RAML Tutorial: Using RAML to Document REST API contracts
In an ideal world, our programs, interfaces, and APIs would not need documentation. Our clients would all be magical beings, able to read our minds and understand precisely what it is our system does and how to use it.
Unfortunately, this is not the status quo today, since many enterprises use hand-written documentation (usually in PDF or Microsoft Word format) in a bid to make life easier for integrating developers. Hypermedia evangelists, in particular, are not pleased with this situation. If we had to compare this to websites, it would be the same as being provided a manual for each site we visit – and like websites, APIs should be self-documenting and give the user with enough information to allow him to use and navigate across API states. Unfortunately, however, many enterprises shy away from not having a “document” – particularly in areas like FinTech – since clients tend to be more conservative in the ways they work and the technologies they adopt.
To add insult to injury, these manual documents are written in a separate sphere from the implementation, sometimes by entirely different departments/teams within the enterprise. As such it is relatively common that synchronization issues occur which are very hard to fix since the manual review is pretty much the only way to identify and correct problems.
At this point many old-school SOAP aficionados rear their heads and make fun of this newfangled REST stuff. “… in our day we had the WSDL!, you could generate everything from the WSDL!, You don’t have a WSDL in REST ha!” And even though SOAP is inferior to REST in many ways, the WSDL is the one thing that was almost universally loved (except maybe by the person who had to author it J) and could facilitate understanding and integration of APIs by clients.
Luckily, REST now has its “WSDL.” Three new emerging technologies: RAML, Swagger, and API Blueprints aim to document the contract that is our API and to do so in a way that is simple and easy to use. For the rest of the article, we will be using RAML for our discussion and examples. However, the same points can be applied to Swagger and API Blueprints. We chose to use RAML since it is straightforward to write (at the time of evaluation) and understand, while at the same time providing constructs which encourage reuse heavily.
What is RAML?
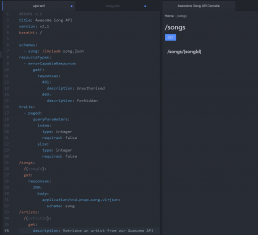
Rest API Markup Language, aka RAML, is an open language designed to document REST APIs which are based on YAML. This means that indentation is used to create structure leaving the document free of braces and other text which is not directly relevant to the body being documented.
My favorite aspect of RAML as a language is that it has a very short learning curve and proper documentation, editors, and tutorials to get developers going. The open nature of the language means that plenty of tooling is being developed in this space. Another great feature is that the language encourages reuse through traits, resource types and other bits and bobs which allow us to define concepts once and reuse across our API stack. This not only saves time but encourages consistency.
The main benefit of using RAML (or any other API Documentation Language) is that we are producing a document that is machine readable. This means that we are adding an extra step toward having some shiny document we can send to prospective clients, but it also means that this same RAML file can be used to generate all sorts of different documentation which can be consumed by different people:
- A simplified version of Management/Evaluation
- Interactive documentation including Sandbox for integrating developers
- Code generation for internal developers
- Test Generation and Verification of endpoints for QA teams and internal developers
- GUI generation for rapid prototyping
And the list goes on.
Contract-first vs Code-first
We can apply RAML to our projects using two approaches: “Contract-First,” i.e., when the RAML file is written before implementation starts or “Code-First,” where the implementation precedes or is done in sync with RAML development. Both have very different use-cases.
Let’s discuss contact-first, first J. In this approach, an effort is made on the API documentation before the coding begins. The main benefit here is that teams will focus on the consumption of the APIs rather than what is available under the hood and take design decisions which will ultimately result in a better experience for integrating clients.
Another benefit is that during the development of the API, tools such as the API Console or other WYSIWYG editors provide a live view of the API as it’s built. This can be mocked and exercised by various team members (UI Developers, Product Stakeholders, etc.) and can provide a very visual way of spotting issues and improve the design. Once the document is complete, this can be used as an integration point between teams – Javascript/UI developers can code against a mocked variant of the RAML file while backend developers can use it to generate code or tests.
We are trying to move all our internal development to a contract-first approach since the only drawback of this approach is that we are adding a small step to the development process. This approach is not always possible, especially with existing projects where there is already a large API footprint. In these cases, a big-bang documentation shift can be hard to justify, and a code-first approach can be adopted.
A Code-first approach does not help improve the overall design. However, there are different benefits. As a starting point, this approach can be applied to our existing code-base to generate documentation and all other associated benefits, with minimal effort. This documentation can provide visibility to teams who might not be operating outside the backend. At phoenixNAP, we have applied this technique successfully using an in-house plugin which generated a RAML file from custom annotations used in the backend of our phoenixNAP Client Portal web application. This internal RAML was used by our front-end teams to improve the communication with the backend developers and to allow us to work together on building a UI and a backend for a task simultaneously.
This plugin was extended to generate RAML from standard Spring MVC annotations and was open-sourced under the Apache 2.0 License and can be found on GitHub.
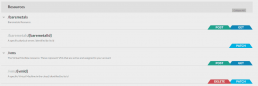
In the architecture department, the RAML plugin is used within our Spring Boot reference container to allow us to create API-driven proofs-of-concept rapidly. For these internal research projects, development speed is critical since their purpose is to validate or illustrate an approach we plan to take. Rather than having to develop an interface, writing simple APIs which are parsed by the SpringMVC RAML plugin provides us with an interface which we can then use to evaluate the solution. This tooling allows for very rapid prototyping and can also allow us to ship the POC to other departments without having to spend time developing an interface or documentation.
Keeping Things in Sync
One of the drawbacks and in some ways benefits of API documentation languages is that they are separate from the implementation. This puts us in a situation where we might have different sources of “truth” similar to how PDFs and their corresponding Word Documents may end up out of sync as changes are applied to one but not the other.
The most significant difference is that unlike PDF/Word, where a manual review is the only solution, in the RAML world we have tooling that can help us keep these documents in check.
Abao (https://github.com/cybertk/abao/) is a tool which parses the RAML file and executes tests on our endpoints to check if the implementation respects the contract. The SpringMVC RAML parser generates a RAML model from the implementation and compares this to the contract being published. This can be used as a Maven plugin which could trigger a build failure when incompatible scenarios are detected.
Conclusion
API documentation languages are at an exciting stage.
The open and straightforward nature of these languages makes adoption and extension reasonably simple – when we introduced RAML there were minimal issues, and many benefits out of the box. We were able to build our own tools on top of these technologies. As such, there is so much brought to the table that is there really any point to using static documents to document our APIs anymore?
Recent Posts
SECaaS: Why Security as a Service is a Trend To Watch
Your company is facing new cybersecurity threats daily. Learn how Security as a Service (SECaaS) efficiently protects your business.
The cybersecurity threat landscape is rapidly expanding. Technology professionals are fending off attacks from all directions.
The lack of security expertise in many organizations is a challenge that is not going away anytime soon.
CIOs and CSOs have quickly realized that creating custom solutions are often too slow and expensive.
They now realize that managed security service providers or MSSP companies are the best way to maintain protection. Software-as-a-service (SaaS) is becoming a more comfortable concept for many technology professionals.
What is Security as a Service?
SECaaS is a way to outsource complex security solutions needs to experts in the field while allowing internal IT and security teams to focus on core business competencies.
Not long ago, security was considered a specialization that needed to be in-house. Most technology professionals spent only a small portion of their time ensuring that backups always, the perimeter was secure, and firewalls were in place. There was a relatively black and white view of security with a more inward focus. Antivirus software offers only basic protection. It is not enough to secure against today’s threats.
Fast forward to today, where risks are mounting from all directions. Data assets spend a significant portion of their life in transit both within and outside the organization. New software platforms are being introduced on a weekly if not a daily timeline with many organizations. It is more difficult than ever to maintain a secure perimeter, and accessible data, while staying competitive and agile.

Threat Protection from All Sides
Today’s business users savvier about accessing secure information. Yet, many are less aware of the ways that they could be opening their networks to external attacks.
This causes a nightmare for system administrators and security professionals alike as they attempt to batten down the hatches of their information and keep it truly secure. Advanced threats from external actors who are launching malware and direct attacks at a rate of thousands per day are a challenge.
The drive towards accessibility of data and platforms at all times causes a constant tension between business users and technology teams. Security technologists seek to lock down internal networks at the same time users are clamoring for the ability to bring their own device to work.
There is a significant shift in today’s workforce towards the ability to work whenever and wherever the individual happens to be.
This makes it crucial that technology teams can provide a great user experience without placing too many hurdles in the way of productivity.
When business users find an obstacle, they are likely to come up with an unacceptable workaround that is less secure than the CSO would like. Account requirements too prohibitive?
No problem. Users will just share their usernames and passwords with internal and external parties. Providing easy access to confidential information. These are only the internal threats. External forces are constantly banging on your digital doors, looking for a point of weakness that they can exploit.
Cybercriminals are active throughout the world. No businesses are immune to this threat. Damage from cybercrime is set to exceed an annual amount of $6 trillion by 2021. Doubling the impact from just 2015.
The amount of wealth changing hands due to cybercrime is astronomical. This can be a heavy incentive both for businesses to become more secure and for criminals to continue their activity. Spending on cybersecurity is also rising at a rapid rate and expected to continue that trend for quite some time. However, businesses are struggling to find or train individuals in the wide spectrum of skills required to combat cyberterrorism.

Benefits of Security as a Service
SECaaS has a variety of benefits for today’s businesses including providing a full suite of managed cloud computing services.
Staffing shortages in information security fields are beginning to hit critical levels.
Mid-size and smaller businesses are unlikely to have the budget to hire these professionals. IT leaders anticipate that this issue will get worse before it improves. Technology budgets are feeling the strain. Businesses need to innovate to stay abreast of the competition.
The costs involved with maintaining, updating, patching and installing software are very high. There are additional requirement to scale platforms and secure data storage on demand. These are all areas cloud-based security provides a measure of relief for strained IT departments.
Managed cloud SECaaS businesses have the luxury of investing in the best in the business from a security perspective — from platforms to professionals. Subscribers gain access to a squad of highly trained security experts using the best tools that are available on the market today and tomorrow. These security as a service providers are often able to deploy new tech more rapidly and securely than a single organization.
Automating Manual Tasks
Having someone continually review your business logs to ensure software and data are still secure is probably not a good use of time. However, SECaaS platforms can monitor your entire employee base while also balancing endpoint management.
Results are delivered back in real time with automated alerts triggered when unusual activity is logged. Completing these tasks automatically allows trained technology professionals to focus more on efforts that move the business forward while much of the protection is done behind the scenes. Benchmarking, contextual analytics, and cognitive insights provide workers with quick access to items that may be questionable. This allows movement to happen without requiring drudge work behind the scenes.
Reducing Complexity Levels
Does your information technology team have at least a day each week to study updates and apply patches to your systems? If not, your business may be a prime candidate for security as a service.
It is becoming nearly impossible for any IT team to stay updated on all platforms. Or, see how their security needs interact with other platforms that you’re utilizing and then apply the appropriate patches. Many organizations require layers of protection due to the storage of personally identifiable information (PII). This can add to the level of complexity.
Protecting Against New Threats
Cybercriminals are always looking for new ways to attack a large number of systems at once. Global ransomware damage costs are in the billions of dollars, and an attack will occur approximately every 14 seconds by 2020.
Industry insiders such as Warren Buffet state that cyber attacks are the worst problem faced by humankind — even worse than nuclear weapons. The upfront cost of paying a ransom is only the tip of the iceberg when it comes to damages that are caused. Businesses are finding hundreds of thousands of dollars in direct and indirect costs associated with regaining access to their information and software.

Examples of Security as a Service Providers Offerings
Traditional managed providers are enhancing security offerings to include incident management, mobile, endpoint management, web, and network security threats and more.
SECaaS is a sub-category of SaaS and continues to be of interest to businesses of all sizes as complexity levels rise.
Today’s security as a service vendors go beyond the traditional central management console and include:
- Security analysis: Review current industry standards and audit whether your organization is in compliance.
- Performance balancing with cloud monitoring tools: Guard against a situation where a particular application or data pathway is unbalancing the infrastructure.
- Email monitoring: Security tools to detect and block malicious emails, including spam and malware.
- Data encryption: Your data in transit is much more secure with the addition of cryptographic ciphers.
- Web security: Web application firewall management that monitors and blocks real-time. Threat management solutions from the web.
- Business continuity: Effective management of short-term outages with minimal impact to customers and users.
- Disaster recovery: Multiple redundancies and regional backups offer a quick path to resuming operations in the event of a disaster.
- Data loss prevention: DLP best practices include tracking and review of data that is in transit or in storage, with additional tools to verify data security.
- Access and identity management: Everything from password to user management and verification tools.
- Intrusion Management: Fast notifications of unauthorized access, using machine learning and pattern recognition for detection.
- Compliance: Knowledge of your specific industry and how to manage compliance issues.
- Security Information Event Management: Log and event information is aggregated and shown in an actionable format.
While offerings from security as a service companies may differ, these are some of the critical needs for external security management platforms.
Once you have a firm grasp of what can be offered, here’s how you can evaluate vendor partners based on the unique needs of your business.

