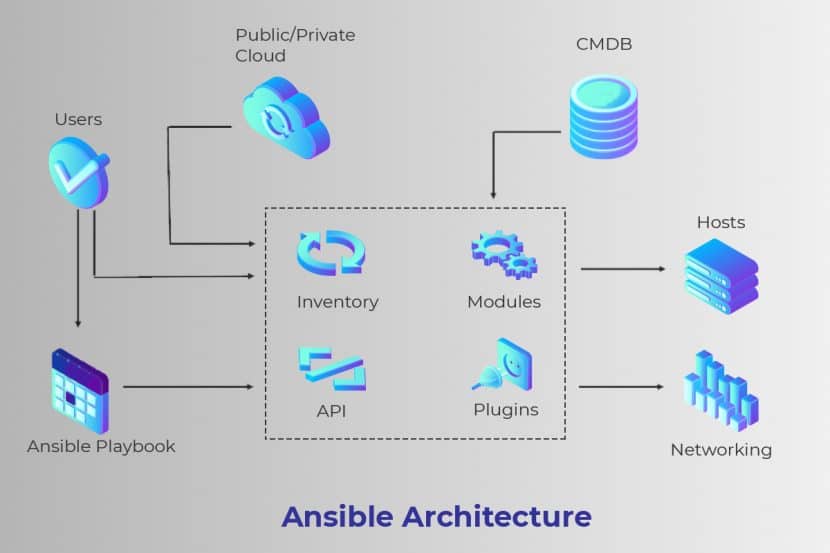
In the ‘DevOps’ world, organizations are implementing or building processes using Infrastructure as Code (IAC). Ansible, Terraform, and Puppet allow enterprises to scale and create repeatable configurations that test and enforce procedures to continually ensure the right results.
We will examine the differences between these three more in-depth. To guide you through choosing a platform that will work best for your needs. All three are advanced-level platforms for deploying replicable and repetitive applications that have highly complex requirements.
Compare the similarities and differences these applications have in terms of configuration management, architecture, and orchestration and make an informed decision.
Infrastructure as Code
Introduced over a decade ago, the concept of Infrastructure as Code (IAC) refers to the process of managing and provisioning computer data centers. It’s a strategy for managing data center servers, networking infrastructure, and storage. Its purpose is to simplify large-scale management and configuration dramatically.
IAC allows provisioning and managing of computer data centers via machine-readable definition files without having to configure tools or physical hardware. In simpler terms, IAC treats manual configurations, build guides, run books, and related procedures as code. Read by software, the code that maintains the state of the infrastructure.
Designed to solve configuration drift, system inconsistencies, human error, and loss of context, IAC resolves all these potentially crippling problems. These processes used to take a considerable amount of time; modern IAC tools make all processes faster. It eliminates manual configuration steps and makes them repeatable and scalable. It can load several hundred servers significantly quicker. It allows users to gain predictable architecture and confidently maintain the configuration or state of the data center.
There are several IAC tools to choose from, with three major examples being Ansible, Terraform, and Puppet. All of them have their unique set of strengths and weaknesses, which we’ll explore further.
Short Background on Terraform, Ansible, and Puppet
Before we begin comparing the tools, see a brief description below:
- Terraform (released 2014 – current version 0.12.8): Hashicorp developed Terraform as an infrastructure orchestrator and service provisioner. It is cloud-agnostic, supporting several providers. As a result, users can manage multi-cloud or multi offering environments, using the same programming language and configuration construct. It utilizes the Haschorp Language and is quite user-friendly as compared to other tools.
- Ansible (released 2012 – current version 2.8.4): Ansible is a powerful tool used to bring services and servers into the desired state, utilizing an assortment of classes and configuration methods. Additionally, it can also connect to different providers via wrapper modules to configure resources. Users prefer it because it is lightweight when coding is concerned, with speedy deployment capabilities.
