31 Must-Know Healthcare Cybersecurity Statistics 2020
The healthcare industry is a prime target of hackers. The importance of cybersecurity in healthcare is an essential consideration for all organizations handling patient data.
Be aware of the latest numbers; read our article on the latest Healthcare Cybersecurity Statistics.
Healthcare Data Breaches, By the Numbers
1. 89% of healthcare organizations experienced a data breach in the past two years. Despite the sophisticated measures put in place by providers to prevent data breaches , they are still common. (Source: Dizzion).
2. A Mid-Horizon study concluded that approximately 100 percent of web applications connected to critical health information is vulnerable to cyber attacks. Network penetration results also showed that hackers could easily access domain level admin privileges of most healthcare applications. As a result, the use of advanced technologies such as block-chain and cloud computing is necessary to ward off such attacks in the future. (Source).
3. It is estimated that the loss of data and related failures will cost healthcare companies nearly $6 trillion in damages in the next three years compared to $3 trillion, in 2017. From a statistical point of view, it is the most significant transfer of wealth in human history. If proper security measures are not taken, experts believe that cybercrime can have a devastating financial impact on the healthcare sector in the next four to five years. (Source).
4. 82% of surveyed healthcare organizations agree that digital security is one of their foremost concerns. (Source: Health IT Security)
5. 55% of healthcare companies in the United States faced cyber attacks. Almost one-fifth confirmed that they had been attacked in the last 12 months. (Source).
Healthcare Ransomware Statistics
Ransomware has brought many a healthcare organization to its knees. It is likely to remain one of the most prominent threats of 2019 and beyond. Despite increasing awareness among healthcare professionals, the number of ransomware attacks continues to grow.
6. Ransomware attacks on the healthcare sector will quadruple by 2020. Attackers like to attack the healthcare sector due to the potential value of such data. The healthcare sector is prone to paying the ransom because the disruption, lost productivity, and damage to the data can be more expansive than preventing the loss by paying the ransom. (Source: Herjavec Group Healthcare Report)
7. As of 2018, the number of ransomware families dropped from 98 to only 28. However, there were 350 different variants of ransomware observed in 2018 compared to 241 in the previous years. It means that ransom-takers are using more sophisticated tactics to hack into vulnerable systems. (Source)
8. Healthcare organizations are more willing to pay ransom to avoid downtime and gain access to critical patient data. It is estimated that 23 percent of healthcare organizations paid some form of payment to the attackers. The healthcare industry is vulnerable because it uses legacy systems that are mostly out-dated and vulnerable to attacks. (Source: Infosecurity Magazine)
9. Organizations that handle healthcare data that fail to update their systems may face grave consequences in the future. The majority of healthcare ransomware attacks were malware related. Of the 2,600 incidents reported, 36 percent were malware related followed by accidental disclosure in 26 percent of the cases. (Source: Beazley Breach Briefing)
Implementation of Advanced Security Technologies To Fight Back
10. The nature of cybersecurity spending in the healthcare sector varies significantly due to the specific requirements of organizations. A majority of companies are spending their budgets on network security and investing in mobile protection measures. Another 51% are also spending on advanced technologies that will make data on the move more secure during data transfers. (Source: HIPPA Journal)
11. A large number of healthcare firms are migrating to a cloud-based solution. Despite the safety as their prime concern, 25% of the firms suggest that they are not encrypting their information during data transfer to the cloud. 38% of firms that have data in a multi-cloud environment such as Amazon Web Service does not use encrypted technology. (Source: Hytrust)
12. 60% of healthcare organizations globally have introduced IoT devices into their facilities. The Internet of Things has seen an exponential rise in the use of IoT enabled devices in a range of fields. Wearable and implantable IoT devices are already widely used in healthcare, including insulin level monitors to pacemakers. (Source: Statista)
Cybersecurity IT Talent: Human Weakness
We tend to think of cybersecurity as a system of digital checks and balances. But while this is important, organizations should still consider the human component. Even if you’re spending heavily on automated systems, it means little if you don’t have the right people to implement and manage them.
13. 42% of healthcare organizations leave their cybersecurity in the hands of a vice president or C-level official (Source: Chime).
14. 39% report their biggest challenge when it comes to implementing cyber defenses is the lack of qualified employees (Source: HIPAA Journal).
15. 37% say that less than 1 in 4 candidates are skilled enough to keep their companies secure (Source: Health IT Security).
16. Cybersecurity requires specific knowledge and skills to secure and combat attacks. Often, these skills are not easy to find as 27 percent of healthcare firms reported that they are unable to find suitable candidates to fulfill cybersecurity roles. Another 14 percent suggested that they are not sure if they will be able to fill vacant positions. The ISACA State of Cyber Security Report also concluded that 45 percent of firms don’t think that their applicants understand the nature of their job (Source).
17. If the budget doesn’t restrict healthcare firms to improve their security, the complexity of the system does. 53 percent of the healthcare firms surveyed revealed that complexity of healthcare systems is the major issue holding them back. Healthcare systems can be complicated as lack of experienced and knowledgeable staff to handle such complex systems is another significant concern, cited by 39 percent of firms (Source: Thales Data Threat Report).
18. For small and medium-sized healthcare firms, cloud adaption is a haven from cyber attacks. Despite the early adaption of cloud-based technology by the healthcare sector, nearly 40 percent of these organizations do not have a dedicated staff that can deal with cloud-based problems. Without a dedicated team, small healthcare organizations can face threats while operating in a cloud environment. (Source: HIPPA Journal)
19. The most significant internal cybersecurity threats to healthcare are often high-ranking officials and senior staff who have deep access to the system. A whopping, 61 percent cited senior-level executives as a potential security loophole that can be vulnerable to cyber threats. Similarly, privileged users, such as executive managers, contractors, and service providers, are potential targets for hackers and cybercriminals. (Source: HIPPA Journal)
20. 59% of healthcare organizations get at least five applications for each cybersecurity job, while 13% receive 20 or more. While these healthcare security statistics make for sobering reading, there is some good news. The right candidates do appear to be out there. (Source: Health IT Security).
21. 54% of healthcare associates say their biggest problem is employee negligence in the handling of patient information (Source: Ponemon Study).
Healthcare Companies are Fighting Back
21. Healthcare organizations are taking cyber security seriously as 62 percent of companies have reported that a Vice President is in charge of cybersecurity issues. 41 percent of organizations are in the process of implementing a fully functional security program to address critical problems. (Source: Health IT Security)
22. Recent attacks on healthcare have prompted healthcare companies to increase their cybersecurity budgets from a maximum of 10 percent to almost 25 percent, in 2018. The increase in the budget is correlated to an increase in hiring staff for a specific purpose. In 2016, eight percent of the healthcare companies had more than 10 employees dedicated to the task, which increased to 11 percent, in 2017. (Source: Health IT Security)
23. In 2018, 60 percent of these firms put particular emphasis on cybercrime by increasing their staff, adding new technologies, and training their employees on such issues. Cybersecurity budgets continue to grow as 81 percent of U.S. firms indicate that they will improve their resources to keep critical systems safe. (Source: Healthcare IT News)
24. 57 percent of companies are ensuring that they meet local and global compliance standards of Internet security required in the healthcare sector. Of these, 34 percent confirmed that they are already looking to implement cybersecurity best practices for employees. (Source: HIPPA Journal)
25. Security breaches caused by the loss of sensitive items, such as laptops and other devices, have decreased sharply. While loss or theft of items accounted for nearly 90 percent of the losses in 2010, it has reduced to only 15 percent, in recent years. This is a clear sign that educating employees to take care of their data devices is critical to preventing incidents of theft. (Source)
26. 54% of healthcare organizations believe they have technologies in place to effectively prevent or quickly detect unauthorized access to patient data. An improvement over the 49% reported in 2015. (Source: Ponemon Institute)
5 Largest Healthcare Cyber Security Attacks & Breaches
Here are some of the most significant healthcare data breaches. What can your organization learn to avoid being the next victim?
1. LifeBridge Health
This Baltimore-based healthcare system experienced a malware attack last March. The attack potentially breached the data of around 500,000 patients. Investigations showed that the hackers first gained access to the system back in September 2016.
2. Health Management Concepts
This ransomware attack fast became a full-blown data breach. Hackers were mistakenly provided with a file containing the personal data of over 500,000 patients.
The organization has not disclosed how or why hackers got this information, but the file contained Social Security numbers, health insurance information, and patient names.
3. CNO Financial Group
Between May and September of last year, hackers gained access to the credentials of CNO employees. This information was then used to access company websites, compromising the data of over 566,000 policyholders and applicants.
Data accessed included dates of birth, insurance details, and partial Social Security numbers.
4. UnityPoint Health
UnityPoint suffered two security breaches last year. The second compromised the data of 1.4 million patients.
A series of phishing emails had been made to look like they were from a top executive within the company. When an employee fell for the scam, it gave hackers access to private email accounts.
5. AccuDoc
The data breach of billing vendor AccuDoc was the biggest of last year. The North Carolina-based vendor prepares patient bills while managing Atrium Health’s billing system. The investigation revealed that while hackers could view the data, they were unable to extract it.
Don’t Become a Healthcare Security Statistic
From these healthcare statistics, it is apparent that there has been an increased awareness among healthcare companies regarding cybersecurity. Despite the response, more needs to be done. All types of hacking attacks are also becoming more sophisticated and the data loss more costly. Solutions start with awareness, updating and maintaining critical systems, and emphasis on security during data transfer.
How vulnerable is your organization? Work with our team of security professionals and ensure that your employee and patient data is secure.
Recent Posts
Security vs Compliance: Are You Secure & Compliant? Learn the Differences
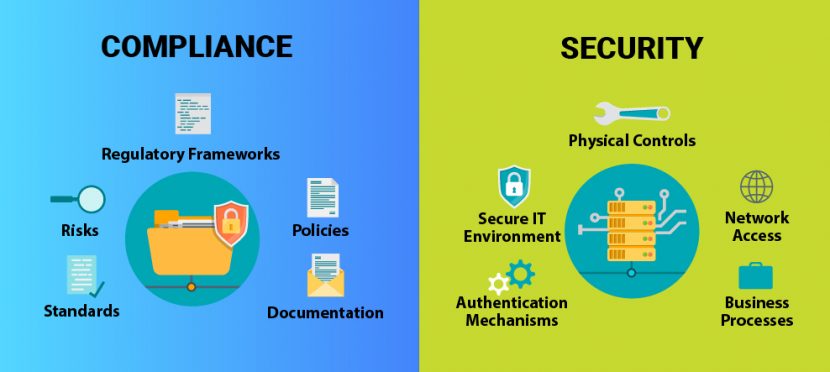
The time has arrived to think differently about security and compliance. Compliance is not security. In fact, you can be compliant but not secure.
Compliance doesn’t always achieve security.
Preparing For Todays Security Challenges
Information technology has grown in leaps and bounds over the last two decades with the industry set to top $5 trillion in 2019. With this immense growth comes complex new compliance and security challenges. Industry insiders know that it’s increasingly important to understand and control how companies share, store, and receive information. IT compliance frameworks are now in place to ensure this regulation of data happens securely, but they can differ extensively.
Breaking it down to its basics, becoming secure and compliant means securing information assets, preventing damage, protecting it, and detecting theft. These are the main mantras and mandates of cybersecurity teams, as they implement frameworks, which are predominantly technical to achieve compliance.
A company can protect its data accordingly if they follow Compliance frameworks and have quality security in place. To have proper protection, companies must understand that Compliance is not the same thing as security. However, security is a big part of compliance.
What are the Differences Between Compliance and Security?
Compliance focuses on the kind of data handled and stored by a company and what regulatory requirements (frameworks) apply to its protection. A company may have to align with multiple frameworks, and understanding these frameworks can be difficult. Their main goal is to manage risk and goes beyond information assets. They oversee policies, regulations, and laws and cover physical, financial, legal, or other types of risk. Compliance means ensuring an organization is complying to the minimum of the security-related requirements.
Security is a clear set of technical systems and tools and processes which are put in place to protect and defend the information and technology assets of an enterprise. Compliance is not the primary concern or prerogative of a security team, despite being a critical business requirement. Security can include physical controls as well as who has access to a network, for example. Standardized methods and tools provided by specialist vendors make security simpler than compliance. Compliance, on the other hand, can be multifaceted and is based on a company’s data type and security processes.
Compliance and Security Based on Specific Frameworks
Compliance studies a company’s security processes. It details their security at a single moment in time and compares it to a specific set of regulatory requirements. These requirements come in the form of legislation, industry regulations, or standards created from best practices.
Specifically, compliance frameworks include:
HIPAA
HIPAA (Health Insurance Portability and Accountability Act) applies to companies in the Health Insurance industry. It legislates how companies should handle and secure patients’ personal medical information. HIPAA compliance requires companies who manage this kind of information, to do so safely. The act has five sections, which it calls Titles. Title 2 is the section that applies to information privacy and security.
Initially, HIPAA aimed to standardize how the health insurance industry processed and shared data. It has now added provisions to manage electronic breaches of this information as well.
SOX
The Sarbanes-Oxley Act (also called SOX) applies to the corporate care and maintenance of financial data of public companies. It defines what data must be kept and for how long it needs to be held. It also outlines controls for the destruction, falsification, and alteration of data.
SOX attempts to improve corporate responsibility and add culpability. The act states that upper management has to certify the accuracy of their data.
All public companies must comply with SOX and its requirements for financial reporting. Classifying data correctly, storing it safely, and finding it quickly are critical elements of its framework.
PCI DSS
PCI DSS compliance is the Payment Card Industry Data Security Standard created by a group of companies who wanted to standardize how they guarded consumers’ financial information.
Requirements that are part of the standard are:
- A secured network
- Protected user data
- Strong access controls and management
- Network tests
- Regular reviews of Information Security Policies
There are four levels of compliance within the standard. The number of transactions a company completes every year determines what level they must comply with.
SOC Reports
SOC Reports are Service Organization Control Reports that deal with managing financial or personal information at a company. There are three different SOC Reports. SOC 1 and SOC 2 are different types with SOC 1 applying to financial information controls, while SOC 2 compliance and certification covers personal user information. SOC 3 Reports are publicly accessible, so they do not include confidential information about the company. These reports apply for a specific period, and new reports consider any earlier findings.
The American Institute for Chartered Public Accountants (AICPA) defined them as part of SSAE 18.
ISO 27000 Family
The ISO 27000 family of standards outlines minimum requirements for securing information. As part of the International Organization for Standardization’s body of standards, it determines the way the industry develops Information Security Management Systems (ISMS).
Compliance comes in the form of a certificate. More than a dozen different standards make up the ISO 27000 family.
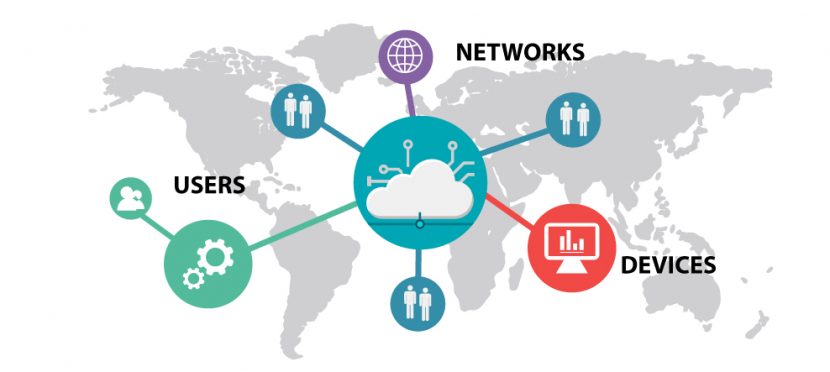
Security Covers Three Main Aspects of Your Business
1. Networks
Networks allow us to share information quickly over vast distances. This also makes them a risk. A breached network can do untold amounts of damage to a company.
A data breach of personal information can cause damage to the company’s image. Data loss or destruction can also open companies to criminal liability, as they are no longer in compliance with regulations. Protecting a network is one of the hardest tasks facing security professionals.
Network security tools prevent unauthorized access to the system. Firewalls and content filtering software protects data as they only allow valid users.
2. Devices
A user’s personal device that connects to a company network can inject unknown code into the system. Similarly, clicking on the wrong email attachment can quickly spread malicious software.
Antivirus and endpoint scanning tools stop attackers from gaining access to the device. Phishing attacks and viruses have known signatures making them detectable and preventable.
Segmenting access to the network by device, user, and facility limits the spread of malicious software.
3. Users
Careless users are a significant risk for any company. They don’t know they have been compromised and don’t know they are enabling an online attack. Phishing emails are now responsible for 91% of successful cyber-attacks.
Training users to be mindful can help limit innocuous yet dangerous actions. Training can increase security if employees know the risks involved in their daily use of technology.
Compliance and Security: The Perfect Alliance
Security is something all companies need. Most will already have some form of protection when it comes to IT infrastructure. This could even mean the bare minimum of having an antivirus installed on a workstation or using the basic Windows Firewall.
Turning security tools into a compliant IT system requires more effort. Company’s need to prove their compliance with the regulatory standards when a compliance audit happens.
Creating one system, an alliance of both security and compliance, in a systematic and controlled way is the first step in reducing risk. A security team will put in place systemic controls to protect information assets. And then a compliance team can validate that they are functioning as planned. This type of alliance will ensure that security controls won’t atrophy, and all the required documentation and reports are accessible for auditing.
Getting Started on a Secure Path
Compliance that meets a specific framework builds trust in a company. Although regulations will be the driving force behind compliance, the added benefits that come with it are helpful.
A formal assessment of security procedures and systems can highlight areas of concern that need clarification and understanding. Although management should trust administrators to make critical decisions affecting a company’s infrastructure, understanding all the relevant information about security rests with management. Using compliance frameworks to find shortcomings in security is essential when looking at those decisions.
The road to compliance starts with:
- Listing the current security tools used.
- Conducting a risk assessment of the types of information processed.
- Studying the requirements related to the framework.
- Analyzing the gaps in your current controls in regards to the requirements.
- Planning the way forward to solve major deficiencies.
- Testing the efficiency of different solutions.
After applying these steps to a system, conducting regular assessments is the key to success. Compliance and security need to work hand in hand; it does not have to be security versus compliance.
They work in unison; how? Using a compliance framework, assessing security systems, correcting deficiencies, and then beginning assessments which are set on a regular schedule.
Security and Compliance: A Symbiotic Relationship
Security and compliance is a necessary component in every sector. Knowing how each relates to data security is critical.
The IT Industry relies heavily on the public’s trust, and companies that provide them with Information Services need to have stellar reputations. A failure in security can break a business.
Security and compliance are different components of a necessary and crucial system. Knowing how each relates to data protection is critical. Each relies on the other to keep data security at its peak. Compliance does not equal security on its own. There needs to be a symbiotic relationship between the two. When a company meets compliance frameworks with its internal security measures, the implementation of both will keep data safe and a company’s integrity and reputation intact.
Now that you understand the differences between security versus compliance read about the best security testing tools recommended by professionals. It’s time to take action against potential data threats and guard your cybersecurity.
Recent Posts
How to Achieve SOC 2 Compliance & Certification
SOC 2 is an audit procedure that displays your company’s commitment to providing trusted services.
All service providers should be trying to achieve SOC 2 Compliance and Certification. User Entities – i.e., companies that are using your service – want to know you’re proactively taking care of their needs.
The guide covers the factors required to achieve SOC 2 Compliance and Certification.
What is SOC 2?
SOC 2 is part of the AICPA’s Service Organization Controls standards based on the AICPA’s Trust Service Criteria. First published in 2011, it follows the same format as the SOC 1 Report. However, the AICPA’s Assurance Services Executive Committee listed a different set of criteria to be measured for SOC 2 Compliance.
The ‘SOC 2 Report on Controls at a Service Organization’ creates a baseline of information safety at a service provider. It is Proof of your organization’s compliance will come in the form of a SOC 2 Report. You can think of the User Entity’s needs as the risks they’re exposed to while they are using your service.
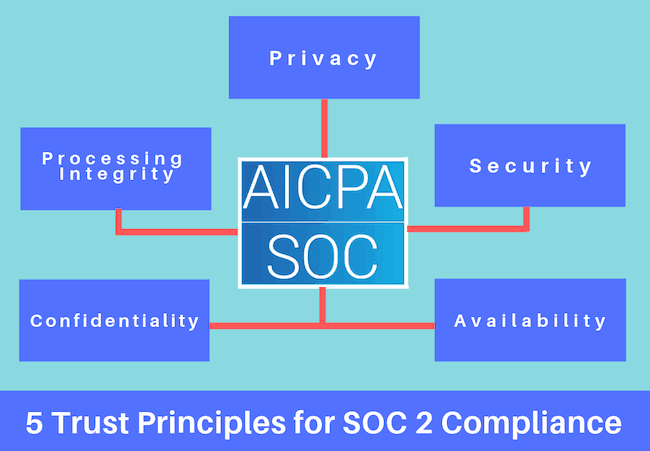
The 5 Trust Principles of SOC 2 Certification
The Trust Service Criteria are defined as principles. Each of the tenets covers an area relating to the safety and control of a user’s information. You should keep in mind that a control – such as a software module – could satisfy one or more of the required principles.
Security
The company should be able to show that their system is protected from unauthorized access. They should also prevent unauthorized disclosure and limit any damage that could influence the availability, integrity, confidentiality, and privacy of the information.
Availability
The system should have controls in place to ensure it’s available as needed by the User Entity.
Processing Integrity
Data and information processing should be checked whether they are complete, valid, accurate, timeously executed and authorized.
Confidentiality
Information that is designated as confidential should be protected according to the User Entity’s needs.
Privacy
The organization should address the User Entity’s needs when they collect, use, retain, disclose and dispose of Personal Information.
Establishing a SOC 2 Compliance Framework
The company’s risk assessment determines the framework for SOC 2 Compliance. The risks are based on the type of services provided.
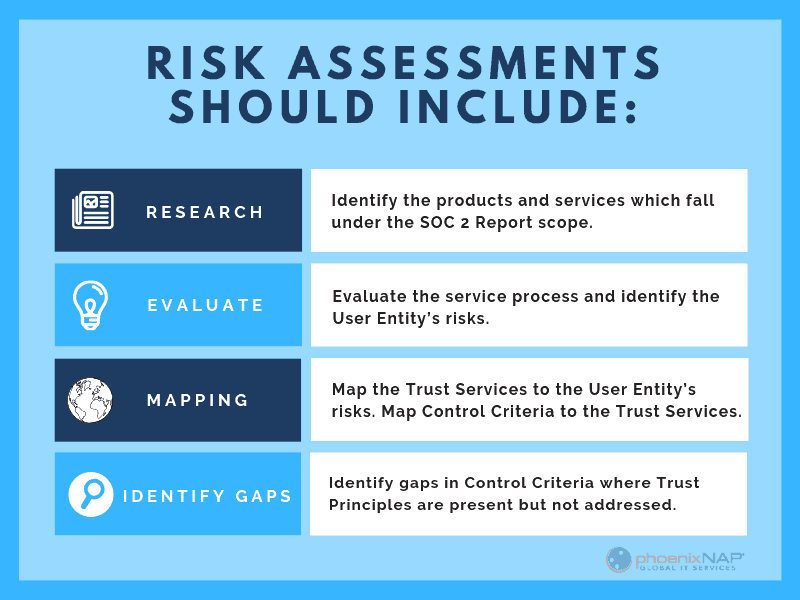
1. Identify the products and services which falls under the SOC 2 Report scope.
2. Evaluate the service process and identify the User Entity’s risks.
3. Map the Trust Services to the User Entity’s risks.
4. Map the Control Criteria to the Trust Services.
5. Identify gaps in the Control Criteria where Trust Principles are present but not addressed.
6. Map internal user controls to the gaps.
The Scope of SOC 2 Reports
Unlike strict PCI Requirements, it is not required for service providers to cover all 5 Trust Principles in a SOC 2 report. Only those that relate to their activities should be included in the scope. Care should be taken when deciding on which of the TSPs will be in the report.
For services that are outsourced, the supplier will have to show adequate controls are in place at their company’s site as part of your report.
Business Processes for the Trust Principle Assessment
The four main areas that are covered during the assessment of the company’s TSP Controls are:
Business Policies
Written policies that are relevant to the Trust Principles.
Communicating the System
The company has disclosed its policies to stakeholders and the responsible entities. This includes the users of the system.
Control Procedures
The company has procedures that will achieve the principles set out in the policies.
System Monitoring:
The company monitors the system and takes action to ensure compliance with the policies.
SOC 1 vs. SOC 2 Reports
Two types of SOC reports can be prepared. The type of report your company will need will likely depend on your User Entity’s needs. A SOC 1 Report deals with the controls at financial institutions while service-orientated companies prepare a SOC 2 Report.
Type 1 Report
The Type 1 Report records the state of the system at a point in time. This will include a description of the system, a written assertion by management, the designed controls, and the Service Auditor’s expressed opinion.
Type 2 Report
A Type 2 report further records the operating effectiveness of the system over a period of time. In addition to the items listed in Type 1, the Type 2 Report will also contain the test results of the system’s controls. It uses the 5 Trust Principles to assess the company’s risk and how they are managing exposure.
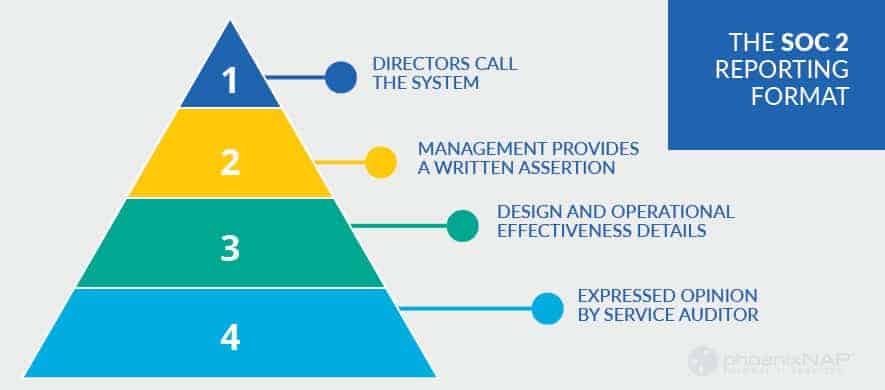
The SOC 2 Reporting Format
The Report has four main sections. Each section covers aspects of the system design, implementation, including whether it is complete and adequate.
Directors Call the System
The description of the system covers details about the services the company offers. It lists the infrastructure (such as hardware and software) that the data processing is done by. Boundaries that relate to these tasks should be recorded.
Additional items to keep in mind as part of the system description:
- Audit compliance solutions
- Risk assessment processes
- Varied system configurations at different locations
- Incident identification and response planning
The system description identifies the Trust Service Principles that should be covered. This enables you to map your Control Criteria to them and measure how effective your system is.
Management Provides a Written Assertion
This section contains the assertions made by management regarding the controls they’ve chosen to use. This is an opportunity to explain each of your methods and the controls that serve the Trust Services Criteria.
If the privacy principle forms part of the report, proof of compliance with the commitments stated in the privacy practice must be shown.
If a subservice is used for any portion of your system, this section should include:
- Details on how information is provided or received from the service provider.
- Controls at the service provider that deals with the handling, processing, maintenance, and storage of information.
Trust Principles that are excluded from the report should be listed along with the reasons why they are not covered.
Design and Operational Effectiveness Details
Section 3 of the SOC 2 Report contains a list of the controls that were designed.
If you are preparing a Type 1 Report, list the designed controls that meet the TSP criteria. For a Type 2 Report, you should include the test results for each of the designed controls. This can be in done in a table format.
To create a suitable control design, your company has to identify the risks that stand in the way of achieving your TSP. You will have to see if your control works as described and make sure there are no other risks that stop you from reaching your TSP.
Expressed Opinion by Service Auditor
The Auditor’s opinion will be based on:
- Whether the description of the system was fair.
- If the controls work as they are supposed to (for a Type 2 Report this is done over a period of time).
- If the description presents how the system was designed and built.
- It doesn’t leave out or distorts information regarding the system.
- The company complies with its privacy practices (if it was part of the scope).
As part of their opinion, the Service Auditor will list deviations and areas that lack control in the system.
Remember – SOC 2 Certification Creates Trust
When you achieve SOC 2 Compliance and Certification, it will inspire and grow trust in your organization.
User Entities may ask for a SOC 2 Report, and they will specify their TSP needs in the request. In cases like this, the report should be based on their request.
Each Trust Principle covered in the SOC 2 Compliance Report is an opportunity to earn the trust of your clients.
Recent Posts
Data Center Security: Physical and Digital Layers of Protection
Data is a commodity that requires an active data center security strategy to manage it properly. A single breach in the system will cause havoc for a company and has long-term effects.
Are your critical workloads isolated from outside cyber security threats? That’s the first guarantee you’ll want to know if your company uses (or plans to use) hosted services.
Breaches into trusted data centers tend to happen more often. The public notices when news breaks about advanced persistent threat (APT) attacks succeeding.
To stop this trend, service providers need to adopt a Zero Trust Model. From the physical structure to the networked racks, each component is designed with this in mind.
Zero Trust Architecture
The Zero Trust Model treats every transaction, movement, or iteration of data as suspicious. It’s one of the latest intrusion detection methods.
The system tracks network behavior, and data flows from a command center in real time. It checks anyone extracting data from the system and alerts staff or revokes rights from accounts an anomaly is detected.
Security Layers and Redundancies of Data Centers
Keeping your data safe requires security controls, and system checks built layer by layer into the structure of a data center. From the physical building itself, the software systems, and the personnel involved in daily tasks.
You can separate the layers into a physical or digital.
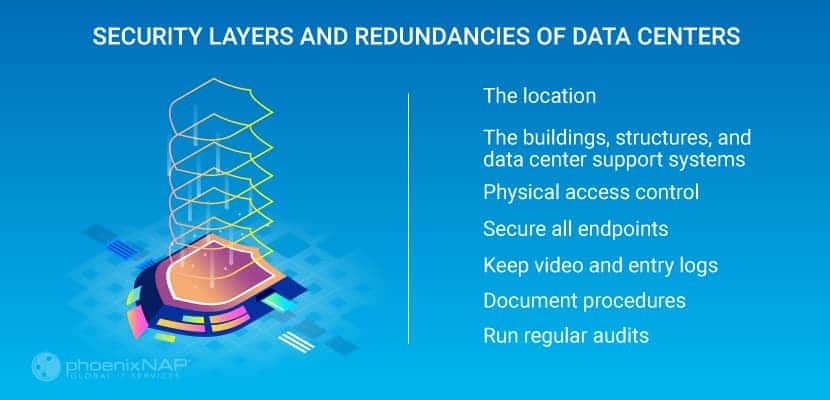
Data Center Physical Security Standards
Location
Assessing whether a data center is secure starts with the location.
A trusted Data Center’s design will take into account:
- Geological activity in the region
- High-risk industries in the area
- Any risk of flooding
- Other risks of force majeure
You can prevent some of the risks listed above by having barriers or extra redundancies in the physical design. Due to the harmful effects, these events would have on the operations of the data center; it’s best to avoid them altogether.
The Buildings, Structures, and Data Center Support Systems
The design of the structures that make up the data center needs to reduce any access control risks. The fencing around the perimeter, the thickness, and material of the building’s walls, and the number of entrances it has. All these affect the security of the data center.
Some key factors will also include:
- Server cabinets fitted with a lock.
- Buildings need more than one supplier for both telecom services and electricity.
- Extra power backup systems like UPS and generators are critical infrastructure.
- The use of mantraps. This involves having an airlock between two separate doors, with authentication required for both doors
- Take into account future expansion within the same boundary
- Separate support systems from the white spaces allow authorized staff members to perform their tasks. It also stops maintenance and service technicians from gaining unsupervised entry.
Physical Access Control
Controlling the movement of visitors and staff around the data center is crucial. If you have biometric scanners on all doors – and log who had access to what and when – it’ll help to investigate any potential breach in the future.
Fire escapes and evacuation routes should only allow people to exit the building. There should not be any outdoor handles, preventing re-entry. Opening any safety door should sound an alarm.
All vehicle entry points should use reinforced bollards to guard against vehicular attacks.
Secure All Endpoints
Any device, be it a server, tablet, smartphone or a laptop connected to a data center network is an endpoint.
Data centers give out rack and cage space to clients whose security standards may be dubious. If the customer doesn’t secure the server correctly, the entire data center might be at risk. Attackers are going to try to take advantage of unsecured devices connected to the internet.
For example, most customers want remote access to the power distribution unit (PDU), so they could remotely reboot their servers. Security is a significant concern in such use cases. It is up to facility providers to be aware of and secure all devices connected to the internet.
Maintain Video and Entry Logs
All logs, including video surveillance footage and entry logs, should be kept on file for a minimum of three months. Some breaches are identified when it is already too late, but records help identify vulnerable systems and entry points.
Document Security Procedures
Having strict, well-defined and documented procedures is of paramount importance. Something as simple as a regular delivery needs to well planned to its core details. Do not leave anything open for interpretation.
Run Regular Security Audits
Audits may range from daily security checkups, and physical walkthroughs to quarterly PCI and SOC audits.
Physical audits are necessary to validate that the actual conditions conform to reported data.
Digital Layers of Security in a Data Center
As well as all the physical controls, software, and networks make up the rest of the security and access models for a trusted data center.
There are layers of digital protection that aim to prevent security threats from gaining access.
Intrusion Detection and Prevention Systems
This system checks for advanced persistent threats (APT). It focuses on finding those that have succeeded in gaining access to the data center. APTs are typically sponsored attacks, and the hackers will have a specific goal in mind for the data they have collected.
Detecting this kind of attack requires real-time monitoring of the network and system activity for any unusual events.
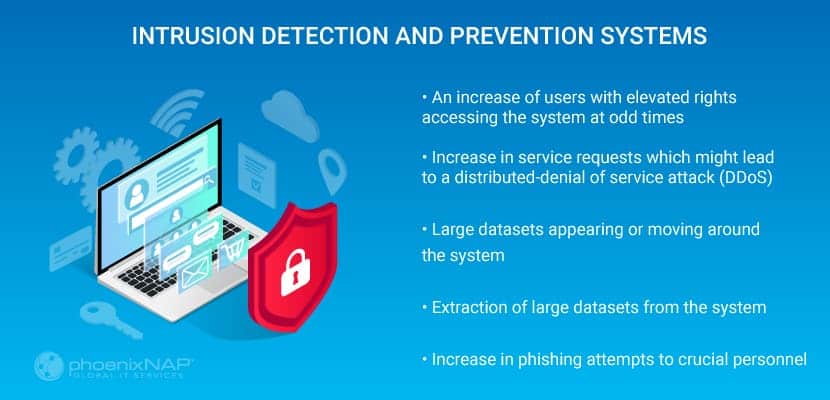
Unusual events could include:
- An increase of users with elevated rights accessing the system at odd times
- Increase in service requests which might lead to a distributed-denial of service attack (DDoS)
- Large datasets appearing or moving around the system.
- Extraction of large datasets from the system
- Increase in phishing attempts to crucial personnel
To deal with this kind of attack, intrusion detection and prevention systems (IDPS) use baselines of normal system states. Any abnormal activity gets a response. IDP now uses artificial neural networks or machine learning technologies to find these activities.
Security Best Practices for Building Management Systems
Building management systems (BMS) have grown in line with other data center technologies. They can now manage every facet of a building’s systems. That includes access control, airflow, fire alarm systems, and ambient temperature.
A modern BMS comes equipped with many connected devices. They send data or receive instructions from a decentralized control system. The devices themselves may be a risk, as well as the networks they use. Anything that has an IP address is hackable.
Secure Building Management Systems
Security professionals know that the easiest way to take a data center off the map is by attacking its building management systems.
Manufacturers may not have security in mind when designing these devices, so patches are necessary. Something as insignificant as a sprinkler system can destroy hundreds of servers if set off by a cyber-attack.
Segment the System
Segmenting the building management systems from the main network is no longer optional. What’s more, even with such precautionary measures, attackers can find a way to breach the primary data network.
During the infamous Target data breach, the building management system was on a physically separate network. However, that only slowed down the attackers as they eventually jumped from one network to another.
This leads us to another critical point – monitor lateral movement.
Lateral Movement
Lateral movement is a set of techniques attackers use to move around devices and networks and gain higher privileges. Once attackers infiltrate a system, they map all devices and apps in an attempt to identify vulnerable components.
If the threat is not detected early on, attackers may gain privileged access and, ultimately, wreak havoc. Monitoring for lateral movement limits the time data center security threats are active inside the system.
Even with these extra controls, it is still possible that unknown access points can exist within the BMS.
Secure at the Network Level
The increased use of virtualization-based infrastructure has brought about a new level of security challenges. To this end, data centers are adopting a network-level approach to security.
Network-level encryption uses cryptography at the network data transfer layer, which is in charge of connectivity and routing between endpoints. The encryption is active during data transfer, and this type of encryption works independently from any other encryption, making it a standalone solution.
Network Segmentation
It is good practice to segment network traffic at the software level. This means classifying all traffic into different segments based on endpoint identity. Each segment is isolated from all others, thus acting as an independent subnet.
Network segmentation simplifies policy enforcement. Furthermore, it contains any potential threats in a single subnet, preventing it from attacking other devices and networks.
Virtual Firewalls
Although the data center will have a physical firewall as part of its security system, it may also have a virtual firewall for its customers. Virtual firewalls watch upstream network activity outside of the data center’s physical network. This helps in finding packet injections early without using essential firewall resources.
Virtual firewalls can be part of a hypervisor or live on their own virtualized machines in a bridged mode.
Traditional Threat Protection Solutions
Well-known threat protection solutions include:
- Virtualized private networks and encrypted communications
- Content, packet, network, spam, and virus filtering
- Traffic or NetFlow analyzers and isolators
Combining these technologies will help make sure that data is safe while remaining accessible to the owners.
Data Center Security Standards

