Data Breach: What It Is and How to Prevent One
Data breaches are occurring at an unprecedented rate, and there are no signs that they will slow down any time soon. If you’re one of the many organizations that store sensitive information online, then you’re at risk. Now is the time to learn more about the impending dangers businesses face and how to implement vital data protection practices.
What is a Data Breach?
In any instance, when information is accessed without authorization, it’s a data breach. The types of violations can vary and evolve as technology diversifies, but to put it simply, the information in the wrong hands constitutes a data breach. Information can become compromised in many ways now; a cyber-attack is only one. As the name implies, it’s a confirmed incident when an unauthorized entity has accessed confidential, sensitive, or protected information. Big data is now the norm, as more devices become connected. Those valuable connections also become points of weaknesses. Data breaches can wreak havoc on the reputations of businesses and induce a ripple of after-effects that can leave lasting repercussions.
For instance, a business may have to pay hefty fines due to a breach. Outside of regulatory penalties, they may have to compensate the victims whose data was compromised. Even a minor data breach could put an SMB out of business due to the financial constraints of fines, lawsuits, and loss of public trust. When someone steals secure data and publishes it on the web, it’s out there for the world to see. As more data becomes digitized, and we generate more original digital data, it’s logical that more data breaches will occur.
Recent History of Data Breaches
For the first time since 2013, this past year ransomware declined down 20 percent overall, but up 12 percent for enterprises according to Symantec. The most successful campaigns in 2019 involved ransomware that relies on open Remote Desktop Protocol (RDP) servers as the initial access point. Attackers more commonly use targeted, manual attacks instead of the one-two punch of malvertising exploits. The first quarter of 2019 saw the detection of several new ransomware families using innovative techniques to target businesses.
One of the most recent and significant data breaches occurred in September 2017 with the Equifax data breach, which exposed the personal data of 147 million people.
A few other prominent data breach examples include:
- Yahoo: Between 2013 and 2014, over three million user accounts affected.
- Marriott International: From 2014 to 2018, over 500 million of their user accounts were breached.
- Target Stores: In December of 2014, approximately 110 million of their user accounts got hacked.
- JP Morgan Chase: In July of 2014, around 76 million residential and seven million small business Chase customers had their financial records breached.
- A May 2019 ransomware attack on the City of Baltimore is expected to cost in excess of $18 Million to recover from.
The average cost per ransomware attack to businesses last year was $133,000. Attacks on Brittan’s National Health Service in 2017 cost nearly $100 Million in IT recovery services alone. Yet, the cost of customer confidence and company reputation can be unmeasurable.
Four Common Causes of Data Leaks
| Human error | Errors cannot be avoided, people make mistakes, and information may get distributed without mal intent. Proprietary data can get sent accidentally to the wrong person, and uploads to public folders or misconfigured servers can bleed sensitive information. |
| Theft or loss of devices | We all have devices. From smartphones to laptops, hard drives, USBs, and other data storage devices can easily get stolen, misplaced, lost, or disposed of incorrectly. Sensitive or protected information saved on those devices can end up in the wrong hands and lead to a more significant data breach. |
| Employee data leak or theft | When a company terminates an employee or ends a contract with notice, that person may deliberately access protected information without permission and copy it. They may use or distribute it with malicious intent. |
| Cyberattacks | Hacking is the most apparent form of a data breach. Hackers use malware, phishing, social engineering, skimming, and scams to get access to sensitive and encrypted information. |
The Reality of Ransomware
Now that we know how data breaches and hacks can occur, we can look at why criminals are looking for a way to penetrate your firewalls. One major ploy cybercriminals use is Ransomware which is a form of extortion. It’s is a malware that infects, overtakes, and locks your data making it inaccessible unless a ransom is paid. The threat could be to publish a company’s data, erase it or perpetually block access to it, which can cripple a business.
The FBI warns not to pay a ransom, but many companies will be at a loss if they can’t access their sensitive data. Since ransomware is so profitable for hackers, attacks have skyrocketed. According to a Quickbridge study, over 4,000 separate ransomware attacks have occurred since 2016. Furthermore, they estimate the damages will reach around $11.9 billion globally.
It’s essential to know which types of information are the most valuable to cybercriminals. Cybercriminals may use programs that mine and lock your data, later using it for ransom. This attack is known as ransomware. Hackers can hold businesses hostage if vital information is leaked and user information exposed. Such an occurrence was the Ashley Madison hack of July 2015.
There are three main reasons a hacker wants your data:
- To sell it on the black market
- Identity theft
- Simply because they can
There’s no such thing as being ‘too safe’ in this digital era. One hundred percent secure may not exist as of yet, but you can take practical steps to mitigate the potential for massive data loss.
What to Do in Case of Ransomware Attack
Here are some ransomware response strategies:
| What you should do: |
|
| What you shouldn’t do: |
|
How to Prevent Security and Data Breaches
If you run a business, then it is likely you store personal information about your employees, customers, and others digitally or online. Since data breaches are on the rise, all organizations must start taking more detailed steps to prevent a data breach. By implementing protection best practices you will stay ahead of potential attacks and ensure the safety of your business.
Ransomware protection and response best practices were in focus of our recent webinar with Veeam. With October being National Cybersecurity Month, we thought it is the right time to revisit it.
Take a look at the recording below and get insights from William Bell, EVP of Products from phoenixNAP, and Brandon McCoy, Cloud Sales Engineer from Veeam.
Here is a detailed checklist we recommend you go through to start consolidating your online security:
Don’t click on email attachments
Spammers and hackers are becoming more ingenious in their attempts to trick people into open email attachments. It’s no longer the Nigerian prince asking you to wire donations to his kingdom. Now you get emails from the IRS, Social Security Administration, and sometimes even someone that looks like one of your relatives. Spammers find relatives by searching your name from any number of person search sites, or social media which display the names of your relatives.
Before clicking on any email attachment, stop and ask yourself if you know the person or organization, and were you notified of an incoming attachment? If you answer no to any of those two questions, don’t open the attachment. In essence, you should delete the email immediately.
When in doubt, you can do a little investigative work to check if an email is legit. For example, check to see if info@paypal.com does originate from the official site. How? In your email client, display the email header information. There, it will be evident if the email did not come from paypal.com. If there are links in the email, hover over one of them, but don’t click it! You should see a popup or hint that displays the full URL. If it doesn’t start with a paypal.com domain, it’s a fake.
Implement and use 2FA
2FA or Two Factor Authentication is a security method that verifies you. You’re already familiar with website logins. 2FA takes logins a step further. It does this by checking if it’s genuinely you that is logging in with your credentials. 2FA does this by asking for additional information. After you enter your login info, the 2FA scheme will send a text code to your verified phone number. Which in turn, you must enter into the login screen to gain access.
There isn’t a field on the login screen to enter your device’s phone number. That would defeat the purpose of 2FA since a spammer would be able to enter their mobile number and hijack the auth code. Instead, the mobile number you saved in your account is used. By involving another device that only you have access to, 2FA provides more confidence that the person logging in is you.
A 2018 study by Carnegie Mellon University found that over 75 percent of study participants thought 2FA made their accounts more secure, but 50 percent thought the process was annoying. 2FA also helped to stop dangerous security practices, such as credential sharing.
Never share your social security number
Most job applications will ask for your social security number to perform a background check. Outside of job applications and government organizations, there is no need to provide your social security number. Some companies may ask for it to set up an account for you. You can decline, and ask that the company uses another identifying number. After all, you have no idea what sort of security practices go on at any company.
Lockdown physical assets
Keep physical locks on any devices which contain sensitive data and are vulnerable to hacking.
Restrict access
Limit access to sensitive data, to employees on a straightforward need-to-know basis.
Update all your operating systems
Through cloud computing, these should be updated consistently and automatically. It’s always safer to ensure you have the latest versions with the most recent security fixes and patches installed.
Schedule regular updates for applications
Some apps will have to be updated manually, where others will be updated automatically. This rule is critical since earlier versions will have loopholes that hackers can exploit.
Use SSL in your email client
When using a desktop email client, the client connects to your email provider’s servers to receive and send emails. With some providers, you have the option to use a non-SSL connection. This can prove risky.
A non-SSL connection will send your non-encrypted email login credentials over the Internet. When you connect to a public or unsecured WiFi network (i.e., coffee shop or hotel), your email credentials will be vulnerable. Always use SSL when connecting to your email provider.
Use machine-generated passwords
With the advent of keyword loggers and even cameras spying on networks and devices, it’s imperative to use a machine-generated password.
Furthermore, hackers often play the guessing game too. One of the most popular passwords are names of personal pets. Using social media, it’s not hard to discover your pet’s name. For example, a simple Facebook search can give any hacker that type of personal information.
Play it safe by using something generated for you, and it is also completely random. If storage and memory pose an issue, then use a password manager.
Use Strong Complex Passwords
Don’t use the same password across multiple logins, even if you have used a password generator. Each login should be different. If one login is compromised, at least your other logins are safe – for now. By diversifying with strong secure passwords, you are essentially creating a firewall between each login.
Use a Credit monitoring service
Credit monitoring services can alert you to suspicious activity within your financial accounts. Credit monitoring services are convenient because you can monitor activity within all of your financial accounts, and through all three credit bureaus.
If you don’t want to pay for a monitoring service, most credit cards and bank accounts have alerts that inform you of suspicious activity. It’s triggered when a transaction exceeds a specific dollar amount, or a questionable purchase has been made on the card.
Contact your financial institution immediately
If you see suspicious activity on one of your business accounts, contact your financial institution right away. Your institution has protocols in place for events like these.
Train and educate your employees
The Office of the Future survey, Canon USA reported that more than one-third of respondents consider malware and ransomware a priority threat. Yet, 25% of respondents say that employees have limited to no security awareness, nor do they understand their role in prevention.
For better overall security, it’s essential to train your employees on your most recent security protocols. Create written privacy and data security policies. Educate your employees on those policies, and make them aware of their responsibilities for keeping company data secure. Offer this type of training at least two or three times per year.
If you’re self-employed, use an EIN instead of your social security number
If you are self-employed and have to fill out W-9s and 1099s, use a federal EIN. Using the Employer Identification Number means you do not need to use your social security number. And this protects you from becoming a victim of identity theft.
Conclusion
Data breaches are an unfortunate part of doing business online and participating in digital activities. In this article, you can learn to arm yourself and your business with protective knowledge and strategies and best practices to avoid data breaches. You can drastically reduce the possibility of your private data ending up online, or in hands, you don’t want it to be.
If you are still unsure about how to secure your business online, contact phoenixNAP today to get more information on how to develop your own strategy.
Recent Posts
What is a Whaling Attack? Identify & Prevent Whale Phishing
Are your company executives vulnerable to an attack?
A whaling attack is very similar to a phishing attack, just with bigger targets such as the c-suite. In this article, learn how to stay ahead of the threat and prevent a data breach.
What is a Whaling Attack?
A whaling attack is a spear phishing attack against a high-level executive. This is usually a C-level employee, like a Chief Executive or Chief Financial Officer.
In this attack, the hacker attempts to manipulate the target. The goal might be high-value money transfers or trade secrets. The term whaling (or whale phishing) refers to the high value of the target.
Differences Between Phishing, Whaling Phishing, and Spear Phishing
With typical phishing, attackers cast a wide net. This often means spamming a mailing list. Only a fraction of recipients needs to respond to make it worthwhile. Regular phishing attacks often ask the target for money and promise to repay more money later. The attacker then takes the money and vanishes.
A spear phishing attack is slightly different. In this type of phishing attack, the attacker identifies a specific target. Hackers learn details about their target and tailor the attack accordingly. A spear phisher might select a person in the IT department of a major corporation. Then learn that person’s habits, likes, and dislikes to use that knowledge for gaining trust. The attacker can then use social engineering against the target. The victim may grant access to sensitive data or even transfer money.
Spear phishing attacks target are regular everyday people. A whaling attack is targeting a high-level or difficult target. This is usually a C-level employee of a corporation. These targets often have better security awareness. A whaler is usually after large money transfers or trade secrets.
How Whale Phishing Works
- Urgency: One common phishing tactic is to create a sense of urgency. Whaling attacks are no different. Whaling attacks usually imply massive consequences and a short time frame. Urgency discourages the target from taking time to consider their actions.
- High risk / low effort: The attacker may threaten a costly lawsuit or public relations exposure. These threats would be disastrous to the company or individual. The hacker wants the target to bypass the security procedure. Usually, the action is simple compared to the danger. One example might be wiring funds to avoid regulatory action. Another might be clicking a link to a website that installs malware. This attack uses a substantial threat to get a low-effort response.
- Specific details: Whaling attacks can yield high rewards. Attackers spend substantial time and effort on the attack. Social engineering is often used to obtain personal information. They research the company to learn the names and achievements of different employees and use the details to exploit the target’s trust. If the target trusts the attacker, they are more likely to comply.
- Impersonation: Another common tactic is the use of impersonation. A hacker can use details from the corporation to impersonate a higher official. For example, an attacker might pose as a senior manager and ask for an employee payroll report. Or, they may pretend to be a fellow employee known by the target. Often, the email address is spoofed – or faked – to look authentic. Spoofing can include a valid-looking email address and company logos.
How to Prevent Whale Phishing
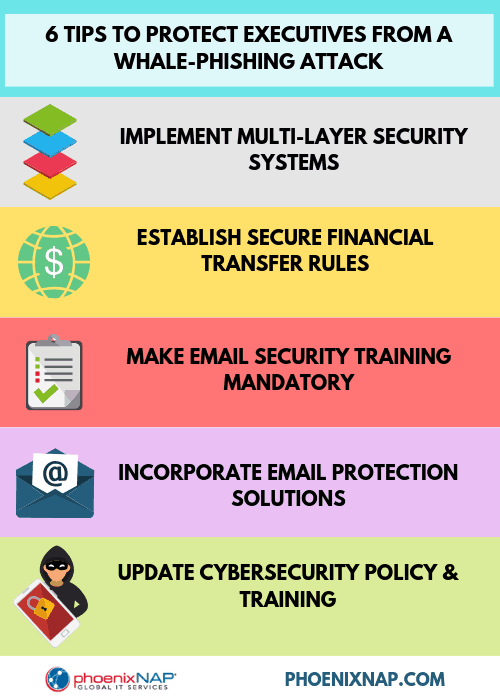
Educate employees in sensitive positions
This includes all of senior management. It’s also wise to educate employees in sensitive positions like IT and accounting. Employees in executive positions also make tempting targets. Train ALL employees to be wary of phishing and whaling attacks. If employees know what to watch for, they can protect themselves.
Senior employees should have private social media profiles
Social media sites provide a wealth of information for social engineering. An attacker might learn that an executive burned the hamburgers at a company picnic, then use that information to build credibility. Keeping profiles private helps limit an attacker’s ability to find compromising data.
Flag emails from outside the company
Whaling attacks often impersonate someone from within the company. Flagging external emails can warn users that the attacker is not who they claim to be. Attackers rarely attack from within the same company. This strategy can raise awareness of an attack.
Practice and enforce good email hygiene
Users should not click suspicious links or unsolicited attachments.
If the employee didn’t specifically request the email, they should take extra care. Anything that requires immediate and drastic action should be verified. Scan emails with a virus and malware scanner. Hover a mouse pointer over the sender’s name to see the real email address. In a web-based email, click the “more information” or “show details” to see the sender.
Use a system of verification for drastic action
Security awareness training is key. Train your staff on data security procedures, and how to check for suspicious phishing emails. Instruct sensitive employees to verify unusual requests.
For example, an employee might check the threat of a lawsuit with the legal department. Or, they might call a senior manager on the phone to verify the transfer of employee tax records. Consider a policy that requires verification for wire transfers.
Use data protection technologies
People make mistakes, and hackers are specialists in social engineering. As a last resort, implement data practices that make it difficult for one individual to cause damage.
Use access management, make sure root user access is limited to point-of-need. Also, make sure all user permissions are appropriate and necessary for each job function. Implement and maintain the usual suite of IT security tools: firewalls, intrusion detection software, and malware scanning utilities.
Active Threat Protection Keeps your Business Safe From Whaling
Whaling is a lot like spear phishing – just with bigger fish.
Whaling targets yield much bigger rewards, which creates an incentive to invest more effort into an attack. Though anyone can be vulnerable to social engineering, security training remains the best defense. High-level employees should expect to be a target, and defend themselves accordingly. In the event of a breach, incident response planning can help mitigate damage.
Recent Posts
What are Man in the Middle Attacks & How to Prevent MITM Attack With Examples
In this article you will learn:
- Learn what a MITM Attack is & How they work including real-life examples.
- Find out how hackers use Man-in-the-middle attacks, to interject between you and financial institutions, corporate email communication, private internal messaging, and more.
- Prevention tactics and best practices to implement immediately.
- Discover how to identify a man in the middle attack before a data breach impacts your organization.
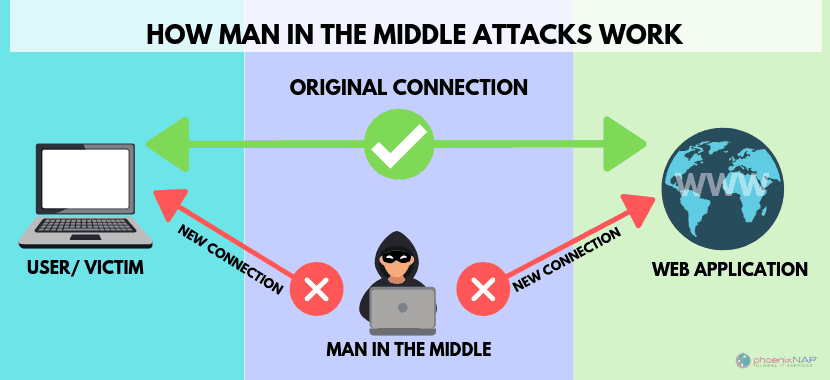
What is a Man in the Middle Attack? How Does it Work?
A Man-in-the-Middle (MITM) attack happens when a hacker inserts themselves between a user and a website. This kind of attack comes in several forms. For example, a fake banking website may be used to capture financial login information. The fake site is “in the middle” between the user and the actual bank website.
Attackers have many different reasons and methods for using a MITM attack. Typically, they’re trying to steal something, like credit card numbers or user login credentials. Sometimes they’re snooping on private conversations, which might include trade secrets or other valuable information.
One thing that almost all attacks have in common is the bad guy is pretending to be someone (or a website) you trust.
Types of Man-in-the Middle Attacks
Wi-Fi Eavesdropping
If you’ve ever used a laptop in a coffee shop, you may have noticed a pop-up that says “This network is not secure.” Public wi-fi is usually provided “as-is,” with no guarantees over the quality of service.
However, unencrypted wi-fi connections are easy to eavesdrop. It’s much like having a conversation in a public restaurant – anyone can listen in. You can limit your exposure by setting your network to “public,” which disables Network Discovery. This prevents other users on the network from accessing your system.
Another Wi-Fi Eavesdropping attack happens when a hacker creates its own wi-fi hotspot, called an “Evil Twin.” They make the connection look just like the authentic one, down to the network ID and passwords. Users may accidentally (or automatically) connect to the “evil twin,” allowing the hacker to snoop on their activity.
Email Hijacking
In this type of cyber security attack, a hacker compromises a user’s email account. Often, the hacker silently waits, gathering information and eavesdropping on the email conversations. Hackers may have a search script that looks for specific keywords, like “bank” or “secret Democrat strategies.”
Email hijacking works well with social engineering. Hackers might use information from a hacked email account to impersonate an online friend. They may use also use spear-phishing to manipulate a user to install malicious software.
IP Spoofing Attacks
As mentioned before, all systems connected to a network have an IP address. Many corporate intranet networks give each system its own IP address. In IP spoofing, hackers mimic the IP address of an authorized device. To the network, the device looks like it’s approved.
This can allow an unauthorized user to infiltrate a network. They may stay silent, and record activity or they may launch a Denial of Service (DoS) attack. IP spoofing can also be used in a MITM attack by standing between two systems:
System A ====== Hacker ====== System B
System A and System B think they’re talking to each other, but the hacker is intercepting and talking to both.
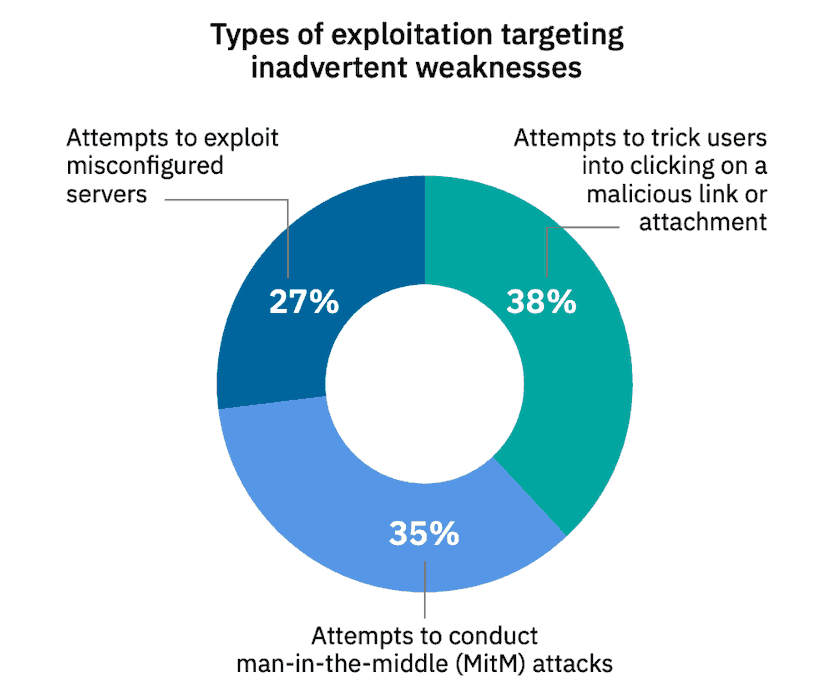
According to IBM X-Force’s Threat Intelligence 2018 Index, 35% of exploitation activity involved attackers attempting MITM attacks.
Image source: IBM Threat Index
DNS Spoofing
The internet works by numeric IP addresses. For example, one of Google’s addresses is 172.217.14.228.
Most websites use a server to translate that address to a catchy name: google.com, for instance. The server that translates 127.217.14.228 into “google.com” is called a Domain Name Server, or DNS.
A hacker can create a fake DNS server. his is called “spoofing.” The fake server routes a real website name to a different IP address. The hacker can create a phony website at the new IP address that looks just like a genuine website. Once you visit the fake site, an attacker can gain access to your sensitive information and personal data.
HTTPS Spoofing
It’s not currently possible to duplicate an HTTPS website.
However, security researchers have demonstrated a theoretical method for bypassing HTTPS. The hacker creates a web address that looks like an authentic address.
Instead of regular characters, it uses letters from foreign alphabets. This appears as spam emails you may have seen with strange characters. For instance, Rolex might be spelled Rólex.
SSL Stripping
SSL stands for Secure Socket Layer. SSL is the encryption protocol used when you see https:// in front of a web address, not http://. With SSL Stripping the hacker intercepts and forwards traffic from a user:
User ====== Hacker ====== Encrypted website
The user tries to connect to the encrypted website. The hacker intercepts and connects to the encrypted site on behalf of the user. Often, the hacker creates a duplicate website to display to the user. The user thinks they are logged in to the regular website, but it’s actually what the hacker wants them to see. The hacker has “stripped” the SSL protocol out of the user’s network connection.
Session Hijacking
This type of Man-in-the attack is typically used to compromise social media accounts. With most social media sites, the website stores a “session browser cookie” on the user’s machine. This cookie is invalidated when the user logs off. But while the session is active, the cookie provides identity, access, and tracking information.
A Session Hijack occurs when an attacker steals a session cookie. This can happen if the user’s machine is infected with malware or browser hijackers. It can also happen when an attacker uses a cross-scripting XSS attack – where the attacker injects malicious code into a frequently-used website.
ARP Spoofing
ARP stands for Address Resolution Protocol.
A user sends out an ARP request, and a hacker sends a fake reply. In this case, the hacker is pretending to be a device like a router, which allows them to intercept traffic. This is typically limited to local area networks (LAN) which use the ARP protocol.
Man-in-the-Browser
This is a type of attack that exploits vulnerabilities in web browsers.
Trojan horses, computer worms, Java exploits, SQL injection attacks, and browser add-ons can all be attack vectors. These are often used to capture financial information.
When the user logs in to their bank account, malware captures their credentials. In some cases, malware scripts can transfer of funds, then modify the transaction receipt to hide the transaction.
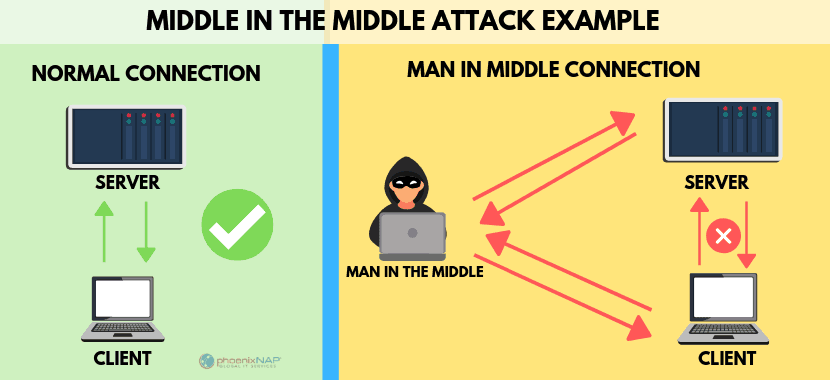
Real Life Man-in-the-Middle Attack Example
In the graphic below, an attacker (MITM) inserted themselves in-between between the client and a server.
As the hacker now controls communication, they can intercept data that is transferred, or interject other data, files, or information.
Man in the Middle Attack Prevention
Use a Virtual Private Network (VPN) to encrypt your web traffic. An encrypted VPN severely limits a hacker’s ability to read or modify web traffic.
Be prepared to prevent data loss; have a cyber security incident response plan.
Network Security
Secure your network with an intrusion detection system. Network administrators should be using good network hygiene to mitigate a man-in-the-middle attack.
Analyze traffic patterns to identify unusual behavior.
Your network should have strong firewalls and protocols to prevent unauthorized access.
Use third-party penetration testing tools, software, and HTTPS encryption to help detect and block spoofing attempts.
Install active virus and malware protection that includes a scanner that runs on your system at boot.
MITM attacks often rely on malware. Running updated anti-virus software is imperative.
Secure Your Communications
Encryption is the best defense to protect against intercepted communication.
The most effective method to stop email hijacking is to enable two-factor authentication. That means that, in addition to your password, you have to provide another vector of authentication. One example is Gmail’s combination of a password and a text to your smartphone.
Use basic internet security hygiene on all devices, including mobile applications.
Watch out for phishing emails as they are the most common attack vector. Carefully examine links before clicking.
Only install browser plug-ins from reputable sources.
Minimize the potential of attacks by signing out unused accounts to invalidate session cookies.
Force encryption by typing https at the beginning:https://www.website.com
If you expect an encrypted connection but don’t have one, stop what you’re doing and run a security scan.
If you use Google Chrome, install a chrome security extension, like HTTPS Everywhere, which forces an SSL connection whenever possible.
You should see a green or gray padlock just to the left of the web address in your browser. If you ever see a red padlock, that means there is something wrong with the encryption — double check domain names and your browser before visiting an insecure site.
Disable “Punycode support” (for rendering characters from different languages) on your browser.
Add an enterprise password management solution; this will avoid auto-filling passwords on a nefarious site.
Remember, mobile security best practices. Mobile applications are often targeted.
Avoid using public wifi networks. If you must use public wi-fi, configure your device to require a manual connection.
MITM attacks can be difficult to detect while they are occuring. The best way to stay safe is consistantly implementing all the prevention best practices above.
Be aware that some attacks are a form of social engineering. If something doesn’t seem right about a website or email, take a few minutes to dig a little deeper.
Protect your organization from falling victim
Detecting an attack is difficult, but they can be prevented.
Many Man In TheMiddle attacks can be prevented with good network hygiene, such as firewalls and security protocols. It is important to supplement these efforts by being mindful of your network habits.
Learn how PhoenixNAP proactively manages, detects, and responds to security indicators with our Threat Management Intelligence Services.
Recent Posts
What is Spear Phishing? Learn How to Prevent Attacks
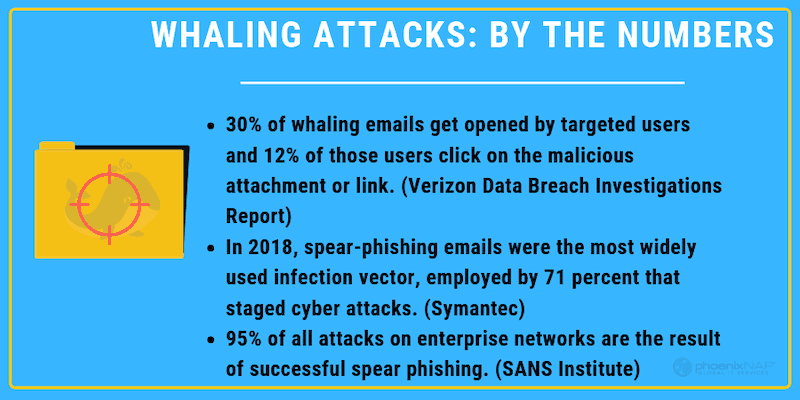
The latest numbers are in, and they aren’t pretty. In 2018, over 90% of cyber attacks and their resulting breaches stemmed from a spear phishing email.
According to SANS Institute’s Allen Paller, spear phishing emails caused 95% of all attacks on enterprise networks. So what is it that makes phishing emails in general and spear phishing emails in specific so dangerous? And how can individuals and enterprises protect themselves against such an invasive tactic?
The following article details what spear phishing attacks are and how to prevent them.
A Definition of Spear Phishing
Spear phishing is a much more targeted type of phishing attack. Here, the perpetrator doesn’t just send out a stock email to thousands or tens of thousands of recipients. Instead, they send out a personalized email to each of their targets. That email is sent out only after the perpetrator has done their research and knows specific details about their victim that will encourage the target to act. Those key details enable the perpetrator to draft the email in such a way as to instill trust in their victim and encourage them to do something that they might not otherwise do.
Spear phishing attacks usually appeal either to human greed or fear. This means they will either offer targets money, discounts, bargains, etc. or threaten targets into acting by saying their checking, PayPal, or eBay account has been frozen.
To encourage their victim to act, the perpetrator of a spear phishing attack will first find their victim and collect critical details to ensure whichever tactic will be believable. For example, they might search out an individual’s profile on a social networking site and from there glean their target’s email address, geographic location, workplace, friends list, and any new big items recently purchased and from where. Such details alone might seem innocuous but together enable the perpetrator to craft a dangerously effective email.
In their spear phishing email, the perpetrator will use the information to pose as a friend, colleague, boss, or other familiar entity to send out a highly convincing but ultimately fraudulent message. Hackers also employ a blend of email spoofing, and dynamic URLs to make emails appear more convincing.
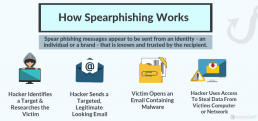
91% of cyberattacks and the resulting data breach begin with a “spear phishing” email, according to research from security software firm Trend Micro.
How Spear Phishing Works
Phishing schemes are any cyber or phone-based schemes designed to trick a victim into giving up personal details.
That information is then later used in some sort of scam. It’s a common hack, and most phishing scheme perpetrators target thousands of people with the goal of fooling a few. Take for example the famous “Nigerian Prince” scam. In this phishing scam, thousands of people receive emails offering a large sum of money on the condition the recipient transfers money for them. Most people will delete the email, but every year there continues to be those who don’t. Those victims who fall prey can lose thousands or even tens of thousands of dollars to the scam.
However, because more people have become aware of such scams and because business IT groups and email servers have tightened up security, the phishers have become more specialized. This is where the hacking technique of spear phishing developed.
Examples of Spear Phishing
Examples and scenarios for how spear phishing works and what it looks like include:
Spear Phishing An Individual: The perpetrator discovers the bank their target uses and using a spoofed email and copied website credentials, sends the target an email stating the account has been breached. That email will use fear-mongering to get the target to call a number or follow a link to provide confidential banking information (such as username and password) to confirm they are the real account holder. The perpetrator will then use that information to siphon out money.
Spear Phishing a business: A spear phishing attack against a company is similar to the one against an individual in that the perpetrator will first research and then use that research to draft a legitimate-looking scam. But the difference is the scale. Networking firm Ubiquiti Networks Inc. learned this the hard when cyber thieves uncovered key details about firm executives. The thieves then used those details to create spoof communications that appeared as though they were the firm executives and directed the firm’s finance department to initiate unauthorized international wire transfers to the tune of $46.7 million.
5 Protection Tactics To Avoid Spear Phishing Attacks
Spear phishing attacks look legitimate but are very dangerous. The following are a few tips both individuals and businesses can use to help prevent perpetrators of such attacks both from harvesting key data and using the data to get hold of critical accounts:
1. Avoid posting personal information online, such as a personal phone number. Every individual should avoid ever posting their phone number on their social media platform and avoid inputting their phone number with an unknown (and even most known) websites and mobile applications. Phone numbers are just as key to identifying a person and their complete financial background as a social security number. With techniques like SIM swapping and phishing scams, a person can essentially take over all of a person’s financial accounts.
2. Never click an unknown email link or attachment, especially from a financial or business institution. Use email security best practices. Perpetrators of spear phishing attacks will commonly send emails posing as a trusted institution their victim is known to frequent, such as Bank of America, Amazon, and eBay. Any emails an individual receives via personal business email should not be wholly trusted. Never click a link from such an organization, instead launch a separate browser window and go directly to the institution’s website to investigate claims and conduct business as usual. Any other emails, from friends, favorite blog writers, or nonprofit organizations, should be considered with care. Check the anchor text and never input personal details or otherwise confidential information on a link clicked from an email.
3. Be careful over-sharing on social media. Be mindful of personal details on their social media profiles and who they allow access to it. Keep privacy configurations high and avoid accepting unknown friend requests.
4. All organizations should implement a wholescale data protection program. Data protection programs are a combination of user education and security awareness training on best digital security practices and the implementation of a wholesale cyber protection solution designed to prevent potential data loss due to cyber attacks like spear phishing.
5. Keep confidential information out of emails. A favorite spear phishing tactic is to email employees from a reputable looking address and request sensitive information such as passwords or business banking details.ion.
Stay Alert & Stay Safe
No person and no organization is immune to becoming a target of cyber thieves.
If your information is on the internet or your smartphone has applications downloaded, then you are a potential target for this and other sophisticated cyber attacks. The best way to prevent falling victim is to stay aware at all time.
Keep information confidential, never trust outside sources and contact an experienced and professional security solutions team to ensure business assets are likewise protected.
Recent Posts
17 Types of Cyber Attacks To Secure Your Company From in 2020
In this article you will learn:
- What a Cyber Security Attack looks like in 2020 and how to identify one.
- An attack could destroy your business overnight, a proper security defense requires understanding the offense.
- How to protect your organization from the most common cyber attack vectors. Different methods require different prevention strategies.
- In the event an attack happens, learn how to be prepared to respond and respond.
What is a Cyber Attack?
A cyber attack is an intentional exploitation of computer systems, networks, and technology-dependent enterprises. These attacks use malicious code to modify computer code, data, or logic. Culminating into destructive consequences that can compromise your data and promulgate cybercrimes such as information and identity theft. A cyber attack is also known as a computer network attack (CNA).
Common Types of Cybersecurity Attacks
Phishing Attacks
Phishing is a type of social engineering usually employed to steal user data such as credit card numbers and login credentials. It happens when an attacker, posing as a trusted individual, tricks the victim to open a text message, email, or instant message. The victim is then deceived to open a malicious link that can cause the freezing of a system as part of a ransomware attack, revealing sensitive information, or installation of malware.
This breach can have disastrous results. For an individual, this includes identity theft, stealing of funds, or unauthorized purchases.
Phishing is often used to obtain a foothold in governmental or corporate networks as part of a more significant plot such as an advanced persistent threat (APT). In such a case, employees are compromised to gain privileged access to secured data, distribute malware in a closed environment, and to bypass security parameters.
Learn more about phishing attacks.
Spear Phishing Attacks
Spear phishing is an email aimed at a particular individual or organization, desiring unauthorized access to crucial information. These hacks are not executed by random attackers but are most likely done by individuals out for trade secrets, financial gain, or military intelligence.
Spear phishing emails appear to originate from an individual within the recipient’s own organization or someone the target knows personally. Quite often, government-sponsored hacktivists and hackers perform these activities. Cybercriminals also carry out these attacks with the aim of reselling confidential data to private companies and governments. These attackers employ social engineering and individually-designed approaches to effectively personalize websites and messages.
Learn more about spear phishing attacks.
Whale Phishing Attack
A whale phishing attack is a type of phishing that centers on high-profile employees such as the CFO or CEO. It is aimed at stealing vital information since those holding higher positions in a company have unlimited access to sensitive information. Most whaling instances manipulate the victim into permitting high-worth wire transfers to the attacker.
The term whaling signifies the size of the attack, and whales are targeted depending on their position within the organization. Since they are highly targeted, whaling attacks are more difficult to notice compared to the standard phishing attacks.
In a business, system security administrators can lessen the effectiveness of such a hack by encouraging the corporate management staff to attend security awareness training.