Evaluating SECaaS Providers
Security has come to the forefront as businesses continue to rely on partners to perform activities from infrastructure support to data networks. This shift in how organizations view information risk makes it challenging to evaluate a potential cloud computing solution as a fit.
The total cost of ownership (TCO) for working with a SECaaS partner should represent significant savings for your organization. This is especially important when you balance against performing these activities internally. Evaluate total costs by looking at the expense of hiring information security professionals, building adequate infrastructure and reporting dashboards for monitoring. Be sure you fully disclose items such as total web traffic, the number of domains and data sources and other key metrics when requesting estimates.
The level of support that is provided, guaranteed uptime and SLAs are also essential statistics. Your vendor should be able to provide you with detailed information on the speed of disaster recovery. You will need the same information on how quickly infiltrations are identified and any issue resolved. A disaster situation is the least likely possibility. You should also review the time to address simple problems. For example, a user who is locked out of their account or adding a new individual to your network. A full security program will allow your network managed service provider to pinpoint problems quickly.
It is critical that the solution you select works with other business systems that are already in use. Secure cloud solutions are often easier to transition between than on-premise options. It is better to work with a single vendor to provide as many cloud services as possible. This allows for bundled pricing. It can enhance how well software packages work together.
Your team can monitor system health and data protection with real-time dashboards and reporting. This is valuable whether or not a vendor is also overseeing the threat detection process. You will improve the internal comfort level of your team while providing ready access to individuals who are most familiar with the systems. This availability of data will keep everything working smoothly. Be sure that your vendor understands how to provide actionable insight. They should also make recommendations for improving your web security. Access is always a concern.
Evaluating core IT security strategy factors help keep your organization’s goals aligned. A proactive SECaaS vendor-partner adds value to the business by providing DDOS protection. Plus, offering risk management and more.
Security challenges for today’s CIOs & CSOs are Real
Hackers target businesses of all sizes for ransomware and phishing attacks. Staying vigilant is no longer enough.
Today’s sophisticated environment requires proactive action taken regularly with the addition of advanced activity monitoring. Keeping all of this expertise in-house can be overly expensive. The costs involved with creating quality audits and control processes can also be quite high.
Security in the cloud offers the best of both worlds.
Learn more about our security as a service. Request a free initial consultation with the experts at PhoenixNAP.
Recent Posts
19 Best Automated Testing Tools For 2020
This article was updated in December 2019.
Before you begin introducing test automation into your software development process, you need a solution. A successful test automation strategy depends on identifying the proper tool.
This post compiles the best test automation tools.
The Benefits of Automated Testing Over Manual
Automated software testing solutions do a significant portion of the work otherwise done by manual testing. Thus, reducing labor overhead costs and improving accuracy. Automated testing is, well, not manual. Rather than having to program everything from the ground up, developers and testers use sets of pre-established tools.
This improves the speed of software testing and also increases reliability and consistency. Testers do not need to worry about the strength of their product, nor do they need to worry about maintaining it and managing it. They need only to test their own application.
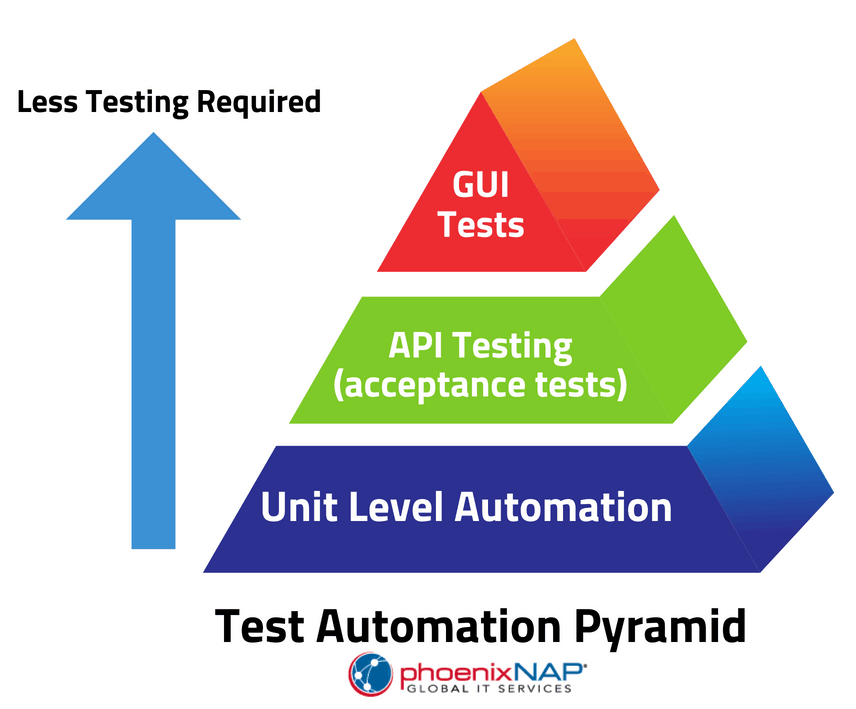
When it comes to automating these tests, being both thorough and accurate is a necessity. Developers have already tested these automated solutions for thoroughness and accuracy. Solutions often come with detailed reporting and analysis that can be used to further improve upon applications.
Even when custom scripted, an automated testing platform is going to provide stability and reliability. Essentially, it creates a foundation on which the testing environment can be built. Depending on how sophisticated the program is, the automated solution may already provide all of the tools that the testers need.
Types of Automated Software Testing Tools
There are a few things to consider when choosing an automated testing platform:
Open-source or commercial?
Though commercial products may have better customer service, open-source products are often more easily customized and (of course) more affordable. Many of the most popular automated platforms are either open source or built on open-source software.
Which platform?
Developers create frameworks for mobile testing applications, web-based applications, desktop applications, or some mix of different environments. They may also run on different platforms; some may run through a browser while others may run as a standalone product.
What language?
Many programming environments favor one language over another, such as Java or C#. Some frameworks will accept scripting in multiple languages. Others have a single, proprietary language that scripters will need to learn.
For testers or developers?
Testers will approach automated testing best practices substantially differently from developers. While developers are more likely to program their automated tests, testers will need tools that let them create scenarios without having to develop custom scripting. Some of the best test automation frameworks are specifically designed for one audience or another, while others have features available for both.
Keyword-driven or data-driven?
Different performance testing formats may have a data-based approach or a keyword-driven approach, with the former being better for developers and the latter being better for testers. Either way, it depends on how your current software testing processes run.
A test automation framework may have more or less features, or provide more robust or less robust scripting options.
Open Source DevOps Automation Testing Tools
Citrus
Citrus is an automated testing tool with messaging protocols and data formats. HTTP, REST, JMS, and SOAP can all be tested within Citrus, outside of broader scope, functional automated testing tools such as Selenium. Citrus will identify whether the program is appropriately dispatching communications and whether the results are as expected. It can also be integrated with Selenium if another front-end functionality testing has to be automated. Thus, this is a specific tool that is designed to automate and repeat tests that will validate exchanged messages.
Citrus appeals to those who prefer tried and true. Citrus is designed to test messaging protocol. It contains support for HTTP, REST, SOAP, and JMS.
When applications need to communicate across platforms or protocols, there isn’t a more robust choice. It integrates well with other staple frameworks (like Selenium) and streamlines tests that compare user interfaces with back-end processes (such as verifying that the send button works when clicked). This enables an increased number of checks in a single test and an increase in test confidence.
Galen
Unique on this list, the Galen is designed for those who want to automate their user experience testing. Galen is a niche, specific tool that can be used to verify that your product is going to appear as it should on most platforms. Once testing has been completed, Galen can create detailed reports, including screenshots, and can help developers and designers analyze the appearance of their application over a multitude of environments. Galen can perform additional automated tasks using JavaScript, Java, or the Galen Syntax.
Karate-DSL
Built on the Cucumber-JVM. Karate-DSL is an API tool with REST API support. Karate includes many of the features and functionality of Cucumber-JVM, which includes the ability to automate tests and view reports. This solution is best left for developers, as it does require advanced knowledge to set up and use.
Robot Framework
Robot is a keyword-driven framework available for use with Python, Java, or .NET. It is not just for web-based applications; it can also test products ranging from Android to MongoDB. With numerous APIs available, the Robot Framework can easily be extended and customized depending on your development environment. A keyword-based approach makes the Robot framework more tester-focused than developer-focused, as compared to some of the other products on this list. Robot Framework relies heavily upon the Selenium WebDriver library but has some significant functionality in addition to this.
Robot Framework is particularly useful for developers who require Android and iOS test automation. It’s a secure platform with a low barrier to entry, suited to environments where testers may not have substantial development or programming skills.
Robot is a keyword-driven framework that excels in generating easy, useful, and manageable testing reports and logs. The extensive, pre-existing libraries streamline most test designing.
This enables Robot to empower test designers with less specialty and more general knowledge. It drives down costs for the entire process — especially when it comes to presenting test results to non-experts.
It functions best when the range of test applications is broad. It can handle website testing, FTP, Android, and many other ecosystems. For diverse testing and absolute freedom in development, it’s one of the best.
Well suited to environments where testers may not have substantial development or programming skills.
Selenium
You may have noticed that many of these solutions are either built on top of or compatible with Selenium testing. Selenium is undoubtedly the most popular automated security testing option for web applications. However, it has been extended quite often to add functionality to its core. Selenium is used in everything from Katalon Studio to Robot, but alone, it is primarily a browser automation product.
Those who believe they will be actively customizing their automated test environments may want to start with Selenium and customize it from there. In contrast, those who wish to begin in a more structured test environment may be better off with one of the systems that are built on top of Selenium. Selenium can be scripted in a multitude of languages, including Java, Python, PHP, C#, and Perl.
Selenium is not as user-friendly as many of the other tools on this list; it is designed for advanced programmers and developers. The other tools that are built on top of it tend to be easier to use.
Selenium can be described as a framework for a framework.
Many of the most modern and specialized frameworks draw design elements from Selenium. They are also often made to work in concert with Selenium.
Its original purpose was testing web applications, but over the years it has grown considerably. Selenium supports C#, Python, Java, PHP, Ruby, and virtually any other language and protocol needed for web applications.
Selenium comprises one of the largest communities and support networks in automation testing. Even tests that aren’t designed initially on Selenium will often draw upon this framework for at least some elements.
Watir
A light and straightforward automated software testing tool, Watir can be used for cross-browser testing and data-driven testing. Watir can be integrated with Cucumber, Test/Unit, and RSpec, and is free and open source. This is a solid product for companies that want to automate their web testing as well as for a business that works in a Ruby environment.
Gauge
Gauge is produced by the same company that developed Selenium. With Gauge, developers can use C#, Ruby, or Java to create automated tests Gauge itself is an extensible program that has plug-in support, but it is still in beta; use this only if you want to adopt cutting-edge technology now. Gauge is a promising product, and when it is complete will likely become a standard, both for developers and testers, as it has quite a lot of technology behind it.
Gauge aims to be a universal testing framework. Gauge is built around being lightweight. It uses a plugin architecture that can be work with every primary language, ecosystem, and IDE in existence today.
It is primarily a data-driven architecture, but the emphasis on simplicity is its real strength. Gauge tests can be written in a business language and still function. This makes it an ideal automated testing tool for projects that span workgroups. It is also a favorite for business experts who might be less advanced in scripting and coding. It is genuinely difficult to find a system that cannot be tested with Gauge.
Commercial Automation Tools
IBM Rational Functional Tester
A data-driven performance testing tool, IBM is a commercial solution that operates in Java, .Net, AJAX, and more. The IBM Rational Functional Tester provides unique functionality in the form of its “Storyboard” feature, whereby user actions can be captured and then visualized through application screenshots. IBM RFT will give an organization information about how users are using their product, in addition to how users are potentially breaking their product. RFT is integrated with lifecycle management systems, including the Rational Quality Manager and the Rational Team Concert. Consequently, it’s best used in a robust IBM environment.
Katalon Studio
Katalon Studio is a unique tool that is designed to be run both by automation testers and programmers and developers. There are different levels of testing skill set available, and the testing processes include the ability to automate tests across mobile applications, web services, and web applications. Katalon Studio is built on top of Appium and Selenium, and consequently offers much of the functionality of these solutions.
Katalon Studio is an excellent choice for larger development teams that may require multiple levels of testing. It can be integrated into other QA testing processes such as JIRA, Jenkins, qTest, and Git, and its internal analytics system tracks DevOps metrics, graphs, and charts.
Ranorex
Ranorex is a commercial automation tool designed for desktop and mobile testing. It also works well for web-based software testing. Ranorex has the advantages of a comparatively low pricing scale and Selenium integration. When it comes to tools, it has reusable test scripts, recording and playback, and GUI recognition. It’s a sufficient all-around tool, especially for developers who are needing to test on both web and mobile apps. It boasts that it is an “all in one” solution, and there is a free trial available for teams that want to test it.
Sahi Pro
Available in both open source and commercial versions, Sahi is centered around web-based application testing. Sahi is used inside of a browser and can record testing processes that are done against web-based applications. The browser creates an easy-to-use environment in which elements of the application can be selected and tested, and tests can be recorded and repeated for automation. Playback functionality further makes it easy to pare down to errors.
Sahi is a well-constructed testing tool for smaller parts of an application. Still, it may not be feasible to use for more wide-scale automated test production, as it relies primarily on recording and playback. Recording and playback is generally an inconsistent method of product testing.
TestComplete
Both keyword-driven and data-driven, TestComplete is a well-designed and highly functional commercial automated testing tool. TestComplete can be used for mobile, desktop, and web software testing, and offers some advanced features such as the ability to recognize objects, detect and update UI objects, and record and playback tasks. TestComplete can be integrated with Jenkins.
TestPlant eggPlant
TestPlant eggPlant is a niche tool that is designed to model the user’s POV and activity rather than simply scripting their actions. Testers can interact with the testing product as the end users would, making it easier for testers who may not have a development or programming background. TestPlant eggPlant can be used to create test cases and scenarios without any programming and can be integrated into lab management and CI solutions.
Tricentis Tosca
A model-based test automation solution, Tricentis Tosca offers analytics, dashboards, and multiple integrations that are intended to support agile test automation. Tricentis Tosca can be used for distributed execution, risk analysis, integrated project management, and can support applications, including mobile, web, and API.
Unified Functional Testing
Though it is expensive, Unified Functional Testing is one of the most popular tools for large enterprises. UFT offers everything that developers need for the process of load testing and test automation, which includes API, web services, and GUI testing for mobile apps, web, and desktop applications. A multi-platform test suite, UFT can perform advanced tasks such as producing documentation and providing image-based object recognition. UFT can also be integrated with tools such as Jenkins.
Cypress
Designed for developers, Cypress is an end-to-end solution “for anything that runs inside the browser.” By running inside of the browser itself, Cypress can provide for more consistent results when compared to other products such as Selenium. As Cypress runs, it can alert developers of the actions that are being taken within the browser, giving them more information regarding the behaviors of their applications.
Debuggers can be quickly introduced directly to applications to streamline the development process. Overall, Cypress is a reliable tool that is designed to be used for end-to-end during project management development.
Serenity
Serenity BDD (also known as Thucydides) is a Java-based framework that is designed to take advantage of behavior-driven development tools. Compatible with JBehave and Cucumber, Serenity makes it easier to create acceptance and regression testing. Serenity works on top of behavior-driven development tools and the Selenium WebDriver, essentially creating a secure access framework that can be used to create robust and complex products. Functionality in Serenity includes state management, WebDriver management, Jira integration, screenshot access, and parallel testing.
Through this built-in functionality, Serenity can make the process of performance testing much faster. It comes with a selection of detailed reporting options out-of-the-box, and a unique method of annotation called @Step. @Step is designed to make it easier to both maintain and reuse your tests, therefore streamlining and improving your test processes. Recent additions to Serenity have brought in RESTful API testing, which works through integration with REST assured. As an all-around testing platform, Serenity is one of the most feature-complete.
RedwoodHQ
RedwoodHQ is an Open Source test automation framework that works with any tool.
It uses a web-based interface that is designed to run tests on an application with multiple testers. Tests can be scripted in C#, Python, or Java/Groovy, and web-based applications can be tested through APIs, Selenium, and their web IDE. Creating test scripts can be completed on a drag-and-drop basis, and keyword-friendly searches make it easier for testers to develop their test cases and actions.
Though it may not be suitable for more in-depth testing, RedwoodHQ is a superb starting place and an excellent choice for those who operate in a primarily tester-driven environment. For developers, this performance testing tool may prove to be too shallow. That being said, it is a complete automation tool suite and has many necessary features built-in.
Appium
Appium has one purpose: testing mobile apps.
That does not mean to imply that it has a limited range of testing options. It works natively with iOS, Android, and other mobile operating systems. It supports simulators and emulators, and it is a darling for test designers who are also app developers. Perhaps the most notable perk of Appium is that it enables testing environments that do not require any changes to the original app code. That means apps are tested in their ready-to-ship state and produces test results that are as reliable as possible.
Apache JMeter
JMeter is made for load testing. It works with static and dynamic resources, and these tests are critical to all web applications.
It can simulate loads on servers, server groups, objects, and networks to ensure integrity on every level of the network. Like Citrus, it works across communication protocols and platforms for a universal look at communication. Unlike Citrus, it’s emphasis is not on basic functionality but in assessing high-stress activity.
A popular function among testers is JMeter’s ability to perform offline tests and replay test results. It enables far more scrutiny without keeping servers and networks busy during heavy traffic hours.

Find the Right Automated Testing Software
Ultimately, choosing the right test solution is going to mean paring down to the test results, test cases, and test scripts that you need. Automated tools make it easier to complete specific tasks. It is up to your organization to first model the data it has and identify the results that it needs before it can determine which automated testing tool will yield the best results.
Many companies may need to use multiple automated products, with some being used for user experience, others for data validation. Others are used as an all-purpose repetitive testing tool. There are free trials available for many of the products listed above. Testee each solution and see how it fits into its existing workflow and development pipeline.
Recent Posts
Choose the Best Cloud Service Provider: 12 Things to Know!
Choosing a cloud service provider is without question more involved than choosing the first result from a Google search. Each business has different requirements, customizations, and financial responsibilities.
It is crucial for the perfect service to meet and exceed businesses expectations.
That said; what does a business need to look for when searching for a cloud service?
The use of cloud and cloud services differ from one client to the next. Finding the right vendor will always vary though there are similar categories to narrow down what your business requires.
Below is a handy guide to help you navigate the plethora of options available to you and your business within the cloud server hosting industry.

Is the Cloud Server User Interface Actually Usable?
The user interface does not often receive the attention it should. An efficient and user-friendly interface goes a long way to allow more people to work on server-based tasks.
In the past, these seemingly trivial actions could require a full IT department to manage.
Amazon Direct Connect (AWS), for example, uses a somewhat cumbersome user interface. This could make it difficult for a business to perform medial tasks without a dedicated IT team. The point of a simple and effective UI is that you as a company need to access your data at all times.
A business needs to be able to access its internal and client data from anywhere; that is the beauty of the cloud. Having a simple UI allows for access from virtually anywhere, at all times, from varying devices just by logging in through the service provider’s client portal. Since it is web-based, using a smartphone, a laptop, or a tablet should not pose a problem.
How Does a Service Level Agreement (SLA) Work?
Cloud service agreements can often appear complicated and aren’t helped by a lack of industry standards for how they are constructed or defined. For SLAs in particular, many providers turn what could be a simple or straightforward agreement into an unnecessarily complicated, or worse, deliberately misleading language.
Having the technical proficiency and knowledge of terms can help decipher much of the complicated information, though it is often more reasonable to partner with a provider that offers transparency.
Most SLAs are split into two groups. The first is a conventional set of terms and conditions. This is a standard document provided to every applicant with the service provider. These types of forms are usually available online and agreed upon digitally.
The next part of the agreement is a customized contract between the client and vendor. Willingness to offer specific customization depends on each provider and should be part of the decision-making process of choosing the ideal solution.
The majority of these customizable SLA’s are for large, enterprise contracts. There are times when a smaller business may attempt to negotiate exclusive agreements and built-in provisions within their contract.
Regularly challenge service providers that appear prepared to offer flexible terms. Ask them to provide details on how they plan to support any requested customization, who is responsible for this modification and what are the steps in place used to administer this variation. Always remember your main components to cover in an SLA; service level objectives, remediation policies and penalties/incentives related to these objectives, and any exclusions or caveats.

Documentation, Provisioning and Account Set-Up
Service level agreement best practices and other contracts are often broken down into four different points of interest (with additional sub-sections as needed for customization). These four points of interest are legal protections, service delivery, business terms, and data assurance.
The legal protections portion of the SLA should cover Limitation of liability, Warranties, Indemnification, and Intellectual property rights. Customers are often wary of offering up too much information to avoid any potential for exposure if there were ever a breach, while the vendor would want to limit their liability if there were ever a claim.
Service delivery often varies depending on the size of the cloud computing service provider. The rule of thumb is to always look for a precise definition of all services and deliverables. Make sure you are crystal clear on all of the service company’s responsibilities relating to their offered services (service management, provisioning, delivery, monitoring, support, escalations, etc.).
The business terms will include points around publicity, insurance policies, specific business policies, operational reviews, fees, and commercial terms.
Within the business terms, specifics with regards to the contract need to include how, or to what extent, the service provider can unilaterally change the terms of the service or contract.
To prevent abrupt increases in billing, it is crucial that the SLA be adhered to, without changes during the course of an agreed upon terms.
The last point of emphasis is data policies and protection. The data assurance portion of an SLA will include detailed information covering data management, data conversion, data security, and ownership and use rights. It is essential to think long-term with any cloud storage provider and review data conversion policies to understand how transferable data may be if you decide to leave.
Reliability and Performance Metrics To Look For
There are numerous techniques for measuring the reliability of cloud server solutions.
First, validate the performance of the cloud infrastructure provider to their SLA’s for the last 6-12 months. Often, a service provider will publish this information publicly, but others should supply it if asked.
Here’s the thing though: don’t expect complete perfection. Server downtime is to be expected, and no solution will have a perfect record.
For more information on acceptable levels of downtime, research details on differentiating Data Center Tiers 1, 2, 3 & 4. What’s valuable about these reports is how the company responded to the downtown. Also, verify that all of the monitoring and reporting tools work with your existing management and reporting systems.
Accurate and detailed reporting on the reliability of the network provides a valuable window into what to expect when working with the service providers.
Confirm with the provider that they have an established, documented, and proven process for handling any planned and unplanned downtime. They should have documentation and procedures in place on their communication practices with customers during an outage. It is best that these processes include timelines, threat level assessments, and overall prioritization.
Ensure to have all documentation covered for all remedies and liability limitations offered when issues arise.
Is Disaster Recovery Important?
Beyond network reliability, a client needs to consider the cloud disaster recovery services protocols with individual vendors.
These days, data centers work to build their facilities in as disaster-free locations as possible, mitigating the risk of natural catastrophes at all possibilities. However, problems can still arise, and expectations have to be set in case something goes wrong. These expectations can include backup and redundancy protocols, restoration, data sources scheduling, and integrity checks (to name a few).
The disaster recovery protocol also needs to include what roles both client and service provider are responsible for. All roles and responsibilities for any escalation process must be documented as your company may be the ones to implement some of these processes.
Additional risk insurance is always a smart idea to help cover the potential costs associated with data recovery (when aspects of recovery fall under the jurisdiction of the client).

