8 Types of Firewalls: Guide For IT Security Pros
Are you searching for the right firewall setup to protect your business from potential threats?
Understanding how firewalls work helps you decide on the best solution. This article explains the types of firewalls, allowing you to make an educated choice.
What is a Firewall?
A firewall is a security device that monitors network traffic. It protects the internal network by filtering incoming and outgoing traffic based on a set of established rules. Setting up a firewall is the simplest way of adding a security layer between a system and malicious attacks.
How Does a Firewall Work?
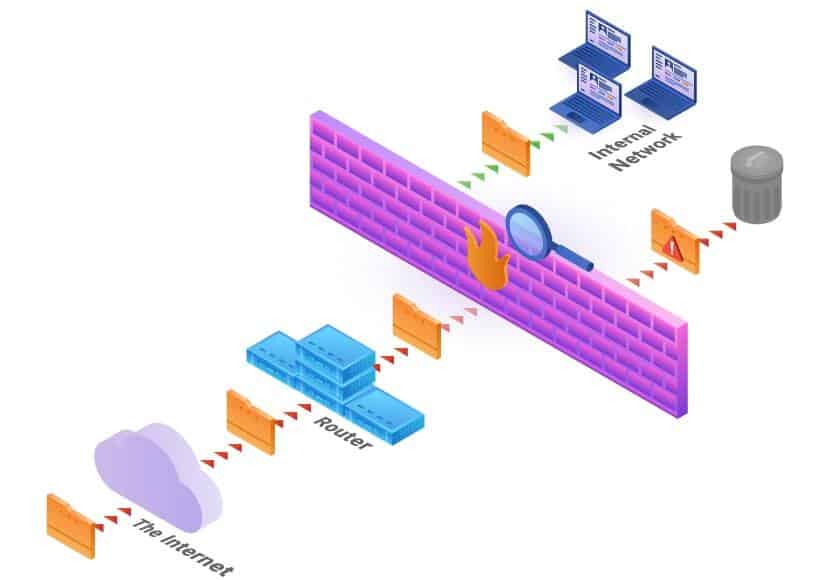
A firewall is placed on the hardware or software level of a system to secure it from malicious traffic. Depending on the setup, it can protect a single machine or a whole network of computers. The device inspects incoming and outgoing traffic according to predefined rules.
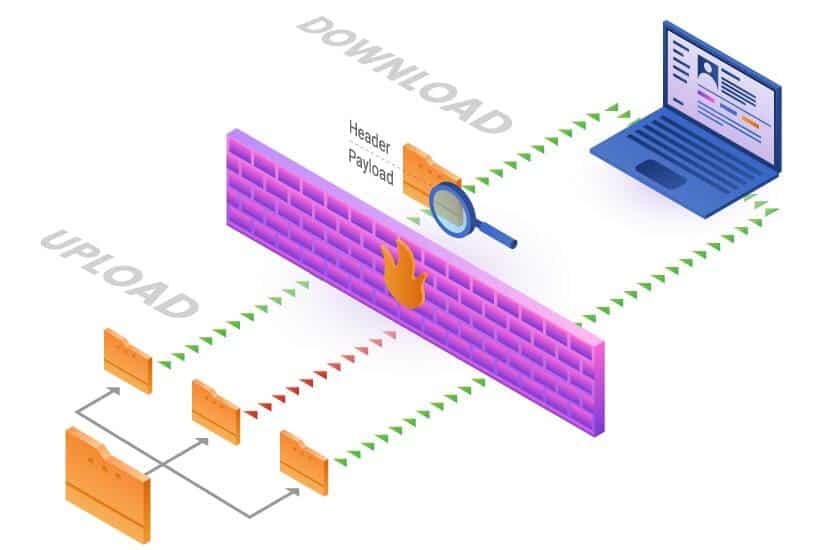
Communicating over the Internet is conducted by requesting and transmitting data from a sender to a receiver. Since data cannot be sent as a whole, it is broken up into manageable data packets that make up the initially transmitted entity. The role of a firewall is to examine data packets traveling to and from the host.
What does a firewall inspect? Each data packet consists of a header (control information) and payload (the actual data). The header provides information about the sender and the receiver. Before the packet can enter the internal network through the defined port, it must pass through the firewall. This transfer depends on the information it carries and how it corresponds to the predefined rules.
For example, the firewall can have a rule that excludes traffic coming from a specified IP address. If it receives data packets with that IP address in the header, the firewall denies access. Similarly, a firewall can deny access to anyone except the defined trusted sources. There are numerous ways to configure this security device. The extent to which it protects the system at hand depends on the type of firewall.
Types of Firewalls
Although they all serve to prevent unauthorized access, the operation methods and overall structure of firewalls can be quite diverse. According to their structure, there are three types of firewalls – software firewalls, hardware firewalls, or both. The remaining types of firewalls specified in this list are firewall techniques which can be set up as software or hardware.
Software Firewalls
A software firewall is installed on the host device. Accordingly, this type of firewall is also known as a Host Firewall. Since it is attached to a specific device, it has to utilize its resources to work. Therefore, it is inevitable for it to use up some of the system’s RAM and CPU.
If there are multiple devices, you need to install the software on each device. Since it needs to be compatible with the host, it requires individual configuration for each. Hence, the main disadvantage is the time and knowledge needed to administrate and manage firewalls for each device.
On the other hand, the advantage of software firewalls is that they can distinguish between programs while filtering incoming and outgoing traffic. Hence, they can deny access to one program while allowing access to another.
Hardware Firewalls
As the name suggests, hardware firewalls are security devices that represent a separate piece of hardware placed between an internal and external network (the Internet). This type is also known as an Appliance Firewall.
Unlike a software firewall, a hardware firewall has its resources and doesn’t consume any CPU or RAM from the host devices. It is a physical appliance that serves as a gateway for traffic passing to and from an internal network.
They are used by medium and large organizations that have multiple computers working inside the same network. Utilizing hardware firewalls in such cases is more practical than installing individual software on each device. Configuring and managing a hardware firewall requires knowledge and skill, so make sure there is a skilled team to take on this responsibility.
Packet-Filtering Firewalls
When it comes to types of firewalls based on their method of operation, the most basic type is the packet-filtering firewall. It serves as an inline security checkpoint attached to a router or switch. As the name suggests, it monitors network traffic by filtering incoming packets according to the information they carry.
As explained above, each data packet consists of a header and the data it transmits. This type of firewall decides whether a packet is allowed or denied access based on the header information. To do so, it inspects the protocol, source IP address, destination IP, source port, and destination port. Depending on how the numbers match the access control list (rules defining wanted/unwanted traffic), the packets are passed on or dropped.
If a data packet doesn’t match all the required rules, it won’t be allowed to reach the system.
A packet-filtering firewall is a fast solution that doesn’t require a lot of resources. However, it isn’t the safest. Although it inspects the header information, it doesn’t check the data (payload) itself. Because malware can also be found in this section of the data packet, the packet-filtering firewall is not the best option for strong system security.
***This table is scrollable horizontally.
| PACKET-FILTERING FIREWALLS | |||
| Advantages | Disadvantages | Protection Level | Who is it for: |
| – Fast and efficient for filtering headers.
– Don’t use up a lot of resources. – Low cost. |
– No payload check.
– Vulnerable to IP spoofing. – Cannot filter application layer protocols. – No user authentication. |
– Not very secure as they don’t check the packet payload. | – A cost-efficient solution to protect devices within an internal network.
– A means of isolating traffic internally between different departments. |
Circuit-Level Gateways
Circuit-level gateways are a type of firewall that work at the session layer of the OSI model, observing TCP (Transmission Control Protocol) connections and sessions. Their primary function is to ensure the established connections are safe.
In most cases, circuit-level firewalls are built into some type of software or an already existing firewall.
Like pocket-filtering firewalls, they don’t inspect the actual data but rather the information about the transaction. Additionally, circuit-level gateways are practical, simple to set up, and don’t require a separate proxy server.
***This table is scrollable horizontally.
|
CIRCUIT-LEVEL GATEWAYS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Resource and cost-efficient.
– Provide data hiding and protect against address exposure. – Check TCP handshakes. |
– No content filtering.
– No application layer security. – Require software modifications. |
– Moderate protection level (higher than packet filtering, but not completely efficient since there is no content filtering). | – They should not be used as a stand-alone solution.
– They are often used with application-layer gateways. |
Stateful Inspection Firewalls
A stateful inspection firewall keeps track of the state of a connection by monitoring the TCP 3-way handshake. This allows it to keep track of the entire connection – from start to end – permitting only expected return traffic inbound.
When starting a connection and requesting data, the stateful inspection builds a database (state table) and stores the connection information. In the state table, it notes the source IP, source port, destination IP, and destination port for each connection. Using the stateful inspection method, it dynamically creates firewall rules to allow anticipated traffic.
This type of firewall is used as additional security. It enforces more checks and is safer compared to stateless filters. However, unlike stateless/packet filtering, stateful firewalls inspect the actual data transmitted across multiple packets instead of just the headers. Because of this, they also require more system resources.
***This table is scrollable horizontally.
|
STATEFUL INSPECTION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Keep track of the entire session.
– Inspect headers and packet payloads. – Offer more control. – Operate with fewer open ports. |
– Not as cost-effective as they require more resources.
– No authentication support. – Vulnerable to DDoS attacks. – May slow down performance due to high resource requirements. |
– Provide more advanced security as it inspects entire data packets while blocking firewalls that exploit protocol vulnerabilities.
– Not efficient when it comes to exploiting stateless protocols. |
– Considered the standard network protection for cases that need a balance between packet filtering and application proxy. |
Proxy Firewalls
A proxy firewall serves as an intermediate device between internal and external systems communicating over the Internet. It protects a network by forwarding requests from the original client and masking it as its own. Proxy means to serve as a substitute and, accordingly, that is the role it plays. It substitutes for the client that is sending the request.
When a client sends a request to access a web page, the message is intersected by the proxy server. The proxy forwards the message to the web server, pretending to be the client. Doing so hides the client’s identification and geolocation, protecting it from any restrictions and potential attacks. The web server then responds and gives the proxy the requested information, which is passed on to the client.
***This table is scrollable horizontally.
|
PROXY FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Protect systems by preventing contact with other networks.
– Ensure user anonymity. – Unlock geolocational restrictions. |
– May reduce performance.
– Need additional configuration to ensure overall encryption. – Not compatible with all network protocols. |
– Offer good network protection if configured well. | – Used for web applications to secure the server from malicious users.
– Utilized by users to ensure network anonymity and for bypassing online restrictions. |
Next-Generation Firewalls
The next-generation firewall is a security device that combines a number of functions of other firewalls. It incorporates packet, stateful, and deep packet inspection. Simply put, NGFW checks the actual payload of the packet instead of focusing solely on header information.
Unlike traditional firewalls, the next-gen firewall inspects the entire transaction of data, including the TCP handshakes, surface-level, and deep packet inspection.
Using NGFW is adequate protection from malware attacks, external threats, and intrusion. These devices are quite flexible, and there is no clear-cut definition of the functionalities they offer. Therefore, make sure to explore what each specific option provides.
***This table is scrollable horizontally.
|
NEXT-GENERATION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Integrates deep inspection, antivirus, spam filtering, and application control.
– Automatic upgrades. – Monitor network traffic from Layer 2 to Layer 7. |
– Costly compared to other solutions.
– May require additional configuration to integrate with existing security management.
|
– Highly secure. | – Suitable for businesses that require PCI or HIPAA compliance.
– For businesses that want a package deal security device. |
Cloud Firewalls
A cloud firewall or firewall-as-a-service (Faas) is a cloud solution for network protection. Like other cloud solutions, it is maintained and run on the Internet by third-party vendors.
Clients often utilize cloud firewalls as proxy servers, but the configuration can vary according to the demand. Their main advantage is scalability. They are independent of physical resources, which allows scaling the firewall capacity according to the traffic load.
Businesses use this solution to protect an internal network or other cloud infrastructures (Iaas/Paas).
***This table is scrollable horizontally.
|
CLOUD FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Availability.
– Scalability that offers increased bandwidth and new site protection. – No hardware required. – Cost-efficient in terms of managing and maintaining equipment. |
– A wide range of prices depending on the services offered.
– The risk of losing control over security assets. – Possible compatibility difficulties if migrating to a new cloud provider. |
– Provide good protection in terms of high availability and having a professional staff taking care of the setup.
|
– A solution suitable for larger businesses that do not have an in-staff security team to maintain and manage the on-site security devices. |
Which Firewall Architecture is Right for Your Business?
When deciding on which firewall to choose, there is no need to be explicit. Using more than one firewall type provides multiple layers of protection.
Also, consider the following factors:
- The size of the organization. How big is the internal network? Can you manage a firewall on each device, or do you need a firewall that monitors the internal network? These questions are important to answer when deciding between software and hardware firewalls. Additionally, the decision between the two will largely depend on the capabilities of the tech team assigned to manage the setup.
- The resources available. Can you afford to separate the firewall from the internal network by placing it on a separate piece of hardware or even on the cloud? The traffic load the firewall needs to filter and whether it is going to be consistent also plays an important role.
- The level of protection required. The number and types of firewalls should reflect the security measures the internal network requires. A business dealing with sensitive client information should ensure that data is protected from hackers by tightening the firewall protection.
Build a firewall setup that fits the requirements considering these factors. Utilize the ability to layer more than one security device and configure the internal network to filter any traffic coming its way. For secure cloud options, see how phoenixNAP ensures cloud data security.
Recent Posts
10 Step Business Continuity Planning Checklist with Sample Template
If you don’t have a Business Continuity Plan in place, then your business and data is already in danger. Believing a business will continue to generate profit in the future without putting safeguards in place is a very risky practice. Ignoring the pitfalls can be catastrophic.
Business continuity as a concept is self-explanatory. Yet, it encompasses much more than an organization’s future profitability. It covers all aspects of a business’s longevity, prosperity and success.
In this article, you will learn how to create an effective business continuity plan to protect your assets.
What is a Business Continuity Plan?
The definition of business continuity planning refers to the process involved in the creation of a system that prevents penitential threats to a company, also aiding in its recovery.
This plan outlines how assets and personnel will be protected during the event of a disaster, and how to function normally through an event. A BCP should include contingencies for human resources, assets and business processes, and any other aspects that could be affected by downtime or failure. The plan consists of input from all key stakeholders and must be finalized in advance.
A BCP is an essential part of a company’s risk management strategy. It should be updated as technology and hardware/software get updated. These risks usually include natural disasters—weather-related events, flood, fire, or cyber and virtual attacks. Any and every risk that can affect a company’s operations is defined beforehand by the BCP. A typical plan includes:
- Identifying all potential risks
- Determining the effect of the risk on the company’s normal operations
- Implementing procedures and safeguards for risk mitigation
- Testing the procedures to ensure their success
- Constantly reviewing the processes to make sure it’s updated
After an organization assess its risks and identifies them, it needs to follow these steps:
- Understanding how these risks will interfere or affect operations
- Setting up procedures and safeguards that mitigate risks and offer rapid solutions
- Systems on how to test solutions to ensure they work, and scheduling them regularly
- Ensuring that processes are systematically reviewed to make sure they’re up to date
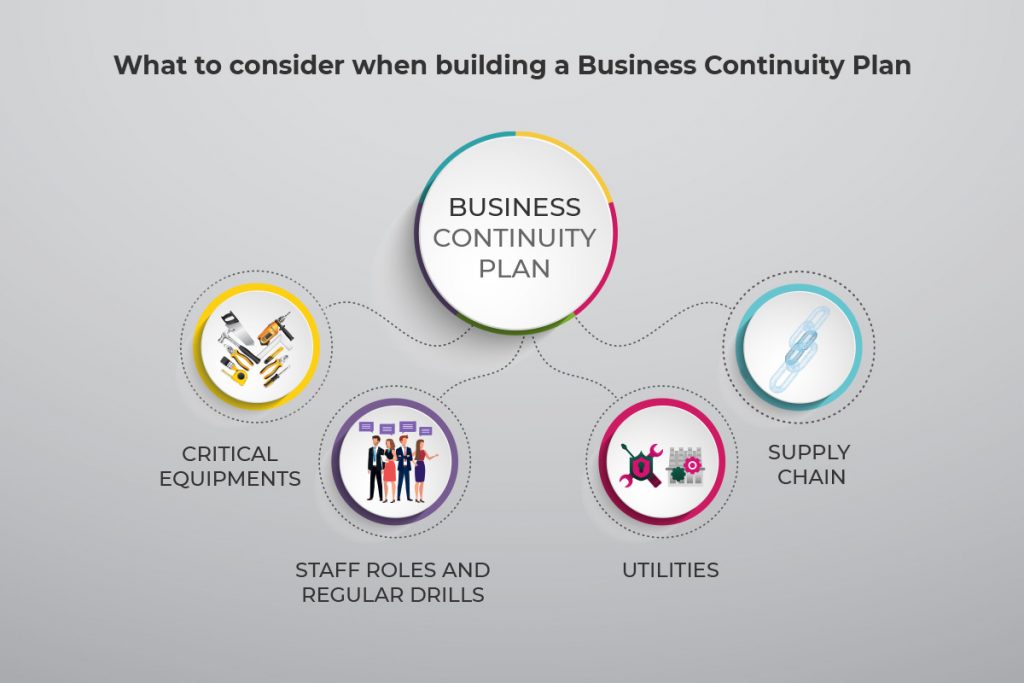
Business Continuity Checklist
A successful business continuity plan is prepared based on the understanding of the impact of a disaster situation on a business. A business continuity checklist includes certain steps, which we have summarized for you below in point form.
Use this step by step guide for preparing your comprehensive preparedness plan. When it comes to disaster recovery strategies, each company will have varying strategies based on geographical locations, the organization’s structure, system, environments, and the severity of the disaster in question.
-
Assemble the Planning Team:
Implementing a BCP plan certainly requires a dedicated team. Teams should be built with hierarchy in mind, with specific roles and recovery tasks assigned to staff members who are accountable for each.
-
Drawing Up the BCP Plan:
Mapping out a strategy is one of the most important components of a business continuity plan. The objectives of the plan should be clearly understood with goals set accordingly. A company should use this opportunity to identify the key processes and the people who will keep it running.
To draw up the plan, companies need to make a list of all the disruptions that could affect a company’s operations. Pinpoint critical functions in everyday business processes and formulate practical recovery strategies for each possible disaster scenario.
-
Conduct Business Impact Analysis:
After identifying all the potential threats, they should be thoroughly analyzed. A proper business impact analysis or BIA should be in place. Extensive lists may need to be prepared, depending on the company’s set up and geographical location.
The list can include floods, hurricanes, fires, volcanoes, and even Tsunamis. Apart from the above natural disasters, others have a much higher probability of occurring. These can include cyberattacks, downtime due to power outages, data corruption, system failures, hardware faults, and other malicious threats to data security.
-
Educate and Train:
Handling business continuity requires knowledge beyond that of IT professionals and those with cybersecurity proficiency. Companies at the upper management level need to layout the objectives, requirements, and key components of the plan before the whole team. Develop a comprehensive training program to help the team develop the required skills.
-
Isolate Sensitive Info:
Every business works with critical data allocated with the topmost security priority. Such data, when compromised or leaked, can spell the end for a company or organization. Data, such as financial records and other mission-critical information such as user login credentials, require storage where recovery is convenient and easy. Store data according to priority based on the importance of the data to the business.
-
Backup Important Data:
Every company has some critical data, which is irreplaceable. Hence, every recovery or backup plan should include creating copies of anything which is not replaceable. In a Managed Service Provider’s (MSP) case, it includes files, data on customer and employee records, business emails, etc. The plan in place should facilitate quick recovery so that businesses can recover tomorrow from any disaster that occurs today.
-
Protect Hard Copy Data:
Electronic or digital data is the main focus of modern IT security strategies. There is still an enormous volume of physical documents that businesses need to maintain daily.
For example, a typical MSP involves working with an assortment of tax documents, contracts, and employee files, which are as important as the data saved on the hard drives. Convert documents that can be digitized to minimize the loss of physical documents.
-
Designate a Recovery Site:
Disasters have the potential to wipe out a company’s data center completely.
Companies should prepare for the worst, by designating a secondary site which would act as a back-up for the primary site. The second site should be equipped with the required tools and systems to recover affected systems to ensure that the business processes continue.
-
Set up a Communications Program:
Communication within the company is vital in times of crisis. Companies should consider drafting sample messages in advance to expedite communications to suppliers and partners in times of crisis.
Business Continuity teams can use a detailed communication plan to coordinate their efforts efficiently.
-
Test, Measure, and Update:
Every important business program should be tested and measured for its effectiveness, and business continuity plans are no exceptions. Testing should include running simulations to test the team’s level of preparedness during a crisis. Based on the results, additional modifications and tweaks can be made.
Download Our Sample Business Continuity Plan Template
Benefits of a Business Continuity Plan
A business continuity plan involves identifying and listing out all potential risks and threats a company may face and laying out appropriate policies to mitigate those risks in case of any disaster or crisis. A properly implemented business continuity plan would help any company to remain operational even in the wake of a disaster. Outlined below are some of the greatest advantages of having a business continuity plan in place:
Business Remains Operational During Disaster
Disasters can happen at any time, unannounced. Businesses need to recover from such incidents as quickly as possible to ensure there are no major disruptions in business processes. Business Continuity Plans can help companies remain operational throughout the disaster or the business recovery phase.
Avoid Expensive Downtime:
An Aberdeen Group report indicated that downtime could cost up to $8600 per hour to small scale organizations. If the system is down, businesses lose money, customers, or even their reputation is in danger in certain cases. A proper BCP in place can prevent losing any opportunities during an outage.
Protect Against Different Disasters
Disasters and crises do not always include disasters such as fire, tornadoes, or pandemics, etc. A crisis can also occur from hardware failures, power outages, cybercrimes, and other forms of human error. Thus, companies need to protect themselves not only from natural disasters but from all other forms of outages and downtime. A BCP mitigates these risks.
Gain a Competitive Advantage
In the event of a national or global crisis, a business’s reputation can be bolstered, if it remains up and running while its competitors are down. Clients can look more favorably towards the company as they associate a certain level of reliability with them. Putting a BCP plan in place can help companies stay operational during such times, giving them a clear competitive edge over their competitors.
Giving Assurance to Employees
It is natural for employees to worry if systems are compromised due to a crisis. This situation makes them worry about how and when to proceed with their delegated tasks, negatively affecting the workflow. This scenario is especially true for customer-centric organizations. Having a BCP plan in place for such situations can help prepare a company’s staff on what to do in such situations, and help keep business processes running smoothly. Having a clear action plan can do wonders for employees as it increases the company’s morale and job satisfaction.
Gain Peace of Mind
Having a detailed, tried, and tested BCP in place can alleviate much of management’s worries and stress, helping them to work on other core competencies. Companies can carry on confidently with their operations, knowing that there are measures in place to counter any system outage or downtime. BCP plans are thus critical to a company’s longevity, helping them defend against potential risks while enhancing a company’s reputation.
Stages of Developing a Strong BCP
Business Impact Analysis: You will identify resources and functions that are time-sensitive and need an immediate reaction.
GAP analysis: You need to analyze aspects of your business continuity management system that you currently have and evaluate your IT emergency management system and see how ready and mature it is to face evolving threats.
Improvement planning: This analysis will tell you what you need to work on to help improve the maturity of your Business Continuity Management (BCM) and what will help it improve over time.
Recovery: A clear plan needs to be outlined on which steps to take to fully recover critical business functions and get all applications back online smoothly.
Organization: A continuity team should be put in place who will come up with this plan and be responsible for managing all types of disruptions.
Training: The continuity team needs to get regular training and undergo testing, who complete scenarios and exercises that deal with the multitude of threats and disasters your company can face. They should also update and regularly go over the plan and strategies.
What Does a Business Continuity Plan Typically Include?
It’s critical to have a detailed plan for how to run business operations and maintain them for both the interim and possible longer-term disruptions and outages.
A BCP plan should outline what to do with data backups, equipment and supplies, and backup site locations, and how to reestablish technical productivity and software integrity so that vital business functions can continue. It should give step by step instructions to administrators, which includes all necessary information for backup site providers, key personnel, and emergency responders.
Remember these three keys to creating a successful business continuity plan:
- Disaster recovery: Consolidate a method to recover a data center, possibly at an external site. If the primary site is compromised, it becomes obsolete and inoperable.
- High availability: Ensure the capability of processes are highly available. In case of a local failure, the business can still function with limited access to applications despite the crisis in hardware/software, business processes, or the shutdown of physical facilities.
- Continuity of operations: The main goal is to keep processes and applications running during an outage, and to test them during planned outages. Scheduling backups and planning for maintenance is key to staying active.
Keep up with your competitors! As the Covid-19 crisis has shown, it’s essential to put a Business Continuity Plan in place to defend against every type of disaster using our best practices. Failure to do so can mean financial loss or damage to your company’s reputation. Start preparing, contact us or use our free BCP template to get started today.
What is Data Integrity? Why Your Business Needs to Maintain it
Definition of Data Integrity
Data Integrity is a process to ensure data is accurate and consistent over its lifecycle. Good data is invaluable to companies for planning – but only if the data is accurate.
Data Integrity typically refers to computer data. It can be applied more broadly, though, to any data collection. Even a field technician who makes onsite repairs can collect data. Protocols can still be used to ensure data stays intact.
Threats to the Integrity of Data
There are a few ways that data can be damaged:
- Damage in transit – Data can become damaged during transfer either to a storage device or over a network.
- Hardware failure – Failure in a storage device or other computer hardware can cause corruption.
- Configuration problems – A misconfiguration in a computing system, such as a software or security application, can damage data.
- Human error – People make mistakes, and can accidentally damage data.
- Deliberate breach – A person or software infiltrates a computer and changes data. For example, some malware encrypts data and holds it hostage for payment. A hacker might breach the system and make changes.
The Importance of Data Integrity
Critical business decisions depend on accurate data. As data collection increases, companies use it to measure effectiveness.
If data is damaged, any decisions based on that data are suspect. For example, a business sets a tracking cookie on its web page. This cookie collects the number of page views and sign-ups by visitors. If the cookie is misconfigured, it might show an artificially high sign-up rate. The business might decide to spend less on marketing, leading to less traffic and fewer sign-ups.
Data integrity is crucial because it’s a window into the organization. If that data is damaged, it’s hard to see the details. Worse, manipulated data can lead to bad business decisions.
Aspects of Data Integrity
Who, what, when
Data should have the time, date, and identity of who recorded it. It could include a brief overview or might be a timestamp of access to a website. It could be noted from a tech support agent.
Readability and Formatting
The data should be formatted and easy to read. In the case of a tech support agent, use a standard format to document the ticket. For a website, logging should be automatic and meaningful. A field technician should write legibly on forms, and consider transcribing them digitally.
Timely
Log data as it happens.Any delay in recording creates an opportunity for loss. Data should record as it is observed, without interpretations.
Original
Good data is kept in its original format, secured, and backed up. Create reports and interpretations using copies of the original data. This helps reduce the chances of damaging the original.
Accurate
Make sure data follows protocols, and is free from errors. A tech support agent might log a script. A website logger might record data in a standard file type like XML. A field technician should complete all fields on a paper form.
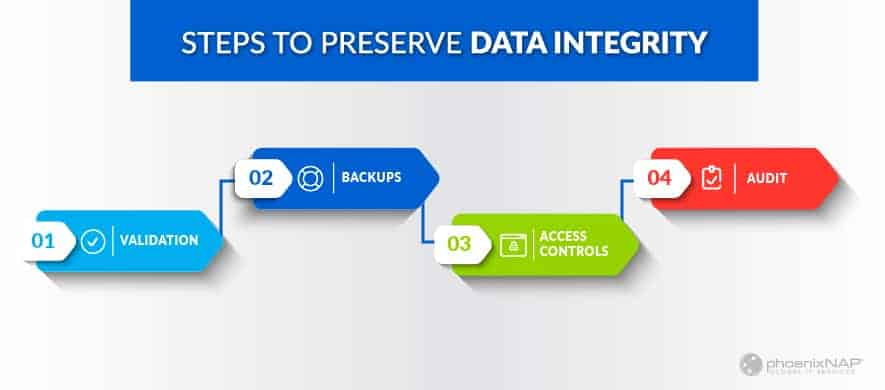
How to ensure data integrity
Validate input
Check input at the time it’s recorded. For example, a contact form on a website might screen for a valid email address. Digital input can be automated, such as electronic forms that allow specific information. Review paper forms and logs and correct any errors.
Input validation can also be used to block cyber attacks, such as SQL injection prevention. This is one-way Data Integrity works together with data security.
Validate data
Once collected, the data is in a raw form. Validation checks the quality of the data to be correct, meaningful, and secure. Automate digital validation by using scripts to filter and organize data. For paper data, transcribe notes into digital format. Alternately, physical notes can be reviewed for errors.
Data validation can happen during transfer. For example, copying to a USB drive or downloading from the internet. This checks to ensure the copy is identical to the original. Network protocols use error-checking, but it’s not foolproof. Validation is an extra step to ensure integrity.
Make backups
A good backup creates a duplicate in a different location. Copying a folder onto a USB drive is one way to create a backup. Storing files in the cloud is another. Even data centers can create backups by mirroring content with a second data center.
Backups should include the original raw data. Reports can always be recreated from the original data. Once lost, raw data is irreplaceable.
Implement access controls
Access to data should be based on a business needs. Restrict unauthorized users from access to data. For example, a tech support agent does not need access to client payment card data.
Even with physical paper data, access controls and management are essential. Sensitive physical records should be kept locked and secure. Limiting access reduces the chances of corruption and loss.
Maintain an audit trail
An audit trail records access and usage of data. For example, a database server might record the username, time, and date for each action in a database. Likewise, a library might keep a ledger of the names and dates of guests.
Audit trails are data and should follow the guidelines in this article. They aren’t typically used unless there’s a problem. The audit trail can help identify the source of data loss. An audit trail might show a username and time stamp for access. This helps identify and stop the problem.
Database Integrity
In database theory, data integrity includes three main points:
- Entity Integrity – Each table needs a unique primary key to distinguish one table from another.
- Referential Integrity – Tables can refer to other tables using a foreign key.
- Domain Integrity – The database has pre-set categories and values. This is similar to screening input and reading reports.
With a database, data integrity works differently. This is useful for the inner workings of a database. Even so, the database is still part of an organization. The advice in this article will help your organization create policies on how to keep the database intact.
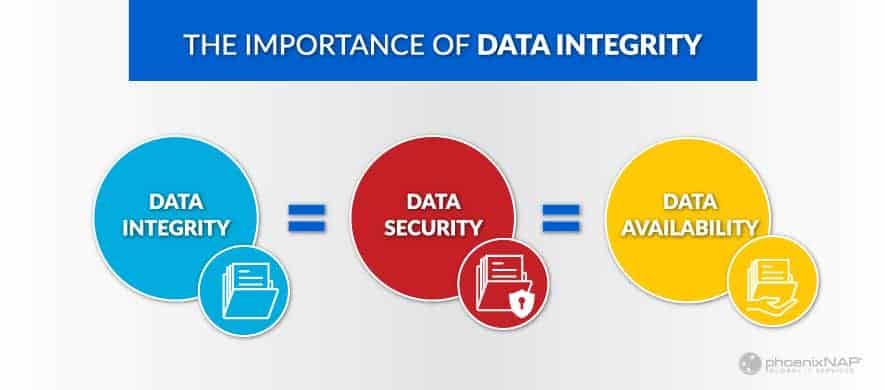
Data Security versus Data Integrity
Data Security is related to Data Integrity, but they are not the same thing. Data Security refers to keeping data safe from unauthorized users. It includes hardware solutions like firewalls and software solutions like authentication. Data Security often goes hand-in-hand with preventing cyber attacks.
Data Integrity is a more broad application of policies and solutions to keep data pure and unmodified. It can include Data Security to prevent unauthorized users from modifying data. But it also provides for measures to record, maintain, and preserve data in its original condition.
Conclusion
Data Integrity ensures keeping electronic data intact. After all, reports are only as good as the data they are based on. Data integrity can also apply to information outside the computer world. Whether it’s digital or printed, ensuring data integrity forms the base for good business decisions.
Recent Posts
RTO (Recovery Time Objective) vs RPO (Recovery Point Objective)
In this article you will learn:
- What Recovery Time Objective (RTO) and Recovery Point Objective (RPO) are. Why they are critical to your data recovery and protection strategy.
- Intelligent data management starts with a plan to avoid catastrophic losses — disaster recovery planning can guarantee the survival of your business when an emergency strikes.
- How business continuity planning minimizes the loss of revenue while also boosting customer confidence.
Recovery Time Objective and Recovery Point Objective may sound alike, but they are entirely different metrics in disaster recovery and business continuity management.
Find out how to plan accordingly with the proper resources before you need them. Much like having insurance, you may never use it – or it may save your company.
In this article, we will examine the critical differences between RPO and RTO and clear up any confusion!
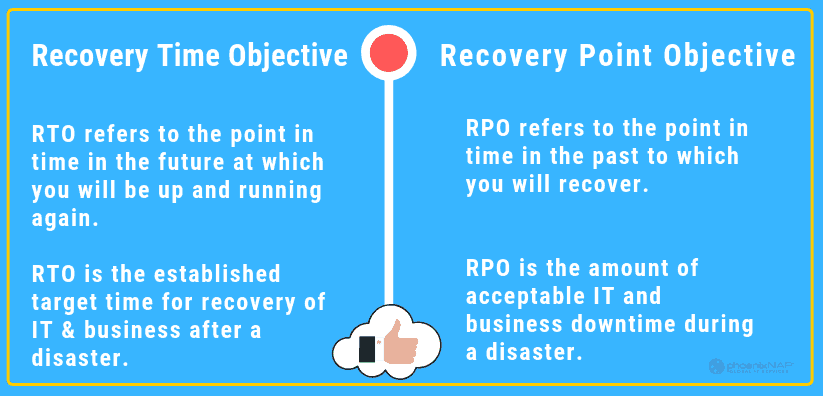
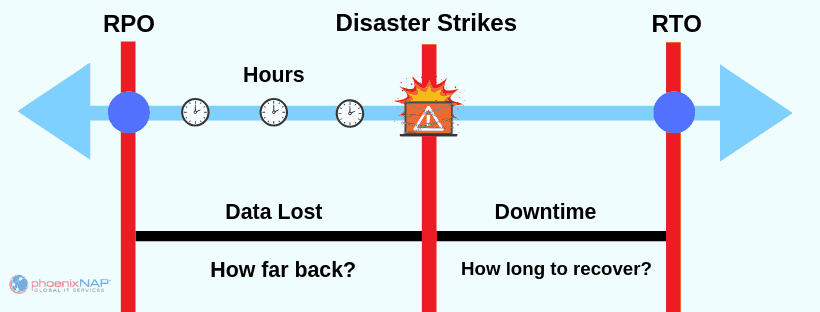
RTO: Recovery Time Objective
RTO dictates how quickly your infrastructure needs to be back online after a disaster. Sometimes, we use RTO to define the maximum downtime a company can handle and maintain business continuity. This is often a target time set for services restoration after a disaster. For example, a Recovery Time Objective of 2 hours aims to have everything back up and running within two hours of service disruption notification.
Sometimes, such RTO is not achievable. A hurricane or a flood can bring down a business, leaving it down for weeks. However, some organizations are more resilient to outages.
For example, a small plumbing company could get by with paperwork orders and invoicing for a week or more. A business with a web-based application that relies on subscriptions might be crippled after only a few hours.
In the case of outsourced IT services, RTO is defined within a Service Level Agreement (SLA). IT and other service providers typically include the following support terms in their SLA:
- Availability: the hours you can call for support.
- Response time: how quickly they contact you after a support request.
- Resolution time: how quickly they will restore the services.
Depending on your business requirements, you may need better RTO. With it, the costs increase as well. Whatever RTO you choose, it should be cost-effective for your organization.
Businesses can handle RTO internally. If you have an in-house IT department, there should be a goal for resolving technical problems. The ability to fulfill the RTO depends on the severity of the disaster. An objective of one hour is attainable for a server crash. However, it might not be realistic to expect a one-hour solution in case of a natural disaster in the area.
RTO includes more than just the amount of time to needed to recover from a disaster. It should also include steps to mitigate or recover from different disasters. The plan needs to contain proper testing for the measures
RPO: Recovery Point Objective
An RPO measures the acceptable amount of data loss after a disruption of service.
For example, lost sales may become an excessive burden against costs after 18 hours. That threshold may put a company below any sales targets.
Backups and mirror-copies of data are an essential part of RPO solutions. It is necessary to know how much data is an acceptable loss. Some businesses address this by calculating storage costs versus recovery costs. This helps determine how often to create backups. Other businesses use cloud storage to create a real-time clone of their data. In this scenario, a failover happens in a matter of seconds.
Similar to RTO and acceptable downtime, some businesses have better loss tolerance for data. Retrieving 18 hours of records for a small plumbing company is possible but may not be detrimental to the business operation. In contrast, an online billing company may find itself in trouble after only a few minutes worth of data loss.
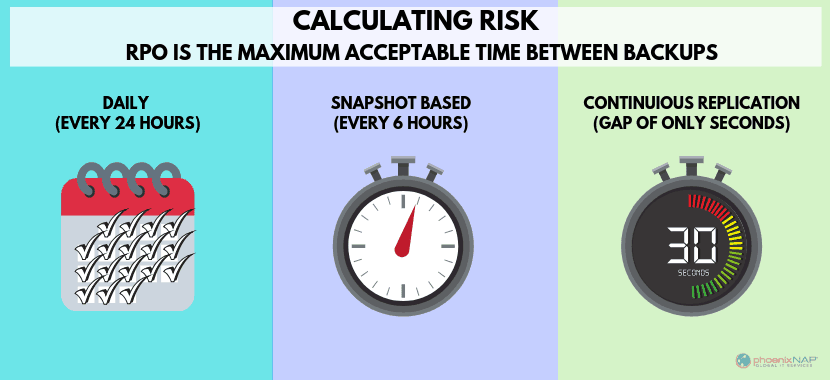
RPO is categorized by time and technology:
- 8-24 hours: These objectives rely on external storage data backups of the production environment. The last available backup serves as a restoration point.
- Up to 4 hours: These objectives require ongoing snapshots of the production environment. In a disaster, getting data back is faster and brings less disruption to your business.
- Near zero: These objectives use enterprise cloud backup and storage solutions to mirror or replicate data. Frequently, these services replicate data in multiple geographic locations for maximum redundancy. The failover and failback are seamless.
Both RTO and RPO involve periods of time for the measurements. However, while RTO focuses on bringing hardware and software online, RPO focuses on acceptable data loss.
Calculation of Risk
Both RTO and RPO are calculations of risk. RTO is a calculation of how long a business can sustain a service interruption. RPO is a calculation of how recent the data will be when it is recovered.
Calculating RTO
We base RTO calculation on projection and risk management. A frequently used application may be critical for business continuity in the same way a seldom-used application is. Hence, the importance of an application does not have to be the same as the frequency of usage. You need to decide which services can be unavailable for how long and if they are critical to your business.
To calculate RTO, consider these factors:
- The cost per hour of outage
- The importance and priority of individual systems
- Steps required to mitigate or recover from a disaster (including individual components or processes)
- Cost/benefit equation for recovery solutions
Calculating RPO
Calculating an RPO is also based on risk. In a disaster, a degree of data loss may be imminent. RPO becomes a balancing act between the impact of data loss on the business and the cost of mitigation. A few angry customers, because their orders are lost, might be an acceptable loss. In contrast, hundreds of lost transactions might be a massive blow to a business.
Consider these factors when determining your RPO:
- The maximum tolerable amount of data loss that your organization can sustain.
- The cost of lost data and operations
- The cost of implementing recovery solutions
RPO is the maximum acceptable time between backups. If data backups are performed every 6 hours, and a disaster strikes 1 hour after the backup, you will lose only one hour of data. This means you are 5 hours under the projected RPO.
Disaster Recovery Planning
Disasters come in many forms. Such as a natural disaster, hurricane, flood, or a wildfire. A disaster could also refer to a catastrophic failure of assets or infrastructure, like power lines, bridges, or servers.
Disasters include all types of cybersecurity attacks that destroy your data, compromise credit card information, or even disable an entire site.
With so many definitions of disaster, it is helpful to define them in terms of what they have in common. For organizations and IT departments, a disaster is an event that disrupts normal business operation.
Dealing with disasters starts with planning and prevention. Many businesses use cloud solutions in different geographical regions to minimize the risk of downtime. Some install redundant hardware to keep the IT infrastructure running.
A crucial step in data recovery is to develop a Disaster Recovery plan.
Consider the probability of different kinds of disasters. Various disasters may warrant different response plans. For example, in the Pacific Northwest, hurricanes are rare, but earthquakes can occur. In Florida, the reverse is true. Cyber-attacks may be more of a threat to larger businesses with extensive online presence than smaller ones. A DDoS attack might warrant a different response than a data breach.
A Disaster Recovery Plan helps to bring systems and processes online much faster than ad hoc solutions. When everyone plays a specific role, a recovery strategy can proceed quickly. A DR plan also helps put resources in place before you need them. Therefore, response plans improve Recovery Time and Recovery Point Objectives.
Difference Between RTO and RPO is Critical
While closely related, it is essential to understand the differences between Recovery Time Objective and Recovery Point Objective
RTO refers to the amount of time you need to bring a system back online. RPO is a business calculation for acceptable data loss from downtime.
Improve these metrics and employ a Disaster Recovery plan today.
Recent Posts
What is Business Continuity Management (BCM)? Framework & Key Strategies
Business continuity management is a critical process. It ensures your company maintains normal business operations during a disaster with minimal disruption.
BCM works on the principle that good response systems mitigate damages from theoretical events.
What is Business Continuity Management? A Definition
Business continuity management is defined as the advanced planning and preparation of an organization to maintaining business functions or quickly resuming after a disaster has occurred. It also involves defining potential risks including fire, flood or cyber attacks.
Business leaders plan to identify and address potential crises before they happen. Then testing those procedures to ensure that they work, and periodically reviewing the process to make sure that it is up to date.