The classification system sets standards for data center’s’ controls that ensure availability. As security can affect the uptime of the system, it forms part of their Tier Classification Standard.
There are four 4 tiers defined by the system. Each tier maps to a business need that depends on what kind of data is being stored and managed.
Tiers 1 & 2
Seen as tactical services, Tier 1 and 2 will only have some of the security features listed in this article. They are low cost and used by companies who do not want real-time access to their data and who won’t suffer financially due to a temporary system failure.
They are mainly used for offsite data storage.
Tiers 3 & 4
These tiers have higher levels of security. They have built-in redundancies that ensure uptime and access. Providing mission critical services for companies who know the cost of damage to a reputation a break in service creates.
These real-time data processing facilities provide the highest standards of security.
Take Data Center Security Seriously
More and more companies are moving their critical workloads and services to hosted servers and cloud computing infrastructure. Data centers are prime targets for bad actors.
Measuring your service providers against the best practices presented in this article is essential.
Don’t wait for the next major breach to occur before you take action to protect your data. No company wants to be the next Target or Equifax.
Want Work With a State of the Art Secure Data Center?
Contact us today!
Recent Posts
HIPAA Compliant Cloud Storage Solutions: Maintain Healthcare Compliance
Hospitals, clinics, and other health organizations have had a bumpy road towards cloud adoption over the past few years. The implied security risks of using the public cloud or working with a third-party service provider considerably delayed cloud adoption in the healthcare industry.
Even today, when 84% of healthcare organizations use cloud services, the question of choosing the right HIPAA compliant cloud provider can be a headache.
All healthcare providers whose clients’ data is stored in the U.S. are a subject to a set of regulations known as HIPAA compliance
Today, any organization that handles confidential patient data needs abide by HIPAA storage requirements.
What is HIPAA Compliance?
HIPAA standards provide protection of health data. Any vendor working with a healthcare organization or business handling health files must abide by the HIPAA privacy rules. There are also many ancillary industries that must adhere to the guidelines if they have access to medical and patient data. This is where HIPPA Compliant cloud storage plays a significant role.
In 1996, “the U.S. Department of Health and Human Services (“HHS”) issued the Privacy Rule to implement the requirement of the Health Insurance Portability and Accountability Act (HIPAA) of 1996.” The Privacy Rule addresses patients’ “electronic protected health information” and how organizations, or “HIPAA covered entities” subject to the Privacy Rules must comply.
Most healthcare institutions use some form of electronic devices to provide medical care. This means that information no longer resides on a paper chart, but on a computer or in the cloud. Unlike general businesses or most commercial entities, healthcare institutions are legally obliged to employ the most reliable data backup practices.
So, how does this affect their choice of a cloud provider?
When planning their move to cloud computing, health care institutions need to ensure their vendor meets specific security criteria.
These criteria translate into requirements and thresholds that a company must meet and maintain to become HIPAA-ready. These come down to a set of certifications, SOC auditing and reporting, encryption levels, and physical security features.
HIPAA cloud storage solutions should work to make becoming compliant simple and straightforward. This way, healthcare organizations have one less thing to worry about and can focus on improving their critical processes.