What Should I Know About Data Security?
Protecting data preserves a business and its clients from data theft. Securing data in the cloud affects both the direct client and those the client conducts business with.
Validate the cloud vendor’s different levels of systems and data security measures. Also, look into the capabilities of the security operations and security governance processes. The provider’s security controls should support your policies and procedures for security.
It is always a smart option to ask for the provider’s internal security audit reports, as well as incident reports and evidence of remedial actions for any issues that may have occurred.
Network Infrastructure and Data Center Location
The location of a data center for a service provider is crucial as it will dramatically affect many factors.
As mentioned previously, having a location where natural disasters are rare is always desirable. These areas are often remote enough that the cost of services can be lower than in a robust urban area.
Location of the data center also affects network latency. The closer a business location to the data center, the lower the latency and the faster data reaches the client. Therefore, a company based in Los Angeles will receive its data from a Phoenix-based data center faster than a data center located in Amsterdam.
For businesses that require more of a global presence, utilizing data centers around the world for distribution and redundancy is always an option. When looking for your ideal provider, it is worth inquiring how many locations globally they offer.

What If I Need Tech Support?
Tech support can be the bane of existence and the cause for insurmountable levels of frustration if not cohesive with the provider. Making sure that the provider you are looking for has reliable, actionable, and efficient support is essential.
If an issue arises, the longer a problem festers, the higher the risk of security threats or worse: a damaged reputation. Clients may become frustrated with a business if they are unable to access their accounts or contact the company. This could wreak havoc on many levels if issues are not resolved quickly.
Some data centers and service providers offer tailored resources to technical problems that could go as far to include 24/7 on-call service.
Tech support is a vital part of the selection process for a CSP. You want to feel at ease with your data and services, and a reliable support system is critical.
Business Health of Service Provider
Technical, logistical, and securities aside, it is essential to take a look at the operational capabilities of cloud service providers
. It is crucial to research your final CSP options’ financial health, reputation, and overall profile.
It is necessary to perform due diligence to validate that the service provider is in a healthy financial position and responsible enough to maintain business through the agreed-upon service term. If the provider were to run into financial troubles during your term, it could cause unrecoverable damage to your company.
Research if the provider has any past or current legal problems by researching and requesting data from the company. Asking about potential changes within the corporate structure (such as acquisitions or mergers) is another point of helpful info. Remember, this does not have to be a doom and gloom conversation. An acquisition could benefit the services and support you are offered down the line.
The background of major decision-makers within the cloud computing providers can be a useful roadmap for identifying trends and future potential issues.
Certifications and Standards
When searching for a cloud service provider, it’s always wise to validate the current best practices and technological understanding that they represent.
One way to do this is to see what certifications a provider has earned and how often they renew. This shows not only how up-to-date they are, how detail oriented a provider is, but also how in tune with industry standards they are. While these criteria may not determine which service provider you choose, they can be beneficial in shortlisting potential suppliers.
There are many different standards and certifications that a service provider can acquire. It depends entirely on the organization, the levels of security, the other clientele that a vendor works with, and numerous other conditions. Some standards to become familiar with in your search are DMTF, ETSI, ISO, Open Grid Forum, GICTV, SNIA, Open Cloud Consortium, Cloud Standards Customer Council, NLST, OASIS, IEEE, and IETF.
More than just a lengthy repertoire of certifications, you want to keep an eye out for structured processes, strong knowledge management, effective data control, and service status visibility. It is also worth researching how the service intends on staying current with new certifications and technology expansion.
Cloud security standards exist on a separate facet and certifications are awarded by different organizations. The primary criteria for security include the CSA (CS-A, SSAE, PCI, IEC, ICO, COBIT, HIPAA, Cyber Essentials, ISAE 3402, COBIT and GDPR.
Operational standards are a third category to consider and to seek out certification. These certifications include ISO, ITIL, IFPUG, CIF, DMTV, COBIT, TOGAF 9, MOF, TM Forum and FitSM.
Cloud and secure data storage solutions should be proud of their earned certifications and display them on their website. If certification badges are not present, inquiring about current certifications is easy enough.
Service Dependencies and Partnerships
Service providers often rely on different vendors for hardware and services. It is necessary to consider the various vendors and how each impacts a company’s cloud and data server experience.
Validating the provider’s relationships with vendors is essential. Also keeping an eye on their accreditation levels and technical capabilities are useful practices.
Think about whether the services of these vendors fit into a broader ecosystem of other services that might complement or support it. Some of the vendors may connect easier with IaaS, SaaS or PaaS cloud services. There could be some overlap or pre-configured in services that your business could see as a benefit.
Knowing the partnerships a provider has and whether it uses one, or several of the three cloud service models is helpful. It illustrates whether the service partner is the best fit for the ultimate goals of the business.

IT Cloud Services Migration Support and Exit Planning
When searching for your ideal partner, take care to look at the long-term strategy.
In the event you ever decide to move your services or grow too large for the service capabilities of a provider. The last thing you want to run into is a scenario called Vendor Lock-In. This is a situation in which you, as a potential customer, using a product or service cannot easily transition to a competitor. This circumstance often arises when proprietary technologies are used by a provider that end up being incompatible with other providers.
There are specific terms to keep an eye out for when comparing build apps and data centers. Some examples of CSPs using vendor lock-in technology includes:
-
- CSP compatible application architecture
- Proprietary secure cloud management tools
- Customized geographic diversity
- Proprietary cloud API’s
- Personalized cloud Web services (e.g., Database)
- Premium configurations
- Custom configurations
- Data controls and applications access
- Secure data formats (not standardized)
- Service density with one provider
Choosing a provider with standard services without relying on tailor crafted systems will reduce long-term pain points and help to avoid vendor lock-in.
Always remember to have a clear cloud migration strategy planned out even before the beginning of your relationship. Transitioning to a new provider is not always a smooth or seamless transition, so it is worth finding out about their processes before signing a contract.
Furthermore, consider how you will access your data, what state it will be in, and for how long the provider will keep it after you have moved on.
Takeaways On Cloud-Based Computing Vendors
Deciding between business cloud server providers seems like a daunting task.
With the right strategy and talking points, a business can find the right solution for a service provider in no time.
Remember to think long-term to avoid any potential for data center lock-in. Avoid the use of proprietary technologies and a build a defined exit strategy to prevent any possible headaches down the line.
Spend the time necessary to build workable and executable SLAs with contractual terms. A detailed SLA is the primary form of assurance you have that the services will be delivered and supported as agreed.
With the right research and remaining vigilant for what your business requires, finding the perfect solution is possible for everyone.
Recent Posts
Speed Up WordPress: 25 Performance and Optimization Tips
Nearly 30% of the entire internet runs on WordPress.
WordPress performance issues are well known.
The fact is, you have seconds, if not fractions of a second, to convince users to stay on a web page.
When a webpage’s loading time increases from just 1 to 3 seconds, the probability of the user leaving a site rises by 32%. If you stretch the load time to 5 seconds, bounces increase dramatically to 90%.
In addition to the effect on user experience and visitor retention, site speed impacts site placement in search engines.
Google has made it clear that it provides preferential treatment to sites that loads faster. All other factors being equal if your site is faster than your competitor’s, Google will favor you in the rankings.
The primary culprits include:
-
-
- Executing numerous scripts
- Downloading graphics and other embedded elements
- Repeated HTTP requests to the server
- Pulling information from the WordPress database
-
Here are 25 tips that answer the question, how to speed up WordPress and stop losing potential customers.
1. Choose a High-Quality Wordpress Hosting Provider
If your website is on shared web hosting with potentially hundreds of other sites competing for the same resources, you may notice frustrating site speed.
For smaller sites, shared web hosting can be completely acceptable, provided it is hosted by a reputable provider that includes sufficient memory.
Once you start hitting roughly 30k monthly visitors and above, consider moving to a dedicated server or at the very least, a virtual private server (VPS). Both of these prevent a “bad neighbor” from hogging all of the shared resources. Experts also recommend looking for a server that is physically located close to your target audience. The less distance your data has to travel, the quicker it will arrive.
Many hosting companies are offering shared WordPress hosting packages. These often provide lower storage options but with faster and more dedicated hardware packages. Even better, a managed server hosting solution is often cheaper and more inclusive than other available options.
2. Apply WordPress Updates Promptly
To any security professional, applying updates quickly seems like a no-brainer. However, in practice, roughly 40 percent of WordPress sites are running the latest version. Software updates often include speed tweaks in addition to security improvements, so be sure to update ASAP.
Updates also apply to WordPress Security plugins as well. Some may say they are even more critical to maintain as they are often the driving force for speed bottlenecks and security vulnerabilities. It is recommended to check daily for available updates.
3. Avoid Bloated Themes
Choose a WordPress theme with speed in mind. It does not mean you have to opt for a bare-bones site, but don’t go for an “everything but the kitchen sink” theme either. Many commercial WordPress themes come packed with features that don’t get used. Those features, stored on the server in an idle state can create a drag on performance.
The default Twenty Fifteen, for example, offers plenty of functionality, including mobile first, while remaining streamlined and trim. Look for a WordPress theme that provides what you need and only what you need.
4. Use a Caching Plugin
Caching your site can dramatically speed up your website and is among the most critical fixes on this list.
With a caching plugin, copies of previously generated pages are stored in memory where they can be quickly retrieved the next time they are needed. Caching a webpage is much faster than querying the WordPress database multiple times and loading from the source. It is also more resource friendly.
Caching plugins are smart enough to refresh the cached copy if the content of the page is updated. Recommended caching plugins to speed up WordPress include WP Super Cache (free), W3 Total Cache (free), and WP Rocket (paid, but the fastest in tests).

5. Optimize Images
Ensure that images are in an appropriate format (PNG or GIF for graphics, JPEG for photos) and no larger than they need to be. This is one of the easiest ways to speed up WordPress.
Compress them to make images smaller so they will download quicker for the end-user. You can do this manually before you upload images or automate the process with a plugin such as WP Smush. With WP-Smush, any images you upload to your WordPress site will automatically be compressed.
Be aware of higher resolution screens when optimizing your images. Utilize @2x (and variations) code if you intend to direct the highest resolution images for specific devices.
6. Consider a CDN
A content delivery network, or CDN, is a geographically distributed group of servers that work together to deliver content quickly. Copies of your static website content are cached in the CDN. Static content includes things like images, stylesheets, and JavaScript files.
When a user’s browser calls for a particular piece of content, it is loaded from the closest node of the CDN. For example: if the user is in the UK, and your website is hosted in the U.S. the data does not need to transit the Atlantic to reach the user. Instead, it is served up by a nearby CDN node.
For high-traffic sites, a CDN offers additional benefits. Without a CDN, all of your pages are served from a single location, placing the full load on a single server. With a CDN, server load is distributed across multiple sites other than your own. A CDN can also help protect from security threats such as distributed denial of service (DDoS) attacks.
A CDN is not a WordPress hosting service. It is a separate service that can be used to leverage performance. Cloudflare is a popular choice for small websites because it offers a free version. StackPath (formerly MaxCDN) isn’t free (it starts at $9/month) but features a beginner-friendly control panel and interfaces with most popular WordPress caching plugins.
7. Configure Lazy Loading
Why spend valuable bandwidth (and time) loading images that your visitor cannot see?
Lazy loading forces only images that are “above the fold” (before a user needs to scroll) to load immediately and delays the rest until the user scrolls down.
Lazy loading is especially valuable if a page contains multiple images or videos that can slow down your site. As with many WordPress speed boosters, there are plugins for this.
The most popular include BJ Lazy Load and Lazy Load by WP Rocket.

8. Best WordPress Speed Plugins
Your WordPress database stores all of your website content. That includes blog posts, revisions, pages, comments, and custom posts such as form content.
It is also where themes and plugins track their data and settings. As your site grows, so does the database, and so does the amount of overhead required by each table in the database. As the size and overhead increase, the database becomes less efficient. Optimizing it from time to time can alleviate this problem. Think of it like defragmenting a hard drive.
You can optimize your database through your hosting control panel’s SQL WordPress database tool. For many, this is phpMyAdmin.
If using phpMyAdmin, click the box to select all tables in the database. Then at the bottom of the screen choose “optimize table” from the drop-down menu.
Alternatively, you can install a plugin such as WP-Optimize or WP-DB Manager. The plugins have the advantage that they will remove additional, unneeded items in addition to optimizing the remaining data.
Why waste time and space storing things like trashed or unapproved comments and stale data?
9. Give Your Plugins a Checkup
Every plugin you add to your site adds extra code. Many add more than that because they can load resources from other domains. A lousy plugin might load 12 external files while an optimized one settles for one or two.
When selecting plugins, only choose those offered by established developers and that are recommended by trusted sources. If you are searching for plugins within the WordPress repository, a quick check is to see how many other people are also using the same plugin.
If you find a plugin is slowing your site, then search for another one that does the same job more efficiently.
Tools like Pingdom (look in file requests section) and GTmetrix (look at the Waterfall tab) can help you find the worst offenders.
10. Remove Unnecessary Plugins
Every plugin consumes resources and reduces site speed. Don’t leave old, unused plugins in your database. Simply, delete them to improve WordPress performance.

11. Set an Expires Header for Static Resources
An expires header is a way to tell browsers not to bother to re-fetch content that’s unlikely to be changed since the last time it was loaded. Instead of obtaining a fresh copy of the resource from your web server, the user’s browser will utilize the local copy stored on their computer, which is much quicker to retrieve.
You can do this by adding a few lines of code to your root .htaccess file as described in this handy article by GTmetrix.

It is worth noting that if you are still developing your site and potentially changing your CSS, don’t add a far-off expiration for your CSS files. Otherwise, visitors may not see the benefit from your latest CSS tweaks.
12. Disable Hotlinking
Hotlinking (a.k.a. leeching) is a form of bandwidth theft. It works like this: another webmaster directly links to content on your site (usually an image or video) from within their content. The image will be displayed on the thief’s website but loaded from yours.
Hotlinking can increase your server load and decrease your site’s performance, not to mention that it is an abysmal use of web etiquette. You can protect your site from hotlinking by blocking outside links to certain types of content, such as images, on your site.
If you have cPanel or WHM provided by your hosting service, you can always use the built-in hotlink protection tools they contain. Otherwise, if your site uses Apache web server (Linux hosting), all you need to do is add a few lines of code to your root .htaccess file.
You can choose from very key code strings that allow internal links and links from search engines such as Google. You could also add more complex rules such as to enable links from sources such as a feed service or to set up a default image to show in place of a hotlinked image.
You can choose from very key code strings that allow internal links and links from search engines such as Google. You could also add more complex rules such as to enable links from sources such as a feed service or to set up a default image to show in place of a hotlinked image.
13. Turn on GZIP
Decreasing the size of your pages is crucial to fast delivery.
GZIP is an algorithm that compresses files on the sending end and restores them on the receiving end. Enabling GZIP compression on your server can dramatically reduce page load times by reducing page sizes up to 70%.
When a browser requests a page, it checks to see if the “Content-encoding: gzip” response header exists. If so, it knows the server has GZIP enabled and content such as HTML, stylesheets, and JavaScript can be compressed. These days GZIP is enabled by default on many servers, but it is best to be sure. This free check GZIP compression tool will tell you.
If you need to turn GZIP on, the easiest way is to use a plugin such as WP Rocket. W3 Total Cache also provides a way for you to turn it on, under its performance options. If you cannot use a plugin because of permission problems or don’t want to and you are using Linux hosting, you can do it yourself by modifying your site’s root .htaccess file. This article explains how to turn on gzip using .htaccess.
14. Optimize Your Home Page for WordPress Site Speed
Your home page will create the first impression of your brand and your business. It is crucial to optimize for mobile responsiveness, a pleasing UI/UX, and most of all for speed.
Steps to take include:
-
- Remove unnecessary widgets. You do not need to display every widget everywhere.
- Don’t include sharing widgets and plugins on the homepage. Reserve them for posts.
- Restrict the number of posts on the homepage. Fewer posts equal a smaller, faster-loading.
- Use excerpts instead of full posts. Again, smaller equals quicker site speed.
- Go easy on the graphics. Images and videos take longer to load than text.

15. Host Videos Elsewhere
Rather than uploading videos as media and serving them on your site, take advantage of video services to offload the bandwidth and processing.
Make use of the second most trafficked search engine on the web and upload your videos to YouTube, or a similar service like Vimeo. Then you can copy a small bit of code and paste it into a post on your site where you want the video to appear. This is known as embedding a video. When a user views the page, the video will stream from the third-party server rather than your own. Unlike hotlinking, this is the recommended practice for media-rich content such as video.
16. Limit Post Revisions
The ability to revert to a previously saved version of a post can come in handy, but do you need to keep every copy of every post you have ever made? Probably not.
These extra copies clutter your database and add overhead, so it is best to put a cap on the number stored. You can do so by using a plugin, such as Revision Control, or you can set a limit by adding the following line to your wp-config.php file:
define( 'WP_POST_REVISIONS', 3 );
Set a number you feel comfortable with. Anything will be less than the default, which automatically stores revisions without a limit.
17. Set the Default Gravatar Image to Blank
Gravatar is a web service that allows anyone to create a profile with an associated avatar image that links automatically to his or her email address. When the user leaves a comment on a WordPress blog, their avatar is displayed alongside. If the user does not have a Gravatar image defined, WordPress displays the default Gravatar image. This means you can have dozens of comments showing the same, uninformative “mystery man” image. Why waste page load time on something that’s not very useful when you can get rid of it?
Changing the default Gravatar image is easy. In your WordPress Admin dashboard, go to Settings > Discussion. Scroll to the Avatars section. Select Blank as the default Avatar. Mission accomplished.
18. Disable Pingbacks and Trackbacks
When Pingbacks and Trackbacks were implemented, they were intended to be a vehicle for sharing credit and referring to related content. In practice, they are mainly a vehicle for spam. Every ping/track you receive adds entries (i.e., more data) to your database.
Since they’re rarely used for anything beyond obtaining a link from your site to the spammer’s, consider disabling them entirely. To do so, go to Settings > Discussion. Under default article settings, uncheck the line that says “Allow link notifications from other blogs (pingbacks and trackbacks).” Note that this will disable ping/tracks going forward, but won’t apply retroactively to existing posts.