Business Continuity Management Framework
Policies and Strategies
Continuity management is about more than the reaction to a natural disaster or cyber attack. It begins with the policies and procedures developed, tested, and used when an incident occurs.
The policy defines the program’s scope, key parties, and management structure. It needs to articulate why business continuity is necessary andGovernance is critical in this phase.
Knowing who is responsible for the creation and modification of a business continuity plan checklist is one component. The other is identifying the team responsible for implementation. Governance provides clarity in what can be a chaotic time for all involved.
The scope is also crucial. It defines what business continuity means for the organization.
Is it about keeping applications operational, products and services available, data accessible, or physical locations and people safe? Businesses need to be clear about what is covered by a plan whether it’s revenue-generating components of the company, external facing aspects, or some other subset of the total organization.
Roles and responsibilities need to be assigned during this phase as well.
These may be roles that are obvious based on job function, or specific, given the type of disruption that may be experienced. In all cases, the policy, governance, scope, and roles need to be broadly communicated and supported.
Business Impact Assessment
The impact assessment is a cataloging process to identify the data your company holds, where it’s stored, how it’s collected, and how it’s accessed It determines which of those data are most critical and what the amount of downtime is that’s acceptable should that data or apps be unavailable.
While companies aim for 100 percent uptime, that rate is not always possible, even given redundant systems and storage capabilities. This phase is also the time when you need to calculate your recovery time objective, which is the maximum time it would take to restore applications to a functional state in the case of a sudden loss of service.
Also, companies should know the recovery point objective, which is the age of data that would be acceptable for customers and your company to resume operations. It can also be thought of as the data loss acceptability factor.
Risk Assessment
Risk comes in many forms. A Business Impact Analysis and a Threat & Risk Assessment should be performed.
Threats can include bad actors, internal players, competitors, market conditions, political matters (both domestic and international), and natural occurrences. A key component of your plan is to create a risk assessment that identifies potential threats to the enterprise.
Risk assessment identifies the broad array of risks that could impact the enterprise.
Identifying potential threats is the first step and can be far-reaching. This includes:
- The impact of personnel loss
- Changes in consumer or customer preferences
- Internal agility and ability to respond to security incidents with a plan
- Financial volatility
Regulated companies need to factor in the risk of non-compliance, which can result in hefty financial penalties and fines, increased agency scrutiny and the loss of standing, certification, or credibility.
Each risk needs to be articulated and detailed. In the next phase, the organization needs to determine the probability of each risk happening and the potential impact of each one. Likelihood and potential are key measures when it comes to risk assessment.
Once the risks have been identified and ranked, the organization needs to determine what its risk tolerance is for each potentiality. What are the most urgent, critical issues that need to be addressed? At this phase, potential solutions need to be identified, evaluated, and priced. With this new information, which includes probability and cost, the organization needs to prioritize which risks will be addressed.
The ranked risks then need to be evaluated as to which risks will be addressed first. Note that this process is not static. It needs to be regularly discussed to account for new threats that emerge as technologies, geopolitics, and competition evolves.
Validation and Testing
The risks and their impacts need to be continuously monitored, measured and tested. Once mitigation plans are in place, those also should be assessed to ensure they are working correctly and cohesively.
Incident Identification
With business continuity, defining what constitutes an incident is essential. Events should be clearly described in policy documents, as should who or what can trigger that an incident has occurred. These triggering actions should prompt the deployment of the business continuity plan as it is defined and bring the team into action.
Disaster Recovery
What’s the difference between business continuity and disaster recovery? The former is the overarching plans that guide operations and establish policy. Disaster recovery is what happens when an incident occurs.
Disaster recovery is the deployment of the teams and actions that are sprung. It is the net results of the work done to identify risks and remediate them. Disaster recovery is about specific incident responses, as opposed to broader planning.
After an incident, one fundamental task is to debrief and assess the response, and revising plans accordingly.