HIPAA Cloud Storage and Data Backup Requirements
A cloud service provider doing business with a company operating under the HIPAA-HITECH act rules is considered a business associate. As such, it must show that it within cloud compliance standards and follows any relevant standards. Although the vendor does not directly handle patient information, it does receive, manage, and store Protected Health Information (PHI). This fact alone makes them responsible for protecting it according to HIPAA-HITECH act guidelines.
Being HIPAA compliant means implementing all of the rules and regulations that the Act proposes. Any vendor offering services that are subject to the act must provide documentation as proof of their conformity. This documentation needs to be sent not only to their clients but also to the Office for Civil Rights (OCR). The OCR is a sub-agency of the U.S. Department of Education, which promotes equal access to healthcare and human services programs.
Healthcare industry organizations looking to work with a HIPAA Compliant cloud storage provider should request proof of compliance to protect themselves. If the provider follows all standards, it should have no qualms about sharing the appropriate documentation with you.
HIPAA requirements for cloud hosting organizations are the same as the requirements for business associates. They fall into three distinct categories: administrative, physical, and technical safeguards.
- Administrative Safeguards: These types of safeguards are transparent policies that outline how the business will comply from an operational standpoint. The operations can include managing security risk assessments, appropriate procedures, disaster and emergency response, and managing passwords.
- Physical Safeguard: Physical safeguards are usually systems that are in place to protect customer data. They might include proper storage, data backup, and appropriate disposal of media at a data center. Important security precautions for facilities where hardware or software storage devices reside are also a part of this category.
- Technical Safeguards: This group of safeguards refers to technical features implemented to minimize data risk and maximize protection. Requiring unique login information, auto-logoff policies, and authentication for PHI access are just some of the technical safeguards that should be in place.

What Makes a HIPAA Certified Cloud Provider Compliant?
Providing HIPAA compliant file storage hardware or software is not as simple as flipping a switch. It takes a tremendous amount of time and effort for a company to become compliant.
The critical element to look for in a HIPAA certified cloud storage provider is its willingness to make a Business Associate Agreement. Known as a BAA, this agreement is completed between two parties planning to transmit, process, or receive PHI. Its primary purpose is to protect both parties from any legal repercussions resulting in the misuse of protected health information.
A Business Associate Agreement BAA must not add, subtract, or contradict the overall standards of the HIPAA. However, if both parties agree, supplementing specific terminology is acceptable. There are also some core terms that make up the groundwork for a compliant business associate agreement and must remain for the contract to be considered legally binding.
The level of encryption enabled by the cloud provider needs proper attention. The company should be encrypting files not only in transit but also at rest. Advanced Encryption Standard (AES) is the minimum level of encryption that it should use for file storage and sharing. AES is a successor to Data Encryption Standard (DES) and was developed by the National Institute of Standards and Technology (NIST) in 1997. It is an advanced encryption algorithm that offers improved defense against different security incidents.

Selecting a Compliant Cloud Storage Vendor
When choosing a HIPAA compliant provider, look for HIPAA web Hosting that meets the measures outlined in the previous section. Make sure you ask them about their data storage security practices to how secure your PHI data will be.
Does the potential vendor offer a service level agreement?
An SLA contract indicates guaranteed response times to threats, typically within a twenty-four-hour window. As a company that transmits PHI, you need to know how quickly the provider can notify you in the event of an incident. The faster you receive a breach notification, the more efficiently you can respond.
Don’t forget that the storage of electronic cloud-based medical records should be in a secure data center.
What are the security measures in place in case of an incident? How is access to the facility determined? Ask for a detailed outline of how they implement and enforce physical security. Check how they respond in the event of a data breach. Make sure you get all the relevant details before you bring your data to risk.
Your selected vendor should also have a Disaster Recovery and Continuity Plan in place.
A continuity plan will anticipate loss due to natural disasters, data breaches, and other unforeseen incidents. It will also provide the necessary processes and procedures if or when such events occur. Concerning data loss prevention best practices, it is also essential to determine how often the proposed method undergoes rigorous testing.
Healthcare Medical Records Security – How can I be Sure?
Cloud providers that take compliance seriously will ensure their certifications are current. There are several ways to check if they follow standards and relevant regulations.
One way is to audit your potential provider using an independent party. Auditing will bring any possible risks to your attention and reveal the vendor’s security tactics. Cloud storage for medical records providers must regularly audit their systems and environments for securing threats to remain compliant. The term ‘regularly’ is not defined by the act, so it is essential to request documentation and information on at least a quarterly basis. You should also ensure you have constant access to reports and documentation detailing the most recent audit.
Another way to determine whether the company is compliant is to assess the qualifications of its employees. All staff needs to be educated on the most current standards and get familiarized with specific safeguards. Only with these in place organizations can achieve compliance.
Ask your potential vendor tough questions. Anyone with access to PHI needs appropriate training on secure data transmission methods. Training needs to include the ability to securely encrypt patient information no matter where they are stored.
A HIPAA compliant company will not ask you for a backdoor to access your data or permission to bypass your access management protocols. Such vendors recognize the risk of requiring additional authentication or access points. Compromising access to authentication protocols and password requirements is a serious violation and should never happen.

Cloud Backup & Storage Frequently Asked Questions
Ask potential cloud vendors which method they use to evaluate your HIPAA compliance.
Is a HIPAA policy template available for use? Does the provider offer guidance and feedback on compliance? How are they ensuring that you are up to date and aware of security rules and regulations? Do they offer HIPAA compliant email?
Does the company have full-time employees on-premise?
Having a presence on site and available around the clock is a mechanism to ensure advanced security. An available representative makes PHI security more reliable and guarantees a quick response if needed. It also gives you peace of mind knowing that the company in charge of your data protection is thoroughly versed in the required standards.
The right provider should also be quick to adapt to the changes and inform you of anything that directly affects your PHI or your access to it.
Data deletion is a crucial component in choosing the appropriate HIPAA business associate. How long is the information kept for a period before being purged? How is data leakage prevented when servers are taken out of commission or erased? Is the data provided to you before deletion? The act offers no guidelines concerning the required length of time, but it is an agreement you and your provider must reach together.
In addition to your knowledge, determine how well your potential provider is versed in HIPAA regulations. Cloud companies often fail to follow the latest regulation changes, and you have to look for the one with consistent dedication.
Shop around. Do not be content with the first quote.
Many companies tout their HIPAA security, only to discover that they fall short of the measuring stick. Do your research, ask questions, and determine which vendor best suits your needs.
HIPAA-Compliant Cloud Storage is Critical
When it comes to protecting medical records in the cloud, phoenixNAP will support your efforts with the highest service quality, security, and dependability.
We provide a selection of data centers which offer state-of-the-art protection for your medical files. With scalable cloud solutions, a 100% uptime guarantee, and unmatched disaster recovery, you can rest assured that your infrastructure is compliant.
HIPAA certifications can be confusing, complicated, and stressful.
You need to be able to trust your cloud provider to keep your files safe. PhoenixNap Global IT Services will allow you the freedom to focus your attention on other areas of your business and ensure the protection of your entities and business associates.
Recent Posts
Understanding Data Center Compliance and Auditing Standards
One of the most important features of any data center is its security.
After all, companies are trusting their mission-critical data to be contained within the facility.
In recent years, security has grown even more critical for businesses. Whether you store your data in an in-house data center or with a third-party provider, cyber-attacks and are a real and growing threat to your operations. Do they have a plan to prevent DDoS attacks?
Every year, the number of security incidents grows, and the volume of compromised data amplifies proportionally.
In the first 6 months of 2018, 3,353,172,708 records were compromised. An increase of 72% compared to the same period of 2017. According to the Breach Level Index,
Correspondingly, data protection on all levels matters more than ever. Securing your data center or choosing a compliant provider should be the core of your security strategy.
The reality is that cyber security incidents and attacks are growing more frequent and more aggressive.
What are Data Center Security Levels?
Data center security standards help enforce data protection best practices. Understanding their scope and value is essential for choosing a service provider. It also plays a role in developing a long-term IT strategy that may involve extensive outsourcing.
This article covers critical data center standards and their histories of change. In addition to learning what these standards mean, businesses also need to keep in the loop with any operating updates that may affect them.
The true challenge is that many outside of the auditing realm may not fully understand the different classifications. They may not even know what to look for in a data center design and certification.
To help you make a more informed decision about your data center services, here is an overview of concepts you should understand.

Data Center Compliance
SSAE 18 Audit Standard & Certification
A long-time standard throughout the data center industry, SAS 70 was officially retired at the end of 2010. Soon after its discontinuation, many facilities shifted to SSAE 16.
However, it’s essential to understand that there is no certification for SSAE 16. It is a standard developed by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA).
Complicated acronyms aside, the SSAE 16 is not something a company can achieve. It is an attestation standard used to give credibility to organizational processes. As opposed to SAS 70, SSAE 16 required service providers to “provide a written assertion regarding the effectiveness of controls.” That way, SSAE 18 introduced a more effective control of a company’s processes and systems, while SAS 70 was mostly an auditing practice.
It is important to mention that SSAE 16 used to result in a Service Organization Control (SOC or security operations center) 1 report. This report is still in use and provides insights into the company’s reporting policies and processes.
After years of existence, SSAE 16 was recently replaced with a revised version. As of May 1, 2017, it can no longer be issued, and an improved SSAE 18 is used instead.
SSAE 18 builds upon the earlier version with several significant additions. Both of them refer to the risk assessment processes, which were previously a part of SOC 2 certification only.
The updates to SSAE 18 include:
- The guidance on risk assessment. This part helps enforce organizations to assess and review potential technology risks regularly.
- Complementary Sub service Organization Controls. A new section in the standard aims to give more clarity to the activities of a specific third-party vendor.
With these changes, the updated standard aims to further improve data center monitoring. One of the most important precautionary measures against breaches and fraudulent actions, monitoring of critical systems and activities, is a foundation of secure organizations. That may have created a bit more work for a service provider, but it also takes their security to the next level.
Of the reports relevant to data centers, SOC 1 is the closest to the old SAS 70. The service organization (data center) defines internal controls against which audits are performed.
The key purpose of SOC 1 is to provide information about a service provider’s control structure. It is particularly crucial for SaaS and technology companies that offer some vital services to businesses. In that respect, they are more integrated into their clients’ processes than a general business partner or collaborator would be.
SOC 1 also applies anytime customers’ financial applications or underlying infrastructure are involved. Cloud would qualify for this type of report. However, SOC 1 does not apply to colocation providers that are not performing managed services.
SOC 2 is exclusively for service organizations whose controls are not relevant to customers’ financial applications or reporting requirements. Colocation data center facilities providing power and environmental controls would qualify here. However, unlike a SOC 1, the controls are provided (or prescribed) by the AICPA (Trust Services Principles) and audited against.
Becoming SOC 2 complaint is a more rigorous process. It requires service providers to report on all the details regarding their internal access and authorization control practices, as well as monitoring and notification processes.
SOC 3 requires an audit similar to SOC 2 (prescribed controls). However, it includes no report or testing tables. Any consumer-type organization might choose to go this route so they could post a SOC logo on their websites, etc.

Additional Compliance Standards
HIPAA and PCI DSS are two critical notions to understand when evaluating data center security.
HIPAA
HIPAA (Health Insurance Portability and Accountability Act) regulates data, Cloud storage security, and management best practices in the healthcare industry. Given the sensitive nature of healthcare data, any institution that handles them must follow strict security practices.
HIPAA compliance also touches data center providers. In fact, it applies to any organization that works with a healthcare provider and has access to medical data. HIPAA considers all such organizations Business Associate healthcare providers.
If you or your customers have access to healthcare data, you need to check if you are using a HIPAA Compliant Hosting Provider. This compliance guarantees that it can deliver the necessary levels of data safety. Also, it can provide the documentation you may need to submit to prove compliance.
PCI-DSS Payment Card Industry Data Security Standard
As for PCI DSS (Payment Card Industry Data Security Standard), it is a standard related to all types of e-commerce businesses. Any website or company that accepts online transactions must be PCI DSS verified. We have created a PCI compliance checklist to assist.
PCI DSS was developed by the PCI SSC (Payment Card Industry Security Standards Council), whose members included credit card companies such as Visa, Mastercard, American Express, etc. The key idea behind their collaborative effort to develop this standard was to help improve the safety of customers’ financial information.
PCI DSS 3.2 was recently updated. It involves a series of updates to address mobile payments. By following the pace of change in the industry, PCI remains a relevant standard for all e-commerce businesses.

