Are you searching for the right firewall setup to protect your business from potential threats?
Understanding how firewalls work helps you decide on the best solution. This article explains the types of firewalls, allowing you to make an educated choice.
What is a Firewall?
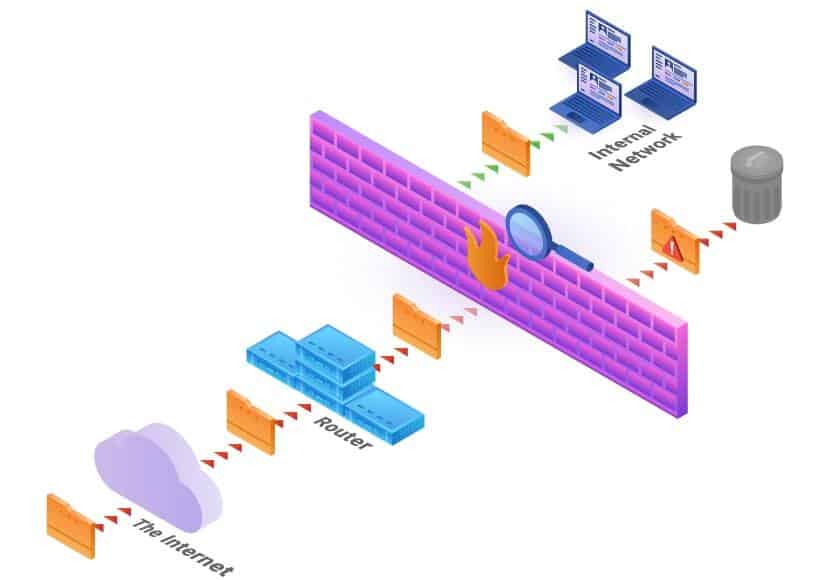
A firewall is a security device that monitors network traffic. It protects the internal network by filtering incoming and outgoing traffic based on a set of established rules. Setting up a firewall is the simplest way of adding a security layer between a system and malicious attacks.
How Does a Firewall Work?
A firewall is placed on the hardware or software level of a system to secure it from malicious traffic. Depending on the setup, it can protect a single machine or a whole network of computers. The device inspects incoming and outgoing traffic according to predefined rules.
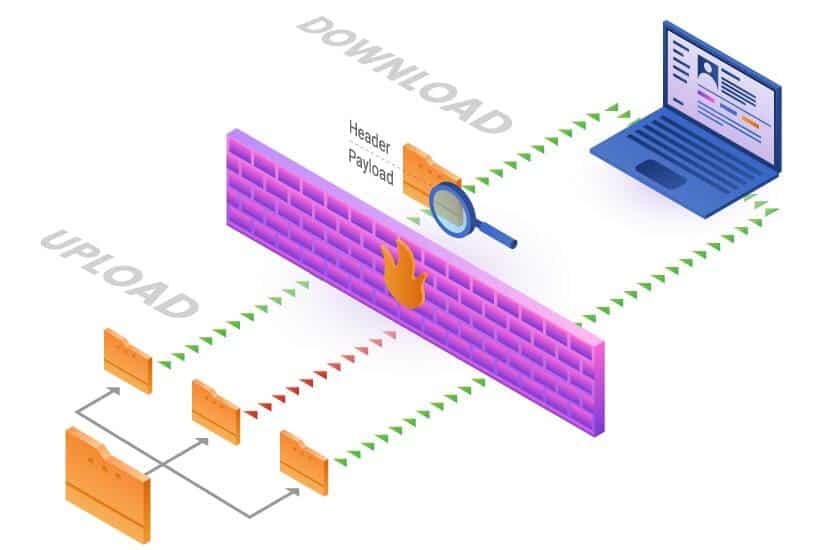
Communicating over the Internet is conducted by requesting and transmitting data from a sender to a receiver. Since data cannot be sent as a whole, it is broken up into manageable data packets that make up the initially transmitted entity. The role of a firewall is to examine data packets traveling to and from the host.
What does a firewall inspect? Each data packet consists of a header (control information) and payload (the actual data). The header provides information about the sender and the receiver. Before the packet can enter the internal network through the defined port, it must pass through the firewall. This transfer depends on the information it carries and how it corresponds to the predefined rules.
For example, the firewall can have a rule that excludes traffic coming from a specified IP address. If it receives data packets with that IP address in the header, the firewall denies access. Similarly, a firewall can deny access to anyone except the defined trusted sources. There are numerous ways to configure this security device. The extent to which it protects the system at hand depends on the type of firewall.
