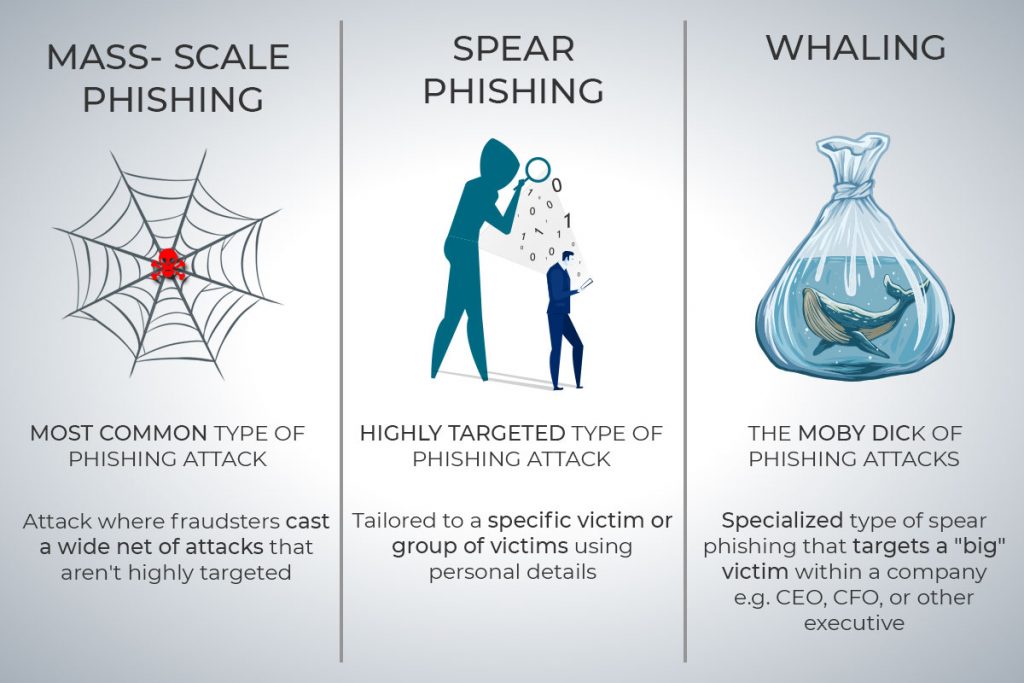
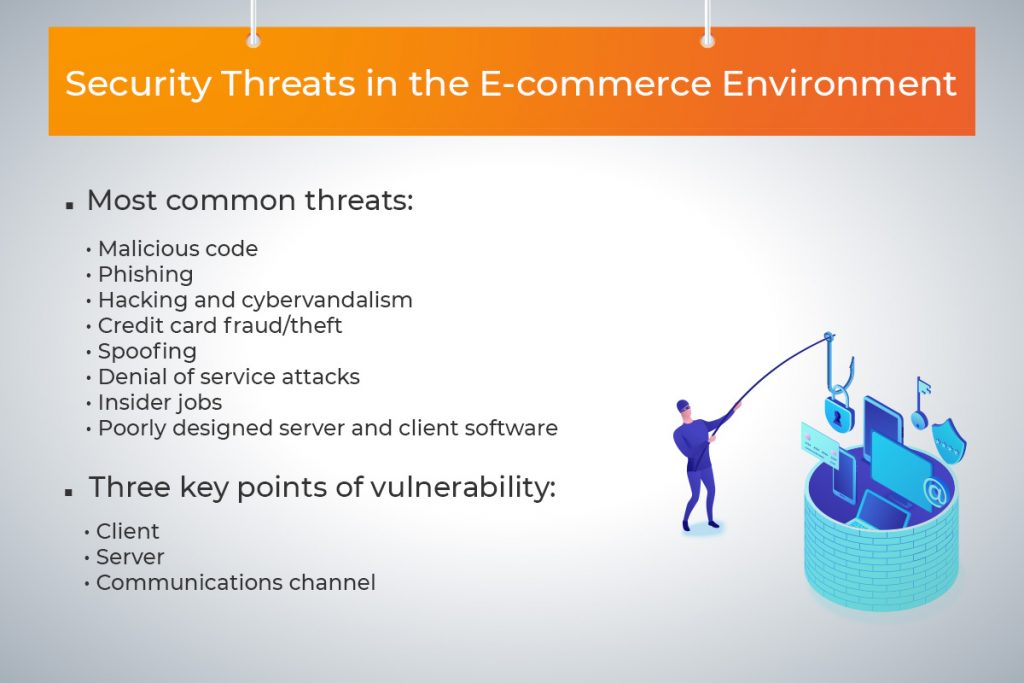
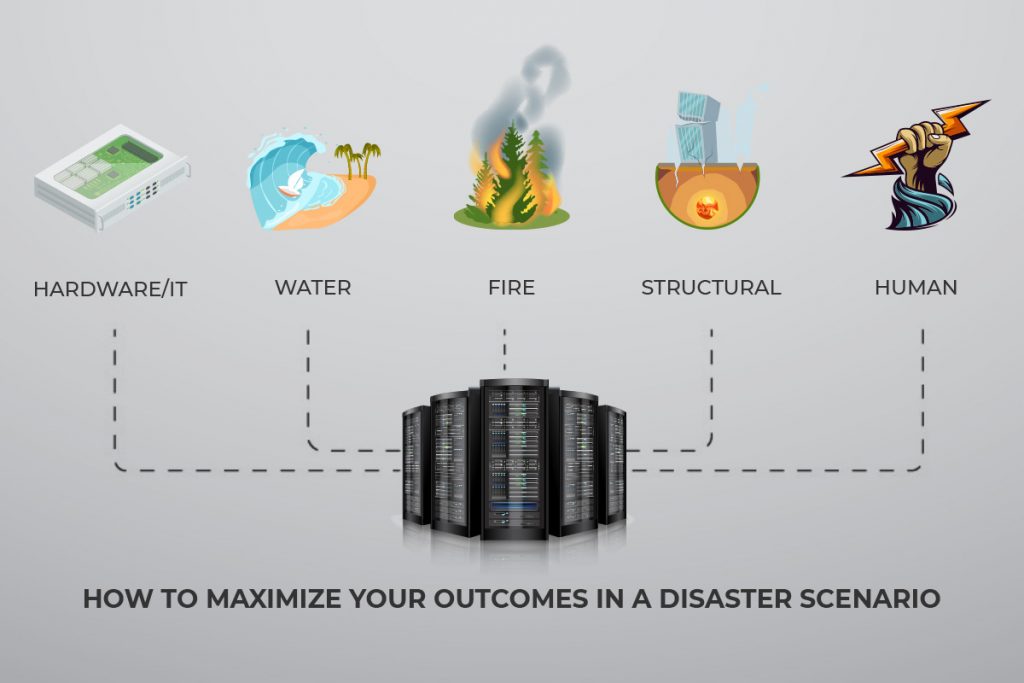
Chaos Engineering: How it Works, Principles, Benefits, & Tools
Finding faults in a distributed system goes beyond the capability of standard application testing. Companies need smarter ways to test microservices continuously. One strategy that is gaining popularity is chaos engineering.
Using this proactive testing practice, an organization can look for and fix failures before they cause a costly outage. Read on to learn how chaos engineering improves the reliability of large-scale distributed systems.
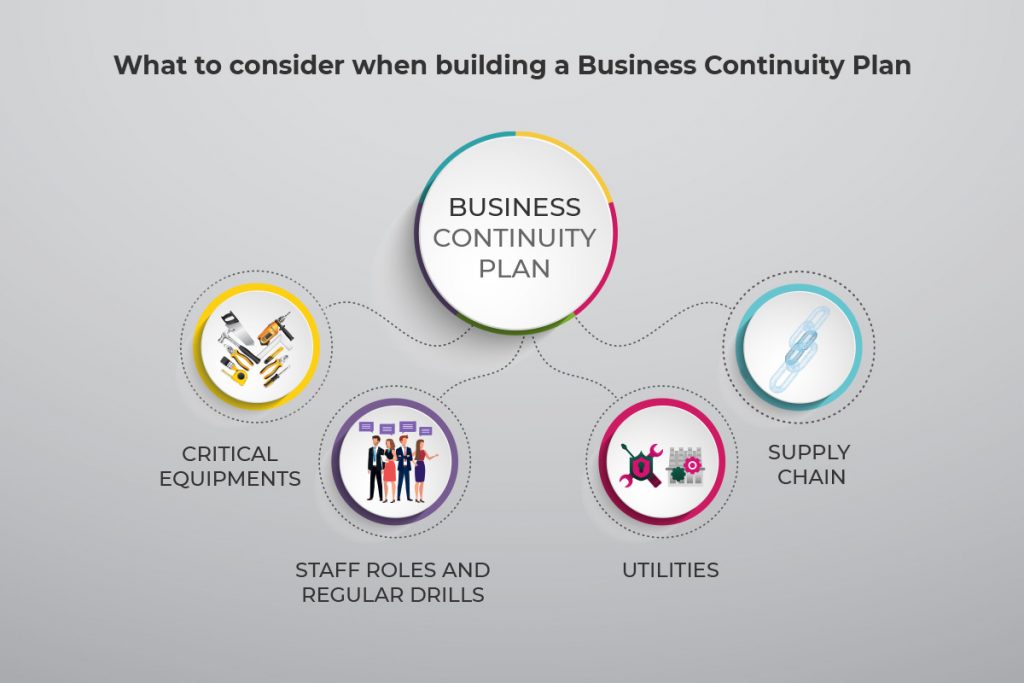
What Is Chaos Engineering? Defined
Chaos engineering is a strategy for discovering vulnerabilities in a distributed system. This practice requires injecting failures and errors into software during production. Once you intentionally cause a bug, monitor the effects to see how the system responds to stress.
By “breaking things” on purpose, you discover new issues that could impact components and end-users. Address the identified weaknesses before they cause data loss or service impact.
Chaos engineering allows an admin to:
- Identify weak points in a system.
- See in real-time how a system responds to pressure.
- Prepare the team for real failures.
- Identify bugs that are yet to cause system-wide issues.
Netflix was the first organization to introduce chaos engineering. In 2010, the company released a tool called Chaos Monkey. With this tool, admins were able to cause failures in random places at random intervals. Such a testing approach made Netflix’s distributed cloud-based system much more resilient to faults.
Who Uses Chaos Engineering?
Many tech companies practice chaos engineering to improve the resilience of distributed systems. Netflix continues to pioneer the practice, but companies like Facebook, Google, Microsoft, and Amazon have similar testing models.
More traditional organizations have caught on to chaos testing too. For example, the National Australia Bank applied chaos to randomly shut down servers and build system resiliency.
The Need for Chaos Engineering
Peter Deutsch and his colleagues from Sun Microsystem listed eight false assumptions programmers commonly make about distributed systems:
- The network is reliable.
- There is zero latency.
- Bandwidth is infinite.
- The network is secure.
- Topology never changes.
- There is one admin.
- Transport cost is zero.
- The network is homogeneous.
These fallacies show the dynamics of a distributed application designed in a microservices architecture. This kind of system has many moving parts, and admins have little control over the cloud infrastructure.
Constant changes to the setup cause unexpected system behavior. It is impossible to predict these behaviors, but we can reproduce and test them with chaos engineering.
Difference Between Chaos Engineering and Failure Testing
A failure test examines a single condition and determines whether a property is true or false. Such a test breaks a system in a preconceived way. The results are usually binary, and they do not uncover new information about the application.
The goal of a chaos test is to generate new knowledge about the system. Broader scope and unpredictable outcomes enable you to learn about the system’s behaviors, properties, and performance. You open new avenues for exploration and see how you can improve the system.
While different, chaos and failure testing do have some overlap in concerns and tools used. You get the best results when you use both disciplines to test an application.
How Chaos Engineering Works
All testing in chaos engineering happens through so-called chaos experiments. Each experiment starts by injecting a specific fault into a system, such as latency, CPU failure, or a network black hole. Admins then observe and compare what they think will occur to what actually happens.
An experiment typically involves two groups of engineers. The first group controls the failure injection, and the second group deals with the effects.
Here is a step-by-step flow of a chaos experiment:
Step 1: Creating a Hypothesis
Engineers analyze the system and choose what failure to cause. The core step of chaos engineering is to predict how the system will behave once it encounters a particular bug.
Engineers also need to determine critical metric thresholds before starting a test. Metrics typically come in two sets:
- Key metrics: These are the primary metrics of the experiment. For example, you can measure the impact on latency, requests per second, or system resources.
- Customer metrics: These are precautionary metrics that tell you if the test went too far. Examples of customer metrics are orders per minute, or stream starts per second. If a test begins impacting customer metrics, that is a sign for admins to stop experimenting.
In some tests, the two metrics can overlap.
Step 2: Fault Injection
Engineers add a specific failure to the system. Since there is no way to be sure how the application will behave, there is always a backup plan.
Most chaos engineering tools have a reverse option. That way, if something goes wrong, you can safely abort the test and return to a steady-state of the application.
Step 3: Measuring the Impact
Engineers monitor the system while the bug causes significant issues. Key metrics are the primary concern but always monitor the entire system.
If the test starts a simulated outage, the team looks for the best way to fix it.
Step 4: Verify (or Disprove) Your Hypothesis
A successful chaos test has one of two outcomes. You either verify the resilience of the system, or you find a problem you need to fix. Both are good outcomes.
Principles of Chaos Engineering
While the name may suggest otherwise, there is nothing random in chaos engineering.
This testing method follows strict principles, which include the following principles:
Know the Normal State of Your System
Define the steady-state of your system. The usual behavior of a system is a reference point for any chaos experiment. By understanding the system when it is healthy, you will better understand the impact of bugs and failures.
Inject Realistic Bugs and Failures
All experiments should reflect realistic and likely scenarios. When you inject a real-life failure, you get a good sense of what processes and technologies need an upgrade.
Test in Production
You can only see how outages affect the system if you apply the test to a production environment.
If your team has little to no experience with chaos testing, let them start experimenting in a development environment. Test the production environment once ready.
Control the Blast Radius
Always minimize the blast radius of a chaos test. As these tests happen in a production environment, there is a chance that the test could affect end-users.
Another standard precaution is to have a team ready for actual incident response, just in case.
Continuous Chaos
You can automate chaos experiments to the same level as your CI/CD pipeline. Constant chaos allows your team to improve both current and future systems continuously.
Benefits of Chaos Engineering
The benefits of chaos engineering span across several business fronts:
Business Benefits
Chaos engineering helps stop large losses in revenue by preventing lengthy outages. The practice also allows companies to scale quickly without losing the reliability of their services.
Technical Benefits
Insights from chaos experiments reduce incidents, but that is not where technical benefits end. The team gets an increased understanding of system modes and dependencies, allowing them to build a more robust system design.
A chaos test is also excellent on-call training for the engineering team.
Customer Benefits
Fewer outages mean less disruption for end-users. Improved service availability and durability are the two chief customer benefits of chaos engineering.
Chaos Engineering Tools
These are the most common chaos engineering tools:
- Chaos Monkey: This is the original tool created at Netflix. While it came out in 2010, Chaos Monkey still gets regular updates and is the go-to chaos testing tool.
- Gremlin: Gremlin helps clients set up and control chaos testing. The free version of the tool offers basic tests, such as turning off machines and simulating high CPU load.
- Chaos Toolkit: This open-source initiative makes tests easier with an open API and a standard JSON format.
- Pumba: Pumba is a chaos testing and network emulation tool for Docker.
- Litmus: A chaos engineering tool for stateful workloads on Kubernetes.
To keep up with new tools, bookmark the diagram created by the Chaos Engineering Slack Community. Besides the tools, the chart also keeps track of known engineers working with chaos tests.
Chaos Engineering Examples
There are no limits to chaos experiments. The type of tests you run depends on the architecture of your distributed system and business goals.
Here is a list of the most common chaos tests:
- Simulating the failure of a micro-component.
- Turning a virtual machine off to see how a dependency reacts.
- Simulating a high CPU load.
- Disconnecting the system from the data center.
- Injecting latency between services.
- Randomly causing functions to throw exceptions (also known as function-based chaos).
- Adding instructions to a program and allowing fault injection (also known as code insertion).
- Disrupting syncs between system clocks.
- Emulating I/O errors.
- Causing sudden spikes in traffic.
- Injecting byzantine failures.
Chaos Engineering and DevOps
Chaos engineering is a common practice within the DevOps culture. Such tests allow DevOps to thoroughly analyze applications while keeping up with the tempo of agile development.
DevOps teams commonly use chaos testing to define a functional baseline and tolerances for infrastructure. Tests also help create better policies and processes by clarifying both steady-state and chaotic outputs.
Some companies prefer to integrate chaos engineering into their software development life cycle. Integrated chaos allows companies to ensure the reliability of every new feature.
A Must for any Large-Scale Distributed System
Continuous examination of software is vital both for application security and functionality. By proactively examining a system, you can reduce the operational burden, increase system availability, and resilience.
Recent Posts
How Kerberos Authentication Works
In traditional computer systems, users prove their identities by typing in passwords. While easy to set up, this authentication method has a severe flaw. If hackers steal or crack the password, it is easy to take on the user’s identity. Intruders log in as the real user, and the system is wide open to an attack.
Kerberos authentication protects user credentials from hackers. This protocol keeps passwords away from insecure networks at all times, even during user verification.
Read on to learn what Kerberos authentication is and how it protects both end-users and systems.
What is Kerberos?
Kerberos is an authentication protocol for client/server applications. This protocol relies on a combination of private key encryption and access tickets to safely verify user identities.
The main reasons for adopting Kerberos are:
- Plain text passwords are never sent across an insecure network.
- Every login has three stages of authentication.
- Encryption protects all access keys and tickets.
- Authentication is mutual, so both users and providers are safe from scams.
MIT developed the first instances of Kerberos in the late ’80s. The protocol was named after Cerberus, a creature from Greek mythology. Cerberus was a ferocious three-headed dog who guarded Hades.
A refined version of Kerberos came out of Microsoft as part of Windows 2000. Since then, Kerberos became Windows’ default authorization protocol. Implementations of Kerberos also exist for Apple OS, FreeBSD, UNIX, and Linux. The Kerberos Consortium treats the protocol as an open-source project.
Three Main Components of Kerberos
Every Kerberos verification involves a Key Distribution Center (KDC). The KDC acts as a trusted third-party authentication service, and it operates from the Kerberos server. KDC consists of three main components:
- An authentication server (AS): The AS performs initial authentication when a user wants to access a service.
- A ticket granting server (TGS): This server connects a user with the service server (SS).
- A Kerberos database: This database stores IDs and passwords of verified users.
All Kerberos authentications take place in Kerberos realms. A realm is a group of systems over which a KDC has the authority to verify users and services.
 How Kerberos Authentication Works
How Kerberos Authentication Works
With Kerberos, users never authenticate themselves to the service directly. Instead, they go through a series of steps performed by different parts of the Key Distribution Center.
The AS Verifies Users with Decryption
The Kerberos protocol starts with the user requesting access to a service through the Authentication Server. This request is partially encrypted with a secret key, the user’s password. The password is a shared secret between the user and the AS.
The AS can only decrypt the request if the user encrypted the message with the right password. If the password is wrong, the AS cannot interpret the request. In that case, AS does not verify the user, and the authentication process fails.
Once it decrypts the request, the AS creates a ticket-granting ticket (TGT) and encrypts it with the TGS’s secret key. This key is a shared secret between the AS and the Ticket Granting Server.
A TGT contains a client/TGS session key, an expiration date, and the client’s IP address. The IP address protects from man-in-the-middle attacks. Once it issues a TGT, the AS sends it to the user.
The TGS Connects Users to Service Servers
The user sends the TGT to the TGS. If the ticket is valid and the user has permission to access the service, the TGS issues a service ticket.
A service ticket contains the client ID, client network address, validity period, and client/server session key. The service ticket is encrypted with a secret key shared with the service server.
The user then sends the ticket to the service server along with the service request. The SS decrypts the key and grants access to the requested resources.
Verification Without Plain Text Passwords
During the entire verification process, a plain text password never reaches the KDC or the service server. Encryption protects all three sets of temporary private keys.
Kerberos works both with symmetric and asymmetric (public-key) cryptography. The protocol can also handle multi-factor authentication (MFA).
Remote work may expose vulnerabilities to potential attacks. Learn how to secure remote access to computer systems.
Kerberos Authentication Steps
Kerberos Authentication is a multi-step process. Let us say a user wishes to access a network file server to read a document. Below are the steps required to authenticate through Kerberos:
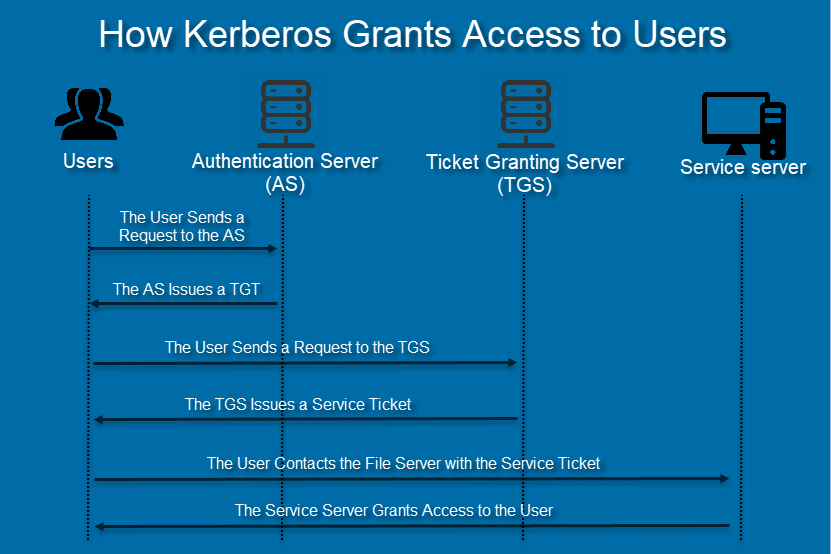
Step 1: The User Sends a Request to the AS
The user issues an encrypted request to the Authentication Server. When the AS gets the request, it searches for the password in the Kerberos database based on the user ID.
If the user typed in the correct password, the AS decrypts the request.
Step 2: The AS Issues a TGT
After verifying the user, the AS sends back a Ticket Granting Ticket.
Step 3: The User Sends a Request to the TGS
The user sends the TGT to the Ticket Granting Server. Along with the TGT, the user also explains the reason for accessing the file server.
The TGS decrypts the ticket with the secret key shared with the AS.
Step 4: TGS Issues a Service Ticket
If the TGT is valid, the TGS issues a service ticket to the user.
Step 5: The User Contacts the File Server with the Service Ticket
The client sends the service ticket to the file server. The file server decrypts the ticket with the secret key shared with TGS.
Step 6: The User Opens the Document
If the secret keys match, the file server allows the user to open the document. The service ticket determines how long the user has access to the record.
Once access expires, the user needs to go through the entire Kerberos authentication protocol again.
Kerberos Authentication Diagram
Benefits of Kerberos Authentication
These are the main benefits of adopting Kerberos:
Improved Security
Cryptography, multiple secret keys, and third-party authorization make Kerberos one of the industry’s most secure verification protocols.
User passwords are never sent across the network. Secret keys pass the system in encrypted form. If someone is logging conversations, it is hard to gather enough data to impersonate a user or the service.
Access Control
Kerberos is a crucial component of today’s enterprises. The protocol allows excellent access control.
With Kerberos, the company gets a single point for enforcing security policies and keeping track of logins.
Transparency and Auditability
Kerberos makes it easy to see who requested what and at what time. Transparent and precise logs are vital for security audits and investigations.
Mutual Authentication
Kerberos enables users and service systems to authenticate each other. At each step of the authentication process, both the user and the server systems know that they are interacting with authentic counterparts.
Limited Ticket Lifetime
All tickets in the Kerberos model have timestamps and lifetime data. Admins control the duration of the users’ authentication.
Short ticket lifetimes are great for preventing brute-force and replay attacks.
Scalability
Several technology giants have adopted Kerberos authentication, like Apple, Microsoft, and Sun. The adoption among enterprises speaks volumes about Kerberos’ ability to keep up with the demands of large companies.
Reusable Authentications
Kerberos authentications are reusable and durable. The user only verifies to the Kerberos system once. For the lifetime of the ticket, the user can authenticate to network services without re-entering personal data.
Single sign-on is the most direct end-user benefit of Kerberos.
Quick Fixes and Updates
Over the years, top programmers and security experts have tried to break Kerberos. This scrutiny ensures that any new weakness in the protocol is quickly analyzed and corrected.
Can Kerberos Be Hacked?
No security model is completely invulnerable, and Kerberos is no exception. As Kerberos is so widely used, hackers had ample opportunities to find ways around it.
The biggest threats to a Kerberos system are forged tickets, repeated attempts to guess a password and encryption downgrading malware. A combination of all three tactics is the usual recipe for successful breaches.
The most successful methods of hacking Kerberos include:
- Pass-the-ticket: A cyber attacker forges a session key and presents the fake credentials to reach the resources. Hackers usually forge a golden ticket (a ticket that grants domain admin access) or a silver ticket (a ticket that grants access to a service).
- Credential stuffing and brute-force attacks: Automated, continued attempts to guess a user password. Most brute-force attacks go after the initial ticketing and the ticket-granting service.
- Skeleton key malware: This malware bypasses Kerberos and downgrades key encryption. The attacker must have admin access to launch the cyberattack.
- DCShadow attack: This hack occurs when attackers gain enough access within the network to set up their own DC for further infiltration.
Despite these dangers, Kerberos remains the best security protocol available today. If users practice good password choice policies, the likelihood of hacks is minimal.
Weaknesses of Kerberos Authentication
While Kerberos effectively deals with security threats, the protocol does pose several challenges:
The Kerberos Server Is a Single Point of Failure
If the Kerberos server goes down, users cannot log in. Fallback authentication mechanisms and secondary servers are typical solutions to this problem.
Strict Time Requirements
Date/time configurations of the involved hosts must always be synchronized within predefined limits. Otherwise, authentications fail because tickets have a limited availability period.
Every Network Service Needs its Kerberos Keys
Each network service that requires a different hostname needs its set of Kerberos keys. Issues with virtual hosting and clusters are not uncommon.
All Nodes Must Be Compatible with Third-Party Authentication
Both user machines and service servers must be designed with Kerberos authentication in mind.
Some legacy systems and local packages are not compatible with third-party authentication mechanisms.
An Old, But By No Means an Outdated Protocol
Cybercrime is an unfortunate element of today’s fiber interconnectivity. Experts predict that the average cost of a data breach for large enterprises will be more than $150 million in 2020. Forbes predicts that an increasing number of criminals will soon be using Artificial Intelligence (AI) to scale and better their attacks.
The cybercrime problem is not going away anytime soon. Kerberos authentication is an excellent way for a company to protect its assets both now and as threats become more advanced.
Recent Posts
What is Managed Detection and Response (MDR Security)?
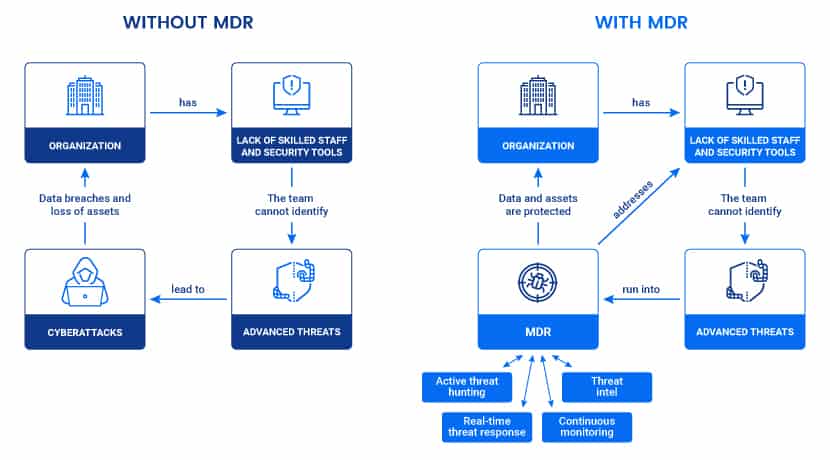
Maintaining high levels of cybersecurity is expensive. To run security operations, companies must invest in skilled staff and set aside resources for the right tools and devices.
Managed Detection and Response (MDR) services are a cost-effective alternative to running an in-house security team.
This article provides everything you need to know about MDR security. Learn how Managed Detection and Response provides real-time protection without the expenses of a fully-staffed internal team.
What is Managed Detection and Response in Cybersecurity?
Managed Detection and Response (MDR) is an outsourced service that monitors a network for malicious activity. MDR offers proactive threat hunting to remove intrusions, data breaches, and malware before an attacker can strike.
It combines analytics and human expertise to detect and eliminate threats in the network. The standard scope of MDR security includes:
- Threat detection: Constant monitoring of data and filtering alerts for analysis.
- Threat analysis: Examining a potential threat to discover its origin, scope, and risk level.
- Incident response: Notifying the client about the issue and removing the threat.
While less expensive than an internal team, MDR provides everything needed to keep a network secure:
- 24/7 monitoring
- Careful alert and incident analysis
- Quick and efficient threat response
- Threat hunting
- Strong threat intelligence
- Damage reduction from successful attacks and breaches
The service provider configures and provides the tools needed for MDR. Once set up, MDR tools analyze event logs and guard gateways to detect threats that evade typical security levels.
phoenixNAP implemented multiple security layers, including MDR, to design the world's safest Cloud computing platform - Data Security Cloud.
Developed in collaboration with VMware and Intel, Data Security Cloud is a cloud infrastructure platform that leverages the latest MDR practices to ensure advanced data protection, vulnerability scanning, and endpoint protection.
While tools play a significant role, Managed Detection and Response primarily relies on humans for network monitoring. Tools filter event logs and detect potential Indicators of Compromise (IoC). Once a threat is recognized, human operators take over and remove the danger.
What is Threat Hunting in Cybersecurity?
Threat hunting in cybersecurity is a proactive approach to detecting, isolating, and removing threats. The main goal of threat hunting is to find malicious elements that evade automated security solutions.