Concluding Thoughts: Data Center Auditing & Compliance
Data center security auditing standards continue to evolve.
The continuous reviews and updates help them remain relevant and offer valuable insight into a company’s commitment to security. It is true that these standards generate a few questions from time to time and cannot provide a 100% guarantee on information safety.
However, they still help assess a vendor’s credibility. A managed security service provider that makes an effort to comply with government regulations is more likely to offer quality data protection. This is particularly important for SaaS and IaaS providers. Their platforms and services become vital parts of their clients’ operations and must provide advanced security.
When choosing your data center provider, understanding these standards can help you make a smarter choice. If you are unsure which one applies to the data center, you can always ask.
Check if their standards match what the AICPA and other organizations set out. That will give you peace of mind about your choice and your data safety.
Recent Posts
11 Steps To Defend Against the Top Cybersecurity Threats in Healthcare
Imagine your patient data being held hostage by hackers. Security threats in healthcare are a genuine concern.
The U.K.’s healthcare industry recently suffered one of the largest cyber breaches ever.
WannaCry, a fast-moving global ransomware attack shut the NHS systems down for several hours. Healthcare institutions all over the country were unable to access patient records or schedule procedures. Appointments were postponed, and operations got canceled while experts worked to resolve the issue.
Although the attack impacted other companies and industries as well, the poorly defended healthcare system took a more significant hit. It was just one of the incidents that showed the extent to which healthcare institutions are vulnerable to cyber threats. Learn how to be prepared against the latest cybersecurity threats in healthcare.

11 Tips To Prevent Cyber Attacks & Security Breaches in Healthcare
1. Consider threat entry points
An entry point is a generic term for a vulnerability in your system that can be easily penetrated by hackers. By exploiting this vulnerability, hackers can deploy a virus to slow your network, access critical health information, or remove defenses to make your system more accessible in the future.
Malware can be introduced from any vulnerable spot in your network or operating system.
An employee can unknowingly click a file, download unauthorized software, or load a contaminated thumb drive. Also, when strong secure passwords are not used, an easy entry point for hackers is created.
Moreover, medical software and web applications used for storing patient data were found to contain numerous vulnerabilities. Healthcare cybersecurity statistics by Kaspersky Security Bulletin found open access to about 1500 devices that healthcare professionals use to process patient images.
2. Learn about ransomware attacks
A ransomware attack is a specific type of malware which threatens to lock one computer or an entire network unless a certain amount of money is paid.
The ransom is not necessarily an impossibly high figure either. Even demanding a few hundred dollars from a business could still be easy money for a hacker, and more manageable for individuals or companies to come up with to get their computers back.
3. Create a ransomware policy
One disabled computer does not necessarily bring much damage. However, the risk of not being able to access larger sectors where electronic records reside could be disruptive, even dangerous to patient treatment.
When such an incident happens, employees must immediately contact someone on their healthcare IT team. This should be part of their security training and overall security awareness. They must follow healthcare organization procedures when they see a ransomware message, instead of trying to resolve the matter themselves.
Authorities warn against paying ransomware culprits since there’s no guarantee a key will be given. Criminals may also re-target companies that paid them in the past.
Many companies solve ransomware attacks by calling the police and then wiping the affected computer and restoring it to a previous state.
Cloud data backups can make it easy to restore systems in the events of an attack. Disaster recovery planning should be done before a cyber security threat occurs.

Employee Roles in Security in Healthcare
4. Focus on Employee Security training
Cybersecurity professionals employ robust firewalls and other defenses, but the human factor remains a weak link as was displayed in the WannaCry exploit.
To minimize human error, system admins need to remind all staff about risky behavior continually. This can include anything from downloading unauthorized software and creating weak passwords to visiting malicious websites or using infected devices.
Educate employees on how to recognize legitimate and suspicious emails, threats, and sites so they can avoid phishing attacks. (Unusual colors in logos or different vocabulary are both warning signs). Training should be refreshed regularly or customized for different employee groups.
5. Create or expand security Measure risk levels
Different employee groups should be provided with varying privileges of network access.
At a hospital, nurses may need to share info with other staff in their unit, but there’s no reason for other departments to see this. Visiting doctors may receive access to only their patient’s info. Security settings should monitor for unauthorized access or access attempts at every level.
Chris Leffel from Digital Guardian suggests training/education first, followed by restricting specific apps, areas and patient healthcare data. He also recommends requiring multi-factor authentication, which is an additional layer of protection.
6. Healthcare Industry Cybersecurity Should Go beyond employee access
Patient concerns about sensitive data security and IT in healthcare should be kept in mind when creating safer, stronger systems, or improving cybersecurity frameworks after a hospital was hacked.
Patients are often already nervous and don’t want to worry about data security. Likewise, system administrators should also make sure that threat intelligence funding remains a priority, which means continuing to invest in security initiatives.
Publicizing you have taken extra steps in your patient security efforts will drive more security-conscious patients your way. Patients care.

7. Protect Health Data on ‘smart’ equipment
Desktops, laptops, mobile phones, and all medical devices, especially those connected to networks, should be monitored and have anti-virus protection, firewalls, or related defenses.
Today’s medical centers also possess other connected electronic equipment such as medical devices like IV pumps or insulin monitors that remotely sync patient information directly to a doctor’s tablet or a nurse’s station. Many of these interconnected devices could potentially be hacked, disrupted, or disabled, which could dramatically impact patient care.
8. Consider cloud migration For Your Data
The cloud offers a secure and flexible solution for healthcare data storage and backup. It also provides a possibility to scale resources on-demand, which can bring significant improvements in the way healthcare organizations manage their data.
Cloud-based backup and disaster recovery solutions ensure that patient records remain available even in case of a breach or downtime. Combined with the option to control access to data, these solutions can provide the needed level of security.
With the cloud, a healthcare organization does not have to invest a lot in critical infrastructure for data storage. HIPAA Compliant Cloud Storage allows for significant IT cost cuts, as no hardware investments are needed. It also brings about a new level of flexibility as an institution’s data storage needs change.
9. Ensure vendors Are Compliant
The Healthcare Industry Cybersecurity Task Force, established by the U.S. Department of Health and Human Services and Department of Homeland Security, warned providers of areas of vulnerability in the supply chain. One of their requirements is for vendors to take proper steps to monitor and detect threats, as well as to limit access to their systems.
Insurance companies, infrastructure providers, and any other healthcare business partners must have spotless security records to be able to protect medical information. This is especially important for organizations that outsource IT personnel from third-party vendors.
10. How HIPAA Compliance can help
Larger healthcare organizations have at least one person dedicated to ensuring HIPAA compliance. Their primary role is creating and enforcing security protocols, as well as developing a comprehensive privacy policy that follows HIPAA recommendations.
Educating employees on HIPAA regulations can contribute to creating a security culture. It also helps to assemble specific HIPAA teams, which can also share suggestions on how to restrict healthcare data or further cyber defenses in the organization.
HIPAA compliance is an essential standard to follow when handling healthcare data or working with healthcare institutions. Its impact on the overall improvement of medical data safety is significant, and this is why everyone in healthcare should be aware of it.
11. Push a top-down Security Program
Every medical facility likely has a security staff and an IT team, but they rarely overlap. Adding healthcare cybersecurity duties at a managerial level, even as an executive position, can bring multiple benefits.
It can make sure correct initiatives are created, launched, and enforced, as well as that funding for security initiatives is available. With cybersecurity threats, being proactive is the key to ensuring safety long term. Regular risk assessments should be part of any healthcare provider’s threat management program.
Healthcare: $3.62 Million Per Breach
Cybersecurity in the healthcare industry is under attack. Cybersecurity threats keep hospital IT teams up at night, especially since attacks on medical providers are expected to increase in 2018.
The latest trends in cybersecurity might be related to the fact that healthcare institutions are moving towards easier sharing of electronic records. That and a potentially nice payoff for patient information or financial records make healthcare a hot target for hackers.
For medical centers themselves, hacks can be costly. The average data breach costs a company $3.62 Million. This includes stolen funds, days spent investigating and repairing, as well as paying any fines or ransoms. Attacks can also result in a loss of records and patient information, let alone long-lasting damage to the institution’s reputation.
As much as hospitals and medical centers try to protect patient privacy, security vulnerabilities come from all sides. A great way to keep up with the latest security threats is to attend a data security conference.
Healthcare organizations want to send patient info to colleagues for quick consultations. Technicians pull and store sensitive data easily from electronic equipment. Patients email or text their doctor directly without going through receptionists, while admins often send a patient record to insurance companies or pharmacies.
So the industry finds itself in a dangerous position of trying to use more digital tools to improve the patient experience while following a legal requirement to safeguard privacy. No wonder IT teams continuously wonder which hospital will be hacked next.
The truth is that healthcare institutions are under a significant threat. Those looking to improve security should start with the steps outlined below.
In Closing, The Healthcare Industry Will Continue to Be Vulnerable
Healthcare facilities are often poorly equipped to defend their network activities and medical records security. However, being proactive and aware of ever-changing cybersecurity risks can help change the setting for the better.
Of course, education alone won’t help much without battle-ready infrastructure. With the assistance of healthcare industry cybersecurity experts like phoenixNAP, your healthcare organization can ensure security on multiple levels.
From backup and disaster recovery solutions to assistance creating or expanding a secure presence, our service portfolio is built for maximum security.
Do not let a disaster like WannaCry happen to your company. Start building your risk management program today.
We have created a free HIPPA Compliance Checklist.
Recent Posts
What is Privileged Access Management? Why It Should Be a Security Priority
According to the latest report from Gartner, Privileged Access Management is the number one cyber security priority for CISO’s.
The question for IT professionals is how to provide secure management for accessing data.
In this article, learn what privileged access management is and how to manage security risks by implementing PAM.
What Is Privileged Access Management? A Definition
Privileged Access management enforces least privilege policies. It also empowers organizations to reduce the threat of security attacks & data breaches.
Privileged Access Management is also often referred to as “Privileged Session Management” or “Privileged Account Management.”
Privileged security provides the power to protect your data and IT systems.
PAM acts as a secure repository, or vault, that protects your data and networks. With privileged user management, users only access the data required for their work. IT teams set these parameters. It prevents users from accessing other systems and information.
For example, a business might have one or two employees with administrator access to a Microsoft Exchange Server. Setting up email security protocols is achieved through administrator access. Only those users can delete an email account or set up a new one.
A business could assign another employee unauthorized access to company financials. Another employee might have a role in installing software.
With privileged management guidelines, you reduce organizational security risks.

What is a Privileged Account?
Privileged account and access management restricts access to privileged users.
It manages administrator access while logging and monitoring all activity.
Manage and Control Access Privileges
Using an Access Manager or Dashboard within the PAM system, a user can manage and control privileges.
It is the central location to set account-level privileges. It provides a user with real-time control over system access.
An organization can manage access for each user. A user can control the information they receive.
With access control, user restrictions can be set to allow for adding, modifying, or even deleting data. In most cases, a system has it’s own level of privileged management, assigning access to users with specific access. Groups of users with similar privileges and access needs are created and assigned a particular group, often known as administrators.
Use Privileged Management To Monitor Administrator Access
PAM security gives organizations additional control over the administrators and privileged users. These are the users with access that increases the risk to the business. They don’t directly access your data and systems.
Instead, they first access the privilege manager dashboard.
The log-in information of a user with admin access is stored inside the PAM system. It is kept within a structure known as a Shared Access Password Manager (SAPM). A SAPM will isolate and protect admin account passwords. Added security protocols can then be assigned to these passwords.
Once inside, the admin user will access their credentials. The system then authenticates the users. Access is always monitored and recorded.
This is another layer of protection for the business.
Additional Protection With Privileged Session Management
Other protocols can be used to manage administrator privileges within a network. Privileged session management protects against suspicious users.
With PSMs, admin sessions are actively monitored by a superuser. A superuser can stop a session immediately if a problem occurs. If there is a concern that the system may be compromised, multiple levels of threat detection will alert for a rapid response to resolving the issue.
When an administrator has finished work, credentials are logged, and the credential system is reset within the PAM system. This provides another layer of securing your data and network ensuring sessions aren’t left open. It removes a potential vulnerability for attackers. No one can gain entry to the system without being authenticated first.
An enterprise password manager or password vault is another way to store credentials.
It provides a direct application-to-application connection. Instead of the user, the Application-to-Application Password Manager (AAPM) logs into the app. No user requires direct access to the software. Users may not even have access to a password as they often don’t need them.
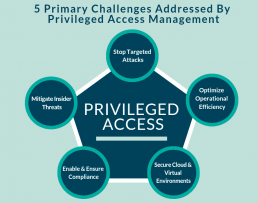
The Benefits of Privileged Access Security
Many companies are concerned about data security. Cybercrime last year cost businesses more than $600 billion.
In the past, organizations have had limited success in increasing cybersecurity. To be successful in preventing cyber attacks, a company needs to have a central strategy to protect critical systems. They need real-time network control. They need to secure access to data without creating vulnerabilities.
Privileged Account Management can help.
PAM security provides a single-management solution to many cybersecurity needs. It protects critical systems. It limits access to your data. It gives you a highly-secure solution for storing and accessing credentials. It provides security without frustrating employees.
Businesses use PAM to reduce the risk of a data breach. It increases security, and limits access to core systems.
Companies see other benefits:
- Streamlined Access: Manage and control access to the network. Don’t use a piecemeal solution that leaves holes in your security. Stop adding IT workarounds when something doesn’t work. Create access protocols. You can then enforce the protocols with the same solution. PAM Solutions allows for the management of your entire network with a single platform.
- Real-time Monitoring and Control: Grant access to data and systems when and where they are needed. Remove access just as quickly when the need is required. It’s easy to add and remove privileges and users, but it is much more difficult once a threat is detected. Monitor activity in real-time. Quickly remove access at first sight of suspicious activity. Take control of critical systems.
- Create an Access Record: As you monitor accounts, you create an audit trail of activity. You can review how and when users accessed the system. Review the audit logs for problems. Don’t be the last to know when issues happen. Stay ahead of the game.
Many highly-regulated industries that deal with sensitive data rely on PAM. Financial records or protected customer information can better be secured using privileged accounts. Patient records and health information are protected by access management. Many healthcare providers use PAM as part of their HIPPA Compliance plan.
Reduce Risk with Privileged Account Best Practices
Privileged credentials limit access and also monitor your systems and network. The system creates a record of each privileged user and provides a history of administrator activity. You know who and when data was accessed.
This allows you to monitor suspicious activity. You’ll know when there is a potential cyber security threat.
Don’t think of PAM as a punishment for employees; it keeps employees and your data safe.
It also helps prevent misuse of administrative access. By limiting user privileges, there are fewer avenues for criminals. Exploiting user access to a system has led to many of the worst cybersecurity data breaches over the last year.
Limiting privileges reduces the risk an attacker will steal admin credentials. With credentials, the attacker can change security protocols. They can take data, install viruses, and even hide, so you don’t know they attacked. PAM security helps prevent these attacks.
The Differences Between PAM Systems and Privileged Identity Management
Privileged Account Management and Privileged Identity Management (PIM) are similar. There are also significant differences between them.
PAM manages privileged user access. It allows exclusive access to core data and systems. The PAM will block and isolate users in the network. They can only access the areas they have the privilege to use.
PIM, or Identity management (IdM), focuses on authorized users. PIM creates an identity for a user in the system. Users authenticate the identity before access is granted. Think of it as the door into your network. It opens the network but provides limited control over privileges inside. Most of the control is on authenticating the identity.
Within that identity, you can set privileges. You can limit access during the creation of the identity. This is the connection between PAM and PIM. The focus of PIM is opening the systems, and not restricting them. It doesn’t monitor access; it adds more protection by creating layers of security for core systems and data. The focus is on protection and reducing risk, especially for critical root access.
Take Privileged Account Management to the Next Level
The first step in your security process is at the very least started: understanding your organization needs a process.
As a beginning stage, start by reviewing how you currently manage user access. Many companies are surprised to find many users have unlimited levels of access.
With an open network, users can access unnecessary data or have system privileges outside the scope of their job needs.
Begin tracking administrator access with a privilege management program. You may find habits and behaviors are also increasing risk.
Start to focus on what employees require on a permission scale and establish a hierarchy system for monitoring and access. This system will be particularly relevant as your organization grows. The larger your company becomes, the more privileges users you will have. Some companies have 2-3x as many privileged users as employees due to factors such as remote contractors, automated users, etc.
Next, reach out to data security experts. Have them review your current practices. The expertise and experience they bring to project are critical. This insight can provide additional server security without sacrificing efficiency.
By centralizing credentials, Privileged Access Management will improve your security.
Remember that PAM is only one stage in the full-scale spectrum of security management.
Recent Posts
PCI Compliance Checklist: 12 Steps To Ensure Staying Compliant
Can your customers trust you with their secure credit card information? If not, your credibility and bottom line may take a hit.
Every company that accepts credit card payments from customers must adhere to the Payment Card Industry and Data Security Standards. Commonly abbreviated as PCI DSS, these standards protect online consumers and e-commerce service providers.
Reading the news, it is easy to understand why PCI compliance standards matter. We often hear stories of data breaches.
Large companies like Target, Uber, and Equifax have also been impacted. Smaller companies are also vulnerable.
Building trust with customers is a priority for every business. PCI Compliant Hosting should be at the top of your security checklist.
Customers who pay you with credit cards do not want to worry about identity theft. It is your job to do whatever you can to minimize their risk.
What is PCI Compliance? What does PCI mean?
Let’s talk about why PCI standards matter. There are two things that PCI standards are supposed to ensure.
- The secure storage of credit card data on site. This concern applies only to companies that store credit card data. If you do not save data, then you do not have to worry about a security breach. Secure storage should include both virtual and physical security.
- The secure transmission of credit card data across public networks. Any time data is in transition; it can be vulnerable. Passwords, PIN numbers, and other methods can keep information safe.
PCI standards protect sensitive cardholder information. They apply whether the data is at rest or in transit, protecting your customers from breaches and identity theft.