19. Break Comments into Pages
Getting loads of comments on your blog is a great thing, but it can slow down overall page load. To eliminate this potential problem, go to Settings > Discussion and check the box next to the “Break comments into pages” option. You can then specify how many comments you would like per page and whether to display the newest or oldest first.
20. Get Rid of Sliders
Whether or not sliders look great is a matter of opinion. But the fact that they will slow down your WordPress website is not.
Sliders add extra JavaScript that takes time to load and reduce conversion rates.
They also push your main content down the page, perhaps out of site. Why take a performance hit for something that only serves as ineffective eye candy?
21. Move Scripts to the Footer
JavaScript is a nifty scripting language that lets you do all kinds of exciting things. It also takes time to load the scripts that make the magic happen. When scripts are in the footer, they will still have to load, but they will not hold up the rest of the page in the process. Be aware that sometimes scripts have to load in a particular order, so keep the same order if you move them.
22. Combine Buttons and Icons into CSS Sprites
A sprite is a large image that’s made up of a bunch of smaller images. With CSS sprites, you load the sprite image and then position it to show the portion you wish to display.
That way only one HTTP request for the image results, instead of individual requests for each component image.
23. Minify JavaScript and CSS
Minification is the process of making certain files smaller, so they transmit more quickly. It is accomplished by stripping out white spaces, line breaks, and unnecessary characters from source code.
Better WordPress Minify is a popular minify plugin. It offers many customization options. Start by checking the first two general options.
Those two specify that JavaScript and CSS files should be minified. The plugin works by creating new, minified copies of the original files. The originals are left in place, so you can quickly revert to them if desired.

24. Avoid Landing Page Redirects
WordPress is pretty smart about many things, and redirects are one of them. If a visitor types http://yourdomain.com/greatarticle.html into their browser, and you have your site set up to use the www prefix, the visitor will automatically be redirected to the correct page (with the www prefix added), http://www.yourdomain.com/greatarticle.html.
What if the user types in https:// instead of http://? They will likely still arrive at the desired page, but there may be another redirect as HTTPS converts to HTTP, and then that is redirected to the www URL. More time spent waiting for the target page to load.
Redirects are handy for landing your visitor on the right page, but they take time, delaying loading. Therefore, you should avoid them when possible. When linking to a page on your site, be sure to use the correct, non-redirected version of the URL. Also, your server should be configured so that users can reach any URL with no more than one redirection, no matter which combination of HTTP/HTTPS or www is used.
To check out the status of redirections currently employed by your site, try a few URLs in this Redirect mapper. If you see more than one redirect, then you will need to modify your server to ensure visitors get to the right place more quickly.
If your site is hosted on Linux, you can accomplish this by adding URL rewrite rules to your .htaccess file. For other hosting platforms, check your dashboard to see if there’s an option to configure redirection. If not, contact technical support and ask them to fix it for you.
25. Replace PHP with static HTML
PHP is a fast-executing language, but it is not as speedy as static HTML. Chances are your theme is executing a half-dozen PHP statements in the header that can be swapped out for static HTML. If you view your header file (Presentation > Theme Editor) you will see many lines that look similar to this:
The part in bold is PHP that gets executed every time your page loads. While this takes up minimal time, it is slower than straight HTML.
If you’re determined to make your website as speedy as possible, you can swap out the PHP for text. To see what you to replace the PHP with, use the View Source option while looking at your web page (right click > view source).
You will see something like this:
The bold area is the text that resulted from the processed PHP code. Replace the original PHP call with this code. If you do so for the main PHP calls in the header alone, you can save at least six calls to PHP. If you use different titles or article titles on separate pages for SEO purposes, don’t change out the PHP in the first line. Check your footer and sidebar for additional opportunities to switch out PHP for text.

Site Speed Putting it All Together: WordPress Optimization
By now, you should have a firm grasp on how to speed up your WordPress site.
You should be able to understand the importance of a responsive site that is focused on performance and speed to gain the attention of your users quickly.
Chances are, as you navigated this guide, you discovered that your website had plenty of room for improvement.
Once you apply the tips above, rerun a WordPress website speed test through Google’s TestMySite and Page Speed Insights.
You should be pleasantly surprised by the improved speed. Remember to monitor Google Analytics data to see how many more visitors you receive and the length of time spent on your pages. This should be an ongoing tool to monitor the effectiveness of your optimizations.
Keep in mind that speed is essential, but it is not everything. You could cut out all images, videos, and plugins and employ a bare-bones theme to achieve a blazing fast loading time, but your site might end up boring.
Instead, balance speed with appearance and function, with an emphasis on the speed end of the equation. Your customers will notice. You can count on it. Now you are ready to speed up your WordPress website!
Recent Posts
Cloud vs Dedicated Server: Which Is Best For Your Business?
Your business has a website. Your company might, in fact, be that website. That site needs to be hosted somewhere that has reliable uptime, doesn’t cost a fortune, and loads lightning fast.
Picking the perfect web host has many implications for a business that are far reaching. One constant does remain: every company needs a website and a fast server to host it on.
Even a one-second difference in page response can cost a company 7% of its customers.
In July 2018, Google will be updating their algorithm to including page speed as a ranking factor. Consider the implications if consumers are leaving your pages due to load time and your rankings are suffering.
Load-time is just one of many examples of the importance of web hosting, and its impacts on the company bottom line. The web host a company chooses is vitally important.
To understand the importance of web hosting servers, let’s break down the difference in the two major types of offered services: cloud hosting and dedicated servers.
Both have their advantages and disadvantages that may become more relevant to a company that is on a budget, facing time constraints or looking to expand. Here are the definitions and differences that you need to know.
The Cloud Ecosystem
The cloud is a technology that allows an infinite number of servers to act as a single entity. When information is stored “in the cloud,” it means that it is being held in a virtual space that can draw resources from different physical hubs strategically located around the world.
These hubs are actual servers, often in data center facilities, that connect through their ability to share resources in virtual space. This is the cloud.
Cloud servers use clustered filesystems such as Ceph or a large Storage Area Network (SAN) to allocate storage resources. Hosted and virtual machine data are accommodated through decentralization. In the event of a failure, this environment can easily migrate its state.
A hypervisor is also installed to handle how different sizes of cloud servers are partitioned. It also manages the allocation of physical resources to each cloud server including processor cores, RAM and storage space.

Dedicated Hosting Environment
The dedicated server hosting ecosystem does not make use of virtual technology. All resources are based on the capabilities and limitations of a single piece of physical hardware.
The term ‘dedicated’ comes from the fact that it is isolated from any other virtual space around it based on hardware. The hardware is built specifically to provide industry-leading performance, speed, durability and most importantly, reliability.
What is a Cloud Server and How Does it Work?
In simple terms, cloud server hosting is a virtualized hosting platform.
Hardware known as bare metal servers provide the base level support for many cloud servers. A public cloud is made up of multiple bare metal servers, usually kept in a secure colocation data center. Each of these physical servers plays host to numerous virtual servers.
A virtual server can be created in a matter of seconds, quite literally. It can also be dismissed as quickly when it is no longer needed. Sending resources to a virtual server is a simple matter as well, requiring no in-depth hardware modifications. Flexibility is one of the primary advantages of cloud hosting, and it is a characteristic that is essential to the idea of the cloud server.
Within a single cloud, there can be multiple web servers providing resources to the same virtual space. Although each physical unit may be a bare metal server, the virtual space is what clients are paying for and ultimately using. Clients do not access the operating system of any of the base units.
What is Dedicated Server Hosting?
Dedicated hosting has the potential to have just a single client on a physical server.
All of the resources of that server are available to that specific client that rents or buys the physical hardware. Resources are customized to the needs of the client, including storage, RAM, bandwidth load, and type of processor. Dedicated hosting servers are the most powerful machines on the market and often contain multiple processors.
A single client may require a cluster of servers. This cluster is known as a “private cloud.”
The cluster is built on virtual technology, with the many dedicated servers all contributing to a single virtual location. The resources that are in the virtual space are only available to one client, however.
Mixing Cloud and Dedicated Servers – the Hybrid Cloud
An increasingly popular configuration that many companies are using is called a hybrid cloud. A hybrid cloud uses dedicated and cloud hosting solutions. A hybrid may also mix private and public cloud servers with colocated servers. This configuration allows for multiple variations on the customization side which is attractive to businesses that have specific needs or budgetary constraints.
One of the most popular hybrid cloud configurations is to use dedicated servers for back-end applications. The power of these servers creates the most robust environment for data storage and movement. The front-end is hosted on cloud servers. This configuration works well for Software as a Service (SaaS) applications, which require flexibility and scalability depending on customer-facing metrics.
Cloud Servers and Dedicated Servers – the Similarities
At their core, both dedicated and cloud servers perform the same necessary actions. Both solutions can conduct the following applications:
- store information
- receive requests for that information
- process requests for information
- return information to the user who requested it.
Cloud servers and dedicated servers also maintain differences from shared hosting or Virtual Private Server (VPS) hosting. Due to the increasing sophistication structure of cloud and dedicated solutions, they outpace shared/VPS solutions in the following areas:
- Processing large amounts of traffic without lag or performance hiccups.
- Receiving, processing and returning information to users with industry standard response times.
- Protecting the fidelity of the data stored.
- Ensuring the stability of web applications.
The current generation of cloud hosting solutions and dedicated servers have the general ability to support nearly any service or application. They can be managed using similar back-end tools, and both solutions can run on similar software. The difference is in the performance.
Matching the proper solution to an application can save businesses money, improve scalability and flexibility, and help maximize resource utilization.
The Difference Between Dedicated Servers and Cloud Computing
The differences between cloud hosting and dedicated servers become most apparent when comparing performance, scalability, migration, administration, operations, and pricing.

Performance
Dedicated servers are usually the most desired choice for a company that is looking for fast processing and retrieval of information. Since they process data locally, they do not experience a great deal of lag when performing these functions.
This performance speed is especially important in industries where every 1/10th of a second counts, such as ecommerce.
Cloud servers must go through the SAN to access data, which takes the process through the back end of the infrastructure. The request must also route through the hypervisor. This extra processing adds a certain level of latency that cannot be reduced.
Processors in dedicated servers are entirely devoted to the host website or application. Unless all of the processing power is used at once (which is highly unlikely), they do not need to queue requests. This makes dedicated servers an excellent choice for companies with CPU intensive load balancing functions. In a cloud environment, processor cores require management to keep performance from degrading. The current generation of hypervisors cannot manage requests without an added level of latency.
Dedicated servers are entirely tied to the host site or application which prevents throttling on the overall environment. Dedication of this magnitude allows networking a simple function when compared to the cloud hosting environment.
In the cloud, sharing the physical network incurs a significant risk of throttling bandwidth. If more than one tenant is using the same network simultaneously, both tenants may experience a myriad of adverse effects. Hosting providers give many cloud-based tenants the option to upgrade to a Network Interface Card (NIC).
This option is often reserved for clients who are bumping up against the maximum available bandwidth that is available on the network. NIC’s can be expensive. But companies often find they are worth the extra cost.
Scale Your Business Hosting Needs
Dedicated hosting scales differently than cloud-based servers. The physical hardware is limited by the number of Distributed Antenna System (DAS) arrays or drive-bays it has available on the server.
A dedicated server may be able to add a drive to an already open bay through an underlying Logical Volume Manager (LVM) filesystem, a RAID controller, and an associated battery. DAS arrays are more difficult to hot swap.
In contrast, cloud server storage is easily expandable (and contractible). Because the SAN is off the host, the cloud server does not have to be part of the interaction to provision more storage space. Expanding storage in the cloud environment does not incur any downtime.
Dedicated servers also take more time and resources to change processors without maintenance downtime. Websites hosted on a single server that requires additional processing capabilities require a total migration or networking with another server.

Migration
Both dedicated and cloud hosting solutions can achieve seamless migration. Migration within the dedicated environment requires more planning. To perform a seamless migration, the new solution must keep both future and current growth in mind. A full-scale plan should be created.
In most cases, the old and new solutions should run concurrently until the new server is completely ready to take over. It is also advisable to maintain the older servers as a backup until the new solution can be adequately tested.
Server Management: Administration and Operations
Dedicated servers may require a company to monitor its dedicated hardware. Therefore in-house staff must understand systems administration more closely. A company will also need a deep understanding of load profile maintain data storage requirements within the proper range.
Scaling, upgrades, and maintenance is a joint effort between client and provider that must be carefully engineered to keep downtime to a minimum.
Cloud servers are more accessible to administer. Scalability is faster with much less of an impact on operations.
Where dedicated platforms require planning to estimate server requirements accurately, the cloud platforms require planning to work around the potential limitations that you may face.

Cloud vs Server Cost Comparison
Cloud servers ordinarily have a lower entry cost than dedicated servers. However, cloud servers tend to lose this advantage as a company scales and requires more resources.
There are also features that can increase the cost of both solutions.
For instance, running a cloud server through a dedicated network interface can be quite expensive.
A benefit of dedicated servers is they can be upgraded. With more memory, network cards and Non-Volatile Memory (NVMe) disks that will improve capabilities at the expense of a company’s hardware budget.
Cloud servers are typically billed on a monthly OpEx model. Physical server options usually are CapEx expenditures. They allow you to oversubscribe your resources without additional cost. You now have a capital expenditure costs that may be written off over a three year period.

Making a Choice: Cloud Servers vs Dedicated Servers
Matching the needs of your business to the configuration is the most crucial aspect of choosing between computing platforms.
This computing platform needs to complement the operating procedures, be scalable, and cost-effective. These variables are critical evaluators when selecting between a cloud or dedicated server solution.
Also, you are not able to take advantage of the new technological benefits as rapidly as you would in a cloud environment.
The value proposition for bare metal technologies is in the historical evidence that suggests most server workloads take advantage of a fraction of the actual physical resources over an extended period. By combining workloads on a single hardware platform, one can optimize the capitalized expenditure of that hardware platform. This is the model cloud service providers use to create cheaper computing resources on their platform.
A dedicated server provides access to raw performance, both processor and data storage. Depending on the computing workload, this may be necessary.
There is a place for both. Utilizing a hybrid strategy, an organization can processor-intensive workloads on dedicated systems. While also running their scalable workloads on cloud infrastructure, taking advantage of the strengths of each platform.
With the current maturity of cloud orchestration tools, and the ability to cross-connect into cloud environments, an organization can have multiple workloads in various environments. Additionally, it can run physical infrastructure that interacts with these cloud services.
Which should you choose? Selecting one over the other based on a single metric is a mistake.
Consider the following:
- The advantages of each solution.
- The current needs of your business.
- Your future scalability needs.
Have Questions?
Not sure which hosting option to choose for your business needs? Contact one of our hosting service experts.
Recent Posts
11 Enterprise Password Management Solutions For Corporate Cybersecurity
Let’s set a scene: It is a Monday morning, and you have just sat down at your office workstation after a long and relaxing weekend.
Coffee in-hand and you are ready to take on the week, only to realize you have been mysteriously locked out of all your accounts.
Did the system administrator push a password refresh? Did you accidentally knock out a LAN cable?
That pit in your stomach and sweat on your brow is how it feels when you suddenly realize your passwords have been stolen or compromised.
Who has access to your information, your accounts, your data? Even worse; how did they get through your security?
In the age of widespread identity theft, security breaches, and corporate espionage, password protection is essential to your digital security. The use of enterprise password management software is becoming a required element in any IT organization.
60% of small-to-medium size companies suffer a from cyber-attack at some point. According to the National Cyber Security Alliance, most close down only six months after an attack.
What is a Password Manager?
Password managers are designed to manage a user’s personal details securely. We all enter our information online, whether it is a bank account login, our social security number, or an e-mail password. Most users have dozens of accounts. Team members in business may have hundreds. All of them protected by usernames and their accompanying passwords.
Remembering all those details can be near-impossible – because we are all using different passwords for each account, right?
Password managers take the burden of remembering each login off the user. The majority of these services are low-cost or free, targeting, and meeting the needs of a single consumer.
They run discreetly in the background. Upon creating or using a new account for the first time, the user receives a prompt. The prompt will most often ask the user to save the password. Once collected, details are logged and held in a “vault.” The password vault manager encrypts all data.
Most managers also can recognize duplicate and weak passwords. If it registers as such, they prompt the user to either create a stronger one or to generate a stronger key randomly.
Why You Need Enterprise Password Management?
The average consumer-level password is enough for the needs of a single user. However, the enterprise world has much higher standards for security.
IT staff need a central point of collection, or a team password manager should a user lose access. Admins must also be able to manage details for shared accounts and to set and revoke permissions. Moreover, enterprise-level managers can store all kinds of data, not just login details. Some options store files of all format types.
The right software can lift much of the burden that server admins endure. Those running an IT system often deal with regular interruptions. Members of the team forget passwords and a simple password reset. Corporate password managers perform many of these functions automatically.

Dangers of Leaving Password Management to Employees
Allowing users to choose their private passwords and management software can be a minefield.
One device can have access to hundreds of account passwords. Users need strong passwords for everything from Twitter to Hootsuite to LinkedIn to MailChimp, and so on. Without a firm, centralized approach to password storage and security, users must find their own means.
Allowing users to decide how to implement password protocol can also be dangerous.
In many cases, team members will use insecure methods such as using .doc files, Excel spreadsheets, or even a post-it note on the front of their screen to store details. The risk of having passwords stolen from such unprotected mediums is much higher than using the right software.
Other employees may instead choose to use their own personal software. Management may see this as a way to ensure protection without added cost.
Single users do not have access management to group passwords, however. Nor do they always set standards for passwords that match company protocol. In the future, they could leave the company with corporate login details still in their accounts. Naturally, these are valid security concerns. Best practices are critical.
Enterprise Software Features to Look For In a Password Management Solution
Enterprise software enables the separation of personal, single-use accounts and shared details.
One of the best features of enterprise password managers is access to central dashboards. These dashboards allow security officers to check user activity and aggregate data. Many include visualization tools that make it easier to monitor behavior and security practices.
Studying user habits can help reinforce and improve your companies password practices.