Role of Communication & Managing Business Continuity
Communication is an essential component of managing business continuity. Crisis communication is one component, ensuring that there are transparent processes for communicating with customers, consumers, employees, senior-level staff, and stakeholders. Consistent communication strategies are essential during and after an incident. Messaging must be consistent, accurate, and coming from a unified corporate voice.
Crisis management involves many layers of communication, including the creation of tools to indicate progress, critical needs, and issues. The types of communication may vary across constituencies but should be based on the same sources of information.
Resilience and Reputation Management
The risks of not having a business continuity plan are significant. The absence of preparing means the company is ill-prepared to address pressing issues.
These risks can leave a company flat-footed and can lead to other significant problems, including:
- Downtime for cloud-based servers, systems, and applications. Even minutes of downtime can result in the loss of substantial revenue.
- Credibility loss to reputation and brand identity. Widespread, consistent, or frequent downtime can erode confidence with customers and consumers. Customer retention can plummet.
- Regulatory compliance can be at risk in industries such as financial services, healthcare, and energy. If systems and data are not operational and accessible, the consequences are severe.
Prepare Today, Establish a Business Continuity Management Program
Managing business continuity is about data protection and integrity, the loss of which can be catastrophic.
It should be part of organizational culture. With a systematic approach to business continuity planning, businesses can expedite the recovery of critical activity.
Recent Posts
Upgrade Your Security Incident Response Plan (CSIRP) : 7 Step Checklist
In this article you will learn:
- Why every organization needs a cybersecurity incident response policy for business continuity.
- The Seven critical security incident response steps (in a checklist) to mitigate data loss.
- What should be included in the planning process to ensure business operations are not interrupted?
- Identify which incidents require attention & When to initiate your response.
- How to use threat intelligence to avoid future incidents.
What if your company’s network was hacked today? The business impact could be massive.
Are you prepared to respond to a data security breach or cybersecurity attack? In 2020, it is far more likely than not that you will go through a security event.
If you have data, you are at risk for cyber threats. Cybercriminals are continually developing new strategies to breach systems. Proper planning is a must. Preparation for these events can decrease the damage and loss you and your stakeholder’s.
Having a clear, specific, and current cybersecurity incident response plan is no longer optional.
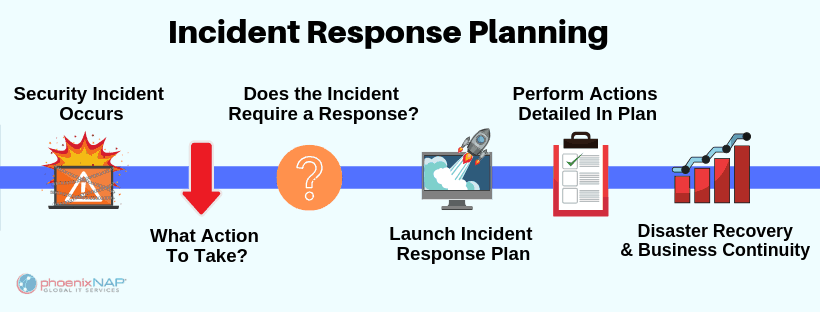
What is an Incident Response Plan?
An incident response (IR) plan is the guide for how your organization will react in the event of a security breach.
Incident response is a well-planned approach to addressing and managing reaction after a cyber attack or network security breach. The goal is to minimize damage, reduce disaster recovery time, and mitigate breach-related expenses.
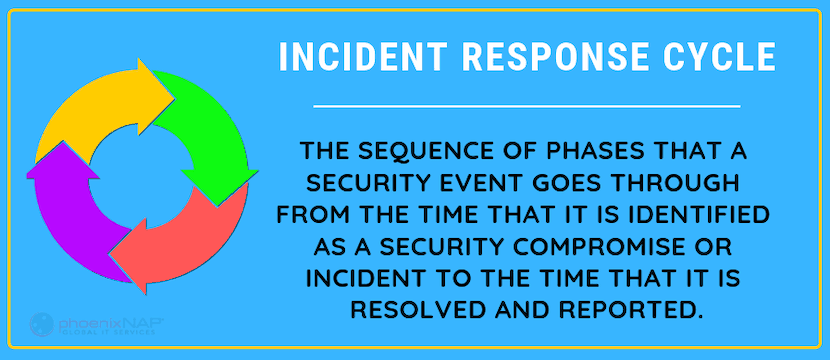
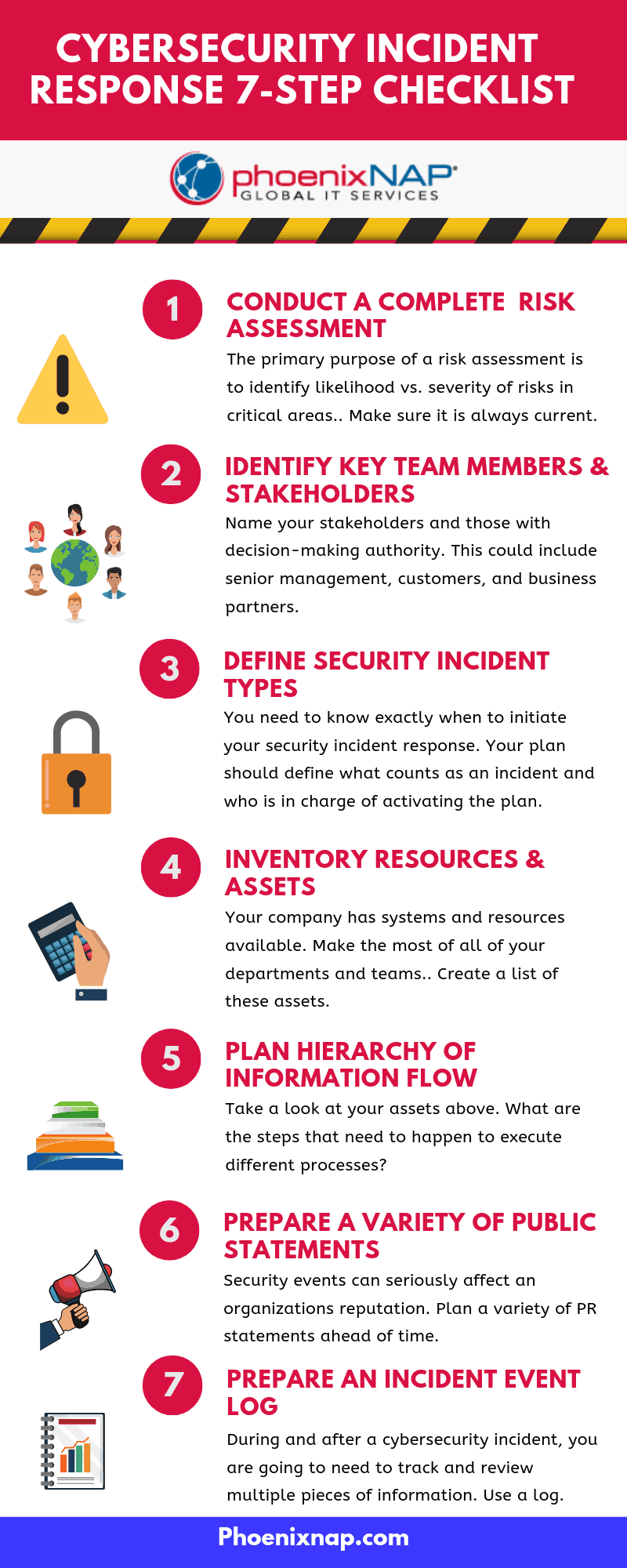
Cybersecurity Incident Response Checklist, in 7 Steps
During a breach, your team won’t have time to interpret a lengthy or tedious action plan.
Keep it simple; keep it specific.
Checklists are a great way to capture the information you need while staying compact, manageable, and distributable. Our checklist is based on the 7 phases of incident response process which are broken down in the infographic below.
Share this Image On Your Site, Copy & Paste
1. Focus Response Efforts with a Risk Assessment
If you haven’t done a potential incident risk assessment, now is the time. The primary purpose of any risk assessment is to identify likelihood vs. severity of risks in critical areas. If you’ve done a cybersecurity risk assessment, make sure it is current and applicable to your systems today. If It’s out-of-date, perform another evaluation.
Examples of a high-severity risk are a security breach of a privileged account with access to sensitive data. This is especially the case if the number of affected users is high. If the likelihood of this risk is high, then it demands specific contingency planning in your IR plan. The Department of Homeland Security provides an excellent Cyber Incident Scoring System to help you assess risk.
Use your risk assessment to identify and prioritize severe, likely risks. Plan appropriately for medium and low-risk items as well. Doing this will help you avoid focusing all your energy on doomsday scenarios. Remember, a “medium-risk” breach could still be crippling.
2. Identify Key Team Members and Stakeholders
Identify key individuals in your plan now, both internal and external to your CSIRT. Name your stakeholders and those with decision-making authority. This could include senior management, customers, and business partners.
Document the roles and responsibilities of each key person or group. Train them to perform these functions. People may be responsible for sending out a PR statement, activating procedures to contact authorities, or performing containment activities to minimize damage from the breach.
Store multiple forms of contact information both online and offline. Plan to have a variety of contact methods available (don’t rely exclusively on email) in case of system interruptions.
3. Define Incident Types and Thresholds
You need to know exactly when to initiate your IT security incident response. Your response plan should define what counts as an incident and who is in charge of activating the plan.
Know the kinds of cybersecurity attacks that can occur — stay-up-to-date on the latest trends and new types of data breaches that are happening.
Defining potential security incidents can save critical time in the early stages of breach detection. The stronger your CSIRT’s working knowledge of incident types and what they look like, the faster you can invoke a targeted active response.
Educate those outside your CSIRT, including stakeholders. They should also be familiar with these incident definitions and thresholds. Establish a clear communication plan to share information amongst your CSIRT and other key individuals to convey this information.
4. Inventory Your Resources and Assets
IR response depends on coordinated action across many departments and groups. You have different systems and resources available, so make the most of all of your departments and response teams.
Create a list of these assets, which can include:
- Business Resources: Team members, security operations center departments, and business partners are all businesses resources. These should consist of your legal team, IT, HR, a security partner, or the local authorities.
- Process Resources: A key consideration is to evaluate the processes you can activate depending on the type and severity of a security breach. Partial containment, “watch and wait” strategies, and system shutdowns like web page deactivation are all resources to include in your IR plan.
Once you have inventoried your assets, define how you would use them in a variety of incident types. With careful security risk management of these resources, you can minimize affected systems and potential losses.
5. Recovery Plan Hierarchies and Information Flow
Take a look at your assets above.
What are the steps that need to happen to execute different processes? Who is the incident response manager? Who is the contact for your security partner?
Design a flowchart of authority to define how to get from Point A to Point B. Who has the power to shut down your website for the short term? What steps need to happen to get there?
Flowcharts are an excellent resource for planning the flow of information. NIST has some helpful tools explaining how to disseminate information accurately at a moment’s notice. Be aware that this kind of communication map can change frequently. Make special plans to update these flowcharts after a department restructure or other major transition. You may need to do this outside your typical review process.
6. Prepare Public Statements
Security events can seriously affect an organizations reputation. Curbing some of the adverse effects around these breaches has a lot to do with public perception. How you interface with the public about a potential incident matters.
Some of the best practices recognized by the IAPP include:
- Use press releases to get your message out.
- Describe how (and with whom) you are solving the problem and what corrective action has been taken.
- Explain that you will publish updates on the root cause as soon as possible.
- Use caution when talking about actual numbers or totalities such as “the issue is completely resolved.”
- Be consistent in your messaging
- Be open to conversations after the incident in formats like Q&A’s or blog posts
Plan a variety of PR statements ahead of time. You may need to send an email to potentially compromised users. You may need to communicate with media outlets. You should have statement templates prepared if you need to provide the public with information about a breach.
How much is too much information? This is an important question to ask as you design your prepared PR statements. For these statements, timing is key – balance fact-checking and accuracy against timeliness.
Your customers are going to want answers fast, but don’t let that rush you into publishing incorrect info. Publicizing wrong numbers of affected clients or the types of data compromised will hurt your reputation. It’s much better to publish metrics you’re sure about than to mop up the mess from a false statement later.
7. Prepare an Incident Event Log
During and after a cybersecurity incident, you are going to need to track and review multiple pieces of information. How, when, and where the breach was discovered and addressed? These details and all supporting info will go into an event log. Prepare a template ahead of time, so it is easy to complete.
This log should include:
- Location, time, and nature of the incident discovery
- Communications details (who, what, and when)
- Any relevant data from your security reporting software and event logs
After an information security incident, this log will be critical. A thorough and effective incident review is impossible without a detailed event log. Security analysts will lean on this log to review the efficacy of your response and lessons learned. This account will also support your legal team and law enforcement both during and after threat detection.
How Often Should You Review Your Incident Response Procedures?
To review the steps in your cybersecurity incident response checklist, you need to test it. Run potential scenarios based on your initial risk assessment and updated security policy.
Perhaps you are in a multi-user environment prone to phishing attacks. Your testing agenda will look different than if you are a significant target for a DDoS attack. At a minimum, annual testing is suggested. But your business may need to conduct these exercises more frequently.
Planning Starts Now For Effective Cyber Security Incident Response
If you don’t have a Computer Security Incident Response Team (CSIRT) yet, it’s time to make one. The CSIRT will be the primary driver for your cybersecurity incident response plan. Critical players should include members of your executive team, human resources, legal, public relations, and IT.
Your plan should be a clear, actionable document that your team can tackle in a variety of scenarios, whether it’s a small containment event or a full-scale front-facing site interruption.
Protecting your organization from cybersecurity attacks is a shared process.
Partnering with the experts in today’s security landscape can make all the difference between a controlled response and tragic loss. Contact PhoenixNAP today to learn more about our global security solutions.
Recent Posts
Information Security Risk Management: Plan, Steps, & Examples
Are your mission-critical data, customer information, and personnel records safe from intrusions from cybercriminals, hackers, and even internal misuse or destruction?
If you’re confident that your data is secure, other companies had the same feeling:
- Target, one of the largest retailers in the U.S. fell victim to a massive cyber attack in 2013, with personal information of 110 million customers and 40 million banking records being compromised. This resulted in long-term damage to the company’s image and a settlement of over 18 million dollars.
- Equifax, the well-known credit company, was attacked over a period of months, discovered in July 2017. Cyber thieves made off with sensitive data of over 143 million customers and 200,000 credit card numbers.
These are only examples of highly public attacks that resulted in considerable fines and settlements. Not to mention, damage to brand image and public perception.
Kaspersky Labs’ study of cybersecurity revealed 758 million malicious cyber attacks and security incidents worldwide in 2018, with one third having their origin in the U.S.
How do you protect your business and information assets from a security incident?
The solution is to have a strategic plan, a commitment to Information Security Risk Management.
What is Information Security Risk Management? A Definition
Information Security Risk Management, or ISRM, is the process of managing risks affiliated with the use of information technology.
In other words, organizations need to:
- Identify Security risks, including types of computer security risks.
- Determining business “system owners” of critical assets.
- Assessing enterprise risk tolerance and acceptable risks.
- Develop a cybersecurity incident response plan.

Building Your Risk Management Strategy
Risk Assessment
Your risk profile includes analysis of all information systems and determination of threats to your business:
- Network security risks
- Data & IT security risks
- Existing organizational security controls
A comprehensive IT security assessment includes data risks, analysis of database security issues, the potential for data breaches, network, and physical vulnerabilities.
Risk Treatment
Actions taken to remediate vulnerabilities through multiple approaches:
- Risk acceptance
- Risk avoidance
- Risk management
- Incident management
- Incident response planning
Developing an enterprise solution requires a thorough analysis of security threats to information systems in your business.
Risk assessment and risk treatment are iterative processes that require the commitment of resources in multiple areas of your business: HR, IT, Legal, Public Relations, and more.
Not all risks identified in risk assessment will be resolved in risk treatment. Some will be determined to be acceptable or low-impact risks that do not warrant an immediate treatment plan.
There are multiple stages to be addressed in your information security risk assessment.
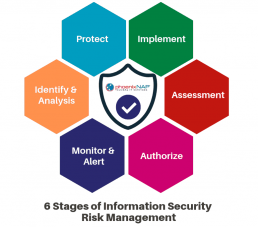
6 Stages of a Security Risk Assessment
A useful guideline for adopting a risk management framework is provided by the U.S. Dept. of Commerce National Institute of Standards and Technology (NIST). This voluntary framework outlines the stages of ISRM programs that may apply to your business.
1. Identify – Data Risk Analysis
This stage is the process of identifying your digital assets that may include a wide variety of information:
Financial information that must be controlled under Sarbanes-OxleyHealthcare records requiring confidentiality through the application of the Health Insurance Portability and Accountability Act, HIPAA
Company-confidential information such as product development and trade secrets
Personnel data that could expose employees to cybersecurity risks such as identity theft regulations
For those dealing with credit card transactions, compliance with Payment Card Industry Data Security Standard (PCI DSS)
During this stage, you will evaluate not only the risk potential for data loss or theft but also prioritize the steps to be taken to minimize or avoid the risk associated with each type of data.
The result of the Identify stage is to understand your top information security risks and to evaluate any controls you already have in place to mitigate those risks. The analysis in this stage reveals such data security issues as:
Potential threats – physical, environmental, technical, and personnel-related
Controls already in place – secure strong passwords, physical security, use of technology, network access
Data assets that should or must be protected and controlled
This includes categorizing data for security risk management by the level of confidentiality, compliance regulations, financial risk, and acceptable level of risk.
2. Protection – Asset Management
Once you have an awareness of your security risks, you can take steps to safeguard those assets.
This includes a variety of processes, from implementing security policies to installing sophisticated software that provides advanced data risk management capabilities.
- Security awareness training of employees in the proper handling of confidential information.
- Implement access controls so that only those who genuinely need information have access.
- Define security controls required to minimize exposure from security incidents.
- For each identified risk, establish the corresponding business “owner” to obtain buy-in for proposed controls and risk tolerance.
- Create an information security officer position with a centralized focus on data security risk assessment and risk mitigation.
3. Implementation
Your implementation stage includes the adoption of formal policies and data security controls.
These controls will encompass a variety of approaches to data management risks:
- Review of identified security threats and existing controls
- Creation of new controls for threat detection and containment
- Select network security tools for analysis of actual and attempted threats
- Install and implement technology for alerts and capturing unauthorized access
4. Security Control Assessment
Both existing and new security controls adopted by your business should undergo regular scrutiny.
- Validate that alerts are routed to the right resources for immediate action.
- Ensure that as applications are added or updated, there is a continuous data risk analysis.
- Network security measures should be tested regularly for effectiveness. If your organization includes audit functions, have controls been reviewed and approved?
- Have data business owners (stakeholders) been interviewed to ensure risk management solutions are acceptable? Are they appropriate for the associated vulnerability?
5. Information Security System Authorizations
Now that you have a comprehensive view of your critical data, defined the threats, and established controls for your security management process, how do you ensure its effectiveness?
The authorization stage will help you make this determination:
- Are the right individuals notified of on-going threats? Is this done promptly?
- Review the alerts generated by your controls – emails, documents, graphs, etc. Who is tracking response to warnings?
This authorization stage must examine not only who is informed, but what actions are taken, and how quickly. When your data is at risk, the reaction time is essential to minimize data theft or loss.
6. Risk Monitoring
Adopting an information risk management framework is critical to providing a secure environment for your technical assets.
Implementing a sophisticated software-driven system of controls and alert management is an effective part of a risk treatment plan.
Continuous monitoring and analysis are critical. Cyber thieves develop new methods of attacking your network and data warehouses daily. To keep pace with this onslaught of activity, you must revisit your reporting, alerts, and metrics regularly.

Create an Effective Security Risk Management Program
Defeating cybercriminals and halting internal threats is a challenging process. Bringing data integrity and availability to your enterprise risk management is essential to your employees, customers, and shareholders.
Creating your risk management process and take strategic steps to make data security a fundamental part of conducting business.
In summary, best practices include:
- Implement technology solutions to detect and eradicate threats before data is compromised.
- Establish a security office with accountability.
- Ensure compliance with security policies.
- Make data analysis a collaborative effort between IT and business stakeholders.
- Ensure alerts and reporting are meaningful and effectively routed.
Conducting a complete IT security assessment and managing enterprise risk is essential to identify vulnerability issues.
Develop a comprehensive approach to information security.
PhoenixNAP incorporates infrastructure and software solutions to provide our customers with reliable, essential information technology services:
- High-performance, scalable Cloud services
- Dedicated servers and redundant systems
- Complete software solutions for ISRM
- Disaster recovery services including backup and restore functions
Security is our core focus, providing control and protection of your network and critical data.
Contact our professionals today to discuss how our services can be tailored to provide your company with a global security solution.
Recent Posts
Definitive Guide For Preventing and Detecting Ransomware
In this article you will learn:
- Best practices to implement immediately to protect your organization from ransomware.
- Why you should be using threat detection to protect your data from hackers.
- What to do if you become a ransomware victim. Should you pay the ransom? You may be surprised by what the data says.
- Where you should be backing up your data. Hint, the answer is more than one location.
- Preventing ransomware starts with employee awareness.
Ransomware has become a lucrative tactic for cybercriminals.
No business is immune from the threat of ransomware.
When your systems come under ransomware attack, it can be a frightening and challenging situation to manage. Once malware infects a machine, it attacks specific files—or even your entire hard drive and locks you out of your own data.
Ransomware is on the rise with an increase of nearly 750 percent in the last year.
Cybercrime realted damages are expected to hit $6 trillion by 2021.
The best way to stop ransomware is to be proactive by preventing attacks from happening in the first place. In this article, we will discuss how to prevent and avoid ransomware.
What is Ransomware? How Does it Work?
All forms of ransomware share a common goal. To lock your hard drive or encrypt your files and demand money to access your data.
Ransomware is one of many types of malware or malicious software that uses encryption to hold your data for ransom.
It is a form of malware that often targets both human and technical weaknesses by attempting to deny an organization the availability of its most sensitive data and/or systems.
These attacks on cybersecurity can range from malware locking system to full encryption of files and resources until a ransom is paid.
A bad actor uses a phishing attack or other form of hacking to gain entry into a computer system. One way ransomware gets on your computer is in the form of email attachments that you accidentally download. Once infected with ransomware, the virus encrypts your files and prevents access.
The hacker then makes it clear that the information is stolen and offers to give that information back if the victim pays a ransom.
Victims are often asked to pay the ransom in the form of Bitcoins. If the ransom is paid, the cybercriminals may unlock the data or send a key to for the encrypted files. Or, they may not unlock anything after payment, as we discuss later.

How To Avoid & Prevent Ransomware
Ransomware is particularly insidious. Although ransomware often travels through email, it has also been known to take advantage of backdoors or vulnerabilities.
Here are some ways you can avoid falling victim and be locked out of your own data.
1. Backup Your Systems, Locally & In The Cloud
The first step to take is to always backup your system. Locally, and offsite.
This is essential. First, it will keep your information backed up in a safe area that hackers cannot easily access. Secondly, it will make it easier for you to wipe your old system and repair it with backup files in case of an attack.
Failure to back up your system can cause irreparable damage.
Use a cloud backup solution to protect your data. By protecting your data in the cloud, you keep it safe from infection by ransomware. Cloud backups introduce redundancy and add an extra layer of protection.
Have multiple backups just in case the last back up got overwritten with encrypted ransomware files.
2. Segment Network Access
Limit the data an attacker can access with network segmentation security. With dynamic control access, you help ensure that your entire network security is not compromised in a single attack. Segregate your network into distinct zones, each requiring different credentials.
3. Early Threat Detection Systems
You can install ransomware protection software that will help identify potential attacks. Early unified threat management programs can find intrusions as they happen and prevent them. These programs often offer gateway antivirus software as well.
Use a traditional firewall that will block unauthorized access to your computer or network. Couple this with a program that filters web content specifically focused on sites that may introduce malware. Also, use email security best practices and spam filtering to keep unwanted attachments from your email inbox.
Windows offers a function called Group Policy that allows you to define how a group of users can use your system. It can block the execution of files from your local folders. Such folders include temporary folders and the download folder. This stops attacks that begin by placing malware in a local folder that then opens and infects the computer system.
Make sure to download and install any software updates or patches for systems you use. These updates improve how well your computers work, and they also repair vulnerable spots in security. This can help you keep out attackers who might want to exploit software vulnerabilities.
You can even use software designed to detect attacks after they have begun so the user can take measures to stop it. This can include removing the computer from the network, initiating a scan, and notifying the IT department.
4. Install Anti Malware / Ransomware Software
Don’t assume you have the latest antivirus to protect against ransomware. Your security software should consist of antivirus, anti-malware, and anti-ransomware protection.
It is also crucial to regularly update your virus definitions.
5. Run Frequent Scheduled Security Scans
All the security software on your system does no good if you aren’t running scans on your computers and mobile devices regularly.
These scans are your second layer of defense in the security software. They detect threats that your real-time checker may not be able to find.