How do PCI Compliant Standards Work?
If your company accepts, stores, or transmits credit card data, you must adhere to PCI standards. However, those standards vary depending on your circumstances.
We are not going to run down all the standards. Though, we want to give you an idea of how PCI compliance works.
How do you know which level of PCI security is required? Here are some things to keep in mind:
- PCI standards were created by the major credit card companies such as Visa, MasterCard, JCB International, and American Express. Their purpose is to protect cardholders.
- There is no such thing as PCI certification. However, you must prove that your company is PCI compliant.
- The level of compliance you must adhere to is determined by the annual volume of your credit card transactions.
- Complying with PCI standards is not cost-free. It may cost you anywhere from $1,000 to $50,000 annually.
- There are penalties if you are not compliant with PCI standards.
It is your job to determine what level of PCI compliance is needed. Then, you will need a PCI compliance checklist. Keep in mind that compliance is an ongoing issue. You will need to continually update your security to comply with PCI standards — for example, the new updated PCI-DSS 3.2 regulations.
What’s in the PCI Compliance Guide?
Lack of merchant PCI compliance can cost your company money and reputation. Having a checklist to refer to can help you complete all the necessary steps to get compliant.
You should use the PCI DSS Audit checklist to make sure you meet each requirement. Remember, the requirements may change based on your transaction volume. It is your job to monitor your transactions and choose the right level of compliance.
To make it a bit easier for you, we created a short guide to PCI self-assessment. It is essential to be thorough as you work your way through this checklist. Keep track to ensure that you have not missed any vital steps.

1. Install and Maintain a Firewall
To meet PCI standards, install a reliable firewall to shield your network security. The firewall is your first line of defense to protect cardholder data, as it helps block unauthorized access to your network.
To enhance its efficiency, you should have a clear firewall configuration policy. Run regular tests on your firewall and ensure that your hosting service has one in place.
2. Do Not Use Vendor-Supplied Defaults
Keeping track of passwords can be a hassle. Some companies cut corners by using vendor defaults. Compliance with PCI standards means assigning unique passwords.
Every password you use should adhere to password best practices. Including lower-case and capital letters, numbers, and symbols makes passwords secure. Using defaults makes it easy for would-be hackers to get into your system.
3. Protect Stored Cardholder Data
Protecting cardholder data by PCI standards requires you to think about your system’s vulnerabilities. You will need to put electronic and physical barriers in place.
Your first loyalty should be to the customers who put their trust in you. Security measures may include:
- Strong password policies
- Authentication protocols
- Locked servers
- Locked storage cabinets
- Additional steps as needed
Making an inventory of existing measures can help you spot problems.
4. Encrypt Transmission of Cardholder Information
Protecting stored cardholder information is a must for complying with PCI standards, but it is equally important to protect it while it is in transit.
If you are sending customer data through an open network, you should make sure to encrypt it. This step adds a layer of protection to protect it from hackers, as they would not be able to read it without encryption keys.
PCI compliance best practices do not recommend storing sensitive data. PINS, security codes, and other verification information should be adequately secured and encrypted both at rest and in transit.
5. Use and Update Anti-Virus Software
To protect cardholder information and comply with PCI standards, you must use anti-virus software. That might seem obvious, but it is not uncommon for companies to have software that’s out of date.
Your software should be reliable and from a company with a good track record. It is your job to update the databases regularly. Train workers to update databases on all devices they use for work and make sure you also run regular scans on your server.
6. Develop and Maintain Secure Systems and Applications
Many companies use both proprietary and third-party systems and applications. To comply with PCI standards, you need to ensure that all systems and software are secure.
The use of third-party apps is sometimes beneficial, but caution is required. You must be confident that their presence on your network is not risking your data. Not all apps are safe to use, so choose wisely before installing anything new.
7. Restrict Access to Cardholder Data
As a business owner, you need to trust your employees. No boss wants to believe that their employees would be careless with customer data. That is understandable, but you must take steps to restrict access as needed.
According to PCI standards, people who do not need access to cardholder data should not have it. Most of your employees will not require access. Only those who need cardholder information should have access to it. Taking this simple step minimizes the risk of an internal data breach.

8. Assign Unique IDs to All Users
Limiting access to secure data reduces the chance of an internal breach. That does not mean that you should not track user activity and access. We recommend this as an additional security measure to adhere to PCI standards.
Assigning each user with access to your system a unique ID is essential. This simple step can help you keep track of who’s accessing your data. When each user has an ID and password, you can monitor who accesses stored data. Letting employees know that their activity is observed can add an extra layer of protection.
9. Restrict Physical Access to Cardholder Data
Preventing hackers from accessing cardholder data electronically is essential, but it is not the only step you should take. You must ensure that only authorized staff who require physical access to cardholder data have it.
This step applies both to servers and other hardware as well as paper records. If you keep any printed records of cardholder information, store them in a secure area. Access to the area should be limited. These areas must not be left unlocked or unguarded.
10. Track and Monitor All Access to Cardholder Data
You want to trust your employees, but you cannot afford to assume the best. Protecting customer data must be your top priority.
If you want to protect cardholder information, it is essential to have a tracking and monitoring system in place. That way, you can see which employees have accessed secure data, as required by PCI standards.
Employees may bristle at the notion of being monitored. That is understandable, but it does not change your obligation to customers. Put a monitoring system in place and then review it periodically. Any unusual or unexpected activity by employees should be addressed immediately.
11. Test Security Systems and Processes
Installing security systems, firewalls, antivirus software, and internal security is essential. These steps are vital to keeping your customers’ data safe, but so is ongoing testing of your existing systems.
Think of these tests as fire drills. We make a point of testing fire alarms and evacuation methods in schools and offices. Likewise, you should test your security systems regularly to ensure they work.
If a test reveals a breach or vulnerability, you must address it immediately. Even the best security measures can fail, so do not make the mistake of assuming that yours are infallible.
12. Write and Enforce a Security Policy
The final step on our PCI DSS checklist is to write and implement a comprehensive security policy. Even with protections in place, you must communicate and work to enforce your policy. Ever employee, third-party vendor, and a customer should know about it.
Letting people know about your policy does several things at once.
- It lets customers know that you take their privacy seriously and want to protect their data.
- It ensures that all personnel understands the importance of safeguarding cardholder data.
- It puts your staff on notice that you will be monitoring their access to secure information.
Your written security policy should include an overview of how you protect customer data. It should also spell out password and access requirements for staff. Make sure to specify your guidelines for accessing data on BYOD and mobile devices. All essential personnel should be made aware of PCI standards and how to comply with them.

Always Verify PCI Compliance
Maintaining an atmosphere of trust with your customers is essential. In fact, a lack of confidence can affect the overall well-being of your business.
Complying with PCI standards is key to inspiring trust in your customers, prospects, and business partners. The items on the PCI compliance checklist should be used in conjunction with the recommended security best practices to maximize your data protection strategies.
At phoenixNAP, we know the importance of security and trust. We offer products to help you build a PCI DSS compliant platform for your company and protect your confidential data.
Recent Posts
HITRUST Certification vs HIPAA: What are the Differences?
There is more to worry about than just HIPAA Compliance in order to secure media data. That’s where HITRUST comes in.
What is HITRUST Compliance?
How is it different from HIPAA?
How can healthcare organizations leverage this framework?
What is HITRUST?
HITRUST or the Health Information Trust Alliance, in and of itself is not just a framework that allows healthcare providers to meet HIPAA security laws. HITRUST goes far beyond that. They are the entity that created and continues to maintain the CSF, or Common Security Framework. The CSF is a certifiable framework that brings together other compliance frameworks, such as HIPAA, NIST, PSI, and ISO.
Many entities in the healthcare industry think of health information security rules as a burden to deal with before they can do their jobs. HITRUST was made to be the core pillar of the union of different health information systems and exchanges. Today’s technology makes risk management and data protection key for healthcare organizations of all kinds, and HITRUST helps covered entities meet information security regulations easier than ever before.
The HITRUST website describes “a not-for-profit organization whose mission is to champion programs that safeguard sensitive information and manage information risk for organizations across all industries and throughout the third-party supply chain. In collaboration with privacy, information security and risk management leaders from both the public and private sectors, HITRUST develops, maintains and provides broad access to its widely adopted common risk and compliance management and de-identification frameworks; related assessment and assurance methodologies; and initiatives advancing cyber sharing, analysis, and resilience.”

What is HITRUST Compliance Certification?
Part of what makes HITRUST different is the fact that it is certifiable. A health care facility can’t be certified in HIPAA compliance or in how well they follow Federal Trade Commission laws. In the past, healthcare practices just signed agreements that they were, in fact, HIPAA compliant. They signed forms that said they had taken the right measures to put security controls in place.
This could never be confirmed or judged by anyone, making it more of an “I promise” sort of situation. Some medical practices took the first step to conduct a HITRUST readiness assessment or hire a HITRUST CSF assessor. This was to make sure that the practice was properly following the HIPAA security rule and other laws set forth. This was the most any practice could do to “prove” they were HIPAA compliant.
A medical practice can become HITRUST certified.
How to become HITRUST Certified?
As said above, HITRUST compliance requirements include HIPAA, FTC, and many other data security regulations.
HITRUST has the option to allow healthcare practices to do their own self-assessment.
It is highly recommended that medical practices first perform a self-audit.
The HITRUST self assessment tool is also an excellent resource for practices to use on a frequent basis.
Any gaps in regulatory compliance can be addressed and lessened before the final CSF assessment is done. They can make any needed changes before the assessor comes to do the validated assessment.
Or, they can have a CSF assessor perform a validated assessment.
The CSF framework and HITRUST assessment and certification have 19 different domains:
- Healthcare Data Protection & Privacy
- Information Protection
- Wireless Protection
- Transmission Protection
- Network Protection
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Third Party Security
- Physical & Environmental Security
- Configuration Management
- Vulnerability Management
- Password Management
- Incident Management
- Risk Management
- Access Control
- Audit Logging & Monitoring
- Education, Training & Awareness
- Business Continuity Management & Disaster Recovery
Many HITUST CSF certification requirements must be met to become certified. These are clearly outlined and can be easily understood and put into practice. HITRUST certifications are good for two years. Then, a healthcare practice will need to go through the assessment, validation, and certification process again.
This may seem like a burden. But with technology and security regulations changing so quickly, certifications require updates
Once a new technology is introduced, or new compliance laws are passed, the certification becomes out of date. When healthcare practices work with HITRUST, they can be sure that every two years the most up-to-date security technology is employed.

HITRUST vs HIPAA Requirements for Certification, The Differences
HIPAA is a law that protects patient medical records. It gives patients some privacy when it comes to who can gain access to the information stored in their file.
Whether or not a health care provider is HIPAA compliant or not is subjective without a certification process. Without being certified, any healthcare practice can say they are HIPAA compliant without following some or all of the laws that HIPAA has set forth.
With growing technology in the healthcare sectors, security compliance can seem strict and at times, unnecessary. Maintaining compliance and IT risk management has been a struggle for many healthcare practices. Costs have increased across the board as practices have had to hire and train more staff to meet the burden of staying compliant with the latest laws in healthcare privacy.
Medical practices in every field have shown a need to simplify how they meet healthcare privacy requirements. Compare HIPAA to HITRUST and learn the differences between the two. Learn how healthcare organizations can use HITRUST to make risk assessment and health care security compliance easy to maintain.
HITRUST
HITRUST is the entity that created and maintains control frameworks that include many different compliance regulations. HITRUST brings together and unifies the various aspects of regulatory compliance. This makes it easy for medical practices to adopt compliant practices and make sure they are using the right security controls to protect sensitive information and patient data.
HIPAA
HIPAA, or the Health Insurance Portability and Accountability Act, are a set of standards and regulations that are meant to protect sensitive information in the healthcare industry. HIPAA compliance involves protecting health information and making sure that only those medical professionals, vendors, and other need-to-know people have access to patient health information.

HITRUST and HIPAA are not interchangeable
HITRUST includes but is not limited to HIPAA. HIPAA is a vital part of data protection and is the baseline for patient information security. However, it does not offer anything beyond guidelines to follow. It doesn’t allow medical practices to engage with complete protection that takes into account the increased threats. These healthcare cybersecurity threats change as technology grows, making it harder to keep up without help.
HITRUST is the organization that formed and updates a comprehensive security platform, or Common Security Framework (CSF). It includes much more than HIPAA regulations. For example, HIPAA includes physical, technical, and administrative safeguards. They outline the policies, procedures, and requirements for organization and documentation that healthcare practices must adhere to.
HITRUST, on the other hand, includes all of the HIPAA safeguards, as well as security guidelines and risk management framework from:
- Control Objectives for Information and Related Technology (COBIT)
- International Organization for Standardization (ISO)
- Federal Trade Commission (FTC)
- Centers for Medicare and Medicaid Services
- National Institute of Standards and Technology (NIST)
- Payment Card Industry Data Security Standard (PCI DSS)
- Other federal and state entities
HITRUST is the framework that allows medical practices to make sure they have all their bases covered. The framework is meant to balance the standards from the different regulatory entities to help healthcare practices simplify.
With HITRUST certification, healthcare facilities can expand their data and patient security coverage.
Planning for Healthcare Security Threats
Data breaches in the healthcare industry can be costly and negatively impact a healthcare practice in many ways.
Sadly, these data breaches are on the rise and are showing no signs of stopping or slowing down. It’s more important than ever to be aware of the risks of technology in a healthcare practice and to adopt controls that minimize those risks. While HIPAA compliance was the first widely adopted set of compliance laws to help keep patient data private and to stop data breaches, it is simply just one piece of an enormous puzzle.
Contrary to popular belief, many entities want to get their hands on private patient data. It may not be relevant to some of them that Joe Smith had a kidney transplant last year. Or, that he was allergic to a particular type of medicine. Remember though that patient data includes much more than just health history.
It includes patient names, addresses, social security numbers, health insurance information, and more. This data can be used to commit different kinds of fraud. With the lack of healthcare available to low income and middle-class people, health insurance fraud is on the rise. Identity theft is also an issue when it comes to patient records. This is because nearly all of an individual’s identifying information is contained within their medical chart.
People who want to get their hands on private patient data don’t have to physically break into a medical office and steal file folders. Technology makes it easy for advanced hackers to get to this information remotely if the right security controls are not in place. Unsecured or unencrypted email can be infiltrated, or hackers can download a wealth of patient data through unprotected cloud services.
Without good cybersecurity framework, a health care facility’s sensitive data is a playground for smart hackers. It’s critical for healthcare practices of all kinds to plan for threats to security. They need to work to adopt controls that keep sensitive information out of any hands it does not belong in.
Next Steps: Protecting Patient Data & Achieving HITRUST Certification
Carefully consider the benefits of becoming HITRUST CSF certified. HITRUST certified medical practices can enjoy the peace of mind that comes with having efficient data security processes and reducing the threat of data breaches.
This certification isn’t one of the business requirements for opening or operating a health care facility of any kind. However, it’s the simplest and most complete way to ensure that your facility is on par with the latest security and regulatory compliance laws.
Get rid of confusion over compliance. Have peace of mind that your practice is protected by a universal cybersecurity framework that accounts for all current industry regulations. Becoming HITRUST certified can also help build the trust between your practice and your patients. Your patients will know their private data and health information is safe.
Recent Posts
HIPAA Compliance Checklist: How Do I Become Compliant?
For healthcare providers, HIPAA compliance is a must. HIPAA guidelines protect patients’ health information, ensuring that it is stored securely, and used correctly.
Sensitive data that can reveal a patient’s identity must be kept confidential to adhere to HIPAA rules. These rules work on multiple levels and require a specific organizational method to implement comprehensive privacy and security policies to achieve compliance.
Most organizations find this to be a daunting task. We have put together a HIPAA compliance checklist to make the process easier.
The first is to understand how HIPAA applies to your organization. The second is to learn how to implement an active process, technology, and training to prevent a HIPAA-related data breach or accidental disclosure. Finally, the third is to put physical and technical safeguards in place to protect patient data.
By the time you’re done with our list, you will know what you need to consider to have a better conversation with your compliance advisors.
What is HIPAA?
Before talking about compliance, let’s recap the basics of HIPAA.
Signed into law by President Bill Clinton in 1996, the Health Insurance Portability and Accountability Act provides rules and regulations for medical data protection.
HIPAA does several important things. It reduces health care abuse and fraud and sets security standards for electronic billing of healthcare. It also does the same for the storage of patients’ healthcare information. The Act mandates the protection and handling of medical data, ensuring that healthcare data is kept private.
The part of HIPAA we are concerned with relates to healthcare cybersecurity. To be compliant, you must protect patients’ confidential records.
HIPAA rules have evolved. When the law was first enacted, it did not mention specific technology. As the HIPAA compliant cloud has become commonplace, it has inspired additional solutions. For example, our Data Security Cloud (DSC) is being developed to create a base infrastructure for a HIPAA compliant solution. Providing a secure infrastructure platform to ride on top of, DSC makes creating a HIPAA-compliant environment easier.
Secure infrastructure handles things at the lowest technical level that creates data, providing the key features to keep data safe. These features include separation/segmentation, encryption at rest, a secure facility at the SOC 2 level of compliance, and strict admin controls among other required security capabilities.

Why Is HIPAA Compliance Important?
HIPAA compliance guidelines are incredibly essential. Failure to comply can put patients’ health information at risk. Breaches can have a disastrous impact on a company’s reputation, and you could be subject to disciplinary action and strict violation fines and penalties by CMS/OCR.
Last year’s Wannacry ransomware attack affected more than 200,000 computers worldwide, including many healthcare organizations. Most notably, it affected Britain’s National Health Service, causing severe disruptions in the delivery of health services across the country.
To gain access to the systems, hackers exploited vulnerabilities in outdated versions of Windows that are still commonly used in many healthcare organizations. With medical software providers offering inadequate support for new OS’s and with medical devices such as MRIs lacking security controls, the attack was easy to carry out.
The attack demonstrated the strength of today’s hackers, highlighting the extent to which outdated technologies can pose a problem in modern organizations. This is precisely why HIPAA also regulates some aspects of technology systems used to store, manage, and transfer healthcare information.
The institutions that fail to implement adequate systems can suffer significant damage. If a breach takes place, the law requires affected organizations to submit various disclosure documents, which can include sending every subject a mailed letter. They may also be required to offer patients a year of identity protection services. This can add up to significant dollars, even before confirming the extent of the breach.