Types of Firewalls
Although they all serve to prevent unauthorized access, the operation methods and overall structure of firewalls can be quite diverse. According to their structure, there are three types of firewalls – software firewalls, hardware firewalls, or both. The remaining types of firewalls specified in this list are firewall techniques which can be set up as software or hardware.
Software Firewalls
A software firewall is installed on the host device. Accordingly, this type of firewall is also known as a Host Firewall. Since it is attached to a specific device, it has to utilize its resources to work. Therefore, it is inevitable for it to use up some of the system’s RAM and CPU.
If there are multiple devices, you need to install the software on each device. Since it needs to be compatible with the host, it requires individual configuration for each. Hence, the main disadvantage is the time and knowledge needed to administrate and manage firewalls for each device.
On the other hand, the advantage of software firewalls is that they can distinguish between programs while filtering incoming and outgoing traffic. Hence, they can deny access to one program while allowing access to another.
Hardware Firewalls
As the name suggests, hardware firewalls are security devices that represent a separate piece of hardware placed between an internal and external network (the Internet). This type is also known as an Appliance Firewall.
Unlike a software firewall, a hardware firewall has its resources and doesn’t consume any CPU or RAM from the host devices. It is a physical appliance that serves as a gateway for traffic passing to and from an internal network.
They are used by medium and large organizations that have multiple computers working inside the same network. Utilizing hardware firewalls in such cases is more practical than installing individual software on each device. Configuring and managing a hardware firewall requires knowledge and skill, so make sure there is a skilled team to take on this responsibility.
Packet-Filtering Firewalls
When it comes to types of firewalls based on their method of operation, the most basic type is the packet-filtering firewall. It serves as an inline security checkpoint attached to a router or switch. As the name suggests, it monitors network traffic by filtering incoming packets according to the information they carry.
As explained above, each data packet consists of a header and the data it transmits. This type of firewall decides whether a packet is allowed or denied access based on the header information. To do so, it inspects the protocol, source IP address, destination IP, source port, and destination port. Depending on how the numbers match the access control list (rules defining wanted/unwanted traffic), the packets are passed on or dropped.
If a data packet doesn’t match all the required rules, it won’t be allowed to reach the system.
A packet-filtering firewall is a fast solution that doesn’t require a lot of resources. However, it isn’t the safest. Although it inspects the header information, it doesn’t check the data (payload) itself. Because malware can also be found in this section of the data packet, the packet-filtering firewall is not the best option for strong system security.
***This table is scrollable horizontally.
| PACKET-FILTERING FIREWALLS | |||
| Advantages | Disadvantages | Protection Level | Who is it for: |
| – Fast and efficient for filtering headers.
– Don’t use up a lot of resources. – Low cost. |
– No payload check.
– Vulnerable to IP spoofing. – Cannot filter application layer protocols. – No user authentication. |
– Not very secure as they don’t check the packet payload. | – A cost-efficient solution to protect devices within an internal network.
– A means of isolating traffic internally between different departments. |
Circuit-Level Gateways
Circuit-level gateways are a type of firewall that work at the session layer of the OSI model, observing TCP (Transmission Control Protocol) connections and sessions. Their primary function is to ensure the established connections are safe.
In most cases, circuit-level firewalls are built into some type of software or an already existing firewall.
Like pocket-filtering firewalls, they don’t inspect the actual data but rather the information about the transaction. Additionally, circuit-level gateways are practical, simple to set up, and don’t require a separate proxy server.
***This table is scrollable horizontally.
|
CIRCUIT-LEVEL GATEWAYS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Resource and cost-efficient.
– Provide data hiding and protect against address exposure. – Check TCP handshakes. |
– No content filtering.
– No application layer security. – Require software modifications. |
– Moderate protection level (higher than packet filtering, but not completely efficient since there is no content filtering). | – They should not be used as a stand-alone solution.
– They are often used with application-layer gateways. |
Stateful Inspection Firewalls
A stateful inspection firewall keeps track of the state of a connection by monitoring the TCP 3-way handshake. This allows it to keep track of the entire connection – from start to end – permitting only expected return traffic inbound.
When starting a connection and requesting data, the stateful inspection builds a database (state table) and stores the connection information. In the state table, it notes the source IP, source port, destination IP, and destination port for each connection. Using the stateful inspection method, it dynamically creates firewall rules to allow anticipated traffic.
This type of firewall is used as additional security. It enforces more checks and is safer compared to stateless filters. However, unlike stateless/packet filtering, stateful firewalls inspect the actual data transmitted across multiple packets instead of just the headers. Because of this, they also require more system resources.
***This table is scrollable horizontally.
|
STATEFUL INSPECTION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Keep track of the entire session.