6. Create Restore & Recovery Points
If using windows, go to the control panel and enter in System Restore into the search function. Once you’re in System Restore, you can turn on system protection and create regular restore points. You should also create restore points.
In the event you are locked out, you may be able to use a restore point to recover your system.
7. Train Your Employees and Educate Yourself
Often, a ransomware attack can be traced back to poor employee cybersecurity practices.
Companies and individuals often fall victim to ransomware because of a lack of training and education.
Ransomware preys on a user’s inattentiveness, expecting an anti ransomware program to do their jobs for them. Nothing protects a system like human vigilance.
Employees should recognize the signs of a phishing attack. Keep yourself and your employees up-to-date on the latest cyber attacks and ransomware. Make sure they know not to click on executable files or unknown links.
Regular employee security awareness training will remind your staff of their roles in preventing ransomware attacks from getting through to your systems.
Stress the importance of examining links and attachments to make sure they are from a reliable source. Warn staff about the dangers of giving out company or personal information in response to an email, letter, or phone call.
For employees who work remotely, make it clear that they should never use public Wi-Fi because hackers can easily break in through this kind of connection.
Also, make it clear that anyone reporting suspicious activity does not have to be sure a problem exists. Waiting until an attack is happening can mean responding too late. Have an open door and encourage employees to express concerns.
8. Enforce Strong Password Security
Utilize a password management strategy that incorporates an enterprise password manager and best practices of password security.
According to background check service Instant Checkmate, 3 out of 4 people use the same password for multiple sites . More staggering is that one-third use a significantly weak password (like abc1234 or 123456. Use multiple strong passwords, especially for sensitive information.
9. Think Before Clicking
If you receive an email with the attachments .exe, .vbs, or .scr, even from a “trusted” source, don’t open.
These are executable files that are most likely not from the source you think it’s from. Chances are the executables are ransomware or a virus. Likewise, be especially vigilant with links supposedly sent by “friends,” who may have their addresses spoofed. When sent a link, be sure the sending is someone you know and trust before clicking on it. Otherwise, it may be a link to a webpage that may download ransomware onto your machine.
10. Set Up Viewable File Extensions
Windows allows you to set up your computers to show the file extensions when you look at a file. The file extension is the dot followed by three or four letters, indicating the type of file.
So, .pdf is a PDF file, .docx is a Window’s Word document, etc. This will allow you to see if the file is an executable, such as a .exe, vbs, or .scr. This will reduce the chance of accidentally opening a dangerous file and executing ransomware.

11. Block Unknown Email Addresses and Attachments On Your Mail Server
Start filtering out and rejecting incoming mail with executable attachments. Also, set up your mail server to reject addresses of known spammers and malware. Icann has listings of free or low-cost services which can help you do that.
If you don’t have a mail server in-house, be sure that your security services can at least filter incoming mail.
12. Add Virus Control At The Email Server Level
Most attacks start with a suspicious email that a victim is fooled into opening. After opening it or clicking on a link, the virus is unleashed and can do its dirty work.
Installing anti-virus and malware software on your email server can act as a safeguard.
13. Apply Software and OS patches ASAP
Malware often takes advantage of security loopholes and bugs within operating systems or software. This is why it is essential to install the latest updates and patches on your computers and mobile devices.
Staying with archaic versions is a guaranteed way of making your systems and their data a target. For example, the ransomware worm, WannaCry, took advantage of a security breach in older versions of Windows, making computers that had not been patched vulnerable. WannaCry spread through the Internet, infecting computers without a patch — and without user interaction. Had the companies that were attacked by WannaCry kept their computer operating systems up to date, there would’ve been no outbreak. A costly lesson for users and companies.
14. Block Vulnerable Plug-Ins
There are many types of web plug-ins that hackers use to infect your computers. Two of the most common are Java and Flash. These programs are standard on a lot of sites and may be easy to attack. As a result, it is important to update them regularly to ensure they don’t get infected by viruses.
You may even want to go the extra step of completely blocking these programs.
15. Limit Internet Connectivity
If you have genuinely critical data, your next step may be keeping your network private and away from the Internet entirely.
After all, if you don’t bring anything into your network, your computers are unlikely to have ransomware downloaded to them. This may be impractical seeing that many companies rely on the Internet and email to do their business, but keeping Internet access away from critical servers may be a way to combat ransomware and viruses.
How to Detect Ransomware
Unfortunately, if you have failed to avoid ransomware, your first sign might be an encrypted or locked drive and a ransom note.
If you run your malware and virus checker frequently with updated virus and malware definitions, your security software may detect the ransomware and alert you to its presence. You can then opt to quarantine and delete the ransomware.
What to Do If Your Computer Is Infected With Ransomware
Hopefully, you never have to deal with your data being held hostage.
Minimize damage by immediately isolating the machine — this critical to prevent further access to your network.
At this stage, rebuild your system and download your backups.
You may be able to recover many resources with a system restore. That is if you can access the system and are not locked out of it.
Otherwise, you’ll have to reinstall everything from backups. If you’ve backed up your crucial data on a cloud server, you should be able to find a safe restore point.
Should You Pay the Ransom?
You may be tempted to pay the ransomers to get your data back.
This is a terrible idea.
According to a Symantec ransomware report, only 47% of people who pay the ransom get their files back.
Every time someone pays the ransom, criminals gain more confidence and will likely keep hurting businesses.
Not only will you encourage them to continue, but you have no idea if they will free your computer. What’s more, even if they release your data, they may still use your information.
In other words, don’t pay. You’re stuck with making a bad situation even worse by paying the ransom. The data is gone (unless you have backups) and, if you pay them, your money is likely gone for good as well.
To quote FBI Cyber Division Assistant Director James Trainor:
“The FBI does not advocate paying a ransom to an adversary. Paying a ransom does not guarantee that an organization will regain access to their data. In fact, some individuals or organizations were never provided with decryption keys after paying a ransom. Paying emboldens the adversary to target other organizations for profit and offers a lucrative environment for other criminals to become involved.”
Finally, by paying a ransom, an organization is funding illicit activity associated with criminal groups, including potential terrorist groups, who likely will continue to target an organization.

Have a Disaster Recovery Plan
Proactive ransomware detection includes active incident response, business continuity, and a plan for disaster recovery.
A plan is essential and should be the cornerstone of a company’s security strategy.
- Set up a communication plan detailing who should contact who.
- Determine what equipment you would need to rent or buy to keep operations going. Plan for your current hardware to be unavailable for days.
- Write explicit instructions on where data is stored and how to retrieve it.
- Implement a policy of backing up regularly to prevent ransomware from causing data loss.
- Implement a disaster recovery service.
- Provide phone numbers for contacting vendors who may be able to restore the systems they provide for you.
Prevent a Ransomware Attack With Preparation
Companies must remain vigilant in today’s era of data breaches and ransomware attacks.
Learn the proper steps to prevent, detect and recover from ransomware, and you can minimize its impact on your business. Use these tips to keep your organization’s information assets safe and stop a ransomware attack before it starts.
Use a trusted data center provider and vendors. Perform due diligence to make sure they are trustworthy.
Recent Posts
11 Steps To Defend Against the Top Cybersecurity Threats in Healthcare
Imagine your patient data being held hostage by hackers. Security threats in healthcare are a genuine concern.
The U.K.’s healthcare industry recently suffered one of the largest cyber breaches ever.
WannaCry, a fast-moving global ransomware attack shut the NHS systems down for several hours. Healthcare institutions all over the country were unable to access patient records or schedule procedures. Appointments were postponed, and operations got canceled while experts worked to resolve the issue.
Although the attack impacted other companies and industries as well, the poorly defended healthcare system took a more significant hit. It was just one of the incidents that showed the extent to which healthcare institutions are vulnerable to cyber threats. Learn how to be prepared against the latest cybersecurity threats in healthcare.

11 Tips To Prevent Cyber Attacks & Security Breaches in Healthcare
1. Consider threat entry points
An entry point is a generic term for a vulnerability in your system that can be easily penetrated by hackers. By exploiting this vulnerability, hackers can deploy a virus to slow your network, access critical health information, or remove defenses to make your system more accessible in the future.
Malware can be introduced from any vulnerable spot in your network or operating system.
An employee can unknowingly click a file, download unauthorized software, or load a contaminated thumb drive. Also, when strong secure passwords are not used, an easy entry point for hackers is created.
Moreover, medical software and web applications used for storing patient data were found to contain numerous vulnerabilities. Healthcare cybersecurity statistics by Kaspersky Security Bulletin found open access to about 1500 devices that healthcare professionals use to process patient images.
2. Learn about ransomware attacks
A ransomware attack is a specific type of malware which threatens to lock one computer or an entire network unless a certain amount of money is paid.
The ransom is not necessarily an impossibly high figure either. Even demanding a few hundred dollars from a business could still be easy money for a hacker, and more manageable for individuals or companies to come up with to get their computers back.
3. Create a ransomware policy
One disabled computer does not necessarily bring much damage. However, the risk of not being able to access larger sectors where electronic records reside could be disruptive, even dangerous to patient treatment.
When such an incident happens, employees must immediately contact someone on their healthcare IT team. This should be part of their security training and overall security awareness. They must follow healthcare organization procedures when they see a ransomware message, instead of trying to resolve the matter themselves.
Authorities warn against paying ransomware culprits since there’s no guarantee a key will be given. Criminals may also re-target companies that paid them in the past.
Many companies solve ransomware attacks by calling the police and then wiping the affected computer and restoring it to a previous state.
Cloud data backups can make it easy to restore systems in the events of an attack. Disaster recovery planning should be done before a cyber security threat occurs.

Employee Roles in Security in Healthcare
4. Focus on Employee Security training
Cybersecurity professionals employ robust firewalls and other defenses, but the human factor remains a weak link as was displayed in the WannaCry exploit.
To minimize human error, system admins need to remind all staff about risky behavior continually. This can include anything from downloading unauthorized software and creating weak passwords to visiting malicious websites or using infected devices.
Educate employees on how to recognize legitimate and suspicious emails, threats, and sites so they can avoid phishing attacks. (Unusual colors in logos or different vocabulary are both warning signs). Training should be refreshed regularly or customized for different employee groups.
5. Create or expand security Measure risk levels
Different employee groups should be provided with varying privileges of network access.
At a hospital, nurses may need to share info with other staff in their unit, but there’s no reason for other departments to see this. Visiting doctors may receive access to only their patient’s info. Security settings should monitor for unauthorized access or access attempts at every level.
Chris Leffel from Digital Guardian suggests training/education first, followed by restricting specific apps, areas and patient healthcare data. He also recommends requiring multi-factor authentication, which is an additional layer of protection.
6. Healthcare Industry Cybersecurity Should Go beyond employee access
Patient concerns about sensitive data security and IT in healthcare should be kept in mind when creating safer, stronger systems, or improving cybersecurity frameworks after a hospital was hacked.
Patients are often already nervous and don’t want to worry about data security. Likewise, system administrators should also make sure that threat intelligence funding remains a priority, which means continuing to invest in security initiatives.
Publicizing you have taken extra steps in your patient security efforts will drive more security-conscious patients your way. Patients care.

7. Protect Health Data on ‘smart’ equipment
Desktops, laptops, mobile phones, and all medical devices, especially those connected to networks, should be monitored and have anti-virus protection, firewalls, or related defenses.
Today’s medical centers also possess other connected electronic equipment such as medical devices like IV pumps or insulin monitors that remotely sync patient information directly to a doctor’s tablet or a nurse’s station. Many of these interconnected devices could potentially be hacked, disrupted, or disabled, which could dramatically impact patient care.
8. Consider cloud migration For Your Data
The cloud offers a secure and flexible solution for healthcare data storage and backup. It also provides a possibility to scale resources on-demand, which can bring significant improvements in the way healthcare organizations manage their data.
Cloud-based backup and disaster recovery solutions ensure that patient records remain available even in case of a breach or downtime. Combined with the option to control access to data, these solutions can provide the needed level of security.
With the cloud, a healthcare organization does not have to invest a lot in critical infrastructure for data storage. HIPAA Compliant Cloud Storage allows for significant IT cost cuts, as no hardware investments are needed. It also brings about a new level of flexibility as an institution’s data storage needs change.
9. Ensure vendors Are Compliant
The Healthcare Industry Cybersecurity Task Force, established by the U.S. Department of Health and Human Services and Department of Homeland Security, warned providers of areas of vulnerability in the supply chain. One of their requirements is for vendors to take proper steps to monitor and detect threats, as well as to limit access to their systems.
Insurance companies, infrastructure providers, and any other healthcare business partners must have spotless security records to be able to protect medical information. This is especially important for organizations that outsource IT personnel from third-party vendors.
10. How HIPAA Compliance can help
Larger healthcare organizations have at least one person dedicated to ensuring HIPAA compliance. Their primary role is creating and enforcing security protocols, as well as developing a comprehensive privacy policy that follows HIPAA recommendations.
Educating employees on HIPAA regulations can contribute to creating a security culture. It also helps to assemble specific HIPAA teams, which can also share suggestions on how to restrict healthcare data or further cyber defenses in the organization.
HIPAA compliance is an essential standard to follow when handling healthcare data or working with healthcare institutions. Its impact on the overall improvement of medical data safety is significant, and this is why everyone in healthcare should be aware of it.
11. Push a top-down Security Program
Every medical facility likely has a security staff and an IT team, but they rarely overlap. Adding healthcare cybersecurity duties at a managerial level, even as an executive position, can bring multiple benefits.
It can make sure correct initiatives are created, launched, and enforced, as well as that funding for security initiatives is available. With cybersecurity threats, being proactive is the key to ensuring safety long term. Regular risk assessments should be part of any healthcare provider’s threat management program.
Healthcare: $3.62 Million Per Breach
Cybersecurity in the healthcare industry is under attack. Cybersecurity threats keep hospital IT teams up at night, especially since attacks on medical providers are expected to increase in 2018.
The latest trends in cybersecurity might be related to the fact that healthcare institutions are moving towards easier sharing of electronic records. That and a potentially nice payoff for patient information or financial records make healthcare a hot target for hackers.
For medical centers themselves, hacks can be costly. The average data breach costs a company $3.62 Million. This includes stolen funds, days spent investigating and repairing, as well as paying any fines or ransoms. Attacks can also result in a loss of records and patient information, let alone long-lasting damage to the institution’s reputation.
As much as hospitals and medical centers try to protect patient privacy, security vulnerabilities come from all sides. A great way to keep up with the latest security threats is to attend a data security conference.
Healthcare organizations want to send patient info to colleagues for quick consultations. Technicians pull and store sensitive data easily from electronic equipment. Patients email or text their doctor directly without going through receptionists, while admins often send a patient record to insurance companies or pharmacies.
So the industry finds itself in a dangerous position of trying to use more digital tools to improve the patient experience while following a legal requirement to safeguard privacy. No wonder IT teams continuously wonder which hospital will be hacked next.
The truth is that healthcare institutions are under a significant threat. Those looking to improve security should start with the steps outlined below.
In Closing, The Healthcare Industry Will Continue to Be Vulnerable
Healthcare facilities are often poorly equipped to defend their network activities and medical records security. However, being proactive and aware of ever-changing cybersecurity risks can help change the setting for the better.
Of course, education alone won’t help much without battle-ready infrastructure. With the assistance of healthcare industry cybersecurity experts like phoenixNAP, your healthcare organization can ensure security on multiple levels.
From backup and disaster recovery solutions to assistance creating or expanding a secure presence, our service portfolio is built for maximum security.
Do not let a disaster like WannaCry happen to your company. Start building your risk management program today.
We have created a free HIPPA Compliance Checklist.
Recent Posts
Bare Metal Backup, Restore, & Recovery: 7 Things IT Pros Need To Know
Many technology professional initially think of bare metal recovery as a tool for emergencies only.
A disaster that impacts your network can take any number of forms. A flood, storm or fire could wipe out your data center or systems; hackers could hold your network for ransom or a malicious insider could let cybercriminals in. In the end, it does not matter if you had a careless employee or faced the wrath of Mother Nature — the result is a catastrophic failure of your network and the total interruption of your organization’s ability to do business.
A backup recovery strategy is paramount. Most incidents allow for recovery.
Simple turn things over to an IT team or even a virtual program and wait for the restoration of your systems. But for those cases where you are unaware of the extent of damage or that destroy your systems beyond repair, bare metal disaster recovery may be needed.
What is Bare Metal Backup?
With traditional bare metal recovery methods, you move information from one physical machine to another.
Enterprise systems allow you to try a variety of bare metal backup combinations.
This can include moving a physical machine to a virtual server; a virtual server to a physical machine; or a virtual machine to another virtual server.
Some methods require converting your original system’s physical image into a virtual image. Utility tools for this include dd in Linux; ddr in IBM VM//370; WBadmin in Windows Server 2008; and Recovery Environment in Windows.
You can also use your original machine information to create multiple identical virtual or physical machines.
These can be useful if you’ve made an optimal machine or a server configuration you like. Backups of your original machine can be handy if you ever need more versions. For instance, you may want to increase space in a server volume.
Your virtual servers will be able to come online quickly from the backup. This is a better option than taking a long time to create something new from scratch each time.
Likewise, if one of your virtual servers appears to be crashing, you can make a quick identical copy.
What is Bare Metal Restore or Recovery?
Bare metal recovery or bare metal restoration is a type of disaster recovery planning for your network.
This is used after a catastrophic failure, breach or emergency; the “bare metal” part of the term refers to starting almost from scratch. When an IT expert performs this task, they are working from the very beginning and recovering, reinstalling and rebuilding your system from the ground (or bare metal) up.
This approach means starting with clean, working hardware and reinstalling operating systems and other software; this way you know your network is being restored on a new, error-free base without any lingering risk or problems.
Begin bare metal restore by saving an image of your existing machine or server onto an ISO file or placing it onto a thumb drive or a network server. Then load the image or file onto your ‘blank’ machine.
The term ‘bare metal’ describes how the second machine contains just a hard drive, a motherboard, processor and a few drivers.
If you perform the formatting correctly, you’ll be able to bring back your settings and data quickly. This can be done in a few hours, faster than a full rebuild. Re-installing all applications and drivers could take days.
A lot could go wrong if recovery takes place incorrectly. If the motherboards, processors or BIOS differ even slightly, the new machine may not boot. Data loss, corrupt or general data failure all could take place.
Newer tools improve the odds of data being adequately restored. Individual drivers can modify system settings on the second machine’s CPU. This can make sure an adequate boot-up occurs even if the hardware is different.
Bare metal restore is recommended as a smart disaster recovery method. Loading data onto a new machine takes place quickly. This can be useful for critical situations such as hardware failure or cyber attacks.
While this is a restore of last resort (no one wants to have to do it), it does provide you with peace of mind about the process and your network’s integrity.
If your disaster was a breach, managing security risk is an essential part of recovery resume your normal functions with confidence.

Benefits of Bare Metal Restoration
Bare metal restoration can be useful for emergencies, virtual environments and hybrid cloud/dedicated systems.
At the same time, a BMR shouldn’t be thought of as a continuous server backup.
Most standard system backup tools allow users to designate which items should be saved. This often includes documents, folders and application data, not the applications themselves. Creating a full backup also may allow you to choose when and how often it takes place.
Another type of backup is a system state, which allows you to recover your operating system files even with a lost registry.
A restoration, on the other hand, copies over an entire drive, including applications. It can be compared to a one-time snapshot of your machine or server at a specific time.
Bare metal restoration is similar to Windows System Restore. This tool restarts your system from a previous save point. A BMR does the same task but does so from within a different machine.
A bare metal restoration can also include a system state backup and disaster recovery.
Data Backup vs. Data Recovery
Bare metal recovery can go beyond emergencies or multiple virtual machines. It can also enhance cloud architecture, improve security and conserve resources. Another use has been found for bare metal recovery. It can be a way to create multiple copies along with backups of virtual machines easily.
You can also create a bare metal dedicated server. This can be useful for companies that use cloud services but have traffic spikes during peak times. For instance, a game server could demand varying cloud storage space and bandwidth throughout the day. These types of situations often require higher costs.
Off-loading data to a bare metal dedicated server instead of the cloud can offer:
- More customization. A dedicated server makes it easy to customize server settings instead of the standard options from a shared cloud.
- Higher performance. Bare metal servers remain separate from shared cloud resources, so there’s less processing demand or lag and no type 1 or 2 hypervisor required.
- Stronger security. A bare metal dedicated server stays private from other shared cloud backup services. The ‘single tenant’ won’t need to co-exist with other cloud businesses, so may be ideal for storing sensitive information.
- Cost Savings. Lower demand, bandwidth, and traffic can mean IT cost savings.

Need to perform a Bare Metal Backup Recovery?
If you have suffered a catastrophic failure and all other recovery measures have failed, it is likely time to consider bare metal recovery. In some cases, your internal team or external data recovery experts may be called in to review the incident and determine the extent of the damage.
Once other measures have been exhausted, bare metal disaster recovery is the final option. How swiftly you decide to proceed with this option will depend on:
- The extent of the damage to your systems
- Type of damage
- Overall possibility of recovery
- How long it takes to troubleshoot or try other, less intensive methods first
What to Expect with During Restoration
Once other avenues have been exhausted and your team makes the decision to go with this form of data recovery, your network will be rebuilt from the ground up:
- Physical location repair: If your emergency was weather-related, fire-related or otherwise resulted in physical damage. Then the first step for any recovery will be restoring and rebuilding the physical setting. Structural work, waterproofing, and HVAC work may be required to ensure that the space is not only safe for your team but that your servers, workstations and other pieces will operate at peak efficiency. This is also the time to add in any additional physical security or measures to prevent attacks in the future.
- New Hardware: This is the “bare metal” referred to in the name of this recovery process. You’ll add new, clean and bare hardware to your server area; by starting from the metal up, you can be sure your pieces are untainted and ready to use. Once these are installed, you’ll be able to recover and rebuild your system.
- Operating Systems: Your operating systems will be added to the hardware to create an optimal environment for the platforms, programs and processes your business relies on.
- Application Installation: The apps you use to run your business will be added to your system. The fresh application ensures that you are working with pristine equipment and creating a new network that won’t be affected by the recent emergency.
- Clean Data Restoration: Backup data that is unaffected by whatever happened to mess up your network in the first place can be added in at this time. Whether you have disks, cloud recovery or another backup, it can be restored into your new system.
- Add Users: Adding back in your team and allowing them to access your restored system is the next step. Ideally, you’ll have clarified your password requirements and ensure that any BYOD (Bring Your Own Device) programs are secure as well.
- Plan for next time: If you already have bare metal disaster recovery software in place, this process is far more simple. Once you have been through a recovery of this nature, it is a good idea to think ahead to next time. What process, material, backup or functionality would have made it easier for you to recover your data? Is there a solution that would complete the task more quickly, allowing you to resolve the issue without a lot of downtime rapidly? Learning from this experience can help you be better prepared for the future and ensure that you don’t have to worry about what comes next.
Why Disaster Recovery?
Every business needs a data recovery plan.
According to the United States Department of Homeland Security, every business that has or relies on a network should have an IT disaster plan.
A whopping 60% of small to mid-sized businesses close forever after a successful breach or failing to a prevent ransomware attack. They can’t afford the downtime and recovery process. Being prepared for any eventuality as part of a business continuity plan can help ensure that your organization avoids this fate.
The need to be prepared has grown in recent years. Criminals have gotten more sophisticated as organizations have begun relying on technology more than ever. The increased reliance on technology coupled with an ongoing and steady increase in risk means that any business with a network needs to be fully prepared for an emergency. This includes preparing for the worst case scenario with bare metal disaster recovery capabilities.
Planning Ahead With Bare Metal Backup and Recovery
Take steps now with server backup to ensure you can recover data later.
Just being aware that threats exist and the extensive damage they can cause is a step in the right direction. Understanding how bare metal disaster recovery differs from general recovery and what is needed for the process allows you to incorporate this into your emergency and business continuity planning.
You have a wide range of options to choose from when it comes to a bare metal disaster recovery system. Select one before you need it. This is the key to a swift and efficient recovery.
If you already have a disaster plan in place and have backed up data, the process will be fast, easy and effective.
If you have to learn about the recovery process after the fact, you’ll face a more complex and less user-friendly process. The resulting delays can have a significant impact on your business. Taking steps now to protect your network can save time, money and headache later.
You’ll be ready for anything, even if the worst happens.
Recent Posts
Cloud Security Tips to Reduce Security Risks, Threats, & Vulnerabilities
Do you assume that your data in the cloud is backed up and safe from threats? Not so fast.
With a record number of cybersecurity attacks taking place in 2018, it is clear that all data is under threat.
Everyone always thinks “It cannot happen to me.” The reality is, no network is 100% safe from hackers.
According to the Kaspersky Lab, ransomware rose by over 250% in 2018 and continues to trend in a very frightening direction. Following the advice presented here is the ultimate insurance policy from the crippling effects of a significant data loss in the cloud.
How do you start securing your data in the cloud? What are the best practices to keep your data protected in the cloud? How safe is cloud computing?
To help you jump-start your security strategy, we invited experts to share their advice on Cloud Security Risks and Threats.
Key Takeaways From Our Experts on Cloud Protection & Security Threats
- Accept that it may only be a matter of time before someone breaches your defenses, plan for it.
- Do not assume your data in the cloud is backed up.
- Enable two-factor authentication and IP-location to access cloud applications.
- Leverage encryption. Encrypt data at rest.
- The human element is among the biggest threats to your security.
- Implement a robust change control process, with weekly patch management cycle.
- Maintain offline copies of your data to in the event your cloud data is destroyed or held ransom.
- Contract with 24×7 security monitoring service.
- Have an security cident response plan.
- Utilize advanced firewall technology including WAF (Web Access Firewalls).
- Take advantage of application services, layering, and micro-segmentation.
1. Maintain Availability In The Cloud