What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule creates national standards. Their goal is to protect medical records and other personally identifiable health information (PHI).
It applies to three types of companies: providers, supply chain (contractors, vendors, etc.) and now service providers (such as data centers and cloud services providers). All health plans and healthcare clearinghouses must be HIPAA compliant.
The rules also apply to healthcare providers who conduct electronic health-related transactions.
The Privacy Rule requires that providers put safeguards in place to protect their patients’ privacy. The safeguards must shield their PHI. The HIPAA Privacy Rule also sets limits on the disclosure of ePHI.
It’s because of the Privacy Rule that patients have legal rights over their health information.
These include three fundamental rights.
-
- First, the right to authorize disclosure of their health information and records.
- Second, the right to request and examine a copy of their health records at any time.
- Third, patients have the right to request corrections to their records as needed.
The HIPAA Privacy Act requires providers to protect patients’ information. It also provides patients with rights regarding their health information.

What Is The HIPAA Security Rule
The HIPAA Security Rule is a subset of the HIPAA Privacy Rule. It applies to electronic protected health information (ePHI), which should be protected if it is created, maintained, received, or used by a covered entity.
The safeguards of the HIPAA Security Rule are broken down into three main sections. These include technical, physical, and administrative safeguards.
Entities affected by HIPAA must adhere to all safeguards to be compliant.
Technical Safeguards
The technical safeguards included in the HIPAA Security Rule break down into four categories.
-
- First is access control. These controls are designed to limit access to ePHI. Only authorized persons may access confidential information.
- Second is audit control. Covered entities must use hardware, software, and procedures to record ePHI. Audit controls also ensure that they are monitoring access and activity in all systems that use ePHI.
- Third are integrity controls. Entities must have procedures in place to make sure that ePHI is not destroyed or altered improperly. These must include electronic measures to confirm compliance.
- Finally, there must be transmission security. Covered entities must protect ePHI whenever they transmit or receive it over an electronic network.
The technical safeguards require HIPAA-compliant entities to put policies and procedures in place to make sure that ePHI is secure. They apply whether the ePHI is being stored, used, or transmitted.
Physical Safeguards
Covered entities must also implement physical safeguards to protect ePHI. The physical safeguards cover the facilities where data is stored, and the devices used to access them.
Facility access must be limited to authorized personnel. Many companies already have security measures in place. If you don’t, you’ll be required to add them. Anybody who is not considered an authorized will be prohibited from entry.
Workstation and device security are also essential. Only authorized personnel should have access to and use of electronic media and workstations.
Security of electronic media must also include policies for the disposal of these items. The removal, transfer, destruction, or re-use of such devices must be processed in a way that protects ePHI.
Administrative Safeguards
The third type of required safeguard is administrative. These include five different specifics.
-
- First, there must be a security management process. The covered entity must identify all potential security risks to ePHI. It must analyze them. Then, it must implement security measures to reduce the risks to an appropriate level.
- Second, there must be security personnel in place. Covered entities must have a designated security official. The official’s job is to develop and implement HIPAA-related security policies and procedures.
- Third, covered entities must have an information access management system. The Privacy Rule limits the uses and disclosures of ePHI. Covered entities must put procedures in place that restrict access to ePHI to when it is appropriate based on the user’s role.
- Fourth, covered entities must provide workforce training and management. They must authorize and supervise any employees who work with ePHI. These employees must get training in the entity’s security policies. Likewise, the entity must sanction employees who violate these policies.
- Fifth, there must be an evaluation system in place. Covered entities must periodically assess their security policies and procedures.

Who Must Be HIPAA complaint?
There are four classes of business that must adhere to HIPAA rules. If your company fits one of them, you must take steps to comply.
The first class is health plans. These include HMOs, employer health plans, and health maintenance companies. This class contains schools who handle PHI for students and teachers. It also covers both Medicare and Medicaid.
The second class is healthcare clearinghouses. These include healthcare billing services and community, health management information systems. Also included are any entities that collect information from healthcare entities and process it into an industry-standard format.
The third class is healthcare providers. That means any individual or organization that treats patients. Examples include doctors, surgeons, dentists, podiatrists, and optometrists. It also includes lab technicians, hospitals, group practices, pharmacies, and clinics.
The final class is for business associates of the other three levels. It covers any company that handles ePHI such as contractors, and infrastructure services providers. Most companies’ HR departments also fall into this category because they handle ePHI of their employees. Additional examples include data processing firms and data transmission providers. This class also includes companies that store or shred documents. Medical equipment companies, transcription services, accountants, and auditors must also comply.
If your entity fits one of these descriptions, then you must take steps to comply with HIPAA rules.
What is the HIPAA Breach Notification Rule?
Even when security measures are in place, it’s possible that a breach may occur. If it does, the HIPAA Breach Notification Rule specifies how covered entities should deal with it.
The first thing you need to know is how to define a breach. A breach is a use or disclosure of PHI forbidden by the Privacy Rule.
The covered entity must assess the risk using these criteria:
-
- The nature of the PHI involved, including identifying information and the likelihood of re-identification;
- The identity of the unauthorized person who received or used the PHI;
- Whether the PHI was viewed or acquired; and
- The extent to which the risk to the PHI has been mitigated.
Sometimes, PHI may be acquired or disclosed without a breach.
The HIPAA rules specify three examples.
-
- The first is when PHI is unintentionally acquired by an employee or person who acted in good faith and within the scope of their authority.
- The second is inadvertent disclosure of PHI by one authorized person to another. The information must not be further disclosed or used in a way not covered by the Privacy Rule.
- The third occurs if the covered entity determines that the unauthorized person who received the disclosure would not be able to retain the PHI.
If there is a breach as defined above, the entity must disclose it. The disclosures advise individuals and HHS that the breach has occurred.
Personal disclosures must be mailed or emailed to those affected by the breach. A media disclosure must be made in some circumstances. If more than 500 people in one area are affected, the media must be notified.
Finally, there must also be a disclosure to the HHS Secretary.
The HIPAA Breach Notification Rule protects PHI by holding covered entities accountable. It also ensures that patients are notified if their personal health information has been compromised.

What Are The HIPAA Requirements for Compliance
The common question is, how to become HIPAA compliant?
The key to HIPAA compliance certification is to take a systematic approach. If your entity is covered by HIPAA rules, you must be compliant. You must also perform regular audits and updates as needed.
With that in mind, we’ve compiled a comprehensive checklist for use in creating your HIPAA compliance policy.
HIPAA Compliance Checklist
These questions cover the components to make you are HIPAA-compliant. You can use the checklist to mark each task as you accomplish it. The list is intended to be used for self-evaluation.
Have you conducted the necessary audits and assessments according to National Institutes of Standards and Technology (NIST) Guidelines?
The audits in question involve security risk assessments, privacy assessments, and administrative assessments.
Have you identified all the deficiencies and issues discovered during the three audits?
There are several things to consider before doing the self-audit checklist. You need to ensure that all security, privacy, and administrative deficiencies and issues are appropriately addressed.
Have you created thorough remediation plans to address the deficiencies you have identified?
After covering the deficiencies and issues mentioned above, you need to provide remediation for each group.
Do you have policies and procedures in place that are relevant to the HIPAA Privacy Rule, the HIPAA Security Rule, and the HIPAA Breach Notification Rule?
You must be aware of these three critical aspects of a HIPAA compliance program and ensure each is adequately addressed.
-
- Have you distributed the policies and procedures specified to all staff members?
- Have all staff members read and attested to the HIPAA policies and procedures you have put in place?
- Have you documented their attestation, so you can prove that you have distributed the rules?
- Do you have documentation for annual reviews of your HIPAA policies and procedures?
- Have all your staff members gone through basic HIPAA compliance training?
- Have all staff members completed HIPAA training for employees?
- Do you have documentation of their training?
- Have you designated a staff member as the HIPAA Compliance, Privacy, or Security Officer as required by law?
- Have you identified all business associates as defined under HIPAA rules?
- Have you identified all associates who may receive, transmit, maintain, process, or have access to ePHI?
- Do you have a Business Associate Agreement (Business Associate Contract) in place with each identify you have identified as a Business Associate?
- Have you audited your Business Associates to make sure they are compliant with HIPAA rules?
- Do you have written reports to prove your due diligence regarding your Business Associates?
- Do you have a management system in place to handle security incidents or breaches?
- Do you have systems in place to allow you to track and manage investigations of any incidents that impact the security of PHI?
- Can you demonstrate that you have investigated each incident?
- Can you provide reporting of all breaches and incidents, whether they are minor or meaningful?
- Is there a system in place so staff members may anonymously report an incident if the need arises?
- Have you distributed the policies and procedures specified to all staff members?
As you work your way through this checklist, remember to be thorough. You must be able to provide proper documentation of your audits, procedures, policies, training, and breaches.
As a final addition to our checklist, here is a review of the general instructions regarding a HIPAA compliance audit.
-
- If a document refers to an entity, it means both the covered entity and all business associates unless otherwise specified
- Management refers to the appropriate officials designated by the covered entity to implement policies, procedures, and standards under HIPAA rules.
- The covered entity must provide all specified documents to the auditor. A compendium of all entity policies is not acceptable. It is not the auditor’s job to search for the requested information.
- Any documents provided must be the versions in use as of the audit notification and document request unless otherwise specified.
- Covered entities or business associates must submit all documents via OCR’s secure online web portal in PDF, MS Word, or MS Excel.
- If the appropriate documentation of implementation is not available, the covered entity must provide examples from “equivalent previous time periods” to complete the sample. If no such documentation is available, a written statement must be provided.
- Workforce members include:
- Entity employees
- On-site contractors
- Students
- Volunteers
- Information systems include:
- Hardware
- Software
- Information
- Data
- Applications
- Communications
- People
Proper adherence to audit rules is necessary. A lack of compliance will impact your ability to do business.
In Closing, HIPAA Questions and Answers
HIPAA rules are designed to ensure that any entity that collects, maintains, or uses confidential patient information handles it appropriately. It may be time-consuming to work your way through this free HIPAA self-audit checklist. However, it is essential that you cover every single aspect of it. Your compliance is mandated by law and is also the right thing to do to ensure that patients can trust you with their personal health information.
One thing to understand is that it is an incredible challenge to try to do this by yourself. You need professional help such as a HIPAA technology consultant. Gone are the days you can have a server in your closet at the office, along with your office supplies. The cleaning personnel seeing a print out of a patient’s file constitutes a ‘disclosable’ event.
Screen servers, privacy screens, and professionally-managed technology solutions are a must. Just because you use a SAS-based MR (Medical Records) solution, does not mean you are no longer responsible for the privacy of that data. If they have lax security, it is still the providers’ responsibility to protect that data. Therefore the burden of due diligence is still on the provider.
Phoenix NAP’s HIPAA compliant hosting solutions have safeguards in place, as audited in its SOC2 certifications. We provide 100% uptime guarantees and compliance-ready platform that you can use to build secure healthcare infrastructure.
Recent Posts
HIPAA Compliance Audit: Expert Security Guide To Stay Compliant
With stories about security breaches, computer hacking, and stolen personal data making the news daily, we are all concerned about the safety and security of our medical data.
Results of the 2019 HIPAA audits were troubling, and they only appear to be getting worse.
Only 14% of the covered entities and businesses scored a 1, the highest rating, for content breach notification. Only 1% of the covered entities and enterprises scored a 1 for right-of-access. No covered entities and businesses scored a 1 for HIPAA security risk analysis.
To ensure the safety and privacy of personal medical data and protected health information, the United States government passed the Health Insurance Portability and Accountability Act of 1996. HIPAA is United States federal legislation covering the data privacy and security of medical information.
The public has a right to demand privacy for personal medical data. We trust healthcare providers with our health. It’s only fair to be able to trust them with our protected health information and medical data. HIPAA sets expectations and guidelines, also known as HIPAA compliance, for healthcare providers to protect our medical data.
The Health and Human Services Office For Civil Rights manages HIPAA. They conduct audits to ensure compliance with the covered entities and businesses that handle medical data.
Unfortunately, some businesses struggle with HIPAA compliance guidelines. Healthcare providers have been reluctant and slow to protect data or upgrade their systems. Medical data-based ransomware attacks and healthcare cybersecurity breaches are rampant. Studies show that it costs more than $250,000 and upwards of six months to become HIPAA-compliant. However, many in the healthcare industry don’t have the time or resources to manage the process correctly.
There are steps you can take to prepare for HIPAA compliance audit.
We’ll look at the compliance rules and HIPAA auditing protocols. Then, go over the steps you can take to meet the demands of an audit and ensure compliance with HIPAA regulations.
Also, we prepared a complete checklist for HIPAA Compliance.

What is a HIPAA audit?
The OCR works closely with health care providers, covered entities and businesses to ensure compliance with HIPAA regulations the HIPAA privacy and security. HIPAA audits are conducted to track progress on compliance and to identify areas where improvement is needed.
To avoid expensive Hipaa violations and fines, secure protected health information. Providers should conduct a risk assessment and take steps to prepare for HIPAA compliance audits.
What Is HIPAA Title II?
While there are five separate sections covered in HIPAA, Title II is the section focused on protecting individual medical information.
Achieving compliance with HIPAA requires meeting the guidelines in Title II. The privacy rule in Title II focuses on Protected Health Information (PHI). It provides laws and standards that protect personal health information, detailing the covered entities and businesses required to abide by HIPPA.
The security rule, the other piece of HIPAA Title II, focuses on the safeguards and protection that must be implemented to safeguard PHI, especially regarding electronically protected health information (also called ePHI). This includes administrative, physical, and technical safeguards as well as organizational requirements and documentation standards. Data security plans and information technology infrastructure are critical to the security rule, which is an area where many healthcare providers struggle.

HIPAA Audit Requirements: 6 Steps To Be Prepared
1. Focus on HIPAA training for employees
Staff training is critical for an understanding of HIPAA compliance requirements. Employees who haven’t been trained or don’t have experience with compliance regulations can increase the risk of a failed audit.
Document your training to show the OCR (Office of Civil Rights), that you are dedicated to employee instruction. Create and publish policies that make training and education a priority. Make sure your team is thoroughly trained before the audit because OCR will ask questions to ensure everyone understands HIPAA regulations and compliance rules.
2. Create a Risk Management Plan and Conduct a Risk Analysis
A risk management plan and a risk analysis are required.
A HIPAA risk analysis looks for any security risks your company might be exposed to – all risks. The risk management plan is a strategy to address those risks.
In conducting the risk assessment, you should also prepare your security documents. Compliance rules state reports should be recorded, written, and kept in an easily accessible location. Rules should be specific to all aspects of your business, and not isolated to one area.
For example, all policies regarding the HIPAA privacy and security rule should be documented. Documents that cover incident response, breach notification, IT and firewalls, and physical security should be included. These documents will not only help in the audit process but provide clear direction in the operation of the business.

3. Select a Security Assessment and Privacy Officer
HIPAA requires a security and privacy officer for each covered entity and business. This does not have to be a new hire, but you do need someone responsible for the security and privacy of PHI. They are responsible for showing the effort being made to meet regulations.
The officer should also review business associate agreements. The OCR will discuss the third-party relationships that involve electronic protected health information. Create a list of vendors and suppliers, and the security and safeguards they have in place through the business associates agreement.
This officer should schedule a regular review of security policies and conduct a risk analysis on IT systems and data security. They should also have a record of any breaches or incidents. Don’t try to hide any problems or data breaches during the audit. Be honest. Incidents happen, and the OCR wants to know how you responded to the security breach.

4. Review Policy Implementation
As important as it is to document policies and procedures, it’s also important to see how those policies are being implemented. The OCR will review how those policies and procedures apply to the daily business operation, and if they are implemented consistently.
Talk to your team to see how the policies are working. If employees are struggling to follow policy, then take the time to analyze the problems and make adjustments as needed. Create an implementation schedule to include in the audit. The OCR wants to see the policies in action. If you are still implementing the plans, then show them the schedule, so that they know progress is being made.
5. Conduct an Internal Audit
An internal audit program is the best way to identify problems in your system before the OCR audit. Regularly conducting internal audits will not only help you solve problems before they turn into a fine, but also keep your team sharp and take pressure off during the actual review.
It’s often a good idea to work with an organization that specializes in compliance or data security to help conduct the internal audit. They can review your security and compliance standards and take a close look at your risk analysis and risk management plan. With an outside perspective, they may be able to identify problems that didn’t show up in your internal risk assessment. Partnering with an IT and data security provider will help ensure a complete and thorough internal audit.
As a best practice, review your policies and procedures as the auditor might. Consider if the policies are meeting the intent of the regulation and improving patient privacy and security. By critically analyzing these methods, you can find areas of improvement in both business operations and HIPAA compliance.
6. Create an Internal Remediation Plan
Once you’ve gone through the above steps and conducted an internal audit in preparation for your HIPAA audit, you should create a remediation plan to reduce risks and correct findings. Attach a schedule with timelines to the remediation plan and be prepared to discuss the plan with OCR during the audit.
While HIPAA sets guidelines and standards for protected health information, it’s also essential to see HIPAA as a continual process. A remediation plan and a schedule help to keep covered entities and businesses on track and compliant, even between audits.
Finally, make sure you limit your internal audit concerns to the policies and procedures of your business. While the business associate agreements are an important part of HIPAA, focusing on vendors and suppliers can leave your operations at risk. Your primary concern with the remediation plan and audit should be internal processes.

Start Preparing For Your HIPAA Compliance Audit
Risk analysis is a critical first step to achieve compliance with HIPAA. Compliance rules are not just crucial for meeting regulations but should be standards of ethical business operation.
Taking the steps above is critical for HIPAA compliance. Work with a HIPAA security compliance expert to review your IT infrastructure. Conduct a risk analysis and identify problems early, before the audit.
As the OCR prepares for the next phase of HIPAA audits, make sure you are ready. Protect your business and the private medical information you are entrusted to keep safe and secure.
Recent Posts
What are HIPAA Violations? What Are The Fines or Penalties?
Signed in 1996, the Health Insurance Portability and Accountability Act (HIPAA) is legislation that provides data privacy and security provisions for safeguarding medical information. Essentially, if you’re handling, transmitting, in possession of, or responsible for any health records; you’re going to need to be in compliance with HIPAA.
Regulation around HIPAA is strict and specific. However, what happens if HIPAA guidelines aren’t followed to the letter?
It’s important to know what constitutes a HIPAA violation for the sake of personal data.
Did you know that there are stiff penalties and fines for a violation? A breach could also destroy your business and your credibility within the healthcare community.