Let’s look at the best password management software for an enterprise on the market.
We will highlight criteria to help you better judge different platforms. These include what operating systems and hardware the software is compatible with, price, security, features, and ease-of-use.
LastPass Enterprise
A premium edition for businesses based on the well known free software. LastPass lets the user generate and store any number of logins in a master vault. Multi-factor or two-factor authentication limits access to the vault.
Besides passwords, the vault offers protection of additional text notes. Secure data syncing allows users to retain the same credentials and security between different platforms. Users can access the vault on any device through the developer’s website.
LastPass also uses a growing database of phishing websites. By highlighting such, users are less likely to leak access to privileged accounts. Admins can also export encrypted data. Exporting makes it easy to switch to another software option down the line if you choose to.
The premium edition offers further cloud protection for all kinds of files. The contingency access feature lets a team member use your account when you are unable to. Without additional support for shared accounts, however, LastPass might not be best suited to large teams.
Dashlane
Dashlane offers many of the same features as LastPass with its enterprise edition. Team account management software is now available on an accessible browser window interface. Some may prefer the downloadable software package, which is equally easy to use.
Active Directory integration makes it easy to share Dashlane through your business network. One of the better resources offered is the bulk password changer. This feature allows you to quickly change large amounts of data in the event of a breach.
Conversely, Dashlane is high in price compared to some of the other solutions here. It may not be an option every business can afford. This edition includes unlimited sharing and syncing between teams and devices. It was rated as the most secure password manager.
Keeper Security
A mobile-centric alternative to other platforms, Keeper Security for Business, operates on a wide range of platforms with a particular focus on responsive design. Like LastPass and Dashlane, it offers a secure vault that stores all kinds of files, not just passwords.
One of the benefits of Keeper Security is the vast range of platforms it works across. The software has versions for Android, iOS, Blackberry, Kindle, iPad, Windows, Mac, and Linux. The centralized vault allows access management to the same credentials across all platforms.
Keeper Security comes with Active Directory integration and an admin control panel. Amongst other features, the panel allows for the fast provisioning of users. Access to specific passwords is easily distributed and revoked.

Centrify Enterprise
This option contains many of the same features you can come to expect from most password managers. These features include autofill, password capture, and password generation. Centrify is one of the most useful tools for capturing and monitoring data cross accounts, too.
Centrify tracks a lot of user data. Data tracking includes logs of the number of attempted logins, valid log-ins, and unusual activity.
Admins can generate reports on each user session. The summary collates all data of activity across a whole enterprise. Centrify has the further ability to separate reports based on different roles. This makes it a worthwhile tool for inspecting security practices company-wide.
CommonKey | Team Password Manager
CommonKey is an affordable solution for smaller businesses. It focuses on password protection alone, lacking the secure data storage features available elsewhere. Shared accounts and user provisioning tools are also included.
It is limited by the platforms you can use it on. CommonKey runs as a Chrome security extension. As a result, it’s only useful when used with websites and services. Passwords for local software cannot be saved.
The local encryption used by the application could be a risk, too. Certain breaches could allow hackers to see encryption methods and break them. Effectively, such a leak would expose all your details.
Larger businesses with more robust password needs may want to search for alternatives. For smaller teams that rely on websites and web applications, however, it can be a reliable tool.
RoboForm For Business
RoboForm for Business allows for centralized protection of an entire team. It includes a site license that stores and manages all passwords used in the company.
RoboForm includes secure provisioning of shared passwords. An admin console allows for easy management of different users.
You can manage users as individuals or as members of role-based groups. Role-grouping saves a lot of time when dealing with larger departments. Advanced reporting allows admins to ensure that users comply with company policy, too.
Pleasant Password Server
One of the few open-source password managers on the market. Pleasant password server lets tech-savvy users fully customize their approach to improve password security. Like many enterprise editions, it includes active directory integration.
Unlike other managers, the encryption and storage of sensitive data do not happen locally. Passwords stored on the client are kept safe in the event of a local data breach.
A refined folder system allows for simple grouping of large amounts of data. Admins can use this data to create reports that work with shared accounts and role-based management. It can generate reports including evaluating password age, strength, expiration, and more.

BeyondTrust
BeyondTrust Privileged Password Management includes powerful data tools on top of the standard features. Session-logging and auditing offer greater monitoring of security practices across the team.
Active Directory and LDAP integration enable the automatic provisioning of users. The management features work with local appliances using government-level security. It’s not just a tool for websites and web applications.
BeyondTrust has one of the most complex and detailed reporting modules on the market. Included, is the ability to track login attempts and session activity across the whole team. In the event of a breach attempt, you can use these reports to ensure regulatory compliance.
ManageEngine
One of the most popular enterprise-level password security programs. The pro password management of ManageEngine includes options to enable multiple admins. Using this option does increase the price of the package, however.
Data sync and Active Directory integration streamline management of multiple accounts. While it doesn’t work with mobile devices, it does include further forensic tools. Chief amongst them is the compliance report generation feature and video logs of sessions. This makes it one of the best tools for inspecting the security practices of your team members.
ZohoVault Online Password Manager For Teams
This software works solely with mobile devices. It sounds limiting, but ZohoVault does bring a surprising depth of features to its platform.
Included, are administrator access and management of user groups as well as smooth password transferal. It allows for the creation of reports on user activity and even allows more in-depth provisioning tools. As well as limiting access by specific users, admins can restrict access by IP address. If your concerned team members use unauthorized devices to access passwords, you can block them.
Zoho works as more than a standalone centralized manager for mobile devices. It also integrates with other password managers like LastPass. A company can use Zoho to extend existing enterprise password management to mobile devices effectively. On top of that, this is one of the cheapest solutions on the list.
1Password Business
Popular consumer software, 1Password from AgileBits may not be full enterprise at the moment, but they are one to keep on your radar. Recently, they expanded their popular subscription-based service for larger teams (replacing the existing, Teams Pro service).
1Password Business provides the features you need as a larger team. It gives you the tools to protect your employees, secure your most important data, and stay compliant. Your administrators will love it for the control it provides them, and your employees will love how easy it is to use,” writes AgileBits in an introductory blog for the product.
AgileBits introduced subscription pricing in 2016, moving away from licensed-based pricing. This may be a deterrent for some businesses, though depending on the size of your company, it could end up being more cost-effective in the long-run.
While 1Password is still geared toward smaller businesses or group users, the new Business plan offers enhanced customer support; more per person document storage; and a more significant number of guest accounts. Worth keeping an eye on in your consideration process.

Choosing the Best Enterprise Password Solution
Unauthorized use of passwords is the most common method of entry in recent data breaches.
All of the options listed above have a reputation for high-security standards. Do not forget, the centralization of your password management is crucial. The solution you choose depends on the needs of your organization.
Recent Posts
Compliance Guide to GDPR, The General Data Protection Regulation
We are at a strange intersection in the ‘GDPR Preparedness’ timeline. Some organizations are so prepared as to put the rest of us to shame. Others are so unprepared that the very mention of the letters “GDPR” is met with blank stares.
Then there is the rest of us… The ones who know what GDPR is, have some idea of what is needed by the 25th May 2018 (when the directive becomes law across the European Union), yet find themselves so overwhelmed by the scope of what they face as to feel almost paralyzed. Thus begins a series of questions:
Where does one start? For that matter, where does one finish? What exactly does ‘being GDPR compliant’ look like? Am I going to face a massive fine?
These are all common questions that are floating around the business world, and there is very little help available. The lack of advice is based on two overriding factors:
- Nobody wants to provide guidance because, if they are wrong, then they’ve potentially left themselves legally vulnerable.
- Even the so-called “experts” have not got a clue what being fully compliant means in a real-world sense.
It is a sad idiosyncrasy of GDPR that those best placed to provide the guidance we need, are also the ones most reluctant to assist. So, let us see if I can help remedy the situation and give some of the real-world advice that is sorely lacking at the moment.
Step 1 – GDPR Overview, What is it All About?
On the 24th May 2016, the European Parliament voted The General Data Protection Regulation (GDPR) into law. After publication of the regulations, a two-year countdown leading up to 25th May 2018 immediately began. On that day, GDPR becomes law throughout the entire European Union, replacing all other digital data privacy laws and provisions that came before it.
The law intends to provide a consistent set of new rules concerning the protections afforded to citizens’ data – wherever that records may reside.
It also equips its citizens with the ability to query, alter and if needed, delete the personal information that references them from any system anywhere in the world. That is right folks, if you are in Bangladesh and you process the private information of an EU citizen, that data is protected under GDPR. “Why is that?” I hear you ask.
Well, EU GDPR 2018 is one of a couple of extraterritorial laws that have been passed in the past decade that affect international trade. These laws affect all jurisdictions everywhere and are expected to be enforced by local authorities regardless of the fact that they were enacted overseas.
For example, the Foreign Account Tax Compliance Act (FATCA) was passed in 2010 and requires all non-US financial institutions to identify assets belonging to US citizens and then report those assets to the U.S. Department of the Treasury (along with the identifies of the asset holders).
GDPR regulation is similar, in that it places a burden on all organizations everywhere to identify the data of EU citizens they hold and ensure that those details can be identified, updated and, if needed, deleted upon request by those citizens.
Easy right? After all, how much personal information can there be out there? Well, as it turns out, quite a bit.
Step 2 – Identifying What Data Falls (And Does Not Fall) Under The GDPR 2018

The GDPR protects two types of data – personal data and sensitive personal data.
Sensitive Personal Data is defined as details consisting of racial or ethnic origin, sexual orientation, political opinions, religious or philosophical beliefs, trade union membership(s), genetic or biometric data and health data.
Personal Data is defined as any information relating to an identified or identifiable natural person.
Sensitive Personal Data is straightforward as definitions go. It essentially identifies some of the most private data of an individual and ensures that that information is protected at the highest levels of discretion. The definition of Personal Data is, however, far more nebulous – and this appears to be by design.
Is my name considered personal data? Yes. How about my home address? Yes.
What about my communications with 3rd parties such as emails, social media, chats and text messages? Yes, yes and yes.
What about IP Addresses or GPS data? Yes – them too. Any information that could be used to trace back to a natural person can be classified as personal data regardless of the form it takes, and this is a huge issue.
Are you aware of just how much data will be reclassified as “personal” when the GDPR comes into force?
I cannot say that I am. Moreover, I am pretty sure you cannot either. In fact, the only thing I can say with any confidence is that if anyone tells you that they have an “all-encompassing” definition of what personal data is, then they have not got a clue what they are talking about.
Most consultants we have spoken to have hedged their bets and classified almost everything as “personal data” regardless of how unrealistic their interpretation may be. The operative assumption appears to be – the EU has not made their definition clear enough to enable concrete advice to be provided. Therefore all such information will be as generic as possible in order not to be exposed to potential legal repercussions.
Organizations that fail to implement the suggested data protection measures are facing two levels of GDPR penalties. Article 83 of the GDPR text defines how administrative fines will be applied.
Essentially, the GDPR fines and penalties for a specific organization will depend on a variety of factors including the nature, gravity, and duration of the infringement, the categories of data affected, the actions taken to prevent the infringement.
The list goes on.
Step 3 – Appointing A GDPR Data Protection Officer (DPO)
Before you get started with the more technical aspects of GDPR implementation within your organization, you will need to appoint someone to spearhead your efforts in this area. That person is your DPO (Data Protection Officer). They will be the one who is ultimately responsible for the application and success of your GDPR EU strategy and will be the focal point for all issues.
At this point in most articles on GDPR, you will likely be reading some blurb about whether or not you need a DPO at all. My advice? Appoint one regardless. You will only truly appreciate the depth of the number of private records your organization stores if you turn your GDPR compliance plan into a full-blown project, and that project is going to need a leader.
Whomever you appoint is going to have a rather large task on their hands. Their responsibilities will include:
- Evangelizing GDPR key points and security awareness throughout the organization and educating staff on compliance;
- Ensuring that adequate training programs are implemented so that all staff involved in the processing of private records are prepared for GDPR and its implications;
- Conducting internal and external audits of systems and data management practices and, where necessary, prescribe remediation;
- Act as the primary point of contact and liaison between your organization and the various protection authorities in Europe;
- Ensuring that all activities conducted as part of your GDPR compliance efforts are adequately documented so that you are prepared for any potential external GDPR audit;
- Contacting data subjects as part of any access request processes you implement to ensure that they are informed about how their data is stored, managed and erased; and that they are aware of the existence of the supporting policies and procedures in place.
Step 4 – Getting Every Department On Board (The War Within)

The first thing you will notice after you have defined what personal data is, is that that data is spread out over an extensive area.
Your operations team will control some of it; your finance team will manage a whole separate part of it. Some departments will use redundant copies of it for their own purposes. And many teams will share common databases.
To form a coherent picture of your data assets and rally everyone to your banner, you are going to have to find some way of bringing order to this chaos. Your team can either view GDPR as overhead, a waste of resources, or it can choose to view it as an opportunity to bring order to a branch of data management policies and processes that your organization never had the time or the inclination to reform.
You’ll need to be measured in your approach:
- Start slowly. If you walk in with visions of doom and gloom about the possible negative consequences of not implementing GDPR reforms, you will lose potential allies. Instead, help your team view this as a chance for genuine inter-departmental co-operation on a scale that rarely occurs.
- Do not Expect Perfection. You will face fear. The kind of reluctance to act that can scupper projects. Ensure that everyone on the team knows that perfection is neither achievable nor desirable. Instead, coach your team to see GDPR as an ongoing process that provides you with a clearer view of your data assets over time. Your first steps may feel like they fall short, but they are an essential part of the process.
- Get Buy-In From The Top. If your organization is like most, then folks only move when they know that an initiative is backed at the highest levels. GDPR is no different. If your C-Level Execs are not pushing it, then nobody will follow. Get their buy-in, and all doors will open.
- Maintain A Positive Outlook. At the risk of sounding like an inspirational poster – GDPR is a journey, not a destination. It will be easy to lose drive and focus along the way. A positive approach to the task at hand will help drive people along the path and ensure a smoother ride to the 25th May deadline and beyond.
Step 5 – Finding The Data You Store And Identifying The Various Actors In Your Business

Whose personal data do you store?
If you are like most businesses, then you store records of your staff (Human Resources), your users (Sales and Operations) as well as those of your partners (Supply Chain and Support).
Each of these actors in your company typically requires different systems to store their records, and each of these systems has probably been in operation for some time. Some systems might be paper-based, some may be fully-automated (i.e., software-based) and some may be a combination of the two.
Either way, a comprehensive audit will have to be conducted to establish where the private records of each of the actors in your business is stored.
Once that exercise is complete, the real work begins.
A central tenet of the GDPR framework is consent. Essentially, this part of the GDPR legislation asks the question – On what basis, under the law, did I collect this personal data that I am storing? The GDPR provides a list of the types of justification that are considered appropriate:
- Explicit Consent – Where you are given a clear and unambiguous go-ahead by the data owner to store their records for a specific purpose.
- Contractual Obligation – Where you need the provision of personal data to fulfill your end of an agreement/contract.
- Vital Interests – Where you require the use of a natural person’s data to protect their life, and they are unable to provide explicit consent (very few organizations can claim this).
- Public Interest – Where you must use specific personal information in the exercise of an official task (even fewer organizations can claim this).
- Legitimate Interest – When you use certain personal information because you are certain that doing so would have a minimal data privacy impact, or where there is a compelling justification for the processing. You must balance your interests against the individual’s and if you could obtain their data by other, less intrusive, means then your basis for processing their records will be considered invalid (this is the most ‘legally flexible’ justification for processing data but also the one most fraught with potential pitfalls).
- Special/Criminal Interests – This information falls under the ‘sensitive personal data’ header and can only be legally processed by particular organizations.
It is pretty clear that most organizations will use Explicit Consent and Contractual Obligation as their two most common bases for consent since they are, typically, the main ways of gathering private details. However, reverse-engineering that consent weeks, months and, sometimes years, after that data was collected is going to take a lot more effort than people think.
Step 6 – Are You A Data Controller Or A Data Processor?

Once you have made an assessment and analyzed the records you use within your organization, you need to understand whether you are that data’s GDPR Controller or whether you are merely its Processor. The difference between the two will determine what your obligations are under the GDPR.
The operative difference between a GDPR Data Controller and a Data Processor is control. The GDPR text specifies that Controllers determine the “purposes and means of the processing of personal data” whereas Processors “process personal data on behalf of the Controller.” It is clear, therefore, that Controllers have far more significant responsibilities and legal obligations than Processors.
Data Controllers are the ones who acquire the data and are therefore responsible for ensuring that there was a clear basis for consent – that the data collected was the minimum amount needed for a specific purpose, that it is as accurate as possible, that it is stored as securely as possible and that it is purged or anonymized when it is no longer needed.
The Processors only use details provided by the Controllers, so there is the operative assumption that all the right checks listed above are in place. However, they still have some responsibilities, namely to “provide sufficient guarantees to implement appropriate technical and organizational measures in such a manner that processing data will meet the GDPR requirements and ensure the protection of the rights of the data subject.”
Step 7 – Determining A Data Retention Policy
If you are like most organizations, then the idea of archiving, anonymizing or outright deleting records is not something you’ve ever considered. Data is a valuable asset, why limit it?
Well, because now, if you do not, you are in violation of GDPR policy, that’s why. There are many questions to be asked:
- How long do I hold on to staff records after those employees have left the organization?
- How long do I hold on to client information once they have ceased to be a client?
- How long do I hold on to marketing records once the reason for its collection has passed?
The answer to all these questions is – It depends. And that is enormously unsatisfying.
Staff data retention varies from country to country within the European Union. There is no hard and fast rule that can be applied to all EU countries. But we do know is that once a member of staff has left your organization, a moment will be reached where their records can no longer be legally held by their former employer. The same is true for customers, partners, and suppliers.
Sales and Marketing information is another thing altogether. The GDPR data retention makes it clear that the reason for the collection of private information for marketing purposes must be made absolutely clear to the natural person at the outset and that only their explicit consent to provide you with this data will be considered legal. Once that consent is revoked or the narrow reason for the collection of their information has ceased to exist (such as a short-term marketing campaign) then those records must be deleted or anonymized in some fashion.
These are some uncomfortable truths that will need to be fully understood and internalized before you can move forward.
Step 8 – How to Prepare For Data Subject Access Requests (DSAR’s)