When most people think about the topic of cloud-based security, they tend to think about Networking, Firewalls, Endpoint security, etc. Amazon defines cloud security as:
Security in the cloud is much like security in your on-premises data centers – only without the costs of maintaining facilities and hardware. In the cloud, you do not have to manage physical servers or storage devices. Instead, you use software-based security tools to monitor and protect the flow of information into and of out of your cloud resources.
But one often overlooked risk is maintaining availability. What I mean by that is more than just geo-redundancy or hardware redundancy, I am referring to making sure that your data and applications are covered. Cloud is not some magical place where all your worries disappear; a cloud is a place where all your fears are often easier and cheaper to multiply. Having a robust data protection strategy is key. Veeam has often been preaching about the “3-2-1 Rule” that was coined by Peter Krogh.
The rule states that you should have three copies of your data, storing them on two different media, and keeping one offsite. The one offsite is usually in the “cloud,” but what about when you are already in the cloud?
This is where I see most cloud issues arise, when people are already in the cloud they tend to store the data in the same cloud. This is why it is important to remember to have a detailed strategy when moving to the cloud. By leveraging things like Veeam agents to protect cloud workloads and Cloud Connect to send the backups offsite to maintain that availability outside of the same datacenter or cloud. Don’t assume that it is the providers’ job to protect your data because it is not.
2. Cloud MIgration is Outpacing The Evolution of Security Controls

According to a new survey conducted by ESG, 75% of organizations said that at least 20% of their sensitive data stored in public clouds is insufficiently secured. Also, 81% of those surveyed believe that on-premise data security is more mature than public cloud data.
Yet, businesses are migrating to the cloud faster than ever to maximize organizational benefits: an estimated 83% of business workloads will be in the cloud by 2020, according to LogicMonitor’s Cloud Vision 2020 report. What we have is an increasingly urgent situation in which organizations are migrating their sensitive data to the cloud for productivity purposes at a faster rate than security controls are evolving to protect that data.
Companies must look at solutions that control access to data within cloud shares based on the level of permission that user has, but they must also have the means to be alerted when that data is being accessed in unusual or suspicious ways, even by what appears to be a trusted user.
Remember that many hackers and insider leaks come from bad actors with stolen, legitimate credentials that allow them to move freely around in a cloud share, in search of valuable data to steal. Deception documents, called decoys, can also be an excellent tool to detect this. Decoys can alert security teams in the early stage of a cloud security breach to unusual behaviors, and can even fool a would-be cyber thief into thinking they have stolen something of value when in reality, it’s a highly convincing fake document. Then, there is the question of having control over documents even when they have been lifted out of the cloud share.
This is where many security solutions start to break down. Once a file has been downloaded from a cloud repository, how can you track where it travels and who looks at it? There must be more investment in technologies such as geofencing and telemetry to solve this.
3. Minimize Cloud Computing Threats and Vulnerabilities With a Security Plan

The Hybrid cloud continues to grow in popularity with the enterprise – mainly as the speed of deployment, scalability, and cost savings become more attractive to business. We continue to see infrastructure rapidly evolving into the cloud, which means security must develop at a similar pace. It is essential for the enterprise to work with a Cloud Service Provider who has a reliable approach to security in the cloud.
This means the partnership with your Cloud Provider is becoming increasingly important as you work together to understand and implement a security plan to keep your data secure.
Security controls like Multi-factor authentication, data encryption along with the level of compliance you require are all areas to focus on while building your security plan.
4. Never Stop Learning About Your Greatest Vulnerabilities
Isacc Kohen, CEO of Teramind
More and more companies are falling victim to the cloud, and it has to do with cloud misconfiguration and employee negligence.
1. The greatest threats to data security are your employees. Negligent or malicious, employees are one of the top reasons for malware infections and data loss. The reasons why malware attacks and phishing emails are common words in the news is because they are ‘easy’ ways for hackers to access data. Through social engineering, malicious criminals can ‘trick’ employees into giving passwords and credentials over to critical business and enterprise data systems. Ways to prevent this: an effective employee training program and employee monitoring that actively probes the system
2. Never stop learning. In an industry that is continuously changing and adapting, it is important to be updated on the latest trends and vulnerabilities. For example with the Internet of Things (IoT), we are only starting to see the ‘tip of the iceberg’ when it comes to protecting data over increased wi-fi connections and online data storage services. There’s more to develop with this story, and it will have a direct impact on small businesses in the future.
3. Research and understand how the storage works, then educate. We’ve heard the stories – when data is exposed through the cloud, many times it’s due to misconfiguration of the cloud settings. Employees need to understand the security nature of the application and that the settings can be easily tampered with and switched ‘on’ exposing data externally. Educate security awareness through training programs.
4. Limit your access points. An easy way to mitigate this, limit your access points. A common mistake with cloud exposure is due to when employees with access by mistake enable global permissions allowing the data exposed to an open connection. To mitigate, understand who and what has access to the data cloud – all access points – and monitor those connections thoroughly.
5. Monitoring the systems. Progressive and through. For long-term protection of data on the cloud, use a user-analytics and monitoring platform to detect breaches quicker. Monitoring and user analytics streamlines data and creates a standard ‘profile’ of the user – employee and computer. These analytics are integrated and following your most crucial data deposits, which you as the administrator indicated in the detection software. When specific cloud data is tampered with, moved or breached, the system will “ping” an administrator immediately indicating a change in character.
5. Consider Hybrid Solutions

There are several vital things to understand about security in the cloud:
1. Passwords are power – 80% of all password breaches could have been prevented by multifactor identification: by verifying your personal identity via text through to your phone or an email to your account, you can now be alerted when someone is trying to access your details.
One of the biggest culprits at the moment is weakened credentials. That means passwords, passkeys, and passphrases are stolen through phishing scams, keylogging, and brute-force attacks.
Passphrases are the new passwords. Random, easy-to-remember passphrases are much better than passwords, as they tend to be longer and more complicated.
MyDonkeysEatCheese47 is a complicated passphrase and unless you’re a donkey owner or a cheese-maker, unrelated to you. Remember to make use of upper and lowercase letters as well as the full range of punctuation.
2. Keep in touch with your hosting provider. Choose the right hosting provider – a reputable company with high-security standards in place. Communicate with them regularly as frequent interaction allows you to keep abreast of any changes or developing issues.
3. Consider a hybrid solution. Hybrid solutions allow for secure, static systems to store critical data in-house while at the same time opening up lower priority data to the greater versatility of the cloud.
6. Learn How Cloud Security Systems Work

Businesses need to make sure they evaluate cloud computing security risks and benefits. It is to make sure that they educate themselves on what it means to move into the cloud before taking that big leap from running systems in their own datacenter.
All too often I have seen a business migrate to the cloud without a plan or any knowledge about what it means to them and the security of their systems. They need to recognize that their software will be “living” on shared systems with other customers so if there is a breach of another customer’s platform, it may be possible for the attacker to compromise their system as well.
Likewise, cloud customers need to understand where their data will be stored, whether it will be only in the US, or the provider replicates to other systems that are on different continents. This may cause a real issue if the information is something sensitive like PII or information protected under HIPAA or some other regulatory statute. Lastly, the cloud customer needs to pay close attention to the Service Level Agreements (SLA) that the cloud provider adheres to and ensure that it mirrors their own SLA.
Moving to the cloud is a great way to free up computing resources and ensure uptime, but I always advise my clients to make a move in small steps so that they have time to gain an appreciation for what it means to be “in the cloud.”
7. Do Your Due Diligence In Securing the Cloud

Understand the type of data that you are putting into the cloud and the mandated security requirements around that data.
Once a business has an idea of the type of data they are looking to store in the cloud, they should have a firm understanding of the level of due diligence that is required when assessing different cloud providers. For example, if you are choosing a cloud service provider to host your Protected Health Information (PHI), you should require an assessment of security standards and HIPAA compliance before moving any data into the cloud.
Some good questions to ask when evaluating whether a cloud service provider is a fit for an organization concerned with securing that data include: Do you perform regular SOC audits and assessments? How do you protect against malicious activity? Do you conduct background checks on all employees? What types of systems do you have in place for employee monitoring, access determination, and audit trails?
8. Set up Access Controls and Security Permissions

While the cloud is a growing force in computing for its flexibility for scaling to meet the needs of a business and to increase collaboration across locations, it also raises security concerns with its potential for exposing vulnerabilities relatively out of your control.
For example, BYOD can be a challenge to secure if users are not regularly applying security patches and updates. The number one tip I would is to make the best use of available access controls.
Businesses need to utilize access controls to limit security permissions to allow only the actions related to the employees’ job functions. By limiting access, businesses assure critical files are available only to the staff needing them, therefore, reducing the chances of their exposure to the wrong parties. This control also makes it easier to revoke access rights immediately upon termination of employment to safeguard any sensitive content within no matter where the employee attempts access from remotely.
9. Understand the Pedigree and Processes of the Supplier or Vendor

The use of cloud technologies has allowed businesses of all sizes to drive performance improvements and gain efficiency with more remote working, higher availability and more flexibility.
However, with an increasing number of disparate systems deployed and so many cloud suppliers and software to choose from, retaining control over data security can become challenging. When looking to implement a cloud service, it is essential to thoroughly understand the pedigree and processes of the supplier/vendor who will provide the service. Industry standard security certifications are a great place to start. Suppliers who have an ISO 27001 certification have proven that they have met international information security management standards and should be held in higher regard than those without.
Gaining a full understanding of where your data will to geographically, who will have access to it, and whether it will be encrypted is key to being able to protect it. It is also important to know what the supplier’s processes are in the event of a data breach or loss or if there is downtime. Acceptable downtime should be set out in contracted Service Level Agreements (SLAs), which should be financially backed by them provide reassurance.
For organizations looking to utilize cloud platforms, there are cloud security threats to be aware of, who will have access to data? Where is the data stored? Is my data encrypted? But for the most part cloud platforms can answer these questions and have high levels of security. Organizations utilizing the clouds need to ensure that they are aware of data protection laws and regulations that affect data and also gain an accurate understanding of contractual agreements with cloud providers. How is data protected? Many regulations and industry standards will give guidance on the best way to store sensitive data.
Keeping unsecured or unencrypted copies of data can put it at higher risk. Gaining knowledge of security levels of cloud services is vital.
What are the retention policies, and do I have a backup? Cloud platforms can have widely varied uses, and this can cause (or prevent) issues. If data is being stored in a cloud platform, it could be vulnerable to cloud security risks such as ransomware or corruption so ensuring that multiple copies of data are retained or backed up can prevent this. Guaranteeing these processes have been taken improves the security levels of an organizations cloud platforms and gives an understanding of where any risk could come from
10. Use Strong Passwords and Multi-factor Authentication

Ensure that you require strong passwords for all cloud users, and preferably use multi-factor authentication.
According to the 2017 Verizon Data Breach Investigations Report, 81% of all hacking-related breaches leveraged either stolen and/or weak passwords. One of the most significant benefits of the Cloud is the ability to access company data from anywhere in the world on any device. On the flip side, from a security standpoint, anyone (aka “bad guys”) with a username and password can potentially access the businesses data. Forcing users to create strong passwords makes it vastly more difficult for hackers to use a brute force attack (guessing the password from multiple random characters.)
In addition to secure passwords, many cloud services today can utilize an employee’s cell phone as the secondary, physical security authentication piece in a multi-factor strategy, making this accessible and affordable for an organization to implement. Users would not only need to know the password but would need physical access to their cell phone to access their account.
Lastly, consider implementing a feature that would lock a user’s account after a predetermined amount of unsuccessful logins.
11. Enable IP-location Lockdown

Companies should enable two-factor authentication and IP-location lockdown to access to the cloud applications they use.
With 2FA, you add another challenge to the usual email/password combination by text message. With IP lockdown you can ring-fence access from your office IP or the IP of remote workers. If the platform does not support this, consider asking your provider to enable it.
Regarding actual cloud platform provision, provide a data at rest encryption option. At some point, this will become as ubiquitous as https (SSL/TLS). Should the unthinkable happen and data ends up in the wrong hands, i.e., a device gets stolen or forgotten on a train, then data at rest encryption is the last line of defense to prevent anyone from accessing your data without the right encryption keys. Even if they manage to steal it, they cannot use it. This, for example, would have ameliorated the recent Equifax breach.
12. Cloud Storage Security Solutions With VPN’s

Use VPNs (virtual private networks) whenever you connect to the cloud. VPNs are often used to semi-anonymize web traffic, usually by viewers that are geoblocked by accessing streaming services such as Netflix USA or BBC Player. They also provide a crucial layer of security for any device connecting to your cloud. Without a VPN, any potential intruder with a packet sniffer could determine what members were accessing your cloud account and potentially gain access to their login credentials.
Encrypt data at rest. If for any reason a user account is compromised on your public, private or hybrid cloud, the difference between data in plaintext vs. encrypted format can be measured in hundreds of thousands of dollars — specifically $229,000, the average cost of a cyber attack reported by the respondents of a survey conducted by the insurance company Hiscox. As recent events have shown, the process of encrypting and decrypting this data will prove far more painless than enduring its alternative.
Use two-factor authentication and single sign-on for all cloud-based accounts. Google, Facebook, and PayPal all utilize two-factor authentication, which requires the user to input a unique software-generated code into a form before signing into his/her account. Whether or not your business aspires to their stature, it can and should emulate this core component of their security strategy. Single sign-on simplifies access management, so one pair of user credentials signs the employee into all accounts. This way, system administrators only have one account to delete rather than several that can be forgotten and later re-accessed by the former employee.
13. Beware of the Human Element Risk

To paraphrase Shakespeare, the fault is not in the cloud; the responsibility is in us.
Storing sensitive data in the cloud is a good option for data security on many levels. However, regardless of how secure a technology may be, the human element will always present a potential security danger to be exploited by cybercriminals. Many past cloud security breached have proven not to be due to security lapses by the cloud technology, but rather by actions of individual users of the cloud.
They have unknowingly provided their usernames and passwords to cybercriminals who, through spear phishing emails, phone calls or text messages persuade people to give the critical information necessary to access the cloud account.
The best way to avoid this problem, along with better education of employees to recognize and prevent spear phishing, is to use dual factor authentication such as having a one time code sent to the employee’s cell phone whenever the cloud account is attempted to be accessed.
14. Ensure Data Retrieval From A Cloud Vendor

1. Two-factor authentication protects against account fraud. Many users fail victim to email phishing attempts where bad actors dupe the victim into entering their login information on a fake website. The bad actor can then log in to the real site as the victim, and do all sorts of damage depending on the site application and the user access. 2FA ensures a second code must be entered when logging into the application. Usually, a code sent to the user’s phone.
2. Ensuring you own your data and that can retrieve it in the event you no longer want to do business with the cloud vendor is imperative. Most legitimate cloud vendors should specify in their terms that the customer owns their data. Next, you need to confirm you can extract or export the data in some usable format, or that the cloud vendor will provide it to you on request.
15. Real Time and Continuous Monitoring

1. Create Real-Time Security Observability & Continuous Systems Monitoring
While monitoring is essential in any data environment, it’s critical to emphasize that changes in modern cloud environments, especially those of SaaS environments, tend to occur more frequently; their impacts are felt immediately.
The results can be dramatic because of the nature of elastic infrastructure. At any time, someone’s accidental or malicious actions could severely impact the security of your development, production, or test systems.
Running a modern infrastructure without real-time security observability and continuous monitoring is like flying blind. You have no insight into what’s happening in your environment, and no way to start immediate mitigation when an issue arises. You need to monitor application and host-based access to understand the state of your application over time.
- Monitoring systems for manual user actions. This is especially important in the current DevOps world where engineers are likely to have access to production. It’s possible they are managing systems using manual tasks, so use this as an opportunity to identify processes that are suited for automation.
- Tracking application performance over time to help detect anomalies. Understanding “who did what and when” is fundamental to investigating changes that are occurring in your environment.
2. Set & Continuously Monitor Configuration Settings
Security configurations in cloud environments such as Amazon Direct Connect can be complicated, and it is easy to inadvertently leave access to your systems and data open to the world, as has been proven by all the recent stories about S3 leaks.
Given the changeable (and sometimes volatile) nature of SaaS environments, where services can be created and removed in real time on an ongoing basis, failure to configure services appropriately, and failure to monitor settings can jeopardize security. Ultimately, this will erode the trust that customers are placing in you to protect their data.
By setting configurations against an established baseline and continuously monitoring them, you can avoid problems when setting up services, and you can detect and respond to configuration issues more quickly when they occur.
3. Align Security & Operations Priorities for Cloud Security Solutions and Infrastructure
Good security is indistinguishable from proper operations. Too often these teams are at odds inside an organization. Security is sometimes seen as slowing down a business— overly focused on policing the activities of Dev and Ops teams. But security can be a business enabler.
Security should leverage automation testing tools, security controls and monitoring inside an organization — across network management, user access, the configuration of infrastructure, and vulnerability management across application layer — will drive the business forward, reducing risk across the attack surface and maintaining operational availability.
16. Use Auditing Tools to Secure Data In the Cloud

1. Use an auditing tool so that you know what all you have in the cloud and what all of your users are using in the cloud. You can’t secure data that you don’t know about.
2. In addition to finding out what services are being run on your network, find out how and why those services are being used, by whom and when.
3. Make that auditing process a routine part of your network monitoring, not just a one-time event. Moreover, if you don’t have the bandwidth for that, outsource that auditing routine to a qualified third party like US Cloud.
17. Most Breaches Start At Simple Unsecured Points

The cloud is very secure, but to ensure you are keeping company data secure it is important to configure the cloud properly.
For AWS specifically, AWS Config is the tool best utilized to do this. AWS, when configured the right way, is one of the most secure cloud computing environments in the world. However, most data breaches are not hackers leveraging complex programs to get access to critical data, but rather it’s the simple unsecured points, the low hanging fruit, that makes company data vulnerable.
Even with the best cloud security, human error is often to blame for the most critical gap or breach in protection. Having routines to validate continuous configuration accuracy is the most underused and under-appreciated metric for keeping company data secure in the cloud.
18. Ask Your Cloud Vendor Key Security Questions

When exploring the possibilities of moving to a cloud-based solution, you should ensure adequate supports are in place should a breach occur. Make sure you ask the following questions before signing an agreement with a cloud-based provider:
Question: How many third-parties does the provider use to facilitate their service?
Reason for question (Reason): Processes and documentation will need to be updated to include procedural safeguards and coordination with the cloud-based solution. Additionally, the level of security provided by the cloud-based provider should be clearly understood. Increased levels of security made need to be added to meet privacy and security requirements for the data being stored.
Question: How will you be notified if a breach of their systems occurs and will they assist your company in the notification of your clients/customers?
Reason: By adding a cloud-based solution to the storage of your data also adds a new dimension of time to factor into the notification requirements that may apply to your data should a breach occur. These timing factors should be incorporated into breach notification procedures and privacy policies.
When switching to the cloud from a locally hosted solution your security risk assessment process needs to be updated. Before making the switch, a risk assessment should take place to understand the current state of the integrity of the data that will be migrated.
Additionally, research should be done to review how data will be transferred to the cloud environment. Questions to consider include:
Question: Is your data ready for transport?
Reason: The time to conduct a data quality assessment is before migrating data to a cloud-based solution rather than after the fact.
Question: Will this transfer be facilitated by the cloud provider?
Reason: It is important to understand the security parameters that are in place for the transfer of data to the cloud provider, especially when considering large data sets.
19. Secure Your Cloud Account Beyond the Password
Contributed by the team at Dexter Edward
Secure the cloud account itself. All the protection on a server/os/application won’t help if anyone can take over the controls.
- Use a strong and secure password on the account and 2-factor authentication.
- Rotate cloud keys/credentials routinely.
- Use IP whitelists.
- Use any role-based accesses on any associated cloud keys/credentials.
Secure access to the compute instances in the cloud.
- Use firewalls provided by the cloud providers.
- Use secure SSH keys for any devices that require login access.
- Require a password for administrative tasks.
- Construct your application to operate without root privilege.
- Ensure your applications use encryption for any communications outside the cloud.
- Use authentication before establishing public communications.
Use as much of the private cloud network as you can.
- Avoid binding services to all public networks.
- Use the private network to isolate even your login access (VPN is an option).
Take advantage of monitoring, file auditing, and intrusion detection when offered by cloud providers.
- The cloud is made to move – use this feature to change up the network location.
- Turn off instances when not in use. b. Keep daily images so you can move the servers/application around the internet more frequently.
20. Consider Implementing Managed Virtual Desktops
Michael Abboud, CEO, and Founder of TetherView
Natural disasters mixed with cyber threats, data breaches, hardware problems, and the human factor, increase the risk that a business will experience some type of costly outage or disruption.
Moving towards managed virtual desktops delivered via a private cloud, provides a unique opportunity for organizations to reduce costs and provide secure remote access to staff while supporting business continuity initiatives and mitigating the risk of downtime.
Taking advantage of standby virtual desktops, a proper business continuity solution provides businesses with the foundation for security and compliance.
The deployment of virtual desktops provides users with the flexibility to work remotely via a fully-functional browser-based environment while simultaneously allowing IT departments to centrally manage endpoints and lock down business critical data. Performance, security, and compliance are unaffected.
Standby virtual desktops come pre-configured and are ready to be deployed instantaneously, allowing your team to remain “business as usual” during a sudden disaster.
In addition to this, you should ensure regular data audits and backups
If you don’t know what is in your cloud, now is the time to find out. It’s essential to frequently audit your data and ensure everything is backed up. You’ll also want to consider who has access to this data. Old employees or those who no longer need access should have permissions provoked.
It’s important to also use the latest security measures, such as multi-factor authentication and default encryption. Always keep your employees up to speed with these measures and train them to spot potential threats that way they know how to deal with them right away.
21. Be Aware of a Provider’s Security Policies

Many, if not most, businesses will continue to expand in the cloud, while relying on on-premise infrastructure for a variety of reasons, ranging from a simple cost/benefit advantages to reluctance to entrust key mission-critical data or systems into the hands of third-party cloud services providers. Keeping track of what assets are where in this hybrid environment can be tricky and result in security gaps.
Responsibility for security in the cloud is shared between the service provider and the subscriber. So, the subscriber needs to be aware not only of the service provider’s security policies, but also such mundane matters as hardware refresh cycles.
Cyber attackers have become adept at finding and exploiting gaps in older operating systems and applications that may be obsolete, or which are no longer updated. Now, with the disclosure of the Spectre and Meltdown vulnerabilities, we also have to worry about threats that could exploit errors or oversights hard-coded at the chip level.
Hardware such as servers and PCs has a limited life cycle, but often businesses will continue to operate these systems after vendors begin to withdraw support and discontinue firmware and software updates needed to counter new security threats.
In addition to being aware of what their cloud provider is doing, the business must keep track of its own assets and refresh them or decommission them as needed. When computer systems are repurposed for non-critical purposes, it is too easy for them to fall outside of risk management and security oversight.
22. Encrypt Backups Before Sending to the Cloud
Mikkel Wilson, CTO at Oblivious.io
1. File metadata should be secured just as vigilantly as the data itself. Even if an attacker can’t get at the data you’ve stored in the cloud, if they can get, say, all the filenames and file sizes, you’ve leaked important information. For example, if you’re a lawyer and you reveal that you have a file called “michael_cohen_hush_money_payouts.xls” and it’s 15mb in size, this may raise questions you’d rather not answer.
2. Encrypt your backups *before* you upload them to the cloud. Backups are a high-value target for attackers. Many companies, even ones with their own data centers, will store backups in cloud environments like Amazon S3. They’ll even turn on the encryption features of S3. Unfortunately, Amazon stores the encryption keys right along with the data. It’s like locking your car and leaving the keys on the hood.
23. Know Where Your Data Resides To Reduce Cloud Threats