Cyber threat hunting focuses on searching and eliminating threats before the attack occurs. This security measure does not involve addressing incidents that already took place.
Once malicious elements are located, threat hunters analyze the issue’s behavior and methods before neutralizing it. Threat hunting also involves identifying trends in attacks to prevent future breaches.
Threat hunting relies on human analysts. Tools speed up processes and repetitive tasks, but human operators make all crucial decisions.
MDR Is Growing in Popularity
When a company expands its IT system, there is a rise in network endpoints like laptops, desktops, and mobile devices. Each new endpoint creates a potential entry point for hackers.
Between constant monitoring and threat hunting, MDR is an excellent method of protecting endpoints. The ability to quickly secure entry points is why Managed Detection and Response is popular among enterprises. Large companies regularly add new devices to their systems, so defending endpoints is a big concern.
Enterprise Strategy Group (ESG) recently surveyed employees from mid-to-large enterprises to examine critical problems related to threat detection and responses.
Below are some exciting discoveries from the ESG research:
- 77% of security experts said that managers are pressuring them to improve threat detection and response tactics.
- According to 76% of companies, security analytics is more complex than two years ago.
- 58% of businesses cited employee skills as the main problem for improving security.
- Manual processes and alert fatigue are viewed as a critical issue by 70% of companies.
Add to those numbers the lack of capable staff on the market, and it becomes easy to see why there is an increase in demand for MDR.
What Problems Does MDR Solve?
Managed Detection and Response solves several common problems security teams face:
High Alert Volume
Too many alerts can overwhelm a small security team. Alert fatigue leads to inadequate monitoring, causes workers to neglect other tasks, and leaves a network open to an attack.
Managed Detection and Response helps handle the volume of alerts that need to be checked individually. Once set up, MDR security does all the monitoring in the system, leaving the staff with ample time to focus on other duties.
Threat Analysis
It is hard to identify severe threats from alert noise. A malicious element may appear to be a random alert, while common errors can raise red flags across the system. To determine the cause, scope, and status of a problem, an IT team must analyze the situation.
By investing in MDR, a company secures advanced analytics tools and security experts capable of interpreting events in the network.
Advanced Attacks and Breaches
A poorly trained IT team can struggle when faced with an advanced threat.
MDR providers are staffed with security specialists capable of keeping up with cyberattacks. By investing in MDR security, you ensure the industry’s best talent monitors your networks and devices.
Endpoint Detection and Response (EDR)
Businesses often lack funds, time, or skills to train operators to use EDR tools properly. MDR services come with high-end EDR tools and the personnel who know how to use them. EDR tools are integrated into detection and response processes, removing the need for in-house endpoint protection.
Benefits of MDR Security
Standard tools for cybersecurity are good at stopping simple breaches and attacks. However, preventive tactics are not enough to secure an entire infrastructure.
MDR offers a thorough method of ensuring network safety. Instead of focusing solely on prevention, MDR goes after threats before they get an opportunity to cause damage.
Better Overall Approach to Security
Managed Detention and Response detects, analyzes, and stops threats, offering a comprehensive security solution.
When an MDR tool detects a problem, the team first verifies the validity of the threat. If the issue has a malicious cause, operators inform you about the situation and eliminate the threat.
Isolating the threat is another significant aspect of MDR. If a potential attack is spotted, the issue is contained within a single system. The threat is then unable to spread to other sectors of the network. That way, MDR reduces damage from successful breaches.
No False Alarms
When a standard security control runs into an alert, it sends unchecked alerts to operators. The process of separating false signals from real dangers wastes time and resources.
MDR performs an in-depth investigation of every suspicious activity in the network. Each threat is analyzed to check its status. Alerts that reach the security team require immediate action, so there are no pointless distractions.
Fast, Seamless Deployment
Setting up a custom detection and response system requires time. One would need to license software tools, set up the system, create procedures and security policies, and train the staff.
MDR solutions require little configuring and follow cybersecurity best practices.
Swift Detection of Threats
The quicker a threat is detected and dealt with, the easier and cheaper it is to remove it. Without MDR security, it takes an average of 280 days to identify and contain a breach.
Managed Detection and Response improves detection levels and reduces dwell time of breaches.
Easier Compliance
All major MDR providers ensure their defense procedures are compliant with regulatory bodies. Your MDR partner can help review processes and implement best practices.
Managed Detection and Response (MDR) vs. Managed Security Services Providers (MSSP)
While the two types of service share similarities, there are differences between MDR and MSSP regarding tools, expertise, and objectives.
Here is a comparison between what typical MDR and MSSP services include:
MDR vs. MSSP Security Services
| Managed Detection and Response | Managed Security Services Providers | |
|---|---|---|
| 24/7 threat detection
|
Yes | Yes |
| Firewalls and other perimeter security infrastructure
|
Yes | Yes |
| Proactive threat hunting
|
Yes | Yes |
| Threat forensics
|
Yes | Yes |
| Responding to attacks
|
Yes | Yes |
| Portals and dashboards are a primary line of communication
|
No | Yes |
| An on-call team of experts
|
Yes | Yes |
| Deep threat intelligence and analysis
|
Yes | No |
| Use of AI and machine learning
|
Yes | Yes |
| Integrated endpoint security
|
Yes | No |
| Compliance Checks
|
No | Yes |
| Vulnerability Hunting
|
No | Yes |
MDR security focuses on detecting and responding to potential malicious elements. MSSP is reactive and focuses on finding and eliminating vulnerabilities and compliance issues. Both types of service play a role in the modern IT landscape, and the better option entirely depends on the use case.
An MSSP system monitors network security controls and sends alerts when it detects an anomaly. It then forwards the report to the assigned IT staff, who inspects the data to analyze and remove any danger. In that regards, an MSSP secures infrastructure on more levels.
It is possible to use MSSP and MDR services at the same time. A company can rely on MSSP to run firewalls and other day-to-day operations. At the same time, MDR can detect and analyze advanced threats.
Does Artificial Intelligence (AI) Play a Role in MDR?
Applying AI to security problems is still in its early stages. Now, and for the foreseeable future, the only reliable security expert is a human operator.
Managed Detection and Response can leverage AI to speed up cyber defense algorithms. For example, advanced threat detection can rely on AI to filter through network events and identify unusual activities. An analyst then reviews to check whether the system ran into a security alert or false alarm.
AI-powered security tools also ensure fast incident-response times. An MDR provider uses AI and machine learning to investigate recurring events, auto-contain threats, and initiate reactions.
Managed Detection and Response for a Secure Cloud
An increasing number of businesses are opting for MDR services. The benefits are clear: threat control, better response times, less downtime, and lower costs of cyber protection.
PhoenixNAP offers the most well-rounded MDR solution on the market as a part of our Data Security Cloud offering. Accessible to both SMBs and enterprises alike, our Data Security Cloud ensures MDR protocols protect all your cloud activities. We provide the right talent and tools to proactively hunt and stop threats, ensuring you can focus on developing your business without distractions.
To learn how we can help you secure your workloads, contact one of our specialists today.
Recent Posts
7 Network Segmentation Security Best Practices
A network breach is an inevitable risk online. Attacks are bound to occur, and every network must be able to withstand a break-in. One cybersecurity mechanism stood out as very effective in limiting the damage in case of a network breach.
That cybersecurity technique is network segmentation.
Network segmentation can protect vital parts of the network during successful data breaches. If the system gets compromised, this defense mechanism limits the damage intruders can cause.
This article presents all the security benefits of network segmentation. You will learn how multi-layer protection can resist attacks and why segmentation is more reliable than flat network structures.
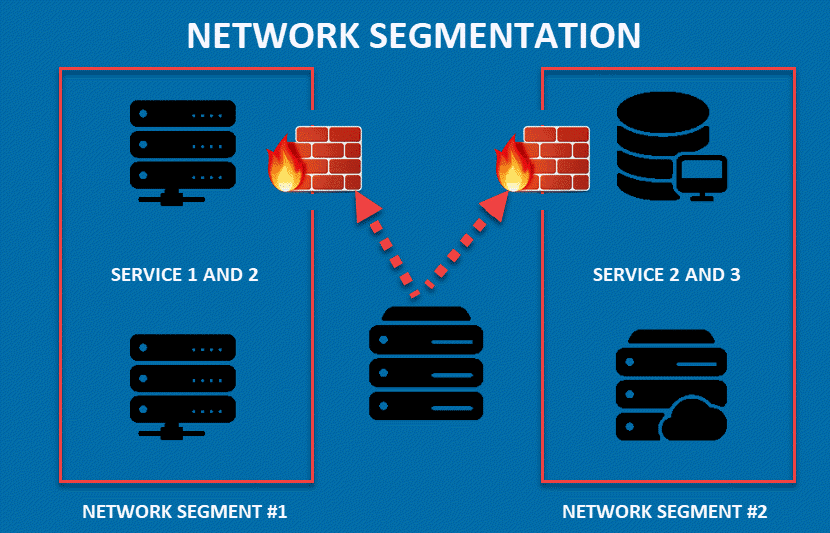
What is Network Segmentation?
Network segmentation is the process of dividing a network into smaller sections. These sections are created by placing barriers between parts of the system that don’t need to interact. For example, a company may create a subnet for its printers, or make a segment reserved for storing data.
Once you segment a network, every subnet functions as an independent system with unique access and security controls. Such network design allows you to control the flow of data traffic between sections. You can stop all traffic in one segment from reaching another. Additionally, network engineers use network segmentation to filter the data flow by traffic type, source, or purpose.
Isolating parts of a network limits a threat’s ability to move freely through the system. If a section of the network gets breached, other segments are not compromised.
Types of Network Segmentation
Network engineers segment a network either physically or virtually. Let’s compare the two segmentation methods:
- Physical segmentation: To physically segment a network, each subnet needs to have its wiring, connection, and a type of firewall. Physical segmentation offers reliable protection, but it can be hard to apply on a large system.
- Virtual segmentation: This is the more common and affordable method of dividing a network. Different segments share the same firewalls, while switches manage the virtual local area network (VLAN).
Both segmentation methods have their pros and cons, but their effect is the same. You limit communication within the network and make it hard for a threat to attack more than one section.
Why Segment a Network?
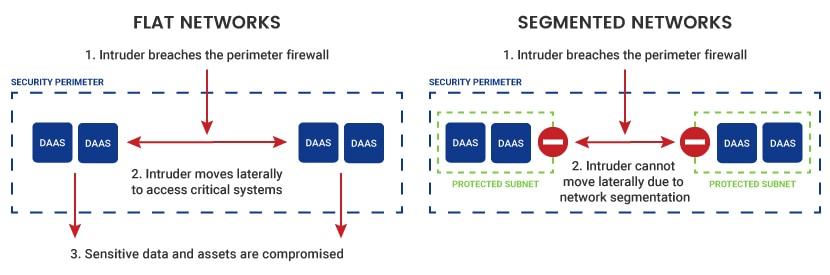
Standard flat networks are simple to manage, but they do not offer reliable protection. Firewalls monitor all incoming traffic in a flat network architecture, and the focus is on stopping attacks from outside the system. If hackers pass the perimeter and enter the network, nothing prevents them from accessing databases and critical systems.
Segmentation eliminates the flaws of flat networks. Segmenting a network also leads to better performance due to less congestion. With fewer hosts per subnet, a segmented network minimizes local traffic and reduces the “noise” in broadcast traffic.
Another benefit of a network segmentation policy is that it helps ease the compliance requirements. You can split a network into zones that contain data with the same compliance rules. Separate zones decrease the scope of compliance and simplify security policies.
Security Advantages of Network Segmentation
Of all the types of network security, segmentation provides the most robust and effective protection.
Network segmentation security benefits include the following:
1. Strong Data Protection
The more you control the traffic in a network, the easier it is to protect essential data. Segmentation builds a wall around your data caches by limiting the number of network sections that access them.
Fewer segments with access to data mean fewer points of access for hackers to steal anything of value. Between limited access and local security protocols, you reduce the risk of data loss and theft.
2. Threat Containment
If hackers breach a segmented network, they are contained within a single subnet. It takes time to break into the rest of the system.
As hackers try to force their way into other subnets, admins have time to upgrade the security of other segments. Once they stop the problem from spreading, admins can turn their attention to the breached section.
PhoenixNAP uses network micro-segmentation and machine learning and behavioral analytics in the world's most secure cloud platform - Data Security Cloud.
3. Limited Access Control
Segmentation protects from insider attacks by limiting user access to a single part of a network. This security measure is known as the Policy of Least Privilege. By ensuring only a select few can reach vital segments of the network, you limit the way hackers can enter critical systems.
The Policy of Least Privilege is vital as people are the weakest link in the network security chain. According to Verizon’s 2020 Data Breaches Report, over two-thirds of malware network breaches happen because of malicious emails.
A segmented network will keep intruders away from critical resources if a user’s credentials are stolen or abused.
4. Improved Monitoring and Threat Detection
Segmentation lets you add more points of network monitoring. More checks make it easier to spot suspicious behavior. Advanced monitoring also helps identify the root and scope of a problem.
Monitoring log events and internal connections enable admins to look for patterns in malicious activity. Knowing how attackers behave allows for a proactive approach to security and helps admins protect high-risk areas.
5. Fast Response Rates
Distinct subnets allow admins to respond to events in the network quickly. When an attack or an error occurs, it is easy to see which segments are affected. These insights help to narrow the focus area of troubleshooting.
Quick responses to events in the network can also improve user experience. Unless a subnet dedicated to users has been breached, customers will not feel the impact of an issue in a segmented network.
6. Damage Control
Network segmentation minimizes the damage caused by a successful cybersecurity attack. By limiting how far an attack can spread, segmentation contains the breach in one subnet and ensures the rest of the network is safe.
Network errors are also contained within a single subnet. The effects of an issue are not felt in other segments, making the error easier to control and fix.
7. Protect Endpoint Devices
Due to constant flow control, segmentation keeps malicious traffic away from unprotected endpoint devices. This benefit of network segmentation is becoming crucial as IoT devices become commonplace.
The endpoint device is both a usual target and starting point of cyberattacks. A segmented network isolates these devices, limiting the risk of exposure for the entire system.
Don’t Overlook The Importance of Network Segmentation
While network segmentation is not a novelty, it is by no means outdated. Between the cut in attack surface and traffic control, segmentation is among the best methods of stopping critical breaches.
Network segmentation is currently more a best practice model than a requirement. However, trends in industries with frequent cyberattacks — most notably the Payment Card Industry — suggest that segmentation could become a mandatory security measure. Whether that happens or not, the demand for subnets in some of the most regulated industries speaks volumes about the security benefits of network segmentation.
If you want to learn more about what it takes to secure a Cloud platform, read our Secure by Design Manifesto and discover how many security layers are necessary to design the most secure Cloud infrastructure in the world.
Recent Posts
8 Types of Firewalls: Guide For IT Security Pros
Are you searching for the right firewall setup to protect your business from potential threats?
Understanding how firewalls work helps you decide on the best solution. This article explains the types of firewalls, allowing you to make an educated choice.
What is a Firewall?
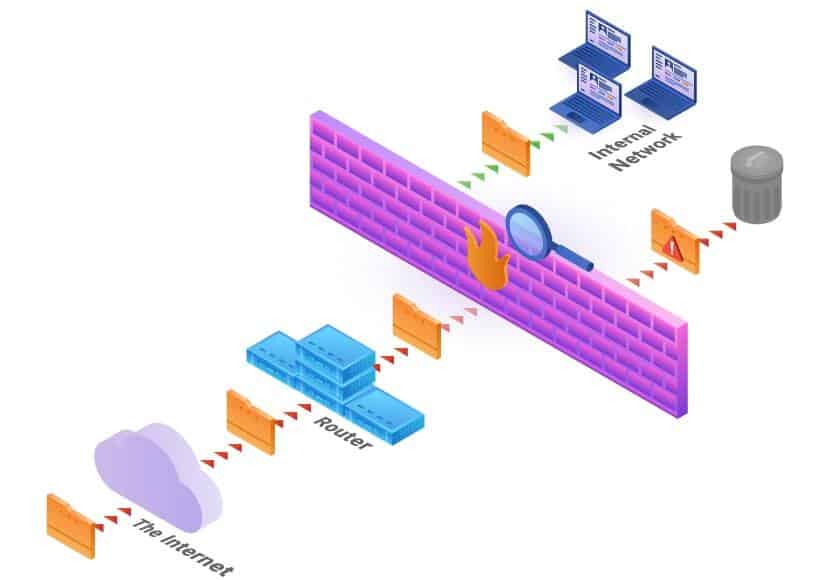
A firewall is a security device that monitors network traffic. It protects the internal network by filtering incoming and outgoing traffic based on a set of established rules. Setting up a firewall is the simplest way of adding a security layer between a system and malicious attacks.
How Does a Firewall Work?
A firewall is placed on the hardware or software level of a system to secure it from malicious traffic. Depending on the setup, it can protect a single machine or a whole network of computers. The device inspects incoming and outgoing traffic according to predefined rules.
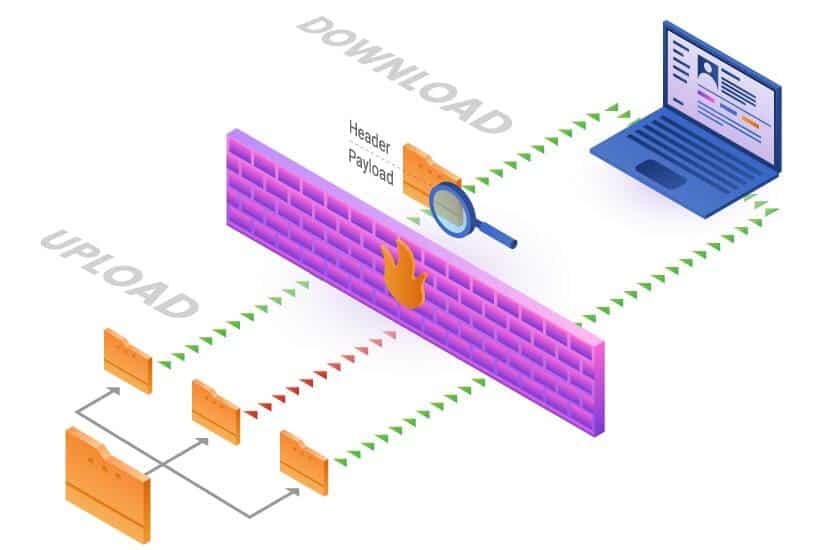
Communicating over the Internet is conducted by requesting and transmitting data from a sender to a receiver. Since data cannot be sent as a whole, it is broken up into manageable data packets that make up the initially transmitted entity. The role of a firewall is to examine data packets traveling to and from the host.
What does a firewall inspect? Each data packet consists of a header (control information) and payload (the actual data). The header provides information about the sender and the receiver. Before the packet can enter the internal network through the defined port, it must pass through the firewall. This transfer depends on the information it carries and how it corresponds to the predefined rules.
For example, the firewall can have a rule that excludes traffic coming from a specified IP address. If it receives data packets with that IP address in the header, the firewall denies access. Similarly, a firewall can deny access to anyone except the defined trusted sources. There are numerous ways to configure this security device. The extent to which it protects the system at hand depends on the type of firewall.
Types of Firewalls
Although they all serve to prevent unauthorized access, the operation methods and overall structure of firewalls can be quite diverse. According to their structure, there are three types of firewalls – software firewalls, hardware firewalls, or both. The remaining types of firewalls specified in this list are firewall techniques which can be set up as software or hardware.
Software Firewalls
A software firewall is installed on the host device. Accordingly, this type of firewall is also known as a Host Firewall. Since it is attached to a specific device, it has to utilize its resources to work. Therefore, it is inevitable for it to use up some of the system’s RAM and CPU.
If there are multiple devices, you need to install the software on each device. Since it needs to be compatible with the host, it requires individual configuration for each. Hence, the main disadvantage is the time and knowledge needed to administrate and manage firewalls for each device.
On the other hand, the advantage of software firewalls is that they can distinguish between programs while filtering incoming and outgoing traffic. Hence, they can deny access to one program while allowing access to another.
Hardware Firewalls
As the name suggests, hardware firewalls are security devices that represent a separate piece of hardware placed between an internal and external network (the Internet). This type is also known as an Appliance Firewall.
Unlike a software firewall, a hardware firewall has its resources and doesn’t consume any CPU or RAM from the host devices. It is a physical appliance that serves as a gateway for traffic passing to and from an internal network.
They are used by medium and large organizations that have multiple computers working inside the same network. Utilizing hardware firewalls in such cases is more practical than installing individual software on each device. Configuring and managing a hardware firewall requires knowledge and skill, so make sure there is a skilled team to take on this responsibility.
Packet-Filtering Firewalls
When it comes to types of firewalls based on their method of operation, the most basic type is the packet-filtering firewall. It serves as an inline security checkpoint attached to a router or switch. As the name suggests, it monitors network traffic by filtering incoming packets according to the information they carry.
As explained above, each data packet consists of a header and the data it transmits. This type of firewall decides whether a packet is allowed or denied access based on the header information. To do so, it inspects the protocol, source IP address, destination IP, source port, and destination port. Depending on how the numbers match the access control list (rules defining wanted/unwanted traffic), the packets are passed on or dropped.
If a data packet doesn’t match all the required rules, it won’t be allowed to reach the system.
A packet-filtering firewall is a fast solution that doesn’t require a lot of resources. However, it isn’t the safest. Although it inspects the header information, it doesn’t check the data (payload) itself. Because malware can also be found in this section of the data packet, the packet-filtering firewall is not the best option for strong system security.
***This table is scrollable horizontally.
| PACKET-FILTERING FIREWALLS | |||
| Advantages | Disadvantages | Protection Level | Who is it for: |
| – Fast and efficient for filtering headers.
– Don’t use up a lot of resources. – Low cost. |
– No payload check.
– Vulnerable to IP spoofing. – Cannot filter application layer protocols. – No user authentication. |
– Not very secure as they don’t check the packet payload. | – A cost-efficient solution to protect devices within an internal network.
– A means of isolating traffic internally between different departments. |
Circuit-Level Gateways
Circuit-level gateways are a type of firewall that work at the session layer of the OSI model, observing TCP (Transmission Control Protocol) connections and sessions. Their primary function is to ensure the established connections are safe.
In most cases, circuit-level firewalls are built into some type of software or an already existing firewall.
Like pocket-filtering firewalls, they don’t inspect the actual data but rather the information about the transaction. Additionally, circuit-level gateways are practical, simple to set up, and don’t require a separate proxy server.
***This table is scrollable horizontally.
|
CIRCUIT-LEVEL GATEWAYS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Resource and cost-efficient.
– Provide data hiding and protect against address exposure. – Check TCP handshakes. |
– No content filtering.
– No application layer security. – Require software modifications. |
– Moderate protection level (higher than packet filtering, but not completely efficient since there is no content filtering). | – They should not be used as a stand-alone solution.
– They are often used with application-layer gateways. |
Stateful Inspection Firewalls
A stateful inspection firewall keeps track of the state of a connection by monitoring the TCP 3-way handshake. This allows it to keep track of the entire connection – from start to end – permitting only expected return traffic inbound.
When starting a connection and requesting data, the stateful inspection builds a database (state table) and stores the connection information. In the state table, it notes the source IP, source port, destination IP, and destination port for each connection. Using the stateful inspection method, it dynamically creates firewall rules to allow anticipated traffic.
This type of firewall is used as additional security. It enforces more checks and is safer compared to stateless filters. However, unlike stateless/packet filtering, stateful firewalls inspect the actual data transmitted across multiple packets instead of just the headers. Because of this, they also require more system resources.
***This table is scrollable horizontally.
|
STATEFUL INSPECTION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Keep track of the entire session.
– Inspect headers and packet payloads. – Offer more control. – Operate with fewer open ports. |
– Not as cost-effective as they require more resources.
– No authentication support. – Vulnerable to DDoS attacks. – May slow down performance due to high resource requirements. |
– Provide more advanced security as it inspects entire data packets while blocking firewalls that exploit protocol vulnerabilities.
– Not efficient when it comes to exploiting stateless protocols. |
– Considered the standard network protection for cases that need a balance between packet filtering and application proxy. |
Proxy Firewalls
A proxy firewall serves as an intermediate device between internal and external systems communicating over the Internet. It protects a network by forwarding requests from the original client and masking it as its own. Proxy means to serve as a substitute and, accordingly, that is the role it plays. It substitutes for the client that is sending the request.
When a client sends a request to access a web page, the message is intersected by the proxy server. The proxy forwards the message to the web server, pretending to be the client. Doing so hides the client’s identification and geolocation, protecting it from any restrictions and potential attacks. The web server then responds and gives the proxy the requested information, which is passed on to the client.
***This table is scrollable horizontally.
|
PROXY FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Protect systems by preventing contact with other networks.
– Ensure user anonymity. – Unlock geolocational restrictions. |
– May reduce performance.
– Need additional configuration to ensure overall encryption. – Not compatible with all network protocols. |
– Offer good network protection if configured well. | – Used for web applications to secure the server from malicious users.
– Utilized by users to ensure network anonymity and for bypassing online restrictions. |
Next-Generation Firewalls
The next-generation firewall is a security device that combines a number of functions of other firewalls. It incorporates packet, stateful, and deep packet inspection. Simply put, NGFW checks the actual payload of the packet instead of focusing solely on header information.
Unlike traditional firewalls, the next-gen firewall inspects the entire transaction of data, including the TCP handshakes, surface-level, and deep packet inspection.
Using NGFW is adequate protection from malware attacks, external threats, and intrusion. These devices are quite flexible, and there is no clear-cut definition of the functionalities they offer. Therefore, make sure to explore what each specific option provides.
***This table is scrollable horizontally.
|
NEXT-GENERATION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Integrates deep inspection, antivirus, spam filtering, and application control.
– Automatic upgrades. – Monitor network traffic from Layer 2 to Layer 7. |
– Costly compared to other solutions.
– May require additional configuration to integrate with existing security management.
|
– Highly secure. | – Suitable for businesses that require PCI or HIPAA compliance.
– For businesses that want a package deal security device. |
Cloud Firewalls
A cloud firewall or firewall-as-a-service (Faas) is a cloud solution for network protection. Like other cloud solutions, it is maintained and run on the Internet by third-party vendors.
Clients often utilize cloud firewalls as proxy servers, but the configuration can vary according to the demand. Their main advantage is scalability. They are independent of physical resources, which allows scaling the firewall capacity according to the traffic load.
Businesses use this solution to protect an internal network or other cloud infrastructures (Iaas/Paas).
***This table is scrollable horizontally.
|
CLOUD FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Availability.
– Scalability that offers increased bandwidth and new site protection. – No hardware required. – Cost-efficient in terms of managing and maintaining equipment. |
– A wide range of prices depending on the services offered.
– The risk of losing control over security assets. – Possible compatibility difficulties if migrating to a new cloud provider. |
– Provide good protection in terms of high availability and having a professional staff taking care of the setup.
|
– A solution suitable for larger businesses that do not have an in-staff security team to maintain and manage the on-site security devices. |
Which Firewall Architecture is Right for Your Business?
When deciding on which firewall to choose, there is no need to be explicit. Using more than one firewall type provides multiple layers of protection.
Also, consider the following factors:
- The size of the organization. How big is the internal network? Can you manage a firewall on each device, or do you need a firewall that monitors the internal network? These questions are important to answer when deciding between software and hardware firewalls. Additionally, the decision between the two will largely depend on the capabilities of the tech team assigned to manage the setup.
- The resources available. Can you afford to separate the firewall from the internal network by placing it on a separate piece of hardware or even on the cloud? The traffic load the firewall needs to filter and whether it is going to be consistent also plays an important role.
- The level of protection required. The number and types of firewalls should reflect the security measures the internal network requires. A business dealing with sensitive client information should ensure that data is protected from hackers by tightening the firewall protection.
Build a firewall setup that fits the requirements considering these factors. Utilize the ability to layer more than one security device and configure the internal network to filter any traffic coming its way. For secure cloud options, see how phoenixNAP ensures cloud data security.
Recent Posts
What is a Brute Force Attack? Types & Examples
Brute force attacks are alluring for hackers as they are often reliable and simple.
Hackers do not need to do much of the work. All they have to do is create an algorithm or use readily available brute force attack programs to automatically run different combinations of usernames and passwords until they find the right combination. Such cyberattacks account for roughly 5 percent of all data breaches. According to statistics on data breaches, it only takes one data breach to create severe adverse implications for your business.
What is a Brute Force Attack?
The phrase “brute force” describes the simplistic manner in which the attack takes place. Since the attack involves guessing credentials to gain unauthorized access, it’s easy to see where it gets its name. Primitive as they are, brute force attacks can be very effective.
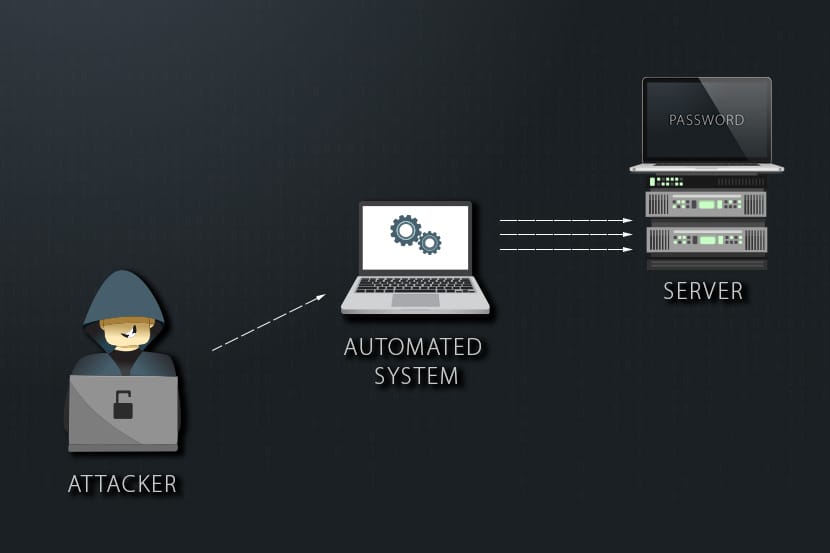
The majority of cyberattackers who specialize in brute force attacks use bots to do their bidding. Attackers will generally have a list of real or commonly used credentials and assign their bots to attack websites using these credentials.