This is the customer/client/people-facing aspect of GDPR.
When the law comes into effect, individuals will be able to ask your organization to provide them with a list of the private content that you hold on them. These requests must be acknowledged immediately upon receipt, and the identity of the individual making the request needs to be established beyond any reasonable doubt. Once that is done, you have a one-month timeline to find their records and provide them to them in electronic form (unless they request other means).
That is the technical part of GDPR directive on data protection out of the way. But what about the operational implications of these requests?
Obviously, you will need to train all your front-line and customer-facing staff about what the GDPR data security is and how to handle these requests. But it goes beyond that. It involves “operationalizing” the entire process from start to finish. For example:
- Will you have a specific email address to handle all incoming DSAR’s?
- Should all your front-line staff redirect all incoming verbal DSAR’s requests to an online form system?
- Will there be a specific training program for all existing and incoming staff that covers this aspect of their jobs?
- Which individual/department will ultimately be responsible for ensuring that DSAR’s are responded to promptly?
- How many DSAR’s are we expecting on day 1, month 1, year 1?
If you are looking for one generic answer to the above questions, think again. The answers will vary based on your technology systems, internal circumstances and technical capabilities.
Step 9 – The Cop Out (aka – Get A Second And Third Opinion)
You are unlikely to get one solid opinion on what GDPR is and how you should apply it.
The views and opinions expressed above and purely my own and are based on my experiences as DPO and the implementation of General Data Protection Regulation 2018 rules within my organization.
It would be foolish to assume that any advice I give is appropriate for all organizations and I would, therefore, advise everyone considering their options regarding the implementation of GDPR requirements and rules to seek external advice. This advice can/should come in the form of legal counsel as well and potentially by engaging the services of a 3rd party audit firm.
The road ahead is unclear. I would advise everyone to acquire as much informed opinion as possible and develop their own GDPR compliance checklist.
Author:
Adrian Camilleri, phoenixNAP’s Head of Operations in Europe
Recent Posts
9 Best Practices for Email Security
Are you concerned about how cybercrime and data theft could affect your business operations? Does your business intend to spend a significant percentage of its budget on security this year?
If the answer is yes, you need to focus at least some of your efforts on securing your email communications.
There are hundreds of different threats out there at the moment, and any of them could damage your brand reputation. We saw this happening with companies that lost vital client data in recent cyber breaches, and that received much bad press for doing so.
Most of these breaches happen due to poor email security practices. The latest Data Breach Investigations Report (DBIR) suggests that 66 percent of malware installed on breached networks come through email attachments. There is a decent chance that anyone who penetrates your email system might manage to steal passwords or any other sensitive data.
Read this post and ensure you take the email security tips onboard and put them into action as soon as possible. The last thing you want is for hackers or the programs they might create to cause issues for your business.
Best email practices for business, Train your employees
The information in this section will offer fundamental security tips while highlighting email security measures you should have in place already. If you are not taking the actions mentioned below, you need to start doing so as soon as possible.
The measures you are going to read make up the very least companies need to do to protect themselves from common threats like hacking.
1. The Best Email Security, Use strong passwords that are unique
There is no getting away from the fact that weak passwords are never going to protect your company from data theft or hacking. You need to take a look at all the passwords and phrases people in your office use right now. You then need to improve them based on the tips mentioned below.
A secure password is almost impossible to guess without some insight. The only way a hacker will break into your system is if they use specialist password-guessing software that will run through millions of combinations.
The more complex the password, the more time it takes for the software to figure it out. The passwords that follow the best practices outlined below would take 200-500 years to break.
Essentials for a strong password:
- Use upper and lower case letters
- Use numbers and special characters
- Use random numbers and letters rather than words
- Never use your birthday, hometown, school, university, or brand name
- Avoid common letter-number substitutions
- Think in terms of phrases rather than words
If you are still not sure why strong passwords matter and how to apply these rules, Edward Snowden sums this up nicely in this video. Your organization needs a solid enterprise password management plan.
2. Using two-tier authentication
It might sound technical, but using two-tier authentication is quite straightforward. Moreover, it is guaranteed to add an extra layer of protection to your emails. There are often options within your email client that will enable you to add that service. You can also download specialized software or use a different cloud email provider if you cannot add two-tier authentication with the system you use at the moment.
The concept is simple. But it is an excellent data loss prevention practice as it makes life much more difficult for hackers and those who wait to sneak a peek at your emails.
Even if a criminal manages to guess or retrieve the passwords to your account, two-tier authentication will mean that the individual will still require a code to get your messages and cause issues. That code is usually sent to your phone via a text message. Do not make the mistake of sending it to your computer because you never know who is watching.
Two-tier authentication is one of the best ways to protect social media or a web application from a data breach. It also works with virtually any cloud storage service you might be using.
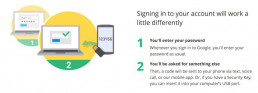
3. Watch out for phishing emails
Before we can help you to keep your eyes peeled for phishing attacks, it is sensible to explain the nature of those domains for people who have not encountered the term in the past. Phishing is a straightforward concept many hackers will use to steal email and account information by tricking individuals into handing over their details.
The process usually works like this:
- The hacker sends emails that contain a link to a site you know.
- The victim clicks the link and finds themselves looking at a familiar website. That is often their bank or something similar, but the site is fake.
- The victim then enters their email address and password to log into their account.
- The fake phishing site steals the email and password before passing it back to the hacker.
When someone at a company falls victim to advanced malware attacks and phishing emails, it can become a disastrous situation.
That is especially the case in instances where the business uses the same passwords for everyone in their office. Hopefully, that should help to highlight how important it can be that you develop strong and unique passwords for all your workers.
A phishing attack is no longer as apparent as it used to be. Hackers are becoming increasingly sophisticated, making it more difficult to identify it unless you pay attention to details.
Just consider this example of a phishing email pretending to be a bank. How long would it take you to figure out it was a scam?
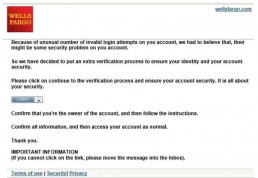
4. Never open unexpected attachments without scanning
Sometimes your business will receive emails that contain file attachments. That is not a problem if you notice the email is from your accountant, and you know you are waiting for them to send information. It is rarely an issue when the emails come from customers or clients either.
However, occasionally, your company will get a phishing email. Such emails come from an unknown source and contain files for you to open.
Of course, you cannot go putting all those messages straight in the trash because many of them might be genuine. For that reason, you need to invest in email threat protection systems. You should consider using antivirus and anti-malware email security software to scan all correspondence, as well as implement advanced spam filters. That should let you know if there is any need for concern when opening the email attachment.
If the program tells you there is a problem, you can delete the message, block the sender, and secure your system. That way, you can prevent a business email compromise and a subsequent data security breach.
5. Do not let employees use company email addresses for private messages
You need to limit the chances of hackers targeting your email system. The best way to achieve this goal is to implement advanced endpoint security solutions and ensure that only work-related messages are hitting your computers.
Discourage all your employees from using company communication systems to talk to friends, shop online or do anything that does not relate to their job roles. It is possible that you could end up attracting cybercriminals if you fail to follow that advice.
You are not awkward when you put measures like that in place. You are just protecting the interests of your operation and everyone it employs.
It is vital to note the same rules will apply to you as the business owner. Never make the mistake of using your professional accounts for anything other than work.
If people in your office need to access their personal accounts for any reason during the working day, tell them to do so using their smartphones and their mobile internet.
Do not allow anyone to connect a smartphone to your office WiFi system if you want to stay under the radar and avoid hackers.
To ensure they understand the reasoning behind this, consider organizing company-wide security awareness training. That can be an excellent way to educate them on the importance of data protection, share email security tips, and raise their awareness of the current cyber threats and technology trends.

6. Scan all emails for viruses and malware
Remember that antivirus malware and software we told you to get a few paragraphs ago?
Well, in most instances, you can use it for far more than just scanning attachments before you open them. Some of the top virus screening solutions on the market will also scan all incoming emails and check them for vulnerabilities as they come into your inbox. The software will present you with an alert if there is any reason for concern. You can usually quarantine the affected email before it has enough time to cause any damage.
Those who use hosted email services will often find their provider follows the same cloud security procedure and lets you know if there is anything dodgy about messages landing in your inbox.
It is your responsibility to check your security settings and enable specific options. Sometimes you have to pay for that service as an extra feature, verify your account now and make sure your provider scans all emails with antivirus solutions.
If you do not have protection, now is the best time to add it.

7. Never access emails from public WiFi
Public WiFi is never secure, and there are many ways in which hackers can steal all the information that passes through a network.
Indeed, criminals only require a laptop and basic software to hack into public WiFi networks and then monitor all the traffic. If you or anyone at your company access emails via a service of that nature, you will make it easy for anyone with the will to steal your passwords and view your sensitive data. That could result in a targeted attack further down the line.
If people need to access their messages outside of the office, there are a couple of options on the table that should not make your operation vulnerable to data theft.
Firstly, if unable to connect to a secure WiFi, your employees could use their smartphone and mobile internet.
That is much more secure than any public WiFi service, and the move should protect your cloud data and your interests.
Secondly, you might consider paying for mobile internet dongles that workers can use with their laptops outside of the office. Both of those options tend to work well, and they should help to protect all your company emails.

8. Use a robust spam filter
One of the best things about cloud-based email services these days is that they tend to come with excellent spam filters.
Indeed, even Google through their service Gmail manages to remove most unwanted messages from your inbox. Make sure you turn your spam filter on or look for a provider who offers better security solutions than those you have right now. Spam filters are an email specialist’s way of attempting to sort the wheat from the chaff and ensure you are not bothered by hundreds of marketing messages and “do you want to lose weight” emails every week.
You can often change the settings on your spam filter to block out any emails that contain specific words or phrases. That can come in handy if you know about some scams going around at the moment because you can block most of the keywords. That should help you to prevent any of your employees from opening a spam email that contains dodgy links or malware by accident.
9. Never click the “unsubscribe” link in spam emails
Let us presume for a moment that an email managed to get through your spam filter and antivirus programs. You open the message and then discover that it looks like a phishing scam or something similar. There is an unsubscribe link at the bottom of the page, and you wonder if it is sensible to click that to prevent further emails from the unwanted source. Whatever happens, make sure you never click that unsubscribe link. Hackers will often place them in emails in an attempt to fool you.
If you decide to click the unsubscribe link or do it by mistake, there is a reasonable chance you will land on a phishing site that will attempt to steal any information it can gather. The link could also provide hackers with a backdoor into your system, and that is why you must never click it. Just mark the message as spam, so your spam filter picks it up next time around, and hit delete.
Remember Safe Email Security Practices
Now you know about email security best practices, nothing should stand in the way of protecting your business.
Combining these with some business data security practices will go a long way regarding your business continuity. You need to make sure all your employees understand this advice too for the best results.
Arrange a meeting or training session where you can hammer the points home and ensure everyone grasps the concept of email data theft and protection.
Whatever you decide, never forget that hackers are everywhere these days. They will stop at nothing to steal your data. Protect yourself with robust email security.
Recent Posts
Data Backup Strategy: Ultimate Step By Step Guide for Business
Cybersecurity is not something to be taken lightly by businesses.
It is not enough to have basic protections like anti-virus software to protect your valuable files. Hackers spend their time finding ways to get around it. Sooner or later, they will.
When that happens, you will not have to worry about permanently losing data.
That is if you have implemented a backup strategy to protect your business’s information.
Why Having a Backup Strategy is Vital
Losing data can not only put your customers’ data at risk but also have a significant impact on your credibility.
The average cost of a breach is seven million dollars as of 2019. It is estimated that 60% of companies that experience data loss close within six months.
Alternatively, you could be at risk of losing data permanently. Viruses and malware that attack your hardware can destroy it, but these are just some of the most dominant threats.
Studies show that 45% of all unplanned downtime is caused by hardware failures, while 60% of IT professionals say that careless employees are the most significant risk to their data.
All of these risks can cost your company money and, without an adequate backup system in place; you could lose everything.
Even if your company manages to survive a data loss, it could be costly. Research shows that, on average, companies pay $7 million to recover from a loss. Many companies do not have that kind of money to spare.
These expenses, as high as they are, only tell part of the story. The other price may be something irreplaceable. I am talking about the faith and trust of your customers. If they feel their data is not safe with you, they will take their business elsewhere.
The solution is to create and implement a data backup strategy. With the right tools, planning, and training, you can protect your data.

The Components of Efficient Backup Strategies
Before you create your backup strategy, you should know what to include.
Let us break down some of the backup strategy best practices:
- Cost. You will need a data backup plan that you can afford. It is a good idea to think beyond dollars. Keep the potential expense of a breach or loss in mind. Then, weigh that against the projected cost of your backup system. That will help guide you.
- Where to store copies of your data? Some companies prefer cloud-based backup. Others like to have a physical backup. The most cautious companies use multiple backup sources. That way, if one backup fails they have another in place.
- What data risks do you face? Every company must think about malware and phishing attacks. However, those might not be the only risks you face. A company in an area that is prone to flooding must consider water damage. Having an off-site backup and data storage solution would be wise.
- How often should you back up your data? Some companies generate data quickly. In such cases, a daily backup may not be sufficient. Hourly backups may be needed. For other companies whose data is rarely updated, a once-weekly backup may be enough.
- Who will be responsible for your backup planning? Employee training is essential to an effective file backup strategy. You need knowledgeable people you can rely on to keep things running.
These things are essential, but they are only the tip of the iceberg. You must consider each aspect of your backup plan in detail. Then, you will have to implement it as quickly and efficiently as possible.

Step #1: Assessing Your Company’s Backup Needs
The first step is to assess your company’s backup needs. There are many things to consider. Let us break it down so you can walk through it.
What Data Do You Need to Protect?
The short answer to this question is everything. Losing any data permanently is not something you want to risk. You need data to keep your business operational.
There are some specific questions to ask, both in the short and long-term. For example:
- You might need the ability to restore data as quickly as possible.
- You might need the ability to recover data.
- You might need to keep services available to clients.
- You may need to back up databases, files, operating systems, applications, and configurations.
The more comprehensive your data backup plan is, the less time it will take for you to get back in business. These questions can help point you in the direction of the right backup solution for your company. You may also want to think about what data is most important.
You might be able to live without an immediate back-p of somethings. However, you might need instant access to others.
What Are Your Data Risks?
Given the current pace of cybercrime growth, you will want to consider the best practices to protect your data from hackers. Here are some questions to ask to determine which risks you must consider.
- Has my company ever been hacked before?
- Are careless employees a concern when it comes to security?
- Is my location at risk for weather-related damage such as flooding or wildfires?
- Do clients log in to my system to access data or services?
Asking these questions will help you identify your risks. A company in a hurricane-prone area might be worried about flooding or wind damage. A customer system linked to your data adds additional risks. Be as thorough as you can as you assess your risks.
What Should Your Backup Infrastructure Be?
The infrastructure of your backup system should match your needs. If you are concerned about the possibility of hardware failure or natural disasters, then you will want to consider off-site backup solutions.
There may also be some benefit to having an on-site physical backup for quick recovery of data. It can save you if you lose your internet service, as might be the case during an emergency. The best way to avoid a continued business disruption is to choose a remote cloud disaster recovery site, possibly with your data center provider. You need to pick a place that would provide you with access to IT equipment, internet service, and any other assets you need to run your business.
Imagine a hurricane hits your facility. A disaster recovery plan enables you to continue your business from a different location and minimize the potential loss of money.
How Long Does Backed Up Data Need to be Stored?
Finally, you will need to consider how long to keep the data you store. Storage is cumulative. If you expect to accumulate a lot of data, you will need space to accommodate it. Some companies have regulatory requirements for backup. If you do, that will impact your decision.
You should evaluate your needs and think about what structure might be best for you.

Step #2: Evaluating Options To Find The Best Backup Strategy
After you assess your backup needs, the next step is to evaluate your options. The backup solution that is best for another company might not work for you. Let us review the backup options available to you.
Hardware Backups
A hard drive backup is kept on-site and often mounted on a wall. They usually come with a storage component. The primary benefit of hard drives is that they can easily be attached to your network.
The downside of a stand-alone hardware backup is that if it fails, you will not have a backup. For that reason, some companies choose to use multiple backup systems.
Software Solutions
Buying backup software may be less expensive than investing in dedicated hardware. Many software options can be installed on your system. You may not need to buy a separate server for it.
You may need to install the software on a virtual machine. A software backup may be the best choice if your infrastructure changes often.
Cloud Services
Cloud services offer backup as a service or offsite backup. These allow you to run your backup and store it in the vendor’s cloud infrastructure.
The benefit of cloud-based storage compared to dedicated servers is that it is affordable and secure. Companies with sensitive data and those who are subject to regulatory requirements may not be able to use it.
Hybrid Solutions
A popular solution is to implement a hybrid backup solution. These combine software and cloud backups to provide multiple options for restoring data.
The benefit of a hybrid service is that it protects you two ways. You will have on-site backups if you need them. Moreover, you will also be able to get your data from the cloud if necessary.
You should also consider what each option means for your staff. Unless you elect to use a comprehensive BaaS option, your employees will need to handle the backups. That is an important consideration.
Backup Storage Options
You will also need to think about where to store your backups. Here again, you have more than one option.
- You can back up your data to local or USB disks. This option is best for backing up individual files and hardware. It is not ideal for networks. If the drive is destroyed, you will lose your backup.
- Network Attached Storage (NAS) and Storage Area Networks (SAN) are also options. These are ideal for storing data for your network. They make for easy recovery network data recovery in most situations. The exception is if your hardware or office is destroyed.
- Backing data up to tapes may be appealing to some companies. The tapes would be shipped to a secure location for storage. This keeps your data safe. The downsides are that you will have to wait for tapes to arrive to restore your data. They are best suited for restoring your whole system, not individual files.
- Cloud storage is increasingly popular. You will need an internet connection to send your data to the cloud. There are options available to help you transmit a significant amount of data. You will be able to access your data from anywhere, but not without an internet connection.
To decide which option is best, you will need to consider two metrics, RTO and RPO. The first is your Recovery Point Objective or RPO. That is the maximum time you are willing to lose data on your systems.
The second is your Recovery Time Objective or RTO. That is how long you want it to take for you to restore normal business operations.
Choosing your backup and storage methods is a balancing act. You will need to weigh your budget against your specific backup needs.
Step #3: Budgeting
The third step is creating a budget for your backup plan.
Some solutions are more expensive than others. Buying new hardware is costly and may require downtime to install.
Cloud-based solutions are more affordable.
As your budget, here are some things to consider.
- What is the maximum amount you want to spend?
- Do you plan to allocate your budget as an item of capital expenditure? Perhaps you would rather log it is an operating expense. Some options will allow you to do the latter.
- What would it cost you if you lost data to a cyber security attack or disaster?
- How much will it cost to train employees to manage the backup? If you are not choosing BaaS, someone in your company will have to take responsibility for backup management.
If you choose backup as a service, then you may be able to pay monthly and avoid a significant, up-front expense. Be realistic about your needs and what you must spend to meet them.
Sometimes, companies underspend on backups. One reason is that a backup system is not viewed as a profit center. It may help to view it as a data loss prevention solution, instead.
Step #4: Select a Platform
Next, it is time to choose a platform.
If you have made careful evaluations, you may already know what you want. As I mentioned earlier, some companies prefer multiple backup options to cover themselves.
Choosing only one backup option may cover your needs. If you are sure you will have an internet connection; a cloud back-up might be sufficient.
You can access it from anywhere and get your data quickly.
The most significant argument against a cloud-based service provider is confidentiality.
If you are storing sensitive data, you may not want to rely on an outside company. Regulations may even prohibit you from doing so. If that is the case, think about off-site, secure storage for your backups. That way, you can get them if your business is damaged.
Step #5: Select a Data Backup Vendor
It is time to choose a vendor to help you implement your new backup strategy. You may opt for an all-in-one service. Some companies can provide hardware, software, and cloud-based solutions. They may also be able to help you with employee training.
Any time you choose a vendor, you should request a data center RFP or proposal. That is the best way to know which options are available to you. As you compare quotes, take all elements of the project into consideration.
These include:
- The overall cost of implementation
- Which options are included
- How long implementation is expected to take
- The vendor’s reputation
Asking for references is a smart idea. Call, and ask them about every aspect of their experience. Make sure to ask about service and support during the process. Then, once you have gathered the information you need, you can award the contract to the vendor you choose.