Who Needs to Worry About HIPAA Compliance?
The short answer is that everyone within the healthcare industry must be compliant. Anyone handling PHI must receive proper authorization and commit to full HIPAA compliance. HIPAA’s prime directive is to protect individually identifiable health information and to become the standard for the healthcare industry.
The standards are in place to protect both sides of the information: the patient and the establishment. These violations and the potential for a poor public reputation could be disastrous. Being aware of your requirements and standards is essential. If the guidelines aren’t followed, HIPAA violation penalties can be assessed
Organizations are required to secure all information and data on-site according to all relevant guidelines. They are also expected to remain compliant with their vendors and service organizations, known as Business Associates (BA). The secure sharing of protected electronic medical records is vital to providing quality medical care.
The intersection between healthcare professionals and the IT/Security industry means that many teams are working tirelessly behind the scenes to remain HIPAA compliant.
Here is a sampling of situations where HIPAA compliance is necessary at all times:
-
- IT vendors that access hospital information systems (containing patient data) to install, update and maintain malware protection and other security services.
- Organizations that hire outside cleaning, security or HVAC services. These services could view unattended documents and/or computer rooms while being unauthorized.
- Software companies that locally host programs that use or process Protected Health Information.
- A consultant granted local network access to PHI records to review compliance, quality or competitive metrics.
- Healthcare organizations that are instructing and monitoring BAs that handle PHI.
- A local or international data center or HIPAA web hosting company that has a focus on compliance for many regulations.

What Constitutes a HIPAA Violation?
You and your team have all of the HIPAA pieces in place: you’ve studied up on the rules, regulations, implementation, and even spoken to your external vendors. But what happens if you think you have missed something and you’re concerned about a violation. What do you need to know and what do you have to watch out for?
As long as you’re vigilant and detailed, you should be able to avoid some of the most common HIPAA violations:
- Sending texts containing PHI.
- Improper mailing or emailing of PHI. Is Gmail Compliant?
- Failure to monitor and maintain PHI access logs.
- The omission of a HIPAA-compliant Business Associate (BA) agreement with vendors before allowing access to the information system containing PHI.
- Accessing patient information on a personal device or home computer.
- Inadequate or lack of limitations as to who may view PHI.
- Failure to remove access authorization to employees who no longer have a reason to access PHI.
- Poor training to ensure that employees understand the many HIPAA requirements and guidelines.
- Lack of documentation of HIPAA compliance efforts.
Lost or Stolen Devices
Professionals in the healthcare industry often travel for work to attend security seminars and conferences. A smartphone, tablet, or laptop is a prime target for theft when left unattended.
A physician or hospital administrator has access to PHI. Therefore, if their device is lost or stolen, it is a direct violation of HIPAA. It is vitally important to keep track of your mobile devices. It’s also worth having remote-wipe systems in place in case a device goes missing.
Employee Disclosure of PHI
Employees must understand that discussing a patient’s condition, medications, or any personal data with co-workers or friends is a direct violation of HIPAA regulations.
Employees must also remain mindful of their environment when discussing a patient with authorized colleagues. Take extra care when discussing anything about a patient.
Improper Disposal of Medical Records
Employees must physically shred all records before placing them in the trash or recycling bin.
Electronic information that is deleted must be tracked and logged.
When in doubt, employees should seek the advice and training of their IT or compliance team to properly dispose of PHI records.
Mishandling of Records
Photocopiers are a high-risk zone for mishandling of PHI.
Most photocopiers feature a storage drive that saves and collects a document to let employee retrieve it at their desk or to re-print at a later time.
If the person creating the resulting document forgets to close their session, the following employee
Failure to Conduct a Risk Analysis
The HIPAA Security Rule and the HHS mandate that healthcare organizations perform a risk analysis. The risk analysis helps organizations discover opportunities and vulnerabilities in their computing system.
If the results indicate issues with confidentiality, integrity, and availability of electronic PHI held by the healthcare organization, the organization may correct the issue.
Left uncorrected, the findings may result in HIPAA violations.

HIPAA Penalty & Fine Structure
What are the consequences of violating HIPAA?
There are four tiers of HIPAA violations:
-
- Tier 1. Lack of awareness where a covered entity or individual was unaware that the act in question was a violation. Fines start at $100 and go up to $50,000 per violation, topping out at $1.5 million each year.
- Tier 2. Reasonable cause to believe the individual or entity knew about the rule or regulation. Issues at this tier are considered a lack of due diligence. The fines range from $1,000 to $50,000 per violation. The maximum fine is $1.5 million per year.
- Tier 3. The HIPAA violation was performed with willful neglect. The party then corrected the violation within the required time period of 30 days after discovery. Fines at this tier start at $10,000 and go to $50,000. The maximum penalty is $1.5 million per year.
- Tier 4. At this tier, the violation was made with willful neglect of HIPAA Rules. Further, the entity made no effort to correct the violation. There is a standard $50,000 fine per violation at this tier with a maximum fine of $1.5 million each year.
There are also criminal penalties for HIPAA violations and potential jail sentences:
-
- Unknowingly or with Reasonable Cause. The person may receive a jail sentence of up to one year.
- False Pretenses may result in a five years’ maximum jail sentence and a fine increase to $100,000 per violation.
- Personal Reasons or to Commit Fraud or a Crime. Malicious intent such as data breaches may lead to a jail sentence of up to 10 years and a fine up to $250,000 per violation.
As you can see from the HIPAA fines chart, the penalty structure for violations can act as a strong deterrent for healthcare organizations.
Recent HIPAA violations cases reported by federal law enforcement include:
-
- Memorial Healthcare System received a fine of $5,500,000 in 2017
- Children’s Medical Center of Dallas incurred a penalty of $3,200,000 in 2017
- Advocate Health Care Network’s violation warranted a $5,500,000 fine in 2016

How Are HIPAA Violations Uncovered?
The most common way that HIPAA violations are uncovered is through internal compliance audits performed by HIPAA-covered entities.
From an internal perspective, risk analysis is a powerful tool in discovering issues with HIPAA compliance. Risk analysis audits give organizations a chance to identify the violation source and correct it before an inspection takes place.
Employees often self-report when accidentally committing a HIPAA violation.
Finally, the Department of Health And Human Services Office for Civil Rights (OCR) may receive a direct complaint or tip on a potential HIPAA violation.
If a HIPAA private rule violation has occurred, there’s a safe bet that it will be uncovered sooner than later. It’s best to abide by all guidelines and regulations to avoid any issue.
Preventing HIPAA Violations
There are a few key steps to staying in-the-know and preventing HIPAA violations:
- Develop a strong PHI policy for employees that reflects current HIPAA rules and regulations. Optimize and update this policy regularly as HIPAA regulation will also change.
- Make sure all BAs sign the necessary PHI agreement.
- Perform regular audits of security systems and procedures.
- Hire an auditing team to perform the appropriate risk assessment to identify and correct potential security risks.
- Regularly monitor HIPAA compliance updates and changes.
With these steps in mind, you can avoid steep HIPAA violation fines.
Avoid Risking Compliance Fines and Penalties
The more you know about HIPAA guidelines and regulations, the better your organization will be when it comes to remaining compliant. The last thing you want is to unknowingly (or knowingly) walk into a situation where you’re handed an avoidable violation face a large fine.
The most important tool at your disposal is information. With the right strategy and training, your organization can stay on track for complete and consistent HIPAA compliance.
Recent Posts
Is Gmail HIPAA Compliant? What You Need to Know
Most industries rely on email to communicate, whether that is for status updates, meeting requests, or general information. The healthcare industry is no exception. Doctors, nurses, and specialists have to speak to one another about patient care just as regularly as the rest of us have to schedule that critical brunch meeting. What you might not have considered is that healthcare professionals must take an extra level of care to keep your private information safe.
Email within the healthcare industry must be HIPAA compliant and have compliant cloud storage and backup, especially when discussing patient-related issues. With over 281 billion e-mails sent worldwide every day, it is vital to maintaining HIPAA compliance for any medical industry.
As the largest email provider in the world, Google’s free service, Gmail, is available to everyone. But can it be used to maintain HIPAA compliance?
Let’s discover how e-mail works with Gmail, HIPAA compliance requirements, and if Gmail can function as a modern and efficient system for managing healthcare correspondence.

HIPAA Compliant Email Defined
Being HIPAA compliant goes back to People, Process, and Technology. “People” need to appropriate training to protect and handle Personal Health Information. “Processes” need to be supportive and simplistic to use, so people don’t circumvent them for more straightforward solutions. Finally, “Technology” should provide a platform that supports all of the above using the latest, auditable technology tools. In other words, you need to be able to capture usage logs, history, etc. into a long-term archive. We break it all down in our HIPAA Compliance Checklist.
Before determining whether an email service is HIPAA compliant or not, you should have a basic understanding of what HIPAA compliance in e-mail is. The Health Insurance Portability and Accountability Act (HIPAA), exists to protect the sensitive personal data of patients. HIPAA laws regulate how insurance and healthcare providers can disclose and use their Protected Health Information (PHI).
In theory, this should mean that if you are following all HIPAA standards and procedures, that e-mail can, in fact, be HIPAA compliant.
One of those standards is a robust level of multi-factor encryption. The goal is to guarantee that the communication between the provider and the patient is limited to those two parties and no one else. Therefore, even an encrypted email accessible by someone else (ex. a family member) who should not have seen it, theoretically is a HIPAA violation. That said, file encryption puts email text in a sort of code that cannot be read without decrypting the content—something that is done by the end user when the email is opened, and the user’s password is entered.
Gmail Itself is Not HIPAA Compliant
It’s easy enough to get a Gmail account. With over a billion active users, it’s clear that Gmail is the most active e-mail service in the world. Here-in lies the issue: this type of personal email is not compliant.
What makes email HIPAA compliant?
To be compliant, an email provider must sign a Business Associate Agreement (BAA). A BAA is a contract between the healthcare provider and anyone they do business with that will have access to protected health information.
Email, or more specifically an email server, is a perfect example of a third party who would have the opportunity to gain access to patient information. Therefore, any email provider that wants to support a healthcare institution must be willing to sign a BAA.
The issue with using an out-of-the-box Gmail account that you or I can sign-up for is that Google is unable to sign a business associate agreement baa. Not having a BAA means you’re not HIPAA compliant.

Introducing G Suite for Business Users
Fortunately, Google offers additional services to businesses. GSuite is a collection of the most-used Google apps for business, including Gmail, Google Drive, and Google Calendar, specially packaged for enterprises. GSuite must be associated with a domain that the user owns and is a paid service.
Although GSuite gives users access to Gmail, the most significant difference lies in Google’s ability to sign a BAA. This means that healthcare providers who wish to use Gmail as an email service for their company have the opportunity to purchase GSuite, link it to their company’s domain, and handle the technology component of the solution triad.
But not so fast: this does not create a HIPAA compliant solution. There’s more to do after a BAA is signed to ensure that all patient data that would be shared over email is protected. Encryption is a critical component of verifying that patient information is safe when being transmitted via email.
Think of it in terms of achieving two goals:
-
- Validate that you are only communicating with the intended party. This falls under the Privacy Component. By using PKI infrastructure and the encryption of the email using the patients Public Key, you can increase the level of confidence in the “privacy” of this communication.
- Confirm that the transmission cannot be intercepted. This component falls under Confidentiality. This is where encryption plays a role. As the communication is encrypted via the patients Public Key, only the patient can decode the message using their Private Key.
Third Party Encryption is Necessary for Full Compliance
While it is possible to encrypt emails using GSuite, this does not meet the encryption requirements to remain HIPAA compliant. Google uses Transport-Layer Security (TLS) to help encrypt e-mails in transit, but by Google’s own published statistics, 10% of emails sent and received remain unprotected. This is well under any limit that is acceptable to comply with HIPAA standards.
Users should be aware that even for GSuite, Google will automatically scan emails for spam and necessary security prevention. In 2017, Google eliminated scanning public e-mails for keyword research.
For Gmail to be genuinely HIPAA compliant, you need to use third-party encryption. A third party service will encrypt emails from inbox to inbox, allowing health providers to remain confident that their emails are compliant with HIPAA laws and keep their patients’ data as protected as possible.

Should You Also Obtain Consent from Patients?
You may want to consider having your patients fill out a consent form if you plan on communicating with them via email. Remember that households often still use shared e-mail addresses. A patient needs to sign off that it is okay to send such an email where others can potentially access the information. With today’s advances in technology and the busy lifestyles that people lead, email is often preferred over other forms of communication when it comes to confirming appointments or sending lab test results. However, patients should be aware that even despite extensive efforts on the part of the healthcare provider to protect sensitive information, no email is 100% safe.
When you obtain written consent from patients, you ensure that your patients are not only aware of the possibility that their data could be compromised when sent over email, but you obtain their permission to do so.
While some people believe that a written consent takes the place of purchasing a G Suite account and working with a third-party encryption service, this is not recommended. Even if your healthcare facility obtains approval from patients to send their data over secure email, you should still make every effort to ensure that data is encrypted and protected.
Sending HIPAA Compliant Email With a Signature
In the past, an email signature would be used to remind the recipient that the email may contain Protected Health Information. It would prompt them to delete the email if they believed that it was not intended for them.
While this in no way guarantees that an email received in error will be removed, it is one more step to show patients and lawmakers that as a healthcare provider, you are making every reasonable attempt to protect patients’ private data.
However in today’s market, if the e-mail is encrypted appropriately, the recipient would never see the footer, to begin with. These types of “security rules” are not considered acceptable and would never be compliant whatsoever.
You should use an email signature to remind patients how they can contact you and have their email removed if they should decide they are no longer comfortable sending and receiving emails that may contain their PHI. Making it easy for patients to opt out is another way to make sure that the only patients who receive emails are those who want to and have accepted the potential risks.

Compliant Email—It’s A Requirement In 2018
With the technology that is available today, there are very few legitimate reasons why a healthcare provider would not employ them to ensure that patient data is safe over email and all reasonable efforts have been made to make Gmail HIPAA compliant.
Not only are HIPAA violations and fines costly, but they can also be detrimental to the reputation of a practice. A healthcare provider that has been saddled with one or more fines due to violating HIPAA laws may find it more challenging to grow their patient base once word gets out.
Simply put, all healthcare providers who plan to use Gmail as an email service to communicate with insurance companies, patients, and other professionals, should use every available resource to protect their patients’ personal health information. Google makes signing up for G Suite and obtaining a business associate agreement is simple. You can even fill out the agreement online. Additionally, working with a third party encryption service is also a fast and straightforward process.
On the one hand, there would appear to be little to fear in regards to sensitive patient data being compromised when the proper steps are taken to ensure emails are as secure as possible.
However, most security assessment professionals would not necessarily agree that utilizing Google services for HIPAA is ideal. It is always going to be a shared platform that the user does not control. It does not provide the expected metadata and logging that is required among other things.
That said, it is better than nothing. When it comes to your data and your healthcare information, it’s always worth taking extra steps to remain private, secure, and compliant.
Recent Posts
PCI DSS 3.2 Compliance Requirements Guide: Updated For 2020
Every day we are becoming more and more a cashless society.
Plastic is the preferred method of payment for most North American businesses, and we even see a significant shift into virtual payment systems and direct-to-consumer banking.
In the modern world of digital currency, e-commerce, and fast-moving transactions, how can your business make sure that it is safely handling customer data?
Do you want to end up as the next headline splashed across the news as another company that has mishandled thousands of sensitive customer records?
If your business is accepting credit card payments and either stores, processes, or transmits cardholder data, then you are required to adhere to Payment Card Industry Data Security Standard compliance standards, otherwise known as PCI DSS.
The latest iteration of the standards is PCI DSS 3.2, as published by the Payment Card Industry Security Standards Council, with version 3.1 was entirely replaced as of October 2016.
This guide is a strong starting point for companies looking to maintain a strong security infrastructure. It also sets a clear and specific standardization of what is expected of companies that handle cardholder data.

What is PCI DSS Compliance?
PCI stands for “payment card industry” and refers to the Payment Card Industry Security Standards Council (PCI SSC).
The Counsel is a compromise between five proprietary data security and operations programs from major credit card companies: Visa, MasterCard, American Express, Discover, and JCB.
These companies aligned their policies to form the PCI DSS standard. This standard means that your company can pass validation of compliance from a Quality Security Assessor (QSA) from a firm-specific Draft Internal Security Assessor.
PCI validation methods culminate in an audit of PCI security standards controls. If the controls are found to be valid, a Report of Compliance (ROC) is issued. When a QSA conducts the audit, an Attestation of Compliance (AOC) is also issued. These are the accepted processes set by the PCI Security Standards Council.
TL:DR – Identify the 6 Most Prevalent Risk Factors in Data Security
Who do PCI DSS 3.2 Requirements Apply To?
Any company or private entity that can process, transmit or store consumer information from any of the five major credit card companies are subject to DSS compliance.
Credit card companies maintain merchant compliance levels depending on the number of annual transactions that a company completes:
-
- Level 1 – Merchants with more than 6 million yearly sales added across all channels. However, global merchants that identify as Level 1 in any region maintain that distinction in all areas.
- Level 2 – Merchants that conduct between 1 and 6 million transactions on an annual basis across all channels.
- Level 3 – Online Merchants that conduct e-commerce between 20K and 1 million transactions on an annual basis across all channels.
- Level 4 – Online Merchants that conduct e-commerce of fewer than 20K transactions on an annual basis across all channels, and merchants processing no more than 1 million yearly transactions across all channels.
Transactions may not be included in the merchant total if they are processed through local merchant locations instead of through the corporate entity.
The credit card companies also state that they maintain the sole right to define a Level 1 Merchant.
What Is the Timeline for the PCI DSS 3.2 Update?
As stated directly from the PCI Council:
“PCI DSS 3.1 will retire on October 31st, 2016, and after this time all assessments will need to use version 3.2. Between now and 31 October 2016, either PCI DSS 3.1 or 3.2 may be used for PCI DSS assessments. The new requirements introduced in PCI DSS v3.2 are considered best practices until January 31st, 2018. Starting February 1st, 2018 they are effective as requirements and must be used.”