Manual brute force cracking is time-consuming, and most attackers use brute force attack software and tools to aid them. With the tools at their disposal, attackers can attempt things like inputting numerous password combinations and accessing web applications by searching for the correct session ID, among others.
How Brute Force Attacks Work
In simple terms, brute force attacks try to guess login passwords. Brute force password cracking comes down to a numbers game.
For most online systems, a password is encouraged to be at least eight characters long. Most passwords are eight characters long but are often a mix of numeric and alphabetic (case sensitive) characters, which is 62 possibilities for a given character in a password chain. If we combine 62 options for every character in an eight-character password, the result would be 2.18 trillion possible combinations. That is a lot of combinations for a cyberattacker to try.
In the past, if a hacker tried to crack an eight-character password with one attempt per second, it would roughly take seven million years at most. Even if the hacker were able to attempt 1000 combinations per second, it would still take seven thousand years.
It’s a different story nowadays with brute force hacking software having the power to attempt vastly more combinations per second than mentioned above. For example, let’s say a supercomputer can input 1 trillion combinations per second. With that amount of power, a hacker can reduce the time it takes to try 2.18 trillion password/username combinations to just 22 seconds!
Computers manufactured within the last decade have advanced to the point where only two hours are necessary to crack an eight-character alphanumeric password. Many cyber attackers can decrypt a weak encryption hash in months by using an exhaustive key search brute force attack.
The example above applies to password combinations of 8 characters in length. The time it takes to crack a password varies depending on its length and overall complexity.
Why Hackers Use Brute Force Attacks?
Hackers use brute force attacks during initial reconnaissance and infiltration. They can easily automate brute force attacks and even run them in parallel to maximize their chances of cracking credentials. However, that is not where their actions stop.
Once they gain access to a system, attackers will attempt to move laterally to other systems, gain advanced privileges, or run encryption downgrade attacks. Their end goal is to cause a denial of service and get data out of the system.
Brute force attacks are also used to find hidden web pages that attackers can exploit. This attack can be programmed to test web addresses, find valid web pages, and identify code vulnerabilities. Once identified, attackers use that information to infiltrate the system and compromise data.
Brute force attack programs are also used to test systems and their vulnerability to such attacks. Furthermore, a targeted brute force attack is a last resort option for recovering lost passwords.
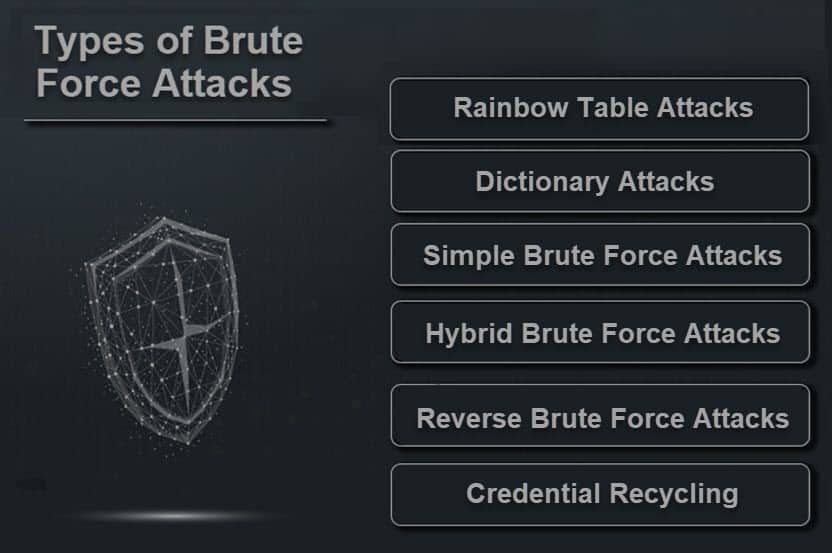
Types of Brute Force Attacks
Brute force cracking boils down to inputting every possible combination access is gained. However, there are variants of this kind of attack.
Dictionary Attack
A dictionary attack uses a dictionary of possible passwords and tests them all.
Instead of using an exhaustive key search, where they try every possible combination, the hacker begins from an assumption of common passwords. They build a dictionary of passwords and iterate the inputs.
With this approach, hackers eliminate having to attack websites randomly. Instead, they can acquire a password list to improve their chances of success.
Dictionary attacks often need a large number of attempts against multiple targets.
Simple Brute Force Attack
A simple brute force attack is used to gain access to local files, as there is no limit to the number of access attempts. The higher the scale of the attack, the more successful the chances are of entry.
Simple brute force attacks circulate inputting all possible passwords one at a time.
Hybrid Brute Force Attack
The hybrid brute force attack combines aspects of both the dictionary and simple brute force attack. It begins with an external logic, such as the dictionary attack, and moves on to modify passwords akin to a simple brute force attack.
The hybrid attack uses a list of passwords, and instead of testing every password, it will create and try small variations of the words in the password list, such as changing cases and adding numbers.
Reverse Brute Force Attack
The reverse brute force attack flips the method of guessing passwords on its head. Rather than guessing the password, it will use a generic one and try to brute force a username.
Credential Recycling
As it sounds, credential recycling reuses passwords. Since many institutions don’t use password managers or have strict password policies, password reuse is an easy way to gain access to accounts.
Because these cyberattacks depend entirely on lists of second-hand credentials gained from data breaches, they have a low rate of success. It’s essential to update usernames and passwords after a breach regularly, to limit the effectiveness of stolen credentials.
Rainbow Table Attacks
Rainbow table attacks are unique as they don’t target passwords; instead, they are used to target the hash function, which encrypts the credentials.
The table is a precomputed dictionary of plain text passwords and corresponding hash values. Hackers can then see which plain text passwords produce a specific hash and expose them.
When a user enters a password, it converts into a hash value. If the hash value of the inputted password matches the stored hash value, the user authenticates. Rainbow table attacks exploit this process.
If you’re concerned about impending cyber threats, a phoenixNAP consultant can walk you through our Data Security Cloud, the world's safest cloud with an in-built threat management system.
Examples of Brute Force Attacks
How common are brute force attacks?
Brute force attacks are so frequent that everyone, from individuals to enterprises operating in the online realm, has experienced such an attack. The organizations that have been hit the hardest in the last couple of years include:
- In 2018, Firefox’s master password feature was proven to be easily cracked with a brute force attack. It is unknown how many users’ credentials were exposed. In 2019. Firefox deployed a fix to resolve this issue.
- In March 2018, Magento was hit by a brute force attack. Up to 1000 admin panels had been compromised.
- In March 2018, several accounts of members of the Northern Irish Parliament had been compromised in a brute force attack.
- In 2016, a brute force attack resulted in a massive data leak in the e-Commerce giant, Alibaba.
- According to Kaspersky, RDP-related brute force attacks rose dramatically in 2020 due to the COVID-19 pandemic.
Every brute force attack’s end-goal attack is to steal data and/or cause a disruption of service.
How to Detect Brute Force Attacks
The key indication a bad actor is trying to brute force their way into your system is to monitor unsuccessful login attempts. If you see there have been many repeated failed login attempts, be suspicious. Watch for signs related to multiple failed login attempts from the same IP address and the use of multiple usernames from the same IP address.
Other signs can include a variety of unrecognized IP addresses unsuccessfully attempting to login to a single account, an unusual numerical or alphabetical pattern of failed logins, and multiple login attempts in a short time period.
It’s also possible for these cyberattacks to add you to a botnet that can perform denial-of-service attacks on your website. Aside from the above, spam, malware, and phishing attacks can all be the prerequisite of a brute force attack.
If you receive an email from your network service provider notifying you of a user from an unrecognized location logged into your system, immediately change all passwords and credentials.
In Conclusion, Stay Safe and Secure
The primitive nature of brute force attacks means there is an easy way to defend against them. The best defense against a brute force attack is to buy yourself as much time as you can, as these types of attacks usually take weeks or months to provide anything of substance to the hacker. The simplest precaution you can take to boost your accounts’ security is to use strong passwords.
It is also highly recommended to monitor servers and systems at all times. Utilizing a threat management system can significantly help as it detects and reports issues in real-time.
For more information, read our detailed knowledge base article on how to prevent brute force attacks.
Recent Posts
7 Best Practices For Securing Remote Access for Employees
How do you maintain security when employees work remotely, and your team is transitioning to a remote workforce?
As remote work is becoming a more prevalent trend in business and considering the recent COVID-19 outbreak, there’s no better time for employees and companies alike to make strides in securing remote work.
This guide aims to instruct employees and management of businesses, both small and large, of the tools and steps available to them.
Employing only one of the following security measures will not be enough to thwart cyber threats. Each security measure, in isolation, will not guarantee secure remote work; however, when used in tandem with multiple measures, it creates a compounding effect for your cybersecurity.
1. Develop a Cybersecurity Policy For Remote Workers
If your business allows remote work, you must have a clear cybersecurity policy in place so that every employee’s access to company data is secure. Without a strategy in place, any employee can easily become an entry-point for a hacker to hijack your organization’s network.
To prevent this from happening, create a cybersecurity policy stipulating guidelines complying with security protocols at home or travel. Policies may include the expected use of approved messaging programs with encryption, such as Signal or WhatsApp; updating and patching computer security schedules, like updating antivirus or anti-malware software; and protocols on remotely wiping devices if lost.
Company-owned Devices
If your business has the means to give its employees laptops, you should consider it. This strategy is the best way to secure remote work because you can have your IT department manually configure firewall settings and install antivirus and anti-malware.
Conduct Regular Back-ups to Hard Drives
Any business is as good as its data. Most companies nowadays store data online on cloud storage services that are protected by encryption; although, regularly backing-up to a physical drive is also encouraged, as they cannot be hacked remotely.
Third-Party Vendors
Direct employees aren’t the only ones who risk compromising your company’s internal network. Third-party vendors are also responsible for creating entry-points into system infrastructure; therefore, your policy should extend to them as well.
Target’s data breach is an example of a breach caused by excessive privileges from third-party vendors. The Target example illustrates the need for organizations to reform their policy when issuing privileges to third-parties; otherwise, they may inadvertently create weak links in their security.
With third-party vendors in mind, you can gain a better understanding of your third-party environment by taking inventory of all vendor connections. Once you have an idea, it’s possible to increase your security by monitoring and investigating vendor activity through conducting session recordings and looking for any sort of malicious activity or policy violation.
Service-Level Agreements
Provide a third-party vendor with a service-level agreement (SLA). This option will force vendors to adhere to your organization’s security policies; otherwise, they face penalties.
Eliminate Shared Accounts
A simple yet effective approach is to eliminate shared accounts among vendors. Without shared accounts, you decrease the risk of unauthorized access; this is yet another reason to invest in a password management tool.
Mobile Security
As business and life become more intertwined, employees often use their phones for work purposes. Although working from your mobile device can pose a security risk to your business.
Inform your employees of the danger of unsecured Wi-Fi networks. When using unsecured Wi-Fi, your phone is exposed to potential hackers looking to compromise your device. To prevent any unwanted intrusions, only use encrypted software to communicate.
It’s also best to restrict the use of applications on your mobile device when working. You can do this by delving into your phone’s permission settings for applications (app permissions).
Finally, turning off Bluetooth when working can limit paths to intrusion.
Network Border Protection
For large businesses, network traffic can be filtered to process the flow of legitimate traffic and block potential intruders looking to exploit your network. This filtering means you can analyze and prevent inbound requests that come from unauthorized IP addresses, as these are inherent risks to your system. Configuration blocking incoming requests from unknown sources can be set in your firewall’s inbound rules.
2. Choose a Remote Access Software
When telecommuting, there are three primary ways to secure your work online. Your options are using either remote computer access, virtual private networks, or direct application access. Each method has its benefits and drawbacks. Choose the method that works best for your organization.
Desktop Sharing
Remote PC access methods, such as desktop sharing, connect a remote computer to the host computer from a secondary location outside of the office. This setup means the operator has the ability to access local files on the host computer as if they were physically present in the office.
By logging in to third-party applications, an employee can turn a portable device into a display to access data on their office computer.
Even though the benefit of direct access exists, this kind of software carries a high risk of exposing the company’s internal network to danger because it creates an additional end-point for external threats to access the business’ local area network.
To combat potential risk, not only does the organization have to encrypt its firewalls and communications, the employee’s computer requires the same level of encryption. Depending on the size of your business, this option may be too costly to avail.
Applications such as LogMeIn, TeamViewer, and GoToMyPC provide this type of service.
Virtual Private Network
A virtual private network (VPN) is software that creates a secure connection over the internet by encrypting data. Through the process of using tunneling protocols to encrypt and decrypt messages from sender to receiver, remote workers can protect their data transmissions from external parties.
Most commonly, remote workers will use a remote access VPN client to connect to their organization’s VPN gateway to gain access to its internal network, but not without authenticating first. Usually, there are two choices when using VPNs: IP Security (IPsec) or Secure Sockets Layer (SSL).
IPsec VPNs are manually installed and configured on the remote device. They will require the operator to input details such as the gateway IP address of the target network as well as the security key to gain access to the corporate network.
SSL VPNs are newer and easier to install. Instead of manually installing the VPN, the network administrator publishes the VPN client to the company firewall and provides it for public download. Afterward, the employee can download the VPN client from a target web page.
The drawback of a VPN connection is any remote device that uses a VPN has the possibility of bringing in malware to the network it connects to.
If organizations plan to use VPNs for remote work, it’s in their best interest to have employees with remote devices to comply with its security policies.
VPN installation varies based on operating system and type; although, it is quite simple to do.
Direct Application Access
The lowest risk option for remote work is directly accessing work applications. Instead of accessing an entire network, employees can remotely work within individual applications on the network.
In using this method to work, there’s little risk in exposing a company’s internal network to cyber predation. Due to the use of granular, perimeter applications on the network’s infrastructure, there are limited attack surfaces for susceptible data breaches.
Direct application access highly limits the risk of bad actors; in the same vein, it constricts work to the confines of one application. With little connection to all the data on the company’s network, the amount of work an employee is capable of pales in comparison to the aforementioned remote access methods.
3. Use Encryption
As important as it is to choose an access method for your online workers, it’s equally important those methods use encryption to secure remote employees’ data and connections.
Simply put, encryption is the process of converting data into code or ciphertext. Only those who possess the key or cipher can decrypt and use the data.
Encryption software is an added layer of protection for businesses and remote workers. For instance, if a remote employee’s computer is lost or misplaced, and a malicious actor recovers it, encryption software is the first line of defense in deterring unauthorized access.
Advanced Encryption Standard
As it stands, most businesses have the security protocol to use Advanced Encryption Standard (AES) to secure data due to its compatibility with a wide variety of applications. It uses symmetric key encryption, meaning the receiver uses a key to decode the sender’s data. The benefit of its use over asymmetric encryption is it’s faster to use. Look for encryption software that uses AES to secure company data.
End-to-end Encryption
When it comes to using things like email and software for general communication, look for applications that use end-to-end encryption, as it uses incredibly strong encryption that cannot be hacked if the two end-points are secure.
4. Implement a Password Management Software
Since most data breaches occur due to the use of illegally acquired credentials, password management software is an invaluable solution to remote work security.
Random Password Generation
Password management software does vastly more than just store passwords; it can also generate and retrieve complex, random password combinations it stores in an encrypted database. With this power, businesses can entirely reduce the use of the same or similar passwords.
Having all similar passwords has far-reaching consequences. For example, if a bad actor obtains your username and password, they can use those credentials as potential logins for other applications or web properties. Suffice to say, humans tend to reuse passwords, with or without small variations, due to our limited memory capacity. Unique strong passwords can eliminate this from ever happening and the rabbit hole of consequence that follows.
Automated Password Rotation
Additionally, password management software can entail automated password rotation. As the name suggests, passwords are constantly reset to limit the time of potential use. By decreasing the lifespan of a password, sensitive data becomes less vulnerable to attack.
One-time-use Credentials
Another strategy you can utilize to protect your data with passwords is to create one-time-use credentials. To enact one-time-use credentials, create a log of passwords in a spreadsheet acting as a “safe.” When you a single-use password for business reasons, have the user label the password in the spreadsheet as “checked out.” Upon completion of the task, have the user check-in the password again and retire it.
5. Apply Two-factor Authentication
Authenticating the identity of a user is an essential aspect of access control. To gain access, typically, one would require a username and password. With two-factor authentication, you can increase remote work security by creating two requirements necessary for login instead of one. Essentially, it creates an added layer of login protection.
Two-factor authentication uses two pieces of information to grant access. It uses credentials such as username and password in conjunction with either a secret question or pin code, which goes to the user’s phone or email. This method makes it hard for malicious actors to access systems, as it’s unlikely they will have access to both pieces of information.
It is recommended businesses adopt this security measure for system log-ins.
6. Employ the Principle of Least Privilege
An effective method to mitigate security risk is to limit the privileges of your workers.
Network security privileges come in three flavors: super users, standard users, and guest users, with diminishing privileges in that order. Guest users have no bearing in this discussion, however.
Superusers are those who have full access to system privileges. They can issue changes across a network by completing actions such as installing or modifying software, settings, and user data. It is when superuser accounts fall into the wrong hands, and calamity occurs on the largest scale. Depending on which operating system you use, super users go by different names: administrator accounts in Windows systems and root accounts in Linux or Unix systems
The second user account of note is the standard user, also known as the least privileged user, and it has a limited set of privileges. This restricted account is the one you want your workers to use most of the time, especially if they don’t belong in your IT department.
As a precaution, we recommend having all employees use standard user accounts for routine tasks. Only give superuser privileges to trusted members of your IT team and have them only use these particular accounts to perform administrative duties when absolutely necessary. This approach, known as the principle of least privilege, dramatically eliminates the risk of a severe data breach by limiting excess.
Remove Orphaned Accounts
Orphaned accounts are problematic because they are old user accounts that contain data encompassing usernames, passwords, emails, and more. These accounts generally belong to former employees, who have no current connection to the company. These past employees may have moved on, but their accounts might still be on your network and remain accessible.
The problem is they are hard to see if your organization doesn’t know they exist. If you possess orphaned accounts on your network and external or internal threats find them, they can be used to escalate their privileges. These attacks are known as pass-the-hash (PtH) attacks. These insidious attacks leverage the use of low-level credentials to gain entry into your network and aim to steal the password hash from an admin account. If stolen, hackers can reuse the hash to unlock administrative access rights.
The best way to find and remove orphaned accounts, and any potential threats, is to use a privileged access management solution. These tools help to locate and remove lingering accounts.
7. Create Employee Cybersecurity Training
Internal personnel represents a large share of the danger facing a company’s network security. In fact, just over one-third of all data breaches in 2019 occurred due to a malicious or negligent employee.
That doesn’t have to be the case. Instead, businesses can alleviate the danger of insider threats by cultivating a security culture through training employees on cybersecurity best practices.
Physical Security of Devices
To begin, secure remote employees by encouraging them to lock computers when traveling physically. If there’s no physical access to their device, the chances of foul play remain low. Secondly, when employees work in public locations, instruct them to be aware of any onlookers when typing in sensitive information, such as logins or passwords. This phenomenon is called “shoulder surfing” and is more effective than it seems.
Instruct employees to always log-off or shut down their computers when not in use. Leaving a computer on that is not password-protected is as effective for system entry as any malware attack.
Lastly, if passwords get written down on paper, have your workers rip-up these papers instead of merely throwing them in the trash.
Safe Internet Protocols
If your business is unable to provide laptops or computers with internet restriction applications to remote staff, you can set guidelines for best practices in safe browsing, installing pop-up blockers, and downloading of trusted applications for work.
Social Engineering Attacks
Malicious actors that use human psychology to trick people into giving sensitive information are called social engineers. These social engineering attacks come in multiple forms; however, the most common are called phishing attacks.
Hackers design these attacks to mislead employees to a fake landing page to steal information or install malware that they use to compromise network security. Most commonly, phishing attacks occur from unsolicited emails. Therefore, train staff to never open unsolicited emails, click unknown links in messages and beware of attachments.
Secure Your Remote Workforce
In a globally decentralized business landscape, malicious actors will continually present a risk to business network security. It is with this danger in mind; businesses must take preventative measures in securing remote work for their employees or suffer the consequences. For more in-depth instruction watch our expert present more on Infrastructure Security for Remote Offices:
No matter the size of your business, there are affordable solutions you can exercise to protect your livelihood. If you need help in determining which option is best for your business, enlist the help of our experts today for a consultation. Hear one of our experts speak about the importance of Keeping a Tight Grip on Office 365 Security While Working Remotely.
Furthermore, learn about vulnerability assessment to complete the process of securing your network.
Recent Posts
5 Automated Security Testing Best Practices
Tech companies suffered countless cyber-attacks and data breaches in 2019 due to ‘compromised’ applications. Security defects in the code are now common occurrences because of rapid software development. Therefore, conducting traditional security tests do not suffice to provide full-proof protection against such attacks.
In the software world, there has never been a better time to integrate Application Security Tools into the Software Development Life Cycle (SDLC) mainly to lend support to development teams with regular and continuous security testing.
What is Automated Security Testing?
Automated testing is a practice (Read: tool) to reveal potential flaws or weaknesses during software development. Automated testing occurs throughout the software development process and does not negatively affect development time. The entire automated security testing process ensures that applications you are developing deliver the expected results and reveal any programming errors in the beginning.
Before we go further, do you know that almost 40% of all significant software testing is now automated?
Despite this, a significant amount of testing nowadays is conducted manually and at the development cycle’s final stages. Why? Because a large number of developers at the companies are not well-equipped to develop automated test strategies. The advantage of automated testing when developing software internally or for production is that you can use it to reveal potential weaknesses and flaws without slowing the development time.
DevSecOps
DevSecOps refers to an emerging discipline in this field. As software companies branch into new sectors such as wearables and IoT, there is a need for a thorough audit of all the current tools to combat security issues that may arise during the development process.
In this article, we are listing the general process and best practices of automated security testing.
-
Conducting a Software Audit:
The first step in automated security testing should begin with a complete audit of the software. During the audit, companies can quickly discover any significant risks emerging from the product. It is also the best way to integrate automation seamlessly into a client’s current workflow.
-
Seeking out Opportunities for Automation:
Since the past few years, companies are facing a strong push towards the automation of routine, repetitive, and mundane tasks. This wave of automation has come to the software testing world as well. In general practice, some primary factors determine if the company should automate a specific task or not. Factors like
If the tasks are straightforward: The very basic factor is the simplicity of the task. The Automation process should start with the simplest tasks available and slowly move towards covering more complex tasks. In companies, all complex tasks, at some point, still need human interaction. Some of the simple tasks include file and database system interactions.
If the tasks are repetitive and mundane: Automation is also ideal for those frequent tasks that are mundane and repetitive. With automated testing processes, you can also repeat a multitude of programmed actions to ensure the program’s consistency.
If the process is data-intensive: Automation is also helpful to comb through large volumes of data at once in an efficient and timely manner, making it ideal for data-intensive processes. To ensure that the correct use of data, testers can also use special automation tools to perform tests with even overwhelming sets of data.
Companies usually perform automated testing on some specific areas of software testing. Those areas include:
- Tools for code analysis: Code analysis tools can secure DevOps efforts, which automatically scan codes and identify any vulnerabilities present within the code itself. As a result, software teams receive some invaluable information while they work and identify problems before the quality assurance team.
- Scanning for appropriate configurations: Certain software tools can ensure the correct configuration of applications to use in specific environments, such as mobile environments or web-based environments.
- Application-level testing: During application-level testing, scanners such as OWASP Zap and Burb Intruder can also ensure that applications are not carrying out any malicious actions.
Bringing the Team on Board
Software teams are traditionally reluctant to integrate automation into their testing process. Why? Apart from the fear of change, the biggest reason is their wrong perception of the results’ accuracy. Many developers also consider automated testing more costly and time-consuming.
Automated security testing is NOT a replacement for manual testing in terms of accuracy. It is only a practice to automate the most mundane, tedious, and repetitive tasks in the testing processes.
Some issues that come up in automation do exist. These are risks in which a human needs to determine the logic that a computer would need to see the flaw. As an example, a system that gives every user permissions to modify and edit all files freely.
An automated system would have no way of knowing what the intended behavior is, nor would it have any idea of understanding the risk that this implies. This is where humans are introduced to the process.
It’s also why automated security testing should not replace manual testing, which is the only way to ensure thoroughness and accuracy.
Instead, it’s intended to automate the most tedious, mundane, and repetitive tasks associated with testing. Through this, the programming team can have more time to test the areas of the solution that requires manual testing, such as the program’s internal logic.
Another common issue with the software teams is the overestimation of the required time to develop an automated process. Modern software testing systems are not overly expensive or time-consuming owing to the number of frameworks and APIs available. The key is to find out what works for your organization or not, and that will ultimately save the organization time, money, and resources.
Selecting the Right Automation Tools
When choosing to automate the software testing process, developers have a myriad of choices to choose from, both commercial as well as open-source solutions. While Open source solutions are robust and have a well-maintained framework, they sometimes lack the advanced technology or customer service that comes with a commercial solution. Some of those tools are.
- Contrast Security: Contract Security is a runtime application security tool that runs inside applications to identify any potential faults.
- Burp Intruder: Burp Intruder is an infrastructure scanner, used to ensure whether applications are interacting correctly with the environment.
- OWASP ZAP: OWASP ZAP is an infrastructure scanner which is open-source in nature. It functions similarly to Burp Intruder.
- Veracode: Veracode refers to a code analysis tool to find vulnerabilities within an application structure.
- BDD Security: BDD Security is a test automation framework where users can employ natural language syntax to describe security functions as features.
- Mittn: Mittn is an open-source test automation framework that uses the Python programming language.
- Microsoft Azure Advisor: Microsoft Azure advisor is a cloud-based consultant service that provides recommendations according to an individual’s requirements.
- GauntIT: GauntIT is a test automation framework, ideal for those accustomed with Ruby development.
Depending on the company’s automation strategy, it may have to create custom scripting for their automation processes. The company’s network can use ‘Custom Scripting’ to make it more lightweight, customized, and optimized.
Custom scripting has the benefit of being tailored to your network security threats. However, it can be a hefty-cost solution, also requiring an internal development team. To make sure you choose the right solution for your needs, consider following the process in the image below:
Integrating Automated Testing Processes
The integration of automated testing processes to a company’s product pipeline is an iterative process. During the software development phase, there is continuous testing to find out potential risks and flaws. Processes like these ensure that the potential vulnerabilities do not remain unaddressed.
A significant chunk of the security-related testing occurs in the later stages of the production cycle, causing issues and delays to the product and the company. However, if the companies perform consistent testing, it leads to a more thoroughly secured product and avoids last-minute delays before release.
Breaking Large Projects into Smaller Steps
When working with large intensive projects, DevSecOps works well if the project consists of smaller, manageable steps. Instead of automating the entire solution at once, the formation of smaller automated processes within the larger production cycle leads to a better result.
Following this process would not only avoid any hiccups within the development cycle but also give developers the required time to adjust to newer automation standards. To acclimatized developers to the latest standards and to ensure training is in-depth and non-disruptive, introducing new tools one by one is also a good practice to follow.
Checking for Code Dependencies
The days of in-house coding has vanished mainly as most organizations do not develop codes in-house. They tend to use many third-party open-source codes for each application, which has some significant vulnerabilities. Organizations are thus required to automate their processes after identifying the code dependencies, ensuring that third-party code has no known vulnerabilities.
Testing against Malicious Attacks
Due to the rise of the rate of cybercrimes, applications should go through rigorous testing to prevent denial of service attacks (DDoS) and other malicious attacks. Broken solutions reveal some particular vulnerabilities, and this is why it is essential to conduct stringent tests on the application under challenging circumstances.
Organizations are seeing an increasing number of malicious attacks. These attacks may focus on any aspect of a client’s organization that is accessible from outside of the network. By regularly testing your application under particularly strenuous circumstances, you can secure it through various scenarios.
Training Development Team in Best Practices
In-depth training of programmers is also vital to avoid already identified vulnerabilities and flaws from occurring again in later production cycles. It is a proactive approach to make applications more inherently secure. This simple approach does not only improve the consistency of the product, but it also avoids costly modifications, if you discover flaws at the later stage.
As you identify vulnerabilities and flaws within your software solutions, programmers will need the training to avoid these issues in further production cycles.
Though the process of identifying issues is automated, the problems that are found should still be logged for the benefit of upcoming projects and future versions of the product. By training programmers proactively, an organization can, over time, make their applications more inherently secure.
Not only does this improve the consistency of the end product, but it also avoids costly modifications when flaws are discovered and require mitigation. Via training and company-wide messaging, developers can be trained on coding more securely.
If developers do not become apprised of issues, the same mistakes will continue to happen. Automated testing will not be as effective as it could be. It isn’t just cheaper and faster than manual testing; it’s also more consistent. Every test will run identically on each application and in each environment.
By automatically testing applications and identifying lax policies, the software life cycle for both on-premise and cloud-based web applications becomes shorter.
Through the years, organizations have still been manually testing their software security in-house or by professionals. However, by implementing automated testing as a standard practice, they can streamline their product deployment process to a high degree, reducing the overheads associated with the process. Regular training ensures that software teams are incorporating automation best practices into their processes.
Choosing Automated over Manual Testing
Automated testing is not only cheaper and faster than manual testing, but it is also much more consistent. It doesn’t make mistakes as each test runs identically on different applications and environments, and that can save you both time and money. Keeping manual tests in place only where human assessment is needed also conserves your company’s human resources.
To implement automated testing, organizations will require large-scale efforts to promote and apply best practices throughout their projects. Including training their software teams so they can incorporate it into their respective processes seamlessly. Need more detailed advice on how to automate security testing? Reach out to one of our experts today.
Next you should read
What is DevSecOps? Best Practices for Adoption
Software applications are the backbone of many industries. They power many businesses and essential services. A security lapse or failure in such an application can result in financial loss, as well as a tarnished reputation. In some extreme cases, it can even result in loss of life.
What is DevSecOps?
DevSecOps is the method that integrates security practices within the DevOps process. It creates and promotes a collaborative relationship between security teams and release engineers based on a ‘Security as Code’ philosophy. DevSecOps has gained popularity and importance, given the ever-increasing security risks to software applications.