Malware Attacks
Malware is a code that is made to stealthily affect a compromised computer system without the consent of the user. This broad definition includes many particular types of malevolent software (malware) such as spyware, ransomware, command, and control.
Many well-known businesses, states, and criminal actors have been implicated of and discovered deploying malware.
Malware differs from other software in that it can spread across a network, cause changes and damage, remain undetectable, and be persistent in the infected system. It can destroy a network and bring a machine’s performance to its knees.
Ransomware
Ransomware blocks access to a victims data, typically threating delete it if a ransom is paid. There is no guarantee that paying a ransom will regain access to the data. Ransomware is often carried out via a Trojan delivering a payload disguised as a legitimate file.
Learn more about ransomware attacks and how to prevent them.
Drive-by Attack
A drive-by attack is a common method of distributing malware.
A cyber attacker looks for an insecure website and plants a malicious script into PHP or HTTP in one of the pages. This script can install malware into the computer that visits this website or become an IFRAME that redirects the victim’s browser into a site controlled by the attacker. In most cases, these scripts are obfuscated, and this makes the code to be complicated to analyze by security researchers. These attacks are known as drive-by because they don’t require any action on the victim’s part except visiting the compromised website. When they visit the compromised site, they automatically and silently become infected if their computer is vulnerable to the malware, especially if they have not applied security updates to their applications.
Trojan Horses
A Trojan is a malicious software program that misrepresents itself to appear useful. They spread by looking like routine software and persuading a victim to install. Trojans are considered among the most dangerous type of all malware, as they are often designed to steal financial information.
Web Attacks
SQL Injection
SQL injection, also known as SQLI, is a kind of attack that employs malicious code to manipulate backend databases to access information that was not intended for display. This may include numerous items including private customer details, user lists, or sensitive company data.
SQLI can have devastating effects on a business. A successful SQLI attack can cause deletion of entire tables, unauthorized viewing of user lists, and in some cases, the attacker can gain administrative access to a database. These can be highly detrimental to a business. When calculating the probable cost of SQLI, you need to consider the loss of customer trust in case personal information like addresses, credit card details, and phone numbers are stolen.
Although SQLI can be used to attack any SQL database, the culprits often target websites.
Cross Site Scripting
Cross-site scripting (XSS) is a kind of injection breach where the attacker sends malicious scripts into content from otherwise reputable websites. It happens when a dubious source is allowed to attach its own code into web applications, and the malicious code is bundled together with dynamic content that is then sent to the victim’s browser.
Malicious code is usually sent in the form of pieces of Javascript code executed by the target’s browser. The exploits can include malicious executable scripts in many languages including Flash, HTML, Java, and Ajax. XSS attacks can be very devastating, however, alleviating the vulnerabilities that enable these attacks is relatively simple.
Other Types of Cyber Security Threats
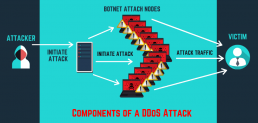
Distributed Denial-of-Service (DDoS) attack?
Denial-of-service (DDoS) aims at shutting down a network or service, causing it to be inaccessible to its intended users. The attacks accomplish this mission by overwhelming the target with traffic or flooding it with information that triggers a crash. In both situations, the DoS onslaught denies legitimate users such as employees, account holders, and members of the resource or service they expected.
DDoS attacks are often targeted at web servers of high-profile organizations such as trade organizations and government, media companies, commerce, and banking. Although these attacks don’t result in the loss or theft of vital information or other assets, they can cost a victim lots of money and time to mitigate. DDoS is often used in combination to distract from other network attacks.
Learn more about DDoS Attacks.
Password Attack
A password attack simply means an attempt to decrypt or obtain a user’s password with illegal intentions.
Crackers can use password sniffers, dictionary attacks, and cracking programs in password attacks. There are few defense mechanisms against password attacks, but usually, the remedy is inculcating a password policy that includes a minimum length, frequent changes, and unrecognizable words.
Password attacks are often carried out by recovering passwords stored or exported through a computer system. The password recovery is usually done by continuously guessing the password through a computer algorithm. The computer tries several combinations until it successfully discovers the password.
Eavesdropping Attack
Eavesdropping attacks start with the interception of network traffic.
An Eavesdropping breach, also known as snooping or sniffing, is a network security attack where an individual tries to steal the information that smartphones, computers and other digital devices send or receive This hack capitalizes on unsecured network transmissions to access the data being transmitted. Eavesdropping is challenging to detect since it doesn’t cause abnormal data transmissions.
These attacks target weakened transmissions between the client and server that enables the attacker to receive network transmissions. An attacker can install network monitors such as sniffers on a server or computer to perform an eavesdropping attack and intercept data as it is being transmitted. Any device within the transmitting and receiving network is a vulnerability point, including the terminal and initial devices themselves. One way to protect against these attacks is knowing what devices are connected to a particular network and what software is run on these devices.
Birthday attack
The birthday attack is a statistical phenomenon that simplifies the brute-forcing of one-way hashes. It is based on the birthday paradox that states that for a 50 percent chance that someone shares your birthday in any room, you need 253 individuals in the room. However, for a chance higher than 50 percent, you only require 23 people. This probability works because these matches depend on pairs. If you choose yourself as one of the pairs, you only need 253 people to get the required number of 253 pairs. However, if you just need matches that don’t include you, you only need 23 people to create 253 pairs when cross-matching with each other. Thus, 253 is the number you need to acquire a 50 percent probability of a birthday match in a room.
Brute-Force and Dictionary Network Attacks
Dictionary and brute-force attacks are networking attacks whereby the attacker attempts to log into a user’s account by systematically checking and trying all possible passwords until finding the correct one.
The simplest method to attack is through the front door since you must have a way of logging in. If you have the required credentials, you can gain entry as a regular user without creating suspicious logs, needing an unpatched entry, or tripping IDS signatures. If you have a system’s credentials, your life is even simplified since attackers don’t have these luxuries.
The term brute-force means overpowering the system through repetition. When hacking passwords, brute force requires dictionary software that combines dictionary words with thousands of different variations. It is a slower and less glamorous process. These attacks start with simple letters such as “a” and then move to full words such as “snoop” or “snoopy.”
Brute-force dictionary attacks can make 100 to 1000 attempts per minute. After several hours or days, brute-force attacks can eventually crack any password. Brute force attacks reiterate the importance of password best practices, especially on critical resources such as network switches, routers, and servers.
Learn more about Brute Force attacks.
Insider Threats
Not every network attack is performed by someone outside an organization.
Inside attacks are malicious attacks performed on a computer system or network by an individual authorized to access the system. Insiders that carry out these attacks have the edge over external attackers since they have authorized system access. They may also understand the system policies and network architecture. Furthermore, there is less security against insider attacks since most organizations focus on defending against external attacks.
Insider threats can affect all elements of computer security and range from injecting Trojan viruses to stealing sensitive data from a network or system. The attackers may also affect the system availability by overloading the network or computer processing capacity or computer storage, resulting in system crashes.
Man-in-the-Middle (MITM) Attacks
Man-in-the-middle (MITM) attacks are a type of cybersecurity breach that allows an attacker to eavesdrop a communication between two entities. The attack occurs between two legitimate communicating parties, enabling the attacker to intercept communication they should otherwise not be able to access. Thus the name “man-in-the-middle.” The attacker “listens” to the conversation by intercepting the public key message transmission and retransmits the message while interchanging the requested key with his own.
The two parties seem to communicate as usual, without knowing the message sender is an unknown perpetrator trying to modify and access the message before it is transmitted to the receiver. Thus, the intruder controls the whole communication.
AI-Powered Attacks
The concept of a computer program learning by itself, building knowledge, and getting more sophisticated may be scary.
Artificial intelligence can be easily dismissed as another tech buzzword. However, it is already being employed in everyday applications through an algorithmic process referred to as machine learning. Machine learning software is aimed at training a computer to perform particular tasks on its own. They are taught to accomplish tasks by doing them repeatedly while learning about certain obstacles that could hinder them.
AI can be used to hack into many systems including autonomous vehicles and drones, converting them into potential weapons. AI makes cyber attacks such as identity theft, password cracking, and denial-of-service attacks, automated, more powerful and efficient. It can also be used to kill or injure people, steal money, or cause emotional harm. Larger attacks can as well be used to affect national security, shut down hospitals, and cut power supplies to entire regions.
Be Prepared For Attacks On Your Network
This article has reviewed the top cyber-security attacks that hackers use to disrupt and compromise information systems.
For you to mount a good defense mechanism, you need to understand the offense. This review of the most common cyber attacks shows you that attackers have many options while choosing attacks to compromise and disrupt information systems. You also need to be proactive in defending and securing your network.
Maintain an updated antivirus database, train your employees, keep your passwords strong, and use a low-privilege IT environment model to protect yourself against cyber attacks.
Recent Posts
Definitive Guide For Preventing and Detecting Ransomware
In this article you will learn:
- Best practices to implement immediately to protect your organization from ransomware.
- Why you should be using threat detection to protect your data from hackers.
- What to do if you become a ransomware victim. Should you pay the ransom? You may be surprised by what the data says.
- Where you should be backing up your data. Hint, the answer is more than one location.
- Preventing ransomware starts with employee awareness.
Ransomware has become a lucrative tactic for cybercriminals.
No business is immune from the threat of ransomware.
When your systems come under ransomware attack, it can be a frightening and challenging situation to manage. Once malware infects a machine, it attacks specific files—or even your entire hard drive and locks you out of your own data.
Ransomware is on the rise with an increase of nearly 750 percent in the last year.
Cybercrime realted damages are expected to hit $6 trillion by 2021.
The best way to stop ransomware is to be proactive by preventing attacks from happening in the first place. In this article, we will discuss how to prevent and avoid ransomware.
What is Ransomware? How Does it Work?
All forms of ransomware share a common goal. To lock your hard drive or encrypt your files and demand money to access your data.
Ransomware is one of many types of malware or malicious software that uses encryption to hold your data for ransom.
It is a form of malware that often targets both human and technical weaknesses by attempting to deny an organization the availability of its most sensitive data and/or systems.
These attacks on cybersecurity can range from malware locking system to full encryption of files and resources until a ransom is paid.
A bad actor uses a phishing attack or other form of hacking to gain entry into a computer system. One way ransomware gets on your computer is in the form of email attachments that you accidentally download. Once infected with ransomware, the virus encrypts your files and prevents access.
The hacker then makes it clear that the information is stolen and offers to give that information back if the victim pays a ransom.
Victims are often asked to pay the ransom in the form of Bitcoins. If the ransom is paid, the cybercriminals may unlock the data or send a key to for the encrypted files. Or, they may not unlock anything after payment, as we discuss later.

How To Avoid & Prevent Ransomware
Ransomware is particularly insidious. Although ransomware often travels through email, it has also been known to take advantage of backdoors or vulnerabilities.
Here are some ways you can avoid falling victim and be locked out of your own data.
1. Backup Your Systems, Locally & In The Cloud
The first step to take is to always backup your system. Locally, and offsite.
This is essential. First, it will keep your information backed up in a safe area that hackers cannot easily access. Secondly, it will make it easier for you to wipe your old system and repair it with backup files in case of an attack.
Failure to back up your system can cause irreparable damage.
Use a cloud backup solution to protect your data. By protecting your data in the cloud, you keep it safe from infection by ransomware. Cloud backups introduce redundancy and add an extra layer of protection.
Have multiple backups just in case the last back up got overwritten with encrypted ransomware files.
2. Segment Network Access
Limit the data an attacker can access with network segmentation security. With dynamic control access, you help ensure that your entire network security is not compromised in a single attack. Segregate your network into distinct zones, each requiring different credentials.
3. Early Threat Detection Systems
You can install ransomware protection software that will help identify potential attacks. Early unified threat management programs can find intrusions as they happen and prevent them. These programs often offer gateway antivirus software as well.
Use a traditional firewall that will block unauthorized access to your computer or network. Couple this with a program that filters web content specifically focused on sites that may introduce malware. Also, use email security best practices and spam filtering to keep unwanted attachments from your email inbox.
Windows offers a function called Group Policy that allows you to define how a group of users can use your system. It can block the execution of files from your local folders. Such folders include temporary folders and the download folder. This stops attacks that begin by placing malware in a local folder that then opens and infects the computer system.
Make sure to download and install any software updates or patches for systems you use. These updates improve how well your computers work, and they also repair vulnerable spots in security. This can help you keep out attackers who might want to exploit software vulnerabilities.
You can even use software designed to detect attacks after they have begun so the user can take measures to stop it. This can include removing the computer from the network, initiating a scan, and notifying the IT department.
4. Install Anti Malware / Ransomware Software
Don’t assume you have the latest antivirus to protect against ransomware. Your security software should consist of antivirus, anti-malware, and anti-ransomware protection.
It is also crucial to regularly update your virus definitions.
5. Run Frequent Scheduled Security Scans
All the security software on your system does no good if you aren’t running scans on your computers and mobile devices regularly.
These scans are your second layer of defense in the security software. They detect threats that your real-time checker may not be able to find.