What To Expect from the PCI 3.2 requirements Update?
The most critical changes that companies can expect from the update to the 3.2 standards are as follows.
Multi-factor authentication – This is different from two-factor authentication, or 2FA. Multi-factor authentication includes all processes that have at least two authentication factors. Every employee who has administrative access control to the cardholder data environment (CDE) must process through multifactor authentication. Previous PCI DSS standards only required 2FA and just remote administrators that were considered “untrusted” were required to verify themselves this way. This is one of the most significant expansions of the authentication requirement standards in the history of published PCI DSS.
SAQ Changes – All Self Assessment Questionnaires (SAQs) added many requirements outside of SAQ B and SAQ P2PE. SAQ B stayed the same as its previous iteration. SAQ P2PE took away two of its obligations. These requirements had to do with emailing and masking PAN data that was not encrypted.
Network segmentation and scoping – Systems outside of the CDE may now be included within the scope of PCI compliance. Many systems that connect to the CDE may also need to be added due to lack of segmentation.
Service providers – There are multiple changes for merchants and service providers including changes in penetration testing and the establishment of responsibilities for data and annual PCI compliance. There are also changes to the personal reviews performed on a quarterly basis, timeliness of reporting and detection of problems and cryptographic architecture.
Deprecation of SSL and Early TLS – All uses of SSL and TLS 1.0 within your CHE must be removed by June 30, 2018. However, TLS 1.1 is allowed though it is highly recommended to upgrade to TLS 1.2.
How Do The Updated Requirements Affect Your Organization?
The change from 3.1 to 3.2 is considered a non-major release and should not impact organizations significantly.
The depreciation of SSL and early TLS will be a challenge for many organizations but is a much-needed rule. SSL and TLS 1.0 have been exploitable for a significant amount of time and businesses are doing themselves a favor by upgrading. Many TLS and SSL exploits have caused many companies problems, including the exploits known as BEAST and POODLE. The National Institute of Standards and Technology (NIST) report that there are currently no patches that can provide a full repair for these TLS and SSL exploits.
How Can You Prepare for Your Next PCI DSS 3.2 Assessment?
Ordering Compliance Efforts Through the 6 Step Prioritized Approach
PCI DSS has identified six security measures that are most important in assessing and protecting against the most prevalent risk factors in business data security. These steps are meant to provide a company with a roadmap that can help to prioritize time and resources towards a fully compliant organization. The process is also intended to improve morale towards an environment of full compliance by creating a pragmatic approach that creates ultimate successes.
This prioritized approach also helps to promote consistency in compliance assessments along with operational and financial planning. Following the steps in order will also help a company to protect its cardholder data environment more quickly than haphazardly applying compliance standards. The approach was cultivated through an assessment of past breaches and feedback from forensic investigators and QSAs.
The six steps are as follows:
-
- The removal of authentication data that may be sensitive and the limitation of data retention – in short, companies should delete all data that they do not need. This is especially true of authentication data and other personal and financial information that may be sensitive. If this data is deleted from the system, its ability to be used to compromise the system is greatly reduced.
- The protection of networks and systems through constant vigilance in preparation for a breach – Companies should identify the most common point(s) of access for a breach or security compromise(s). The company should then identify and begin to prep the processes by which it will respond to these challenges.
- Securing all applications of payment card information – Weaknesses in application processes, servers, and controls for applications are straightforward ways for hackers to compromise company systems. This event should be considered on its own because of the importance of securing payment card applications.
- Monitoring who has physical access to company systems and controlling data access – Companies should implement a tiered system that limits the access of administrators to information that is outside of their jurisdiction. This system should be monitored, and all processes for the security of the system fully documented.
- The protection of cardholder data that is stored within the system – First, companies must determine whether they need to store highly sensitive information such as Primary Account Numbers. If a company has made this determination through a complete assessment of its internal processes, then it must create protection measures for that data.
- Ensuring that all protection controls are fully operational and finalizing any extra compliance efforts – By the time that milestone six is completed, all PCI DSS 3.2 requirements should be fulfilled. Additionally, any related processes, policies, and procedures that relate in any way to PCI DSS compliance should be fully operational as well.

Here are 10 best practices to prepare for your next PCI assessment.
Consistent Monitoring of Security Controls
Because of the speed with which malicious hackers improve their techniques, companies must continuously monitor their security controls. Part of being compliant with PCI DSS v3.2 is determining if a company can protect itself between assessments. If it cannot, then the assessment itself may not serve as an adequate deterrent for hackers looking for a weak target. It is also a requirement to review your PCI controls on a quarterly basis (if not monthly).
Timely Identification and Response to Failures of Security Controls
If a security control fails, then specific processes must be invoked within a timely manner to remain compliant. These processes include identification of why the control failed, identifying security issues that occurred during failure, full restoration of the control, the creation of procedures to ensure the failure doesn’t happen again, and the implementation of a monitoring strategy to verify operation of the control.
Determination of Changes Made before Upgrades Can be Completed
If any system is to be added into a PCI DSS environment, the impact of that system must be assessed. This system can be entirely new or modified from an existing system. Any part of a company’s infrastructure that connects to the addition must be evaluated for its compliance with PCI DSS 3.2. The company is responsible for identifying that new compliance requirements are met for all systems and networks modified by the change. The scope of the PCI DSS must be updated, and all new security controls required must be implemented and penetration tested.
Changes to the Organizational Structure Must be Reviewed
All employees must have privileged security access management controls that are relevant to his or her responsibilities and job description within the company. This structure should be reviewed from multiple scopes, including the individual and group levels.
Companies Should Initiate Consistent Reviews
A company should perform a regular review of its compliance measures to ensure that all requirements are implemented and up-to-date. These reviews must be conducted, at a minimum, quarterly to remain compliant. A company should also check to make sure that its processes have been properly updated as suggested by PCI 3.2. These internal reviews should include all company locations and all system components. A company has some leeway to determine how often these reviews should be completed, based upon the size and complexity of its infrastructure.
A main focus of these reviews should be to verify that appropriate records are being kept to maintain and prove PCI DSS v3.2 compliance efforts.
Regular Documentation of Both Software and Hardware Technologies
The vendor must fully support all equipment that is used within the company. All equipment must also meet the PCI DSS version 3.2 security requirements of the client. The company should immediately take action if any hardware is not vendor supported or the requirements are not met.
The same level of scrutiny should be applied to all software that the company is using. Software that is out of compliance accounted for 44% of data breaches in 2018.

Ensuring Accountability for Security Notifications
Five new requirements are introduced with 3.2 dealing specifically with the need for companies to notify customers of problems promptly.
The changes deal with detection of critical security systems and control mechanisms as well as cryptographic architecture. The amendments also require that a company perform quarterly reviews to vet all internal security personnel. The timely notification of severe issues to customers was found to be one of the aspects of security most lacking in companies, even those compliant with past iterations of the PCI DSS.
Ensuring the Proper Masking of Primary Account Numbers
To remain compliant with PCI DSS 3.2, a company must mask all instances of primary account numbers. At a maximum, only the last four digits or the first six digits may be shown. Any employee who is allowed to see more than this maximum must be accounted for. A company must create a list of these employees, including their roles within the company and the reasoning behind allowing them to see more than the masked primary account number.

Going Over the Designated Entities Supplemental Validation (DESV)
Because payment brands have the power to require service providers to fulfill additional DESV validations, companies should go over these requirements from the beginning of the compliance process. These requirements are covered in Appendix 3 and only will be penetration tested when instructed by an acquirer or a payment brand. PCI DSS 3.2 has the Designated Entities Supplemental Validation process as an appendix, including all new requirements that service providers will be expected to follow. These updated requirements include interviewing personnel to ensure documentation of cryptographic architecture. Additionally, companies are expected to implement a full change management process that keeps up with all system changes that may impact any system that is within the auspices of the PCI DSS.
Properly Scoping the Affected Environment
Evaluating the company environment is one of the most critical steps that you can take towards compliance and implementation of PCI DSS version 3.2.
To begin the process of scoping, a company should identify every component of the system that is either connected to or located within the CDE. The PCI SSC has given suggestions for compliance. Currently, there is a process to assess, report and remediate all data within the scope of the PCI DSS.
The Future Importance Of PCI Compliance
No one is quite sure exactly how malicious hackers will attack ecommerce in the coming years. There is a consensus, however, when you discuss data breaches in general. The problem is not going away.
Unprotected companies can almost expect to be targeted. Having a data security standard is essential to protecting your company and the information of the people who trust you. Take the above PCI compliance guide into account, consider PCI Compliant Web Hosting to bolster your security controls.
Recent Posts
SOC 2 Compliance Checklist For 2020: Be Ready For an Audit
This article was updated in December 2019.
Data is the lifeblood of your business. Your clients must be confident that their information is safe. They trust you to maintain it. If you fail, you will lose your clients’ trust.
Reassuring clients is the goal of SOC 2 compliance and certification. The integrity, confidentiality, and privacy of your clients’ data are at stake. Potential clients will want proof that you have measures in place to protect them. The SOC 2 compliance audit provides it.
What is SOC 2?
SOC stands for “System and Organization Controls” and is the agreed upon procedures of controls set by the American Institute of Certified Public Accountants (AICPA).
These defined controls are a series of standards designed to help measure how well a given service organization conducts and regulates its information. They are designed to provide clients confidence that an organization can be trusted to keep their data secure.
The purpose of an audit is to achieve SOC attestation or SOC certification.
Who can perform a SOC 2 audit?
This attestation can only be given after the organization is audited by an independent certified public accountant or CPA Firm who determines if the appropriate safeguards and procedures are in place.
Three Report Types An Organization Can Choose
The first is type 1.
These reports show the service organization’s controls over its client’s financial reporting standards. The organization being audited defines the objectives that are important to its business, and the controls it follows to achieve those objectives. Since the scope of the audit objective is self-defined, this is a very flexible standard and can be customized to each service provider.
The second is the type 2 report.
It focuses on five trust principals: security, availability, integrity, confidentiality, and privacy. Each trust principal has a standard set of controls and testing criteria for all service providers. When undergoing a Service Organization Control Type 2, the service organization selects which principals are relevant to their business.
The third is the type 3 report.
It is a simplified version of the SOC 2 report and was designed to attest that the service provider has completed a SOC 2 assessment, while also limiting the information to what is relevant to public parties.
SOC 1 and 2 also come in two report types.
Type 1 reports review the policies and procedures that are in operation at a specific moment in time.
The SOC Type II examines the policies and procedures over a period of time no less than six months. Since the Type II report takes into account the historical processes, it is a more accurate and comprehensive audit.

What Is Included in a SOC 2 Certification Report?
What the SOC 2 reports contain depends on the type of service the organization provides.
A service organization can be evaluated on one or more of the following trust services criteria (TSC) categories:
-
- Security – Information and systems are protected against unauthorized access, unauthorized disclosure of information and damage to systems that could compromise security availability confidentiality, integrity, and privacy of data or systems and affect the entity’s ability to meet its objectives.
- Availability – Information and organizational systems are available for operation and use to meet the entity’s objective requirements.
- Processing Integrity – System processing is complete, valid, accurate, timely and authorized to meet the entity’s objectives.
- Confidentiality – Information designated as confidential is protected to meet the entity’s objectives.
- Privacy – Personal information is collected, used, retained, disclosed and disposed of to meet the entity’s objectives.
The categories above all share a set of trust services criteria known as the standard criteria.
The common principles are:
-
- Control environment
- Communication and information
- Risk assessment
- Monitoring activities
- Control activities – which are further broken out by:
-
-
- Logical and physical access
- System Operational Effectiveness
- Change Management
- Risk Mitigation
-
These criteria must be addressed in every SOC audit. Depending on which TSC categories are being assessed, there may be more TSC’s which needed to be evaluated in addition to the standard criteria.
With the changes made in 2017, organizations can also get a SOC 2+ report which allows the services organization to address additional criteria from other compliance standards such as HITECH, HIPAA compliance, ISO 27001, Cloud Security Alliance (CSA), NIST 800-53 or COBIT 5.
When you order your compliance audit, you can decide which TSC categories are the most important. Base your decisions on what clients are most likely to want. Doing so will ensure that clients get the information they need. They will be less likely to come back to you with questions if they are addressed in the SOC 2 report.
The key is to reassure clients that you will keep their data secure. Your organizational controls should be explained. That way, clients can be confident that their data is safe with you.
Prepare with a SOC Audit Checklist
There are standard sense steps you can take. Being prepared will make the auditor’s job as comfortable as possible.
Your goal is to anticipate issues and try to resolve them beforehand.
Here are six steps you can take to prepare.
-
- Define the operating goals of your audit. You should ask yourself what your clients are most likely to want to know. You know the parameters of the SOC 2 audit. If you handle financial information, you may need a SOC 1 audit, as well.
- Define the scope of your SOC 2 audits. They typically address infrastructure, software, data, risk management, procedures, and people. You will also need to decide which trust principles to include. Any TSC you add will increase the scope of your audit. Again, choose the TSCs that are most likely to concern your clients.
- Address regulatory and compliance requirements. Every industry has regulations. For example, healthcare providers must comply with HIPAA compliance while those handling credit cards require PCI compliance. Doing a review of your enterprise’s compliance will help streamline the audit.
- Review and write security procedures. The auditor you hire will use your written policies as a guideline. Many companies fall behind. If your systems are out of date, you should update them. If you lack written procedures for anything covered by the audit, you should create them now. Written policies will help your employees adhere to internal rules.
- Perform a readiness assessment. A readiness assessment is your final chance to prepare. You can do the evaluation yourself. Alternatively, you can hire an auditing firm to do it for you as they abide by strict auditing standards. Think of it as a dress rehearsal. You can use the results to fill in holes in your audit prep.
- Evaluate and hire a certified auditor. As I mentioned before, hire someone with experience in your industry. The auditor will:
-
- Work with you to choose agreed-upon testing dates
- Give you a list of required documentation in advance of the audit
- Visit your site for document reviews, employee interviews, and walk-throughs
- Document the test results and review any issues with you
- Provide you with a completed type II report to share with your clients
-
Following these six steps of our SOC 2 compliance checklist will ensure that you have a smooth audit process. It is your job to do as much as you can to prepare. Even if you think your company is in good shape, periodic reviews are a must.
You may want to put a system in place to review written procedures. Doing so on a regular basis will make sure your next audit is without problems.
Who Can Request SOC 2 Compliance Reports?
Any organization contracting with a service provider should be concerned about security. That is true regardless of industry. However, it is not necessary to get a new audit every time.
SOC 1 and SOC 2 reports are meant to be confidential, limited-use documents for the service provider and its customers; however, they were often distributed publicly. The SOC 3 report was created as a result of the growing demand for a public facing report.
Now, any party who is knowledgeable about the services provided may request one. Parties who need to know how the entity’s system interacts with others may also get the report. These include user entities, sub-service user organizations, and other parties.
Of course, those interested in the internal controls may also request SOC reports. Before you entrust your data to anyone, requiring a SOC compliance audit is a good idea.
Many companies order SOC 2 audits. Then, they provide a report to prospective clients and other qualified parties.
Of course, it is possible that a client might have questions not covered by the SOC 2 report. In that case, you will need to decide how to respond. The report includes many of the most common questions and concerns clients will have.
How Have SOC Audits Changed?
The standards used for auditing have evolved over the years. Up until 2011, AICPA applied the SAS 70 standard. The SAS 70 standard became extremely popular, and subsequently, it was being used too broadly, and it started to lose the desired focus. In response, AICPA replaced SAS 70 with the Statement on Standards for Attestation Engagements (SSAE) No. 16 in 2011 and recently updated to version SSAE 18, in May of 2017.
The new requirements for the SSAE 18 are as follows.
-
- IPE, or Information Produced by the Entity. Companies must get evidence of the accuracy of any information provided. Examples might include standard queries or report parameters.
- Vendor management and monitoring of sub-service organizations. Service providers or data centers must include controls for sub-service organizations. The goal is to ensure that anybody with access to the data is adhering to control standards.
- CUECs or Complementary User Entity Controls must be in place. They should be limited to controls that are needed to achieve the stated control objectives
- Internal audit and regulatory examinations. SSAE 18 requires service organizations to read specific reports. Specifically, they relate to internal and regulatory examinations.
The SSAE will continue to evolve as new security risks come to light. Keeping up with risks can feel a bit like a game of Whack-A-Mole.
One example is the new SOC Cybersecurity examination and updated trust services principles that went into effect on December 15th, 2018. AICPA’s goal is to stay abreast of information security needs and respond accordingly.
How Much Does SOC 2 Auditing Cost?
The expense can vary depending on what is included.
Some of the things that can affect the cost include:
-
- The scope of services included in the report
- The TSCs you choose to add
- The size of your organization
- The number of in-scope systems and processes
In other words, if you have multiple systems and methods to include, the price will increase. Any system that affects the security of clients’ sensitive data must be audited. That is the only way to reassure clients to trust you with their data.
For the best result, choose a firm with IT auditing experience. They should identify the employees who will complete your audit. It is essential to ensure that the firm does background checks on anyone who will have access to your customer data.
Finally, make sure that you ask for (and check) references before hiring an audit firm. Ideally, the firm you choose should have experience in your industry.

Understand The Importance of SOC Compliance Audits
Compliance with SOC 2 reassures clients. Upon auditing, you can provide them with the reports for their records. Having a current report on hand will ensure that prospective clients know they can trust you. Use our SOC 2 compliance checklist to prepare for an audit.