DevSecOps integrates security within your product pipeline in an iterative process. It thoroughly incorporates security with the rest of the DevOps approach.
As teams develop software, testing for potential security risks and flaws is critical. Security teams must address issues before the solution can move ahead. This iterative process will ensure that vulnerabilities do not go unaddressed.
As DevSecOps is still a new and emerging discipline, it may require some time to gain mainstream acceptance and integration. A significant amount of security tests take place late in the production cycle. This delay can cause major issues for companies and their products. As security is usually is one of the last features considered in the development process. If you keep security at the end of the development pipeline, when security issues come up near launch, then you will find yourself back at the start of long development cycles.
When security concerns are raised late in the production cycle, teams will have to make significant changes to the solution before rolling it out. An interruption in production will ultimately lead to a delay in deliverables. Thus, ignoring security issues can lead to security debt later in the lifecycle of the product. This is an outdated security practice and can undo the best DevOps initiatives. So the DevSecOps goal is to begin the security team’s involvement as early as possible in the development lifecycle.
How Does DevSecOps Work?
The DevSecOps method needs development and operations teams to do more than just collaborate. Security teams also need to join in at an early stage of the iteration to ensure overall software security, from start to end. You need to think about infrastructure and application security from the start.
Not only does consistent testing lead to secure code, but it also avoids last-minute delays by spreading the work predictably and consistently throughout the project. Through this process, organizations can better achieve their deadlines and ensure that their customers and end-users are satisfied.
IT security needs to play an integrated role in your applications’ full life cycle. You can take advantage of the responsiveness and agility of a DevOps approach by the incorporation of security into your processes.
The primary areas of software security testing are being adopted:
Application security testing
As software applications are run, solutions can scan the application to ensure that malicious actions are not being taken. Scanners such as Burb Intruder and OWASP Zap automation will test and examine applications, to ensure that they aren’t taking steps that could be perceived as malicious by end-users.
Scanning for the appropriate configurations
Software tools can be designed to ensure that the application is configured correctly and secured for use in specific environments, such as the Microsoft Azure Advisor tool for cloud-based infrastructure. Many automated testing tools are designed to operate in a particular environment, such as a mobile environment or web-based environment. During the development of software, it can be ensured that the software is being built to these appropriate standards.
Code analysis tools
Code analysis tools can strengthen DevOps security efforts by automatically scanning the code and identifying potential and known vulnerabilities within the code itself. This can be invaluable information as the software teams work, as they will be able to identify problems before they are caught in quality assurance. This can also help them in developing better coding habits.
DevSecOps Best Practices
DevSecOps integrates security into the development lifecycle, but it is not possible to do so hastily and without planning. Include it in the design and development stages. Companies can work to change their workflows by following some of the best practices of the industry.
Get your teams on board
It may seem trivial, but getting all the required teams working together can make a huge difference in your DevSecOps initiative. Development teams are familiar with the typical process of handing off newly released iterations to Quality Assurance teams. This isolated behavior is the norm in companies that have each team in a silo.
Companies should eliminate silos and bring development, operations, and security teams together. Unity across teams will enable the experts in these groups to work together from the beginning of the development process and foresee any challenges.
Threat modeling is one way to plan for and identify possible security threats to your assets. You examine the types and sensitivities of your assets and analyze existing controls in place to protect those assets. By identifying the gaps you can address them before they become an active problem.
These types assessments can help identify flaws in the architecture and design of your applications that other security approaches might have missed.
The first step in implementing a DevSecOps culture is to educate your teams that security is a shared responsibility of teams from all three disciplines. Once development and operations teams take on the shared responsibility of securing code and infrastructure, DevSecOps becomes a natural part of the development cycle.
Many DevOps teams still have the misconception that security assessment causes delays in software development and that there should be a trade-off between security and speed. DevSecOps events and training are excellent opportunities to rid teams of these misconceptions. Real-life examples and case studies can help to get buy-in from teams and management alike.
Educate your developers
Developers are almost single-handedly responsible for the quality of the code they develop. Coding errors are the cause of many security vulnerabilities and issues. But companies pay little attention to their developers’ training and skill enhancement when it comes to producing secure code.
Educating them in the best practices of coding can directly contribute to improved code quality. Better code quality leaves less room for security vulnerabilities. Security teams will also find it easier to assess and remedy any vulnerabilities in high-quality code.
‘Common software weaknesses’ is another area in which most developers are unfamiliar. Teams can use online tools like the Common Weakness Enumeration list as a reference. Listings are useful to developers who are not that familiar with security practices.
Security teams, as part of their commitment to DevSecOps, must undertake to train development and operations teams regarding security practices. Such training will enable developers to integrate security controls into the code.
Compliance (HIPAA, GDPR, PCI) is vital for applications in industries such as finance and medicine. Development teams must be familiar with these standards and keep in mind the requirements to ensure compliance.
Verify code dependencies
Very few organizations today develop their code all in-house. It is more likely that each application will be built on a large amount of third-party, open-source code.
Despite the risk, many companies use third-party software components and open-source software in applications instead of developing from scratch. Yet they lack the automatic identification and remediation tracking for bugs and flaws that may exist in open-source software. Due to the pressure of meeting customer demands developers rarely have the opportunity to review code or documentation.
This is where automated testing plays a significant role in regularly test open-source and third-party components. It’s a main requirement in the DevSecOps methodology. It’s critical to find out if open-source usage is causing any weaknesses or vulnerabilities in your code. You need to find out how it impacts dependent code. It will help you identify issues that help reduce the meantime to resolution.
Third-party code can represent some significant vulnerabilities. Organizations will need to identify their code dependencies and automate the process of ensuring that their third-party code has no known vulnerabilities and is being updated as it should be throughout the process of creation.
There are utilities available that can continuously check a database of known vulnerabilities to quickly identify any issues with existing code dependencies. This software can be used to swiftly mitigate third-party threats before they are incorporated into the application.
Enhance Continuous Integration with DevOps Security
DevOps teams typically use Continuous Integration (CI) tools to automate parts of the development cycle, such as testing and building. These are routine tasks that teams need to repeat with each release.
Enhancing Continuous Integration processes and tools with security controls ensures that security practitioners identify issues before validating builds for Continuous Delivery (CD). CI also reduces the time spent on each iteration.
For example, using (SAST) static application security testing on daily builds will help you ensure that you’re only scanning for instances or items of interest in the changes to your code that were committed that day.
DevSecOps teams need to use vulnerability assessment scanning tools to ensure that they identify security issues early in the development cycle. They can use pre-production systems for this type of testing.
Simplify your code
Simpler code is easier to analyze and fix. Developers will find debugging their code much easier when it is simple and easier to read. Simple and clean code will also lead to reduced security issues. Developers will be able to quickly review and work on each other’s code if it is simple.
More significantly, security teams will be able to analyze simple code more efficiently. So releasing code in smaller chunks will allow security teams to identify issues sooner and with less effort. By choosing one section to analyze and prove it works, before moving on to the next bit will streamline the process. It will reduce the probability of security vulnerabilities and leads to robust applications.
Security as code
‘Security as Code’ is the concept of including security best practices into the existing DevOps pipeline. One of the most critical processes that this concept entails is the static analysis of code. Security practitioners can focus testing on code that has changed, in contrast to analyzing the entire code base.
Implementing a good change management process will allow members of all teams to submit changes and improvements. This type of process will enable security teams to remedy security issues directly without disrupting the development cycle.
Automation is another essential aspect of ‘security as code.’ Teams can automate security tasks to ensure that they conventionally verify all iterations. This uniformity will help to reduce or eliminate the presence of known security issues. Automation can significantly reduce the time spent on troubleshooting and fixing security issues later in the development cycle.
Put your application through security checks
Your application should be subject to regular testing. It should also undergo more rigorous testing such as preventing denial of service attacks.
There may be vulnerabilities in a solution that are only evident when that solution is broken. These are still genuine problems that the product owner may face.
Organizations are seeing an increasing number of malicious attacks. These attacks may focus on any aspect of a client’s organization that is accessible from outside of the network.
By testing your application under particularly strenuous circumstances, you can secure it through various scenarios.
How to Implement DevSecOps?
Each of the teams involved in DevSecOps needs to contribute towards its success.
Development
Developers perform an essential role in the DevSecOps process. Developers must be open to the involvement of operations and security teams. The participation of these teams from an early stage of the design and development process will facilitate a secure DevOps transformation and make applications overall more secure.
Training developers in security best practices is essential to success. Companies can supplement this training with hiring developers who have experience in DevSecOps so that they can guide the rest of the team.
Companies must build a culture where developers are aware that developing security is a shared responsibility between them and security teams. Security practitioners can only recommend security practices. It is the responsibility of developers to implement them.
Operations
The contribution of the operations team is similar to that of the development team. Operations teams must collaborate with security practitioners. They are responsible for subjecting infrastructure and network configurations to security tests.
Security teams will also need to train operations teams regarding security practices to make DevSecOps successful. Operations and security teams, in collaboration, will then set up both manual and automated security tests to ensure compliance with network configurations.
Security
DevSecOps is as much of an adjustment for security teams as it is for development and operations teams. Security teams have to gradually increase their involvement while cooperating with development and operations teams.
Security practitioners should start with the concept of ‘shifting left.’ That is, collaborating with development and operations teams to move security reviews and automated tests towards the beginning of the software development lifecycle. This process of shifting left is essential to reduce the chances of unforeseen security issues popping up later.
Development and operations teams usually see security tests as a tedious and complicated task. So the duty of security teams does not stop at developing security tests but extends to involving and training the other teams.
DevSecOps is the Future
DevSecOps methodology has gained momentum due to the high cost of correction of security issues and security debt. As Agile teams release applications more frequently, security testing becomes more crucial. We hope some of the best practices mentioned in this article will help your company to transition from DevOps to a DevSecOps approach.
If you wish to learn more about how to adopt DevSecOps, contact our experts today.
Next you should read
17 Best Vulnerability Assessment Scanning Tools
Vulnerability scanning or vulnerability assessment is a systematic process of finding security loopholes in any system addressing the potential vulnerabilities.
The purpose of vulnerability assessments is to prevent the possibility of unauthorized access to systems. Vulnerability testing preserves the confidentiality, integrity, and availability of the system. The system refers to any computers, networks, network devices, software, web application, cloud computing, etc.
Types of Vulnerability Scanners
Vulnerability scanners have their ways of doing jobs. We can classify the vulnerability scanners into four types based on how they operate.
Cloud-Based Vulnerability Scanners
Used to find vulnerabilities within cloud-based systems such as web applications, WordPress, and Joomla.
Host-Based Vulnerability Scanners
Used to find vulnerabilities on a single host or system such as an individual computer or a network device like a switch or core-router.
Network-Based Vulnerability Scanners
Used to find vulnerabilities in an internal network by scanning for open ports. Services running on open ports determined whether vulnerabilities exist or not with the help of the tool.
Database-Based Vulnerability Scanners
Used to find vulnerabilities in database management systems. Databases are the backbone of any system storing sensitive information. Vulnerability scanning is performed on database systems to prevent attacks like SQL Injection.
Vulnerability Scanning Tools
Vulnerability scanning tools allow for the detection of vulnerabilities in applications using many ways. Code analysis vulnerability tools analyze coding bugs. Audit vulnerability tools can find well-known rootkits, backdoor, and trojans.
There are many vulnerability scanners available in the market. They can be free, paid, or open-source. Most of the free and open-source tools are available on GitHub. Deciding which tool to use depends on a few factors such as vulnerability type, budget, frequency of how often the tool is updated, etc.
1. Nikto2
Nikto2 is an open-source vulnerability scanning software that focuses on web application security. Nikto2 can find around 6700 dangerous files causing issues to web servers and report outdated servers based versions. On top of that, Nikto2 can alert on server configuration issues and perform web server scans within a minimal time.
Nikto2 doesn’t offer any countermeasures for vulnerabilities found nor provide risk assessment features. However, Nikto2 is a frequently updated tool that enables a broader coverage of vulnerabilities.
2. Netsparker
Netsparker is another web application vulnerability tool with an automation feature available to find vulnerabilities. This tool is also capable of finding vulnerabilities in thousands of web applications within a few hours.
Although it is a paid enterprise-level vulnerability tool, it has many advanced features. It has crawling technology that finds vulnerabilities by crawling into the application. Netsparker can describe and suggest mitigation techniques for vulnerabilities found. Also, security solutions for advanced vulnerability assessment are available.
3. OpenVAS
OpenVAS is a powerful vulnerability scanning tool that supports large-scale scans which are suitable for organizations. You can use this tool for finding vulnerabilities not only in the web application or web servers but also in databases, operating systems, networks, and virtual machines.
OpenVAS receives updates daily, which broadens the vulnerability detection coverage. It also helps in risk assessment and suggests countermeasures for the vulnerabilities detected.
4. W3AF
W3AF is a free and open-source tool known as Web Application Attack and Framework. This tool is an open-source vulnerability scanning tool for web applications. It creates a framework which helps to secure the web application by finding and exploiting the vulnerabilities. This tool is known for user-friendliness. Along with vulnerability scanning options, W3AF has exploitation facilities used for penetration testing work as well.
Moreover, W3AF covers a high-broaden collection of vulnerabilities. Domains that are attacked frequently, especially with newly identified vulnerabilities, can select this tool.
5. Arachni
Arachni is also a dedicated vulnerability tool for web applications. This tool covers a variety of vulnerabilities and is updated regularly. Arachni provides facilities for risk assessment as well as suggests tips and countermeasures for vulnerabilities found.
Arachni is a free and open-source vulnerability tool that supports Linux, Windows, and macOS. Arachni also assists in penetration testing by its ability to cope up with newly identified vulnerabilities.
6. Acunetix
Acunetix is a paid web application security scanner (open-source version also available) with many functionalities provided. Around 6500 vulnerabilities scanning range is available with this tool. In addition to web applications, it can also find vulnerabilities in the network as well.
Acunetix provides the ability to automate your scan. Suitable for large scale organizations as it can handle many devices. HSBC, NASA, USA Air force are few industrial giants who use Arachni for vulnerability tests.
7. Nmap
Nmap is one of the well-known free and open-source network scanning tools among many security professionals. Nmap uses the probing technique to discover hosts in the network and for operating system discovery.
This feature helps in detecting vulnerabilities in single or multiple networks. If you are new or learning with vulnerabilities scanning, then Nmap is a good start.
8. OpenSCAP
OpenSCAP is a framework of tools that assist in vulnerability scanning, vulnerability assessment, vulnerability measurement, creating security measures. OpenSCAP is a free and open-source tool developed by communities. OpenSCAP only supports Linux platforms.
OpenSCAP framework supports vulnerability scanning on web applications, web servers, databases, operating systems, networks, and virtual machines. Moreover, they provide a facility for risk assessment and support to counteract threats.
9. GoLismero
GoLismero is a free and open-source tool used for vulnerability scanning. GoLismero focuses on finding vulnerabilities on web applications but also can scan for vulnerabilities in the network as well. GoLismero is a convenient tool that works with results provided by other vulnerability tools such as OpenVAS, then combines the results and provides feedback.
GoLismero covers a wide range of vulnerabilities, including database and network vulnerabilities. Also, GoLismero facilitates countermeasures for vulnerabilities found.
10. Intruder
Intruder is a paid vulnerability scanner specifically designed to scan cloud-based storage. Intruder software starts to scan immediately after a vulnerability is released. The scanning mechanism in Intruder is automated and constantly monitors for vulnerabilities.
Intruder is suitable for enterprise-level vulnerability scanning as it can manage many devices. In addition to monitoring cloud-storage, Intruder can help identify network vulnerabilities as well as provide quality reporting and suggestions.
11. Comodo HackerProof
With Comodo Hackerproof you will be able to reduce cart abandonment, perform daily vulnerability scanning, and use the included PCI scanning tools. You can also utilize the drive-by attack prevention feature and build valuable trust with your visitors. Thanks to the benefit of Comodo Hackerproof, many businesses can convert more visitors into buyers.
Buyers tend to feel safer when making a transaction with your business, and you should find that this drives your revenue up. With the patent-pending scanning technology, SiteInspector, you will enjoy a new level of security.
12. Aircrack
Aircrack also is known as Aircrack-NG, is a set of tools used for assessing the WiFi network security. These tools can also be utilized in network auditing, and support multiple OS’s such as Linux, OS X, Solaris, NetBSD, Windows, and more.
The tool will focus on different areas of WiFi security, such as monitoring the packets and data, testing drivers and cards, cracking, replying to attacks, etc. This tool allows you to retrieve the lost keys by capturing the data packets.
13. Retina CS Community
Retina CS Community is an open-source web-based console that will enable you to make a more centralized and straightforward vulnerability management system. Retina CS Community has features like compliance reporting, patching, and configuration compliance, and because of this, you can perform an assessment of cross-platform vulnerability.
The tool is excellent for saving time, cost, and effort when it comes to managing your network security. It features an automated vulnerability assessment for DBs, web applications, workstations, and servers. Businesses and organizations will get complete support for virtual environments with things like virtual app scanning and vCenter integration.
14. Microsoft Baseline Security Analyzer (MBSA)
An entirely free vulnerability scanner created by Microsoft, it’s used for testing your Windows server or windows computer for vulnerabilities. The Microsoft Baseline Security Analyzer has several vital features, including scanning your network service packets, checking for security updates or other windows updates, and more. It is the ideal tool for Windows users.
It’s excellent for helping you to identify missing updates or security patches. Use the tool to install new security updates on your computer. Small to medium-sized businesses find the tool most useful, and it helps save the security department money with its features. You won’t need to consult a security expert to resolve the vulnerabilities that the tool finds.
15. Nexpose
Nexpose is an open-source tool that you can use for no cost. Security experts regularly use this tool for vulnerability scanning. All the new vulnerabilities are included in the Nexpose database thanks to the Github community. You can use this tool with the Metasploit Framework, and you can rely on it to provide a detailed scanning of your web application. Before generating the report, it will take various elements into account.
Vulnerabilities are categorized by the tool according to their risk level and ranked from low to high. It’s capable of scanning new devices, so your network remains secure. Nexpose is updated each week, so you know it will find the latest hazards.
16. Nessus Professional
Nessus is a branded and patented vulnerability scanner created by Tenable Network Security. Nessus will prevent the networks from attempts made by hackers, and it can scan the vulnerabilities that permit remote hacking of sensitive data.
The tool offers an extensive range of OS, Dbs, applications, and several other devices among cloud infrastructure, virtual and physical networks. Millions of users trust Nessus for their vulnerability assessment and configuration issues.
17. SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager has consistently received high praise from users. The vulnerability assessment tool features that it includes addresses a specific type of vulnerability that many other options do not, such as misconfigured networking equipment. This feature sets it apart from the rest. The primary utility as a vulnerability scanning tool is in the validation of network equipment configurations for errors and omissions. It can also be used to check device configurations for changes periodically.
It integrates with the National Vulnerability Database and has access to the most current CVE’s to identify vulnerabilities in your Cisco devices. It will work with any Cisco device running ASA, IOS, or Nexus OS.
Vulnerability Assessment Secures Your Network
If an attack starts by modifying device networking configuration, the tools will be able to identify and put a stop to it. They assist you with regulatory compliance with their ability to detect out-of-process changes, audit configurations, and even correct violations.
To implement a vulnerability assessment, you should follow a systematic process as the one outlined below.
Step 1 – Begin the process by documenting, deciding what tool/tools to use, obtain the necessary permission from stakeholders.
Step 2 – Perform vulnerability scanning using the relevant tools. Make sure to save all the outputs from those vulnerability tools.
Step 3 – Analyse the output and decide which vulnerabilities identified could be a possible threat. You can also prioritize the threats and find a strategy to mitigate them.
Step 4 – Make sure you document all the outcomes and prepare reports for stakeholders.
Step 5 – Fix the vulnerabilities identified.
Advantages of Scanning for Vulnerabilities
Vulnerability scanning keeps systems secure from external threats. Other benefits include:
- Affordable – Many vulnerability scanners are available free of charge.
- Quick – Assessment takes a few hours to complete.
- Automate – can use automated functions available in the vulnerability tools to perform scans regularly without manual involvement.
- Performance – vulnerability scanners perform almost all the well-known vulnerability scan.
- Cost/Benefit – reduce cost and increase benefits by optimizing security threats.
Vulnerability Testing Decreases Risk
Whichever vulnerability tool you decide to use, choosing the ideal one will depend on security requirements and the ability to analyze your systems. Identify and deal with security vulnerabilities before it’s too late.
Take this opportunity now to look into the features provided by each of the tools mentioned, and select one that’s suitable for you. If you need help, reach out to one of our experts today for a consultation.
Learn about more of the best networking tools to improve your overall security.
Next you should read
19 Cybersecurity Best Practices to Protect Your Business
Cybersecurity is high on the list of concerns for rapidly evolving businesses online. As more small businesses move services or store data online, they are putting themselves at risk for cyberattacks.
At the forefront of this battle against cybercrime and hackers, companies must consolidate a solid defense by implementing cybersecurity best practices. This article will cover key strategies every company should adopt to avoid attacks and become less exposed.
Cyberattacks aim to compromise systems and access relevant data that they can monetize, ranging from stolen credit card information or credentials for identity theft.
Strong cybersecurity policies and procedures can save millions of dollars for organizations. It does require an initial investment to set up a stable network and protect against intrusions. But the severity and scale of cyberattacks are increasing daily, and the threat is imminent. Thus, the need for safeguarding against such dangers is critical.
Recommended Cybersecurity Best Practices
Adopt the cybersecurity best practices below to prepare your organization against cyber threats and ensure the continuity of your business.
1. Create a Dedicated Insider Threat Role
An insider threat program is considered a core part of a modern cybersecurity strategy. Having employees who have access to data is risky since they can leak information or damage equipment. Creating an insider threat program is essential for companies that have sensitive data, and could have their reputations ruined due to exposure via an insider attack. It does come with a cost and can be considered a low priority task, businesses should not delay, and instead, gain the support of top management to develop policy across all departments.
2. Conduct Phishing Simulations
As of 2020, phishing attacks are one of the most prevalent forms of cyber threats experienced by companies on a global level. Phishing simulations should train employees on how to avoid clicking on malicious links or downloading unknown files. Raising cybersecurity awareness, such as simulated phishing attacks, helps employees understand the far-reaching effects of a phishing attack. The simulation creates a safe space where employees’ knowledge is tested, to ask questions, and find out what the latest tricks are.
3. Secure Remotely Working and Travelling Employees
Many corporate employees have the dangerous habit of accessing corporate networks through unsecured public Wi-Fi networks while traveling on work trips. Sacrificing security for convenience is unacceptable in the corporate world, and employees should be aware of the huge risks they are taking. Training and education on the precautions one can take to avoid risks is essential. Options, such as using VPNs while surfing the web when traveling installing anti-malware programs, will tighten the security gaps in your workforce outside the office. Read our article on remote access security.
4. Prioritize Employee Privacy
Data privacy awareness and digital data sensitivity concerns are at an all-time high, with new legislation coming out to better regulate it. Employee privacy can be prioritized by “anonymizing” their data and taking steps to protect them from threats in a prevention capacity. Educate employees using workshops and presentations about different cybersecurity policies and local laws, emphasizing the impact on their privacy.
5. Create a Cybersecurity Awareness Training Program
Company surveys have found that two out of three insider threat incidents are initiated by an employee or contractor, which can be prevented (ObserveIT). Employees are the first line of defense against cybercrime. Their education is vital in developing all the skills and knowledge needed to protect an organization. A comprehensive cybersecurity awareness program will create a critical “security-first culture.” It would address aspects such as identifying risks, changing employee behaviors, and tracking metrics of improvement.
6. Inform Third-Party Contractors of Cybersecurity Policy
Due to globalization and interconnectivity, many businesses take advantage of allocating specialized workloads to third-party partners or outsourced entities. However, these third-party contractors have to be made aware of the cybersecurity policies you are using. Both in-house staff, as well as third-party contractors, have to be made aware or trained to follow the cybersecurity policies put in place.
7. Implement IS Governance Approach
Every company should establish and maintain an information security (IS) framework that aligns with the business’s existing assurance strategies. When selecting one of these methods, it should ensure that the program selected provides all levels of management with the ability to employ a risk-based approach. This strategy enables staff to detect incidents, investigate, and respond to them faster.
8. Monitor User and File Activity
Malicious insider threats tend to take advantage of multiple channels to exfiltrate data. Developing a good user and file activity monitoring system is one of the best solutions available to this problem. Existing solutions such as Data loss prevention, which focus on only on data and not on user activity, fall short of preventing all malicious insider threats inside the system. If you monitor users closely and know what files they access, it’s easier to react to an incident or prevent one.
9. Be Aware of State-Sponsored Threats
It is well-documented that employees belonging to high-value industries such as healthcare, technology, and banking may be susceptible to monetary incentives to sell data to foreign governments and entities. Understanding the motivation of such entities and potential insider targets is of the utmost priority so that you can spot patterns of suspicious and underhanded behavior.
10. Enforce the Use of Password Managers, SSOs, and MFAs
The use of repetitive or weak passwords is still a very common practice among employees of multinationals today. Implementing a enterprise password manager is the most viable option available to combat potential security soft spots in your company.
11. Audit Privileged Access
For the company’s head management, it’s advisable to review the number of users who have privileged access to sensitive areas of the business or data. Granting privileged access is a necessary risk, especially when there is a changeover in staff or changing roles, etc. Businesses should regularly look at permissions, adopt a system of temporary or rotating credentials, or develop a system of auditing privileged accesses.
Essential Network Security Practices
Security teams are held accountable for addressing the risk of insider breaches. To develop a strong plan against insider risk, take a systematic approach when organizing security measures. Here are some essential network security practices:
12. Stop Data Loss
Enterprises regularly experience the problems caused by leaked and stolen data. One of the top security concerns for modern companies is the act of data exfiltration from an endpoint. Companies should always control access, monitor contractors and vendors, as well as employees, to get a clear picture of how all parties access and handle data.
13. Detect Insider Threat
While well-trained users are a company’s first line in security and defense, technology remains the main tool. Companies can detect unauthorized behavior by regularly monitoring user activity. This strategy helps companies verify user actions that do not violate security policies while flagging the ones that do.
14. Back-Up Data
Backing up data regularly should be mandatory practice, especially when you consider the malicious ransomware out there like “Wannacry” and “Petya.” Data back-ups are good practice to include in one’s basic security hygiene, as well as to combat emerging cyber threats.
Beware of Social Engineering
Social engineering tactics are considered a threat and have been used for decades to gain login credentials and access to files that are encrypted. Such attempts may come from phone devices, emails, social media profiles, etc. In such circumstances, the best defense is to do the following:
15. Outline Clear Use Policies for New Hires and Third Parties
Requirements and expectations that the company has, regarding IT security, should be clearly stated in the employment contracts and the various SLAs and SOPs that a company might have.
16. Update Software and Systems
Cyber threats and crimes are ever-increasing, and an optimized security network might eventually fall prey to it. Thus, a company’s network should always be protected. Plan regular software updates and schedule maintenance on hardware security.
17. Create an Incident Response Playbook
No matter how many security measures a company takes against rising cybercrimes, vulnerability to unseen threats remain. Thus, companies should have a security incident esponse plan in case they get attacked. This planning will allow management to limit the damage of a security breach, allowing them to remediate the situation effectively.
18. Educate and Train Users
Employees should be trained on how to create and maintain strong passwords, recognize phishing emails, avoid dangerous applications, etc. ensuring that valuable information doesn’t flow out of the company in the case of an external attack.
19. Maintain Compliance
No matter what level of cybersecurity a company implements or already has, it should always comply with regulatory bodies such as; HIPAA, PCI, ISO, and DSS and keep up with their latest guidelines.
Preparation is Prevention
There are numerous cybersecurity best practices that a business can consider implementing when creating a security management strategy. We have highlighted ten of those practices as a jumping-off point to begin the journey of securing their business and assets in-house and online. A comprehensive cybersecurity program will protect companies from lasting financial consequences, as well as prevent reputational damage. It’s essential to prepare to prevent incidents and attacks, and the key to modern-day businesses’ survival. Contact our experts today and find out how you can become compliant and better secure data online.
Additional Practices to Improve Cybersecurity
- Build Processes before Choosing Tools: Organizers should implement a formal security governance program and think through the strategies that they will implement before deciding on tools, equipment, or software.
- Recruit HR to Halt Data Loss: Companies should recruit HR teams that can develop and execute better off-boarding processes to protect data. They can do this by systematically removing accesses from employees who have left or are on the verge of leaving.
- Prioritize Visibility: Insider threats that are malicious and accidental can be prevented by continuously monitoring user activity. Thus, the software chosen should also give management, unfettered visibility.
- Automation: Small things such as system updates should never depend on user discretion. Whenever possible, automatic updates, incident detection, etc. should be automated to avoid the instances of human error. Only complex and strategic actions and other activities requiring human intervention can rely on employees.
- Compliance with GDPR: The General Data Protection Regulation (GDPR) is the regulatory body responsible for regulating data privacy for all European citizens. Most companies operating inside the European Union need to ensure that they comply with the directive under this law.
- Securing Site with HTTPs: Companies should protect their site and users with an SSL certificate. Additionally, Google encourages businesses to use HTTPs to ensure secure and private connections to protect their user’s connection to their website. This extra level of security is one of the first steps in implementing the essential methods of site encryption, data integrity, and authentication.
Next you should read
Top eCommerce Security Threats with Solutions for 2020
Ecommerce security isn’t something to be taken lightly. Major data leaks have fundamentally damaged trust in digital security. Consumers are comfortable making payments through familiar systems (PayPal, Amazon, Google, Apple, etc.) but take a bit more convincing to risk their credit card details with unknown companies. After all, they know what’s at stake.
Failing to secure an online retail business can directly impact sales or worse, ruin your reputation. Once it’s known that a business cannot be relied upon to keep data secure, no one will want to buy from them again.
Get serious about protecting your online business. Learn the basics of what you need to know about eCommerce security threats and solutions.