- Puppet (released 2005 – current version 6.8.0): Puppet is one of the oldest declarative desired state tools available. It is server/client-based, one which refreshes the state on clients via a catalog. It uses “hieradata”, a robust metadata configuration method. It enforces system configuration with programs through its power to define infrastructure as code. It’s widely used on Windows or Linux to pull strings on multiple application servers simultaneously.
Orchestration vs Configuration Management
Ansible and Terraform have some critical differences, but the two do have some similarities as well. They differ when we look at two DevOps concepts: orchestration and configuration management, which are types of tools. Terraform is an orchestration tool. Ansible is mainly a configuration management tool (CM); they perform differently but do have some overlaps since these functions are not mutually exclusive. Optimized for various usage and strengths, use these tools for situations.
Orchestration tools have one goal: to ensure an environment is continuously in its ‘desired state.’ Terraform is built for this as it stores the state of the environment, and when something does not function properly, it automatically computes and restores the system after reloading. It’s perfect for environments that need a constant and invariable state. ‘Terraform Apply’ is made to resolve all anomalies efficiently.
Configuration management tools are different; they don’t reset a system. Instead, they locally repair an issue. Puppet has a design that installs and manages software on servers. Like Puppet, Ansible also can configure each action and instrument and ensure its functioning correctly without any error or damage. A CM tool works to repair a problem instead of replacing the system entirely. In this case, Ansible is a bit of a hybrid since it can do both, perform orchestration and replace infrastructure. Terraform is more widely used. It’s considered the superior product since it has advanced state management capabilities, which Ansible does not.
The important thing to know here is that there is an overlap of features here. Most CM tools can do provisioning to some level, and vice versa, many provisioning tools can do a bit of configuration management. The reality is that different tools are a better fit for certain types of tasks, so it comes down to the requirements of your servers.
Procedural vs. Declarative
DevOps tools come in two categories that define their actions: ‘declarative’ and ‘procedural.’ Not every tool will fit this mold as an overlap exists. Procedural defines a tool that needs precise direction and procedure that you must lay out in code. Declarative refers to a tool ‘declaring’ exactly what is needed. It does not outline the process needed to gain the result.
In this case, Terraform is wholly declarative. There is a defined environment. If there is any alteration to that environment, it’s rectified on the next ‘Terraform Apply.’ In short, the tool attempts to reach the desired end state, which a sysadmin has described. Puppet also aims to be declarative in this way.
With Terraform, you simply need to describe the desired state, and Terraform will figure out how to get from one state to the next automatically.
Ansible, alternatively, is somewhat of a hybrid in this case. It can do a bit of both. It performs ad-hoc commands which implement procedural-style configurations and uses most of the modules that perform in a declarative-style.
If you decide to use Ansible, read the documentation carefully, so you know its role and understand the behavior to expect. It’s imperative to know if you need to add or subtract resources to obtain the right result or if you need to indicate the resources required explicitly.
Comparing Provisioning
Automating the provisioning of any infrastructure is the first step in the automation of an entire operational lifecycle of an application and its deployment. In the cloud, the software runs from a VM, Docker container, or a bare metal server. Either Terraform, or Ansible is a good choice for provisioning such systems. Puppet is the older tool, so we’ll take a closer look at the newer DevOps programs for managing multiple servers.
Terraform and Ansible approach the process of provisioning differently, as described below, but there is some overlap.
Provisioning with Terraform:
There are certain behaviors not represented in Terraform’s existing declarative model. This setup adds a significant amount of uncertainty and complexity when using Terraform in the following ways:
The Terraform model is unable to model the actions of provisioners when it is part of a plan. It requires coordinating more details than what is necessary for normal Terraform usage to use provisioners successfully.
It requires additional measures such as granting direct network access to the user’s servers, installing essential external software, and issuing Terraform credentials for logging in.
Provisioning with Ansible:
Ansible can provision the latest cloud platforms, network devices, bare metal servers, virtualized hosts, and hypervisors reliably.