6. Create Restore & Recovery Points
If using windows, go to the control panel and enter in System Restore into the search function. Once you’re in System Restore, you can turn on system protection and create regular restore points. You should also create restore points.
In the event you are locked out, you may be able to use a restore point to recover your system.
7. Train Your Employees and Educate Yourself
Often, a ransomware attack can be traced back to poor employee cybersecurity practices.
Companies and individuals often fall victim to ransomware because of a lack of training and education.
Ransomware preys on a user’s inattentiveness, expecting an anti ransomware program to do their jobs for them. Nothing protects a system like human vigilance.
Employees should recognize the signs of a phishing attack. Keep yourself and your employees up-to-date on the latest cyber attacks and ransomware. Make sure they know not to click on executable files or unknown links.
Regular employee security awareness training will remind your staff of their roles in preventing ransomware attacks from getting through to your systems.
Stress the importance of examining links and attachments to make sure they are from a reliable source. Warn staff about the dangers of giving out company or personal information in response to an email, letter, or phone call.
For employees who work remotely, make it clear that they should never use public Wi-Fi because hackers can easily break in through this kind of connection.
Also, make it clear that anyone reporting suspicious activity does not have to be sure a problem exists. Waiting until an attack is happening can mean responding too late. Have an open door and encourage employees to express concerns.
8. Enforce Strong Password Security
Utilize a password management strategy that incorporates an enterprise password manager and best practices of password security.
According to background check service Instant Checkmate, 3 out of 4 people use the same password for multiple sites . More staggering is that one-third use a significantly weak password (like abc1234 or 123456. Use multiple strong passwords, especially for sensitive information.
9. Think Before Clicking
If you receive an email with the attachments .exe, .vbs, or .scr, even from a “trusted” source, don’t open.
These are executable files that are most likely not from the source you think it’s from. Chances are the executables are ransomware or a virus. Likewise, be especially vigilant with links supposedly sent by “friends,” who may have their addresses spoofed. When sent a link, be sure the sending is someone you know and trust before clicking on it. Otherwise, it may be a link to a webpage that may download ransomware onto your machine.
10. Set Up Viewable File Extensions
Windows allows you to set up your computers to show the file extensions when you look at a file. The file extension is the dot followed by three or four letters, indicating the type of file.
So, .pdf is a PDF file, .docx is a Window’s Word document, etc. This will allow you to see if the file is an executable, such as a .exe, vbs, or .scr. This will reduce the chance of accidentally opening a dangerous file and executing ransomware.

11. Block Unknown Email Addresses and Attachments On Your Mail Server
Start filtering out and rejecting incoming mail with executable attachments. Also, set up your mail server to reject addresses of known spammers and malware. Icann has listings of free or low-cost services which can help you do that.
If you don’t have a mail server in-house, be sure that your security services can at least filter incoming mail.
12. Add Virus Control At The Email Server Level
Most attacks start with a suspicious email that a victim is fooled into opening. After opening it or clicking on a link, the virus is unleashed and can do its dirty work.
Installing anti-virus and malware software on your email server can act as a safeguard.
13. Apply Software and OS patches ASAP
Malware often takes advantage of security loopholes and bugs within operating systems or software. This is why it is essential to install the latest updates and patches on your computers and mobile devices.
Staying with archaic versions is a guaranteed way of making your systems and their data a target. For example, the ransomware worm, WannaCry, took advantage of a security breach in older versions of Windows, making computers that had not been patched vulnerable. WannaCry spread through the Internet, infecting computers without a patch — and without user interaction. Had the companies that were attacked by WannaCry kept their computer operating systems up to date, there would’ve been no outbreak. A costly lesson for users and companies.
14. Block Vulnerable Plug-Ins
There are many types of web plug-ins that hackers use to infect your computers. Two of the most common are Java and Flash. These programs are standard on a lot of sites and may be easy to attack. As a result, it is important to update them regularly to ensure they don’t get infected by viruses.
You may even want to go the extra step of completely blocking these programs.
15. Limit Internet Connectivity
If you have genuinely critical data, your next step may be keeping your network private and away from the Internet entirely.
After all, if you don’t bring anything into your network, your computers are unlikely to have ransomware downloaded to them. This may be impractical seeing that many companies rely on the Internet and email to do their business, but keeping Internet access away from critical servers may be a way to combat ransomware and viruses.
How to Detect Ransomware
Unfortunately, if you have failed to avoid ransomware, your first sign might be an encrypted or locked drive and a ransom note.
If you run your malware and virus checker frequently with updated virus and malware definitions, your security software may detect the ransomware and alert you to its presence. You can then opt to quarantine and delete the ransomware.
What to Do If Your Computer Is Infected With Ransomware
Hopefully, you never have to deal with your data being held hostage.
Minimize damage by immediately isolating the machine — this critical to prevent further access to your network.
At this stage, rebuild your system and download your backups.
You may be able to recover many resources with a system restore. That is if you can access the system and are not locked out of it.
Otherwise, you’ll have to reinstall everything from backups. If you’ve backed up your crucial data on a cloud server, you should be able to find a safe restore point.
Should You Pay the Ransom?
You may be tempted to pay the ransomers to get your data back.
This is a terrible idea.
According to a Symantec ransomware report, only 47% of people who pay the ransom get their files back.
Every time someone pays the ransom, criminals gain more confidence and will likely keep hurting businesses.
Not only will you encourage them to continue, but you have no idea if they will free your computer. What’s more, even if they release your data, they may still use your information.
In other words, don’t pay. You’re stuck with making a bad situation even worse by paying the ransom. The data is gone (unless you have backups) and, if you pay them, your money is likely gone for good as well.
To quote FBI Cyber Division Assistant Director James Trainor:
“The FBI does not advocate paying a ransom to an adversary. Paying a ransom does not guarantee that an organization will regain access to their data. In fact, some individuals or organizations were never provided with decryption keys after paying a ransom. Paying emboldens the adversary to target other organizations for profit and offers a lucrative environment for other criminals to become involved.”
Finally, by paying a ransom, an organization is funding illicit activity associated with criminal groups, including potential terrorist groups, who likely will continue to target an organization.

Have a Disaster Recovery Plan
Proactive ransomware detection includes active incident response, business continuity, and a plan for disaster recovery.
A plan is essential and should be the cornerstone of a company’s security strategy.
- Set up a communication plan detailing who should contact who.
- Determine what equipment you would need to rent or buy to keep operations going. Plan for your current hardware to be unavailable for days.
- Write explicit instructions on where data is stored and how to retrieve it.
- Implement a policy of backing up regularly to prevent ransomware from causing data loss.
- Implement a disaster recovery service.
- Provide phone numbers for contacting vendors who may be able to restore the systems they provide for you.
Prevent a Ransomware Attack With Preparation
Companies must remain vigilant in today’s era of data breaches and ransomware attacks.
Learn the proper steps to prevent, detect and recover from ransomware, and you can minimize its impact on your business. Use these tips to keep your organization’s information assets safe and stop a ransomware attack before it starts.
Use a trusted data center provider and vendors. Perform due diligence to make sure they are trustworthy.
Recent Posts
27 Terrifying Ransomware Statistics & Facts You Need To Read
Ransomware is a form of malware or a virus that prevents users from accessing their systems or data until a sum of money is paid.
Clicking on infected links is still a primary way for cybercriminals to deliver their payloads. Ransomware was the most significant malware threat of 2018, with numerous high profile ransomware attacks. These malicious attacks show no signs of slowing in 2019.
Only with a proactive disaster recovery plan can increase your chances of withstanding a ransomware attack.
Let’s look at the staggering facts.
50% of a surveyed 582 cybersecurity professionals do not believe their organization is prepared to repel a ransomware attack. (Source: Pwnie Express)
Ransomware costs businesses more than $75 billion per year. (Source: Datto)
The average cost of a ransomware attack on businesses was $133,000. (Source: Sophos)
75% of companies infected with ransomware were running up-to-date endpoint protection. (Source: Sophos)
Want to learn the key tactics to preventing and detecting ransomware attacks? Read This.
Rate Of Ransomware Attacks
- A new organization will fall victim to ransomware every 14 seconds in 2019, and every 11 seconds by 2021. (Source: Cyber Security Ventures)
- 1.5 million new phishing sites are created every month. (Source: webroot.com)
- Ransomware attacks have increased over 97 percent in the past two years. (Source: Phishme)
- A total of 850.97 million ransomware infections were detected by the institute in 2018.
- 34% of businesses hit with malware took a week or more to regain access to their data. (Source: Kaspersky)
- In 2019 ransomware from phishing emails increased 109 percent over 2017. (Source: PhishMe)

Statistics on Ransom Demands
Ransomware financial demands are often severe and significant.
Ransomware Statistics show that hackers are focusing more steadily on large businesses who will often pay tens of thousands of dollars to receive their data back.
- An IBM study suggested that over a quarter of all companies would pay more than $20,000 to hackers to retrieve data that had been stolen.
- Ransomware generates over $25 million in revenue for hackers each year. (Source: Business Insider)
- The NotPetya ransomware attack cost FedEx $300 million in Q1 2017. (Source: Reuters)
- More than half of ransoms were paid bitcoin.
- The average ransom demand increased in 2018 to $1,077.
- Ten percent of all ransom demands are over $5,000. (Source: Datto)
- Fewer than a third of organizations who pay the ransom receive all of their money back. (Source: Courant
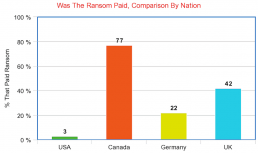
- 97% of United States’ companies refused to pay a ransom. 75% of Canadian companies paid, followed by, 22% of German businesses, and 58% in the UK.
Facts on The Biggest Ransomware Attacks of 2018
Recent ransomware attacks in 2018 crippled businesses large and small. Here is an insight into just a few high profile cases.
TSMC
A new variant of WannaCry ransomware wreaked havoc with Taiwan Semiconductor Manufacturing Company (TSMC) this summer.
The manufacturer was forced to shut down several of its chip-fabrication factories in August temporarily. This was after the virus spread to 10,000 machines in TSMC’s most secure and advanced facilities.
Under Armour
Fitness brand Under Armour was also dealt a black eye by ransomware. Their app “MY Fitness Pal”- a portal through which users could track their diet and fitness was breached by malware.
The brand insists that the data did not contain sensitive data like social security numbers and drivers license numbers (which the app does not collect). Nor were customer payment details affected. This breach affected 150 million users.
The City of Atlanta
In March this year, the alleged creators of the SamSam ransomware launched an attack on the infrastructure of the city of Atlanta GA. The attack affected many of the city’s essential municipal functions. Among those affected were citizens’ ability to pay water bills or parking tickets.
- The ransomware demand was $51,000 (unpaid) while the recovery costs were estimated at $17 million.
- Local government in Atlanta spent over $5 million to rebuild their infrastructure after a SamSam ransomware attack in March 2018.
Industries under attack
The Healthcare Industry
The healthcare industry has historically been low hanging fruit for malware. 2018 was no exception.
- Almost half of the ransomware incidents reported in 2018 involved healthcare companies. (Source: Beazley)
- 90% of healthcare organizations saw an increase in ransomware infection rates from 2017 to 2018. (Ponemon Institutes)
- 18% of healthcare devices have been the target of malware. (Source: Healthcare IT News)
- A report by CSO online estimates healthcare related malware attacks will likely quadruple by 2020.
Financial Institutions
90% of all financial institutions have experienced ransomware in the past year. (betanews.com)
These businesses have a virtual treasure trove of bank account numbers, routing numbers, and Social Security numbers that hackers can steal and later sell on the dark web.
In Q1 of 2019, Kaspersky Labs reported:
- More than 204,448 users experienced an attempt to log their banking information
- More than 280,000,000 URLs were identified as malicious
- Cybersecurity statistics show attacks were launched from within more than 190 countries
- Attacks on individuals doubled in 2018.
- Attacks on Businesses increased to one every 40 seconds.
Mobile Ransomware Threats Grow
The frightening rise of mobile malware is staggering. You may not realize that their handheld electronics are the next battlefield for domination of their personal information. In an increasingly mobile work environment, all businesses and their employees must be extra vigilant.
- Mobile malware, banking malware, and ransomware are the primary threats to expect in 2019. (Source: Fortinet)
- More than 18 million mobile malware instances were detected by Symantec in 2018. (source: Symantec)
- In Q1 2018 alone, Kaspersky Labs detected over 8,000 mobile banking ransomware Trojan installations.
- Kaspersky Labs found that the majority of the malware in 2018 was targeting phones on the Android operating system.
- Cybersecurity giant Symantec identified mobile use as a significant point of vulnerability for businesses and private users in 2018. In their annual Internet Security Threat Report (ISTR) they state “Threats in the mobile space continue to grow year-over-year, including the number of new mobile malware variants which increased by 54 %”.
- Less than 20% of mobile malware is delivered via a browser — the remainder of the payloads come through an app. (Source: RSA Current State of Cybercrime)
2019 Global Ransomware Predictions, By The Numbers
What are experts predicting for 2019 and beyond?
- 81 % of cybersecurity experts believe there will be a record number of ransomware attacks in 2019. (Source: CIO Dive)
- McAfee analysts suggest that individuals with a large number of connected devices and a high net worth are some of the most attractive targets.
- Attacks against Linux and Macs are expected to rise, according to IT Security Guru.
- The average costs of data breaches will reach into the hundreds of millions of dollars by 2020. (Source: Juniper Research)
- Recent studies have shown that ransomware attacks are increasing more than 300% year over year. (dimensiondata.com)
- Cybercriminals will target SaaS (Software as a Service) and cloud computing businesses, which store and secure private data. (Source: Massachusetts Institute of Technology)
- The cybersecurity research body suggests that ransomware damage costs will rise to $11.5 billion in 2019.
- Mobile malware, banking malware, and ransomware are the primary threats to expect in 2019 according to Fortinet.
- The Internet of Things (IoT) is primed to revolutionize life for businesses and consumers alike. However, the inherent vulnerability of this nascent technology can leave it wide open to ransomware attacks. A report by Kaspersky Lab indicated that new malware targeting IoT enabled devices grew threefold in 2018. Since 2017, the number of IoT focused malware attacks rose 10x from 2016.
Final Thoughts On Ransomware Statistics
As cybercriminals continue to see the value in encrypting data and restricting the access of users, ransomware will continue to grow.
While newer cyber threats increase, these final stats quickly show that ransomware isn’t going away anytime soon.
50% of companies report that they do not feel as though they are adequately prepared for the threat. (healthitsecurity.com)
With damage related to cybercrime set to hit $6 trillion by 2021, investing in security spending should be a priority for 2019.
Recent Posts
Preventing a Phishing Attack : How to Identify Types of Phishing
It takes one click on a link to put an organization’s data at risk for a breach.
Phishing attacks often disguise themselves as people we trust, thus lowering our defenses. No industry is safe from the threat of cyber attacks.
Businesses make prime targets due to the amount of sensitive data they store. It is vital to understand how to identify phishing. Read this article to learn more about the types of phishing attacks and protection tactics with examples.

What is a Phishing Attack? A Definition
The term phishing defines attempts by outside parties to gain access to private information about users. Hackers seek passwords, credit card numbers, bank account info – or any information capable of being used to access data.
Most successful phishing campaigns end with the user downloading malware into their system.
How Do Phishing Attacks Work?
Phishing typically involves casting a wide a net as possible hoping a few people will take the bait. Attackers turn to more targeted methods when going after individual companies. They also look to rope in specific individuals with access to valuable information.

The Facts Behind Phishing
A report from the Anti-Phishing Working Group (APWG) showed that companies responding to their survey experienced a steady stream of phishing scams during the first half of 2018. The most targeted business sectors were:
- Payment Providers
- Financial Institutions
- SAAS/Webmail
- Cloud Storage/Cloud Hosting
Popular Phishing Methods
Responses to the APWG survey showed the below methods being used the most:
Emails – The most popular tool for attackers at an average of 98,723 per month.
Websites – Attempts using this method averaged 48,516 per month.
Phishing URLs – Averaged around 18,113 attempts per month.
Hackers targeted a small number of brands at an average of 443 times per month. APWG contributor PhishLabs noted an uptick in free web hosting sites being used to build malicious websites. They do this to lend credibility to the site being built by using an established provider.
76% of companies experienced some type of phishing attack. That number rose in the first quarter of 2018 to 81% for US companies. Businesses saw a rise in malware infections of 49%, up from 27% in 2017.
Other security stats suggest that spear phishing accounted for 53% of phishing campaigns worldwide. That number went up to 57% for the United States. Phone calls and text messages, on the other hand, accounted for 45% of phishing attempts worldwide.
Things have come a long way since the days of the Nigerian prince scam emails. Hackers use more sophisticated phishing email methods.
They come with stolen or altered business logos to trick the recipient. Or they infiltrate social networking platforms, disguising themselves as a friend or someone who shares your interests.
Common Types Of Phishing Attacks & How To Identify
Email Phishing
Email remains a popular choice for most attackers. They mimic a popular brand or institution reaching out to you to help you resolve an issue. The official-looking communication asks you to confirm a password or other account information.
More sophisticated deceptive phishing emails make the sender address match those of people or businesses you communicate with regularly. They contain malicious attachments or links designed to deliver malware to your device.
Spear Phishing Attacks
Cyber attackers use this phishing technique to target particular businesses. They go beyond sending out mass emails or blanketing random sites with ads. They tailor their efforts toward people who work in an industry they find valuable.
Target became the victim of a spear phishing attack when information on nearly 40 million customers was stolen during a cyber attack. Hackers went after a third-party vendor used by the company. They captured their credentials and used them to access the customer information from a database using malware downloaded from a malicious attachment.
Whaling
John Podesta, the chairman of Hillary Clinton’s presidential campaign, found out about whaling the hard way. His account received an email purporting to be a Google alert letting him know his system had been compromised. It was urgent that his credentials be reset immediately at the link provided.
His assistant did just that after receiving erroneous information from their IT person that it was legitimate. That is all it took for malicious spyware to be released into their systems. Thousands of document and emails were stolen by Russian hackers.
Whaling attacks target high-level executives with credentials giving them access to a wide range of information. Factors like human error and lousy advice play a big part in the success of these type of attacks.
Clone Phishing
Cloning involves mimicking a trusted site a user frequents. People receive emails warning them about an issue with their account. Hackers create an entire malicious website that looks like the one the user logs into regularly.
The attackers hope to fool users into providing them with personal credentials. Many users of Reddit fell victim to clone phishing. A clone of the site popped up with the apparent intent of tricking people into thinking they were logging into the regular Reddit site.
Phone and Text Phishing
Not all attacks come over the internet. Many businesses use automated voice messages to alert people to things like an upcoming doctor appointment. Hackers use this method to leave voicemails warning you about an issue. They may reference your bank account or a company you’ve obtained services from.
Hackers employ similar methods using text messages. This allows them to send you malicious links directing you to a phishing website. Once you get there, they mask the address bar with a picture of a real URL to fool you into thinking you are on an actual site.
Social Media
Phishing attacks tend to go after a large pool of targets on platforms like Facebook or other favorite social media sites. You receive a request from a friend asking you to respond to a quiz. It asks questions like “What are your favorite vacation spots close to home?” or something equally innocuous.
The information you give out may seem like nothing. You might reference where you live and places you like to visit. Hackers need only a small bit of data to gain more information about you. That is enough to figure out your passwords and hack your accounts.
Thieves use the pictures posted to your Instagram or Snapchat account as sources of information. Korean officials at the 2018 Winter Games warned people not to post pictures of their tickets since they contained a barcode. Hackers could scan the pictures and capture all of their personal data.
Fraudulent Websites
Hackers build fake phishing sites designed to steal your information. For example, people searching for a site that lets them update a passport get fooled by a login page that appears legitimate. The credentials they enter end up being used to compromise other personal accounts.
Scammers also lure visitors to these sites by creating fake ads on sites like Google or Craigslist. Bitcoin users fooled by fake ads on Google have been frequent victims of theft in recent months. The problem got so bad that Facebook recently banned all ads related to cryptocurrencies from their site.
False or Fake Advertisements
Websites make a significant amount of revenue by designing ads that get your attention. Hackers use this to their advantage by embedding these ads with malware. Clicking on the ads allows the software to embed itself in your system and go to work.

How to Prevent Phishing
It only takes one moment of inattention to make yourself or your company the victim of identity theft. While there is no easy way to prevent phishing, a multi-pronged approach to combating the threat can minimize the risk.
1. Protect Your Inbox
The best defense is a good offense. Stop potentially damaging emails from entering company inboxes by using strong email spam filters and following email security best practices. Most security software companies offer versions compatible with both computer and mobile devices.
Your software should automatically scan any links or attachments. This prevents new or unrecognizable URLs from sneaking past company safeguards. New computer network security threats show up every day. Hackers also continuously work to evolve and hide malware. Keeping your software updated and running continuously is essential.
2. Analyze Web Traffic
Attackers love to find vulnerable points when users access personal accounts on their work computers. Check any access attempts to non-company websites or email servers. It does no good to have top-level security on a work email account, only to have someone download malware by clicking on a Facebook ad.
3. Raise Employees’ Security Awareness
Human error still accounts for the majority of data breaches. Hackers only need one person in an organization to click on the malicious link in an email to cause damage. Multiple steps should be taken to train employees on how to recognize phishing and handle them appropriately.
First of all, employees need to understand that they are all potential victims of cybercrime. They need to be educated on the most common threats. Companies should provide comprehensive training on how to recognize a phishing message, social engineering tactics, and suspicious web addresses.
The training should also cover identity management, as well as cloud security and mobile security to enable employees to protect themselves.
4. Test Employees on how to identify a phishing email
Establish a security awareness program.
Target specific people within different areas of your company with test phishing emails. Track those who correctly identify suspicious emails versus those who do not. Interview them to gain insight as to why they did or did not recognize the problems within. Use that feedback to modify or redesign your cyber security training courses.
In addition to testing employees, you should also regularly check the stability of your critical infrastructure. If you are hosting your data with a third-party data center provider, you should ensure it provides advanced protection against the most common threats such as DDoS, phishing, and ransomware attacks.
If your entire infrastructure is managed internally, you need to ensure you have all these systems in place to keep your data safe. You should also consider running a penetration test every once in a while to be confident about your platform’s security.
5. Communicate Effectively Between Departments
One of the easiest ways to manage passwords is with a corporate password management solution.
Make sure your employees understand the recommended cybersecurity best practices for companies and receive frequent reminders about their importance. Coordinate across all departments so that everyone gets the same education.
6. Use A Variety of Teaching Methods
Everyone absorbs information differently. Some prefer visual cues, while others like thing documented in a manual to refer back to. You also have those who prefer to gain knowledge audibly. Provide your employees with different options to obtain online security education.
7. Make Phishing Training Personal
Employees often cannot comprehend how their actions could hurt the entire company. Bring it down from an abstract and show how it affects them. Demonstrate how the damage done by malicious software impacts their job.
8. Create a Tutorial On What Not To Share
Cyber thieves continuously scour social media for information posted by employees of companies they are targeting.
Advise them to avoid sharing information like:
- Birthdays
- Personal Address
- Phone Numbers
- Vacation Days
- Online Banking and Credit Card Details
Attackers use this information to guess at passwords they use to access accounts at work. Letting people know when you will be away from your computer gives hackers a window of opportunity to target you while you are not there.
9. Establish a System to Report Threats
Inform employees on what to do if they encounter a fraudulent email. They should report even if they are unsure if the message is a threat. They should also beware random text messages seeming like official communications from the company.
10. Celebrate Cybersecurity Due Diligence
Show employees your appreciation for following security protocols. Prepare a luncheon or off-site event to show your company’s appreciation for the dedication shown by workers to keeping company information safe.