Be aware of where their data is stored these days so that they can proactively identify if any of the data may be at risk of a breach.
These days, data is being stored in multiple cloud locations and applications in addition to storage devices in business. Companies are adopting cloud storage services such as Google Drive, Dropbox, OneDrive, etc. and online software services for all kind of business processes. This has led to vast fragmentation of company data, and often managers have no idea where all the data may be.
For example, a confidential financial report for the company may get stored in cloud storage because devices are automatically synching with cloud or a sensitive business conversation may happen in cloud-based messaging services such as Slack. While cloud companies have all the right intentions to keep their customer data safe, they are also the prime target because hackers have better ROI in targeting such services where they can potentially get access to data for millions of subscribers.
So, what should a company do?
While they will continue to adopt cloud services and their data will end up in many, many locations, they can use some search and data organization tools that can show them what data exists in these services. Using full-text search capabilities, they can then very quickly find out if any of this information is a potential risk to the company if breached. You cannot protect something if you do not even know where it is. And more importantly, you will not even know if it is stolen. So, companies looking to protect their business data need to take steps at least to be aware of where all their information is.
24. Patch Your Systems Regularly To Avoid Cloud Vulnerabilities

Business users are not defenseless, even in the wake of recent attacks on cloud computing like WannaCry or Petya/NotPetya.
The best antidote is patch management. It is always sound practice to keep systems and servers up to date with patches – it is the shortest path to peace of mind. Indeed, “patch management consciousness” needs to be part of an overarching mantra that security is a process, not an event — a mindset, not a matter of checking boxes and moving on. Vigilance should be everyone’s default mode.
Spam is no one’s friend; be wary of emails from unknown sources – and that means not opening them. Every small and midsize business wins by placing strategic emphasis on security protections, with technologies like clustered firewalls and intrusion detection and prevention systems (IDPS).
25. Security Processes Need Enforcement as Staff Often Fail to Realize the Risk

1. Security as a Priority
Enforcing security measures can become difficult when working with deadlines or complex new features. In an attempt to drive their products forward, teams often bend the rules outlined in their own security process without realizing the risk they are putting their company into. A well thought out security process needs to be well enforced in order achieve its goal in keeping your data protected. Companies that include cloud security as a priority in their product development process drastically reduce their exposure to lost data and security threats.
2. Passwords & Encryption
Two important parts of securing your data in the cloud are passwords and encryption.
Poor password management is the most significant opportunity for bad actors to access and gain control of company data. This usually accomplished through social engineering techniques (like phishing emails) mostly due to poor employee education. Proper employee training and email monitoring processes go a long way in helping expose password information. Additionally, passwords need to be long, include numbers, letters, and symbols. Passwords should never be written down, shared in email, or posted in chat and ticket comments. An additional layer of data protection is achieved through encryption. If your data is being stored for in the cloud for long periods, it should be encrypted locally before you send it up. This makes the data practically inaccessible in the small chance it is compromised.
26. Enable Two-factor Authentication

For the best cloud server security, we prefer to see Two Factor Authentication (also known as 2FA, multi-factor authentication, or two-step authentication) used wherever possible.
What is this? 2 Factor combines “something you know” with “something you have.” If you need to supply both a password and a unique code sent to your smartphone via text, then you have both those things. Even if someone knows your password, they still can’t get into your account. They would have to know your password and have access to your cell phone. Not impossible, but you have just dramatically made it more difficult for them to hack your account. They will look elsewhere for an easier target. As an example, iCloud and Gmail support 2FA – two services very popular with business users. I recommend everyone use it.
Why is this important for cloud security?
Because cloud services are often not protected by a firewall or other mechanism to control where the service can be accessed from. 2FA is an excellent additional layer to add to security. I should mention as well that some services, such as Salesforce, have a very efficient, easy to use implementation of 2FA that isn’t a significant burden on the user.
27. Do Not Assume Your Data in the Cloud is Backed-Up

Backing up data that’s in the cloud: There’s a big misconception around how cloud-based platforms (ex. Shopify, QuickBooks Online, Mailchimp, Wordpress) are backed up. Typically, cloud-based apps maintain a disaster recovery cloud backup of the entire platform. If something were to happen to their servers, they would try to recover everyone’s data to the last backup. However, as a user, you don’t have access to their backup to restore your data.
This means that you risk having to manually undo unwanted changes or permanently losing data if:
- A 3rd party app integrated into your account causes problems.
- You need to unroll a series of changes
- Your or someone on your team makes a mistake
- A disgruntled employee or contractor deletes data maliciously
Having access to a secondary backup of your cloud accounts gives you greater control and freedom over your own data. If something were to happen to the vendor’s servers, or within your individual account, being able to quickly recover your data could save you thousands of dollars in lost revenue, repair costs, and time.
28. Minimize and Verify File Permissions

1. If you are using a cloud-based server, ensure monitoring and patching the Spectre vulnerability and its variations. Cloud servers are especially vulnerable. This vulnerability can bypass any cloud security measures put in place including encryption for data that is being processed at the time the vulnerability is being utilized as an exploit.
2. Review and tighten up file access for each service. Too often accounts with full access are used to ensure software ‘works’ because they had permission issues in the past. If possible, each service should use its own account and only have restricted permission to access what is vital and just give the minimum required permissions.
29. When Securing Files in the Cloud, Encrypt Data Locally First

Most cloud storage users assume such services use their own encryption. They do, Dropbox, for example, uses an excellent encryption system for files.
The problem, however, is because you’re not the one encrypting, you don’t have the decryption key either. Dropbox holds the decryption key so anyone with that same key can decrypt your data. The decryption happens automatically when logged into the Dropbox system so anyone who accesses your account, e.g., via hacking can also get your now non-encrypted data.
The solution to this is that you encrypt your files and data, using an encryption application or software, before sending them to your chosen cloud storage service.
30. Exposed Buckets in AWS S3 are Vulnerable

1. The most common and publicized data breaches in the past year or so have been due to giving the public read access to AWS S3 storage buckets. The default configuration is indeed private, but people tend to make changes and forget about it, and then put confidential data on those exposed buckets.
2. Encrypt data, both in traffic and at rest. In the data center, where end users, servers, and application servers might all be in the same building. By contrast, with the Cloud, all traffic goes over the Internet, so you need to encrypt data as it moves around in public. It’s like the difference between mailing a letter in an envelope or sending a postcard which anyone who comes into contact with it can read the contents.
31. Use the Gold-standard of Encryption

There’s a false sense of privacy being felt by businesses using cloud-based services like Gmail and Dropbox to communicate and share information. Because these services are cloud-based and accessible by password, it’s automatically assumed that the communications and files being shared are secure and private. The reality is – they aren’t.
One way in which organizations can be sure to secure their data is in using new encryption methods such as end-to-end encryption for emailing and file sharing. It’s considered the “gold standard” method with no central points of attack – meaning it protects user data even when the server is breached.
These advanced encryption methods will be most useful for businesses when used in conjunction with well-aligned internal policies. For example, decentralizing access to data when possible, minimizing or eliminating accounts with privileged access, and carefully considering the risks when deciding to share data or use SaaS services.
32. Have Comprehensive Access Controls in Place

All cloud providers have the capability of establishing access controls to your data. This is essentially a listing of those who have access to the data. Ensure that “anonymous” access is disabled and that you have provided access only to those authenticated accounts that need access.
Besides that, you should utilize encryption to ensure your data stays protected and stays away from prying eyes. There is a multitude of options available depending on your cloud provider. Balance the utility of accessing data with the need to protect it – some methods are more secure than others, like utilizing a client-side key and encryption process. Then, even if someone has access to the data (see point #1), they only have access to the encrypted version and must still have a key to decrypt it
Ensure continuous compliance to your governance policies. Once you have implemented the items above and have laid out your myriad of other security and protection standards, ensure that you remain in compliance with your policies. As many organizations have experienced with cloud data breaches, the risk is not with the cloud provider platform. It’s what their staff does with the platform. Ensure compliance by monitoring for changes, or better yet, implement tools to monitor the cloud with automated corrective actions should your environment experience configuration drift.
33. 5 Fundamentals to Keep Data Secure in the Cloud
David Gugick, VP of Product Management at CloudBerry
- Perform penetration testing to ensure any vulnerabilities are detected and corrected.
- Use a firewall to create a private network to keep unauthorized users out.
- Encrypt data using AES encryption and rotate keys to ensure data is protected both in transit and at rest.
- Logging and Monitoring to track who is doing what with data.
- Identity and Access Control to restrict access and type of access to only the users and groups who need it.
34. Ensure a Secure Multi-Tenant Environment

When we think of the cloud, we think of two things. Cost savings due to efficiencies gained by using a shared infrastructure, and cloud storage security risk.
Although many published breaches are attributed to cloud-based environment misconfiguration, I would be surprised if this number was more than, the reported breaches of non-cloud based environments.
The best cloud service providers have a vested interest in creating a secure multi-tenant environment. Their aggregate spending on creating these environments are far more significant than most company’s IT budgets, let alone their security budgets. Therefore I would argue that a cloud environment configured correctly, provides a far higher level of security than anything a small to medium-sized business can create an on-prem.
Furthermore, in an environment where security talent is at a grave shortage, there is no way an organization can find, let alone afford the security talent they need. Resulting in the next best thing, create a business associate relationship with a provider that not only has a strong secure infrastructure but also provides cloud monitoring security solutions.
Cloud Computing Threats and Vulnerabilities: Need to know
- Architect solution as you would any on-prem design process;
- Take advantage of application services layering and micro-segmentation;
- Use transaction processing layers with strict ACLs that control inter-process communication. Use PKI infrastructure to authenticate, and encrypt inter-process communication.
- Utilize advanced firewall technology including WAF (Web Access Firewalls) to front-end web-based applications, to minimize the impact of vulnerabilities in underlying software;
- Leverage encryption right down to record level;
- Accept that it is only a matter of time before someone breaches your defenses, plan for it. Architect all systems to minimize the impact should it happen.
- A flat network is never okay!
- Robust change control process, with weekly patch management cycle;
- Maintain offline copies of your data, to mitigate the risk of cloud service collapse, or malicious attack that wipes your cloud environment;
- Contract with 24×7 security monitoring services that have an incident response component.
Recent Posts
2020 Disaster Recovery Statistics That Will Shock Business Owners
This article was updated in December 2019.
Data loss can be chilling and has serious financial implications. Downtime can occur at any time. Something as small as an employee opening an infected email, or as significant as a natural disaster.
Yet, 75% of small businesses have no disaster recovery plan objective in place.
We have compiled an interesting mix of disaster recovery statistics from a variety of sources from technology companies to mainstream media. Think of a disaster recovery plan a lifeboat for your business.
Hardware failure is the number one cause of data loss and/or downtime.
According to Dynamic Technologies, hardware failures cause 45% of total unplanned downtime. Followed by the loss of power (35%), software failure (34%), data corruption (24%), external security breaches (23%), and accidental user error (20%).
17 more startling Disaster Recovery Facts & Stats
1. 93% of companies without Disaster Recovery who suffer a major data disaster are out of business within one year.
2. 96% of companies with a trusted backup and disaster recovery plan were able to survive ransomware attacks.
3. More than 50% of companies experienced a downtime event in the past five years that longer than a full workday.
Recovering From A Disaster Is Expensive
When your business experiences downtime, there is a cost associated with that event. This dollar amount can be pretty tough to pin down as it includes direct expenses such as recovery labor and equipment replacement. But, also indirect costs such as lost business opportunity.
The cost can be staggering:
4. Corero Network Security found that organizations spend up to $50,000 dealing with a denial of service attack. Preventing DDoS attacks is critical.
4. Estimate are that unplanned downtime can cost up to $17,244 per minute, with a low-end estimate of $926 per minute.
5. On average, businesses lose over $100,000 per ransomware incident due to downtime and recovery costs. (source: CNN)
6. 40-60% of small businesses who lose access to operational systems and data without a DR plan close their doors forever. Companies that can recover do so at a much higher cost and a more extended timeframe than companies who had a formal backup and disaster recovery (BDR) plan in place.
7. 96% of businesses with a disaster recovery solution in place fully recover operations.

Numbers Behind Security Breaches and Attacks
9. In a 2017 survey of 580 attendees of the Black Hat security conference in Las Vegas, it was revealed that the more than half of the organizations had been the target of cyber attacks. 20% of those came from ransomware attacks.
10. 2/3 of the individuals responding to the survey believe that a significant security breach will occur at their organization in the next year
11. More than 50% of businesses don’t have the budget to recover from the attack.
The Human Element Of Data Loss
Cybercriminals often utilize a human-based method of bypassing security, such as increasingly-sophisticated phishing attacks.
12. Human error is the number one cause of security and data breaches, responsible for 52 percent of incidents.
13. Cybersecurity training for new employees is critical. Only 52% receive cybersecurity policy training once a year.
14. The painful reality is that malware can successfully bypass anti-spam email filters, and are mostly ineffective against a targeted malware attack. It was reported that in 2018, malware attacks increased by 25 percent.

Evolving Security Threat Matrix
15. By 2021, cybercrimes will cost $6 trillion per year worldwide.
16. Cybersecurity spending is on the rise; reaching $96 billion in 2018.
17. Cryptojacking attacks are increasing by over 8000% as miners exploit the computing power of unsuspecting victims.
Don’t Become a Disaster Recovery Statistic
The good news is that with adequate planning, you can minimize the costs regarding time and lost sales that are associated with disaster recovery.
Backing up and securing your data and systems and having the capability to maintain business as usual in the face of a disaster is no longer a luxury, it is a necessity. Understanding how to put a disaster recovery plan in place is essential. Read our recent article on data breach statistics for 2020.
Recent Posts
Business Continuity vs Disaster Recovery: What’s The Difference?
The terms Business Continuity and Disaster Recovery are not interchangeable though many seem to think otherwise. Disaster Recovery (DR) versus Business Continuity (BC) are two entirely different strategies, each of which plays a significant aspect in safeguarding business operations.
When it comes to protecting your data, it is critical to understand the differences and plan ahead. Those differences arise from both usage and application after a catastrophe strikes.
Business continuity consists of a plan of action. It ensures that regular business will continue even during a disaster.
Disaster recovery is a subset of business continuity planning.
Disaster recovery plans involve restoring vital support systems. Those systems are mostly communications, hardware, and IT assets. Disaster recovery aims to minimize business downtime and focuses on getting technical operations back to normal in the shortest time possible.

Business Continuity Has a Wider Scope
Business Continuity management refers to the processes and procedures that associates take to make sure that regular business operations continue during a disaster.
It can mean the difference between survival and total shutdown. It is based on a relentless analysis and isolation of critical business processes.
One of the key benefits is the focus on business processes. You assess what you must do in the event of a disaster. You articulate benefits versus cost. This is just solid data management, even if catastrophe never occurs.
So, you have already decided which business functions are critical. You have flagged what can be suspended until you fully recover. You have a priority list.
For example, would you concentrate on active customers only? What are your priorities for supply and warehouse management?
Federal and state laws require formal disaster recovery planning.
For example, financial enterprises must have a business continuity plan. The healthcare industry must comply with HIPAA requirements.
With business continuity planning, you have earmarked your resources.
Those resources support your most essential functions. They include any support equipment, software, and stock required to move forward. You manage that stock by keeping your inventory current. You rotate consumable supplies through your emergency stock.
Moreover, you have identified your key staff people. They know what they must do and when they must do it. For every job there is to do, someone must be designated to do it. The designated “doers” must be qualified to carry on the business in the event of a disaster. So, the plan has to include practice and update of the plan as necessary.
The plan must also focus on customers and the supply chain. Suppliers must know that their payment invoices are in the pipeline and ready for payment. Customers must be confident that their orders will be filled or only temporarily delayed, perhaps with a discount premium.
Finally, your BC plan must include a process to replace and recover your IT systems. That contains valuable business data. For example, is your network designed for data backup and recovery?
Failover is where a secondary system kicks in when the first one goes down. How much will it cost you to replace storm-ruined hardware?
Disaster Recovery Plan
Disaster recovery is a subspace of total business continuity planning. A DR plan includes getting systems up and running following a disaster.
IT disasters can range from small hardware failures to massive security breaches.
The statistics on companies that suffer an IT disaster are incredible.
93 percent will file for bankruptcy within one year. Of that 93 percent, 60 percent can expect to shut down within six months. A complete system crash and loss of data is like the aftermath of a burglary. You don’t know what is missing until you go looking for it.
One contributing cause in those business failures is the lack of a written plan. The plan should include a business impact analysis. Many businesses write the plan, but neglect to update it, at least annually. For example, when the natural disaster Hurricane Harvey caused unexpected inland flooding in Houston. Many businesses were quickly inundated as people struggled to evacuate.
Infrastructure technology-related planning failures also include a lack of recovery and business continuity procedural guides. How do you methodically restore each critical application in your IT structure? How long will it take to restore your system by way of backups? What is your restore-point tolerance? A restore point is a time between your last cloud backup and when your system went down.
Finally, if no single person is responsible for data recovery preparedness, how can it occur? That person has to have the authority to work across the organization.

Don’t rely on business insurance
A business insurance policy may only cover loss or damage to your inventory and equipment.
Even if your organization survives a disaster, without effective planning, you will face the following losses:
- Financial: Lost profits, a lower market share, government fines because of data breaches. HIPAA fines, for example, have amounted to multi-millions.
- Damage to your reputation, brand through negative publicity.
- Sanctions: Loss of your business license, or legal liability. You could lose time and money even if you win the lawsuit.
- Breach of contract: Your inability to meet your obligations to clients. Includes a ripple effect up and down your supply chain. This could even drive some of your suppliers and customers out of business.
- Dead in the water: Stalled or frozen business objectives and plans, missed market opportunities.
Bottom Line: Recovery and Business Continuity
The difference between business continuity and disaster recovery is quite specific.
Business continuity planning is a strategy. It ensures continuity of operations with minimal service outage or downtime. A business disaster recovery plan can restore data and critical applications in the event your systems are destroyed when disaster strikes.
Balancing two planning strategies is a matter of priorities. If the majority of your business transactions are online, you need to make data protection your number one concern. Losing all or some of your data could halt your operations. You could not bill customers, pay vendors, or access your inventory information. Your competitive intelligence would disappear.
You need to know how long you can wait to get back to full operation before the pain starts. You also must weigh that delay against the costs of planning and execution. Fortunately, reliable managed services providers and consultants know how to do that. They can address your concerns in a cost-effective and compliant manner.
Looking for a business continuity recovery plan example?
Recent Posts
What is High Availability Architecture? Why is it Important?
Achieving business continuity is a primary concern for modern organizations. Downtime can cause significant financial impact and, in some cases, irrecoverable data loss.
The solution to avoiding service disruption and unplanned downtime is employing a high availability architecture.
Because every business is highly dependent on the Internet, every minute counts. That is why company computers and servers must stay operational at all times.
Whether you choose to house your own IT infrastructure or opt for a hosted solution in a data center, high availability must be the first thing to consider when setting up your IT environment.
High Availability Definition
A highly available architecture involves multiple components working together to ensure uninterrupted service during a specific period. This also includes the response time to users’ requests. Namely, available systems have to be not only online, but also responsive.
Implementing a cloud computing architecture that enables this is key to ensuring the continuous operation of critical applications and services. They stay online and responsive even when various component failures occur or when a system is under high stress.
Highly available systems include the capability to recover from unexpected events in the shortest time possible. By moving the processes to backup components, these systems minimize downtime or eliminate it. This usually requires constant maintenance, monitoring, and initial in-depth tests to confirm that there are no weak points.
High availability environments include complex server clusters with system software for continuous monitoring of the system’s performance. The top priority is to avoid unplanned equipment downtime. If a piece of hardware fails, it must not cause a complete halt of service during the production time.
Staying operational without interruptions is especially crucial for large organizations. In such settings, a few minutes lost can lead to a loss of reputation, customers, and thousands of dollars. Highly available computer systems allow glitches as long as the level of usability does not impact business operations.
A highly available infrastructure has the following traits:
- Hardware redundancy
- Software and application redundancy
- Data redundancy
- The single points of failure eliminated
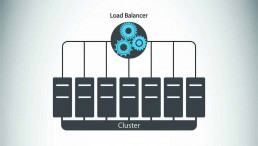
How To Calculate High Availability Uptime Percentage?
Availability is measured by how much time a specific system stays fully operational during a particular period, usually a year.
It is expressed as a percentage. Note that uptime does not necessarily have to mean the same as availability. A system may be up and running, but not available to the users. The reasons for this may be network or load balancing issues.
The uptime is usually expressed by using the grading with five 9’s of availability.
If you decide to go for a hosted solution, this will be defined in the Service Level Agreement (SLA). A grade of “one nine” means that the guaranteed availability is 90%. Today, most organizations and businesses require having at least “three nines,” i.e., 99.9% of availability.
Businesses have different availability needs. Those that need to remain operational around the clock throughout the year will aim for “five nines,” 99.999% of uptime. It may seem like 0.1% does not make that much of a difference. However, when you convert this to hours and minutes, the numbers are significant.
Refer to the table of nines to see the maximum downtime per year every grade involves:
| Availability Level | Maximum Downtime per Year | Downtime per Day |
| One Nine: 90% | 36.5 days | 2.4 hours |
| Two Nines: 99% | 3.65 days | 14 minutes |
| Three Nines: 99.9% | 8.76 hours | 86 seconds |
| Four Nines: 99.99% | 52.6 minutes | 8.6 seconds |
| Five Nines: 99.999% | 5.25 minutes | 0.86 seconds |
| Six Nines: 99.9999% | 31.5 seconds | 8.6 milliseconds |
As the table shows, the difference between 99% and 99.9% is substantial.
Note that it is measured in days per year, not hours or minutes. The higher you go on the scale of availability, the cost of the service will increase as well.
How to calculate downtime? It is essential to measure downtime for every component that may affect the proper functioning of a part of the system, or the entire system. Scheduled system maintenance must be a part of the availability measurements. Such planned downtimes also cause a halt to your business, so you should pay attention to that as well when setting up your IT environment.
As you can tell, 100% availability level does not appear in the table.
Simply put, no system is entirely failsafe. Additionally, the switch to backup components will take some period, be that milliseconds, minutes, or hours.
How to Achieve High Availability
Businesses looking to implement high availability solutions need to understand multiple components and requirements necessary for a system to qualify as highly available. To ensure business continuity and operability, critical applications and services need to be running around the clock. Best practices for achieving high availability involve certain conditions that need to be met. Here are 4 Steps to Achieving 99.999% Reliability and Uptime.
1. Eliminate Single Points of Failure High Availability vs. Redundancy
The critical element of high availability systems is eliminating single points of failure by achieving redundancy on all levels. No matter if there is a natural disaster, a hardware or power failure, IT infrastructures must have backup components to replace the failed system.
There are different levels of component redundancy. The most common of them are:
- The N+1 model includes the amount of the equipment (referred to as ‘N’) needed to keep the system up. It is operational with one independent backup component for each of the components in case a failure occurs. An example would be using an additional power supply for an application server, but this can be any other IT component. This model is usually active/passive. Backup components are on standby, waiting to take over when a failure happens. N+1 redundancy can also be active/active. In that case, backup components are working even when primary components function correctly. Note that the N+1 model is not an entirely redundant system.
- The N+2 model is similar to N+1. The difference is that the system would be able to withstand the failure of two same components. This should be enough to keep most organizations up and running in the high nines.
- The 2N model contains double the amount of every individual component necessary to run the system. The advantage of this model is that you do not have to take into consideration whether there was a failure of a single component or the whole system. You can move the operations entirely to the backup components.
- The 2N+1 model provides the same level of availability and redundancy as 2N with the addition of another component for improved protection.
The ultimate redundancy is achieved through geographic redundancy.
That is the only mechanism against natural disasters and other events of a complete outage. In this case, servers are distributed over multiple locations in different areas.
The sites should be placed in separate cities, countries, or even continents. That way, they are entirely independent. If a catastrophic failure happens in one location, another would be able to pick up and keep the business running.
This type of redundancy tends to be extremely costly. The wisest decision is to go for a hosted solution from one of the providers with data centers located around the globe.
Next to power outages, network failures represent one of the most common causes of business downtime.
For that reason, the network must be designed in such a way that it stays up 24/7/365. To achieve 100% network service uptime, there have to be alternate network paths. Each of them should have redundant enterprise-grade switches and routers.
2. Data Backup and recovery
Data safety is one of the biggest concerns for every business. A high availability system must have sound data protection and disaster recovery plans.
An absolute must is to have proper backups. Another critical thing is the ability to recover in case of a data loss quickly, corruption, or complete storage failure. If your business requires low RTOs and RPOs and you cannot afford to lose data, the best option to consider is using data replication. There are many backup plans to choose from, depending on your business size, requirements, and budget.
Data backup and replication go hand in hand with IT high availability. Both should be carefully planned. Creating full backups on a redundant infrastructure is vital for ensuring data resilience and must not be overlooked.
3. Automatic failover with Failure Detection
In a highly available, redundant IT infrastructure, the system needs to instantly redirect requests to a backup system in case of a failure. This is called failover. Early failure detections are essential for improving failover times and ensuring maximum systems availability.
One of the software solutions we recommend for high availability is Carbonite Availability. It is suitable for any infrastructure, whether it is virtual or physical.
For fast and flexible cloud-based infrastructure failover and failback, you can turn to Cloud Replication for Veeam. The failover process applies to either a whole system or any of its parts that may fail. Whenever a component fails or a web server stops responding, failover must be seamless and occur in real-time.
The process looks like this:
- There is Machine 1 with its clone Machine 2, usually referred to as Hot Spare.
- Machine 2 continually monitors the status of Machine 1 for any issues.
- Machine 1 encounters an issue. It fails or shuts down due to any number of reasons.
- Machine 2 automatically comes online. Every request is now routed to Machine 2 instead of Machine 1. This happens without any impact to end users. They are not even aware there are any issues with Machine 1.
- When the issue with the failed component is fixed, Machine 1 and Machine 2 resume their initial roles
The duration of the failover process depends on how complicated the system is. In many cases, it will take a couple of minutes. However, it can also take several hours.
Planning for high availability must be based on all these considerations to deliver the best results. Each system component needs to be in line with the ultimate goal of achieving 99.999 percent availability and improve failover times.
4. Load Balancing
A load balancer can be a hardware device or a software solution. Its purpose is to distribute applications or network traffic across multiple servers and components. The goal is to improve overall operational performance and reliability.
It optimizes the use of computing and network resources by efficiently managing loads and continuously monitoring the health of the backend servers.
How does a load balancer decide which server to select?
Many different methods can be used to distribute load across a server pool. Choosing the one for your workloads will depend on multiple factors. Some of them include the type of application that is served, the status of the network, and the status of the backend servers. A load balancer decides which algorithm to use according to the current amount of incoming requests.
Some of the most common load balancing algorithms are:
- Round Robin. With Round Robin, the load balancer directs requests to the first server in line. It will move down the list to the last one and then start from the beginning. This method is easy to implement, and it is widely used. However, it does not take into consideration if servers have different hardware configurations and if they can overload faster.
- Least Connection. In this case, the load balancer will select the server with the least number of active connections. When a request comes in, the load balancer will not assign a connection to the next server on the list, as is the case with Round Robin. Instead, it will look for one with the least current connections. Least connection method is especially useful to avoid overloading your web servers in cases where sessions last for a long time.
- Source IP hash. This algorithm will determine which server to select according to the source IP address of the request. The load balancer creates a unique hash key using the source and destination IP address. Such a key enables it always to direct a user’s request to the same server.
Load balancers indeed play a prominent role in achieving a highly available infrastructure. However, merely having a load balancer does not mean that you have a high system availability.
If a configuration with a load balancer only routes the traffic to decrease the load on a single machine, that does not make a system highly available.
By implementing redundancy for the load balancer itself, you can eliminate it as a single point of failure.

