A cyber-attack may only last for a few hours, but what do you do afterward?
How quickly can your business recover from one?
The consequences of a cyber-breach and its ability to disrupt your business do not stop when the breach is repaired. Sometimes, the impact is not immediately known, and the problems can take years to fix.
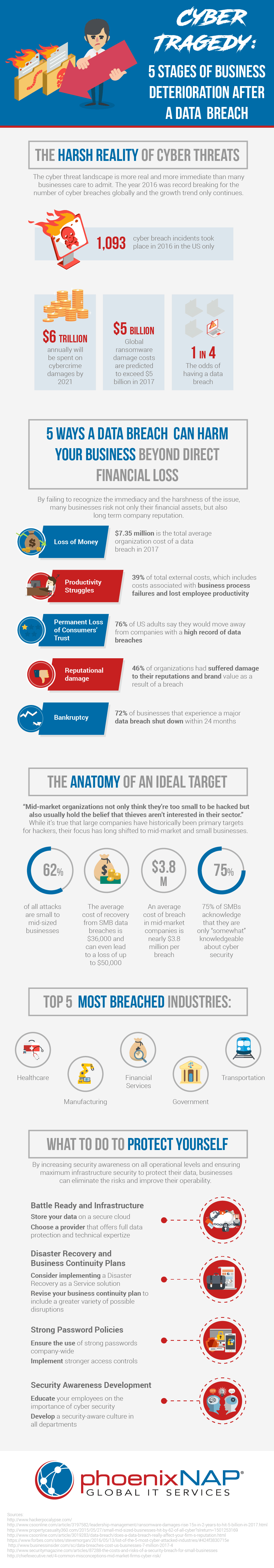
Recent reports paint a grim picture: 72% of businesses that experience a severe data breach shut down within 24 months.
A recent major example is Equifax. Experts suggest that the company won’t be able to recover after exposing the personal data of 143 million US citizens.
Two weeks after the breach was reported in the media, technology attorney Mark Grossman said that Equifax had lost $6 billion in market capitalization, and the losses are expected to climb to as much as $20 billion in the coming months. It is likely Equifax won’t be able to recover from this.
Equifax is far from an isolated case. Examples of companies who struggle to recover from cyber-attacks abound.
One thing all of these companies share is that their downward spiral following a major attack can be divided into five stages:
 5 Stages of Business Deterioration after a Data Breach
5 Stages of Business Deterioration after a Data Breach
STAGE 1: FINANCIAL LOSS
Direct financial damage comes from many sources.
First, there is the direct loss caused by the breach itself. Your systems or products may be down or unsellable while the breach is in progress, and they may remain down for minutes to hours to days once the attack ends. As a general estimate, every minute of downtime can cost a company $250,000.
Then, there are direct costs to recover from the breach, such as repairing systems, updating procedures and processes, purchasing new hardware or software to prevent future attacks and the costs of the people needed to complete these tasks. You may even have to hire more people to help with the cleanup.
Finally, there is the possibility of reputational damage or lawsuits. Costs to hire a public relations firm or retain attorneys can skyrocket quickly.
Compared to these costs, the implementation of a battle-ready infrastructure and advanced security systems provides a clear return on your investment. A proactive approach to cyber defense makes a great deal of sense in today’s marketplace.
STAGE 2: LOWERED PRODUCTIVITY

Beyond direct financial costs, a cyber-attack can dramatically reduce a company’s productivity on several fronts such as the inability to complete tasks while the attack is in progress (or due to the damage it caused) as well as further lost work as resources are redirected to repair and recovery tasks afterward.
Productivity loss is even more severe when an attack takes place during a peak season. According to Business Insider, “business disruption accounts for 39% of total external costs,” including costs of discontinued business processes and lost employee productivity.
One way to reduce this lost productivity is to invest in business continuity best practices. A continuity plan lets you recover more quickly and helps reduce the chances your company becomes another data breach statistic.
STAGE 3: DAMAGED CUSTOMER RELATIONSHIPS
While financial and productivity losses can be calculated and quantified directly, it is much more difficult to price the damage to your relationships with your customers. Consumers will lose confidence in your company and the products and services it provides. Furthermore, that loss is long-term, challenging to mitigate, and affects both your existing customers as well as any new ones you hoped to gain.
Research suggests that 76% of US adults would stay away from companies with a track record of data breaches. Regaining consumers’ trust after compromising their data is not impossible, but it will not be easy, and it will not be fast. You need to plan and execute an effective strategy to regain consumer trust.
Ways to rebuild trust often involve changes in messaging, increased interactions with consumers, and a greater focus on security. Even with a brilliant strategy, it will take months—perhaps even years—to bring people back and start generating new sales.
STAGE 4: DAMAGED COMPANY REPUTATION
In parallel with the customer relationship damage, the company’s overall reputation in the marketplace also deteriorates. Following a breach, your company might gain a notorious reputation for being a hacker target or for having terrible security practices or similar.
Customers looking for a product in your market will consider your company’s reputation. For example, if a customer is looking for a bank, they would be unlikely to pick Tesco Bank (in the UK) which had a significant breach last year in which hackers stole money from more than 20,000 accounts. The customer will naturally prefer a bank that hasn’t had any money stolen from it recently.
With the media increasingly talking about cyber breaches, it is impossible to leave people in the dark regarding such incidents. A brand with a stigma is a failing brand, and this influences a company’s operations long term.
Stage 5: Total Bankruptcy

Once all communications and brand recovery strategies fail and existing customers flee and potential new customers avoid you, your company will eventually go bankrupt. This process may take a long time, but it may also be inevitable that the damage is irreparable, and any further investments of time or money are futile.
Two recent examples are The Dutch certificate company DigiNotar back in 2011 and, more recently, 21st Century Oncology. The latter is a striking example, as it involved exposure of 2.2 million patient records. Previously, the world’s largest operator of cancer treatment, the company could do nothing to fix the reputational damage.
While both of those examples are extreme, and not every hacked company is destined for bankruptcy, they illustrate the importance of focusingon cybersecurity in today’s business world.
In summary
The past year has seen a record-breaking number of cyber-attacks and breaches. Experts don’t expect this trend of frequent, aggressive attacks to slow. Cyber breaches are on the rise, and the five stages above may play out over and over again in the next few years.
The common pattern across many companies sends a strong message about the importance of cyber protection and IT security practices. Companies need to be proactive in protecting themselves and reducing the chances of being a cyber-attack victim; otherwise, you run the risk of being the next statistic and case study.
The best way to do this is to understand the threat and all of its possible outcomes. The infographic above summarizes what awaits your company after an attack. It can help you better plan your cyber defense strategies.
Like what you see? Just copy and paste the following code to share the infographic.
<textarea style=”margin:0px; width:100%; height:200px;”>
<img src=”https://resource.phoenixnap.com/hubfs/blog-files/Infographic/Cyber%20Tragedy%20-%205%20Stages%20of%20Business%20Deterioration%20Afterr%20a%20Data%20Breach.png” width=”540″ alt=”Cyber Tragedy: 5 Stages of Business Deterioration after a Data Breach”>
<a href=”Cyber Tragedy: 5 Stages of Business Deterioration after a Data Breach”>
</a><p><strong>Cyber Tragedy: 5 Stages of Business Deterioration after a Data Breach</strong>, courtesy of <a href=”Cyber Tragedy: 5 Stages of Business Deterioration after a Data Breach”>PhoenixNap Global IT Services</a></p>
</textarea>
 5 Stages of Business Deterioration after a Data Breach
5 Stages of Business Deterioration after a Data Breach