Major Threat: Transaction fraud
Vast amounts of money change hands online with each passing second, and as much as we’d like to think that technology has moved past transactions being dangerous to consumers, it hasn’t. There are two primary forms of payment fraud. The first is stolen credit cards, whose details are used to make unauthorized payments (with the purchased products kept or sold on, even if the payments get canceled). The second is transactions on insecure systems that are interrupted or get redirected.
Online buyers now have access to systems offering unprecedented financial convenience. Bank support is available through live chat, and you can even cancel payments through apps. But this doesn’t fully protect from this type of fraud. The reason is simple: even the most diligent among us will forget to check our bank records on occasion, and it only takes one lapse in attention for a cybercriminal to make numerous payments.
Online shoppers are now aware of the importance of website security markers, such as the HTTPS indicator. Still, such indicators can often be spoofed in a manner that’s sufficiently convincing for most people. This type of forgery can make it quite tricky to tell when a website is providing a secure service. Consumers need to be educated and get better at being vigilant online.
Solution: PCI DSS compliance
The PCI DSS standard was set up to raise levels of online payment security dramatically. Any eCommerce business that wants to protect its transactions (and bolster its credibility in the process) should take action to meet it. Compliance is still nowhere near as common as it should be. It’s frustrating, as it shouldn’t be an issue for the individual retailer since essentially, it’s a benefit. Compliant sellers stand out more through ridding their sales funnels of damaging dead ends (a key conversion optimization tactic) and showing their investment in buyer safety.
Major Threat: Direct site attacks
While phishing is a passive approach, eCommerce sites can sometimes be subjected to direct attacks in the form of DDoS (dedicated denial of service) campaigns. Here’s how it works: those who want to put a store under siege will program many internet-capable devices to near-constantly attempt to use the store site.
This orchestrated attack will overwhelm the store’s hosting and prevent the site from loading for most (if not all) regular visitors. It’s mainly about keeping it so busy that it can’t focus on the visits that actually matter. This attack type can also burn through hosting data allowances, causing other costly issues for businesses. These campaigns are relatively rare, but not so much so that they’re not a threat.
What’s the end goal of a DDoS attack? It depends on the situation. Sometimes it will be to inconvenience the store and damage its reputation, as a matter of corporate sabotage. More often, a DDoS attack will be coupled with a blackmail demand: pay a certain sum, and the attack will be disabled.
Solution: Active protection
An eStore can be attacked at any time, regardless of its fundamental level of security, this threat requires more vigorous measures, so make use of a DoS protection service. The concept is simple enough – incoming traffic is monitored and parsed, and when visit requests are considered to be fraudulent in nature, they are entirely blocked. This defense prevents the DDoS attack from slowing the site down to a crawl, or significantly affecting its performance.
Major Threat: Password assault
Password strategy has been frustrating security consultants since the very beginnings of the internet, all due to the irritating balance needed between protection and convenience. If you choose long and complex passwords, you can end up forgetting them and losing all access. Creating easy-to-remember passwords leaves systems highly vulnerable and open to attack.
There are two main methods for this type of attack to occur. The first is brute forcing, using a program to run through thousands upon thousands of passwords in the hope of eventually getting it right. And second, what can reasonably be called informed guessing: using pieces of information from a user’s life, gleaned off social media to identify the words most likely to appear in their passwords.
And if a key admin password is discovered, the resulting access can prove massively damaging because it might not be noticed for some time. Significant alterations can be made, systems can be taken offline, data can be stolen, and money can be transferred, all with minimal risk to the person with access. It’s like breaking into someone’s house by picking the lock – there’s no apparent damage, but it happens when you’re supposed to be home.
Solution: Stronger passwords and multi-factor authentication
How do eCommerce sellers address the threat of discovered passwords, both for their internal systems and their customers?
There are two strategies they can implement. Firstly, they should use and require that more complex passwords are used internally. They don’t need to be comically long or awkward, but they mustn’t be as simple as “1234” or “password”.
Secondly, they should start using multi-factor authentication for their admin accesses (or for major changes to customer accounts). This setup requires the logged-in user to couple their password access with another form of authentication, such as an authentication code sent via text message. It’s also worth creating regular site backups: that way, in the unlikely event, that someone does gain unauthorized access and makes sweeping changes, they can quickly revert to prior backups.
Major Threat: Social engineering
Social engineering is a broad method for gaining access to systems, money, or assets through deception at a social level instead of directly through technology. One of the most common forms of social engineering is phishing, which involves pretending to be someone trustworthy when contacting someone and exploiting that trust to get something from them.
In the recent past, phishing most commonly occurred through phone calls, letters, and even house visits. An example of a phishing attack is calling someone and claiming to be from their bank saying they need to confirm credit card details. When online shopping and eCommerce developed and became more popular, it grew more sophisticated.
At this point, phishers can learn about which retailers a shopper uses, and spoof emails from them. Emails that are loaded with risks such as fraudulent forms to keylogger installers. They can also pose as retailers through social media or set up stores that appear very similar to legitimate sites by using slightly-different URLs and steal data. These cybercriminals often use misspellings and build a store that copies the design of a trusted retailer, i.e., copying Amazon’s design and making it live at www.amazom.com.
Solution: Wider education
Phishing is difficult to prevent because it’s such a broad category, and it involves no force. It comes down to the criminals laying down the bait and hoping that people will take it. The best way to proceed is for retailers to educate their customers about how they operate. They should add tips to their site content and use their general marketing materials. Customers should know that when they receive emails, they know how to identify them as legit. Clients need to know what they might be asked for and what will never be asked of them. Retailers need to encourage their customers to reach out for confirmation if they ever receive questionable emails.
Other eCommerce Threats You Should Know
For eCommerce businesses dealing in daily monetary transactions, security must become the number one concern. Intensive security measures need to be implemented to obstruct threats effectively and keep transactions protected. Here are other common threats eCommerce sites face:
Brute Force Attacks
Brute force attacks target an online store’s admin panel. Why? They want to figure out the password and gain access, the directness of the attack makes it brute-force. After using software to connect to a site, it using code-crunching programs to crack passwords by using every possible combination imaginable. The solution is easy, protect your system by creating strong and complex passwords, changing them regularly.
Bots
Bots can be both good and bad. The good ones are those that crawl the Internet and determine how to rank your site in search engines. Bots can also scrape websites too for inventory information and pricing and alter prices on a site, freeze popular items in shopping carts, and thereby damage site sales and revenues.
The solution is to protect exposed APIs and mobile apps, and examine traffic sources regularly looking for spikes, and then blocking those hosting providers and proxy services.
Malware
There are different types of malware that want to penetrate the backend to steal sensitive site data and customer information.
Malware are those that use malvertising, ransomware, cross-site scripting, SQL injections, targeting credit card info and personal data. Malicious JavaScript coding is the most common. WordPress sites using WooCommerce and Shopify regularly get targeted by malware injections via widgets and plugin upgrades. The solution is to use professional antivirus and anti-malware software, switch to HTTPS, secure servers and admin panels and use SSL certificates while using employing multi-layer security.
Phishing
Receiving fake “you must take action” emails, either to your company or customers is a widely-used ploy and form of trickery used by hackers. It does require follow-through and unintentionally offering up login information or personal identification information. The solution here is employee training and educating consumers.
Spam
Contact forms and text boxes for blog comments are wide open to spammers. They can leave infected links that others can click on, ruining your reputation and site security. Also known as SQL injections, these cyber-attacks want to access databases via query forms. These links quietly wait for employees in inboxes and can affect site speed also. The solution is employee training and downloading spam filtering tools and anti-virus software, updating it regularly.
eCommerce Security Best Practices
Now that you’re familiar with eCommerce security concerns, and how costly they can be to the bottom line and reputation. Let’s look at solutions to help put a threat protection strategy into action.
PCI Compliance
PCI Security Standards Council releases a strict set of guidelines on how to secure an eCommerce website. It outlines which type of web hosting should be used, the level of security needed at the payment processing level, etc., Adopt their guidelines to ensure your site stays safe.
CDN
Content delivery networks (CDN) are another layer of hosting for an eCommerce website. They improve processes by storing content on servers situated across the country in data centers knows as ‘points of presence.’ These data centers have their own security, meaning it adds another layer of security.
Security Plugins
Security plugins are important for maintaining WordPress sites, ensuring the safe installation of plugins, and keeps the front-end of a site safe. They defend sites DDoS attacks, malware, and hacking, keeping you informed when threats are detected in real-time.
Backup Data
Always back up data and do this regularly. A backup and restore plugin will help. Despite investing in many levels of security, no eCommerce site is impenetrable. Hackers have the patience and time to find new ways of cracking through a site. It’s critical to back up data so a business can recover quickly if an attack happens.
Server Security
Be sure to use a well-established ecommerce web hosting company you can trust and has top-level security features. That should include a server-side firewall, CDN, or SSL certificates and dedicated hosting plans where share server environments are not shared with other sites. Make sure they follow server security best practices.
Payment Gateway Security
Just as critical as web hosting, it’s also key to make sure that the payment gateway provider takes security very seriously and ensure all third-party websites connected to yours, prioritizes security.
Antivirus and Anti-malware Software
Always upkeep and update the network’s servers and equipment with antivirus and anti-malware software.
Firewall
The web host should have a firewall for servers, but it’s also good to have one specifically for your website and computer too. There are many security plugins that come with built-in firewalls.
SSL Certificate
ECommerce sites must have an SSL certificate as it’s the Google standard. But it’s free, and quite a simple way to add more layers of encryption and security to onsite transactions.
Update Software Regularly
Software only works so well as its latest version, so if it’s not updated when suggested by the provider, your eCommerce site and business is put at risk. Schedule updates and keep all programs, software, and plugins updated regularly.
Ecommerce Security: Plan Ahead to Stay Safe
The major threats to eCommerce security that we’ve looked at are potentially devastating not only for retailers but customers as well. For this reason, the appropriate measures must be taken, and strategies put into place to address them. You simply can’t afford to be casual about the protection of websites or customer data.
The goal should be to provide a safe place for consumers online. By protecting them, you protect the bottom line as well. Outside of the eCommerce security threats and solutions we have outlined here, do regular site security audits to stay ahead of the dangers.
Get into the habit of offering sensible security advice to your visitors. Invest in meeting the PCI DSS standard to safeguard transactions. Set up high-quality active site protection to ward off DDoS campaigns. And lastly, get into the habit of using high-quality passwords, and configure multi-factor authentication to prevent the entire site from being compromised as the result of a critical password being left on an office post-it note.
Put a security plan into effect! Find out how to secure an eCommerce business by speaking with one of our experts today.
Next you should read
10 Step Business Continuity Planning Checklist with Sample Template
If you don’t have a Business Continuity Plan in place, then your business and data is already in danger. Believing a business will continue to generate profit in the future without putting safeguards in place is a very risky practice. Ignoring the pitfalls can be catastrophic.
Business continuity as a concept is self-explanatory. Yet, it encompasses much more than an organization’s future profitability. It covers all aspects of a business’s longevity, prosperity and success.
In this article, you will learn how to create an effective business continuity plan to protect your assets.
What is a Business Continuity Plan?
The definition of business continuity planning refers to the process involved in the creation of a system that prevents penitential threats to a company, also aiding in its recovery.
This plan outlines how assets and personnel will be protected during the event of a disaster, and how to function normally through an event. A BCP should include contingencies for human resources, assets and business processes, and any other aspects that could be affected by downtime or failure. The plan consists of input from all key stakeholders and must be finalized in advance.
A BCP is an essential part of a company’s risk management strategy. It should be updated as technology and hardware/software get updated. These risks usually include natural disasters—weather-related events, flood, fire, or cyber and virtual attacks. Any and every risk that can affect a company’s operations is defined beforehand by the BCP. A typical plan includes:
- Identifying all potential risks
- Determining the effect of the risk on the company’s normal operations
- Implementing procedures and safeguards for risk mitigation
- Testing the procedures to ensure their success
- Constantly reviewing the processes to make sure it’s updated
After an organization assess its risks and identifies them, it needs to follow these steps:
- Understanding how these risks will interfere or affect operations
- Setting up procedures and safeguards that mitigate risks and offer rapid solutions
- Systems on how to test solutions to ensure they work, and scheduling them regularly
- Ensuring that processes are systematically reviewed to make sure they’re up to date
Business Continuity Checklist
A successful business continuity plan is prepared based on the understanding of the impact of a disaster situation on a business. A business continuity checklist includes certain steps, which we have summarized for you below in point form.
Use this step by step guide for preparing your comprehensive preparedness plan. When it comes to disaster recovery strategies, each company will have varying strategies based on geographical locations, the organization’s structure, system, environments, and the severity of the disaster in question.
-
Assemble the Planning Team:
Implementing a BCP plan certainly requires a dedicated team. Teams should be built with hierarchy in mind, with specific roles and recovery tasks assigned to staff members who are accountable for each.
-
Drawing Up the BCP Plan:
Mapping out a strategy is one of the most important components of a business continuity plan. The objectives of the plan should be clearly understood with goals set accordingly. A company should use this opportunity to identify the key processes and the people who will keep it running.
To draw up the plan, companies need to make a list of all the disruptions that could affect a company’s operations. Pinpoint critical functions in everyday business processes and formulate practical recovery strategies for each possible disaster scenario.
-
Conduct Business Impact Analysis:
After identifying all the potential threats, they should be thoroughly analyzed. A proper business impact analysis or BIA should be in place. Extensive lists may need to be prepared, depending on the company’s set up and geographical location.
The list can include floods, hurricanes, fires, volcanoes, and even Tsunamis. Apart from the above natural disasters, others have a much higher probability of occurring. These can include cyberattacks, downtime due to power outages, data corruption, system failures, hardware faults, and other malicious threats to data security.
-
Educate and Train:
Handling business continuity requires knowledge beyond that of IT professionals and those with cybersecurity proficiency. Companies at the upper management level need to layout the objectives, requirements, and key components of the plan before the whole team. Develop a comprehensive training program to help the team develop the required skills.
-
Isolate Sensitive Info:
Every business works with critical data allocated with the topmost security priority. Such data, when compromised or leaked, can spell the end for a company or organization. Data, such as financial records and other mission-critical information such as user login credentials, require storage where recovery is convenient and easy. Store data according to priority based on the importance of the data to the business.
-
Backup Important Data:
Every company has some critical data, which is irreplaceable. Hence, every recovery or backup plan should include creating copies of anything which is not replaceable. In a Managed Service Provider’s (MSP) case, it includes files, data on customer and employee records, business emails, etc. The plan in place should facilitate quick recovery so that businesses can recover tomorrow from any disaster that occurs today.
-
Protect Hard Copy Data:
Electronic or digital data is the main focus of modern IT security strategies. There is still an enormous volume of physical documents that businesses need to maintain daily.
For example, a typical MSP involves working with an assortment of tax documents, contracts, and employee files, which are as important as the data saved on the hard drives. Convert documents that can be digitized to minimize the loss of physical documents.
-
Designate a Recovery Site:
Disasters have the potential to wipe out a company’s data center completely.
Companies should prepare for the worst, by designating a secondary site which would act as a back-up for the primary site. The second site should be equipped with the required tools and systems to recover affected systems to ensure that the business processes continue.
-
Set up a Communications Program:
Communication within the company is vital in times of crisis. Companies should consider drafting sample messages in advance to expedite communications to suppliers and partners in times of crisis.
Business Continuity teams can use a detailed communication plan to coordinate their efforts efficiently.
-
Test, Measure, and Update:
Every important business program should be tested and measured for its effectiveness, and business continuity plans are no exceptions. Testing should include running simulations to test the team’s level of preparedness during a crisis. Based on the results, additional modifications and tweaks can be made.
Download Our Sample Business Continuity Plan Template
Benefits of a Business Continuity Plan
A business continuity plan involves identifying and listing out all potential risks and threats a company may face and laying out appropriate policies to mitigate those risks in case of any disaster or crisis. A properly implemented business continuity plan would help any company to remain operational even in the wake of a disaster. Outlined below are some of the greatest advantages of having a business continuity plan in place:
Business Remains Operational During Disaster
Disasters can happen at any time, unannounced. Businesses need to recover from such incidents as quickly as possible to ensure there are no major disruptions in business processes. Business Continuity Plans can help companies remain operational throughout the disaster or the business recovery phase.
Avoid Expensive Downtime:
An Aberdeen Group report indicated that downtime could cost up to $8600 per hour to small scale organizations. If the system is down, businesses lose money, customers, or even their reputation is in danger in certain cases. A proper BCP in place can prevent losing any opportunities during an outage.
Protect Against Different Disasters
Disasters and crises do not always include disasters such as fire, tornadoes, or pandemics, etc. A crisis can also occur from hardware failures, power outages, cybercrimes, and other forms of human error. Thus, companies need to protect themselves not only from natural disasters but from all other forms of outages and downtime. A BCP mitigates these risks.
Gain a Competitive Advantage
In the event of a national or global crisis, a business’s reputation can be bolstered, if it remains up and running while its competitors are down. Clients can look more favorably towards the company as they associate a certain level of reliability with them. Putting a BCP plan in place can help companies stay operational during such times, giving them a clear competitive edge over their competitors.
Giving Assurance to Employees
It is natural for employees to worry if systems are compromised due to a crisis. This situation makes them worry about how and when to proceed with their delegated tasks, negatively affecting the workflow. This scenario is especially true for customer-centric organizations. Having a BCP plan in place for such situations can help prepare a company’s staff on what to do in such situations, and help keep business processes running smoothly. Having a clear action plan can do wonders for employees as it increases the company’s morale and job satisfaction.
Gain Peace of Mind
Having a detailed, tried, and tested BCP in place can alleviate much of management’s worries and stress, helping them to work on other core competencies. Companies can carry on confidently with their operations, knowing that there are measures in place to counter any system outage or downtime. BCP plans are thus critical to a company’s longevity, helping them defend against potential risks while enhancing a company’s reputation.
Stages of Developing a Strong BCP
Business Impact Analysis: You will identify resources and functions that are time-sensitive and need an immediate reaction.
GAP analysis: You need to analyze aspects of your business continuity management system that you currently have and evaluate your IT emergency management system and see how ready and mature it is to face evolving threats.
Improvement planning: This analysis will tell you what you need to work on to help improve the maturity of your Business Continuity Management (BCM) and what will help it improve over time.
Recovery: A clear plan needs to be outlined on which steps to take to fully recover critical business functions and get all applications back online smoothly.
Organization: A continuity team should be put in place who will come up with this plan and be responsible for managing all types of disruptions.
Training: The continuity team needs to get regular training and undergo testing, who complete scenarios and exercises that deal with the multitude of threats and disasters your company can face. They should also update and regularly go over the plan and strategies.
What Does a Business Continuity Plan Typically Include?
It’s critical to have a detailed plan for how to run business operations and maintain them for both the interim and possible longer-term disruptions and outages.
A BCP plan should outline what to do with data backups, equipment and supplies, and backup site locations, and how to reestablish technical productivity and software integrity so that vital business functions can continue. It should give step by step instructions to administrators, which includes all necessary information for backup site providers, key personnel, and emergency responders.
Remember these three keys to creating a successful business continuity plan:
- Disaster recovery: Consolidate a method to recover a data center, possibly at an external site. If the primary site is compromised, it becomes obsolete and inoperable.
- High availability: Ensure the capability of processes are highly available. In case of a local failure, the business can still function with limited access to applications despite the crisis in hardware/software, business processes, or the shutdown of physical facilities.
- Continuity of operations: The main goal is to keep processes and applications running during an outage, and to test them during planned outages. Scheduling backups and planning for maintenance is key to staying active.
Keep up with your competitors! As the Covid-19 crisis has shown, it’s essential to put a Business Continuity Plan in place to defend against every type of disaster using our best practices. Failure to do so can mean financial loss or damage to your company’s reputation. Start preparing, contact us or use our free BCP template to get started today.
38 Cyber Security Conferences to Attend in 2020
Global cybersecurity ensures the infrastructure of global enterprises and economies, safeguarding the prosperity and well-being of citizens worldwide. As IoT (Internet of Things) devices rapidly expand, and connectivity and usage of cloud services increases, cyber-related incidents such as hacking, data breaches, and infrastructure tampering become common.
Global cybersecurity conferences are a chance for stakeholders to address these issues and formulate strategies to defend against attacks and disseminate knowledge on new cybersecurity policies and procedures.
Benefits of Attending a Cyber Security Conference in 2020:
- Networking with peers
- Education on new technologies
- Outreach
- New strategies
- Pricing information
- Giving back and knowledge-sharing
- Discovering new talent
- Case studies
Here is a list below of the top 37 cybersecurity conferences to attend in 2020. As future conference details become confirmed for later in the year, bookmark the page and check back for the latest info.
1. National Privacy and Data Governance Congress
- Date: January 28, 2020
- Location: Toronto, Canada
- Cost: $150
- https://pacc-ccap.ca/events
The National Privacy and Data Governance Congress Conference is an occasion to discover critical problems at the landmark of privacy, law, security, access, and data authority. This event joins specialists from the academe, industry, and government who are involved with compliance, data governance, privacy, security, and access within establishments.
The conference is extensive but provides an adequate amount of time for representatives to present inquiries, receive impromptu responses, and participate in eloquent discussions with hosts, associates, and decision-makers.
2. NextGen SCADA Europe 2020
- Date: January 30 - February 1, 2020
- Location: Berlin, Germany
- Cost: €995 - €5,230.05
- https://www.smartgrid-forums.com/forums/nextgen-scada-global/?ref=infosec-conferences.com
The 6th Annual NextGen SCADA Europe exhibition and networking conference is back thanks to the high demand. It is a dedicated forum that will provide content depth and networking emphasis you need to help with making critical new decisions. A decision such as upgrading your SCADA structure to meet the needs of the digital grid better.
In a matter of three intensive days, you can take part in 20+ utility case-studies. Such vital studies like the critical subjects of integration, system architecture, cybersecurity, and functionality. Enroll now to gain insight into the reason why these studies are the newest buzz around the cyber circle.
3. Sans Security East
- Date: February 1 - 8, 2020
- Location: New Orleans, Louisiana, United States
- Cost: Different prices for different courses. Most courses cost $7,020. An online course is available.
- https://www.sans.org/event/security-east-2020
Jump-start the New Year with one of the first training seminars of 2020. Attend the SANS Security East 2020 in New Orleans for an opportunity to learn new cybersecurity best practices for 2020 from the world’s top experts. This training experience is to assist you in progressing your career.
SANS’ development is unchallenged in the industry. The organization provides fervent instructors who are prominent industry specialists and practitioners. Their applied knowledge adds significance to the teaching syllabus. These skilled instructors guarantee you will be capable of utilizing what you learn immediately. From this conference, you can pick from over twenty information security courses that are prepared by first-rate mentors.
4. International Conference on Cyber Security and Connected Technologies (ICCSCT)
- Date: February 3 - 4, 2020
- Location: Tokyo, Japan
- Cost: $260 - $465
- https://iccsct.coreconferences.com
The 2020 ICCSCT is a leading research session focused on presenting new developments in cybersecurity. The seminar happens every year to make a perfect stage for individuals to share opinions and experiences.
The International Conference on Cyber Security and Connected Technologies centers on the numerous freshly forthcoming parts of cybersecurity and connected technologies.
5. Manusec Europe: Cyber Security for Critical Manufacturing
- Date: February 4 - 5, 2020
- Location: Munich, Germany
- Cost: $999 - $2,999
- https://europe.manusecevent.com
As the industrial division continues to adopt advancements in technology, it becomes vulnerable to an assortment of cyber threats. To have the best tools to tackle cyber threats in the twenty-first century, organizations must involve all levels of employees to cooperate and institute best exercise strategies to guard vital assets.
This event will bridge the gap between the corporate IT senior level and process control professionals. Such practices will allow teams to discuss critical issues and challenges, as well as to debate cyber security best practice guidelines.
6. The European Information Security Summit
- Date: February 12 - 13, 2020
- Location: London, England, United Kingdom
- Cost: £718.80 - £2400.00
- https://www.teiss.co.uk/london
This organization, known as TEISS, is currently one of the leading and most wide-ranging cybersecurity meetings in Europe. It features parallel sessions on the following four streams:
- Threat Landscape stream
- Culture and Education stream
- Plenary stream
- CISOs & Strategic stream
Join over 500 specialists in the cybersecurity industry and take advantage of different seminars.
7. Gartner Data & Analytics Summit
- Date: February 17 - 18, 2020
- Location: Sydney, Australia
- Cost: $2,750 - $3,350
- https://www.gartner.com/en/conferences/apac/data-analytics-australia
Data and analytics are conquering all trades as they become the core of the digital transformation. To endure and flourish in the digital age, having a grasp on data and analytics is critical for industry players.
Gartner is currently the global leader in IT conference providers. You, too, can benefit from our research, exclusive insight, and unmatched peer networking. Reinvent your role and your business by joining the 50,000+ attendees that walk away from this seminar annually, armed with a better understanding and the right tools to make their organization a leader in their industry.
8. Holyrood Connect’s Cyber Security
- Date: February 17 - 23, 2020
- Location: Edinburgh, Scotland, United Kingdom
- Cost: £99
- http://cybersecurity.holyrood.com/about-the-event
With cyber threats accelerating in frequency, organizations must protect themselves from the potentially catastrophic consequences due to security breaches.
In a time where being merely aware of security threats is unsustainable, Holyrood’s annual cybersecurity conference will research the latest developments, emerging threats, and constant practice.
Join relevant stakeholders, experts, and peers as they research the next steps to reinforce defenses, improve readiness, and maintain cyber resilience.
Critical issues to be addressed:
- Up-to-date briefing on the latest in cybersecurity practice and policy
- Expert analysis of the emerging threat landscape both at home and abroad
- Good practice and innovation in preventing, detecting and responding to cyber attacks
- Developing a whole-organization approach to cyber hygiene – improving awareness, culture, and behavior
- Horizon scanning: cybersecurity and emerging technology
9. 3rd Annual Internet of Things India Expo
- Date: February 19 - 21, 2020
- Location: Pragati Maidan, New Delhi, India
- Cost: Free for Visitors
- https://www.iotindiaexpo.com
The Internet of Things is a trade transformation vital to government, companies, and clients, renovating all industries. The Second Edition IoT India Expo will concentrate on the Internet of Things environment containing central bodies, software, services, and hardware. Distinct concentration for this symposium will be on:
- Industrial IoT
- Smart Appliances
- Robotics
- Cybersecurity
- Smart Solutions
- System Integrators
- Smart Wearable Devices
- AI
- Cloud Computing
- Sensors
- Data Analytics
- And much more…
10. BSides Tampa
- Category: General Cyber Security Conference
- Date: February 20, 2020
- Location: Tampa, Florida, United States
- Cost: General Admission - $50; Discount for specific parties like Teachers, Military and Students
- https://bsidestampa.net
The BSides Tampa conference focuses on offering attendees the latest information on security research, development, and uses. The conference is held yearly in Tampa and features various demonstrations and presentations from the best available in industry and academia.
Attendees have the opportunity to attend numerous training classes throughout the conference. These training classes provide individual technical courses on subjects ranging from penetration testing, security abuse, or cybersecurity certifications.
11. RSA Conference, the USA
- Date: February 24 - 28, 2020
- Location: San Francisco, California, United States
- Cost: $750 - $1,995
- https://www.rsaconference.com/usa
With the simplicity of joining the digital space opens the risk of real-world cyber dangers. The 2020 RSA Conference focuses on the topics of managing these cyber threats that prominent organizations, agencies, and businesses are facing.
This event is famous in the US as well as in Abu Dhabi, Europe, and Singapore. The RSA Conference is renowned for being one of the leading information security seminars that occur yearly. The event’s real objective is to utilize the active determination the leaders place into study and research.
12. RSA Conference, Cryptographers’ Track
- Date: February 24 - 28, 2020
- Location: San Francisco, California, United States
- Cost: $750 - $1,995
- https://www.rsaconference.com/usa
More than 40,000 industry-leading specialists attend the event as it is the first industry demonstration for the security business. As one of the industry-leading cybersecurity events, 2020 is the pathway to scientific documents on cryptography. It is a fantastic place for the broader cryptologic public to get in touch with attendees from the government, the industry, and academia.
13. Hack New York City 2020
- Date: March 6 - 8, 2020
- Location: Manhattan, New York, United States
- Cost: Free
- https://hacknyu.org
Hack NYC is about sharing ideas on how we can improve our daily cybersecurity practices and the overall economic strength. The threat of attack targeting the Critical National Infrastructure is real as provisions supporting businesses and communities face common weaknesses and an implicit dynamic threat.
Hack NYC emphasis’ on our planning for, and resistance to, the real potential for Kinetic Cyberattack. Be part of crucial solutions and lighten risks aimed at Critical National Infrastructure.
14. Healthcare Information and Management Systems Society (HIMSS)
- Date: March 9 - 13, 2020
- Location: Orlando, Florida, United States
- Cost: $195 - $1,485
- https://www.himssconference.org
Over 40,000 health IT specialists, executives, vendors, and clinicians come together from all over the globe for the yearly HIMSS exhibition and seminar. Outstanding teaching, first-class speakers, front-line health IT merchandise, and influential networking are trademarks of this symposium. Over three hundred instruction programs feature discussions and workspaces, front-runner meetings, keynotes, and an entire day of pre-conference seminars.
15. 14th International Conference on Cyber Warfare and Security
- Date: March 12 - 13, 2020
- Location: Norfolk, Virginia, United States
- Cost: £365 - £690
- https://www.academic-conferences.org/conferences/iccws
The 14th Annual ICCWS is an occasion for academe, consultants, military personnel, and practitioners globally to explore new methods of fighting data threats. Cybersecurity conferences like this one offer the opportunity to increase information systems safety and share concepts.
New risks that exist from migrating to the cloud and social networking are a growing focus for the research group, and the sessions designed to cover these matters particularly. Join the merging of crucial players as CCWS uniquely addresses cyber warfare, security, and information warfare.
16. PROTECT International Exhibition and Conference on Security and Safety
- Date: March 16 - 17 2020
- Location: Manila, Philippines
- Cost: for visitors - Free; For delegates - $625
- http://protect.leverageinternational.com
Leverage International (Consultants) Inc. arranges this annual international seminar and demonstration on safety and security. PROTECT first started in 2005 by the Anti-Terrorism Council. This conference is the one government-private division partnership sequence in the Philippines dedicated to protection and security. It contains a global display, an excellent level symposium, free to go to practical workspaces, and networking prospects.