In Closing: Implement High Availability Architecture
No matter what size and type of business you run, any kind of service downtime can be costly without a cloud disaster recovery solution.
Even worse, it can bring permanent damage to your reputation. By applying a series of best practices listed above, you can reduce the risk of losing your data. You also minimize the possibilities of having production environment issues.
Your chances of being offline are higher without a high availability system.
From that perspective, the cost of downtime dramatically surpasses the costs of a well-designed IT infrastructure. In recent years, hosted and cloud computing solutions have become more popular than in-house solutions support. The main reason for this is the fact it reduces IT costs and adds more flexibility.
No matter which solution you go for, the benefits of a high availability system are numerous:
- You save money and time as there is no need to rebuild lost data due to storage or other system failures. In some cases, it is impossible to recover your data after an outage. That can have a disastrous impact on your business.
- Less downtime means less impact on users and clients. If your availability is measured in five nines, that means almost no service disruption. This leads to better productivity of your employees and guarantees customer satisfaction.
- The performance of your applications and services will be improved.
- You will avoid fines and penalties if you do not meet the contract SLAs due to a server issue.
Recent Posts
What is Cloud Disaster Recovery? 9 Key Benefits
Your business data is under constant threat of attack or data loss.
Malicious code, hackers, natural disasters, and even your employees can wipe out an entire server filled with critical files without anyone noticing until it is too late.
Are you willing to fully accept all these risks?
What is cloud disaster recovery?
Cloud-based storage and recovery solutions enable you to backup and restore your business-critical files in case they are compromised.
Thanks to its high flexibility, the cloud technology enables efficient disaster recovery, regardless of the type or intensity of workloads. The data is stored in a secured cloud environment architected to provide high availability. The service is available on-demand, which enables organizations of different sizes to tailor DR solutions to their needs.
As opposed to traditional solutions, cloud-based disaster recovery is easy to set up and manage. Businesses no longer need to wast hours on transferring backup data from their in-house servers or tape drives to recover after a disaster. The cloud automates these processes, ensuring fast and error-free data recovery.

Always be prepared for with proper data security
As companies continue to add new hardware and software applications and services to their daily processes, related security risks increase. Disasters can occur at any moment and leave a business devastated by massive data loss. When you consider how much they can cost, it is clear why it makes sense to create a data backup and recovery plan.
Disaster recovery statistics show that 98% of organizations surveyed indicate that a single hour of downtime can cost their business over $100,000. Any amount of downtime can cost a business tens of thousands to hundreds of thousands in man-hour labor spent to recover or redo the work lost. In some cases, an 8-hour downtime window can cost a small company up to $20k and large enterprises in the tens of thousands.
Considering the figures, it is clear why every second of service or system interruption counts and what is the actual value of having a disaster recovery plan in place.
Cloud recovery helps businesses bounce back from natural disasters, cyber-attacks, ransomware, and other threats that can render all files useless in an instant. Just by minimizing the time needed to take workloads back online, it directly lowers the cost of a system failure.
Although most companies and their IT departments are aware of the risk, few make an effort to implement disaster recovery until it is too late. Now, let us take a more in-depth look at how it can translate into business benefits.

Benefits of a cloud-based disaster recovery solution
One of the most significant advantages of cloud-based options over standard disaster recovery management is their cost-efficiency. Traditional backup involves setting up physical servers at a remote location, which can be costly. The cloud, on the other hand, enables you to outsource as many hardware and software resources as you need while paying only for what you use.
When considering the cost of disaster recovery, it is essential to think beyond the actual price of the solution.
Just think about how much it would cost not to have it. Small companies can choose a service plan that fits their budget. The implementation of data management does not require any additional maintenance costs or hiring IT teams. Your provider handles all the technical activities, so you do not have to worry about them.
Another benefit of cloud-based technology is its reliability. Service providers have data banks to provide redundancy, which ensures maximum availability of your data. It also makes it possible for your backups to be restored faster than what would be the case with traditional DR.
The workload migration and failover in cloud-based environments can take only several minutes. With traditional recovery solutions, this time frame is usually longer since the failover involves physical servers set up in a remote location. Depending on the amount of data you need to back up, you can also choose to migrate data in phases.
Cloud backup services offer a high degree of scalability. Compared to physical systems, cloud backup is virtually endless. As organizations grow, their systems can grow with them. All you need to do is extend your service plan with your provider and get additional resources as the need arises.

Failover and failback capabilities in the cloud
When it comes to business-critical data, cloud data backup and recovery provides the most reliable business continuity and failback option.
During a data outage, workloads are automatically shifted to a different location and restarted from there. This process is called failover, and it is initiated when the primary systems experience an issue. After the issues on the original location are resolved, the workloads are failed back to it. This is done using professional disaster recovery and replication tools, which are available from the data center and infrastructure-as-a-service providers.
Although failover and failback activities can be automated in the cloud, businesses should regularly run tests on designated network locations to make sure there is no impact to live or production network data.
When establishing the data set in a disaster recovery solution, you can select data, virtual machine images, or full applications to fail over. This process may take a while, and this is why organizations need to discuss every step of it with their data center provider.

Disaster Recovery as a Service (DRaaS)
Part of a cloud disaster recovery plan might include DRaaS disaster recovery as a service. It is designed to help organizations protect themselves against loss of critical business data.
These disaster recovery solutions require a business to help them understand what they need from their service.
A business might identify a general pool of data they need to be backed up, how often it should be backed up. Further, companies should determine the level of effort required to invest in backing up the data during disaster recovery. Once a company clarifies the requirements, they can look for DRaaS providers to suit their needs.
How cloud computing backup and recovery is evolving
With cyber attacks and system failures becoming more commonplace, companies are increasingly turning to disaster recovery in the cloud.
As the demand grows, providers continue improving their offerings. Recent reports suggest that the market for backup and DR cloud services is on the rise with a growing number of solutions being offered to companies of different sizes.
The increase in demand also illustrates a greater awareness of their value. Cyber attacks and system failures are occurring on a daily basis and businesses are justifiably concerned about the safety of their data. They need an option that can protect their data in a diversity of scenarios that are putting their daily operations at risk.
Studies have also found that the principal cause of downtime is the power outage. This means that no matter how many copies you have of your files in-house, they can all be lost if the power goes out. With cloud-based DRaaS, your data is saved remotely with reliable power sources. In most cases, cloud services distribute data to different power grids ensuring sufficient redundancy.
Many older services included physical backups at offsite locations. Offsite backups are expensive and inefficient as they involve duplicating physical equipment at another location or having a combination of on-premises and physical backups.
Cloud Service Level Agreements
Service level agreements (SLAs) hold cloud computing disaster recovery providers responsible for all maintenance and management of services rendered. They also include details on recourse and penalty for any failures to deliver promised services.
For example, an SLA agreement can ensure disaster recovery providers reimburse their clients with service credit in the events of a service outage or in case data cannot be recovered in a disaster. From there, customers can use their credits toward their monthly bill or from another service offered by the DR provider even though these credits will not make up the entire loss the business experiences in delayed cloud recovery.
An SLA also includes guaranteed uptime, recovery point, and recovery time goals. For example, the latter can be any set time from an hour to 24 hours or more depending on the amount of data to be backed up and recovered. More specifically, this is defined in terms of RTOs and RPOs, which are essential concepts in disaster recovery.
The recovery time objective (RTO) is the acceptable period for applications to be down. Recovery point objectives (RPO) are the acceptable period data is down for. Based on these two criteria, companies define their needs and can choose an adequate solution.

Define Your Recovery Requirements
A large part of any cloud backup and disaster recovery plan is the amount of bandwidth and network capacity required to perform failover.
A sufficient analysis of how to make data available when needed is essential for choosing the best fit for a company. Part of the considerations should be if the network and bandwidth capacity can handle redirecting all users to the cloud at once.
Another consideration for hybrid environments is how to restore data from the cloud to an on-premise data center network and how long it will take to perform this. Backup sets for recovery will need to be designed as part of any disaster recovery solution as well.
When defining these requirements, RTOs and RPOs play a major role. Both of these goals are included as part of the business impact analysis.
Recovery points are the points at which data must be recovered. This may include the frequency of backup as it is based on the methods the data is used. For instance, information and files that are frequently updated might have a recovery point of a few minutes, while less essential data would need to be recovered within a few hours.
Both recovery time and recovery point objectives represent the impact on the bottom line. The smaller these values are, the higher the cost of the DRaaS.
Part of the recovery time and recovery point should include a schedule for automated backups. Keep in mind the difference in the length required to backup data versus applications and create two schedules or note the differences in one schedule.

Creating a custom cloud backup & disaster recovery plan
There is no magic blueprint for back up and disaster recovery solutions. Each company must learn more about the industry’s best practices and determine the essential workloads required to continue operations after a data loss or other catastrophe.
The overall principle used to derive an IT recovery plan is triage. This is the process of creating a program that begins with the identification and prioritization of services, applications, and data, and determining an appropriate amount of downtime before the disaster causes a significant impact on business operations. These efforts include developing a set of recovery time objectives that will define what type of solution a business needs.
By identifying essential resources and appropriate downtime and recovery, a business has a solid foundation for a cloud DR solution.
All critical applications and data must be included in this blueprint. On the other hand, to minimize costs and ensure a fast recovery when the strategy is put into practice, a business should remove all irrelevant applications and data.
After the applications and data are identified and prioritized, the recovery time objectives are defined. The most cost-effective way of achieving the goals should use a separate method for each application and service.
Some businesses may require a separate method for data and applications running in their private or public cloud environments. Most likely, this scenario would return different means to protect application clusters and data with parallel recovery time objectives.
Once the design for disaster recovery is final, periodic tests should be performed to ensure it works as needed. Many companies have backups in place but are not sure how to use them when they need them. This is why you need to test both internal and external procedures regularly and even update them as needed.
A general recommendation is to test your systems on an annual basis, carefully following each step of the outlined process. However, in companies that have dynamic multi-cloud strategies or those that are expanding at an unsteady pace, these tests may need to be performed even more frequently. As new systems or infrastructure upgrades are implemented, the disaster recovery plan should be updated to reflect the changes.
It is also important to use a cloud monitoring tool.
Options for disaster data recovery in the cloud
Data centers offer varying options businesses can choose from for data protection.
Managed applications are popular components of a disaster recovery cloud strategy. In this case, both primary production data and backup cases are stored in the cloud and managed by a provider. This allows companies to reap the cloud’s benefits in a usage-based model while moving away from dependency on on-premises backups.
A managed or hosted recovery solution brings you a comprehensive cloud-based platform with the needed hardware and software to support your operations. With this option, data and applications remain on-premises, and only data is backed up on the cloud infrastructure and restored as needed. Such a solution is more cost-effective than a traditional option such as local, offsite data backup. However, the process of recovery for applications may be slow.
Some application vendors may already offer cloud backup services. Businesses should check with their vendors if this is an option to make the implementation as easy as possible. Another viable option is to back up to and restore from the cloud infrastructure. Data is restored to virtual machines in the cloud rather than on-premises servers, requiring cloud storage and cloud computing resources.
The restore process can be executed when a disaster strikes, or it can be recurring. Recurring backups ensure data is kept up-to-date through resource sharing and is essential when recovery goals are short.
For applications and data with short or aggressive objectives, replication to virtual machines in the cloud is a viable DRaaS service. By replicating to the cloud, you can ensure data and applications are protected both in the cloud and on-premises.
Replication is viable for cloud VM to cloud VM and on-premises to cloud VM. The products in the replication to VMs are based on continuous data protection.

Getting Started With Cloud Disaster Recovery
After a business has determined which type of recovery solution they want, the next step is to make an overview of the options available with different providers and data centers.
The key to finding a solution that suits the business needs is discussing options with multiple service providers.
Many vendors offer variances in their pricing packages which may include a certain number of users, application backup, data backup, and frequency of backup.
The only efficient way to choose a managed cloud backup and disaster recovery provider is to assess your needs adequately. Discuss needs with all stakeholders in the business in all departments to discover critical data and applications to ensure business continuity.
Determine recovery time and point objectives and create a schedule with appropriate downtime for data and applications. Next, consider the budget allotted for disaster recovery.
Examine various options to find the best one for your business.
Recent Posts
- 5 Cloud Deployment Models: Learn the Differences October 23, 2020
- Automating Server Provisioning in Bare Metal Cloud with MAAS (Metal-as-a-Service) by Canonical October 21, 2020
- Chaos Engineering: How it Works, Principles, Benefits, & Tools October 15, 2020
- Infrastructure as Code with Terraform on Bare Metal Cloud October 8, 2020
- How Kerberos Authentication Works October 1, 2020
Data Backup Strategy: Ultimate Step By Step Guide for Business
Cybersecurity is not something to be taken lightly by businesses.
It is not enough to have basic protections like anti-virus software to protect your valuable files. Hackers spend their time finding ways to get around it. Sooner or later, they will.
When that happens, you will not have to worry about permanently losing data.
That is if you have implemented a backup strategy to protect your business’s information.
Why Having a Backup Strategy is Vital
Losing data can not only put your customers’ data at risk but also have a significant impact on your credibility.
The average cost of a breach is seven million dollars as of 2019. It is estimated that 60% of companies that experience data loss close within six months.
Alternatively, you could be at risk of losing data permanently. Viruses and malware that attack your hardware can destroy it, but these are just some of the most dominant threats.
Studies show that 45% of all unplanned downtime is caused by hardware failures, while 60% of IT professionals say that careless employees are the most significant risk to their data.
All of these risks can cost your company money and, without an adequate backup system in place; you could lose everything.
Even if your company manages to survive a data loss, it could be costly. Research shows that, on average, companies pay $7 million to recover from a loss. Many companies do not have that kind of money to spare.
These expenses, as high as they are, only tell part of the story. The other price may be something irreplaceable. I am talking about the faith and trust of your customers. If they feel their data is not safe with you, they will take their business elsewhere.
The solution is to create and implement a data backup strategy. With the right tools, planning, and training, you can protect your data.

The Components of Efficient Backup Strategies
Before you create your backup strategy, you should know what to include.
Let us break down some of the backup strategy best practices:
- Cost. You will need a data backup plan that you can afford. It is a good idea to think beyond dollars. Keep the potential expense of a breach or loss in mind. Then, weigh that against the projected cost of your backup system. That will help guide you.
- Where to store copies of your data? Some companies prefer cloud-based backup. Others like to have a physical backup. The most cautious companies use multiple backup sources. That way, if one backup fails they have another in place.
- What data risks do you face? Every company must think about malware and phishing attacks. However, those might not be the only risks you face. A company in an area that is prone to flooding must consider water damage. Having an off-site backup and data storage solution would be wise.
- How often should you back up your data? Some companies generate data quickly. In such cases, a daily backup may not be sufficient. Hourly backups may be needed. For other companies whose data is rarely updated, a once-weekly backup may be enough.
- Who will be responsible for your backup planning? Employee training is essential to an effective file backup strategy. You need knowledgeable people you can rely on to keep things running.
These things are essential, but they are only the tip of the iceberg. You must consider each aspect of your backup plan in detail. Then, you will have to implement it as quickly and efficiently as possible.

Step #1: Assessing Your Company’s Backup Needs
The first step is to assess your company’s backup needs. There are many things to consider. Let us break it down so you can walk through it.
What Data Do You Need to Protect?
The short answer to this question is everything. Losing any data permanently is not something you want to risk. You need data to keep your business operational.
There are some specific questions to ask, both in the short and long-term. For example:
- You might need the ability to restore data as quickly as possible.
- You might need the ability to recover data.
- You might need to keep services available to clients.
- You may need to back up databases, files, operating systems, applications, and configurations.
The more comprehensive your data backup plan is, the less time it will take for you to get back in business. These questions can help point you in the direction of the right backup solution for your company. You may also want to think about what data is most important.
You might be able to live without an immediate back-p of somethings. However, you might need instant access to others.
What Are Your Data Risks?
Given the current pace of cybercrime growth, you will want to consider the best practices to protect your data from hackers. Here are some questions to ask to determine which risks you must consider.
- Has my company ever been hacked before?
- Are careless employees a concern when it comes to security?
- Is my location at risk for weather-related damage such as flooding or wildfires?
- Do clients log in to my system to access data or services?
Asking these questions will help you identify your risks. A company in a hurricane-prone area might be worried about flooding or wind damage. A customer system linked to your data adds additional risks. Be as thorough as you can as you assess your risks.
What Should Your Backup Infrastructure Be?
The infrastructure of your backup system should match your needs. If you are concerned about the possibility of hardware failure or natural disasters, then you will want to consider off-site backup solutions.
There may also be some benefit to having an on-site physical backup for quick recovery of data. It can save you if you lose your internet service, as might be the case during an emergency. The best way to avoid a continued business disruption is to choose a remote cloud disaster recovery site, possibly with your data center provider. You need to pick a place that would provide you with access to IT equipment, internet service, and any other assets you need to run your business.
Imagine a hurricane hits your facility. A disaster recovery plan enables you to continue your business from a different location and minimize the potential loss of money.
How Long Does Backed Up Data Need to be Stored?
Finally, you will need to consider how long to keep the data you store. Storage is cumulative. If you expect to accumulate a lot of data, you will need space to accommodate it. Some companies have regulatory requirements for backup. If you do, that will impact your decision.
You should evaluate your needs and think about what structure might be best for you.