Types Of Malware Used In Phishing Attacks
Hackers come up with new types of malware every day. The term malware covers various types of malicious software designed to gain access to information on a user’s device.
Botnet Malware
Hackers in recent years started using computer networks designed to take control of devices in your home or business to launch malicious attacks. Remote controllers manipulate these malevolent botnets to turn your devices against you.
The laptop you use for work become a tool to steal your information. New technology like Amazon Echo speakers also presents new frontiers for hackers. The growing attacks on IoT (Internet of Things) devices make the consequences of phishing more severe.
The threat of botnets increased in 2018 with over 40% of automated login attempts to websites being malicious. The hospitality sector was the hardest hit with an 82% malicious login rate. Botnets leverage the fact that most people use the same account credentials to access multiple sites.
After obtaining credentials, the botnets attack site after site. This only stops once the user becomes aware of the theft and changes their information.
Ransomware
The rise of ransomware in the last decade brought a new type of danger to deal with. This software locks users out of the files in their system. Hackers demand payment in exchange for removing the malware and giving back access.
Sony Pictures found itself the victim of such an attack in 2014 and again in 2017. It is not just businesses being targeted. The government of the town of Yarrow Point in Washington grappled with frequent ransomware attacks throughout 2018. Find out how to protect yourself from ransomware.
Computer Viruses
Code or software engineered to disrupt the way a device functions. They attach themselves to legitimate programs for code execution, often corrupting or destroying system files along the way.
Trojan horse
Disguises itself as a legitimate program within an email. They open the door to access the user’s information once executed.
Spyware
These programs embed themselves in your device to record your activities. They track sites you visit and capture any personal details entered by you.
Worm
These programs require nothing from your system. They are self-sustaining and duplicate themselves everywhere without needing human interaction.
Learn To Identify Phishing Attacks
The best defense against all types of phishing attacks is to learn to identify them.
Learn about the deceptive tactics used to obtain information. Do not let your company become a statistic and being used as an example to other businesses.
Recent Posts
15 Best Google Chrome Security Extensions You Need to Install
Chrome is the most common internet browser for individuals and businesses. The layout is simple, clean, responsive, and provides a secure browsing experience.
Even though Google Chrome antivirus settings are the best the industry, there are always new and emerging threats online.
To create an extra layer of security protection, there are many security extensions for Google Chrome available in the Chrome web store.
Blur
Just about every website you go into that you are a subscriber to requires a password. They aren’t simple passwords either. You have to include special characters, upper and lower case letters, and numbers. It’s not something that can easily be remembered any more. The days of writing them down on a piece of paper are gone.
Password management tools are available online and through the Chrome browser. You will often be asked if you want to save a password when you enter it on a specific site. If you’re using your home personal computer, it might be okay. However, how safe is it really to have your passwords stored like that? You want to have those passwords encrypted just in case someone gains access to that managing tool. Blur does it all. It will save your passwords and encrypt them for safe keeping.
Online shopping is a lot more secure as well because all the credit card information that gets entered is encrypted. So, you aren’t sharing any of your credit card or personal details. The tracking protection keeps trackers from being able to see what you’re doing. It even blocks those trackers that aren’t working with cookies, so it appears to be a better option than an insecure browsing experience.
TeamPassword
Employees can come and go from a project or an entire company. While they are working for you, you want them to be able to have access to various services, tools, and applications that require passwords and logins that keep your business information kept private. With the password generation option that TeamPassword has, you can get strong passwords created for you that can be shared across a team that is working on the same platforms with just one click of a mouse.
When an employee leaves a project, the company, or you don’t want them to have access to specific password and login information anymore due to security reasons, you can quickly remove access in one step.
If a different employee is being added into the system, that can be completed with just two steps. TeamPassword manager offers a free trial so that you can explore the beneficial online security and privacy options.
Sneekr Security Extension
Monitoring browser history can be a tricky task for employers, parents, and others that want to see what suspicious activity is taking place on a shared device. Users can wipe out their search history or use Incognito mode to keep what they are doing privately. If you’re running a business, you can’t afford not to have complete transparency with all of your employees. They could potentially be breaching security and getting into delicate information that they shouldn’t have access. The same goes for others you suspect are looking at websites that should be restricted.
With Sneekr, that is no longer an option for them. This extension allows for the moderator to keep a hidden browser history that is protected by a password. Even when the user tries to wipe out the history, it can’t be removed.
It’s also nice if you want to work in Incognito mode because you don’t want others to see your browser history. You still can recover where you’ve been in case you need to get back to a specific site.
SiteJabber
SiteJabber is one of the largest community-based Google Chrome extensions. Other users review websites for authenticity and safety.
When you are browsing for shopping or just surfing around for ideas for a project, you will get to see what others think about the web page you are considering of checking out. There will be a small icon displayed that is either red, yellow, or green to help you quickly determine where it falls on the rating list. Some of the factors that are considered during the rating process include how safe it is along with whether or not it is a site that can be trusted not to damage your computer or flood you with malware or phishing links.
By hovering your mouse over the icon, you will see a display that includes a short summary of the site. If you click on it, you can get more detailed reviews or even leave a review of your own. There is an option to ask questions to members of the SiteJabber community as well if you have a specific inquiry about any site.
Secure Mail for Gmail
Many emails contain sensitive material. Email security should be a priority.
While in most instances it can be encrypted so that other people can’t read it, there is still a chance that Google could pick up what is included in the message. Secure mail for Google changes that. All that you have to do is encrypt the email with a password before sending it through cyberspace.
When the recipient gets it, he or she will have to use that same password to open and decrypt the message. Before thinking about using this add-on, remember that the people you intend on sending these secure encrypted messages to must have the same extension.
Avast Online Antivirus Chrome Extension
Rated as the best antivirus chrome extension, Avast Online Security will warn you instantly if a page you are visiting is a fake.
Likewise, it will tell you if the URL you are entering is legitimate. You have probably entered a domain name at one time or another and misspelled something. Chrome doesn’t realize that you have made an error, so they take you to whatever site you told it to. This extension will auto-correct those mistakes so that you don’t accidentally end up somewhere that you shouldn’t be.
Analytics are everywhere using tracking cookies to follow your activity. The Avast chrome extension prevents that from happening. It runs on a community rating system so that other users can share any dangerous sites they ended up on and which ones were exactly what they said they were. They also offer the Avast password chrome extension.
Ghostery
At any given time there can be people tracking your online activity. This slows down your browsing and can invade on your privacy. With Ghostery, you can see who is tracking you, and it gives you the ability to either block or unblock them from seeing what you are doing.
When you are visiting a specific website, you can click to see who is tracking that site as well, not necessarily you as an individual. You can disable those trackers if you don’t want them to know that you are there. If you need to block trackers of a specific category like analytics, social media, or advertisements, those can be found in the add-on when you look in the settings.
Click&Clean
There may be an emergency that arises that requires you to completely erase all of your saved passwords, cache, download history, form data, and more due to some breach of your security. Usually, this could be a very lengthy process. The Click&Clean Chrome security extension allows you to wipe everything out with just one click, like a panic button.
By opening the icon on the toolbar, you will be given an option to delete everything or individual items. It’s one way to ensure that all of your browsing sessions are private and secure. This Google Chrome extension also offers clearing data from Incognito mode and alphanumerical password generation.
Windows Defender
Microsoft provides real-time protection from malicious websites, phishing, and other suspicious activity through the Windows Defender extension for Chrome.
You have safety from falling victim to those phishing links that when clicked on, something unwanted starts downloading to your device without your approval. Some downloads can be extremely harmful software that can damage your computer and uncover sensitive information stored there.
In the event you click on any unsecured external links, you will be led to a red screen of warning that tells you the site is known to be harmful. Windows Defender at this point has already scanned the site against an up-to-date list of sites. If they find a match, you get the notification. That red warning screen will give you the option to return to a previous screen with just one click safely. It’s one of the most useful add-ons to protect you from falling victim to malware and other phishing attempts.
uMatrix
uMatrix is an extension for more experienced users looking to improve security. You get to use a point-and-click method to decide what kind of information can be downloaded to a device, what types of browsers can connect, and various other actions that can or cannot take place.
This extension can be a bit overwhelming when you first open it, but with continued use, it becomes easier to navigate. You will get a big box of information about various websites and what they offer or don’t regarding scripts, frames, images, cookies, CSS, and various other codes. Many rows are similar, and you have the choice of blocking them all from being accessed. For instance, if you wanted to prevent the use of all social media on your devices, you could do that with uMatrix. It’s something that employers take advantage of when trying to hold their employees to work-related internet activity only.
You always can alter what sites you consider to be blacklisted or whitelisted, and you don’t have to include all of one row or column if you want to make an exception. The primary goal of uMatrix is to allow you to have full control of the privacy and security of your browsing and internet experience. You can also expect protection from malware sites, trackers, phishing attacks, and more.
HTTPS Everywhere
You most likely already know that when you look at the domain name of a website, if it starts out with HTTPS that means that it is secure. It has an SSL certificate that encrypts any information sent and received while on that site.
It’s something that websites rely on to show customers that they can be trusted. Any personal messages, contact information, or credit card numbers are securely encrypted.
With the HTTPS Everywhere security Chrome extension, those sites that don’t have that ‘S’ for secure get turned into one. The add-on works for thousands of websites, but there are some that won’t be receptive to it. An error for privacy will be displayed, and then you have to disable the extension if you want to continue forward. You are opening yourself up to a security risk by doing so, but at a minimum, you know that you are working on a page that isn’t encrypted.
AdBlocker Ultimate
Advertisements are flashy, and you might be drawn to click on something that pops up on your screen. Unfortunately, some ads are dangerous. They could be hiding malware that instantly starts downloading dangerous software to your computer. AdBlocker Ultimate can take the risk away from that happening.
Unlike other ad-blocking extensions, there aren’t any advertisements that Ad Blocker Ultimate considers to be white-listed or acceptable. That means that you aren’t going to see any slip through the program because someone out there somewhere thinks that it’s okay. They are all completely gone. It’s free to add on this extension, and because there are no more ads, there isn’t going to be anything slowing down of your browsing experience. If for some reason you want to turn advertisements on for a specific site, that’s a feature that can be utilized. The overall secure browsing experience is improved.
PixelBlock
Were you aware that people can track the emails that they send you and see if you’ve opened it or not? That means that if you are taking some time to respond, they are going to either start bothering you about an answer or they will sit back wondering why you haven’t given them a response. You want to be able to check your email without someone else knowing what you are doing in the privacy of your home or office.
The PixelBlock extension prevents the tracking of your activity. If a website attempts to track you, a red eye will appear near the name of the sender. That shows you that the sender has tried to view whether or not you’ve seen it, but they weren’t granted an answer because the Chrome security extension blocked them from intruding.
DotVPN
When you require online activity anonymity, DotVPN is arguably one of the best security extensions available there. It’s free and reliable with fast service that can be spread across 12 different locations. They don’t put any limit on their switches either. A few of the options you have with this Chrome security extension include the use of 4096-bit encryption, the ability to open .onion websites, compressing data, and protection from inbound connections through the built in-firewall.
Public Wi-Fi connections and cell data networks can be used without worry of intruders intercepting any information or viewing what you are doing from your device. You can activate all the features offered through this add-on by just clicking it on.
SurfEasy VPN – Security, Privacy, Unblock
SurfEasy VPN gives you a wide assortment of options when it comes to your privacy protection while online. You can unblock websites, stay secure when using public Wi-Fi, and encrypt data both in and out of your browser.
Sometimes you don’t want others to see your IP address or where you are located geographically. That can be achieved through the activation of this chrome extension for security. All financial activity, shopping, and other banking activity can be completed without worry.
Final Thoughts On Chrome extensions for security
Before you start surfing the internet, be aware that security awareness goes beyond just adding Google Chrome extensions.
It’s a good idea to take a careful look at which ones are going to be the most beneficial. You want to be able to utilize what they have to offer fully.
Contact phoenixNAP today For a Security Review
Complete the form below and our experts will contact you within 24 hours.
Recent Posts
What is Social Engineering? Understanding The Latest Types & Threats
Social engineering has become a malicious tool for hackers to conduct cyber attacks.
Virus protection or your firewall won’t help if you are duped into clicking a malicious link thinking it came from a colleague or social media acquaintance.
Here’s what you need to understand to stay safe and protect your data.
What is Social Engineering?
By definition, social engineering is an attack vector used to gain access to gain access to networks, systems, or physical locations, or for financial gain by using human psychology, rather than using technical hacking methods. It relies on social interaction to manipulate people into circumventing security best practices and protocols.
Social engineering is the new preferred tactic among the hacker community. It is easier to exploit users’ flaws than to discover a vulnerability in networks or systems.
Understanding different types of social engineering attacks is an essential aspect of protection.
TYPES OF SOCIAL ENGINEERING THREATS
Phishing
Phishing is one of the most common types of social engineering.
When a website, article, or online community is presented to a targeted individual as authentic and secure but instead uses a URL that is not official it is called phishing. Hackers and thieves alike utilize phishing attacks to gain false hope and trust from potential victims to receive sensitive information such as usernames, email addresses, and passwords that are linked to social media accounts and bank login websites. Phishing involves the participation of users for the theft of information and data to be completed.
Phishing is most common among users who are not well-versed in browsing the internet or those who are new to using social media and online resources to search for information, content, and media. Many phishing attacks target individuals who are elderly or those who do not work in the tech industry to obtain sensitive information without the risk of being caught.
Preventing phishing starts by ensuring each URL you visit is official and authentic. Phishing attacks often target social media platforms, banking websites, and online service sites to gather crucial information from users who fall for the faked URL.
Phishing attempts increased by 30 million from 2017 to 2018, according to Kaspersky Lab.

Baiting
Baiting is used in both the digital and physical world.
Baiting consists of leaving devices in public areas that are packed with malware, spyware, or other damaging software which is then used to steal and collect the information of users who are tempted to see the contents of the device.
Most commonly, flash USB drives are left in areas such as bathrooms, libraries, subway stations, or even on airplanes in hopes to attract the curiosity of individuals.
Once the user plugs the device into their computer, malware is downloaded onto the hard drive.
Keyloggers and malicious software then send data directly to the hacker, allowing them access to websites and accounts.
Digital baiting is also found in advertisements that showcase enticing deals or free items, only to lead users to websites that immediately trigger a download of malware and spyware software.
In some cases, malware and spyware programs are disguised as traditional software or software updates.
When browsing for software, it is imperative to verify the authenticity of the URL and the provider.
Spear Phishing
Spear phishing is designed to personally attack an individual or organization to appear more authentic and legitimate.
Spear phishing attacks often utilize a user’s personal information or details about an individual to gain the trust and curiosity of the user before stealing information, installing malware, or delivering a keylogger to the individual’s hard drive. Hackers who use spear-phishing tactics are well-versed in scraping data of users from social media sites, official blogs, and even email newsletters or previous online leaks and security breaches.
When a user is presented with a spear phishing attack, they are likely to feel that the attack is a genuine attempt to share information, content, or free products due to the overwhelming personal details provided.
Spear phishing is becoming more popular than traditional phishing attacks as users become aware of checking URLs and verifying the websites they shop and browse on whenever they are online. With a spear phishing attack, it becomes increasingly difficult to determine whether or not the URL or information is malicious, even for those who are seasoned internet users.
Tailgating
Tailgating is a social engineering threat that is purely physical and involves real-world interaction to work. When a hacker is interested in obtaining the information of a specific individual or organization, they may follow them to local cafes or locations where free Wi-Fi is available. Hacking into a public Wi-Fi hotspot provides thieves with the ability to learn more about individuals using the connection while obtaining sensitive and personal data.
Other forms of tailgating may include asking an individual to utilize their access pass while entering a building or going to work in their office by lying about forgetting their pass to quickly steal information. Tailgating is often used by hackers who have a vested interest in an individual or organization believed to have wealth or unsecured banking accounts that are easy to hack and steal from once access is provided.
Tailgating is one of the most personal forms of social engineering and also one of the most threatening in the real world.
Remaining vigilant and secure when accessing Wi-Fi hotspots or internet anywhere outside of the home is essential to prevent the risk of exposing personal information and data that belongs to you. It is also necessary to maintain an encrypted and protected internet connection to keep potential hackers from obtaining access to your data.
Scareware
Scareware is extremely successful in obtaining user information and financial details.
Often presented as popups or programs while prompting users with warnings or threats to receive information such as names, credit card details, and even social security numbers.
An individual is likely to be threatened with contact from the FBI or other areas of the government, prompting quick responses to avoid further action. When users are unfamiliar with this tactic, they are much more likely to fall for a scareware attack.
Scareware does not always include personal or direct threats. Scareware is also commonplace when browsing on unofficial websites or sites that provide free content or programs that are otherwise not free.
In many cases, scareware is used to prompt individuals to download malicious software due to a threat of spyware or malware already infecting the user’s hard drive.
Once the individual downloads the solution presented by the scareware campaign, their computer is compromised and hackers then gain direct access to personal information or the entire hard drive itself.
Pretexting
Pretexting scams are used to collect personal information from individuals by impersonating police, government officials, bank account managers, or even co-workers.
Hackers use pretexting to target unsuspecting individuals who are likely to feel threatened or fearful of retribution if they do not share the requested information. Pretexting is done over the phone, via email, or in some cases, even with the use of social media messenger applications.
Perpetrators who use pretexting often inform individuals that they are in need of highly sensitive information to complete a task or to prevent the individual from legal trouble.
When an individual feels threatened, vulnerable, or scared, they are much more likely to reveal bank account numbers, routing numbers, social security numbers, and other sensitive data.
Quid Pro Quo
Quid pro quo involves hackers requesting information from unsuspecting individuals with the promise of offering something in return.
Individuals presented with a quid pro quo attack are likely to receive offers of compensation, free vacations, or gifts such as new products that are most relevant to the individual’s lifestyle.
Quid pro quo attacks occur over the phone, while using social media, or even through traditional email newsletters that have been hacked, compromised, or impersonated. Users are presented with the promise of money, free travel, or gifts in exchange for login information, credential verification, or other sensitive details such as social security numbers and bank account and routing numbers.
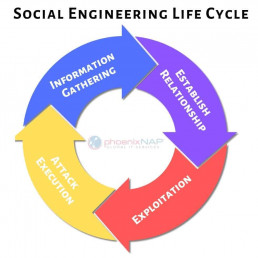
3 Phases of Social Engineering
Research Phase
The first phase of any social engineering attack is research. During this phase, attackers search for information about you. The easiest route to find potential information is through a web or social media search. Social media security best practices are key as people often post personal information that attackers can use against them.
If the target is a business, attackers may be able to collect information about employees or security rules that may aid future attacks. Managers and other high-value targets are at a higher risk because attackers are more likely to do more research for these targets.
Skilled social engineers often research what companies you might work with. They can then use this information to better pretend to be a technician or consultant with the company to gain access to sensitive areas. Through this pretext, they may trick targets into revealing sensitive or secure data.
Contact Phase
After the research phase has finished, attackers will move on to the contact phase. During this phase, attackers will use researched information to look for other weaknesses and gain the target’s trust. This often includes pretending to be someone the target trusts. Once the victim trusts the attackers, the attackers can then leverage this for more information or access.
For example, attackers might use social media to find which employees of a company have left for vacation. They might then contact the company pretending to be a vacationing employee who forgot to give them important information before leaving. Knowing that one employee was out of the office, another person at the company might try to help them by sending attackers the desired information.
Attack Phase
The attack phase builds on the previous two phases. In most cases, this means that attackers have the necessary information and access to you or your company’s systems.
Basic attacks will use this access to steal information from a system, but some hackers go further. Advanced attacks will use this access to aid them in future attacks. They might then leave a backdoor into the system, or copy your credentials.
Understand Social Engineering Threats
Social engineering is not new. However, it is becoming the go-to attack vector of hackers.
With a clear understanding of the definition of social engineering, take control of your online activity while remaining protected.
Recent Posts
Network Security Threats, 11 Emerging Trends For 2020
This article was updated in December 2019.
Most experts agree that 2020 will bring a higher sophistication of malicious hacking.
More of these network security threats and attacks will be high profile and reinforce the importance of cybersecurity plan. Hackers will target well-known brands, looking for notoriety as well as money.
As a result, the security response of the business community must rise to the occasion.
Any network with a connection to the Internet is potentially vulnerable. The number one thing you can do to protect your systems is to establish a backup strategy for your data, now.
Types of network threats to be aware of in 2020
Ransomware (and Micro Ransomware)
As the so-called “as a Service” services increase, we can expect a proliferation of ransomware to showcase itself across networks.
Ransomware is an attack vector that focuses on vulnerabilities that are much different from any other form of malware. It is also one of the easier malicious attacks to employ, giving relative newbies the leverage to troll their way into crime.
The more severe users of malware will use ransomware to focus on easily penetrable industries such as healthcare. The proliferation of big data has made sensitive medical information much more valuable than it has ever been. Other industries that traffic in sensitive consumer data will also find themselves targeted by this unique form of malware.
Ransomware can also shutdown POS systems, blocking payments from ever reaching the recipient. Currently, email is the number one delivery method for ransomware and viruses. This will also change as technology becomes more sophisticated.
Although the trend will expand, not all attacks will be massive. Ransomware is one one the fastest growing cybersecurity threats to network security. Experts say that we can also expect ransomware attacks targeting smaller companies.

Long-Term Extortion
An offset of the growing ransomware plague is long-standing extortion techniques. Once a vulnerability has been opened through a ransomware attack, it can be quite challenging to close. This can leave a digital door open for a malicious user to require ongoing payments in order to keep from accessing the vulnerability again.
In this way, ransomware scams can last for much longer than the initial attack, creating an environment of fear for companies that do not have the appropriate technology to ensure closing digital backdoors.
Companies that are looking to expand will find themselves targeted by this kind of extortion. Even if a security network is relatively secure at its base, when it takes on new third-party applications, new security backdoors can be opened because of the interaction between legacy apps and new apps. Companies that rely on automated updates may also face ongoing extortion efforts from hackers who follow the schedule of these updates and plan attacks around the “changing of the guard.”
Malware in the Mobile Device Space
Smartphones are no longer safe. As commerce moves into the mobile space, hackers will move with it. 35% of the general public uses smartphones for banking, and these people will be targeted by hackers. There are many malware families dedicated specifically to mobile device platforms. They are becoming very good at stealing the financial information of online bankers.
Keyloggers, for instance, are no longer a sickness relegated only to desktop and laptop computers. Mobile keyloggers can steal passwords from other apps that are downloaded into a phone. If a user has the same password for that app and a financial app, the hacker now has access to the online banking credentials of that user. Take the time to create ideas for great secure strong passwords.
Hackers may also use creative techniques to get users to download malicious apps. These apps work in the same way as an email phishing campaign or a silent.exe download. Once they open a small hole in the security of the hardware, a hacker can come in and make it much bigger over time.

Exploits Directed at the Windows Subsystem for Linux
The Windows Subsystem for Linux (WSL) will likely be a huge target in 2020. WSL is a new technology that shipped out with Microsoft Windows 10. It was created to allow Windows tend to run alongside a limits environment. However, the many security exploits that have already been found within the Windows 10 environment do not speak well to this premature expansion.
There are many companies that have not upgraded to Windows 10.
As this upgrade is forced into many environments, you can expect that hackers will continue to focus their efforts on it. Microsoft has yet to respond adequately to many of the criticisms leveled its way about forcing implementation of its operating systems before adequately testing for exploits.

IoT Botnets
As people plug into the Internet of Things, hackers will make this new system one of the first locations for significant incidents.
The leaked Mirai code of 2016 that created a very effective legion of bots will expand and grow into IoT, says Bitdefender senior analyst Bogdan Botezatu. The DDoS or denial of service attacks that were created from these bots will seem rather tame in the face of the dual ransomware/botnet attacks that will show themselves in 2020.
Modern botnets even can directly defeat systems with machine learning capabilities. The sheer volume of these botnets makes it possible to attack with brute force some of the weaker infrastructures. GPU based encryption is another advancement that many cybersecurity systems have yet to catch up with.
Polymorphism and Powershell
The proliferation of open-source tools will bring with it an increased level of abuse.
Even network security tools that have a decent reputation in the freeware space may be targeted as Trojans. Commercial actors and APT groups are already beginning to include PowerShell manipulation in their malware toolkits. The more sophisticated these tools become, the more security products they will be able to bypass.
Many types of malware also can change their signatures. This is known as polymorphic malware. Qbot is just one example of incredibly sophisticated polymorphic engines that are currently taking up space in the cloud. The creators of these engines are actually renting them out to other malicious entities, with the two entities splitting the profits of whatever haul they bring in. In short, the creation of malicious software has been crowdsourced. There are simply not enough companies with the in-house staff to handle this kind of teamwork.
Artificial Intelligence Security Tools
It is difficult enough for a company to keep up with and respond to the last major publicized cybersecurity breach. In 2020, hackers will employ AI tools that will consistently scan the environment for new exploits.
Hackers will be able to upgrade and modify their techniques in real time. Most organizations only have access to scanning tools that were based on policy compliance and configuration. These tools are looking to the past, not to the future. They just cannot keep up with AI-based tools that are creating and testing scenarios for the sole purpose of breaking into a system.
There is no in-house DevOps security best practices or team that can keep up with the amount of analysis and data that is necessary to ward off real-time attacks that can consistently change form. It is the equivalent of chasing a fly around a huge room. Companies will need to employee third-party experts that can accurately conduct impact and context analysis.