Step #6: Create a Timetable
The vendor you choose may provide you with an estimated timeframe for implementation. You should still create a timetable of your own. It can help you plan for implementation. A timeline is essential. Having one will allow you to prepare to support the new backup protocol.
Here are some things to consider as you create your timetable.
- What things do you need to do before the vendor can begin work? Examples might be creating a master backup of existing data or designating a team to oversee the process.
- Do you need to get budget approval before you begin? If so, how long will it take?
- What timeline has the vendor provided for completion of the system? You may want to build a bit of extra time into your schedule. That way, a delay on the vendor’s end will not throw you off.
- Will the installation of your system interrupt business? Can you schedule hardware installation on a night or weekend to avoid it?
- How will the project affect your clients, if at all? What can you do to shield them from delays?
Taking these things into consideration, create your timetable. Adding a bit of cushioning is smart. It allows you to make room for the unexpected. There are always things you cannot control. Building some extra time into your schedule can help you prepare for them.
Step #7: Create a Step-by-Step Recovery Plan
As your plan is constructed, put together detailed instructions on how to use it. Ideally, this should include an easy to follow a security incident response checklist.
Keep in mind that the people in charge of backups may refine your procedures. That is a natural part of doing business.
At the minimum, your recovery process should include:
- The type of recovery to necessary
- The data set to be recovered
- Dependencies that affect the recovery
- Any post-restoration steps to be taken
You may need input from your vendors or service providers. As much as possible, the people who will be responsible for backups should be involved.
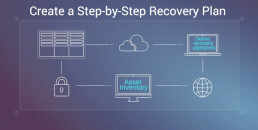
Step #8: Test Your New Backup System
The final step is to test your backups. Testing should be an ongoing task. Ideally, you would do it after every backup. Since that is not practical, you will need to choose a schedule that works.
Let us start by talking about what to test.
You will want to check to make sure that:
- Your backup was successful, and the data you to secure is there
- Your restoration process is smooth and goes without a hitch
- Employees know what to do and when to do it
- There are no glitches or problems with the backup
That is a lot to test. Let us start with the data, since for most companies that is the most important thing. Data testing may involve:
- File recovery. Can you retrieve an individual file from the backup? This is the most straightforward test, but a necessary one. Users may accidentally delete or damage files. You need to be able to get them back.
- VM recovery. Virtual machines only apply to virtual environments. If that applies to you, you will want to make sure you can restore the VM from your backups. You will also want to check your application licensing for conflicts.
- Physical server recovery can vary depending on your hardware configuration. Some back up from SAN, while others use a local disk. Make sure you know what the process is and how to do it.
- Data recovery may also vary. However, if you are backing up a database at the app level, you may want to check that you can restore it.
- Application recovery can be complicated. You will need to understand the relationships between your apps and servers. It may be best to conduct this test in an isolated environment.
Once you have confirmed the backups work, you will want to create a testing schedule. There are several options:
- Set up a time-based schedule. For example, you might do a complete test of your backup once a week, or once a month. The frequency should be decided by your needs.
- Schedule additional tests after changes in your data. For example, if you add a new app or upgrade an old one, testing is a good idea.
- If you have an influx of data, schedule a test to make sure it is secure. The data may come with a new application. Alternatively, it may be the result of a merger with another company. Either way, you will want to be sure that the backup is capturing the new data.
With a schedule in place, you will be sure that your backups will be there if you need them.

Don’t Overlook Backup Strategies For Your Business
No company should be without a comprehensive backup system.
It is the only way to prevent data loss. Every business has some risk. Whether your primary concern is a natural disaster, cybercrime, or employee carelessness, having a secure backup system can give you the peace of mind you need.
Recent Posts
Overcoming The Challenges Hybrid Cloud Adoption in 11 Steps
Congratulations on choosing the hybrid cloud. Are you ready to address the challenges that go with it?
Many IT admins have valid concerns about handing production applications to a third party or the possibility of investing in expensive on-premises infrastructure.
This is why you choose a hybrid solution to begin with. Allowing you to build a flexible environment, it is the most widely used cloud deployment model.
There are many benefits you can capitalize on by combining public and private cloud. However, there are also some challenges you should be aware of.

Compliance and security of cloud storage
One of the most significant challenges you will face with a hybrid cloud deployment is meeting compliance and security requirements. Depending on your industry, you may find specific security requirements challenging to implement across multiple cloud instances.
Often the number one security challenge is the lack of redundancy, which can be a severe security risk to hybrid cloud deployment. If redundancy is not present, you will not have backup copies of data distributed across your infrastructure.
Backup and failover are vital to any cloud infrastructure. You need to achieve redundancy across the entire data center to eliminate the possibility of data loss and ensure your data stays available even during an outage. If your server goes down, another one is automatically switched on to minimize downtime.
In addition to achieving redundancy, another challenge is demonstrating compliance with industry standards and regulations. You must ensure not only that your public cloud provider complies with relevant standards, but also that coordination efforts between the cloud and on-premises servers are compliant.
For example, if your data includes customer bank and financial data, you will have to demonstrate your infrastructure is compliant with the Payment Card Industry Data Security Standard (PCI DSS). Use our PCI Checklist to ensure you are protected.
Consumers are already skeptical about data breaches, especially incidents such as the Equifax data breach.
When a single attack compromises personal information of over 143 million people, and all the public hears about it, cybersecurity awareness rates grow significantly.
Another critical challenge with a hybrid cloud model is establishing clear identity and access management policies. When you entrust a third-party with access to your critical data, you need to establish new rules for both your and your vendor’s employees. Clearly outlined processes related to who can view, alter, and move files goes a long way in keeping your data safe.
For organizations looking to circumvent the public Internet and have their data transferred via private networks, solutions such as AWS Direct Connect can help achieve compliance. AWS Direct Connect lets you link any cloud application you need directly to Amazon S3 or other Amazon web services.
Vaguely Written SLAs
When you sign an SLA with your cloud or infrastructure as a service (IaaS) provider, make sure you read the fine print. Your SLA defines many of your critical business processes, so you need to ensure it is fully tailored to your needs.
Ask yourself if you can hold your cloud provider to their SLA. While you already have standards set for your on-premises infrastructure, make sure the cloud provider agrees to the same terms and documents it in the SLA.
You can test this out by sampling data on your on-premises servers under typical workloads and simulate issues that could disrupt service. If one of the primary drivers for your business is keeping sensitive data on your on-premises servers, service level agreement best practices should mirror the security requirements for hosting your data on a private cloud.
Data integration in a cross-cloud deployment
You may choose to keep sensitive data on-premises and other workloads in the cloud. Over a third of cloud users experience errors and downtime with a hybrid cloud. These errors can cost a significant amount of lost revenue and downtime to recover.
Data integration is another issue associated with hybrid cloud deployment models. The accurate data and file versions must be exchanged between the on-premises and cloud servers, which is not always straightforward to achieve. Continuous software updates and patches can contribute to errors in data transport across the data center. Part of this challenge includes real-time access to data that can be impacted due to errors.
How much downtime can your business afford? The question is straightforward, and you should factor it into your deployment and include it in the SLA. A certain amount of downtime per any given point in time or throughout the year should be acceptable. If your business peaks at specific aspects of the year, your affordable downtime will vary.
Just calculate the amounts of data you can lose if you experience downtime. Besides having it specified in your SLA, you should also consider what kind of disaster recovery solutions your provider offers. If you can eliminate downtime, you will not have to worry about possible business disruptions. This is why it would be smart to think about cloud disaster recovery options at this point.
Rigorous readiness
Business leaders often need rigor in plans and readiness. The more departments participate in making decisions, the more control is required.
For instance, decisions for purchases might prove a strong business case. Some line of business decisions could lack proper analysis without considering the data integration required.
To address this challenge, you must ensure to curb any extraneous decisions that involve expenditures of your infrastructure. Your IT leadership should not be able to arbitrarily decide on how, when, or where data is moved in a hybrid cloud deployment.
They need to have a detailed plan on what workloads should reside in public and private environments. They should ensure critical data such as developer tools, active directory information, and user data are stored in the private cloud. Testing environments, public documents, and less sensitive business information can be outsourced to public cloud providers.
Getting ready for a new infrastructure model also involves new cost management strategies. You need to be confident that your IT, security, business planning, and accounting departments are on the same page regarding costs necessary for hybrid cloud deployment options.

Skill gaps in a hybrid cloud environment
One of the most overlooked challenges in a hybrid cloud strategy is training. Does your IT staff have adequate knowledge about how hybrid cloud storage? Do they understand the responsibilities of your data center provider versus their requirements?
Too often, IT administrators in a multi-cloud infrastructure rely too heavily on the provider to handle everything. When asked how to fill knowledge gaps in such environments, company leaders considered four fundamental data points. They include application architecture design, business processes, application development, and integration development, as well as cloud monitoring and governing.
To fill these gaps, business leaders will have to work with the cloud service provider who already knows the ins and outs of their cloud limits and capabilities. They will also need to train their staff on hybrid cloud computing and develop new cloud management strategies. They should also bring new talent who has past work experience with similar cloud architectures. When in doubt, hire someone who has been around the block a few times in a hybrid environment. They are very likely to be able to offer a new perspective and increased efficiency of daily operations.
Use cases for hybrid cloud architecture
You should learn from others’ past mistakes, so you do not follow down the same path. Statistically speaking, the total cost of ownership among those who adopted a cloud-based environment was 40% in 2017.
Cloud Technology Partners reported methods for making a business case for cloud deployments. The report also explored the ways a company can quantify cloud benefits. Regardless of the industry, an organization can expect a total cost of ownership savings of about 40%.
In the Bain Brief last year, 21% of companies reported that they are “safety-conscious” about their cloud environment. This means those who are safety-conscious are more willing to adopt a cloud environment. Many may prefer a private cloud due to regulations and compliance rules based on the industry.
Right Scale reported that hybrid cloud adoption is up and private cloud adoption is down. The percentage jumped 3% between 2017 and 2018 and will most likely grow a few more percentage points this year.
Hybrid cloud network elements
The network is a critical component when working in a hybrid cloud environment. The assumption by most application developers is that all application components reside close to each other.
In a hybrid cloud environment, this is not the case. While physically and virtually separated, the two settings must be linked correctly. Correct mapping of network topology can help in overcoming the problem. This process will involve security and latency among multiple layers between the internal and external resources.
Trusted data centers already have an answer to the connectivity issue and deploy hybrid cloud solutions to respond to the challenge. Your applications must be able to run seamlessly within the environment. To do this, you may need to host specific applications with network dependencies in one place or the other (on-premises or in the cloud).
Depending on the application’s size, you will have to run it on its own stack in one environment or the other. Hybrid management should be viewed operationally to find a solution on the infrastructure.
Finding the proper cloud technology balance
A hybrid cloud deployment involves finding common ground for flexibility between the two environments within the same infrastructure. This flexibility may include the use of public cloud resources for testing and staging.
The basics of components in both environments should include how each is operated and how the application programming looks. One of the main challenges with this is that business and technology solutions seek the lowest common denominator to offer a seamless experience for users.
Your employees should be able to perform their daily work without noticing in which part of the environment they are working. As long as they experience the same speed, security, and bandwidth, they will not even know the difference.
Advantages of hybrid cloud storage
Another thing to keep in mind is the stability you will require in your computing environment. Do you plan to grow your business over the next few years? Will you be splitting up your departments?
These are all important considerations of the scalability of your hybrid cloud. With scalability comes scaling costs. What will happen if you need to increase cloud usage and storage? This may be included in the SLA so check with your cloud provider. If you need the flexibility to scale up or down or place some of your business capabilities behind a firewall, what flexibility will your hybrid cloud have to do this and in what capacity can this be accomplished?
In other words, if you need to add or delete users to the environment, will they be using both on-premises and cloud resources? As previously mentioned, your SaaS applications may require more capacity in the future than they did when you first deployed them over the network. Think of it like this, the more data you add, the more storage you will need. You may also wish to consider the age of the data and performing a periodic cleanup. Why waste storage space by holding onto old data you will never need to use again?
Compatibility challenges
Cross-compatibility is another challenge you may face in a hybrid cloud. With two levels of infrastructure – on-premise and the public cloud – the odds are that both will operate on different stacks.
Will your IT administrators be responsible for managing both with the same tools or will they have to learn how to use new ones based on what your cloud provider uses? Will the cloud provider offer the flexibility for your administrators to use whichever tools they need to for continuity across the entire environment?
Governance in hybrid environments
Another challenge to overcome is to develop a list of best practices when governing your hybrid cloud. The five critical elements of cloud computing include broad access to network resources, resource pooling, measured service, on-demand self-service, and elasticity.
Additionally, you may want to develop best practices that focus on evolving automation. Do not forget to communicate this to your users. It is always a best practice to inform your users about any network changes, so they are aware of what is happening behind the scenes. They can also help by acting as your watchdogs to report any errors or anomalies they incur daily.
There is no such thing as a one-size-fits-all solution
Every business requires a unique solution to address a variety of business challenges. The computing environment adapts to the business needs and meets multiple efficiency criteria.
Consider different factors such as cost, scalability, reliability, security, and compatibility. Of course, data safety is a significant challenge, but you need to find a hybrid cloud that meets all your needs. You should consider what your business needs are now and what they may be in the future. Only then you can find a cloud provider capable and willing to meet those needs. Whether your needs change six months from now or six years from now, you need to go with a cloud solution that will be able to support your business long term.
Discuss your security, performance, and SLA needs with the cloud service provider. Make sure you tackle these common issues before they grow into a serious challenge. Make sure you understand what your cloud infrastructure should deliver and how you can achieve consistency across the entire environment. The sooner you address this, the sooner your business will be on its way to boosted efficiency.
Recent Posts
IT Cost Reduction Strategy: 7 Proven Tactics to Optimize your Budget
Are you looking for proven IT cost optimization tactics and success strategies?
It is well know how technology can reduce costs. But what about when it comes time to evaluate your companies spending on information technology?
If you feel your information technology budget is too constrained to keep up with new requirements, you are not alone.
Many technology and business leaders struggle to meet the demand while managing a tight budget.
A CIO Magazine survey findings showed that smaller businesses spend about 6.9% of their revenue on IT infrastructure costs, which is above the recommended 4-6% range. Medium companies spent an average of 4.1%, while larger-sized businesses paid 3.2%.
However, spending a lot on IT infrastructure costs does not make one a top performer. CIO Magazine concluded that successful SMBs found creative ways to reduce IT infrastructure costs.
How much should your company spend on IT?