After completing bootstrapping, Ansible allows separate teams to connect nodes to the storage. It can add them to a load balancer, or any security patched or other operational tasks. This setup makes Ansible the perfect connecting tool for any process pipeline.
It aids in automatically taking bare infrastructure right through to daily management. Provisioning with Ansible, allows users to use a universal, human-readable automation language seamlessly across configuration management, application deployment, and orchestration.
Differences between Ansible and Terraform for AWS
AWS stands for Amazon Web Services, a subsidiary of Amazon, which provides individuals, companies, and business entities on-demand cloud computing platforms. Both Terraform and Ansible treat AWS management quite differently.
Terraform with AWS:
Terraform is an excellent way for users who do not have a lot of virtualization experience to manage AWS. Even though it can feel quite complicated at first, Terraform has drastically reduced the hurdles standing in the way of increasing adoption.
There are several notable advantages when using Terraform with AWS.
- Terraform is open-source, bringing with it all the usual advantages of using open-source software, along with a growing and eager community of users behind it.
- It has an in-built understanding of resource relationships.
- In the event of a failure, they isolate to dependent resources. Non-dependent resources, on the other hand, continue to be created, updated, and destroyed.
- Terraform gives users the ability to preview changes before being applied.
- Terraform comes with JSON support and a user-friendly custom syntax.
Ansible with AWS:
Ansible has offered significant support for AWS for a long time. This support allows interpretation of even the most complicated of AWS environments using Ansible playbooks. Once described, users can deploy them multiple times as required, with the ability to scale out to hundreds and even thousands of instances across various regions.
Ansible has close to 100 modules that support AWS capabilities. Such as Virtual Private Cloud (VPC), Simple Storage Service (S3), Security Token Service, Security Groups, Route53, Relational Database Service, Lambda, Identity Access Manager (IAM), AMI Management and CloudTrail to name a few. Also, it includes over 1300 additional modules for managing different aspects of a user’s Linux, Windows, UNIX, etc.
Here are the advantages when using Ansible with AWS.
- With Ansible Tower’s cloud inventory synchronization, you will find out precisely which AWS instances register despite no matter how they launched.
- You can control inventory by keeping track of deployed infrastructure accurately via their lifecycles. So, you can be sure systems manage properly, and security policies execute correctly.
- Safety in automation with its set of role-based access controls ensuring users will only have access to the AWS resources they need to fulfill their job.
- The same simple playbook language manages infrastructure and deploys applications on a large scale and to different infrastructures easily.
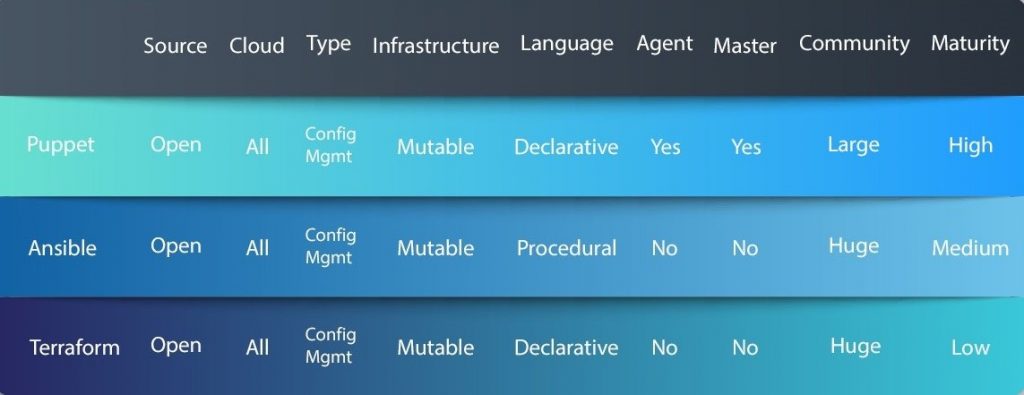
Comparison of Ansible, Puppet, and Terraform
Puppet, Terraform, and Ansible have been around for a considerable period. However, they differ when it comes to set up, GUI, CLI, language, usage, and other features.