Cybersecurity Third Party Breach Threat
Breaches do not have to come from a direct attack. In 2018, more breaches were made possible through a third-party source. These nerd parties may have been trusted. However, that third-party does not always have an awareness that it is being used as an open hallway to a target that it is connected to.
Hackers can sanitize their trail so that it cannot be quickly followed. The company that is attacked may believe that it was the direct target of the attacker with no roundabout pathway made to its doorstep through the naïve third-party.
The past few years have seen many security breaches accomplished through third parties. Hackers were able to access the network of major retailer Target through one of its HVAC vendors. A point-of-sale vendor was the gateway for hackers to break into the networks of Home Depot, Inc. and Hilton Hotels. These were not the only companies that suffered a data breach through some aspect of their supply chains.
Companies may also become vulnerable through a third-party connection without a firewall. It is imperative that companies that are doing business with each other in the digital space expand and share their security features with each other. For instance, the app structure of a third-party company may also affect the ability of a targeted company to adequately secure its own borders.
Network Security Risk Management
Companies that haphazardly expand their digital ecosystems will be the most highly targeted. Hackers are continually monitoring these ecosystems, standing just outside the doorway waiting for an expansion that they can exploit.
Governments are attempting to rein in the ability of individual companies to expand their digital real estate too fast. However, there are limitations on what regulations can protect.
The issue of regulatory compliance will come into the spotlight during the implementation of the General Data Protection Regulation (GDPR) across the digital landscape. Experts believe this will cause an outbreak of attacks as companies to adjust their security measures to remain in compliance with GDPR.
It is essential to remember that hackers do not care if you comply with the latest government regulation. They only care about getting your private data.

Business Email Network Security Risks
Email vulnerabilities are the grandfather of all types of threats in network security.
It continues to be a massive problem across industries because it still works with a very high frequency. It is also a relatively easy way to breach a companies systems. Hackers do not need a great deal of technical expertise. All that is necessary is control of a resource that executes when a phish is triggered by an errant employee. Often, the security risks of wireless networks are not taken seriously.
A lack of training on the best practices of email security is the number one culprit in email hacks. Large companies can still be targeted because of the higher probability of an untrained employee opening a phishing email. Many experts believe that the financial industry, ransacked by ransomware and other malware in 2020, will remain a top target of this form of breach.
Criminals looking to break into companies through emails may also use relevant information from employees. Hackers may attend an industry event, gain the contact information of a high-ranking employee, and use that information to break in relatively undetected. It is essential to protect your company from a physical standpoint as well as in the digital space.
Cloud Network Security and Vulnerabilities
The public cloud continues to be a massive target for cybercriminals. Again, large companies continue to rest in the center of the bulls-eye. Companies without a strong tiered program of access are at the most significant risk. All it takes is one untrained employee with access to open up any number of cloud security vulnerabilities across the network.
Hackers can access this information in a number of ways. It is up to the organization to quarantine employee access so that physical hacks will only allow access to a controllable, easily trackable dataset.

The Hijacking of Search Results
Many companies are unaware that the major search engines have personalized search results quite effectively. Depending on the previous searches of a company and its behavior during those searches, it can receive different results from any other entity in the world.
In short, there is no such thing as generalized search results anymore. Hackers are acutely aware of the targeting that search engines employ. If they can hack into the behavioral patterns of an organization, they can also hack into that companies search engine results.
Search tampering involves hijacking one or more of the results on a search engine page. Under the guise of following relevant links, a company can be directed to a malicious site. From here, hackers have a number of options. Once a company has access to this site, a hacker can tap into anything from digital files to security cameras.

Always Be Prepared for the latest network security threats
Knowing about security threats is one thing. Responding to them is another. The tips above should drive you into action.
Take the appropriate steps to protect your data streams. This year will not have mercy on any company without the proper security!
Preparation is the only defense. Start with a network risk management, incident response planning, and evaluating current security protocols.
In most cases, the security industry is functioning in response to attacks from malicious hackers. You must remain proactive and up-to-date on the latest types of network threats. You must also employ the newest protection strategies using AI, machine learning and systems analysis.
Recent Posts
17 Security Experts on How To Prevent Social Engineering Attacks
In the most simple terms, social engineering is defined as when one person manipulates another to gain access to systems, networks or locations, or for financial gain.
Social engineering is the process of bypassing security rules by exploiting human targets. Social engineering’s primary goal is to gain access to data or systems that attackers don’t have permission to access. These attacks are especially damaging because they often abuse your prosocial impulses to gain this illicit access.
Social engineering scams are often used by hackers who want to gain access to systems because technological security is so advanced. People tend to be much easier to manipulate, and many will give help to someone posing as a colleague or even an online advisor simply because it is the socially acceptable thing to do. In other words, people are much more vulnerable because, ironically, we want to help.
In many cases, a social engineering attack is fronted by someone posing as a trusted source such as a bank or customer support.
They build the trust of their target, using their alleged position to persuade people to drop their guard and provide confidential information to gain access to data
Just as people tend to accept people who wear a badge as people of authority, hackers persuade others that they are figures of authority to gain trust and encourage their target they want to be helpful.
Examples and Types of The Latest Common Attack Techniques
Physical Attacks
Tailgating or Piggybacking
Tailgating, also known as piggybacking, is one of the simplest and most effective attacks. This involves attackers gaining access to a protected area by following someone else in. Attackers might wait for another person to enter the building and follow them inside. This needs very little planning because the attacker avoids standard security procedures.
By avoiding security completely, attackers can save time and avoid more complicated tactics. After gaining access to a location, attackers may be able to forge authentication.
Pretexting
In practice, face-to-face pretexting is similar to an actor playing a part.
This involves scammers assuming a false identity to lure you into revealing protected information.
One simple version of this tactic involves pretending to be a technician or consultant. Attackers then trick other people into giving them access, usually by pretending that they were called or have an appointment.
Attackers may also pretend to be an employee. If attackers include research into their role, they may trick other employees into trusting them. With this trust they can gain access to sensitive company information. When attackers include high-pressure tactics or confusion, like claiming that the employee could be fired if they refuse to help, the attackers may be able to trick even otherwise cautious people.
Baiting
Baiting is when attackers use a physical item as bait.
For example leaving a USB stick, or some other device, somewhere and wait for you to pick it up. The device is loaded with self-installing malware. When you connect the device to your computer, the malware installs automatically on your system.
Another form of baiting uses your own USB drive or mobile device. This type of malware can lay in wait until connected to your computer. It then loads malware on the target.
Online Based Attacks
Phishing
Phishing attempts to gather personal information
Phishing involves pretending to be someone you trust. Attackers can pretend to be a personal friend, a bank or even part of the government. Once contact has been established, they usually try one of two tactics.
If they are pretending to be a friend, they may send an email from your friend’s hacked email account or from one that looks similar. This type of attack is successful because people are less suspicious of names or people they trust.
Other may try to scare or intimidate you. The attacker may try to convince you that you have a virus on your computer, then direct you to a website to download a software fix. If you download the software, it can load malware on your system.
Spear Phishing or Whaling
Spear phishing is like phishing but aimed at those with authority. These high-value targets are often victims because of the increased payoff. Scammers can spend months researching the best way to attack these people.
For example, attackers hack into the computer of an executive’s assistant. At the right time, attackers can email the executive and ask them for the information that would allow resetting the executive’s passwords or login information.
Watering Hole
In a watering hole attack, the bad guys let you come to them. This involves taking control of a website or network that you trust. With this control, attackers can wait for you to access the network or website. When you enter your login information or other sensitive data, the attackers can steal it.
A successful watering hole attack involves at least two separate attacks. The first on the trusted website or network, and the second on you. As these attacks are more sophisticated, they are harder to detect and more likely to be successful.
Typosquatting
Typosquatting is when attackers register the URLs of the common mistakes people type when trying to go to a popular website.
An example of typosquatting is registering a URL that is one letter off from the URL of a large bank. When a customer accidentally types in the incorrect URL that the attackers own, it takes you to a website that looks like your bank’s website.
Without realizing the difference, you might put in your own login information. Hackers can then later use this information at the real website to steal money from your account.
We asked our security experts: What are the more frequent or common social engineering attacks organizations experience? What steps can be taken to prevent them?
Our Cyber Security Experts On Social Engineering Prevention

Rema Deo
CEO and Managing Director at 24by7Security Inc.
Rema is certified as a Health Care Information Security & Privacy Practitioner (HCISPP) from (ISC)2. She holds a certificate in Cybersecurity: Technology, Application, and Policy from the Massachusetts Institute of Technology.
The most frequent social engineering attacks are caused by phishing. Phishing is known to be the leading cause of ransomware attacks.
Tailgating is another way in which attackers may obtain information or plan or execute a cyber attack by physically gaining access to your premises, especially sensitive areas. In businesses, whaling is also a popular social engineering method, distinguished a bit from phishing in that whaling targets are usually high-value targets like executives or high ranking government officials.
-
-
- Do not allow tailgating into the office premises. If someone asks you to let them into the premises, do not let them in unless they have the appropriate credentials and authorization to be on the premises.
- Phishing, vishing, spear phishing, and whaling are forms of social engineering. Do not click on unknown links in emails or messages.
- Check the sender’s email address before taking any action. If suspicious, report the email to your security or compliance officer.
- Password security is critical. Do not provide your password to anyone. If you have inadvertently provided your password for any of your work systems to someone, change those passwords immediately.
- If you have any reason to doubt the instructions provided by a colleague or executive via email, be sure to call or otherwise confirm before implementing especially if those instructions are likely to grant access to someone else, or to wire funds or anything that might adversely impact the company.
-

Mike Bousquet
Co-founder & CEO, Groove.id Inc.
Phishing remains so pervasive because it is effective. Even sophisticated, well-trained end users can fall victim to a well-crafted phishing email that lands in their inbox. Attackers utilize many different strategies to harvest the credentials of valid users. Nearly every data breach involves stolen passwords. The result is that at some point in every intrusion, the attacker stops hacking and starts just logging in, making it very difficult for IT & security teams to detect their presence and prevent data loss. Unfortunately, despite significant investments in technology and user education, this trend is likely to continue.
Preventing phishing attacks is a significant challenge. Email security solutions help, but like anti-virus software, it’s a never-ending battle to keep up with changing attacker tactics. Some bad traffic inevitably finds its way through the controls. Training and educating users is a worthy step toward building up a defense against human error. However, expecting people to demonstrate flawless performance in identifying phishing attempts is unrealistic. Most people are just trying to get their jobs done productively.
We believe a better solution is to focus on removing the target the attackers seek: account credentials.Passwords have been in use for over 60 years as the mechanism to identify valid users of a technology service and its time to decommission them. Even two-factor authentication has limits tied to a fundamental architecture that relies upon something a user knows that they can easily be tricked into giving up. A better approach is to leverage modern identity solutions that eliminate the use of passwords.
Today, technologies like hardware security keys, user behavior analytics and biometric authentication methods can be combined to eliminate passwords. When that happens, there’s nothing for users to remember and nothing for attackers to steal, which closes off the attack surface that phishing attempts to compromise.

Paul Bischoff
Privacy Advocate with Comparitech
Paul Bischoff has been covering IT-related subjects since 2012. He previously worked as the China editor at Tech in Asia and is a regular contributor at Mashable, as well as several blogs for internet startups around the world.
When talking about social engineering attacks against organizations, we’re mainly referring to phishing.
Phishing campaigns against organizations are typically more targeted than your typical Nigerian prince scam. Spear phishing attacks can target specific staff members or departments, and common targets include IT staff, executives, accountants, and human resources staff in charge of payroll and tax documents. Scammers may impersonate other employees or executives at the company, or the company bank, an affiliate, or a contractor. The goal of a phishing attack is to get private information. This can range from employee tax documents to passwords to financial information, and in some cases even trade secrets. Other scams may attempt to trick staff into transferring money to the criminal.
Companies can prevent such scams by raising awareness about phishing and implementing clear dos and don’ts for staff.
For example, staff should know the warning signs of phishing emails, and no sensitive information should ever be sent in an email. Safeguards should be put in place so that staff in possession of such valuable information can verify the identities of whoever requests it. For example, the HR department should contact an executive by phone before making any non-routine money transfers. Companies can test their policies with their own imitation phishing campaigns to ensure everyone can reliably spot and prevent phishing.

Oliver Münchow
Security Consultant and Evangelist at Lucy Security
Oliver Münchow has worked in IT security since 1998 and in 1999 started his first company specializing in penetration testing. His current company, Lucy Security, helps build employee awareness and uncover vulnerabilities in their infrastructure. He conducts training courses including Certified Ethical Hacker (C|EH) and the Open Web Application Security Project (OWASP).
While phishing attacks via email, social media or SMS are undoubtedly the most common, it is wrong for a company to focus solely on these attacks.
The danger of an employee entering a password on a hacker-controlled website, for example, is often overestimated. I was once contracted by a nuclear operator to use social engineering to penetrate secured facilities, so more effective methods were used. This included, above all, face-to-face contact on site. With a good story and the right clothes, you can always gain the trust of employees.
Once on site, there are no limits.
In the beginning, we installed Trojans on servers under the pretext of IT support. Later we walked through the rooms with trolleys and simply stacked the servers and laptops on them and walked out with them. The possibilities are limitless.
So what can you do?
Employee sensitization is undoubtedly essential. But you never cover all use cases anyway, and in the daily business, the learned is quickly lost. Helping is only a matter of very clear guidelines that have to be adhered to. If, for example, an unannounced visitor comes, this must be verified with the responsible person. If you see an unknown person in the corridor without a badge, this must be reported. And so on.

Ryan Manship
President of RedTeam Security
Ryan has a BS in Information Technology with an emphasis on Networking and Security and regularly speaks at various security events.
Three of the most common types of social engineering are:
Credential harvesting: This is what it sounds like. You have some website or something you sent directly to the target, prompting them to enter their credentials. When they do so, their credentials are sent to the attacker. Preventing this attack is as simple as not entering your credentials into anything you don’t trust or expect. If you encounter a prompt for credentials which you have not seen before, check with your IT or security department before entering credentials.
Clickbait: This is very simple and typically only used in SE campaigns to test employee awareness. The objective is to entice the targets to click a link in a phishing email. If the user clicks the malicious link, typically, that activity is logged. Occasionally, the link may open something telling the user it was a phishing test. This isn’t as prevalent in the wild because it doesn’t get the attacker anything. Attackers want something from the user and just clicking a link is often not enough. While this is not a typical attack in real life, this attack could be combined with some other tactic designed to remotely do something to the targets machine, browser, or something else (and may even still show the test splash page). Employee awareness training and learning not to click on unexpected links are how you train users to avoid these kinds of attacks.
Gaining access to the target’s system. This can come in many different varieties. The attack could include an attachment with a document. The document may prompt the user for some permissions, or it may not. The attack could also contain a link. That link could appear to do anything (or nothing), but it may also initiate a download or otherwise run malicious code in such a way as to compromise the targets system.
No matter how this is achieved, the result of this attack is that code is executed on the target system in such a way that a connection is created out to the attacker. The attacker may then use that connection to further exploit that target system and possibly even pivot within the company network. Preventing this type of attack requires employee awareness training, but technical solutions can also help to mitigate the likelihood of such an attack being successful.
In short, nearly all social engineering attacks are designed to do one of those three things. This doesn’t mean that all of them will use these techniques, but those are most likely.
A motivated, and creative, attacker may come up with a derivative of this or something entirely novel when creating an SE campaign against your company’s users.

Mike Brengs
Managing Partner, Optimal IdM
Michael Brengs has over 20 years of experience in the software industry and has been deploying identity management solutions since joining OpenNetwork Technologies in 2000. He is currently Chief Revenue Officer and a managing partner with Optimal IdM.
Frequent attacks most commonly are emails crafted to look “legitimate” such as saying “Bank of America Customer Service” for the display name of the “from” in the email. But if you look at the detail of what the real email account is, it may be something entirely different.
Look at any hyperlinks by hovering over them (don’t click!). The text of the hyperlink might look legit, but the actual redirect URL could be something bogus. Look for misspellings or poor grammar. Many scammers are not native English speakers and make grammatical mistakes. Never give up any personal information from an unsolicited email. If your gut says this is “fishy,” it probably is Phishy.
Do NOT click on any attachments from unknown sources. If this is your corporate email, notify your IT staff.
The 2018 Verizon data breach report states that 81% of hacking-related breaches leveraged either stolen and/or weak passwords. And that makes sense because the human element of any security system will always be the weakest link.
But there is a simple step to reduce the chances of being hacked.
Get security training. Often, employers provide education about security vulnerabilities, like e-mail phishing, ransomware programs, and social engineering.
What should you do if you fall for a phishing campaign?
Re-set the password for that site. Do NOT use a password or login information similar to another site’s password. Monitor that account closely for at least 90 days on a daily basis. If a bank or other sensitive nature, contact them.

Jonathan Broche
President, Leap Security
Jonathan Broche is the Founder of Leap Security Inc., an Information Security company specializing in adversary simulation. With over ten years of experience in Information Technology, Jonathan specializes in penetration testing, social engineering, and secure system configurations. Jonathan is recognized for his exploits and open source tools.
We are living in an era of security where users are becoming more aware of social engineering attacks. Organizations are implementing and enforcing security awareness training more, and this is great. This is something security professionals have been pushing to accomplish for years, so seeing it being done is satisfying.
Attackers, however, always stay one step ahead. What we see now in the industry is a move from generic social engineering scenarios too much more targeted. Attackers are now taking their time to craft social engineering scenarios. Before sending out an email, making a phone call or physically approaching an organization or individual, they are doing their research.
Common Attack Vectors
They use information that is publicly accessible on the internet to gain more knowledge about their target. Most individuals enjoy posting their professional accomplishments on LinkedIn. More often than not this includes technologies implemented within an organization. Others share information on social media and don’t adequately protect it allowing attackers to get an understanding of what someone’s likes or hobbies are to build rapport and gain trust during an interaction quickly.
The goal of the attacker is to use social engineering to build trust and leverage that trust to obtain information. A typical attack is having users open an email attachment, or visit a website. By leveraging mshta.exe to execute code and compromise the system ultimately. The same goes for phone-based social engineering; the attacker will build trust and leverage that trust to have the user to visit a website or open an attachment.
Prevention
Ensure that users do not provide information unless they confirm the identity of the individual calling them.
Also, teach individuals within your organization to communicate. If someone suspicious calls them asking for sensitive information, or they receive a phishing email inform! If individuals communicate then the IT Security department within the organization can act quickly to blacklist that domain/email to ensure it doesn’t spread.
Consider implementing an email protection solution within your environment that’ll protect from spam, malware, or threats. Email protection technologies will automatically scan incoming emails and attachments giving more control to network administrators.
Lastly, organizations should continue to perform security awareness training. Then, leverage an Information Security company to perform social engineering to determine the real world risk within their organization. Social engineering assessments will allow organizations to test their users knowledge in a simulated attack.

Tom DeSot
EVP and CIO of Digital Defense, Inc.
Currently, the most popular form of social engineering is “whaling.” Whaling, for the uninitiated, is a social engineering attack either from a phone call, or more than likely, a well-crafted email that is targeted at the C-Suite within an organization. Typically, the attacks ask the end user to either make a transfer of money or to approve the transfer of money to a foreign bank account. Often the email is urgent and prompts the reader to take quick action to resolve the matter.
Another type of attack that remains active and successful is the “USB drop.” In this scenario, the attacker drops USBs near employee entrances or other entry points. The USB flash drives are often labeled “Bonuses 2018” or “CEO Salary Review” to prompt the user to want to put the USB in a computer to look at the contents. When the user executes the file (a fake spreadsheet or Word document), the file can attempt to infect the system with a virus or other types of malware such as ransomware or it may attempt to exfiltrate data that is located on the user’s computer and transfer it outside the organization.
User training = Prevention! Users are the first line of defense when it comes to any type of social engineering attack. They should be trained in ways to recognize social engineering. If they have been appropriately trained, spotting “whaling” attacks and avoiding USB drops, the company stands a much better chance of withstanding an attack. What is critical is that this training takes place from the C-Suite all the way down to frontline staff to ensure that the entire organization is aware of the dangers of social engineering.
Another way to protect the organization is to hire a firm to conduct a “live fire” exercise against the company and send in fraudulent emails or conduct USB drops and then measure how well the organization reacts to the exact. This is a perfect way to determine if the training that is being undertaken is sinking in and is being retained by staff at all levels.

Jeff Wilbur
Technical Director of the Online Trust Alliance
Jeff is technical director of the Internet Society’s OnlineTrust Alliance (OTA). The Online Trust Alliance is an initiative of the Internet Society, the global non-profit dedicated to ensuring the open development, evolution, and use of the Internet founded by the “fathers of the Internet,” Vint Cerf and Bob Kahn.
By far the most prevalent social engineering attack on organizations involves spear phishing.
Fake email pretending to be from a company executive, employee or third-party vendor that requests the recipient open an attachment or perform an action. The message can seem as innocent as an attached monthly report (which actually contains malware), or as serious as a request to transfer millions of dollars to a “new” account or to send sensitive employee information to a personal email address.
By mining information from public sources (such as where an executive is traveling or who an organization’s third-party vendors are), attackers can create compelling social engineering ploys that ring true to company employees, and the urgency of the requests can cause employees to abandon standard precautions.
Since most of these attacks happen via email (though more are happening via telephone as well), it is important to build in proper layers of defense.
For email protection, the first step is the implementation of email authentication technologies that can verify whether a message is coming from the purported sender. This allows malicious messages to be discarded immediately.
Additional steps are email security services that assess the legitimacy of messages from unfamiliar senders and scan attachments for installing malware. Messages thought to be at risk can be examined more closely or discarded. Finally, for emails that make it through to the inbox (and this would cover phone calls as well), it is crucial that employees are alert to such scams. Established processes should be in place to verify the request or require multiple executives’ approval on large financial transfers or access to sensitive data.

Amar Singh
CEO & Founder of Cyber Management Alliance Ltd
Industry Influencer & Leader, Amar’s an experienced cybersecurity and privacy practitioner, guest lecturer at universities, CISO, and a mentor. An industry acknowledged expert and public speaker Amar’s regularly invited to speak and share his insights by organizations like BBC, The Economist’s Intelligence Unit, FT, SC-Magazine, Computer Weekly and The Register.
The good news is that the complexity of social engineering attacks are NOT yet AI, or Machine Learning powered, but we are probably not far from that day. Its sad news because we, humans and organizations, can’t seem to protect ourselves from what are ridiculously lousy quality phishing attempts, what chance to do we stand when cybercriminals employ machine learning and or AI.
Phishing emails (not targeted phishing) are still the weapon of choice for most wannabe and established cybercriminals. SMS text-based phishing carries on as another one that still seems to work for criminals. I would argue that the industry is causing unnecessary confusion by deriving complex monikers for what is essentially the same problem.
Interestingly as LinkedIn is increasingly becoming the external, B2B-communication medium of choice so are criminals turning to it for launching social engineering attacks. There seems to be a certain level of inherent trust when a stranger, with a reasonable sounding title and employer, reaches out to connect and share files and exchange information.
Merely educating and making the end user aware of this threat is NOT good enough.
Technology must underpin and provide transparent data security where the overall damage to the business and user is low, even if the user does open a malicious file or enters his or her password.

Trave Harmon
Chief Executive Officer at Triton Technologies
The first rule: Do not put any contact information in any shape or form on your website in regards to the operation of your business. No CFO, no account manager, just a generic email and or I link to a generic email within the company. Email such as bills@, AR@ our best practices which for our clients has been a boon.
I also recommend utilizing cloud flare to stop any scraping of the website of personal or corporate information.
The most common scams I see in order are:
- Your account is suspended/email cannot be delivered / over quota. Usually associated with office 365 accounts.
- A sum of money needs to be transferred, to a charity, outstanding invoice, or repo company, usually representing the CEO to the CFO or office manager.
- Attached is your document that you are looking for, FedEx shipment, UPS shipment, scan details, or more. This is usually associated with targeted malware if you are a publicly traded company, or are on a public list of some type.

Greg Scott
Cybersecurity Professional & Author of Bullseye Breach and Virus Bomb
Far and away, the most common social engineering attacks come via email. Email security has an architectural weakness that allows anyone to impersonate anyone else. Attackers exploit this weakness in all kinds of creative schemes. If Alice trusts Bob, Criminal Carol might impersonate Bob and try to persuade Alice to do something stupid. We all see these every day with emails claiming to come from our banks or credit card companies. Or fake invoices. Or variations on the Nigerian prince. Or phony tech support schemes. The only limit is the creativity of the attacker.
Fun with names is also a biggie. It’s really a subset of phishing, but prevalent enough for a mention on its own. Let’s say, Clarence, pretending to be Bob, sends Alice an email with a link to, say, a favorite cake recipe. The link points to recipes.bob.com.abazillionweirdcharacters.evilclarence.com.
Alice sees the first part of that name and assumes it’s a safe link. So she clicks or taps it. But she doesn’t know how Internet names work, and so she ends up on Clarence’s evil website, where Clarence steals every piece of information inside her computer. She defends herself by investing 10 minutes into education about how names work and staying vigilant.
Malicious emails aren’t the only attack vector. People fall victim to fake tech support calls all the time. If somebody calls unsolicited and claims they’re from Microsoft, or maybe the corporate IT Department, and they want to fix your computer, just say no. I had fun with one such call when I asked where the caller was from and he said, downtown Ohio. I asked him if his mom knew he was stealing from people.
Trust violations can also do it. Visit a site pretending to be, say, Amazon or maybe your banking site, and unwittingly give away your credentials. Sometimes phishing schemes entice us to visit imposter sites; other times its typos in the URL. Defend it by being aware of certificate anomalies, but even that is not one hundred percent effective.
In general, attackers are intelligent, they collaborate, and they want to manipulate you into doing something against your own interest. Fight back by staying vigilant and exercising skepticism.
Unfortunately, no technology exists to prevent social-engineering email attacks. The key to prevention is education and vigilance.