17. TROOPERS20
- Date: March 16 - 20, 2020
- Location: Heidelberg, Germany
- Cost: 2,190€ - 3,190€
- https://www.troopers.de
The TROOPERS20 conference is a two-day event providing hands-on involvement, discussions of current IT security matters, and networking with attendees as well as speakers.
During the two-day seminar, you can expect discussions on numerous issues. There are also practical demonstrations on the latest research and attack methods to bring the topics closer to the participants.
The conference also includes discussions about cyber defense and risk management, as well as relevant demonstrations of InfoSec management matters.
18. 27th International Workshop on Fast Software Encryption
- Date: March 22 - 26, 2020
- Location: Athens, Greece
- Cost: $290 - $630
- https://fse.iacr.org/2020
The 2020 Fast Software Encryption conference arranged by the International Association for Cryptologic Research, will take place in Athens, Greece. FSE is broadly renowned as the globally prominent occasion in the field of symmetric cryptology.
This event will cover many topics, both practical and theoretical, including the design and analysis of block ciphers, stream ciphers, encryption schemes, hash functions, message authentication codes, authenticated encryption schemes, cryptanalysis, and evaluation tools, and secure implementations.
The IACR has been organizing FSE seminars since 2002 and is an international company with over 1,600 associates that brings researchers in cryptology together.
The conference concentrates on quick and protected primitives aimed at symmetric cryptography which contains the examining and planning of:
- Block Cryptographs
- Encryption Structures
- Stream Codes
- Valid Encryption Structures
- Hash Meanings
- Message Valid Schemes
- Cryptographic Variations Examination and
- Assessment Apparatuses
They’ll address problems and resolutions concerning their protected applications.
19. Vienna Cyber Security Week 2020
- Date: March 23 - March 27, 2020
- Location: Vienna, Austria
- Cost: $295
- https://www.energypact.org
Austrian non-governmental affiliates, international governmental entities, and the Energypact Foundation present this year’s conference. Its focus is to connect with significant global investors in the discussion and collaboration of the discipline of cybersecurity. The primary focus is an analytical structure with an emphasis on the energy subdivision.
20. Cyber Security for Critical Assets (CS4CA) the USA
- Date: March 24 – 25, 2020
- Location: Houston, Texas, United States
- Cost: $1,699 - $2,999
- https://usa.cs4ca.com
The Yearly CS4CA features two devoted issues for OT and IT authorizing representatives to enhance their professional areas of attention. The discussions intend to tackle some of the most common problems that connect both sets of specialists.
Each issue is curated by a set of industry-prominent professionals to be as significant, up-to-date, and detailed as possible for two days. Throughout this conference, you can expect the opportunities to take relevant tests, as well as to get inspired by some of the world’s prominent cybersecurity visionaries and network with colleagues.
21. World Cyber Security Congress 2020
- Date: March 26 - 27, 2020
- Location: London, England, United Kingdom
- Cost: £195 - £295
- https://www.neventum.com/tradeshows/world-cyber-security-congress
The World Cyber Security Seminar is an advanced international seminar that interests CISOs as well as other cybersecurity specialists from various divisions. Its panel of 150 + outstanding speakers represent a wide range of verticals, such as:
- Finance
- Retail
- Government
- Critical Infrastructure
- Transport
- Healthcare
- Telecoms
- Educational Services.
The World Cyber Security Congress is a senior-level meeting created with Data Analytics, Heads of Risk and Compliance, CIOs, and CTOs, as well as CISOs and Heads of Information of Security in mind.
22. InfoSec World 2020
- Date: March 30 - April 1, 2020
- Location: Lake Buena Vista, Florida, United States
- Cost: $50 - $3,695
- https://www.infosecworldusa.com
The 2020 InfoSec World Seminar will feature over one hundred industry specialists to provide applied and practical instructions on a wide array of security matters. The 2020 conference offers an opportunity for security specialists to research and examine concepts with colleagues.
Throughout the conference, attendees will have plenty of opportunities to increase their knowledge from this world-class seminar platform headed by the industry’s prominent specialists. They will also have a chance to receive 47 CPE credits over the one week course or attend New Tech Lab assemblies presented in real-life scenarios. Attendees also have the opportunity to participate in a virtual career fair where you can join via your tablet or at the fair section of the Expo.
Lastly, attendees have availability to take advantage of the Disney Resort with associates and guests.
23. 19th Annual Security Conference
- Date: March 30 - April 1, 2020
- Location: Las Vegas, Nevada, United States
- Cost: $398 - $498
- http://www.security-conference.org/w
The 19th Annual Security Conference provides an opportunity for discussions on security, assurance, and privacy that improve the understanding of current events but also encourage future dialogues related to cybersecurity.
The 2020 security seminar is a portion of the Vegas Conferences prepared by:
- University of Houston, USA
- University of Arkansas, USA
It provides a forum for discourses in Security, Assurance, and Privacy that enhance the understanding of current events, but also nurture future dialogues related to cybersecurity.
24. World Border Security Congress
- Date: March 31 - April 2, 2020
- Location: Athens, Greece
- Cost: €200 - €7980
- https://world-border-congress.com/conference/programme
The 2020 World Border Security Congress is a conference which is planned by Torch Marketing. This seminar will contain subjects such as perimeter surveillance methods and schemes and will include:
- The Latest Threats and Challenges at the Border
- Continuing efforts against foreign terrorist fighters, irregular migration, and human trafficking
- Capacity Building and Training in Border and Migration Management
- Securing the Littoral Border: Understanding Threats and Challenges for Maritime Borders
- Pre-Travel Risk Assessment and Trusted Travellers
- The developing role of Biometrics in identity management & document fraud
- Smuggling & Trade in Illicit Goods, Antiquities and Endangered Species
- The Future Trends and Approach to Alternatives for Securing Borders
Join global leaders as they discuss issues surrounding improvements to the defense and administration of protracted land boundaries.
25. Black Hat Asia 2020
- Date: March 31 - April 3, 2020
- Location: Singapore, Asia
- Cost: $1,700 - $2,200
- https://www.blackhat.com/asia-20
The sharpest industry professionals and scholars will come together for a four-day event at the 2020 Black Hat Asia. This function contains two days of intense applied training followed by another two days of the most current studies and susceptibility discoveries at these meetings. The Black Hat Executive Summit offers CISOs and other cybersecurity executives an opportunity to hear from a variety of industry experts who are helping to shape this next generation of information security strategy.
Black Hat delivers attendees practical lessons on subjects such as:
- Wider-ranging Offensive Security
- Penetration Testing
- Analyzing Automotive Electrical Systems
- Mobile Application Automation Testing Tools and Security
- Infrastructure Hacking
These practical attack and defense lessons created entirely for Black Hat Asia and prepared by some of the prominent specialists in the industry are available to you. They each share the objective of distinguishing and protecting tomorrow’s information security environment.
26. ASIS Europe
- Date: April 1 - 3, 2020
- Location: Prague, Czech Republic
- Cost: £420 - £1,175
- https://asiseurope.org
This event’s purpose is to assist security professionals in finding the best ways to assess risks and act accordingly – not in legal arrangements or disclaimers but having the risk owner and user make educated decisions.
CONFERENCE
For aspiring and established leaders in need of a comprehensive learning experience, including masterclasses, executive sessions, keynotes, and show pass.
CLASSROOM TRAINING
For managers and team members who are seeking to gain attentive, practical skills with precise learning outcomes. Show pass included.
27.
- Date: Apri 2, 2020
- Location: Falls Church, United States
- Cost: $300
- https://event.potomacofficersclub.com/event/summary/701f30000016AR5AAM
The 2020 forum will feature keynote speaker Katie Arrington, chief information security officer at the Office of the Assistant Secretary of Defense for Acquisition of the USA. She is a 2020 Wash100 Award recipient. The themes to be addressed are the Cybersecurity Maturity Model Certification’s (CMMC) timeline. And how the certification process could change, explaining the functionality of the newly established CMMC accrediting body. Learn about the impact DoD’s CMMC will have on supply chain security, cybersecurity practices, and other aspects of the federal market.
28. CyberCentral 2020
- Date: Apri 4 - 5, 2020
- Location: Prague, Czech Republic
- Cost: €799 - €1,349
- https://infosec-conferences.com/events-in-2019/cybercentral
The 2020 CyberCentral conference is a two-day event where participants collaborate with a global community of compatible cybersecurity enthusiasts. This event is a limited occasion, which allows its participants to walk away revitalized with resilient H2H networks, instead of with a lot of brochures and business cards.
29. Infiltrate Security Conference
- Date: April 19 - 24, 2020
- Location: Miami Beach, Florida, United States
- Cost: $1,800 - $2,200
- https://infiltratecon.com
Infiltrate is an in-depth technical conference whose focus is on aggressive security issues. Innovative researchers come together to evaluate and share experiences regarding the latest technological strategies that you cannot find elsewhere. Infiltrate is the leading event for those who are focused on the technical aspects of offensive security issues, such as:
- Reverse-Engineering
- Modern Wi-Fi Hacking
- Linux Kernel Exploitation
- IoT Exploit Development
- Vulnerability Research
Infiltrate avoids policy and elaborate presentations in favor of just diehard thought-provoking technical topics.
30. Industrial Control Systems (ICS) Cyber Security Conference
- Date: April 21 - 23, 2020
- Location: Singapore, Asia
- Cost: $895 - $1,295
- https://www.icscybersecurityconference.com
The ICS Cyber Security Conference is an event where ICS users, vendors, system security providers, and government representatives meet to discuss industry trends. The convention’s goal is to analyze the latest threats and their causes to offer effective solutions for businesses of different sizes.
31. QuBit 2020 Cybersecurity Conference
- Date: April 22 - 23, 2020
- Location: Prague, Czech Republic
- Cost: 450€ - 1,170€
- https://qubitconference.com
The 2020 QuBit Cybersecurity Conference aims to provide up-to-date data to the cyber community of Central Europe from the western realm. Also, it hopes to aid in the circulation of security materials such as IT and internet tools that are now available to over two billion individuals internationally.
QuBit offers you a unique way to meet advanced and elite individuals with impressive backgrounds in the information security industry. Connect with QuBit today and discover the latest revolutions and ideas that are paving tomorrow‘s industry platform.
32. CSO50 Conference + Awards
- Date: April 27 - 29, 2020
- Location: Scottsdale, Arizona, United States
- Cost: $495
- http://www.csoconference.com
The yearly CSO50 Awards acknowledges fifty businesses, including the employees, for their security development or inventiveness that exhibits exceptional commercial worth. The award-winning organizations are revealed in a special announcement and have their project summarized in an editorial on csoonline.com.
Attending this seminar is one of the best ways to boost your employees’ and colleagues’ esteem, as it gathers some of the industry’s top thought leaders. It can also be an excellent hiring device for those seeking to find new cybersecurity talents. Another benefit includes project winners asked to exhibit their projects at the CSO Conference + Awards.
Team members of winning projects are also offered courtesy registrations to the seminar. Lastly, the winning company will be announced at the CSO50 Awards dinner and summoned on stage to accept their award.
33. 15th Annual Secure360 Twin Cities
- Date: May 5 - 6, 2020
- Location: Minneapolis, Minnesota, United States
- Cost: $749
- https://secure360.org/secure360-twin-cities
The 2020 Secure360 Twin Cities conference is a seminar for education in comprehensive security and risk organization. This event offers partnership and teaching for your whole team.
Secure360 concentrates on the following:
- Risk and Compliance
- Governance
- Information Security
- Professional Development
- Continuity Management
- Business Continuity
- Physical Security
Key speakers will cover topics such as “Leading from any seat: Stories from the cockpit & lessons from the Grit Project” and Information Warfare: How our phones, newspapers, and minds have become the battlefield.”
34. THOTCON 0x9
- Date: May 8 - 9, 2020
- Location: Chicago, Illinois, United States
- Cost: $75 - $370
- https://www.thotcon.org/registration.html
THOTCON 0x9 is a yearly hacking seminar that takes place in Chicago, Illinois. More than 1,300 specialists and speakers from all over the world attend the event each year.
THOTCON is a non-profit, non-commercial event offering the best seminar conceivable on a restricted budget. When you go to a THOTCON event, you will have undergone one of the best information security conferences around the globe, combined with an exclusively casual and social experience.
35. CyberTech Asia
- Date: June 19 - 20, 2020
- Location: Singapore, Asia
- Cost: $525 - $865
- https://www.cybertechisrael.com/asia
CyberTech Asia 2020 provides attendees with innovative and unique opportunities to gain insight into the latest improvements and resolutions presented by the global cyber public.
The conference’s central focus is on networking as well as reinforcing associations and establishing new contacts. CyberTech also delivers an unbelievable stage for B2B collaboration. CyberTech Asia will join the following:
- Leading Multinational Corporations
- Start-ups
- Corporate and Private Investors
- Specialists
- Clients
- SMB’s
- Venture capital firms
36. The 18th International Conference on Applied Cryptography and Network Security
- Date: June 22 - 25, 2020
- Location: Rome, Italy
- Cost: £250 - £450
- http://www.wikicfp.com/cfp/servlet/event.showcfp?eventid=89998©ownerid=100775
ACNS is an annual conference concentrating on current advances in the fields of practical cryptography and its implementation to systems and network security. The objective of this workshop is to exemplify academic research in addition to advances in engineering and practical frontiers.
The Computer Security group is organizing the conference at Sapienza University. The proceedings of ACNS 2020 are to be published by Springer in the LNCS series.
37. ToorCamp 2020
- Date: June 23 - 28, 2020
- Location: San Juan, Washington, United States
- Cost: $1,337
- https://toorcamp.toorcon.net
The ToorCamp first opened in 2009 in Washington State at the Titan-1 Missile Silo and is the American hacker camp. The next two conferences occurred in 2012 and 2014 on the Washington Coast. At these seminars, you are encouraged to display projects, share ideas, and collaborate with technology specialists that are attending the event.
38. 20th International Conference on Cyber Security Exercises (ICCSE)
- Date: July 16 - 17, 2020
- Location: Bali, Indonesia
- Cost: €250 - €350
- https://waset.org/cybersecurity-and-security-engineering-conference-in-july-2020-in-bali
The 2020 International Conference on Cyber Security Exercise focuses on joining prominent researchers, experts, and professors to discuss and disclose their knowledge and investigations on every feature of cybersecurity implementations. This year’s focus is on the fields of Cybersecurity and Security Engineering.
Don’t Miss Out!
When you attend security conferences, you benefit in multiple ways. Specialists teach you. You can take advantage of colleague-to-colleague discussions for professional improvement.
Most importantly, attending seminars presents the opportunity for you to obtain the information you need to tackle cyber attacks. Every minute of the day, there is someone somewhere creating the next cyber threat that could shut your business down.
Take advantage of learning how to stay one step ahead but getting your company and its employees ready and prepared for the next threat. It is no longer a matter of if it is a matter of when.
Are you ready?
Recent Posts
81 Eye-Opening Data Breach Statistics for 2020
Living in the modern world means integrating technology into almost every aspect of our daily lives. This symbiotic relationship with technology opens us up to becoming highly susceptible to hacking. This vulnerability extends from our smartphones, personal and work computers, transport, bank, and credit card purchases to every small smart device you have installed in the home or workplace.
Why are Data breaches and Cybersecurity breaches a growing concern?
Internet users and consumers might not be concerned enough about the threat of hacking, the real scenario is far from being safe. It is estimated that the world over a typical “hacking activity” attack occurs every 39 seconds.
Large companies and Federal Departments including The US Office of Personnel Management (OPM), Anthem Blue Cross, Yahoo, Uber, Quora, Facebook, Cathay Pacific, Marriott International, Equifax, LinkedIn, etc., have all experienced cyber threats in the past few years. No one is immune.
Recently it’s become apparent that the complexity, frequency, and expense of data breaches are ever-increasing. Many major cyber-attacks have targeted high profile companies in the United States, Europe, and Australia. To counter this, new legislation has been introduced in affected countries, aimed at changing the rules related to threat timeframes and user notification.
We aim to present a comprehensive picture of an alarming threat of cybercrimes and data breaches, something which affects customers, social network users, and even companies. Information is presented in a series of points, covering the most critical cybersecurity statistics for 2019-20.
Costs of a Data Breach
A single instance of a data breach can have immense implications on a business. A smaller sized-company could be put out of business due to a large breach. Below are some statistics related to how costly data breaches are, as of 2019/20.
- Experts agree that by the year 2020, the average cost of a data security breach for a major business would be over $150 million. This estimate is due to the higher level of digitalization and connectivity that the world has experienced over the last few years. [BigCommerce]
- The average total cost per data breach worldwide in 2019 amounted to a total of $3.92 million and $3.5 million in 2014. [IMB]
- The average price for a Business Email Compromise hack is $24,439 per case, according to a 2019 report by Verizon. [Verizon]
- Organizations reporting phishing and social engineering attacks are increasing by 16% year over year. [Accenture]
Data Breach Numbers and Risks
The 2019 Thales Data Threat Report – Global Edition issued by Zurich Insurance, found that rapid digitalization and the internet of things has expanded the connectivity of the developed world and its infrastructure.
To keep up with rapidly expanding and sophisticated technologies, many companies are investing in their service usability. Chasing greater competitiveness, they are migrating to cloud or multi-cloud environments very quickly. This is when the data storage is maintained by a company itself or in tandem with a third party. This hybrid structure can make data very difficult to secure, states the Threat Report.
Most organizations are finding it challenging to control internet security breaches and implement strong safety measures. It’s even harder for smaller and mid-sized companies who due to budget constraints or lack of staff make them vulnerable to attack. The risk of a data breach can be due to a combination of reasons, with some companies being more susceptible than others. The top risk factors are explained below using the relevant statistics.
- A typical user has a 27.9% chance of experiencing a data breach that could affect a minimum of 10000 records. With a total of 6,466,440 (estimated) records succumbing to data breaches worldwide daily. [Security Intelligence]
- The financial sector accounts for 14% of all data breaches. In 47% of all financial data breaches, the victim is a bank. [Fortunly]
- Increasingly more malware attacks, 25.7%, are targeting global financial services and banks. [Intsights Cyber Intelligence]
- Year-over-year increases for compromised credit cards is 212%, credential leaks are 129%, and malicious apps is 102%. [Intsights Cyber Intelligence]
- The United States is in the number one position when it comes to the risk of data breaches. [Statista]
- Reports from 2018 indicate that phishing attacks targeted 76 % of businesses. [Wombat]
- Almost 41% of US-based companies allow employees unrestricted access to sensitive data. [Varonis]
- Experts have calculated that almost 25% of enterprises would succumb to data breaches through IoT devices by the year 2020. The figure poses a problem, as a mere 10% of IT security budgets allocated by companies are directed towards smart device security. [Gartner]
- An estimated 10 million records have been compromised worldwide due to data breaches, as calculated by the Breach Level Index since 2013. The average cost of the data breaches is somewhere around $3.86 million. [Thales Security]
- 88% of businesses have over 1 million folders, do not limit employee access to company files. [Varonis]
- Over 4.5 billion data records were affected by data breaches in the first half of 2018, which equates to over 1 million data breaches per hour. [Gemalto]
- Data breach instances were reported in 2019, with the first half of 2019, experiencing an 11% increase compared to the previous year. [Accenture]
- According to the Imperva 2019 Cyberthreat Defense Report, It’s expected that 57.6% of Government organizations, 73.5% of educational organizations, and 74.5% of retail organizations are at direct risk of suffering data breaches or compromises.
- The 2019 Thales Global Threat Report study revealed that there are some areas where encryption rates are higher, thereby preventing attacks. They are the IoT (42%), containers (47%), and big data (45%). Data encryption makes information unreadable and therefore useless to hackers and allows companies to guard their sensitive data and corporate secrets.
Business Continuity Plan
Having a Business Continuity Plan (BCP) is critical in the face of a data breach. A plan would outline the type of data being stored, where it’s stored, and what the potential liabilities are when implementing data security and recovery actions. AON’s 2019 Cyber Security Risk Report outlined that most organizations are missing a BCP.
When you investigate what’s causing data breaches, many times, it’s criminal activity or human error, or a mix of both. But the most common cause is the failure of organizations to prepare and do assessments in advance to identify their weaknesses. And failing to come up with answers to remedy and recover from their disadvantages. Taking care of weak passwords, improper configuration, untrained staff, or an outdated OS are all things companies can do beforehand to prevent attacks.
Incident Response
A BCP will also entail an effective cyber incident response plan. This refers to an organized approach that is aimed at addressing, managing, and rectifying the damages, in the aftermath of a cyber-attack or data breach incident.
- Organizations take up to 197 days on an average to detect data breaches. [IBM’s Ponemon Institute]
- Companies that contain a data breach in less than 30 days are expected to save over $1 million in finances.[IBM’s Ponemon Institute]
- The FBI’s Internet Crime Complaint Center (IC3), reports that the number of cybercrimes reported account for only 10-12% of the actual number occurring. [FBI IC3]
Largest Data Breaches in History
The number of instances related to data breaches has been steadily increasing since 2013, with an estimated 14,717,618,286 cases where data has been either stolen or lost. Below are some of the most prominent instances of data breaches ever recorded in recent years.
- Target in 2013: The data breach was carried out via malicious software installed on machines used by customers to pay with their cards. A total of 110 million Target accounts were compromised. [Forbes]
- E-Bay in 2014:The data breach was carried out using stolen login credentials from a small number of employees. A total of 145 million eBay accounts were compromised. [Business Insider]
- Anthem Inc. in 2015: The data breach was carried out by hackers after they infiltrated the company server. A total of 37.5 million personally identifiable records of customers were stolen. [Threatpost]
- Yahoo! in 2013/2014: One of the most significant data breaches occurred in 2013-2014, where Yahoo’s 3 billion accounts got compromised. It was a coordinated attack by an organized, unidentified cyber-criminal organization. [REUTERS]
- AOL in 2003: An estimated 92 million customer accounts were compromised after Jason Smathers, a 24-year-old AOL software engineer, caused the security breach. [WIRED]
- Quora in 2018: The data breach was caused due to unauthorized access by a malicious third party. One hundred million user accounts were compromised. [Quora]
- Facebook in 2018: This data breach was caused after hackers exploited a vulnerability in Facebook’s “View As” code. They were left with 50 Million compromised accounts. [The Guardian]
- Marriott International in 2014/2018: The breach occurred due to unauthorized access to the guest’s information database. As a result, over 500 million user accounts were compromised. [Forbes]
- Uber in 2016: Attackers, in this case, obtained credentials and accessed Uber’s cloud servers. They then got access to sensitive user information. As a result, more than 57 million users and driver accounts were compromised. [TechCrunch]
- Equifax in 2017: The data breach occurred as a result of a vulnerability in the open-source software used to access its servers. As a result, the personal information of 143 million consumers was exposed. [Forbes]
- Aadhar Data breach in 2018: The Indian Government’s national ID database, which stores “Aadhar” information, succumbed to a cyber-attack in March 2018. The personal data of over 1.5 billion Indian citizens, including phone numbers, addresses, ID numbers, etc., were left exposed on the web. Experts have labeled this as one of the worst data breaches of all time. [TechCrunch]

Click here to see the full infographic!
Data Hacking Trends
With the exponential growth of the cloud and IoT applications, such as connected health devices, house or child monitoring equipment, and smart cars. The demand for data-centers keeps increasing. This is also increasing new forms of cybercrime since all these devices are now hackable, susceptible to IoT attacks. It’s not surprising since connected devices are becoming more and more entangled and integrated into everyday lives.
In only 2 years, the total data stored in the cloud – which includes everything from public clouds operated by third-party vendors, government-owned clouds, social media companies, and private clouds run by mid-to-large-sized companies – will be a hundred times greater than today.
Modern hacking trends include a myriad of cybercrime techniques aimed at compromising data. Some of the most dangerous and common types of security threats include:
- Attacks related to ransom malware have caused damages worth almost $1 billion. US users have paid $ 25 million worth of ransom. [Whitehouse Council of Economic Advisors]
- Hacking crimes due to Social engineering account for 97% of the total hacking cases in the world. It also accounts for 93% of data breaches. [PwC Report 2018]
- An estimated 4000,000 DDos attacks were reported monthly in the last few years. [Caliptix Security]
- Service Denial attacks have numbered close to 800000 cases in the first couple of months in 2018 alone.
- [PwC Report 2018]
- 2018 has also seen almost 61% of organizations succumbing to IoT device hacks. That number has risen to 64% in 2019. At the end of 2018, more than 23 billion IoT devices were installed worldwide. [Newsweek]
- Attacks related to phishing and pretexting comprise of nearly 98% of the total incidents involving social channels in 2019. Verizon’s 2017 DBIR revealed that it was still a significant factor in data breaches. [Verizon]
- In a report from Forrester, their research revealed that only 12% of breaches were targeting public cloud environments. 37% of decision-makers believed that heightened security made the migration to the public cloud vital to future success. [Forrester]
The motivation behind cybercrime remains financial gain and has remained the dominant motivator behind cyberattacks, at a rate of 88.1%. Cyberattacks as a form of technology warfare have been rising recently, up to 4% as of January 2019, when only a month earlier, in December 2018, the rate was 2% according to Privacy Affairs. Governments and non-government organizations have taken part in cyber warfare, and that rate should continue to grow as technologies become more integrated into the public’s lives.
C-suite and Cybersecurity
- According to a recent survey carried out on C-suite users, a total of 53% of respondents indicated “cybercrime and data breaches” as the number one concern when it comes to cybersecurity. [IBM Study]
Increased attacks on Service Providers
Attacks on service providers such as Yahoo, AML, etc. have seen a stark rise in the last 6 or 7 years.
- Yahoo faced the worst service provider attack with instances affecting 3 million, 500 million, and 200 million user accounts in 2013, 2014, and 2016 respectively. [NYTimes]
Organizational vulnerabilities
- Both medium and small-scale organizations are losing an estimated $120,000 on average due to service denial attacks. Another figure indicated that enterprises could lose more than $2 million in total, due to denial of service attacks. [Security Intelligence]
- An estimated 61% of organizations worldwide have succumbed to IoT system hacking in 2018 alone. [CSO Online]
- In 2019, 64% of companies that allocate more than 10% of their budget towards cybersecurity experienced at least one breach. 34% of the companies indicated that they experienced a data breach last year. [Helpnet Security]
Third-party/Supply-chain risk
- Most data breaches are caused by malicious activities outside the entity, as a study found that it accounts for 56% of total data breaches in 2018. Malicious insiders account for only 7% of the violations. [Statista]
- Intrusions caused by Phishing attacks have affected 82% of manufacturers in the U.S, which also covers the industrial supply chains present in the manufacturing sectors. [phishing box]
- Almost 59% of UK and US-based companies who have used a third-party service have experienced data breaches. Of them, a measly 16% of them think that the third party’s risk management system is effective enough in 2019. [Business Wire]
Skills Shortage in CyberSecurity
The overall level of skills when it comes to Cybersecurity measures has not matched up to the required standards.
- 38% of global organizations claim that they can handle a sophisticated cyber-attack. [IBM]
- This is a worrying statistic, as over 54% of the world’s organizations have experienced some sort of significant cyber-attack in the past year. [IBM]
- In 2018-2019, almost 53 percent of organizations reported a problematic shortage of cybersecurity skills. [Security Intelligence]
- Cybersecurity engineers will soon be the highest-paid among all IT professionals in 2020, more than software engineers, systems administrators, IT auditors, and software architects. With salaries exceeding $225,000 annually. [InfoSec]
Trends in HIPAA Data Breaches
- In America, the total number of medical records that have been exposed throughout 2019 amounts to a total of 38 Million. [HIPAA JOURNAL]
- The U.S. Department of Health and Human Services experienced 52 data breaches in October 2019 alone. [HIPAA JOURNAL]
- 2015 is still the worst year for data breaches in this sector, with two instances exposing 78.8 million and 11 million customers, respectively. [appknox]
Cybersecurity Spending
As the threat of cybersecurity intensifies, the overall amount spent on cybersecurity has been increasing since 2015.
- The U.S. President’s Budget allocated towards cybersecurity rose to $15 Billion for 2019. [Whitehouse Cybersecurity Funding]
- This is a stark increase of $583.4 Million of almost 4.1% from the budget allocated for 2018. [Whitehouse Cybersecurity Funding]
- The largest contributor to the budget was the Department of Defense, which allocated $8.5 Billion, an increase of $340 million compared to the previous year (2018). [Whitehouse Cybersecurity Funding]
- How much are companies spending on cybersecurity? In 2018, in excess of $114 billion was spent globally on information-security products and services. It’s expected to grow to $170.40 billion by 2022. What’s driving this spending are business needs, security risks, and industry changes. Privacy has also become an important factor according to 2019 cybersecurity statistics. [Gartner]
- In 2020, almost fifty-two percent of companies believe that cloud computing is a priority for cybersecurity investment. [Safe At Last]
- Cloud computing providers will spend more on security spending by 57%. The other areas that will see more development are IoT, mobile computing, cybersecurity analytics, and robotic process automation. [Forrester]
- by 2023, businesses are expected to spend $12.6 billion on cloud security tools, that’s more than double from the $5.6 billion spent in 2018. [Forrester]
Prevention and the Future
The modern, inter-connected world is increasingly falling under threat from growing instances of cybercrimes. Many large companies have fallen prey to such elaborate cybercrime schemes and have lost millions on lawsuits to recover the situation.
In 2018 alone, data breaches affected 45.9% of businesses, 29.2% of medical and healthcare institutions, 10.9% of banking, credit or financial institutions, and 8% of government or military associated companies and departments. [Digital Information World]
The number of data breaches per year in the United States has gradually increased since 2014: [Statista]
- 783 cases in 2014
- 781 cases in 2015
- 1093 cases in 2016
- 1579 cases in 2017
- 1244 cases in 2018
When it comes to 2019, however, the numbers have skyrocketed.