– Inspect headers and packet payloads. – Offer more control. – Operate with fewer open ports. |
– Not as cost-effective as they require more resources.
– No authentication support. – Vulnerable to DDoS attacks. – May slow down performance due to high resource requirements. |
– Provide more advanced security as it inspects entire data packets while blocking firewalls that exploit protocol vulnerabilities.
– Not efficient when it comes to exploiting stateless protocols. |
– Considered the standard network protection for cases that need a balance between packet filtering and application proxy. |
Proxy Firewalls
A proxy firewall serves as an intermediate device between internal and external systems communicating over the Internet. It protects a network by forwarding requests from the original client and masking it as its own. Proxy means to serve as a substitute and, accordingly, that is the role it plays. It substitutes for the client that is sending the request.
When a client sends a request to access a web page, the message is intersected by the proxy server. The proxy forwards the message to the web server, pretending to be the client. Doing so hides the client’s identification and geolocation, protecting it from any restrictions and potential attacks. The web server then responds and gives the proxy the requested information, which is passed on to the client.
***This table is scrollable horizontally.
|
PROXY FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Protect systems by preventing contact with other networks.
– Ensure user anonymity. – Unlock geolocational restrictions. |
– May reduce performance.
– Need additional configuration to ensure overall encryption. – Not compatible with all network protocols. |
– Offer good network protection if configured well. | – Used for web applications to secure the server from malicious users.
– Utilized by users to ensure network anonymity and for bypassing online restrictions. |
Next-Generation Firewalls
The next-generation firewall is a security device that combines a number of functions of other firewalls. It incorporates packet, stateful, and deep packet inspection. Simply put, NGFW checks the actual payload of the packet instead of focusing solely on header information.
Unlike traditional firewalls, the next-gen firewall inspects the entire transaction of data, including the TCP handshakes, surface-level, and deep packet inspection.
Using NGFW is adequate protection from malware attacks, external threats, and intrusion. These devices are quite flexible, and there is no clear-cut definition of the functionalities they offer. Therefore, make sure to explore what each specific option provides.
***This table is scrollable horizontally.
|
NEXT-GENERATION FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Integrates deep inspection, antivirus, spam filtering, and application control.
– Automatic upgrades. – Monitor network traffic from Layer 2 to Layer 7. |
– Costly compared to other solutions.
– May require additional configuration to integrate with existing security management.
|
– Highly secure. | – Suitable for businesses that require PCI or HIPAA compliance.
– For businesses that want a package deal security device. |
Cloud Firewalls
A cloud firewall or firewall-as-a-service (Faas) is a cloud solution for network protection. Like other cloud solutions, it is maintained and run on the Internet by third-party vendors.
Clients often utilize cloud firewalls as proxy servers, but the configuration can vary according to the demand. Their main advantage is scalability. They are independent of physical resources, which allows scaling the firewall capacity according to the traffic load.
Businesses use this solution to protect an internal network or other cloud infrastructures (Iaas/Paas).
***This table is scrollable horizontally.
|
CLOUD FIREWALLS |
|||
|
Advantages |
Disadvantages | Protection Level |
Who is it for: |
| – Availability.
– Scalability that offers increased bandwidth and new site protection. – No hardware required. – Cost-efficient in terms of managing and maintaining equipment. |
– A wide range of prices depending on the services offered.
– The risk of losing control over security assets. – Possible compatibility difficulties if migrating to a new cloud provider. |
– Provide good protection in terms of high availability and having a professional staff taking care of the setup.
|
– A solution suitable for larger businesses that do not have an in-staff security team to maintain and manage the on-site security devices. |
Which Firewall Architecture is Right for Your Business?
When deciding on which firewall to choose, there is no need to be explicit. Using more than one firewall type provides multiple layers of protection.
Also, consider the following factors:
- The size of the organization. How big is the internal network? Can you manage a firewall on each device, or do you need a firewall that monitors the internal network? These questions are important to answer when deciding between software and hardware firewalls. Additionally, the decision between the two will largely depend on the capabilities of the tech team assigned to manage the setup.
- The resources available. Can you afford to separate the firewall from the internal network by placing it on a separate piece of hardware or even on the cloud? The traffic load the firewall needs to filter and whether it is going to be consistent also plays an important role.
- The level of protection required. The number and types of firewalls should reflect the security measures the internal network requires. A business dealing with sensitive client information should ensure that data is protected from hackers by tightening the firewall protection.
Build a firewall setup that fits the requirements considering these factors. Utilize the ability to layer more than one security device and configure the internal network to filter any traffic coming its way. For secure cloud options, see how phoenixNAP ensures cloud data security.