Ron Schlecht
Managing Partner BTB Security
Ron has almost two decades of experience in cybersecurity and regularly performs penetration tests on companies, which includes social engineering, to find and then secure companies’ weak points.
Believe it or not, the fake email asking employees to log in to a company look-alike website, or to download software updates still seems to get most organizations. Any time an employee reads an email and feels like they should help a coworker by downloading something or clicking a document, it should be suspect.
All companies should take the time to educate their employees on the types of communications they receive from the within the organization. Also educating with examples of spam and social engineering, and on the impact, fraudulent emails can have on the organization.
To help prevent social engineering attacks, companies also need to make it simple for employees to identify whether a message is an attempt at social engineering and to report it quickly. Furthermore, just like other security assessments, organizations should be performing computer security exercises regularly to test employees, technical controls, and incident detection and response.

Gregory Morawietz
VP of Operations Single Point of Contact
Gregory is an IT Security Specialist with over twenty years’ of network and security experience. He has worked with hundreds of firms on improving IT environments, consulting and integrating technology for the enterprise network.
Employ Access management. Restrict remote access to key files only to the people that require them. Try and use whatever MDM (Mobile Device Management) software capabilities that are available or even buy an MDM product. This way you can use mobile wipe device and control data that is on your employee’s devices. Beware of phishing attacks and ensure your procedures for pay, and commission to employees.
I have seen hackers infiltrate a company’s financial procedures and use false domains to get money wire transferred to accounts.
Be suspicious of emails. Train employees to check and recheck email domains.
Try and let employees also know that whatever they post on social media might be able to be used to launch a phishing attack on them.
Beyond training and education. Some companies now regularly launch phishing attacks on employees so they can see who might still be susceptible to attacks or who might need some additional training or help.

Robert Siciliano
Security Awareness Expert & Best Selling Author at Safr.Me
Robert is a United States Coast Guard Auxiliary Flotilla Staff Officer of the U.S. Department of Homeland Security. He is fiercely committed to informing, educating, and empowering people so they can be protected from violence and crime in the physical and virtual worlds.
Telephone and inbound email communications are ripe with fraud.
Employees need to be tested again and again. When they fail, they need to be reminded and instructed what to do when they receive such communications.
Consistency is critical while making it fun, and interesting. Repetitive training utilizing Phishing simulations is the best way to keep employees on their toes.

Steven J.J. Weisman
Attorney & College Professor at Scamicide
Steve Weisman is an attorney, college professor at Bentley University where he teaches White Collar Crime and one of the country’s leading experts in cybersecurity, scams and identity theft. Among his ten books are “The Truth About Avoiding Scams” and “Identity Theft Alert.” identity theft.
By definition, social engineering depends on personal information of the targeted employee to be manipulated to disseminate information in an email or text message.
Companies should consider how much information they make public about their employees.
Company policy should have rules regarding social media use by employees such that they do not provide information to be used to make them victims of such socially engineered attacks.
Training employees never to click on links unless they have been verified is critical. Social engineering by which employees are lured to bogus websites or click on tainted links in emails or text messages that have been specifically tailored to appear trustworthy is the primary way that a variety of malware including keystroke logging malware and ransomware is delivered. Also, companies should consider the use of whitelisting or antivirus software which will prevent the downloading of any software that has not been previously approved. This provides tremendous protection even if an employee clicks on an infected link.
Malware that can steal data can be used for purposes of identity theft of both employees and clients. Malware can steal financial data used to access company bank accounts or social engineering, such as in the case of the Business Email Compromise can convince an employee to send payments to the thief believing it is a legitimate transaction.
Employees are also targeted by spear phishing emails to lure them into clicking on links in emails and downloading a wide range of malware.
Ransomware or malware can harvest company financial information that can be exploited for identity theft or direct theft from financial accounts of the company. Companies should make sure that they are using the most up to date security software that can recognize spear phishing emails.
It is also essential to update security software as soon as the latest patches are issued. Equifax suffered its massive data breach when a vulnerability in its Apache software was exploited although Apache had a patch for the particular vulnerability months in advance. However, Equifax failed to update its software in a timely fashion.
Social engineering also encompasses infected bogus websites that may be attractive to employees. Certain types of websites should be blocked by work computers or devices. Also, some advanced kind of malvertising malware can be downloaded merely by going to the infected site without even clicking on anything. This type of malvertising can often appear on legitimate websites which is why it makes sense to use adware software to prevent it from being downloaded.
Education is the most essential part of protecting companies from social engineering attacks. Education should be an ongoing process with frequent testing of employees as to vulnerability management.
Of course, security software that can recognize phishing emails should be used, but companies should realize that this type of software is far from totally effective. For this reason, companies should also consider using whitelisting software that will not permit the downloading of any program that has not been previously approved. This is good protection from when social engineering manages to convince the employee to click on an infected link because it will prevent the malware from being downloaded.

Dennis Chow
CISO at SCIS Security
Dennis leads the Cyber Threat Intelligence planning grant for the entire U.S. healthcare vertical in collaboration With DHS and Health and Human Services.
The most common attacks are through the mediums from email, text messaging, and social media. At the end of the day, the attackers are interested in direct passwords, credit card numbers, or answers to password recovery questions for password resets. The victims tend to vary, but it is almost always everyone in the organization because there’s some form of network access.
It’s not feasible to ‘prevent’ them per se, but you can reduce your risk and threat surface as a whole including:
- Unsubscribing and reducing your sign ups with 3rd parties and advertisements. The more your email or names associated with an email list, the more eyes have access to target campaigns on their victims.
- Take security awareness training seriously and look for signs that an email or other communication ‘isn’t quite right.’
- Encourage your cybersecurity or IT provider to enhance their spam filters and PBX call filtration systems.
Recent Posts
7 Most Famous Social Engineering Attacks In History, Be Prepared
Social engineering, in the context of IT, often refers to the manipulation of people to perform actions or give up confidential information.
As long as there has been any proprietary or private information, bad actors have been attempting to steal it. Recently, with the acceleration of technology and the accessibility to the internet, hackers have refocused their strategy. Where, in the past, an assailant would be required to be physically in the room to breach a system, now a simple email is all that is necessary.
The goal of such an attack is to extract information, commit fraud, or gain system access by tricking an unsuspecting user by gaining their confidence.
Naturally, as technology becomes more widely adopted, there has been an uptick in such attacks. Social engineering attacks are worth keeping an eye on. At the very least, to monitor your company’s vulnerabilities.
The Sony Pictures Hack
On Monday, November 24, 2014, many of Sony Picture’s employees began to see skulls appearing on their computer screens with software rendering their machines inoperable. It was quickly discovered that many of Sony’s official Twitter accounts had been compromised as well. A group identifying themselves as the Guardians of Peace took credit for the hack and began to issue demands. They claimed that they were in possession of over 100 terabytes of stolen data and would start releasing it if their demands were not met.
Unfortunately for Sony, the e-mail, outlining the demands of the group, was missed, likely caught up in a spam filter or the daily barrage of messages we are all used to receiving. Shortly after the deadline for the demands had passed, Guardians of Peace began leaking unreleased films to social media. In addition to unreleased content, they also leaked personal information about employees of Sony Pictures including their families, inter-office e-mails, salary information, and more.
Guardians of Peace then demanded that Sony stop production on its upcoming film, The Interview. This film, a comedy produced and directed by Seth Rogan and Evan Goldberg, had a plot to assassinate North Korean leader Kim Jong-un. The group then threatened attacks on movie theaters that were intending to screen the film. Eventually, after much public out-cry and theater chains opting not to screen the film, Sony scrapped the film’s premiere and release.
Though it seems that the main aim was to take down the film, the information leak may be deemed as more disastrous to Sony. Emails showing that female actors Amy Adams and Jennifer Lawrence were paid less than their male co-stars were revealed amongst other embarrassing and racist private emails from producers and (then) Sony Executive Amy Pascal. The Interview was eventually released digitally, for free.
The fallout for this hack continued with multiple government agencies becoming involved. An investigtation on whether North Korea itself had purpotrated the hack was launched. Additionally many organizations such as Color of Change called for the firing of Amy Pascal who was eventually dismissed.
A caveat to the hack, however, is that the gender pay debate quickly became a mainstream conversation.

Target Data Breach
In 2013, hackers accessed over 40 million of Target customers’ credit and debit card information through a large scale social engineering attack on Target’s point-of-sale (POS) systems. The systems were infected with malware, confirming what security experts suspected since the massive data breach was announced in December of that year. What is interesting is that it was discovered that hackers went through another company to get to Target. It was later announced that information such as names, emails, addresses, and phone numbers of an additional 70 million customers had also been stolen.
A PoS attack such as this is often called a “RAM scraper.” The term originates from the way the malware scans a point-of-sale terminal’s random access memory (RAM) for transaction data with the intent to steal it. When a card is swiped, the data encoded on the magnetic stripe is passed along with the transaction request to the payment application and then on to the company’s payment processing provider.
Target made many mistakes that eventually lead to this attack.
First, Target gave remote access to its network to its HVAC vendor Fazio Mechanical Services. This company was then targeted with a phishing email that installed malware onto their system. The hacker then used this to route into Target’s network, installing malware that recorded and extracted the information for every credit and debit card used on an infected machine.
At the end of 2015, Target announced a loss of $162 million due to data breach-related fees.
2016 Democratic National Committee Email Leak
In June and July of 2016, during the 2016 Democratic National Convention, an e-mail leak occurred that was allegedly obtained by Russian intelligence agency hackers. The leak, published by DCLeaks and WikiLeaks, included e-mails from seven key DNC staff members as well as the governing body of the United States Democratic Party, totaling 19,252 emails and 8,034 attachments.
The leaked documents suggested that the party’s leadership had attempted to sabotage Bernie Sanders’ bid for President. In response, the chair of the DNC, Debbie Wasserman Schulz, resigned. Once the convention wrapped, DNC CEO Amy Dacey, CFO Brad Marshall, and Communications Director Luis Miranda also resigned.
Though WikiLeaks founder, Julian Assange, has stated that his source of the e-mails was not Russian, on July 13, 2018, Special Counsel Robert Mueller indicted 12 Russian military intelligence agents allegedly responsible for the attack.
On July 22, 2016, more than 150,000 additional e-mails, stolen from personal Gmail accounts or accounts linked to the DNC hack were released to the DCLeaks and WikiLeaks websites. It turns out that the hack was perpetrated via a simple case of spear phishing. The hackers sent an email that looked just like it had been sent by Google requesting that the user click a bit.ly link to reset their password due to malicious activity on their accounts. This successfully tricked people into entering their information, giving complete access to the hackers. Once they were in, the hackers started to release information.
On August 12, 2016, DCLeaks released information about more than 200 Democratic lawmakers that included personal cell phone numbers.
Associated Press Twitter Accounts
In April of 2013, the Associated Press’ (AP) Twitter account posted a tweet stating, “Breaking: Two Explosions in the White House and Barack Obama is injured” to it’s more than 2 million followers.
In the 3 minutes that the tweet was public and the account compromised, the DOW had plummeted 150 points, equivalent to $136 billion in equity market value.
The Associated Press received an email that appeared to be from others within the company. In fact, the email was from the Syrian Electronic Army. The email included a link that led to a page requesting the login details for the AP Twitter account. That the name in the ‘From’ field of the email didn’t match the name in the signature line was the only clue that the email was fake.
Once the attackers had the login details, the Syrian Electronic Army posted a single tweet, sending the financial market into chaos.
Though the impact of the tweet was quickly contained, there is no telling how devastating an effect on the economy this type of attack can do.
Similar attacks have been used to shift markets with false information. In August of the same year, information began to spread on Twitter that suggested Syrian President, Bashar al-Assad had been killed. This sent the price of crude oil spiking.

RSA SecurID Cybersecurity Attack
On March 17, 2011, it was announced that RSA had been the victims of an “extremely sophisticated cyber attack”.
The breach began with a spam email that purported to come from a recruiter. Four employees at RSA opened the attached spreadsheet where a 0day (zero-day attack) Flash exploit was buried inside. This installed backdoor access to their computers which put the whole system in jeopardy.
RSA initially denied that any information the hackers gained access to could be used against its users. However, there are reports that the breach involved the theft of RSA’s database mapping token serial numbers to the secret token “seeds” that were injected to make each one unique. Further reports that RSA executives were telling customers to “ensure that they protect the serial numbers on their tokens” lend credibility to this theory.
The breach was estimated to have cost EMC, which is the parent company of RSA, $66.3 million.
In April of 2011, there were rumors of L-3 Communications being attacked as a result of the RSA breach. Moreover, in May of the same year, Lockheed Martin thwarted its own attempted breach from the RSA attack.
Yahoo! Security Breaches
In 2016, the one-time internet giant, Yahoo!, reported two significant data breaches had occurred, compromising user data.
The first breach occurred in 2014 and compromised half a billion user accounts. The second, in August of 2013 was initially believed to have affected over 1 billion accounts. In reality, in October 2017, it was disclosed that all 3 billion user accounts were impacted. A simple spear-phishing email to a semi-privileged engineer was all it took to compromise all the customer accounts at the company.
Both breaches, individually and combined, are considered to be the largest discovered in the history of the internet. Compromised details include names, e-mail addresses, phone numbers, security questions (encrypted or unencrypted), dates of birth, and passwords. Furthermore, the breach was used to falsify login data, allowing hackers to grant access to any account without the use of a password.
The data accessed in the incident was put up for sale on the dark web and no doubt used by others for their scams.
Yahoo! has been criticized and publically shamed for the length of time it took to disclose the breach. The breach ultimately impacted the sale of the company to Verizon. Initially, the sale was estimated to be at $4.8 billion but decreased over $350 million after the disclosure.
15 Year Old Kane Gamble & The CIA
He may have been only 15 at the time, but Kane Gamble successfully used social engineering to get into the email accounts of CIA Director John Brennan and James Clapper, Director of National Intelligence, amongst others. This gave him access to highly sensitive military documents and intelligence operations in Iraq and Afghanistan.
Gamble used vishing (phishing via the phone) to persuade Verizon to reveal information about Brennan which he then used to impersonate Brennan when he contacted AOL. His method was simple but efficient, leading him to change security questions and numbers and gain access to many other accounts. He also managed to set up an auto-forward service directing phone calls from Clapper’s home to the Free Palestine Movement.
Gamble’s other targets included:
- Jeh Johnson, the then-Secretary of Homeland Security
- Mark Giuliano, FBI’s Deputy Director at the time
- John Holdren, the senior science and technology adviser to former US president Barack Obama
- Avril Haines, the White House deputy national security adviser
- The US Department of Justice
In April 2018, Gamble was sentenced to 2 years detention, and all his computers were seized.
Get Started With Social Engineering Prevention Today
All of these social engineering attacks show that simplicity is often the best way to gain access to a system. People are the most vulnerable point in any business. Whether the attacker went through some people or just required one person’s details, it is remarkable how quickly any socially engineered attack can escalate.
It’s important to remain vigilant in your security. Question every type of communication you receive and always be on the lookout for potential threats, no matter how small they may seem.
Recent Posts
What is UPnP or Universal Plug and Play? A Little Known Security Risk
Universal Plug and Play (UPnP) was marked as a significant technological advance.
But, it comes with its share of drawbacks that might leave your systems vulnerable to potential cyber-attacks. In fact, it is enabled by default on millions of routers.
This article will discuss what UPnP is and the risks it poses to your network’s security.
What is Universal Plug and Play (UPnP)?
Universal Plug and Play is a set of networking protocols. It enables network devices such as computers, Internet gateways, printers, media servers, and Wi-Fi access points to discover each other’s presence on the network and create functional network services for data sharing.
UPnP was intended for private networks that do not have enterprise connectivity.
This technology operates under the assumption that a network runs IP (Internet Protocol) after which it leverages SOAP, XML, and HTTP so that it can provide service/device description, data transfers, actions, and eventing. Advertisements and device search requests are enabled by running HTTP in addition to UDP – port 1900 – using HTTPMU (multicast). Search requests’ responses are usually sent over the UDP.
This technology was endorsed by the UPnP forum which is an industry initiative to promote robust and straightforward connectivity to personal computers and stand-alone devices from different vendors. The panel comprised of over 800 vendors who were involved in everything from network computing to consumer electronics. But as from 2016, Universal Plug and Play is managed by the Open Connectivity Foundation.
In concept, Universal Plug and Play is supposed to extend plug and play (a technology that dynamically attaches devices directly to a machine) to zero-configuration networking for SOHO and residential wireless networks.
Thus, UPnP devices are archetypical plug and play. When they are connected to a network, they automatically seek and create working configurations with other hardware.
What Does UPnP Do?
If the above definition seemed a bit complex, then let us use a printer as an example.
In an office setup, the first step would be to connect it physically to the network router – even though you can do it via Wi-Fi today. In the past, you would have to search for the printer manually and then set it up so that other devices within the network can find the printer. Today, however, this process happens automatically thanks to Universal Plug and Play.
Once they are connected, the devices on that network will continue communicating with each other by receiving and sending data. As such, a computer can instruct the printer to print documents; a media center can transmit audio data, while mobile devices can mount themselves onto the computer. The possibilities are endless.
This is why it is called plug and play. You plug in a device and can start playing it right away without having to go through the hassles of setting up and configuring the connection. This makes it one of the most convenient networking technologies that are available to us.
However, UPnP technology has serious security flaws.
For instance, if a computer or some other device connected to the router exploited, the attacker may gain remote control of all devices and security systems. Thus, allowing access to your passwords and access all the other devices that are connected to the network. Additionally, once a device has been compromised, it can be utilized as part of a botnet to issue DDoS (distributed denial of service) campaigns to take down sites while hiding the attacker’s location. It might also provide them with a starting point for other attacks.
Some of the most significant cyber-crimes in recent history have leveraged internet-based devices to launch major DDoS attacks.
With more and more devices utilizing this technology to get connected to the internet, they are the ideal targets for hackers who have to accumulate devices so that they can overwhelm a business network.
Security Risks of Universal Plug and Play
A security survey by Akamai discovered that hackers are actively exploiting the weaknesses of this technology as a starting point for more prominent attacks.
For example malware distribution, DDoS, credit card theft, and phishing attacks.
The evidence found suggested that over four million devices were potentially susceptible to being used in a DDoS attack. This number accounts for approximately 38 percent of the 11 million internet-facing UPnP devices that are being used all over the world. This serves as a big pool for hackers to leverage what would have been small and local attacks into serious threats.
Primarily, these cybercriminals exploit this technology’s weaknesses to reroute the traffic in your business repeatedly until it is untraceable. And in spite of the industry’s knowledge about these vulnerabilities, hackers continue to take advantage of the general apathy towards strengthening the technology.
By default, this technology does not employ authentication.
This means that to ensure security, the devices in the network have to incorporate the additional Device Security Service or the Device Protection Service. There is also a non-standard solution that exists known as Universal Plug and Play – User Profile (UPnP-UP) which proposes an extension to enable user authentication and authorization techniques for UPnP-applications and devices. Sadly, most universal plug and play device implementations do not have authentication methods because they assume that local systems and their users can be trusted.
If authentication techniques are not implemented, firewalls and routers that run the UPnP-protocol become vulnerable to attacks.

Don’t Overlook Securing Your Network
The purpose of Universal Plug and Play technology is to make devices on a specific network to be easily discoverable by other utilities on the same network. Unfortunately, some Universal Plug and play control interfaces can be exposed to the public internet thereby enabling individuals with malicious intent to locate and obtain access to your devices.
A device that is compromised is nothing short of a ticking time bomb for your business network. Because of the complicated nature of these attacks, detecting one as it happens can be very difficult for the user.
In our current world where a fluid work culture is ideal, more and more employees are taking connected devices to and from their workplaces. There is no room for error when it comes to your business’s cybersecurity.
The takeaway here is that you should ensure that your UPnP router settings are disabled.
Recent Posts
Start a Cyber Security Awareness Training Program Your Staff Can't Ignore
Corporate cybersecurity is a mindset as much as it is a strategy.
According to Verizon’s 2018 Data Breach Investigations Report, internal actors still account for an alarming number of data breaches. Last year, 28% of attacks involved insiders.
Although adequate security systems are vital, these findings point to the importance of educating employees on cybersecurity best practices. To efficiently protect their data, organizations need to develop a security culture throughout the company. The best way to do so is to introduce relevant, engaging, and regular security training for employees.
For those who tried to do so but failed and for those who are not sure how to start, we asked top cybersecurity experts for their best advice. Take a look at what they said and start implementing their tips today.
- Jef Towle, Intel Corporation
- James Olivier, Shades of Security
- Lisa Parcella, Security Innovation
- Lauren Hilinski, Shred Nations
- Robert Douglas, PlanetMagpie IT Consulting
- Wade Yeaman, Fluid IT services
- Neil Readshaw, Anonyme Labs
- Greg Scott, Author
- Mihai Corbuleac, ComputerSupport
- Sean Spicer, AgileIT
- Derek Anderson, Biztek Solutions, Inc.
- Joshua Crumbaugh, PeopleSec, LLC
- Eyal Benishti, IRONSCALES
- James Goepel, ClearArmor Corporation
- Tom Evans, Ashton Technology Solutions
- Morey Haber, BeyondTrust
- Dean Coclin, DigiCert
- Peter J. Canavan, Safety Expert
- Robert Huber, Eastwind Networks
- Benjamin Dynkin, Atlas Cybersecurity
- Eric Sheridan, WhiteHat Security
- Mike Meikle, SecureHIM
- Bryan Dykstra, Atlantic Data Forensics
- Joshua Feinberg, Data Center Sales & Marketing Institute
- Larry Kahm, Heliotropic Systems, Inc.
- Tom DeSot, Digital Defence, Inc.
- Kevin Gray, EnvisionIT Solutions
- Justin Lavelle, BeenVerified
- John C. Ahlberg, Waident Technology Solutions
- Robert Siciliano, HotSpot Shield
- Amanda Bigley, Hummingbird Networks
- Isaac Kohen, Teramind
Cyber Security Awareness Training, Advice From Industry Experts

Jeff Towle
Sr. Cloud Solution Security Architect, Intel Corporation
Jeff Towle is an industry veteran in the Information Security, Governance, Risk and Compliance industries. At Intel, Mr. Towle specializes in optimizing Intel-based security designs to contend with modern-day threat vectors for Cloud Service Providers.
Mindfulness with safeguarding your Identity
An employees’ Corporate Identity is THE critical component to safeguarding all valuable top secret or highly classified documents, customer records, Intellectual Property, or design secrets. Hackers will go to great lengths to trick employees/end-users to steal their access credentials. This goes way beyond just making sure you update your password with strong alpha-numeric characters regularly per corporate password reset policy. A good rule of thumb is to treat all the files, folders, documents, social media, corporate websites you have been granted access to as would your own bank account. Sharing your corporate ID is never a good idea, even under temporary circumstances. It’s also a good idea from time to time to check with IT to see what exactly you have access to. Especially if you have been at the company for a long time. Do you want access to systems you used 5 years ago? This only creates risk, and it’s OK to ask for a list of things you still may be able to access and request that access be removed.
Attribution of all Business Communications
What is attribution? Simply put, “Do I REALLY know who sent this message to me? It’s important to train yourself to get into the habit of verifying the author or creator of a digital communication to you (via email, text, social media, automated message, website alert/notification, etc.). This is an awareness technique that’s easy to adopt once you start to just ask the question. With email, you can double-click on a name or hover your mouse on the From: field, and it will resolve to the actual email address. SPAM, Phishing attacks and Malicious Ransomware messages often resolve to a string of characters that are easily seen as suspicious. If the email doesn’t end in “companyname.com” you likely are being subjected to some sort of deceptive communication. The same is true of malicious URL’s. Instead of clicking on the link to find out what it resolves to, hover your mouse or right click to see what the whole string looks like. These changes in behavior can really make a difference beyond just updating antivirus, OS patching, and firewall security controls.
Cyber Attitude
You can be your own best anti-hacking expert with these simple tips:
- Don’t leave your laptop or desktop alone with applications open. Make sure to have a password enabled screen saver activated any time you leave your workstation
- Don’t tailgate. Remember your Identity is critical, and this is true of your employee access badge. It’s only meant to let you into the building, parking lot or server room. Make sure you don’t just let people follow you as a matter of courtesy or convenience.
- Hackers love social engineering. They will call and posture as a co-worker or service agent. They can be very crafty about piecing together information to hack into systems or break or sneak into a building. So beware of those asking questions about scheduling and where people will be at what time. Safeguard information around people’s system access just like you do your own.
- Don’t even read it, delete it. And the worst thing you can do is forward it to others.
- Make sure you have a backup of your laptop or workstation’s data. Ask the IT staff if your data is being backed up regularly. This may be the only way to recover from severe ransomware attacks.
- Believe it or not, you can become a frontline defense security expert to assess whether any application or system you access is vulnerable to some attack. Pay attention to irregular content that’s posted, the amount of time it takes to process information on systems or any strange errors reported in a business process flow. Hackers rely on a lack of incident response planning to have their malware spread and escalate access to damage or steal data so the sooner your report something that is not normal, the better.