You can find a detailed comparison between the three below:
| Point of Difference | Ansible | Puppet | Terraform |
| Management and Scheduling | In Ansible, instantaneous deployments are possible because the server pushes configurations to the nodes. When it comes to scheduling, Ansible Tower, the enterprise version, has the capabilities while it is absent in the free version. | Puppet focuses mainly on the push and pulls configuration, where the clients pull configurations from the server. Configurations must be written in Puppet’s language. When it comes to scheduling, Puppet’s default settings allow it to check all nodes to see if they are in the desired state.
|
In Terraform, resource schedulers work similarly as providers enabling it to request resources from them. Thus, it is just not limited to physical providers such as AWS, allowing its use in layers. Terraform can be used to provision onto the scheduled grid, as well as setting up the physical infrastructure running the schedulers. |
| Ease of Setup and Use | Ansible is simpler to install and use. It has a master without agents, running on the client machines. The fact that it is agentless contributes significantly to its simplicity. Ansible uses YAML syntax, written in the Python language, that comes built-in most Linux and Unix deployments. | Puppet is more model-driven, meant for system administrators. Puppet servers can be installed on one or more servers, while the puppet agent requires installation on all the nodes that require management. The model is thus a client-server or agent-master model. Installation times can take somewhere around ten to thirty minutes. | Terraform is also simpler to understand when it comes to its setup as well as usage. It even allows users to use a proxy server if required to run the installer. |
| Availability: | Ansible has a secondary node in case an active node falls. | Puppet has one or more masters in case the original master fails. | Not Applicable in Terraform’s case. |
| Scalability: | Scalability is easier to achieve | Scalability is less easy to achieve | Scalability is comparatively easily achieved |
| Modules | Ansible’s repository or library is called Ansible Galaxy. It does not have separate sorting capabilities and requires manual intervention. | Puppet’s repository or library is called Puppet Forge. It contains close to 6000 modules. Users can mark puppet modules as approved or supported by Puppet, saving considerable time. | In Terraform’s case, modules allow users to abstract away any reusable parts. These parts can be configured once and can be used everywhere. It thus enables users to group resources, as well as defining input and output variables. |
| GUI | Less developed is Ansible’s GUI, first introduced as a command-line only tool. Even though the enterprise version offers a UI, it still falls short of expectations suffering from syncing issues with the command-line. | Puppet’s GUI is superior to that of Ansible, capable of performing many complex tasks. Used for efficiently managing, viewing, and monitoring activities. | Only third party GUIs are available for Terraform. For example, Codeherent’s Terraform GUI. |
| Support | Ansible also includes two levels of professional support for its enterprise version. Additionally, AnsibleFest, which is a big gathering of users and contributors, is held annually. The community behind it is smaller when compared to Puppet. | Puppet has a dedicated support portal, along with a knowledge base. Additionally, two levels of professional support exist; Standard and Premium. A “state of DevOps” report is produced annually by the Puppet community. | Terraform provides direct access to HashiCorp’s support channel through a web portal. |
Three Comprehensive Solutions To Consider
After looking at the above comparisons, Ansible is quite beneficial for storage and configuring systems in script-like fashion, versus the others. Users can efficiently work in short-lived environments. It also works seamlessly with Kubernetes for configuring container hosts.
Puppet is more mature when it comes to its community support. Puppet has superior modules that allow it to work more as an enterprise-ready solution. Its robust module testing is easy to use. Ansible is suitable for small, temporary, and fast deployments. Whereas, Puppet comes recommended for longer-term or more complex deployments and can manage Docker containers and container orchestrators.
Terraform performs better when it comes to managing cloud services below the server. Ansible is excellent at provisioning software and machines; Terraform is excellent at managing cloud resources.
All three have their benefits and limitations when designing IAC environments for automation. Success depends on knowing which tools to use for which jobs.
Find out which platform can best help redefine the delivery of your services. Reach out to one of our experts for a consultation today.