- There were more than 3800 reported cases of breaches in 2019. [Forbes]
- Compared to the first six months of 2018, there has been a 54% increase in the number of reported breaches. [TechRepublic]
- These breaches exposed records which were 52% more than that of 2018. [Risk Based Security]
The largest data breaches in 2019:
- A total of 620 million accounts suffered a data breach in 2019, from a total of 16 websites. [Forbes]
- Websites such as Dubsmash, Armor Games, ShareThis, Whitepages and 500px were among those affected. [IT Governance UK]
Prevention is always better than cure and is most applicable when dealing with cybercrimes. With different forms of cybersecurity, ranging from malware, phishing, denial of service, SQL injection, Zero-day exploits, DNS tunneling, and others, the need for effective cybersecurity measures is of utmost priority.
Cybersecurity measures range from simple to complex. Necessary preventive measures such as password protection and authentication, are not enough to prevent more elaborate and complex cyber threats that are faced by companies today.
From a business perspective, data breaches can never be ignored, and appropriate measures must be taken by the companies, something which is lacking as of now. As hackers find more elaborate ways to breach security, countermeasures need to be in place. The only way to tackle such threats is to develop sophisticated security techniques, as well as to educate users and employees about the dangers of the different forms of cybersecurity threats prevalent currently.
If left untreated, cybercrimes and data breaches can hamper the reputation of a company, assets, finances, and even their existence, which means there will be no future if you don’t start prevention now. Find out more on how to secure your data in the cloud, by connecting with one of our experts.
Key Takeaways for Statistics on Data Breaches
- As an increasingly large number of systems and processes go online, customers, businesses, and governments become more vulnerable to cybercrime and attacks.
- To counter the threat of cybercrime, organizations must increase their investments in cybersecurity and deploy them correctly. Also, to train their workforce regularly.
- Outside comparing the numbers of attacks in 2019, what’s evident is that the variety and severity of cyberattacks are on the rise.
- Plan and prepare by updating your OS regularly. Train employees on the dangers of social engineering. Disallow the downloading of unfamiliar apps from unknown sources.
- If a cyberattack does occur and hackers demand payment, by not reporting it and giving in, will be the easy way out. Hackers will come back for more if they can profit. To avoid future cyberattacks means reporting crimes to the authorities and refusing to pay. This will make future attacks less likely.
Recent Posts
Data Breach: What It Is and How to Prevent One
Data breaches are occurring at an unprecedented rate, and there are no signs that they will slow down any time soon. If you’re one of the many organizations that store sensitive information online, then you’re at risk. Now is the time to learn more about the impending dangers businesses face and how to implement vital data protection practices.
What is a Data Breach?
In any instance, when information is accessed without authorization, it’s a data breach. The types of violations can vary and evolve as technology diversifies, but to put it simply, the information in the wrong hands constitutes a data breach. Information can become compromised in many ways now; a cyber-attack is only one. As the name implies, it’s a confirmed incident when an unauthorized entity has accessed confidential, sensitive, or protected information. Big data is now the norm, as more devices become connected. Those valuable connections also become points of weaknesses. Data breaches can wreak havoc on the reputations of businesses and induce a ripple of after-effects that can leave lasting repercussions.
For instance, a business may have to pay hefty fines due to a breach. Outside of regulatory penalties, they may have to compensate the victims whose data was compromised. Even a minor data breach could put an SMB out of business due to the financial constraints of fines, lawsuits, and loss of public trust. When someone steals secure data and publishes it on the web, it’s out there for the world to see. As more data becomes digitized, and we generate more original digital data, it’s logical that more data breaches will occur.
Recent History of Data Breaches
For the first time since 2013, this past year ransomware declined down 20 percent overall, but up 12 percent for enterprises according to Symantec. The most successful campaigns in 2019 involved ransomware that relies on open Remote Desktop Protocol (RDP) servers as the initial access point. Attackers more commonly use targeted, manual attacks instead of the one-two punch of malvertising exploits. The first quarter of 2019 saw the detection of several new ransomware families using innovative techniques to target businesses.
One of the most recent and significant data breaches occurred in September 2017 with the Equifax data breach, which exposed the personal data of 147 million people.
A few other prominent data breach examples include:
- Yahoo: Between 2013 and 2014, over three million user accounts affected.
- Marriott International: From 2014 to 2018, over 500 million of their user accounts were breached.
- Target Stores: In December of 2014, approximately 110 million of their user accounts got hacked.
- JP Morgan Chase: In July of 2014, around 76 million residential and seven million small business Chase customers had their financial records breached.
- A May 2019 ransomware attack on the City of Baltimore is expected to cost in excess of $18 Million to recover from.
The average cost per ransomware attack to businesses last year was $133,000. Attacks on Brittan’s National Health Service in 2017 cost nearly $100 Million in IT recovery services alone. Yet, the cost of customer confidence and company reputation can be unmeasurable.
Four Common Causes of Data Leaks
| Human error | Errors cannot be avoided, people make mistakes, and information may get distributed without mal intent. Proprietary data can get sent accidentally to the wrong person, and uploads to public folders or misconfigured servers can bleed sensitive information. |
| Theft or loss of devices | We all have devices. From smartphones to laptops, hard drives, USBs, and other data storage devices can easily get stolen, misplaced, lost, or disposed of incorrectly. Sensitive or protected information saved on those devices can end up in the wrong hands and lead to a more significant data breach. |
| Employee data leak or theft | When a company terminates an employee or ends a contract with notice, that person may deliberately access protected information without permission and copy it. They may use or distribute it with malicious intent. |
| Cyberattacks | Hacking is the most apparent form of a data breach. Hackers use malware, phishing, social engineering, skimming, and scams to get access to sensitive and encrypted information. |
The Reality of Ransomware
Now that we know how data breaches and hacks can occur, we can look at why criminals are looking for a way to penetrate your firewalls. One major ploy cybercriminals use is Ransomware which is a form of extortion. It’s is a malware that infects, overtakes, and locks your data making it inaccessible unless a ransom is paid. The threat could be to publish a company’s data, erase it or perpetually block access to it, which can cripple a business.
The FBI warns not to pay a ransom, but many companies will be at a loss if they can’t access their sensitive data. Since ransomware is so profitable for hackers, attacks have skyrocketed. According to a Quickbridge study, over 4,000 separate ransomware attacks have occurred since 2016. Furthermore, they estimate the damages will reach around $11.9 billion globally.
It’s essential to know which types of information are the most valuable to cybercriminals. Cybercriminals may use programs that mine and lock your data, later using it for ransom. This attack is known as ransomware. Hackers can hold businesses hostage if vital information is leaked and user information exposed. Such an occurrence was the Ashley Madison hack of July 2015.
There are three main reasons a hacker wants your data:
- To sell it on the black market
- Identity theft
- Simply because they can
There’s no such thing as being ‘too safe’ in this digital era. One hundred percent secure may not exist as of yet, but you can take practical steps to mitigate the potential for massive data loss.
What to Do in Case of Ransomware Attack
Here are some ransomware response strategies:
| What you should do: |
|
| What you shouldn’t do: |
|
How to Prevent Security and Data Breaches
If you run a business, then it is likely you store personal information about your employees, customers, and others digitally or online. Since data breaches are on the rise, all organizations must start taking more detailed steps to prevent a data breach. By implementing protection best practices you will stay ahead of potential attacks and ensure the safety of your business.
Ransomware protection and response best practices were in focus of our recent webinar with Veeam. With October being National Cybersecurity Month, we thought it is the right time to revisit it.
Take a look at the recording below and get insights from William Bell, EVP of Products from phoenixNAP, and Brandon McCoy, Cloud Sales Engineer from Veeam.
Here is a detailed checklist we recommend you go through to start consolidating your online security:
Don’t click on email attachments
Spammers and hackers are becoming more ingenious in their attempts to trick people into open email attachments. It’s no longer the Nigerian prince asking you to wire donations to his kingdom. Now you get emails from the IRS, Social Security Administration, and sometimes even someone that looks like one of your relatives. Spammers find relatives by searching your name from any number of person search sites, or social media which display the names of your relatives.
Before clicking on any email attachment, stop and ask yourself if you know the person or organization, and were you notified of an incoming attachment? If you answer no to any of those two questions, don’t open the attachment. In essence, you should delete the email immediately.
When in doubt, you can do a little investigative work to check if an email is legit. For example, check to see if info@paypal.com does originate from the official site. How? In your email client, display the email header information. There, it will be evident if the email did not come from paypal.com. If there are links in the email, hover over one of them, but don’t click it! You should see a popup or hint that displays the full URL. If it doesn’t start with a paypal.com domain, it’s a fake.
Implement and use 2FA
2FA or Two Factor Authentication is a security method that verifies you. You’re already familiar with website logins. 2FA takes logins a step further. It does this by checking if it’s genuinely you that is logging in with your credentials. 2FA does this by asking for additional information. After you enter your login info, the 2FA scheme will send a text code to your verified phone number. Which in turn, you must enter into the login screen to gain access.
There isn’t a field on the login screen to enter your device’s phone number. That would defeat the purpose of 2FA since a spammer would be able to enter their mobile number and hijack the auth code. Instead, the mobile number you saved in your account is used. By involving another device that only you have access to, 2FA provides more confidence that the person logging in is you.
A 2018 study by Carnegie Mellon University found that over 75 percent of study participants thought 2FA made their accounts more secure, but 50 percent thought the process was annoying. 2FA also helped to stop dangerous security practices, such as credential sharing.
Never share your social security number
Most job applications will ask for your social security number to perform a background check. Outside of job applications and government organizations, there is no need to provide your social security number. Some companies may ask for it to set up an account for you. You can decline, and ask that the company uses another identifying number. After all, you have no idea what sort of security practices go on at any company.
Lockdown physical assets
Keep physical locks on any devices which contain sensitive data and are vulnerable to hacking.
Restrict access
Limit access to sensitive data, to employees on a straightforward need-to-know basis.
Update all your operating systems
Through cloud computing, these should be updated consistently and automatically. It’s always safer to ensure you have the latest versions with the most recent security fixes and patches installed.
Schedule regular updates for applications
Some apps will have to be updated manually, where others will be updated automatically. This rule is critical since earlier versions will have loopholes that hackers can exploit.
Use SSL in your email client
When using a desktop email client, the client connects to your email provider’s servers to receive and send emails. With some providers, you have the option to use a non-SSL connection. This can prove risky.
A non-SSL connection will send your non-encrypted email login credentials over the Internet. When you connect to a public or unsecured WiFi network (i.e., coffee shop or hotel), your email credentials will be vulnerable. Always use SSL when connecting to your email provider.
Use machine-generated passwords
With the advent of keyword loggers and even cameras spying on networks and devices, it’s imperative to use a machine-generated password.
Furthermore, hackers often play the guessing game too. One of the most popular passwords are names of personal pets. Using social media, it’s not hard to discover your pet’s name. For example, a simple Facebook search can give any hacker that type of personal information.
Play it safe by using something generated for you, and it is also completely random. If storage and memory pose an issue, then use a password manager.
Use Strong Complex Passwords
Don’t use the same password across multiple logins, even if you have used a password generator. Each login should be different. If one login is compromised, at least your other logins are safe – for now. By diversifying with strong secure passwords, you are essentially creating a firewall between each login.
Use a Credit monitoring service
Credit monitoring services can alert you to suspicious activity within your financial accounts. Credit monitoring services are convenient because you can monitor activity within all of your financial accounts, and through all three credit bureaus.
If you don’t want to pay for a monitoring service, most credit cards and bank accounts have alerts that inform you of suspicious activity. It’s triggered when a transaction exceeds a specific dollar amount, or a questionable purchase has been made on the card.
Contact your financial institution immediately
If you see suspicious activity on one of your business accounts, contact your financial institution right away. Your institution has protocols in place for events like these.
Train and educate your employees
The Office of the Future survey, Canon USA reported that more than one-third of respondents consider malware and ransomware a priority threat. Yet, 25% of respondents say that employees have limited to no security awareness, nor do they understand their role in prevention.
For better overall security, it’s essential to train your employees on your most recent security protocols. Create written privacy and data security policies. Educate your employees on those policies, and make them aware of their responsibilities for keeping company data secure. Offer this type of training at least two or three times per year.
If you’re self-employed, use an EIN instead of your social security number
If you are self-employed and have to fill out W-9s and 1099s, use a federal EIN. Using the Employer Identification Number means you do not need to use your social security number. And this protects you from becoming a victim of identity theft.
Conclusion
Data breaches are an unfortunate part of doing business online and participating in digital activities. In this article, you can learn to arm yourself and your business with protective knowledge and strategies and best practices to avoid data breaches. You can drastically reduce the possibility of your private data ending up online, or in hands, you don’t want it to be.
If you are still unsure about how to secure your business online, contact phoenixNAP today to get more information on how to develop your own strategy.
Recent Posts
What is Cyber Security? Challenges and Threats Organizations Face
Cyber Security is a vital component of every companies infrastructure. Success depends on a company’s ability to protect its proprietary information and customer data from those who would abuse it. Regardless of size, scope, or industry, every company that wants to survive must answer two fundamental questions:
What is Cyber Security?
How to create a successful Cyber Security strategy?
This article will answer both of these questions.
A Definition of Cyber Security
Cybersecurity is a series of protocols that a company or an individual follows to enure information maintains its “ICA” – integrity, confidentiality and availability. If you have the right security in place, you will have the ability to recover very quickly from power outages, errors or hard drive failures. It will make your ogranization less vulnerable to external attacks and hackers. You will get protection from sophisticated criminal groups and ‘script kiddies’ that have the capacity to execute APTs, otherwise known as advanced persistent threats.
The concepts of business continuity and disaster recovery are the base strategies of good cybersecurity. Business continuity is essential to the survival of a business. Recovering from threats quickly means you can retain your audience during problematic situations. Problems will less likely become customer-facing issues if there is a plan in place. Disaster recovery means maintaining the integrity of your data and your infrastructure after a catastrophic event. These threats are ultimately classified by the level of cybersecurity currently implemented in your digital infrastructure.
The Importance of Cybersecurity
Why should security be at the forefront every company’s agenda? Why should senior management, including non-tech C-suite decision-makers, concern themselves with cybersecurity?
There is one undeniable reason: The digital world in which we do business is vulnerable and open to attack.
Digitization brings with it endless opportunities for innovation. It still has a long way to go before becoming a fully secure ecosystem that is programmed to regulate and control itself. Decision-makers should ensure that all systems in their company adhere to the latest high-security standards. Employees must also be trained in basic cyber-security protocols too. This is especially true of non-tech employees. For instance, everyone needs to know how to identify a phishing email and how to quarantine it, while notifying the proper authority, both internal and external.
The odds are against you without the right security strategy. Even with the strongest controls in place, count on those controls to be tested. Attackers know how to find weak spots and exploit them, opening holes up that bring down stronger systems. The solution is having good ‘cyber hygiene’, or practicing the fundamental security tasks that will keep the majority of threats out.
Challenges of Cyber Security
The best cybersecurity strategies go well beyond the basics mentioned above. Any sophisticated hacker can avoid these simple defenses. Cybersecurity also becomes more difficult as a company expands. For example, the ‘attack surface’ of a Fortune 1000 company is much larger than a small to medium-sized business.
Expanded Attack Opportunities for Hackers
Another challenge of cybersecurity is dealing with the increasing overlap between the physical and virtual worlds of information exchange. As driverless cars and other self-regulated devices become the norm, the Internet of Things (IoT) and BYOD business policies give criminals more access to cyber-physical systems. That include cars, factories, the smart fridge and toaster in your kitchen, to even one’s medical pacemaker. In the future, infiltrating one of these systems may mean infiltrating them all.
Complicated Regulation
The regulatory environment is also complicating cybersecurity, especially the political discussions around consumer privacy. The European Union recently implemented the General Data Protection Regulation (GDPR) framework, creating more hurdles for companies to ensure they can do business without incurring hefty fines. The security mandates of regulatory agreements like the GDPR require all companies to be held to a higher standard, which can translate into more complications for SMBs and startups in the short term. In the long term, the virtual environment would likely be safer for everyone involved. However, there is a balance that must be achieved between protecting the consumer and offering that same consumer the choice of new business.
Lack Of IT Talent
A critical challenge of cybersecurity is the lack of qualified professionals to do the job. There are many people on the low end of the cybersecurity spectrum with generic skills. Security Experts who know how to protect companies from sophisticated hackers are rare. Those who know how to get things done understand how in-demand they are. When they work, they charge fees that most smaller enterprises cannot afford. Only the biggest and richest companies in the world can afford these elite-level services, another hurdle that SMBs have to overcome to compete online.
Types of Cyber Security
Cybersecurity covers is a wide subject matter. Below, we will go through the core types of cybersecurities. A holistic strategy includes all of these aspects and overlooks none.
Critical Infrastructure
The critical infrastructure of the world functions as a cyber-physical hybrid.
Everything from hospitals to water purification plants to the electricity grid are now plugged into the online world and digitized. We gain many advantages from this super-structure. Putting a system online, however, also creates new vulnerabilities to cyber-attacks and hacking. When a company first connects itself to the physical and then digital world, the first infrastructure it plugs itself into is the critical infrastructure.
Company decision-makers must include this perspective into their plan on how attacks might affect their functionality. If a company does not have a contingency plan, it should create one immediately.
Network Security
The security of a network protects a company against unauthorized access and intrusions. Proper security over a network can also find and destroy internal threats to the system as well.
Effective implementation of network security often requires some compromise and trade-offs. For instance, extra logins help to protect a company’s information from unauthorized access, but it also slows down company productivity. One of the significant problems of network security is that it uses a lot of company resources.
Network security tools generate huge amounts of data. Even if a network security system finds a threat, it might slip through the cracks, ignored, due to the sheer volume of data that’s being produced. IT teams are now using machine learning to automate the identification of legitimate security threats, thereby reducing human error. But it’s far from a perfect system.
Cloud Security
Cloud security is a set of policies, controls, and procedures, combined with technologies that work together to protect data, infrastructure, and cloud-based systems.
They are specific security measures which are configured to protect a customer’s privacy, guard data, support regulatory compliance, and also sets authentication rules for devices and users. This means anything from filtering traffic, authenticating access, and configuring cloud security for specific client needs. It’s mobile since it’s configured and managed in one location, and frees up businesses to focus resources on other security needs.
Application Security
Many of the best modern hackers find web application security the weakest point to attack an organization.
It’s hard to keep up with them due to the proliferation of new relationships with apps companies have which are not yet properly vetted and secured. Application security starts with great coding, which is also challenging to find. After attaining secure coding practices, penetration testing and fuzzing are the two other security practices every company should begin to implement now.
Internet of things (IoT) Security
The IoT is an important cyber-physical system in how online systems communicate. More specifically, IoT refers to a system of interrelated computing devices, which can be defined as mechanical and digital machines, or objects, animals or people which are given unique identifiers (UIDs) and become digitized in some capacity. It also refers to the distinct ability of this system to transfer data over a network without needing human-to-human or human-to-computer interactions.
IoT will only become more critical to business as time goes on. The Internet of Things will connect consumers in neighborhoods and neighborhoods to critical infrastructure in an unprecedented manner. In a few years, a hacker may open up and exploit someone’s refrigerator or choose to shut down electricity to an entire town – if we are not careful. Today, IoT devices often are shipped to consumers in an insecure state. There are many devices that have no patching for security either, which makes them prime targets for botnets.
Developing a Cyber Security Strategy
Every strategy should be custom-designed. A cybersecurity strategy that works for one company will not necessarily be effective for another. It’s different for every entity based on their specific needs and vulnerabilities.
However, there are some overarching themes that you can take into account regardless of your company size, scope, or industry.
Understanding risks to critical business operations
Cybersecurity is continually becoming more complex. Organizations must have a ‘security vision’ about what cybersecurity means to their operations. This includes generating an acceptable level of risk and prioritizing areas to target for the majority of security investments.
Integrating the strategy across departments
A good security strategy must work across all the security measures that a company already has in place. Companies should intervene smartly in crucial areas to close off backdoors and improve overall security.
Deter the threats on the inside
Many of the backdoors and vulnerabilities that doom a company to cyber victimhood begin from an internal problem. A part of every cybersecurity package should include internal monitoring to prevent insiders from using their access maliciously. Protective monitoring also helps a company to differentiate between insider attacks that are purposeful or accidental.
Plan for breaches ahead of time
Understand that hackers are always one step ahead of the curve in security. No matter how good your defenses may be, they will be breached at some point in time. Instead of waiting in fear for the inevitable, prepare for it. Boost your disaster recovery and business continuity metrics so that when something does happen, you can return to normal functionality as quickly as possible.
With the basics of cybersecurity covered, should a company now feel relaxed with their new insights into protections? Not at all. Cybersecurity means remaining eternally vigilant in a constantly moving digital ecosystem. The solutions that work today will not work tomorrow. Hackers will have figured out something else by then, and they will be at your front door with even more powerful executions.
Here is a cybersecurity checklist to get you started:
- Put Policies and Procedures in Place
- Ensure Gateway Security
- Have End Point Security
- Implement Identity and Access Management
- Implement Multi-Factor Authentication
- Get Mobile Protection, Secure Remote Access, and Virtual Private Networks
- Have Wireless Network Security
- Back up and Disaster Recovery
- Provide Employee Security Awareness Training
Reduce Your Cybersecurity Risk
It’s imperative to use the best practices and tips mentioned above as a starting point to ensure that you’re moving in the right direction. It can mean the difference between life and death for your business. Or save you millions in legal fees that can come along with e-Commerce security threats. Don’t allow the trust that your customers have placed in you to be threatened or breached. And that’s exactly you need to invest in smart cybersecurity services today.
Recent Posts
31 Must-Know Healthcare Cybersecurity Statistics 2020
The healthcare industry is a prime target of hackers. The importance of cybersecurity in healthcare is an essential consideration for all organizations handling patient data.
Be aware of the latest numbers; read our article on the latest Healthcare Cybersecurity Statistics.
Healthcare Data Breaches, By the Numbers
1. 89% of healthcare organizations experienced a data breach in the past two years. Despite the sophisticated measures put in place by providers to prevent data breaches , they are still common. (Source: Dizzion).
2. A Mid-Horizon study concluded that approximately 100 percent of web applications connected to critical health information is vulnerable to cyber attacks. Network penetration results also showed that hackers could easily access domain level admin privileges of most healthcare applications. As a result, the use of advanced technologies such as block-chain and cloud computing is necessary to ward off such attacks in the future. (Source).
3. It is estimated that the loss of data and related failures will cost healthcare companies nearly $6 trillion in damages in the next three years compared to $3 trillion, in 2017. From a statistical point of view, it is the most significant transfer of wealth in human history. If proper security measures are not taken, experts believe that cybercrime can have a devastating financial impact on the healthcare sector in the next four to five years. (Source).
4. 82% of surveyed healthcare organizations agree that digital security is one of their foremost concerns. (Source: Health IT Security)
5. 55% of healthcare companies in the United States faced cyber attacks. Almost one-fifth confirmed that they had been attacked in the last 12 months. (Source).
Healthcare Ransomware Statistics
Ransomware has brought many a healthcare organization to its knees. It is likely to remain one of the most prominent threats of 2019 and beyond. Despite increasing awareness among healthcare professionals, the number of ransomware attacks continues to grow.
6. Ransomware attacks on the healthcare sector will quadruple by 2020. Attackers like to attack the healthcare sector due to the potential value of such data. The healthcare sector is prone to paying the ransom because the disruption, lost productivity, and damage to the data can be more expansive than preventing the loss by paying the ransom. (Source: Herjavec Group Healthcare Report)
7. As of 2018, the number of ransomware families dropped from 98 to only 28. However, there were 350 different variants of ransomware observed in 2018 compared to 241 in the previous years. It means that ransom-takers are using more sophisticated tactics to hack into vulnerable systems. (Source)
8. Healthcare organizations are more willing to pay ransom to avoid downtime and gain access to critical patient data. It is estimated that 23 percent of healthcare organizations paid some form of payment to the attackers. The healthcare industry is vulnerable because it uses legacy systems that are mostly out-dated and vulnerable to attacks. (Source: Infosecurity Magazine)
9. Organizations that handle healthcare data that fail to update their systems may face grave consequences in the future. The majority of healthcare ransomware attacks were malware related. Of the 2,600 incidents reported, 36 percent were malware related followed by accidental disclosure in 26 percent of the cases. (Source: Beazley Breach Briefing)
Implementation of Advanced Security Technologies To Fight Back
10. The nature of cybersecurity spending in the healthcare sector varies significantly due to the specific requirements of organizations. A majority of companies are spending their budgets on network security and investing in mobile protection measures. Another 51% are also spending on advanced technologies that will make data on the move more secure during data transfers. (Source: HIPPA Journal)
11. A large number of healthcare firms are migrating to a cloud-based solution. Despite the safety as their prime concern, 25% of the firms suggest that they are not encrypting their information during data transfer to the cloud. 38% of firms that have data in a multi-cloud environment such as Amazon Web Service does not use encrypted technology. (Source: Hytrust)
12. 60% of healthcare organizations globally have introduced IoT devices into their facilities. The Internet of Things has seen an exponential rise in the use of IoT enabled devices in a range of fields. Wearable and implantable IoT devices are already widely used in healthcare, including insulin level monitors to pacemakers. (Source: Statista)
Cybersecurity IT Talent: Human Weakness
We tend to think of cybersecurity as a system of digital checks and balances. But while this is important, organizations should still consider the human component. Even if you’re spending heavily on automated systems, it means little if you don’t have the right people to implement and manage them.
13. 42% of healthcare organizations leave their cybersecurity in the hands of a vice president or C-level official (Source: Chime).
14. 39% report their biggest challenge when it comes to implementing cyber defenses is the lack of qualified employees (Source: HIPAA Journal).
15. 37% say that less than 1 in 4 candidates are skilled enough to keep their companies secure (Source: Health IT Security).
16. Cybersecurity requires specific knowledge and skills to secure and combat attacks. Often, these skills are not easy to find as 27 percent of healthcare firms reported that they are unable to find suitable candidates to fulfill cybersecurity roles. Another 14 percent suggested that they are not sure if they will be able to fill vacant positions. The ISACA State of Cyber Security Report also concluded that 45 percent of firms don’t think that their applicants understand the nature of their job (Source).
17. If the budget doesn’t restrict healthcare firms to improve their security, the complexity of the system does. 53 percent of the healthcare firms surveyed revealed that complexity of healthcare systems is the major issue holding them back. Healthcare systems can be complicated as lack of experienced and knowledgeable staff to handle such complex systems is another significant concern, cited by 39 percent of firms (Source: Thales Data Threat Report).
18. For small and medium-sized healthcare firms, cloud adaption is a haven from cyber attacks. Despite the early adaption of cloud-based technology by the healthcare sector, nearly 40 percent of these organizations do not have a dedicated staff that can deal with cloud-based problems. Without a dedicated team, small healthcare organizations can face threats while operating in a cloud environment. (Source: HIPPA Journal)
19. The most significant internal cybersecurity threats to healthcare are often high-ranking officials and senior staff who have deep access to the system. A whopping, 61 percent cited senior-level executives as a potential security loophole that can be vulnerable to cyber threats. Similarly, privileged users, such as executive managers, contractors, and service providers, are potential targets for hackers and cybercriminals. (Source: HIPPA Journal)
20. 59% of healthcare organizations get at least five applications for each cybersecurity job, while 13% receive 20 or more. While these healthcare security statistics make for sobering reading, there is some good news. The right candidates do appear to be out there. (Source: Health IT Security).
21. 54% of healthcare associates say their biggest problem is employee negligence in the handling of patient information (Source: Ponemon Study).
Healthcare Companies are Fighting Back
21. Healthcare organizations are taking cyber security seriously as 62 percent of companies have reported that a Vice President is in charge of cybersecurity issues. 41 percent of organizations are in the process of implementing a fully functional security program to address critical problems. (Source: Health IT Security)
22. Recent attacks on healthcare have prompted healthcare companies to increase their cybersecurity budgets from a maximum of 10 percent to almost 25 percent, in 2018. The increase in the budget is correlated to an increase in hiring staff for a specific purpose. In 2016, eight percent of the healthcare companies had more than 10 employees dedicated to the task, which increased to 11 percent, in 2017. (Source: Health IT Security)
23. In 2018, 60 percent of these firms put particular emphasis on cybercrime by increasing their staff, adding new technologies, and training their employees on such issues. Cybersecurity budgets continue to grow as 81 percent of U.S. firms indicate that they will improve their resources to keep critical systems safe. (Source: Healthcare IT News)
24. 57 percent of companies are ensuring that they meet local and global compliance standards of Internet security required in the healthcare sector. Of these, 34 percent confirmed that they are already looking to implement cybersecurity best practices for employees. (Source: HIPPA Journal)
25. Security breaches caused by the loss of sensitive items, such as laptops and other devices, have decreased sharply. While loss or theft of items accounted for nearly 90 percent of the losses in 2010, it has reduced to only 15 percent, in recent years. This is a clear sign that educating employees to take care of their data devices is critical to preventing incidents of theft. (Source)
26. 54% of healthcare organizations believe they have technologies in place to effectively prevent or quickly detect unauthorized access to patient data. An improvement over the 49% reported in 2015. (Source: Ponemon Institute)
5 Largest Healthcare Cyber Security Attacks & Breaches
Here are some of the most significant healthcare data breaches. What can your organization learn to avoid being the next victim?
1. LifeBridge Health
This Baltimore-based healthcare system experienced a malware attack last March. The attack potentially breached the data of around 500,000 patients. Investigations showed that the hackers first gained access to the system back in September 2016.
2. Health Management Concepts
This ransomware attack fast became a full-blown data breach. Hackers were mistakenly provided with a file containing the personal data of over 500,000 patients.
The organization has not disclosed how or why hackers got this information, but the file contained Social Security numbers, health insurance information, and patient names.
3. CNO Financial Group
Between May and September of last year, hackers gained access to the credentials of CNO employees. This information was then used to access company websites, compromising the data of over 566,000 policyholders and applicants.
Data accessed included dates of birth, insurance details, and partial Social Security numbers.
4. UnityPoint Health
UnityPoint suffered two security breaches last year. The second compromised the data of 1.4 million patients.
A series of phishing emails had been made to look like they were from a top executive within the company. When an employee fell for the scam, it gave hackers access to private email accounts.