James Olivier
Principal Cybersecurity Consultant, Shades of Gray Security
James Chad Olivier, author of Trust Me I’m Lying: Banks Pay Me to Rob Them is the owner and Principal Cybersecurity Consultant of Shades of Gray Security.
Make Your Security Training Program More Personal
Training is much more effective following a social engineering test. If you can show them how you tricked them into letting you into the facility, the success statistics of a spear phishing attack, and/or the success of phone call social engineering, it leaves a big impact. Especially on the ones that know they were tricked. I never reveal who was to blame as I explain the test is not a witch hunt, but an awareness exercise.
I use colorful stories from my past exploits to make the lessons more enjoyable. They have just seen one example of a test, so I tell them some other ways an attacker might exploit them. My style is to lighten the mood and tell them from my perspective which makes it more cinematic in their mind. Like a good suspense thriller. Their responses range from amusement to frightened out how easy it is to con people. When I visit them for the next training (often a year later), my clients remember the old tales and tell me how they have seen similar things during that time, and are excited to learn some new stories. This keeps them much more attentive than just a boring statement of policy and procedures.
I don’t make it just about the company. I tell people about how they are tricked personally. How to avoid scams, credit card protection (how to avoid skimmers), and encourage them to share the material with their friends in family. I explain that if we can make ourselves safe, it is better for our employer, our family, and society in general.
If nothing else, no one wants a boring recitation of policy, procedures, and best practices. Liven it up, don’t speak in a monotone voice, and don’t just read bullet points. That applies to any presentation though.
Lisa Parcella
VP of Product Management & Marketing, Security Innovation
Lisa Parcella designs and delivers comprehensive security-focused products and educational solutions for Security Innovation’s diverse client base.
Training Should Engage Staff
Training needs to be engaging to build internal expertise and competency. Here are four ways to keep cybersecurity training exciting for employees:
- Keep it Interactive: Leverage multiple types of interactions to keep learners engaged. Hands-on simulations/real-world training and tabletop exercises are influential in building offensive and defensive cybersecurity skills and help assess an organization’s situational preparedness. This supplemented with computer-based training, and reinforcement assets are effective in reinforcing lessons learned.
- Groom security champions: It’s much easier to get staff to jump on the security bandwagon if one of their own is driving the adoption versus having it come down as a “must-do” from high-level management.
- Motivate with incentives: From simple recognition to formal awards, incentive programs like belts, certificates, spot bonuses, gift cards, etc. help to facilitate progression and motivate employees to want to learn more. Role-Based: Security is a shared organizational responsibility, and there are many stakeholders including general staff, infrastructure, cloud, and development teams, and managers that need to write policy and ensure adherence to compliance and other mandates. Progressive topic-driven modules customized for specific roles are useful in building the required cybersecurity skills.

Lauren Hilinski
Digital Marketing Specialist, Shred Nations
Lauren’s company partners with document shredders across the nation and aim to make it easy to keep private business and personal information safe.
Use Real-Life Scenarios in Awareness Training
- Create consequences. If you are implementing new cybersecurity rules, create consequences for following or not following them. Whether its a reward or special monthly recognition, or if its some kind of punishment for not following your new security rules, give your employees a reason to get engaged.
- Use examples from real life cases. Yahoo, Blue Cross Blue Shield, Equifax and other large organizations have experienced devastating data breaches. Bring these cases to life with numbers and data proving the seriousness of the topic and showing that it can happen to the most sophisticated systems.
- People don’t like change, so if you are implementing new rules make sure to explain *why*, in simple terms that your employees will understand. You know your team better than anyone, explain the information in a way that makes them understand why behavior needs to change, so that even if they don’t like the changes, they understand that they are important.
- Make the information relevant. Too often these types of presentations aren’t industry specific and seem out of touch with what your employees do every day. Bring the information down to their level so that it is at the very least relevant.

Robert Douglas
President, PlanetMagpie IT Consulting
Robert has worked in the IT industry for 30+ years, consulting on everything from network infrastructure to cybersecurity.
Build each training session around a theme
- Basic email security. Never click on an email link or attachment you are not expecting. Email is the #1 delivery method for malware & ransomware. 60% of all successful hacks occur because of one person’s mistaken click.
- Never use personal email for work. Consumer email does not have business-grade security, backup & compliance features, and all of your emails could become discoverable in a lawsuit.
- Use complex passwords! Store your passwords in password management software and not on sticky notes attached to your monitor! (Begging you here.)

Wade Yeaman
Founder and CEO, Fluid IT Services
Founder and CEO of Fluid IT Services has more than twenty years of experience including leadership and operational responsibility for functions related to both business and information technology.
Use Current Events To Resonate
- Make the training engaging by using real-life scenarios. For example, drop a USB drive in the audience before the training and then during the class ask if anyone found it. Once they respond, ask them what they would do with it. The typical answer is ‘plug it into my computer to see what is on it.’ This is a great tool to show how social engineering works on the human gullibility to infect a machine and an organization.
- Make it relevant and use actual examples from recent current events. Technology is already complicated for non-technical employees to understand, the language is foreign, and most technology professionals are not proficient at translating critical technical terms into easy to understand and relevant business terms. Using actual present-day examples not only makes bridging the gap easier, but it also engages the audience in ways relevant to their experiences. One way is to show real examples of malicious emails and point to specific objects and pieces of information within each email that makes them illegitimate. I always include examples from the past 2-3 weeks to demonstrate what is happening now and also to show the importance of always being diligent.
- Make the presentation fun. This is probably one of the most challenging aspects of the training because nothing about cybersecurity is fun, but mixing in more light-hearted material, such as videos (from The Jimmy Kimmel Show in my example), change up the monotony of delivery and make use of humor to get the points across on serious topics.
- Make it collaborative. Many in the audience may be there because they were forced to, but there are always those wanting to learn and participate. Know the industry and business of your audience and ask them questions related to their specific industry, operational area, and even job type. Throughout ask what they have experienced and what they did about it. Include examples of real security incidents, breaches, ransomware and how those companies dealt with it and recovered. Understanding the amount of time, effort and money expended to recover from an incident is often hidden from employees is very eye-opening. Making cybersecurity ‘real’ will leave everyone more aware of the actual risks they will encounter both professionally and personally.
Neil Readshaw
Chief Security Officer, Anonyome Labs
Neil Readshaw is a seasoned security and compliance executive, who spent over 20 years at IBM overseeing technical direction for security architecture, leading the security workstream for the IBM Cloud Computing Reference Architecture, and programming new global data security products.
Context is the most critical aspect of security awareness training
Context means a few things to me:
– Why it matters to our company, not just generic statements about risk management.
– When the message is relevant to the employees.
– For whom the message matters most, i.e., vary the training content or its delivery by job role, as much as is practical.
Here are some examples of how we train employees:
I try and spend some time with each new employee to reinforce our security culture from the beginning. I hope that also helps the new hires see that my team is approachable and helpful. I also get a benefit from this, as I can learn what the security environment was like at their previous company. It is a great way to get new ideas and challenge the ones with which I am currently comfortable. And it is the right way for new hires from the get-go to understand the robust security and data protection culture we have at Anonyome, and thus what will be expected of them.32. Teaching employees how to detect a phishing email is very important, especially as the mailbox is so often the key to password recovery/password reset for other services.
What has been most impactful is showing people real phishing emails that have been received by our employees, as opposed to boilerplate examples. I try and share these examples through our intranet platforms as they happen, to try and capitalize when other employees may be receiving similar phishes.
For the developers in our company, security about our internal assets, but also how we build and operate systems for our products. The unfortunate data breach at Equifax became relevant for our product teams when they understood that the issues at Equifax were due to old, unpatched software. That was a reminder of why we have procedures around patching systems and keeping our use of open source software components up to date.
We keep formal, recurrent security training to a minimum to avoid cyber safety burnout from employees. However, we regularly check in with key account and data owners to ensure compliance and processes are being adhered to and of course answer any questions employees have.

Greg Scott
Author of Bullseye Breach: Anatomy of an Electronic Break-In
Greg Scott is a veteran of the tumultuous IT industry. Greg started Scott Consulting in 1994 and Infrasupport Corporation in 1999. In late summer, 2015, after Bullseye Breach was published, he accepted a job offer with a large, open source software company.
- Keep it simple. Start with care and share to be prepared and expand from there. You have to make the case it is worth their time to care about cyber-security. Once you have made that case, persuade them to share what they learn.
- Make this happen by relating every concept you teach to real-world scenarios, ideally with stories that have protagonists, antagonists, conflict, and high stakes.
- Entertain. Boredom leads to apathy, which is your worst enemy.

Mihai Corbuleac
Senior IT Consultant, ComputerSupport
I am Mihai Corbuleac, Senior IT Consultant at ComputerSupport.com – IT support company providing professional IT support, cloud and information security services.
Start sessions with relevant and scary cybersecurity statistics.
Facts like 46% of entry-level employees don’t know if their company has a cybersecurity policy or the fact that ransomware threats increased by 36% in 2018 or that 1 in 130 emails contains malware etc. It’s important for people to understand the risks of not being informed and educated regarding cybersecurity.
Secondly, always emphasize how destructive lack of knowledge and negligence could be. Finally, don’t forget to mention that most cyber-attacks could have been prevented if specific protocols would have been followed and that due diligence and staying alert represents the state of normality in today’s cybersecurity.

Sean Spicer
Director of Inbound Marketing, AgileIT
Sean Spicer is a 17-year digital marketing veteran who studied Marketing at U.C. Berkeley and earned a computer science certificate from Harvard.
The biggest issue with any security awareness training program is that the people most qualified to teach it are the same ones who are most liable to talk above their audience’s skill level.
While many of the issues in online security are fascinating, it is easy to lose the attention of your team if you get too detailed.
- Keep it fun. Roleplaying phishing scenarios, talking through real work attacks, watching the Pwn videos from Rapid 7 that detail some of the ways they have successfully breached client’s security are all fun ways to engage the audience.
- Keep it actionable. Knowing the dangers of ransomware and identity theft is useless if your team members do not know what to do if they are suspicious of something. Have a point contact or shared email box where they can forward suspicious links.
- Do not victimize, or make examples out of your team. Phishing test exercises are a valuable tool to demonstrate vulnerabilities. However, your most vulnerable employees can feel victimized if they are publicly outed or shamed, which leads to a loss of engagement with the training. Instead of highlighting who failed the assessment, highlight who did the right thing, by forwarding the emails to IT or reporting an unsuccessful penetration testing attempt.
- Be consistent. Complacency is the biggest threat to security, no matter if it is physical security or computer security. Keep your staff up to date on new developments and tools, and make sure to run assessments and micro-training at regular intervals to keep your team vested in the process, and aware of new and emerging threats.

Cyber Security training should be personable and relatable
- Speak to the employees and how they can secure themselves in their personal lives, not just company policies. This gives them more buy-in and reason to pay attention as you are now delivering them value on what they can do to protect themselves and then translate that into how the same principles apply to the organization. I always give my audience a handful of tips they can use personally first, then move on to company policies and then connect the two. It comes back to the old what’s in it for me? If companies just speak about how employees should protect their business, there is less interest, but if you give them personable tools and tips that also relate to the business, you will find greater success.
- Find engaging content. Videos are best in this day in age. I use videos that demonstrate how easy it is for criminals to hack and gain access to personal information. The videos need to be entertaining not lecturing.
- Get out of the classroom/meeting room and get hands-on. We provide a service (and several companies do) that provide real-life employee awareness training that involves sending fake malicious phishing emails to our clients’ staff. The emails do no harm, but replicate what actual bad emails do. When employees fall for our emails, they are kindly told that they failed and need to watch a video on what key points they missed. We provide owners and management reports on their companies phish prone score which gets improved quickly (30 days) with testing and sending these emails and watching the videos. This becomes more random and on-demand training that can be as little as 1 minute to 15 minutes but is consistently ongoing and raising awareness amongst the team.

Joshua Crumbaugh
Chief Hacker at PeopleSec, LLC
Joshua Crumbaugh is one of the world’s leading security awareness experts and internationally-renowned cybersecurity speaker. He is the developer of the Human Security Assurance Maturity Model (HumanSAMM) and Chief Hacker at PeopleSec.
- Shorten the length of training sessions to under 1 minute to accommodate short attention spans.
- Simplify messaging to its bare essentials and do not cover more than one topic in a single security awareness program.
- Phish users on a weekly basis.
- Capitalize on just-in-time training by educating at the moment a mistake is realized.
- Anchor lessons in emotion.

Eyal Benishti
Founder & CEO, IRONSCALES
Eyal Benishti is a veteran malware researcher and founder and CEO of IRONSCALES, the world’s first automatic phishing prevention, detection and response platform.
Most cybersecurity security awareness training conducted for employees is related to email phishing, specifically providing tips and tricks for how business workers can better identify a malicious email. In theory, this is a sound investment. With nine out of ten attacks beginning with phishing, there is a human vulnerability that needs to be addressed.
The challenge is that today’s attacks are so sophisticated and complex that even hyper-phishing aware employees cannot identify them. As an example, 1 in 3 workers in the utility industry in Michigan recently opened a fake phishing email even though those people are mandated to go through security training. In fact, Verizon estimates that only 17 percent of phishing attacks get reported.
So what should companies do?
For starters, if they are going to invest in phishing training, then they should adopt tools that are gamified and tailored to each user’s specific level of awareness. This method is proven to keep people’s attention spans longer and help trigger information retention. Secondly, and most importantly, organizations must realize that humans alone – no matter how much training – can never be relied upon as an actual security safeguard. Instead, companies should look for ways to have humans and machines work together in layers so that when one misses an attack, the other has its back. In this scenario, each time there is an attack, both the human firewall and the machine get a little smarter, further reducing the risk of future phishing emails being successful.

James Goepel
James Goepel, Vice President, General Counsel, and Chief Technology Officer at ClearArmor Corporation
Improving cybersecurity awareness requires cultural changes
Employees need to better appreciate the potential business impacts of their actions, and they need to be held accountable. Until that happens, training is just something employees have to suffer through, rather than being something they understand they need to do. Accountability does not mean the company focuses on punishing those who do not comply. It can also reward those who do.
This can be achieved, for example, through gamification, with employees who do comply receiving positive rewards, such as Starbucks or Panera gift cards if they achieve and maintain certain scores. These kinds of positive reinforcements help move security from being an afterthought to the forefront of employees’ minds, which in turn helps security become part of the culture.

Tom Evans
Over 35 years in IT. Cyber security awareness training for employees is a part-time occupation now that I am retired. End-user support and dealing with security issues occupied most of my working career.
- Actually do training. Even boring training is better than no training. If you do not have the resources in-house, seek outside sources. There are many.
- People enjoy videos these days. There are lots of them out there that help emphasize the severity of the issues. Believe or not NOVA (PBS) has some excellent ones on YouTube. Cisco and others have videos that can be used in training.
- I give out candy when someone answers a question posed to the group. it is not a lot but it gets people involved.
- Once a year is not enough. You cannot train one time and expect people to remember everything. The threat landscape continues to change and training needs to evolve to keep up.

Morey Haber
CTO, BeyondTrust
With more than 20 years of IT industry experience and author of Privileged Attack Vectors, Mr. Haber joined BeyondTrust in 2012 as a part of the eEye Digital Security acquisition. He currently oversees BeyondTrust technology for both vulnerability and privileged access management solutions.
Test The Effectiveness Of Your Staff Training
- Make it interactive. Whether the training is online or in a classroom, it must be interactive and engaging. Watching videos, hours of powerpoint, or even mindless cartoons does not work. Any training, regardless of media, must require the end user to engage the instructor, scenarios on the screen, and provide feedback. Making it fun is important but making it positively interactive is critical.
- Make it real-world. Too often training is based on what-if use cases. If you click on this link, if you open this email, if you share your password, etc. this will happen. While these are informative, good cybersecurity training includes real-world examples from other companies (or from within your own) of people doing bad things and the real-world ramifications. If it included the public details from Uber, Equifax, Ashley Madison, Delta, etc. – then employees can relate better to their own experiences.
- Include role-playing and testing. Employees will learn best if they are placed in actual situations that reinforce what they just learned. While standard role-playing is good, testing and cybersecurity certification are required. There is no reason that security teams should stop there. They should perform a light-hearted pen test after training. This could sample phishing emails; a few loosely dropped USB thumb drives or even fake phone calls. People always remember training best when tested with real-world role-playing and testing.
- Do not do it in isolation. Any staff security awareness and training should not be from a person’s desk. It should have dedicated time and location even if it requires them to use their own laptop. There are too many distractions.
Dean Coclin
Senior Director of Business Development, DigiCert
Dean Coclin has more than 30 years of business development and product management experience in cybersecurity, software, and telecommunications.
More useful than training videos are actual tests or exercises.
For example, a phishing exercise where employees are sent random phishing emails to see if they click on links or attachments provides valuable feedback to both the IT department and the employees. A contest amongst employees to see who can spot the most phishing emails (by forwarding them to an alias) puts some friendly competition into the mix while providing a valuable exercise. Rewards can be simple gift cards or a more complex points program which can be redeemed for prizes. Similar activities can target mobile devices or laptops by asking employees to download unauthorized software.

Peter J. Canavan
- Social engineering attacks are the most insidious. You must educate and train your employees on what phishing attack emails may look like including official-looking logos, a sense of urgency, the need to wire funds or check account or package tracking information immediately. By hovering over the links in a message and noting the URL that appears, many of these phishing attacks can be thwarted. When in doubt, look up the company’s phone number or customer support email on your own and do not rely on the contact information in the email to ascertain validity. However, more and more various websites are hacked, and code installed on them that the site owner is unaware of. Just visiting a compromised site can allow malware to get into your systems.
- A great exercise is to have your employees try to spot fake vs. valid emails and to make a game out of it. Divide employees into teams, and then have them mark which emails are legitimate and which are not. The winning team gets a prize (lunch, leave work early, PTO time, etc.)
- Passwords are one of the easiest places to gain entry into a system. Stress the need for strong password security. Use passwords that are LONGER and not necessarily complex. Any password that is 12 characters or longer is almost uncrackable. It would take too much time for a computer/hacker to crack it. Teach them to use easy to use phrases as passwords such as turning vacation time in Aruba into Vaca710n71m31nAruba! which makes an easy-to-remember phrase into a super strong 20 character password.
- Drill into your employees the need to be vigilant and not complacent. Just because they (or your company) have not been hacked before, does not mean it cannot happen. A recent survey by the National Small Business Association found that 50% of businesses they surveyed had reported being victims of cyber attacks, and 3 out of 4 were small businesses with less than 250 employees. The average cost of a cyber attack is around $21,000, and within six months, 60% of those attacked go out of business. Let your employees know that if they want job security, they need to help contribute to your company’s security!
- The apparent need for a robust and centrally managed antivirus solution on all your servers and workstations is a must. Besides, your router’s firewall must be hardened by an expert who knows exactly what the best practices are. Having a solution that combines the two is an excellent option for small businesses.

Robert Huber
Robert Huber, CSO, Eastwind Networks
Eastwind Networks is a cloud-based breach analytics solution that aims to protect government agencies and enterprise organizations from cyber threats that bypass traditional security measures.
- Ensure cybersecurity is a part of every employee’s performance goals.
- Gamify the security awareness training program, so there are points amassed, a leaderboard or prizes.
- Ensure the situations reflect real-life concerns of the enterprise. Rather than using generic scenarios, show how a loss of control, loss of personal information, loss of client sensitive information, intellectual property or similar related to the business affects the bottom line, company profits, reputation, stock price, etc.

Benjamin Dynkin
Benjamin is a cybersecurity attorney specializing in helping businesses understand, manage, and mitigate their cyber risk. He has published extensively and has been featured in a TEDx on cybersecurity and cyberwarfare.
Information security awareness requires hardening the human element
While there are countless strategies for making a data security program useful, to transform a compliance checkbox into a strong security posture.
- Security Awareness training should be a constant presence in the lives of employees. To be effective, a program cannot merely be a quarterly, semiannual, or annual gathering of employees to be lectured on not clicking a link. Instead, it is essential to create an iterative and dynamic process that tests employee through various types of cybersecurity attack vectors, pair that with general education, and finally, to develop specific interventions for ‘habitual clickers’ and other weak links in the organization.
- In the same spirit as the previous tip, small nuggets of knowledge dolled out regularly are far more effective than drawn out lengthy presentations that are spaced over time. 2-3 minute refreshers or targeted lessons with a specific purpose (risk of phishing, operational security, specific compliance issues, etc.) are far more effective than lumping everything together into a single hour-long (or often longer) session.
- Gamification. The average person is more interested in clicking a link than protecting their company from abstract threats. Thus it is vital for a cybersecurity awareness program to change that dynamic. One of the most useful tools for doing that is gamifying security awareness programs. Gamification refers to the process of turning a mundane task into a game. How to gamify security awareness training is a question that involves creativity and an understanding of the employees of the organization. Depending on the scale of the organization and the resources available, gamification can be something as simple as publicly calling out good acts of security awareness such as reporting a phishing link or completing a training course. For a more intricate and involved solution, an organization can create a public point system that rewards proper conduct and punishes poor practice. The company can give rewards and other benefits to top scorers while hoping that poor performers are encouraged to step up their training.

Eric Sheridan
Chief Scientist, WhiteHat Security
As the Chief Scientist of the Static Code Analysis division at WhiteHat Security, Eric oversees all research and development for Sentinel Source and related products, defining and driving the underlying technology.
The pace of change within and outside of an organization is staggering. Many businesses are in the process of digital transformation where applications and the APIs that connect them are becoming the digital fabric connecting the world. No longer is it taking months or years to build out IT infrastructure and applications. In many businesses today, it might be just a matter of days or hours. We have customers who are pushing application updates multiple times a day.
Cybercriminals are staying on top of this change too, evolving their capabilities at a similar pace. Organizations and individuals must be vigilant when it comes to security education and training, and security vendors need to make it as easy as possible for businesses and consumers to get the training and education they need to stay current on potential cyber threats.
To stay ahead of security risks, here are the top three practices to put in place:
- Enroll in Training Programs: People’s understanding of Security generally falls in two buckets: either the person is uninformed, or the person is informed but their knowledge quickly goes stale. A big part of thwarting attacks is to keep the team trained. There are training programs, some even free such as the WhiteHat Certified Developer Program, that can add to a company’s training and education arsenal and help both security teams and IT/development teams learn valuable secure coding skills and how to secure applications through the entire software development lifecycle.
- Phishing Training: People rely on emails and websites to function on a day-to-day basis, and phishing continues to be an effective means of victimizing users. According to the Verizon Data Breach Investigations Report, 30 percent of phishing messages were opened, and around 12 percent then actually clicked the malicious link or attachment. The best phishing attacks target something that you rely on, whether it be online banking, email or credit cards. Continued education and possibly warnings before executing the links are the best way to combat phishing attacks. Two-factor authentication is a great barrier for anyone attempting to hijack your account. Not only will an attacker need to compromise your username and password, but they will also need to compromise a device as well.
- Security in Context: Covering general security topics will only go so far. Optimal training programs provide curriculums that are tailored to the roles and responsibilities of the individual partaking in the curriculum. By way of example, Software Engineers need to have an understanding of the security implications of clicking an untrusted link, and they must also have an understanding of the security implications of building SQL queries at runtime using user-data.

Mike Meikle
Partner, SecureHIM
Mike Meikle is a Partner at secureHIM, a security consulting and education company that provides cybersecurity training for clients on topics such as data privacy and how to minimize the risk of data breaches.
Companies should include information on general security threats, how hackers compromise systems (social engineering, malware, etc.), top hacker targets (Facebook, Twitter, LinkedIn), defense techniques, an overview of the hacking ecosystem, and the cost of lost data to the organization.
Initially, training should be done in-person with a presenter. A slide presentation with topics that highlight how hackers affect the specific organization’s industry should be included. Live websites and video should be used to keep the audience engaged.
Follow-up security awareness presentation can be via a recorded webinar that is updated to reflect the changing threat landscape. After the recorded session there should be a quiz to measure how effective the presentation was with the target employees.
Also, the Information Security group can send out regular email blasts on threats and create a monthly newsletter or blog to keep security in the forefront of employee’s minds.
The best way for organizations to protect their data and keep their employees from compromising security is to train them on information security best practices. This must be done on a continual basis, in layman’s terms and at a minimum of six-month intervals. Sixty to seventy percent of data breaches are due to social engineering and hardware theft; an issue best addressed by training.
If an organization keeps the issue of information security in front of employees, makes it engaging and keeps the organization informed on how threats are impacting the company, then the employees with have a reference point on how their behavior is or could impact the company.
People love hacker stories. As part of our business we handle data breaches for companies, so we have plenty of stories on how hackers broke into organizations and what they did once inside the network. Many of these stories are relatable and get people interested in the topic. Often we will have 2-3 hacker stories in a briefing to introduce better security practices or ideas.
People like to talk about themselves. I make sure that I provide plenty of time for people to ask questions about their personal cybersecurity concerns related to their email, social media and smartphone use. The concerns that are typically expressed by one person in the group are usually shared by others and always leads to lively discussion and better training.