Apptio founder Sunny Gupta said that most CIOs spend 70-80% of their IT budget on maintenance. The last 20-30% of the budget goes into innovation.
It is clear that CIOs must reduce infrastructure costs to be able to focus on innovation. Imagine how much money you can save by utilizing cost-cutting techniques.
Gartner managing Vice President Michele Caminos agrees.
“By lowering the cost to ‘keep the lights on’ – otherwise known as ‘run’ costs – you can start freeing up funds,” she said. “Since infrastructure and operations (O&O) compromises two-thirds of overall IT run costs, this is the most obvious area for reducing expenses.”
Gartner now forecasts that global IT spending will reach $3.7 trillion in 2018. However, the company suggests that businesses should use specific strategies to reduce IT expenses by 10% in 12 months and 25% in three years.
The sooner you start to reduce IT infrastructure costs, the better.
Consider how much you spend on IT infrastructure per worker per year. Now calculate how much cost savings you can achieve by lowering those by 10%. If you can find a way to do it, you would be able to reallocate all these funds into better prospects.
How does technology reduce IT infrastructure costs?
There are countless techniques to make significant IT cost reductions.
CIOs should examine their budget and identify ways to cut expenses. Determine which areas you can consolidate and which require more attention.
Here are seven cost optimization techniques and success strategies to reduce IT infrastructure costs:
1. Virtualization
Virtualization is one of the methods that can help you achieve significant cost savings.
This process is merely replacing physical hardware with their virtual counterparts.
One of the advantages of virtualization over traditional infrastructure is the ability to maximize the use of server resources. Some bare metal virtual environments have minimal utilization levels, often under 15%. Virtualization can quadruple that percentage.
It means that companies do not need to depend on physical servers. They can switch to virtual environments to decrease energy and hardware expenses. Memory and CPUs separate from hardware which allows space and flexibility for other uses.
2. Software-Defined Data Center
A software-defined data center (SDDC) is merely the next step in virtualization and can significantly help in lowering operational costs related to information technology systems.
In fact, Gartner once declared that three-fourths of Global 2000 enterprises which utilize hybrid clouds and DevOps tactics would need SDDCs by 2020.
This means that service providers deliver networking, storage, computing, telecommunications, and other IT functions. These resources are pooled together, allowing businesses to eliminate the need for extra space during high demand phases. It also minimizes the need for employees to spend as much time or money maintaining the systems. Companies save on hardware as they no longer have to store expensive and cumbersome equipment in their buildings.
Furthermore, many service providers put a team of expert staff at your disposal. A fault in your computing or networking can easily hamper your company’s output and cost you thousands of dollars in lost productivity. It is crucial to choose a provider with support specialists who are available at a moment’s notice.
3. Outsourcing IT Staff and Services
Outsourcing is another method to reduce IT infrastructure costs. In an average company, for example, IT support accounts for 8% of all costs associated with information technology. This figure is the main reason some companies turn to outsourcing.
A 2016 report by Deloitte found that 72% of companies contracted out their IT staff. 31% of respondents in that survey wanted to outsource even further. These findings speak about the popularity and convenience of staff outsourcing.
In most cases, outsourcing is an excellent way to reduce IT operating costs. This is most evident in the tech industry, but many other companies turn to it as well.
Enterprise Systems Journal reported that they will experience a spending reduction of 25-40% due to outsourcing. It is no wonder that 78% of small businesses use freelancers to gain an edge over opponents. Freelancing helps small companies reduce IT infrastructure costs and hiring expenses by 50% or more.
In addition to outsourcing IT staff, companies can outsource infrastructure components on a pay-per-use model. Such an operating model enables businesses to access various advanced services and technologies. Security as a service, Disaster-Recovery-as-a-Service, and Backup-as-a-Service are just some of the solutions that bring advanced IT an affordable price point.
With these technologies typically being quite expensive, paying them on-demand could be an excellent cost-cutting initiative.
4. Outsourcing Security Services
Hiring outside contractors to protect against network security threats can be beneficial. Working with a Managed Security Service Provider (MSSP) is likely to offer you more efficient protection from cyber attacks.
Hackers have grown more cunning over the years. Businesses need to defend themselves against new threats.
At the same time, managed security services are a cost-effective alternative to implementing in-house security teams and systems.
For example, a mid-level enterprise would have to pay thousands of dollars a year for a single security system, which is roughly equivalent to an information security specialist’s salary.
However, the employee will come with added expenses such as benefits, vacation days, sick days, and onboarding and offboarding costs.
Plus, you may need to purchase specialized security hardware and hire multiple employees. Once you start to compare both options, it is easy to see how that managed security has an enormous business value.
MSSPs also provide an in-house team of trained expert staff members who offer real-time customer service 24/7. Instant response is critical because you never know when the next data breach will occur.
5. Hybrid Cloud Implementation
Cloud storage is a popular way for companies to reduce IT infrastructure costs. A study from Cloud Security Alliance found that about one-third of businesses are incredibly enthusiastic about cloud adoption. 86% of companies already include cloud computing in their IT budget.
Even enterprises turn to the cloud. In the 2017 report from RightScale, enterprises were found to run three-fourths of their workloads in the cloud.
There’s little wonder about the reasons cloud adoption is so widespread. Earlier market research by Vanson Bourne revealed that the cloud helps companies save:
- 16.18% of operational costs,
- 15.07% of total IT spending, and
- 16.76% on IT maintenance.
Furthermore, the report stated that organizations see 18-20% increase in process efficiency, growth, and time to market. It is easy to see that cloud computing helps companies save money and boost productivity.
Companies that need extra security can lower their costs with a hybrid cloud model. Today the most popular and the most effective form of cloud computing, the hybrid cloud allows for an optimal distribution of workloads between public and private environments.
Businesses can choose to store critical data in private environments while utilizing the public cloud for less sensitive data and applications. In addition to this, hybrid clouds are incredibly scalable. They allow for easy resource upgrades to better adjust to your business requirements. It is crucial to choose a cloud provider that can help you build the right platform to meet your needs.
6. Consolidating Systems to Reduce Cost
Consolidation is nothing more than combining multiple processes into a single unit.
This way, companies can save space, time, and money. Merging several information technology solutions into a unique and streamlined platform requires a lot of work and effort upfront.
However, this technique will help your business run smoother.
It also helps you seize various cost reduction opportunities. The small efficiencies here and there will significantly reduce your information technology spending.
It is essential to keep the business running as usual while making these critical changes. New company processes, data transfers, and adding or removing individual elements can significantly impact the flow of business. You must test each business operation beforehand to ensure that it functions as expected after implementation.
7. Standardize Your IT Infrastructure for Savings
Standardization means ensuring consistency across different hardware and software applications.
This is a form of a business process improvement that can help maintain compatibility. It also significantly contributes to IT cost optimization. Standardizing your platforms could be as simple as providing all employees with the same type of computer or operating system. With everyone on the same page, nobody will question what application works on which platform.
This is one of the key actions that can eliminate IT infrastructure costs and save money on training.
Imagine if one specialist spent their time trying to master each different computer or program. It would take an enormous amount of energy to learn each new platform. Furthermore, all other employees will be familiar with the same platforms and have an easier time resolving issues.
Summary of The Best Cost Optimization Ideas and Initiatives
Developing new information technology cost optimization technique is not rocket science. Utilizing the strategies above will require some research and planning to implement. However, the upfront effort is nothing compared to the long-term cost savings you can achieve.
Just how much money can your company keep by using these proven strategies to reduce IT infrastructure costs?
How does technology cut costs?
You will find that the hundreds, if not thousands or millions, of dollars saved, can be used for growth and business innovation opportunities. Gain a competitive edge with efficient budgeting techniques. Revitalize your financial plan and significantly reduce IT infrastructure costs with these tactics.
Recent Posts
Exposing 10 Cloud Security Myths Putting Your Business Data at Risk
When it comes to cloud computing, the benefits are too significant to ignore.
According to the 2018 Cloud Security Report, 9 of 10 security professionals report they are concerned about cloud security, an increase of 11% from 2017.
While most of those myths have been debunked, certain misconceptions exist even today. The general understanding of technology has improved significantly. However, many businesses still hesitate to embrace it. They fear the change and fail to leverage cloud computing’s potential.
To combat these misperceptions and clear up some of the common myths, we created the below infographic. Take a look at these findings to understand the cloud better!
Share The Infographic On Your Site, Just Copy & Paste This Code
<p><a href='https://devtest.phoenixnap.com/blog/cloud-computing-myths'><img src='https://devtest.phoenixnap.com/blog/wp-content/uploads/2017/12/Common-Cloud-Myths-Final.png' alt='Infographic of cloud computing myths' width='1080' border='0' /></a></p><br />
<p>
Cloud Computing Myths Debunked
Ever since the cloud started entering business ecosystems, data security has been a prevalent concern for CIOs. In a recent 2018 Cloud Security Issues Spotlight Report, the majority of respondents said that they doubt the cloud’s security.
Their top three concerns include:
- Protecting against data loss (57%)
- Threats to data privacy (49%)
- Breaches of confidentiality (47%)
Although justified to a certain extent, these concerns are largely inflated.
The public cloud platform does have some flaws that make it inconvenient for sensitive data. As a shared multi-tenant environment, it gives businesses little control over their data and application security. However, this does not mean third-parties can easily access them.
On the other hand, advents of security technologies made a significant difference in how data is protected in the cloud. Today’s vendors have a greater variety of systems and resources at their disposal to secure their clients’ data. Even the public cloud is better protected than most traditional in-house data centers.
Also, data security is not only the vendor’s responsibility. Clients themselves also need to do their part in protecting their workloads. As recently reported by Gartner, customers will account for 95% of cloud security failures through 2020.
This figure may indicate the roots of the myth of cloud security. While it is true that security breaches will continue to happen in the future, they are not always the provider’s fault. Businesses themselves need to take responsibility for their IT choices.
Both service providers and clients need to take steps toward greater security. If both sides follow cloud security best practices, there is no need to fear cyber attacks.
Understanding security and security responsibilities
The latest analyst reports predict that the cloud is becoming growingly secure. Gartner suggests that the number of security incidents on public cloud IaaS platforms will be 60% lower than those in traditional data centers through 2020. As more businesses start implementing advanced security tools, the number of breaches will gradually decrease.
The same report also predicts that enterprises following cloud security best practices will experience fewer security failures. About 60% of companies are expected to benefit that way next year.
Apparently, the sky is clearing out for a lot of businesses. Companies are becoming more knowledgeable about the cloud. They are also savvier about its security. This trend is helping shape a better future for cloud implementations in business.
Data Migration Challenge
The cloud has long been considered a form of disruptive innovation. As an emerging technology, it is both exciting and frightening. In addition to security concerns, businesses also often fear the cloud migration process.
Depending on the volume of workloads that you want to move, cloud migration can be quite challenging. However, it does not have to be complicated or risky. Today’s cloud systems can efficiently estimate workloads and set up new environments in a matter of hours.
Of course, once the workloads are transferred, companies need to implement new data management policies. They need to rework their security and access control guidelines to reflect the changes. Even for companies with large IT teams, this often means some shifts in duties.
If properly planned, the migration does not have to take too long. It can be very efficient, and some of the benefits are immediate. These include improved bandwidth, data availability, and 24/7/365 support. Long-term benefits are advanced protection, availability of backup and disaster recovery resources, and scalability.
Cost-effectiveness of Cloud Implementations
Another major misconception is related to the expected ROI of using cloud services. Depending on the type of service, the prices of cloud resources can vary. Businesses can opt for different storage, backup, networking or computing plans. Some of these may appear pricey, especially if designed for enterprise.
However, the cloud eliminates the need to invest in hardware equipment or IT teams. That already makes it more affordable than traditional platforms. In fact, the ability to outsource these resources on a pay-per-use basis accelerated the cloud’s adoption. Even small businesses can leverage cloud technologies as they are available at a fraction of the price of an in-house environment.
The cloud also makes advanced cloud backup and disaster recovery solutions easier to access. Businesses no longer have to invest in expensive one-off solutions. Even security services are more affordable. Almost any type of enterprise-grade technology can be commoditized through the cloud.
The overall savings are much higher than it may appear at first. Just consider the recent statistics – 47% of respondents in CompTIA’s report said that cost-cutting was the top benefit of moving to the cloud.
By being able to scale resources according to your needs, you have greater control over your infrastructure costs. This advantage enables businesses to plan their IT budgets better while ensuring they always use the most appropriate solutions and resources.

Conclusion: Cloud computing myths and realities
Cloud implementations may take a wide variety of forms. To leverage the cloud’s potential, businesses need to understand its true power and how it can serve their specific needs. Only that way can they plan its deployment correctly.
By falling prey to the common cloud myths and misconceptions about the cloud, businesses can miss out on some significant advantages. The facts listed on our infographic should help you ensure this is not so!
Recent Posts
Service Level Agreement Best Practices: Everything You Need to Know
Does your organization have firm ground rules regarding service delivery and client communication? Are your best practices for service level management clear?
If you want to be a quality network service provider, establishing SLA’s is a must.
The services you offer may vary from IT, hybrid cloud, hosting, internet, or anything else under the sun. Regardless of the type, you need to develop clear standards to ensure your services meet the business requirements of your clients. At the same time, you should make it a part of your strategy to do so continually.
A mutual understanding that facilitates this is called a Service Level Agreement.
The SLA helps keep service providers accountable since they agree to follow the standards set in the agreement. For example, if it says you offer 5GB worth of cloud storage, but you only provide your customer with 3GB, you will be held accountable for not keeping your end of the bargain.
What is a Service Level Agreement (SLA)?
A service level agreement is a legal contract between you and the end user.
Its primary purpose is to make sure that both parties involved agree on the services you are providing and the standards to which you will adhere.
If you did not have an SLA, you would be able to deliver your customer as little cloud storage space as you wanted to and they would not have any proof that you promised them more.
A good SLA makes expectations between the client and contractor crystal clear. It is focused on defining the service levels, availability and performance standards, as well as the company’s performance goals. It also serves to help respond to dramatic changes and ensure the client’s business operates smoothly and efficiently.
3 Types of Service Level Agreements
There are three main kinds of SLA’s. Each one provides a different purpose that depends on the service provided.
Single Service Agreement
Service Level Agreements cover a single service for each customer. For example, you might be providing IT services to a company’s human resources department, administrative department, and marketing department. A service-level agreement would apply to all three offices, and they would all follow the same guidelines.
Customer-level SLA’s
Customer-level SLA’s are individual agreements between the customer and the cloud service provider. These kinds of SLA’s often cover several requests made by the same customer. For example, you would use it if a customer needed your company’s cloud software, hosting capabilities, and IT support.
Multi-level Agreements
Multi-level Agreements are compromised of service-level, customer-level, and corporate levels. They cover general service level issues for each customer in the organization.

Establishing SLA Best Practices: 8 Elements
Each agreement consists of many essential elements that help lay down what you do and what your clients should expect. How to develop a service level agreement?
1. A description of your service
Define what your customer is getting and what they need to know about your duties. Use plain language to ensure that your agreement is easy to understand.
2. Availability
Let your customer know what level of availability you offer and how often they can use your services. Some services might only be available during specific hours. Others might be more available depending on subscription levels.
You should also include any other limitations that the customer may face. For example, you might only provide IT support to a certain number of computers unless the customer is willing to pay more money for expanded services.
3. Metrics
Measure your performance indicators by meeting specific benchmarks. Trackable metrics might range from how much cloud storage you are providing or how quickly you will provide IT duties for their laptop.
4. Support and Customer Service
Tell your customer how they can report issues and how long it takes to solve those problems. Customers will get frustrated if it takes too long to resolve their issues as such complications make it difficult for them to get what they paid for.
5. Monitoring
Let them know if performance and activity will be tracked or recorded. You often must collect data to prove that you are meeting the established metrics, but some customers will be reluctant to give up such information.
6. Duration
How long will your services last?
Is it an ongoing agreement or a monthly contract? Establish a time frame with your client so that they know how long they can use your services per the agreement. They may want to extend their contract based on their future needs.
7. Consequences for failure to meet obligations
What happens if you do not provide the expected service?
Will you reimburse the customer or make it up to them somehow? This section ensures that you will provide the services you promised or be forced to compensate the customer in some way if you do not.
8. Constraints and escape clauses
There might be situations where you cannot provide your services. An escape clause might be something as simple as your customer breaching the contract but may include other conditions such as if your provided equipment gets irreparably damaged.
Each definition should be as specific and quantifiable as possible. You want to make sure that there are no misunderstandings between you and your client.

The SMART Model of Building an SLA
You should craft your SLA with the customer’s best interests and business management objectives in mind. You want it to be easy to understand, yet comprehensive enough to cover any situations that may arise. You should write it by using the SMART method, which ensures that it is:
Simple: Your end user should have a clear understanding of everything in the agreement. Language needs to be clear and direct with no room for misinterpretation. Do not load your agreement with too many superfluous words or complex definitions.
Measurable: As mentioned earlier, you must set metrics to track how efficient your services are. Typical parameters include uptime, information security measures, defect rates, technical quality, and business results. For example, a website host’s SLA might promise an uptime of 99.999% because the client wants their site running as often as possible. Monitoring the site’s uptime helps prove that you are delivering what you promised.
Achievable: You should be realistic and set down performance and technical goals that you can effortlessly meet. Do not try to shoot for the moon if you cannot reach it. Goals that are too hard to achieve will only discourage your team members and raise your client’s expectations to unreasonable heights.
Relevant: Everything in your SLA should apply to your customer’s needs and goals. Aligning it with your user’s broader business strategy ensures that both parties will work very well together.
Time-bound Priority Level: Set time limits as to when you will fulfill your customer’s needs. Users want their services to be as quick and responsive as possible. Failing to deliver on time will result in unhappy customers that might take their business elsewhere.
All businesses are susceptible to external factors.
Many times, the cause of disruption will be entirely out of their control. Your cloud storage service might run into network issues, suffer from hardware or software failure, need to undergo scheduled maintenance to protect against DDoS attacks. These situations will cause several problems for you and your customers as they will render your services obsolete.
Determine the best ways for your team to cope with unexpected events so that you can recover quickly and efficiently. You should also define security measures and practices to prevent such incidents from happening. For example, you could establish firewalls to protect your data from potential DDoS attacks. Also, make use of our PCI Compliance checklist.
It should also provide your SLA performance requirements so that clients know how you will protect their data.
Explain how you will uphold data privacy, reliability, disaster recovery, and preservation. Ensure that your clients are also following security best practices to protect their data by taking precautions such as revoking cloud access to disgruntled former employees. You should have a disaster recovery plan to mitigate damage when tragedies occur.
Your customers are looking for a service that best fits their needs.
Whether focused on capacity planning or increasing their performance and capacity levels, they want someone who will help their business run smarter, faster, better, and more efficiently. You should already have a good idea of what your market is looking for and adjust your service level agreement to meet that demand.
Craft your SLA’s with your customers to get the best results possible.
Get a better understanding of what exactly they want out of your service. Their goals should be your goals. When your clients have reached their personal or professional milestones, that means you have achieved yours as well.
SLAs need to be reviewed and updated from time to time.
Your team should always strive to improve the way it does things, so the agreement itself will have to be adjusted whenever new practices are suggested or promised. You want to increase your productivity, efficiency, performance, flexibility, capacity, and standardization.
You will want to notify customers about any updates you made to the service level agreement, especially the ones affecting work hours, availability, turnaround time, response time, and costs. Events such as software updates and organizational changes will also prompt review.
Use whatever metrics you have to compare your performance levels to the standards you have set. These parameters might include average response time, average problem resolution time, number of requests, and so on. If you have been exceeding your goals, you could set them higher.
If your team’s efforts have been slacking, perhaps it is time to realign your strategy.
Service Level agreement can be confusing to craft, especially from scratch, but they are an essential asset for every service provider.
Without an operational level agreement in place, contractors and clients would face a lot of legal headaches. They would lack focus and would find it challenging to maintain the efficiency of their operations.
Even when you have it developed, your work on it does not stop. You need to periodically review what you have written and always be mindful of suggestions and improvements. That way, you can ensure that you are continually meeting the expectations of your clients and partners.
Recent Posts
8 Benefits of Cloud Computing for your Business in 2020
Cloud services can change everything about your business. Hosting your business systems, custom applications, and infrastructure on remote servers protects your business and prevents data loss.Read more
IT Strategy: Be Future-Proof With These 7 Simple Steps
Do You Really Need End Of The Year Business Hacks?
Equifax Breach Raises Questions IT Security and Compliance
How to Keep Your Web Hosting Customers Happy?
If you are a web hosting company, you might be facing the need to re-invent your business model. Regardless whether your servers are owned or leased; if you are paying for server colocation hosting in a top-notch data center facility or using a VPS solution.
There is one factor that’ll set you apart from the rest of web hosting providers out there – your clients’ satisfaction.