5. AccuDoc
The data breach of billing vendor AccuDoc was the biggest of last year. The North Carolina-based vendor prepares patient bills while managing Atrium Health’s billing system. The investigation revealed that while hackers could view the data, they were unable to extract it.
Don’t Become a Healthcare Security Statistic
From these healthcare statistics, it is apparent that there has been an increased awareness among healthcare companies regarding cybersecurity. Despite the response, more needs to be done. All types of hacking attacks are also becoming more sophisticated and the data loss more costly. Solutions start with awareness, updating and maintaining critical systems, and emphasis on security during data transfer.
How vulnerable is your organization? Work with our team of security professionals and ensure that your employee and patient data is secure.
Recent Posts
35 Network Security Tools You Should Be Using, According To The Experts
Securing a network can seem overwhelming. The world of Security can be complicated. Network security tools assist in securing your monitoring IT environment.
The more tools an InfoSec professional has to work with, the better they will be able to address the task at hand. Access to a wide range of computer network security software is only the start. Knowing how to put them to use is the essence of network protection.
New security threats seemingly appear daily. The progressive nature of these attacks requires dynamic multi-point security solutions. It is critical administrators quickly identify vulnerabilities to protect data security.
We have collected the best security tools to combat network threats. These applications should make for a strong starting point for anyone working in Information Security. Don’t miss the expert contributors!

Network Security Monitoring Tools
Argus
One of the best free and open source tools available for network traffic analysis. Argus stands for Audit Record Generation and Utilization System. The program does just what the acronym says. Efficient, in-depth analysis of network data, sifting through big chunks of traffic with fast, comprehensive reporting. Whether or not it’s the only traffic monitoring tool users need, it provides a solid foundation.
P0f
P0f remains popular in spite of a lack of updates. The program has scarcely changed in over a decade because it was just about perfect on release. Streamlined and efficient, P0f generates no additional traffic. It can be used to identify the operating system of any host with which it interacts. Many tools in this category create probes, name lookups, assorted queries, and so on. P0f is light, fast, and clean-running. A must-have for advanced users, but not the easiest to learn for the rookies on the team.
Nagios
Nagios monitors hosts, systems, and networks, delivering alerts in real-time. Users can specify exactly which notifications they want to
receive. The program can monitor network services, including HTTP, NNTP, ICMP, POP3, and SMTP, among others.
To many, Nagios is The name in traffic monitoring. A comprehensive, all-bases-covered approach to network management. One of the most powerful free tools for cybersecurity professionals and small businesses alike.
Splunk
Designed for both real-time analysis and historical data searches. Splunk is a fast and versatile network monitoring tool.
One of the more user-friendly programs with a unified interface. Splunk’s strong search function makes application monitoring easy. Splunk is a paid app with free versions available. The free version is limited. This is an excellent tool to put on the list for those who have a budget to work with. Independent contractors tend to be careful about the premium tools they buy. Splunk is well worth the cost. Any information security professional with a strong enough client base should invest in Splunk.
OSSEC
OSSEC open-source intrusion detection service provides real-time analytics of system security events.
It can be configured to be constantly monitoring all possible sources of entry and access, including files, rootkits, logs, registries, and processes. It is also available for a variety of platforms, such as Linux, Windows, Mac, BSD, and VMWare ESX. The OSSEC user community is also good at sharing strategies, modifications, support, and other useful information. Other available tools include “Atomicorp,” which provides ‘self-healing’ to automatically fix detected vulnerabilities, and Wazuh, which offers training and support.
InfoSec professionals honestly need a lot of tools to do their work. If only had to choose one; it would be a properly tuned Data Analytics Aggregator or SIEM software; e.g., Splunk
There's too much data to try to parse and correlate between devices and hosts on your own. You need to be collecting decrypted packets and logs and then enriching it with threat intelligence.
At least for our group, our backbone is Splunk-the features that set it apart from most SIEMs is that it handles unstructured data quite well and can scale easy. Most shops only utilize logs, and maybe NetFlow.
With Splunk, we can utilize every use case our engineers can create use cases and content for. Splunk while not a SIEM by itself, can be made to do it and add the predictive analytics out of the box. It also Supports both push and pull models.
Dennis Chow CISO of SCIS Security
Encryption Tools
Tor
Tor gained a lot of press when people started talking about the “dark web” some years back. The dark web turned out not to be as scary as urban legends made it out to be. Tor is just a tool to ensure privacy on the Internet. The system routes requests to proxy web servers for privacy, making users harder to track. Although there are malicious exit nodes used to sniff traffic, this isn’t a significant concern with careful use. Tor’s applications in InfoSec are more plentiful than its applications in cybercrime.
KeePass
Used in identity management, KeePass is a necessity for many office settings. A simple password management system. KeePass allows users to access all of their accounts with one password. Combining convenience with security, KeePass lets users set unique passwords for different accounts with an auto-fill function when typing in the master password. Those who have dealt in InfoSec for more than a day know how important this can be. Sometimes a security issue just comes down to bad password management. KeePass helps network security officers manage the human element of the job.
TrueCrypt
TrueCrypt remains popular despite having gone years without updates. Abandoned by its developer in 2014, TrueCrypt is technically outdated, yet still a strong tool. A disk encryption system, TrueCrypt allows for layered content encryption with two tiers of access control. Free, powerful, open software. It’s easy to see why TrueCrypt remains popular despite not having been updated in four years. One of the best open source security programs available.
Kali Linux is a security system designed for digital forensics and penetration testing which now can run on both Linux distributions and Windows operating systems. It is compatible with a wide range of wireless devices. It is valued for more than 600 tools geared towards various information security tasks, such as Penetration Testing, Security Research, Computer Forensics, and Reverse Engineering.
QRadar SIEM, IBM's Security Intelligence Platform that provides real-time visibility of the entire IT infrastructure. The system boasts an extensive set of modules (Log Management, Security Intelligence, Network Activity Monitoring, IT Security Risk management, Vulnerability Management, and Network Forensics) that are available through a single web-based console. QRadar is a commercial tool, but you can use its free version with 50 Events per Second (EPS) limit known as Community Edition.
Dmitry Nikolaenya, SIEM department coordinator at ScienceSoft

Web Vulnerability Scanning Tools
Burp Suite
A powerful tool for network protection. Burp Suite is a real-time network security scanner designed to identify critical weaknesses. Burp Suite will determine how cybersecurity threats might invade a network via a simulated attack. The suite is available in three versions: Community, Professional, and Enterprise. Professional and Enterprise are paid application testing tools, including the web vulnerability scanner. The Community version is free but severely limited. Community includes only the essential manual tools. Burp Suite is a potent tool for businesses, but perhaps pricey for smaller organizations. Still, a critical application security testing tool.
Nikto
One of the best open-source vulnerability scanner management tools. Nikto will scan web servers and networks for matches with a database of over 6400 threats. Although the network protection software itself has not been updated in some time, it is still up to date. This is because the threat database is regularly updated. There are also countless plugins being released and continuously updated. For many security professionals, Nikto is a cornerstone of the vulnerability scanning routine.
Paros Proxy
Java-based web proxy Paros Proxy includes several useful tools for running security tests. These include a web spider, traffic recorder, and vulnerability scanner. Excellent for detecting network intrusion openings to some of the most common threats, including detecting SQL injection attacks and cross-site scripting.
Very easy to edit with even rudimentary Java or HTTP/HTTPS knowledge. Anyone who can write a web application can edit Paros Proxy. An excellent network protection software testing tool for identifying a security risk before it becomes a security breach.
NMap
Companies seeking improved access to potential weak spots in their network can use this free open source monitoring tool. It has been designed to offer a close look at every network. Including indicating hosts, what services are being provided at each host, what types of packet filters are in use and other features.
Nmap also includes a debugging tool for all major platforms and can be used to scan one network at a time or multiple networks at once. The network security tool is designed to be user-friendly and can be easily customized.
Nessus Professional
For all the times that your organization may have improperly configured security settings or put in the wrong patch, this software corrects mistakes and improves the integrity of your networks.
Nessus identifies and repairs detected vulnerabilities, including missing or incomplete patches; software bugs; or other general misconfigurations throughout applications, devices, and operating systems.
Along with the Pro version, admins/security experts can consider a free open source scanner that looks for possible exploits. One advantage of the Nessus service is daily database updates. Current information about threats and patches are always available. It also just doesn’t check to see if version numbers match, but programs are doing what they’re supposed to. Users can access a variety of security plug-ins as well as develop their own and scan individual computers as well as networks.
Available for Unix and Linux systems, there’s also a Win32 GUI client that works with Windows products. Users pay an annual subscription to utilize all its services. Nessus is used by more than 24,000 companies worldwide and claims to have the lowest false positive rate among its competitors, plus offers access to more than 100,000 security plug-ins that are regularly updated.
Nexpose
Nexpose offers real-time, on-premises vulnerability scanning and management.
It helps security/IT teams look for, detect, and reduce possible weak points, and presents ‘live’ views of the network. It also continually refreshes and adapts to new threats in software and data. Another useful feature is its ability to help security teams prioritize the highest vulnerabilities by providing a risk score. This is useful for coordinating responses to multiple breaches or delegating workflow, starting with the weakest areas where the more serious/potentially damaging breaches are more likely to take place.
Kali Linux comes with a number of tools for pen testing and wireless scanning that hackers like to use for scanning networks
It is recommended that security professionals use it as it is a comprehensive toolset that will allow infosec professionals to conduct reconnaissance, scanning, and penetration all on one network security platform, it's also a free tool.
Sanjay Deo, President 24 By 7 Security

Penetration Testing
Metasploit
If you are looking for a penetration testing tool, you’ll appreciate this framework of Metasploit. Available in open source versions for developers/security staff or a commercial Pro version.
Users can use the network security tool from Rapid7 to look for more than 1,500 exploits, including network segmentation security. It also allows companies to perform various security assessments and improve their overall network defenses, so they’re more thorough and responsive.
Kali Linux
Kali Linux offers a security auditing operating system and toolkit with more than 300 techniques to ensure your sites and Linux servers stay safe from attack.
Funded and maintained by Offensive Security, which also operates and moderates an active user community and an extensive database of threats and exploits. Part of this knowledge base includes certification in pen tests and a free online course called Metasploit Unleashed. The toolkit is designed for all security skill levels to use, not just advanced IT pros.
Rapid fire tools helps us identify weaknesses within the network, potential issues, and be able to detect when and where problems will occur. It is more of a proactive than a reactive tool. But it is effective.
Auvik is an on-demand threat monitoring tool for potential network issues. It shows us traffic, connectivity, and networks that we may or may not have seen before. It allowed us to find in multiple companies hidden wireless routers, switches, and more at even the client didn't know about.
We also use an image-based virtual addition of OpenVAS to penetrate test a network for when we get to a new client. It's open source, free, and easy to use. We drop off the computer at a location, let it cook for a week and then produce a report so we can then go back to the client and show them what we have found. Some are surprised, others are terrified.
Trave Harmon, Chief Executive Officer, Triton Computer Corporation
Packet Sniffers and Password Auditing Tools
John the Ripper
Ready to crack some passwords, or at least test how strong yours are?
Openwall is designed to detect weak passwords quickly.
Initially designed for Unix environments, it now works with Windows, OpenVMS, and DOS systems. John looks for common hash-type passwords as well as more complex ciphers and encrypted logins. The Openware community continually provides updates and patches as password technology and security evolves. Users can access a standard wordlist for more than 20 languages that often appear in passwords, plus varieties that include words and letters in several languages.
Cain and Abel
Anyone working in network security will know that UNIX tends to lead the way in free security apps. Windows and Mac users get the ports late, if ever.
However, Cain and Abel is a Windows-only password recovery tool that leads the pack. Capable of recording VoIP conversations; it can decode scrambled passwords and analyze routing protocols. It uncovers cached passwords, reveals password boxes, cracks encryption with brute force style attacks and cryptanalysis, and on and on. Virtually a must-have starting point for packet sniffing routines.
Tcpdump
A Mac, Windows, and Linux app predating market leader Wireshark. Although Tcpdump is not the newest packet sniffer available, it set the standard in the field. Tcpdump remains a favorite network sniffer with ongoing active development and fresh approach. The tool uses fewer system resources than competing options and opens little security risk.
Wireshark
Ethereal was the name that Wireshark debuted under. Modeled mainly after Tcpdump, the console-based tool is an excellent protocol analyzer.
Wireshark offers real-time network analysis. It allows users to view reconstructed TCP session streams. Many prefer Tcpdump for security and system-resource reasons, but Wireshark remains the most popular packet sniffer. The software receives regular updates to outfit its robust packet-sniffing capabilities. Wireshark is an essential tool, even if it’s not every security pro’s first choice.
I would say every IT and Cybersecurity Networking Professional should be using Kali Linux. Some say this is a hacking only tool. I beg to differ.
Kali Linux (historically called Backtrack) is a freely available collection of tools that offers everyone, (network, applications security, information security) something. There are about 100 or more tools in there, and there is a tool for every capability and intention.
You can download the ISO image, burn it on to a CD or put it in a USB flash drive and boot almost any computer into Kali Linux. The image is also bootable into a VM and works from a MAC.
Amar Singh, Founder, Cyber Management Alliance Ltc
Network Defense Wireless Tools
Aircrack
A suite of WEP and WPA cracking tools. Aircrack features ideal internet security solutions for mobile devices. Aircrack is vital for cracking algorithms. The suite’s tools include airdecap for WEP/WPA capture file decryption and airplay for packet injection. Several other tools are included as well, creating a robust set of apps for InfoSec use. For many wireless security tasks, Aircrack is an all-in-one solution. The series of tools available within the suite allows for pros to handle an entire job at once. Some tasks may demand more than AirCrack has to offer. Many tasks can be accomplished only with AirCrack tools.
Netstumbler
Free security software for Windows users. A necessary tool for wardriving, finding open access points in a wireless network. The software is Windows only, and no source code is provided. This can make for a hard sell to some. Being able to edit open source code can be critical for security. NetStumbler’s active WAP-seeking approach makes it very popular nonetheless. NetStumbler is known for detecting vulnerabilities that other security scanner tools miss.
KisMAC
Free software for Mac with an attractive It is accessible even for less experienced users. The Mac OS X port of Kismet, with a very different codebase. KisMAC excels at mapping and penetration testing with deauthentication attacks.
Fognigma creates an encrypted security network by linking randomly leased virtual machines from multiple cloud providers, which then work as one network. Hidden inside this network are an organization's fileshare, chat server, video conferencing, and more - all protected by the same two layers of AES encryption as every connection inside a Fognigma network.
The software is entirely under the control of the organization using it - so there isn't any reliance on a third-party company for intervention or oversite (which is often where breaches occur).
All these features protect against external threats, but Fognigma can protect from internal threats as well. Fognigma gives network admins granular user controls to make Identity and Access Management oh-so-much easier. For each component (be it a fileshare, exit/entry point, files, etc.), groups are created. Put a user in a group, and the user can access that component. A few mouse clicks and precise access to organization resources is completely under control.
Chris Mindel, Dexter Edward
Network Intrusion & Detection
Snort
An enterprise-grade open-source IDS is compatible with any OS and hardware. The system performs protocol analysis, content searching/matching, and detection of various network security attacks (buffer overflow, stealth port scanner, CGI attacks, OS fingerprinting attempts to name a few).
Snort’s ease of configuration, rules’ flexibility, and raw packet analysis make it a powerful intrusion detection and prevention system.
Forcepoint
Forcepoint’s SD-WAN can be customized to keep users from accessing certain types of content, as well as blocking a variety of intrusion attempts and exploits.
Admins also can quickly see activity on all networks and can take action rapidly, instead of taking time to track down problems. The service is primarily for enterprise clients working in the cloud, including being able to block or provide warnings about risky cloud servers. It also can provide extra protection and higher levels of access for more critical areas.
GFI LanGuard
GFI LanGuard includes continuous monitoring, scanning, and patching.
The network security tool is so popular and useful that applying it through a network can help a company demonstrate security compliance. It also provides software and network auditing as needed for vulnerable areas in desktops or mobile devices, and automatically creates patches for Mac, Windows, and Linux systems.
Acunetix
There is always legitimate fear that hackers may attack your business directly through your firewall or via internal threat/social engineering.
Less attention is given to the security risks of web-based applications like shopping carts, login pages, or online forms. Acunetix helps businesses set up defenses for more than 4,500 threats to these types of applications and sites, such as SQL injections. It regularly crawls through your site architecture and performs conventional hacking methods to make sure your security defense respond appropriately. Manual testing is also available for specific areas of concern.
Musubu, R2i's network intelligence service is my preferred tool. It includes open source threat detection engines such as Suricata or AlienVault. Musubu provides an enhanced set of data points. The user experience provides a real sense of the overall security posture of the network.
It focuses on the network of origin in context, as well as what threat is posed by the subnet, and the broader environment of origin. Musubu complements the open source threat detection engines by providing greater detailed business intelligence, including a unique threat score, threat classification, detailed location information, and reduction of false positives.
Bradford Lee, Director of Operations, Release 2 Innovation
In Closing, Information Security Tools
Good network security describes everything that potentially could impact your company’s systems and everything that helps keep those threats away.
Network security tools focus on hardware, software, even policies, and procedures to encourage everyone in an organization to practice smart approaches to keeping data safe. Network security also can include keeping up with global threats and making sure systems stay safe from everyone from individual hackers to larger organized breach attempts.
Recent Posts
Security vs Compliance: Are You Secure & Compliant? Learn the Differences
The time has arrived to think differently about security and compliance. Compliance is not security. In fact, you can be compliant but not secure.
Compliance doesn’t always achieve security.
Preparing For Todays Security Challenges
Information technology has grown in leaps and bounds over the last two decades with the industry set to top $5 trillion in 2019. With this immense growth comes complex new compliance and security challenges. Industry insiders know that it’s increasingly important to understand and control how companies share, store, and receive information. IT compliance frameworks are now in place to ensure this regulation of data happens securely, but they can differ extensively.
Breaking it down to its basics, becoming secure and compliant means securing information assets, preventing damage, protecting it, and detecting theft. These are the main mantras and mandates of cybersecurity teams, as they implement frameworks, which are predominantly technical to achieve compliance.
A company can protect its data accordingly if they follow Compliance frameworks and have quality security in place. To have proper protection, companies must understand that Compliance is not the same thing as security. However, security is a big part of compliance.
What are the Differences Between Compliance and Security?
Compliance focuses on the kind of data handled and stored by a company and what regulatory requirements (frameworks) apply to its protection. A company may have to align with multiple frameworks, and understanding these frameworks can be difficult. Their main goal is to manage risk and goes beyond information assets. They oversee policies, regulations, and laws and cover physical, financial, legal, or other types of risk. Compliance means ensuring an organization is complying to the minimum of the security-related requirements.
Security is a clear set of technical systems and tools and processes which are put in place to protect and defend the information and technology assets of an enterprise. Compliance is not the primary concern or prerogative of a security team, despite being a critical business requirement. Security can include physical controls as well as who has access to a network, for example. Standardized methods and tools provided by specialist vendors make security simpler than compliance. Compliance, on the other hand, can be multifaceted and is based on a company’s data type and security processes.
Compliance and Security Based on Specific Frameworks
Compliance studies a company’s security processes. It details their security at a single moment in time and compares it to a specific set of regulatory requirements. These requirements come in the form of legislation, industry regulations, or standards created from best practices.
Specifically, compliance frameworks include:
HIPAA
HIPAA (Health Insurance Portability and Accountability Act) applies to companies in the Health Insurance industry. It legislates how companies should handle and secure patients’ personal medical information. HIPAA compliance requires companies who manage this kind of information, to do so safely. The act has five sections, which it calls Titles. Title 2 is the section that applies to information privacy and security.
Initially, HIPAA aimed to standardize how the health insurance industry processed and shared data. It has now added provisions to manage electronic breaches of this information as well.
SOX
The Sarbanes-Oxley Act (also called SOX) applies to the corporate care and maintenance of financial data of public companies. It defines what data must be kept and for how long it needs to be held. It also outlines controls for the destruction, falsification, and alteration of data.
SOX attempts to improve corporate responsibility and add culpability. The act states that upper management has to certify the accuracy of their data.
All public companies must comply with SOX and its requirements for financial reporting. Classifying data correctly, storing it safely, and finding it quickly are critical elements of its framework.
PCI DSS
PCI DSS compliance is the Payment Card Industry Data Security Standard created by a group of companies who wanted to standardize how they guarded consumers’ financial information.
Requirements that are part of the standard are:
- A secured network
- Protected user data
- Strong access controls and management
- Network tests
- Regular reviews of Information Security Policies
There are four levels of compliance within the standard. The number of transactions a company completes every year determines what level they must comply with.
SOC Reports
SOC Reports are Service Organization Control Reports that deal with managing financial or personal information at a company. There are three different SOC Reports. SOC 1 and SOC 2 are different types with SOC 1 applying to financial information controls, while SOC 2 compliance and certification covers personal user information. SOC 3 Reports are publicly accessible, so they do not include confidential information about the company. These reports apply for a specific period, and new reports consider any earlier findings.
The American Institute for Chartered Public Accountants (AICPA) defined them as part of SSAE 18.
ISO 27000 Family
The ISO 27000 family of standards outlines minimum requirements for securing information. As part of the International Organization for Standardization’s body of standards, it determines the way the industry develops Information Security Management Systems (ISMS).
Compliance comes in the form of a certificate. More than a dozen different standards make up the ISO 27000 family.
Security Covers Three Main Aspects of Your Business
1. Networks
Networks allow us to share information quickly over vast distances. This also makes them a risk. A breached network can do untold amounts of damage to a company.
A data breach of personal information can cause damage to the company’s image. Data loss or destruction can also open companies to criminal liability, as they are no longer in compliance with regulations. Protecting a network is one of the hardest tasks facing security professionals.
Network security tools prevent unauthorized access to the system. Firewalls and content filtering software protects data as they only allow valid users.
2. Devices
A user’s personal device that connects to a company network can inject unknown code into the system. Similarly, clicking on the wrong email attachment can quickly spread malicious software.
Antivirus and endpoint scanning tools stop attackers from gaining access to the device. Phishing attacks and viruses have known signatures making them detectable and preventable.
Segmenting access to the network by device, user, and facility limits the spread of malicious software.
3. Users
Careless users are a significant risk for any company. They don’t know they have been compromised and don’t know they are enabling an online attack. Phishing emails are now responsible for 91% of successful cyber-attacks.
Training users to be mindful can help limit innocuous yet dangerous actions. Training can increase security if employees know the risks involved in their daily use of technology.
Compliance and Security: The Perfect Alliance
Security is something all companies need. Most will already have some form of protection when it comes to IT infrastructure. This could even mean the bare minimum of having an antivirus installed on a workstation or using the basic Windows Firewall.
Turning security tools into a compliant IT system requires more effort. Company’s need to prove their compliance with the regulatory standards when a compliance audit happens.
Creating one system, an alliance of both security and compliance, in a systematic and controlled way is the first step in reducing risk. A security team will put in place systemic controls to protect information assets. And then a compliance team can validate that they are functioning as planned. This type of alliance will ensure that security controls won’t atrophy, and all the required documentation and reports are accessible for auditing.
Getting Started on a Secure Path
Compliance that meets a specific framework builds trust in a company. Although regulations will be the driving force behind compliance, the added benefits that come with it are helpful.
A formal assessment of security procedures and systems can highlight areas of concern that need clarification and understanding. Although management should trust administrators to make critical decisions affecting a company’s infrastructure, understanding all the relevant information about security rests with management. Using compliance frameworks to find shortcomings in security is essential when looking at those decisions.
The road to compliance starts with:
- Listing the current security tools used.
- Conducting a risk assessment of the types of information processed.
- Studying the requirements related to the framework.
- Analyzing the gaps in your current controls in regards to the requirements.
- Planning the way forward to solve major deficiencies.
- Testing the efficiency of different solutions.
After applying these steps to a system, conducting regular assessments is the key to success. Compliance and security need to work hand in hand; it does not have to be security versus compliance.
They work in unison; how? Using a compliance framework, assessing security systems, correcting deficiencies, and then beginning assessments which are set on a regular schedule.
Security and Compliance: A Symbiotic Relationship
Security and compliance is a necessary component in every sector. Knowing how each relates to data security is critical.
The IT Industry relies heavily on the public’s trust, and companies that provide them with Information Services need to have stellar reputations. A failure in security can break a business.
Security and compliance are different components of a necessary and crucial system. Knowing how each relates to data protection is critical. Each relies on the other to keep data security at its peak. Compliance does not equal security on its own. There needs to be a symbiotic relationship between the two. When a company meets compliance frameworks with its internal security measures, the implementation of both will keep data safe and a company’s integrity and reputation intact.
Now that you understand the differences between security versus compliance read about the best security testing tools recommended by professionals. It’s time to take action against potential data threats and guard your cybersecurity.

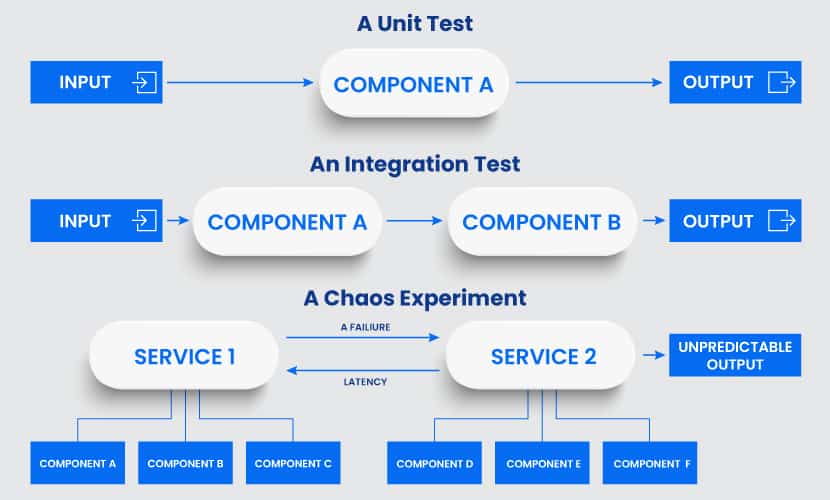
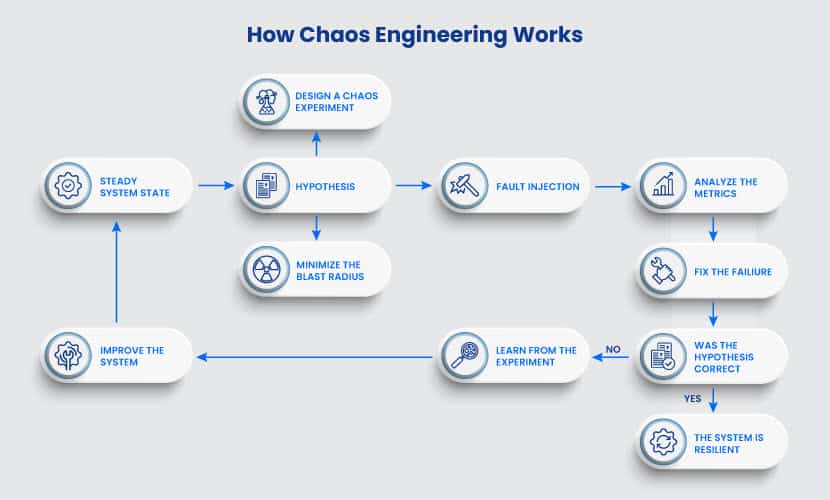
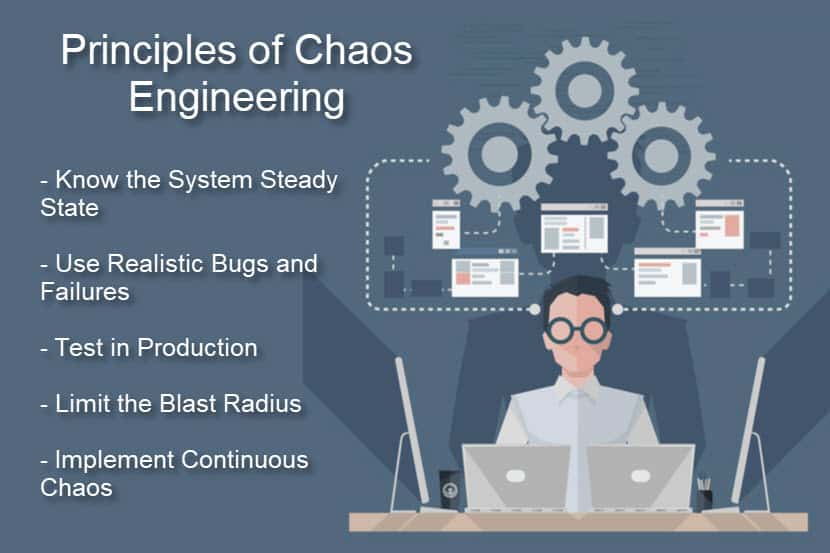

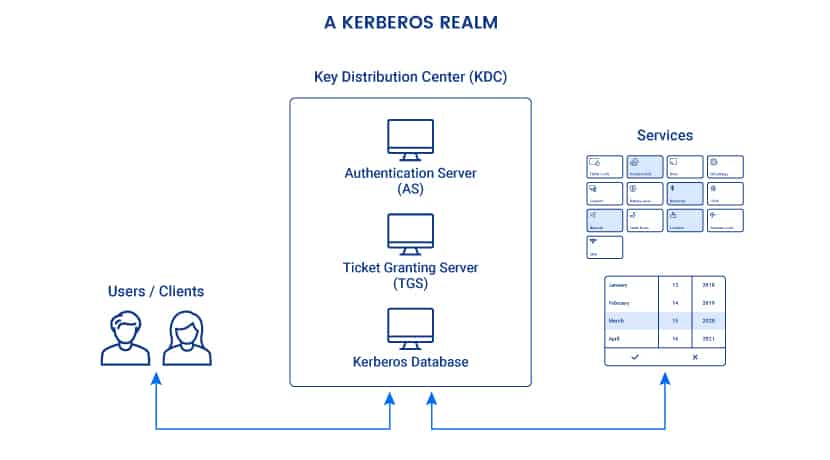 How Kerberos Authentication Works
How Kerberos Authentication Works