Joshua Feinberg
President, Data Center Sales & Marketing Institute
Joshua Feinberg is a digital strategist and revenue growth consultant, specializing in the data center, mission-critical, and cloud services industries. He is also a president of the Data Center Sales & Marketing Institute.
- Avoid cyber security courses where IT teams are scolding employees for being careless about their use of IT assets. While the 1990’s SNL skit with Jimmy Fallon (Nick Burns, Your company’s computer guy) is sure to be an excellent icebreaker for what your IT team shouldn’t be acting like, it’s far better to infuse a tip or two into other company meetings that employees want to attend.
- Use stories/videos to drive home the point. A few minutes on YouTube, looking for current events about breaches should yield plenty of 2-5 minute videos worth watching. For example, it’s widely known that a very high-ranking 2016 U.S. presidential campaign manager was compromised over essentially not having two-factor authentication turned on. (which brings me to my next point)
- Accept that shadow IT exists and provide department/application-specific advice. For example, show what should be done in settings to protect against the basics: turning on two-factor authentication, enforcing strong passwords, and forcing SSL usage in webapps. A tech-savvy power user in finance or marketing can often be a great person for your IT team to partner with on these efforts.
- Point out the dangers of public WiFi and why VPN software is so critical. Anyone with young kids, or who remembers being a kid, can relate to the telephone game, where you whispered in your friend’s ear to reveal a secret. This is an excellent analogy for this topic.

Larry Kahm
President, Heliotropic Systems, Inc.
Larry Kahm is president and owner of Heliotropic Systems, an IT provider for small businesses and entrepreneurs, located in Fort Lee, NJ. He has clients throughout eastern Bergen County, New York City, and Long Island.
Some general “rules of thumb” about emails that ask you to pay for invoices or to send out financial or client data:
- The same rule as you would use for a phishing email: Be very skeptical.
- If you have an admin handling your mail, make sure they ASK directly, or by phone or text, before they take any action.
- If the email is from someone you know, call them to double-check.
- If the email is from someone you do not know – do NOT call them. It is likely that they will try to use social engineering to convince you to send it.
- Do NOT send attachments if you do not know who requested them
- If you are at all uncertain about the email’s legitimacy, delete it. If someone really and truly needs something – they will get back to you!
I realize that this last one flies in the face of all social contracts. But each of you has to weigh how much you value your businesses’ security program over some possibly ruffled feathers.

Tom DeSot
EVP and CIO, Digital Defense, Inc.
As chief information officer, Tom is charged with key industry and market regulator relationships, public speaking initiatives, key integration and service partnerships, and regulatory compliance matters. Additionally, Tom serves as the company’s internal auditor on security-related matters.
Build A Powerful In House Defense Against Cybercrime
- Arm employees with the required knowledge to thwart information security intrusions designed to help train, educate and reinforce a security-aware employee base.
- Use All Tools Available to Fight Hackers – Kick off a new way of training and create maximum excitement and support by leveraging a fun and enjoyable staff security awareness program.
- Improve Your Team’s Security IQ – Easily deploy fun and engaging animated videos to all employees regardless of keeping security awareness top of mind. Easy and convenient, these videos will be accessible from multiple platforms (PC, laptop, iPad/tablet or mobile device).

- Employees need to be educated on what a phishing email looks like and why they are BAD. We do this by sending out test phishing emails and track which employees click on the link in the test email, and then we can educate that employee on a personal level.
- Another great tip is to not use or connect your devices to public WIFI. (i.e., hotels, airports, Starbucks, etc.) use your phone’s hotspot, so you are not allowing other devices to view your network access.
- Sessions are often boring wastes of time, both for employees and the IT teams responsible for them. How do you avoid this? – Whether we are educating our clients or presenting at a cyber security conference, we always do 2 things to make the event not a boring waste of time 1.) FOOD – we always have food and provide catering at our events and 2.) Giveaway gift cards throughout the presentation and at the end. Ask questions to get audience participation and give away $$. The bottom line on cybersecurity and reducing your risk is TRAINING/EDUCATION. You have to make it a priority to educate your employees.
Justin Lavelle
Chief Communications Officer, BeenVerified
BeenVerified is a leading source of online background checks and contact information. It allows individuals to find more information about people, phone numbers, email addresses, property records, and criminal records in a way that’s fast, easy, and affordable.
Start an Employee Security Awareness Program ASAP
The secret sauce for cybersecurity is focusing on two simple things – Talk about it and think about it. The reality is that dealing with security is a business issue (not an IT issue) and it involves hundreds of little things (usually not expensive or time-consuming) and not just the several big things you think you need to be doing (which can be costly and time-consuming).
Talk about it. We have found great success just getting people in the same room and telling stories. Call it a lunch and learn or do it in the afternoon and call it a snack and learn. The company buys some food, and everyone has to show up. Takes an hour or less and have someone come prepared with some best practices and stories of how people have made poor security decisions (we play this part for our clients). It is amazingly powerful seeing one employee explain how they got a phishing email and how they fell for it and say how they avoid it in the future and then hearing weeks later that someone else in the room saw the same thing but were not a victim because they listened to that story. It is super simple and really works. Just talk about it.
Think about it. Most people do not want to bother thinking about security. It is easier to turn a blind eye and think nothing bad will ever happen to you. All the business person needs to do is to make a conscious effort to think about security. Ask their IT for information about their business applications and such – manage who has access with privileged access management, what rights do users have, what is the password policy (complex and expire after X months), should you be using MFA (Multifactor Authentication), reports for antivirus and software updates, etc. Also think about if there are any concerns with other business areas – physical access control, third parties like banks, etc. Think about it and you will be more secure.

Robert Siciliano
Identity Theft Expert with HotSpot Shield
Train your staff and test your employees
- After presenting information about security awareness, come up with a scheme to set up a situation where employees are given the opportunity to open a very alluring link in their email. This is called a “phishing simulation.” This link will actually take the worker to a safe page, but you must make the page have a message, such as “You Fell For It.” You should also make sure that these emails look like a phishing email, such as adding a misspelling. The people who fall for this trick should be tested again in a few days or weeks. This way, you will know if they got the message or not.
- Do not make it predictable as to when you are giving out these tests. Offer them at different times of day and make sure that the email type changes.
- Consider hiring a professional who will attempt to get your staff to hand over sensitive business information over the phone, in person, and via email. This test could be invaluable, as it will clue you into who is falling for this.
- Quiz your staff throughout the year, to allow you to see who is paying attention. You want to focus on educating your staff, not disciplining them. They should not feel bad about themselves, but they should be made aware of these mistakes.
- Make sure your staff knows any data breach could result in legal, financial or criminal repercussions.
- Schedule workstation checks to see if employees are doing things that might compromise your business’ data, such as leaving sensitive information on the screen and walking away. Explain how important security is to your business and encourage staff to report any suspicious activity.
Amanda Bigley
Marketing Associate, Hummingbird Networks
Amanda Bigley is a marketing associate for Hummingbird Networks. She enjoys researching and writing about all things cybersecurity.
- Make a game out of it. Provide your employees with security basics of identifying social engineering through a quick read or cheat sheet and then incentivize them to put their knowledge to the test. Consider something like a department-wide game of Jeopardy. This method eliminates the boring lecture and boosts employee morale.
- Train employees as they come. Create material for training employees as they join the company. This will eventually cancel out the need for a large group training and ensure employees are properly vetted from day one. A quarterly quiz could help ensure their cybersecurity knowledge stays fresh and relevant.
- Create entertaining literature. Using the good old ambient marketing method, consider printing bathroom literature that provides employees with some easily consumable content. Taking a humorous tone, inform employees of current cybersecurity risks and tips, or company security news with a weekly, bi-monthly or monthly print which is then displayed on the back of stall doors. Create a simple template that requires little time to update with new info.

Isaac Kohen
Founder and CEO, Teramind
Isaac Kohen is the founder and CEO of Teramind, an employee monitoring, insider threat prevention platform that detects, records, and prevents malicious user behavior.
Cybersecurity awareness sessions for employees can often be boring wastes of time.
Combat the snooze fest of employee education sessions by making them engaging. This can be done by making the courses relatable. Create cybersecurity scenarios that employees can easily understand.
Utilize games, trends, gifs, memes, etc. whatever you need to convey your cybersecurity message. Understand your environment and hone in on whatever applies to your employees. You can easily incorporate funny and relatable scenarios to keep your employees attention all while helping them understand why cybersecurity is vital.
Recent Posts
11 Enterprise Password Management Solutions For Corporate Cybersecurity
Let’s set a scene: It is a Monday morning, and you have just sat down at your office workstation after a long and relaxing weekend.
Coffee in-hand and you are ready to take on the week, only to realize you have been mysteriously locked out of all your accounts.
Did the system administrator push a password refresh? Did you accidentally knock out a LAN cable?
That pit in your stomach and sweat on your brow is how it feels when you suddenly realize your passwords have been stolen or compromised.
Who has access to your information, your accounts, your data? Even worse; how did they get through your security?
In the age of widespread identity theft, security breaches, and corporate espionage, password protection is essential to your digital security. The use of enterprise password management software is becoming a required element in any IT organization.
60% of small-to-medium size companies suffer a from cyber-attack at some point. According to the National Cyber Security Alliance, most close down only six months after an attack.
What is a Password Manager?
Password managers are designed to manage a user’s personal details securely. We all enter our information online, whether it is a bank account login, our social security number, or an e-mail password. Most users have dozens of accounts. Team members in business may have hundreds. All of them protected by usernames and their accompanying passwords.
Remembering all those details can be near-impossible – because we are all using different passwords for each account, right?
Password managers take the burden of remembering each login off the user. The majority of these services are low-cost or free, targeting, and meeting the needs of a single consumer.
They run discreetly in the background. Upon creating or using a new account for the first time, the user receives a prompt. The prompt will most often ask the user to save the password. Once collected, details are logged and held in a “vault.” The password vault manager encrypts all data.
Most managers also can recognize duplicate and weak passwords. If it registers as such, they prompt the user to either create a stronger one or to generate a stronger key randomly.
Why You Need Enterprise Password Management?
The average consumer-level password is enough for the needs of a single user. However, the enterprise world has much higher standards for security.
IT staff need a central point of collection, or a team password manager should a user lose access. Admins must also be able to manage details for shared accounts and to set and revoke permissions. Moreover, enterprise-level managers can store all kinds of data, not just login details. Some options store files of all format types.
The right software can lift much of the burden that server admins endure. Those running an IT system often deal with regular interruptions. Members of the team forget passwords and a simple password reset. Corporate password managers perform many of these functions automatically.

Dangers of Leaving Password Management to Employees
Allowing users to choose their private passwords and management software can be a minefield.
One device can have access to hundreds of account passwords. Users need strong passwords for everything from Twitter to Hootsuite to LinkedIn to MailChimp, and so on. Without a firm, centralized approach to password storage and security, users must find their own means.
Allowing users to decide how to implement password protocol can also be dangerous.
In many cases, team members will use insecure methods such as using .doc files, Excel spreadsheets, or even a post-it note on the front of their screen to store details. The risk of having passwords stolen from such unprotected mediums is much higher than using the right software.
Other employees may instead choose to use their own personal software. Management may see this as a way to ensure protection without added cost.
Single users do not have access management to group passwords, however. Nor do they always set standards for passwords that match company protocol. In the future, they could leave the company with corporate login details still in their accounts. Naturally, these are valid security concerns. Best practices are critical.
Enterprise Software Features to Look For In a Password Management Solution
Enterprise software enables the separation of personal, single-use accounts and shared details.
One of the best features of enterprise password managers is access to central dashboards. These dashboards allow security officers to check user activity and aggregate data. Many include visualization tools that make it easier to monitor behavior and security practices.
Studying user habits can help reinforce and improve your companies password practices.

Let’s look at the best password management software for an enterprise on the market.
We will highlight criteria to help you better judge different platforms. These include what operating systems and hardware the software is compatible with, price, security, features, and ease-of-use.
LastPass Enterprise
A premium edition for businesses based on the well known free software. LastPass lets the user generate and store any number of logins in a master vault. Multi-factor or two-factor authentication limits access to the vault.
Besides passwords, the vault offers protection of additional text notes. Secure data syncing allows users to retain the same credentials and security between different platforms. Users can access the vault on any device through the developer’s website.
LastPass also uses a growing database of phishing websites. By highlighting such, users are less likely to leak access to privileged accounts. Admins can also export encrypted data. Exporting makes it easy to switch to another software option down the line if you choose to.
The premium edition offers further cloud protection for all kinds of files. The contingency access feature lets a team member use your account when you are unable to. Without additional support for shared accounts, however, LastPass might not be best suited to large teams.
Dashlane
Dashlane offers many of the same features as LastPass with its enterprise edition. Team account management software is now available on an accessible browser window interface. Some may prefer the downloadable software package, which is equally easy to use.
Active Directory integration makes it easy to share Dashlane through your business network. One of the better resources offered is the bulk password changer. This feature allows you to quickly change large amounts of data in the event of a breach.
Conversely, Dashlane is high in price compared to some of the other solutions here. It may not be an option every business can afford. This edition includes unlimited sharing and syncing between teams and devices. It was rated as the most secure password manager.
Keeper Security
A mobile-centric alternative to other platforms, Keeper Security for Business, operates on a wide range of platforms with a particular focus on responsive design. Like LastPass and Dashlane, it offers a secure vault that stores all kinds of files, not just passwords.
One of the benefits of Keeper Security is the vast range of platforms it works across. The software has versions for Android, iOS, Blackberry, Kindle, iPad, Windows, Mac, and Linux. The centralized vault allows access management to the same credentials across all platforms.
Keeper Security comes with Active Directory integration and an admin control panel. Amongst other features, the panel allows for the fast provisioning of users. Access to specific passwords is easily distributed and revoked.

Centrify Enterprise
This option contains many of the same features you can come to expect from most password managers. These features include autofill, password capture, and password generation. Centrify is one of the most useful tools for capturing and monitoring data cross accounts, too.
Centrify tracks a lot of user data. Data tracking includes logs of the number of attempted logins, valid log-ins, and unusual activity.
Admins can generate reports on each user session. The summary collates all data of activity across a whole enterprise. Centrify has the further ability to separate reports based on different roles. This makes it a worthwhile tool for inspecting security practices company-wide.
CommonKey | Team Password Manager
CommonKey is an affordable solution for smaller businesses. It focuses on password protection alone, lacking the secure data storage features available elsewhere. Shared accounts and user provisioning tools are also included.
It is limited by the platforms you can use it on. CommonKey runs as a Chrome security extension. As a result, it’s only useful when used with websites and services. Passwords for local software cannot be saved.
The local encryption used by the application could be a risk, too. Certain breaches could allow hackers to see encryption methods and break them. Effectively, such a leak would expose all your details.
Larger businesses with more robust password needs may want to search for alternatives. For smaller teams that rely on websites and web applications, however, it can be a reliable tool.
RoboForm For Business
RoboForm for Business allows for centralized protection of an entire team. It includes a site license that stores and manages all passwords used in the company.
RoboForm includes secure provisioning of shared passwords. An admin console allows for easy management of different users.
You can manage users as individuals or as members of role-based groups. Role-grouping saves a lot of time when dealing with larger departments. Advanced reporting allows admins to ensure that users comply with company policy, too.
Pleasant Password Server
One of the few open-source password managers on the market. Pleasant password server lets tech-savvy users fully customize their approach to improve password security. Like many enterprise editions, it includes active directory integration.
Unlike other managers, the encryption and storage of sensitive data do not happen locally. Passwords stored on the client are kept safe in the event of a local data breach.
A refined folder system allows for simple grouping of large amounts of data. Admins can use this data to create reports that work with shared accounts and role-based management. It can generate reports including evaluating password age, strength, expiration, and more.

BeyondTrust
BeyondTrust Privileged Password Management includes powerful data tools on top of the standard features. Session-logging and auditing offer greater monitoring of security practices across the team.
Active Directory and LDAP integration enable the automatic provisioning of users. The management features work with local appliances using government-level security. It’s not just a tool for websites and web applications.
BeyondTrust has one of the most complex and detailed reporting modules on the market. Included, is the ability to track login attempts and session activity across the whole team. In the event of a breach attempt, you can use these reports to ensure regulatory compliance.
ManageEngine
One of the most popular enterprise-level password security programs. The pro password management of ManageEngine includes options to enable multiple admins. Using this option does increase the price of the package, however.
Data sync and Active Directory integration streamline management of multiple accounts. While it doesn’t work with mobile devices, it does include further forensic tools. Chief amongst them is the compliance report generation feature and video logs of sessions. This makes it one of the best tools for inspecting the security practices of your team members.
ZohoVault Online Password Manager For Teams
This software works solely with mobile devices. It sounds limiting, but ZohoVault does bring a surprising depth of features to its platform.
Included, are administrator access and management of user groups as well as smooth password transferal. It allows for the creation of reports on user activity and even allows more in-depth provisioning tools. As well as limiting access by specific users, admins can restrict access by IP address. If your concerned team members use unauthorized devices to access passwords, you can block them.
Zoho works as more than a standalone centralized manager for mobile devices. It also integrates with other password managers like LastPass. A company can use Zoho to extend existing enterprise password management to mobile devices effectively. On top of that, this is one of the cheapest solutions on the list.
1Password Business
Popular consumer software, 1Password from AgileBits may not be full enterprise at the moment, but they are one to keep on your radar. Recently, they expanded their popular subscription-based service for larger teams (replacing the existing, Teams Pro service).
1Password Business provides the features you need as a larger team. It gives you the tools to protect your employees, secure your most important data, and stay compliant. Your administrators will love it for the control it provides them, and your employees will love how easy it is to use,” writes AgileBits in an introductory blog for the product.
AgileBits introduced subscription pricing in 2016, moving away from licensed-based pricing. This may be a deterrent for some businesses, though depending on the size of your company, it could end up being more cost-effective in the long-run.
While 1Password is still geared toward smaller businesses or group users, the new Business plan offers enhanced customer support; more per person document storage; and a more significant number of guest accounts. Worth keeping an eye on in your consideration process.

Choosing the Best Enterprise Password Solution
Unauthorized use of passwords is the most common method of entry in recent data breaches.
All of the options listed above have a reputation for high-security standards. Do not forget, the centralization of your password management is crucial. The solution you choose depends on the needs of your organization.
Recent Posts
What is Object Storage? How it Protects Data
Object storage architecture inherently provides an extra security layer for your data. As such, it can be an ideal solution to avoid ransomware threats.
First, let’s start with explaining the differences between traditional storage solutions and object storage.
Object storage vs. Block Storage
With traditional block and file storage, information is typically stored in file systems that allow you to locate each item by following the defined path to that file.
If you need to share data among a group of users through a network, it is best to do so over network-attached storage (NAS). This will work great on a local architecture network (LAN) but might not be so great via wide area network (WAN).
While managing several NAS boxes is not that hard; doing so with hundreds of boxes makes things difficult. When the number of files and users grows substantially, it takes a lot of time and effort to find a particular file. In addition to this, you might even reach your storage file-limit sooner than expected.
Traditional storage was not designed for terabytes of data, so there is a good chance of data loss in the first two years.
Prominent characteristics of traditional storage include:
- Files are shared via NAS or SAN
- Each edit deletes the previous version of that file, and it cannot be restored on the device
- Connecting NAS boxes for scaling
- A file system is located by following its destination path
- Initially, it is straightforward to set up
- Configured with standard file level protocols, like NTFS, NFS, etc.
When talking about cost-considerations, you need to plan your requirements over time carefully. Having too much storage means you will pay for resources you do not need. On the other hand, not having any buffer room might put you in a tight spot when faced with no storage space.
Ransomware was explicitly created to take advantage of the shortcomings of block-and-file storage by encrypting files and locking out users.
Malicious software can even circumvent a volume snapshot service (VSS). That means that you would not be able to recover shadow versions either.
How Object Storage Works
Object storage creates immutable sets of data. It includes versioning and elaborate geo-diverse data replication schemes.
When I say immutable, I mean that data cannot be modified once created. To further clarify, it can be modified, but each edit is saved as a new version.
Object Storage uses flat-file data architecture and stores data in unchangeable containers or so-called buckets. Data, along with its metadata and unique ID, is bundled up in objects.
IT admins gain more control over their objects by assigning a virtually unlimited number of metadata fields. This is an inherent advantage over traditional storage. Thanks to metadata and the unique identifier that lets you locate objects easily, object storage works perfectly for unstructured data such as 4K videos, medical archives, or other large files.
Due to its lack of data hierarchy, object storage features scalability which could not have ever been achieved with block storage.
Advantages of object storage include:
- Continually scalable without any significant performance degradation
- Perfect for high volumes and large files
- Safer thanks to immutable data
- Capable of versioning
- Features replication schemes
- Good at maintaining data integrity
- Cost-effective
- Excellent for dealing with ransomware
- Perfect for file-sharing
- Unparalleled when it comes to metadata
This may sound like object storage is the best thing ever. However, the truth is that this approach is quite specific and not a good fit for every use case.
For example, object storage does not work well for frequently modified data, as there is no guarantee that a GET request will return the most recent version of the object. Furthermore, since objects are accessed via REST API, you may need to do a little bit of coding to make direct REST-based calls.
Even if it is not a one-fits-all solution, object storage does address problems that cannot be solved efficiently with traditional storage.
Object storage is perfect for:

1. Big Data
Big data is a huge (no pun intended) part of 21st century IT. It provides an answer to the ever-growing demand for more storage. In most cases, big data is unstructured and varies in the file type.
Let’s take for example Facebook and the social media phenomenon. This is a relatively new and non-traditional source of data that are being processed by analytics apps. The results are massive amounts of unstructured data. In such conditions, an object storage environment offers the necessary scalability, security, and accessibility.
2. Creating Backup Copies
I cannot stress enough the fact that it is an excellent fit for frequently used, but seldom modified data.
If you are not using a supported backup utility, such as Veeam Cloud Connect of R1Soft, you can leverage object storage for backing up your data. To do this, you would need to use the right cloud backup solution or software, such as Cloudberry Backup.
3. Archives
An archive is not the same as a backup. Backups are files that are very rarely used, and we turn to backups only if something goes wrong. Archives are similar but serve a different purpose.
Compared to backups, archives are accessed more frequently and serve to store and quickly obtain large quantities of data. Businesses with various backgrounds may store medical files in the cloud, engineering documents, videos, and other unstructured data.
After a while, it may become increasingly difficult to find an individual file, not to mention secure all data. However, with object storage IT admins can quickly secure and maintain data integrity, all the while providing easy access.
4. Media & Entertainment
It has never been easier to share information, whether you are on the receiving or giving end. However, nobody seems to think about the resources necessary to store such vast amounts of unstructured data. S3 object storage is especially useful for this use case, as it is easy to build entire front-facing apps based on its API. Perfect for media & entertainment.
5. Hosting a Static Website
Object storage has a suitable architecture for hosting static websites thanks to its virtually infinite scalability. This means it will scale automatically to your traffic needs.
Public users will access your data via the web, just like with any other hosted website. However, it must be noted that no personalized data can be displayed based on cookies and there is no support for server-side scripting. So, there are some limitations.
6. Streaming Services
With the emergence of online video streaming services and the internet becoming globally available, keeping chunks of data in a single location no longer makes much sense. You need fast global access, unlimited storage (a 1h raw 4k video can take as much as 130GB!), scalability, durability, and excellent metadata management.
Object storage technology ticks all the right checkboxes, and it helps that it was built for HTTPS. The best thing is that you can use object storage for several use cases at the same time.
Ransomware, the Role That Object Storage Vendors Can Play
Official statistics claim that ransomware took in $209 million in 2016 alone, while the cost of downtime was even higher. Datto’s report found that 48% of businesses lost critical data when faced with such threats. This is a loss that cannot be easily measured in dollars.
In 2018, ransomware continued to dominate the world of cybersecurity. 6 out of 10 malware payloads in Q1 were ransomware. From WannaCry to NotPetya and BadRabbit, we can safely say that ransomware threats have marked the year behind us. Furthermore, we can safely assume that ransomware has become the biggest security threat any organization or individual may face in the cyber realm.
Recent Posts
Cyber Tragedy: 5 Stages of Business Deterioration after a Data Breach
A cyber-attack may only last for a few hours, but what do you do afterward?