Step #2: Evaluating Options To Find The Best Backup Strategy
After you assess your backup needs, the next step is to evaluate your options. The backup solution that is best for another company might not work for you. Let us review the backup options available to you.
Hardware Backups
A hard drive backup is kept on-site and often mounted on a wall. They usually come with a storage component. The primary benefit of hard drives is that they can easily be attached to your network.
The downside of a stand-alone hardware backup is that if it fails, you will not have a backup. For that reason, some companies choose to use multiple backup systems.
Software Solutions
Buying backup software may be less expensive than investing in dedicated hardware. Many software options can be installed on your system. You may not need to buy a separate server for it.
You may need to install the software on a virtual machine. A software backup may be the best choice if your infrastructure changes often.
Cloud Services
Cloud services offer backup as a service or offsite backup. These allow you to run your backup and store it in the vendor’s cloud infrastructure.
The benefit of cloud-based storage compared to dedicated servers is that it is affordable and secure. Companies with sensitive data and those who are subject to regulatory requirements may not be able to use it.
Hybrid Solutions
A popular solution is to implement a hybrid backup solution. These combine software and cloud backups to provide multiple options for restoring data.
The benefit of a hybrid service is that it protects you two ways. You will have on-site backups if you need them. Moreover, you will also be able to get your data from the cloud if necessary.
You should also consider what each option means for your staff. Unless you elect to use a comprehensive BaaS option, your employees will need to handle the backups. That is an important consideration.
Backup Storage Options
You will also need to think about where to store your backups. Here again, you have more than one option.
- You can back up your data to local or USB disks. This option is best for backing up individual files and hardware. It is not ideal for networks. If the drive is destroyed, you will lose your backup.
- Network Attached Storage (NAS) and Storage Area Networks (SAN) are also options. These are ideal for storing data for your network. They make for easy recovery network data recovery in most situations. The exception is if your hardware or office is destroyed.
- Backing data up to tapes may be appealing to some companies. The tapes would be shipped to a secure location for storage. This keeps your data safe. The downsides are that you will have to wait for tapes to arrive to restore your data. They are best suited for restoring your whole system, not individual files.
- Cloud storage is increasingly popular. You will need an internet connection to send your data to the cloud. There are options available to help you transmit a significant amount of data. You will be able to access your data from anywhere, but not without an internet connection.
To decide which option is best, you will need to consider two metrics, RTO and RPO. The first is your Recovery Point Objective or RPO. That is the maximum time you are willing to lose data on your systems.
The second is your Recovery Time Objective or RTO. That is how long you want it to take for you to restore normal business operations.
Choosing your backup and storage methods is a balancing act. You will need to weigh your budget against your specific backup needs.
Step #3: Budgeting
The third step is creating a budget for your backup plan.
Some solutions are more expensive than others. Buying new hardware is costly and may require downtime to install.
Cloud-based solutions are more affordable.
As your budget, here are some things to consider.
- What is the maximum amount you want to spend?
- Do you plan to allocate your budget as an item of capital expenditure? Perhaps you would rather log it is an operating expense. Some options will allow you to do the latter.
- What would it cost you if you lost data to a cyber security attack or disaster?
- How much will it cost to train employees to manage the backup? If you are not choosing BaaS, someone in your company will have to take responsibility for backup management.
If you choose backup as a service, then you may be able to pay monthly and avoid a significant, up-front expense. Be realistic about your needs and what you must spend to meet them.
Sometimes, companies underspend on backups. One reason is that a backup system is not viewed as a profit center. It may help to view it as a data loss prevention solution, instead.
Step #4: Select a Platform
Next, it is time to choose a platform.
If you have made careful evaluations, you may already know what you want. As I mentioned earlier, some companies prefer multiple backup options to cover themselves.
Choosing only one backup option may cover your needs. If you are sure you will have an internet connection; a cloud back-up might be sufficient.
You can access it from anywhere and get your data quickly.
The most significant argument against a cloud-based service provider is confidentiality.
If you are storing sensitive data, you may not want to rely on an outside company. Regulations may even prohibit you from doing so. If that is the case, think about off-site, secure storage for your backups. That way, you can get them if your business is damaged.
Step #5: Select a Data Backup Vendor
It is time to choose a vendor to help you implement your new backup strategy. You may opt for an all-in-one service. Some companies can provide hardware, software, and cloud-based solutions. They may also be able to help you with employee training.
Any time you choose a vendor, you should request a data center RFP or proposal. That is the best way to know which options are available to you. As you compare quotes, take all elements of the project into consideration.
These include:
- The overall cost of implementation
- Which options are included
- How long implementation is expected to take
- The vendor’s reputation
Asking for references is a smart idea. Call, and ask them about every aspect of their experience. Make sure to ask about service and support during the process. Then, once you have gathered the information you need, you can award the contract to the vendor you choose.

Step #6: Create a Timetable
The vendor you choose may provide you with an estimated timeframe for implementation. You should still create a timetable of your own. It can help you plan for implementation. A timeline is essential. Having one will allow you to prepare to support the new backup protocol.
Here are some things to consider as you create your timetable.
- What things do you need to do before the vendor can begin work? Examples might be creating a master backup of existing data or designating a team to oversee the process.
- Do you need to get budget approval before you begin? If so, how long will it take?
- What timeline has the vendor provided for completion of the system? You may want to build a bit of extra time into your schedule. That way, a delay on the vendor’s end will not throw you off.
- Will the installation of your system interrupt business? Can you schedule hardware installation on a night or weekend to avoid it?
- How will the project affect your clients, if at all? What can you do to shield them from delays?
Taking these things into consideration, create your timetable. Adding a bit of cushioning is smart. It allows you to make room for the unexpected. There are always things you cannot control. Building some extra time into your schedule can help you prepare for them.
Step #7: Create a Step-by-Step Recovery Plan
As your plan is constructed, put together detailed instructions on how to use it. Ideally, this should include an easy to follow a security incident response checklist.
Keep in mind that the people in charge of backups may refine your procedures. That is a natural part of doing business.
At the minimum, your recovery process should include:
- The type of recovery to necessary
- The data set to be recovered
- Dependencies that affect the recovery
- Any post-restoration steps to be taken
You may need input from your vendors or service providers. As much as possible, the people who will be responsible for backups should be involved.
Step #8: Test Your New Backup System
The final step is to test your backups. Testing should be an ongoing task. Ideally, you would do it after every backup. Since that is not practical, you will need to choose a schedule that works.
Let us start by talking about what to test.
You will want to check to make sure that:
- Your backup was successful, and the data you to secure is there
- Your restoration process is smooth and goes without a hitch
- Employees know what to do and when to do it
- There are no glitches or problems with the backup
That is a lot to test. Let us start with the data, since for most companies that is the most important thing. Data testing may involve:
- File recovery. Can you retrieve an individual file from the backup? This is the most straightforward test, but a necessary one. Users may accidentally delete or damage files. You need to be able to get them back.
- VM recovery. Virtual machines only apply to virtual environments. If that applies to you, you will want to make sure you can restore the VM from your backups. You will also want to check your application licensing for conflicts.
- Physical server recovery can vary depending on your hardware configuration. Some back up from SAN, while others use a local disk. Make sure you know what the process is and how to do it.
- Data recovery may also vary. However, if you are backing up a database at the app level, you may want to check that you can restore it.
- Application recovery can be complicated. You will need to understand the relationships between your apps and servers. It may be best to conduct this test in an isolated environment.
Once you have confirmed the backups work, you will want to create a testing schedule. There are several options:
- Set up a time-based schedule. For example, you might do a complete test of your backup once a week, or once a month. The frequency should be decided by your needs.
- Schedule additional tests after changes in your data. For example, if you add a new app or upgrade an old one, testing is a good idea.
- If you have an influx of data, schedule a test to make sure it is secure. The data may come with a new application. Alternatively, it may be the result of a merger with another company. Either way, you will want to be sure that the backup is capturing the new data.
With a schedule in place, you will be sure that your backups will be there if you need them.

Don’t Overlook Backup Strategies For Your Business
No company should be without a comprehensive backup system.
It is the only way to prevent data loss. Every business has some risk. Whether your primary concern is a natural disaster, cybercrime, or employee carelessness, having a secure backup system can give you the peace of mind you need.
Recent Posts
What is Object Storage? How it Protects Data
Object storage architecture inherently provides an extra security layer for your data. As such, it can be an ideal solution to avoid ransomware threats.
First, let’s start with explaining the differences between traditional storage solutions and object storage.
Object storage vs. Block Storage
With traditional block and file storage, information is typically stored in file systems that allow you to locate each item by following the defined path to that file.
If you need to share data among a group of users through a network, it is best to do so over network-attached storage (NAS). This will work great on a local architecture network (LAN) but might not be so great via wide area network (WAN).
While managing several NAS boxes is not that hard; doing so with hundreds of boxes makes things difficult. When the number of files and users grows substantially, it takes a lot of time and effort to find a particular file. In addition to this, you might even reach your storage file-limit sooner than expected.
Traditional storage was not designed for terabytes of data, so there is a good chance of data loss in the first two years.
Prominent characteristics of traditional storage include:
- Files are shared via NAS or SAN
- Each edit deletes the previous version of that file, and it cannot be restored on the device
- Connecting NAS boxes for scaling
- A file system is located by following its destination path
- Initially, it is straightforward to set up
- Configured with standard file level protocols, like NTFS, NFS, etc.
When talking about cost-considerations, you need to plan your requirements over time carefully. Having too much storage means you will pay for resources you do not need. On the other hand, not having any buffer room might put you in a tight spot when faced with no storage space.
Ransomware was explicitly created to take advantage of the shortcomings of block-and-file storage by encrypting files and locking out users.
Malicious software can even circumvent a volume snapshot service (VSS). That means that you would not be able to recover shadow versions either.
How Object Storage Works
Object storage creates immutable sets of data. It includes versioning and elaborate geo-diverse data replication schemes.
When I say immutable, I mean that data cannot be modified once created. To further clarify, it can be modified, but each edit is saved as a new version.
Object Storage uses flat-file data architecture and stores data in unchangeable containers or so-called buckets. Data, along with its metadata and unique ID, is bundled up in objects.
IT admins gain more control over their objects by assigning a virtually unlimited number of metadata fields. This is an inherent advantage over traditional storage. Thanks to metadata and the unique identifier that lets you locate objects easily, object storage works perfectly for unstructured data such as 4K videos, medical archives, or other large files.
Due to its lack of data hierarchy, object storage features scalability which could not have ever been achieved with block storage.
Advantages of object storage include:
- Continually scalable without any significant performance degradation
- Perfect for high volumes and large files
- Safer thanks to immutable data
- Capable of versioning
- Features replication schemes
- Good at maintaining data integrity
- Cost-effective
- Excellent for dealing with ransomware
- Perfect for file-sharing
- Unparalleled when it comes to metadata
This may sound like object storage is the best thing ever. However, the truth is that this approach is quite specific and not a good fit for every use case.
For example, object storage does not work well for frequently modified data, as there is no guarantee that a GET request will return the most recent version of the object. Furthermore, since objects are accessed via REST API, you may need to do a little bit of coding to make direct REST-based calls.
Even if it is not a one-fits-all solution, object storage does address problems that cannot be solved efficiently with traditional storage.
Object storage is perfect for:

1. Big Data
Big data is a huge (no pun intended) part of 21st century IT. It provides an answer to the ever-growing demand for more storage. In most cases, big data is unstructured and varies in the file type.
Let’s take for example Facebook and the social media phenomenon. This is a relatively new and non-traditional source of data that are being processed by analytics apps. The results are massive amounts of unstructured data. In such conditions, an object storage environment offers the necessary scalability, security, and accessibility.
2. Creating Backup Copies
I cannot stress enough the fact that it is an excellent fit for frequently used, but seldom modified data.
If you are not using a supported backup utility, such as Veeam Cloud Connect of R1Soft, you can leverage object storage for backing up your data. To do this, you would need to use the right cloud backup solution or software, such as Cloudberry Backup.
3. Archives
An archive is not the same as a backup. Backups are files that are very rarely used, and we turn to backups only if something goes wrong. Archives are similar but serve a different purpose.
Compared to backups, archives are accessed more frequently and serve to store and quickly obtain large quantities of data. Businesses with various backgrounds may store medical files in the cloud, engineering documents, videos, and other unstructured data.
After a while, it may become increasingly difficult to find an individual file, not to mention secure all data. However, with object storage IT admins can quickly secure and maintain data integrity, all the while providing easy access.
4. Media & Entertainment
It has never been easier to share information, whether you are on the receiving or giving end. However, nobody seems to think about the resources necessary to store such vast amounts of unstructured data. S3 object storage is especially useful for this use case, as it is easy to build entire front-facing apps based on its API. Perfect for media & entertainment.
5. Hosting a Static Website
Object storage has a suitable architecture for hosting static websites thanks to its virtually infinite scalability. This means it will scale automatically to your traffic needs.
Public users will access your data via the web, just like with any other hosted website. However, it must be noted that no personalized data can be displayed based on cookies and there is no support for server-side scripting. So, there are some limitations.
6. Streaming Services
With the emergence of online video streaming services and the internet becoming globally available, keeping chunks of data in a single location no longer makes much sense. You need fast global access, unlimited storage (a 1h raw 4k video can take as much as 130GB!), scalability, durability, and excellent metadata management.
Object storage technology ticks all the right checkboxes, and it helps that it was built for HTTPS. The best thing is that you can use object storage for several use cases at the same time.
Ransomware, the Role That Object Storage Vendors Can Play
Official statistics claim that ransomware took in $209 million in 2016 alone, while the cost of downtime was even higher. Datto’s report found that 48% of businesses lost critical data when faced with such threats. This is a loss that cannot be easily measured in dollars.
In 2018, ransomware continued to dominate the world of cybersecurity. 6 out of 10 malware payloads in Q1 were ransomware. From WannaCry to NotPetya and BadRabbit, we can safely say that ransomware threats have marked the year behind us. Furthermore, we can safely assume that ransomware has become the biggest security threat any organization or individual may face in the cyber realm.
Recent Posts
Protecting Business Data During a Natural Disaster: A Hurricane Irma Story
Definitive 7 Point Disaster Recovery Planning Checklist
The need for a comprehensive disaster recovery plan cannot be felt more than in the aftermath of massive hurricanes that recently ravaged the west coast of the US.
Days-long power knockouts, physical blows, and supply chain breakdowns left thousands of businesses in the dark. Most of them are now facing insurance fights and significant infrastructure rebuilds to get back on track.
These are complex challenges that many will struggle to overcome. The organizations that had disaster recovery and business continuity plans in place now have one less thing to worry about.
Designed to enable businesses to reduce damages of unpredicted outages, a disaster plan is a long-term assurance of business operability. While a disaster of this scale is not an everyday scenario, it can be fatal to business operations.
And it can happen to anyone.
In one form or another, natural disasters and human errors are a constant possibility, and this is why it makes sense to prepare for them. When you add different types of cyber-attacks to the mix, the value of a disaster recovery checklist is even more significant.
This is especially true when you take into account that the average cost of downtime can go up to $5600 per minute in mid-sized businesses and up to $11,000 per minute in enterprises.
With every second of outage counting against your profits, avoiding any impact of downtime is a strategic aim. This is best achieved by preparing your entire infrastructure to resist and stay operational even in the harshest situations.
Why You Need Disaster Recovery Plan: Case Study
While the probability of a disaster may often seem hypothetical, some recent events confirmed that hazards are a real thing. And costly, too.
Hurricanes Irma and Harvey are some of the most striking examples, but a lot of other things can go wrong in business and cause disruptions. One of the cases in point took place earlier in May when British Airways suffered a significant infrastructure technology system collapse. The three-day inoperability left thousands of passengers stuck at airports across the world, while the company worked to identify and fix the error to get their critical systems back online. The entire data disaster reportedly cost 500 million pounds to the company, while its reputation is still on the line.
When it comes to business disruptions, it does not get more real than that.
The BA case is yet another unfortunate confirmation of the fact that unplanned outages can take place anytime and in any company. The ones that have no stable disaster recovery and business continuity plans are bound to suffer extreme financial and reputational losses. This is especially the case with those that have complex and globally dispersed IT infrastructures, where 100% availability is paramount.
Events like these call for a discussion on the disaster recovery best practices that may help companies like this avoid any similar collapses in the future. Below is an overview of the critical items that need to be in the data management plan. What is disaster recovery planning?
1. Risk assessment and business impact analysis (BIA)
The best way to fight the enemy is to get to know the enemy.
The same goes for disaster recovery planning, where the first step is to identify possible threats and their likelihood to impact your businesses. The outcome of this process is a detailed risk analysis with an overview of some common threats in the context of your business.
Start the disaster recovery planning process with a risk assessment. Develop a risk matrix, where you will classify the types of disasters that can occur. The risk matrix is essential to establish priorities and identify the scope of damage that can be devastating for business.
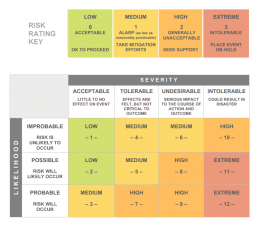
Resource: smartsheet
After you identify and analyze the risks, you can create a business impact analysis (BIA). This document should help you understand the actual effects of any unfortunate event that can hit your business. Whether it is a loss of physical access to premises, system collapse, or inability to access data files, this matrix is a base for planning the next steps.
To get started with BIA, you can use FEMA’s resource with a simple disaster recovery plan template.
2. Recovery Time Objective (RTO) and Recovery Point Objective (RPO)
RTO and RPO are critical concepts in disaster recovery planning, whether your data resides in a dedicated hosting or virtualized environments.
As a reminder, these two refer to the following:
- The amount of time needed to recover all applications (RTO)
- The amount of data loss that you risk losing during disaster recovery, calculated in relation to the amount of time required to complete the process (RPO)
RTO and RPO real-life values will vary between companies. Setting RTO and RPO goals should involve a cross-department conversation to best assess business needs in this respect.
The objectives you define this way are the foundation of an effective disaster recovery plan. They also determine which solutions to deploy. This refers to both hardware and software configurations needed to recover specific workloads.

3. Response strategy guidelines and detailed procedures
Documenting a written DR plan is the only way to ensure that your team will know what to do and where to start when a disaster happens.
Written guidelines and procedures should cover everything from implementing DR solutions and executing recovery activities to infrastructure monitoring and communications. Additionally, all the relevant details about people, contacts, and facilities should be included to make every step of the process transparent and straightforward.
Some of the general process documents and guidelines to develop include:
- Communication procedures, outlining who is responsible for announcing the disaster and communicating with employees, media, or customers about it;
- Data Backup procedures, with a list of all facilities or third-party solutions used for document backups.
- Guidelines for initiating a response strategy (responsible staff members, outline of critical activities, contact persons, etc.)
- Post-disaster activities that should be carried out after critical apps and services are reestablished (contacting customers, vendors, etc.).
The key to developing effective procedures is to include as many details as possible about every activity. The essential ones are a) name of a responsible person with contact details, b) action items, c) activity timeline, and e) how it should be done. This way, you can achieve full transparency for every critical process in the overall DRP.
4. Disaster recovery sites
Putting the plan to work also involves choosing the disaster recovery site where all vital data, applications, and physical assets can be moved in case of a disaster. Such a site needs to support active communications, meaning that they should have both critical hardware and software in place.
Traditionally, three types of sites are used for disaster recovery:
- A hot site, which is defined as a site that allows a “functional data center with hardware and software, personnel and customer data;”
- A warm site that would allow access to all critical applications excluding customer data;
- A cold site, where you can store IT systems and data, but that has no technology until the IT disaster recovery checklist is put into motion.
Most DR solutions automatically backup and replicate critical workloads at multiple sites to strengthen and speed up the recovery process. With the advances in virtualization and replication technologies, DR capabilities that are at the disposal of modern companies are many. Choosing the right one involves finding the balance between price, technology, and a provider’s ability to cater to your own needs.

5. Incident Response Team
When a disaster strikes, all teams get involved. To efficiently carry out a disaster recovery plan, you should name specific people to handle different recovery activities. This is key to ensuring that all the tasks will be completed as efficiently as possible.
The activities of the incident response team will vary, and they should be defined within DR guidelines and procedure documents. Some of these include communicating with employees and external media, monitoring the systems, system setup and recovery operations.
Like with all the other guidelines and procedures, details about incident response team should include:
- The action to complete
- The job role of a person responsible for completing the work
- Name/contact details of a person responsible
- The timeframe in which the activity should be completed
- Steps that more closely describe the operation
The Incident response team will involve multiple departments – from technicians to senior management – each of which may have an essential role in minimizing the effects of a disaster.
6. IT Disaster Recovery Services
Recovering complex IT systems may require massive manpower, hardware resources, and technical knowledge. Many of these can be supplemented by third-party resources and cloud computing solutions. Cloud-based resources are particularly handy to optimize costs and shift parts of the infrastructure to remote servers, which brings higher security and better use of costs.
In companies where not all workloads are suitable for public cloud backup, a balanced distribution between on-site and cloud servers is a cost-effective way to configure infrastructure. Similarly, a hybrid approach to an IT disaster recovery plan is ideal for companies with advanced recovery needs.
A particularly convenient option for businesses of any size is Disaster-Recover-as-a-Service (DRaaS), which offers greater flexibility to teams operating within a limited DR budget. DRaaS allows access to critical infrastructure and backup resources at an affordable price point. It can also be used in both virtualized and dedicated environments, which makes it suitable for companies of any size and any infrastructure need.

7. Maintenance and testing activities
Once created, a disaster recovery plan needs to be reviewed and tested regularly. This is the only way to ensure that it is efficient long-term and that it can be applied in any scenario.
While most modern businesses now have recovery strategies in place, many of them are outdated and not aligned with a company’s current needs. This is why the plan needs to be updated to reflect any organizational or staff changes, especially in companies that grow rapidly.
All the critical applications and procedures should be regularly tested and monitored to ensure they are disaster-ready. This is best achieved by assigning a specific task to the defined disaster recovery teams and training employees on disaster recovery best practices.
Closing Thoughts: IT Disaster Recovery Planning & Procedures
Given the dynamics of today’s business, occasional disruptions seem inevitable, no matter the company size. The significant disasters we have seen recently only enhance the sense of uncertainty and the need to protect critical data and applications.
While a disaster recovery checklist may have many goals, one of its most significant values is its ability to reassure company staff that they can handle any scenario and restore normal business operations. The suggestions given above are intended to guide your company up to this path.
Need more details about DR? Follow the link below to download our FREE guide!
Recent Posts
Business Continuity Plan Best Practices
As companies continued to amass customer information and business analytics, ensuring their constant availability has only become more instrumental for organizational development.
Today, business continuity and disaster recovery are crucial parts of business growth strategies. They have become key to ensuring consistent access to mission-critical assets, especially as disastrous events grew in size and number.
As illustrated in the DRaaS infographic by Zerto, about 45% of companies experienced an outage or downtime this year, and each of them resulted in some form of business disruption. Cloud disaster recovery has become a viable solution for disaster and backup protection.
Even the slightest moment of downtime may translate into an economic loss. Business continuity recovery plans can help businesses realize the following benefits:
- Achieve maximum availability of mission-critical data
- Maintain continuity of business operations even in the harshest scenarios
- Have processes in place to minimize recovery time after a disaster
- Ensure the highest level of data security
- Enhance business resiliency and maintain reputability
Considering all these advantages, safeguarding business assets with business continuity planning is critical for every organization. Companies need to rethink their IT infrastructure and deploy reliable solutions that utilize industry-leading DR technologies.

Best Practices of Business Continuity Planning
Even the slightest moment of downtime can be not only a frustrating but also a costly experience. According to a 2016 survey by Veeam, the estimated average annual cost of downtime in enterprises can be up to $16 million, which is a $6 million increase compared to 2014. This figure alone points to the enormous need to develop and implement business continuity best practices, which should address the most common issues.
From UPS battery failure, human error, and IT equipment failure to weather-related disasters, which are among the most frequent causes of downtime, an effective business continuity plan should cover a diversity of situations. It should be highly flexible and contain a set of guiding principles for different parts of an organization that should be developed and followed with the ultimate care.
- Use Proactive IT risk management through a set of procedures regulating risk mitigation, response, recovery, and restoration.
- Training staff or hiring a reliable third-party provider.
- Establish a seamless and effective business continuity checklist.
- Assess risk sensitivity to meet any specific compliance requirements.
- Implement consistent review and design of a proper recovery architecture.
- Create adequate budgets that cover every aspect of the plan.

Where disaster recovery fits into your business plan
The interdependence of business continuity management and disaster recovery plans lies in the fact that the latter typically supports several aspects of the former.
A single BC plan can thus involve a set of disaster recovery plans. Its purpose is to document all the steps needed to protect the IT environment and ensure its quick recovery after a disastrous event. While there are many technical definitions of disaster recovery, the one given by Phil Goodwin, IDC Research Director, captures its essence. Namely, he states that “Disaster recovery is the classic combination of people, process, and technology,” which suggests that DR includes not only stable infrastructure but also a team that can follow the DR plan effectively.
The disaster recovery plan should include risk assessment, identifying sets of data to protect, ensuring the availability of IT teams (either in-house or externally), and deciding on the capabilities you need to allow for rapid restoration of data within the budget. In addition to this, it should also cover analysis, migration, and facility planning to ensure its maximum efficiency.
In companies with small IT teams, some of these responsibilities would be shifted to the chosen IT vendor that would be expected to provide the best in class hardware solutions and technical assistance. For such teams, in particular, Disaster Recovery as a Service (DRaaS) emerges as a cost-effective solution to support the overall business continuity plan with high-performance IT systems that improve business resiliency. Powerful and affordable, DRaaS helps organizations enhance their operability and ensure better preparedness for disastrous events.
For CIOs and CTOs contemplating the implementation of powerful DRaaS solutions, further information on how they can best be utilized is given in the Zerto DRaaS guide below.