Using hardware-based, programmatic trust, Intel solutions make sensitive data accessible only to the applications and code that need it. Watch this video for a quick rundown of Trust Boundaries, Confidential Computing, and how Intel technology secures your organization’s workloads while maintaining high levels of performance.
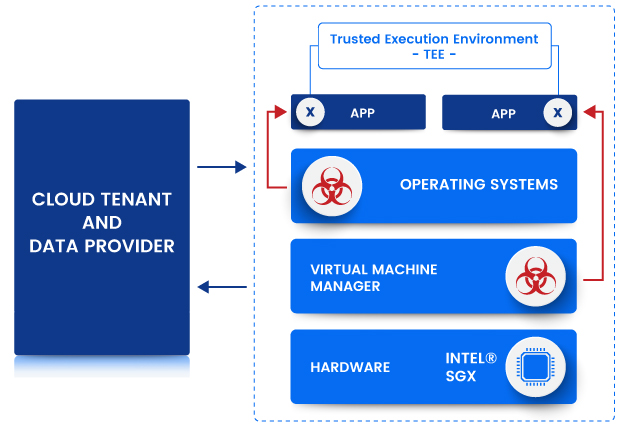
Confidential Computing with Intel® SGX
Data-in-use encryption can be implemented by creating hardware-based Trusted Execution Environments (TEE), also known as enclaves. Enclaves isolate an application from the rest of the system, providing better control of access than encryption keys. TEEs dramatically reduce the possibility of a data breach, even if a bad actor gains privileged access to the production environment.
TEEs are created through hardware security technologies such as Intel® Software Guard Extensions (SGX). As a set of instructions for hardware-based isolation and in-memory encryption, SGX enables encrypted data processing within protected enclaves. Data is processed in-memory and protected from system-wide exposure. Through full memory encryption and accelerated cryptographic performance, Intel SGX helps enable Confidential Computing on both dedicated and virtualized platforms.
Lock bad actors out of access. Facilitate federated learning.
Intel-Powered Confidential Computing Solutions for Your Data
Boasting cutting-edge Intel processors with SGX technology, phoenixNAP’s IaaS portfolio provides unmatched performance and security. Encrypt data during its most vulnerable lifecycle stages using powerful traditional or cloud-native IT solutions.
- More cores and better performance per core
- Built-in accelerator engines
- High-bandwidth DDR5
- High-performance NVMe drives
- Enterprise-grade security
- Low-latency 50 Gbps network
- 20 Gbps DDoS protection
- Expert 24/7 support
Bare Metal Cloud
Bare Metal Cloud is phoenixNAP's API-driven dedicated server platform that enables automated provisioning of servers with 4th Gen Intel® Xeon® Scalable CPUs. Spin up servers with Intel SGX in minutes, manage them through API, CLI, or IaC tools, and consume resources with hourly, monthly, or yearly billing.
Data Security Cloud
As a secure multi-tenant cloud platform, Data Security Cloud provides multiple layers of security to ensure maximum data protection. High-performance Intel Xeon Scalable processors at the foundation of the platform provide hardware-enhanced encryption and Confidential Computing potential.
Dedicated Servers
phoenixNAP's selection of dedicated servers includes a wide variety of Intel-powered platforms with outstanding levels of performance, flexibility, and security. Powered by high-end Intel processors, our dedicated servers are ideal for storing sensitive data and running mission-critical applications.