9 Best Practices for Email Security
Are you concerned about how cybercrime and data theft could affect your business operations? Does your business intend to spend a significant percentage of its budget on security this year?
If the answer is yes, you need to focus at least some of your efforts on securing your email communications.
There are hundreds of different threats out there at the moment, and any of them could damage your brand reputation. We saw this happening with companies that lost vital client data in recent cyber breaches, and that received much bad press for doing so.
Most of these breaches happen due to poor email security practices. The latest Data Breach Investigations Report (DBIR) suggests that 66 percent of malware installed on breached networks come through email attachments. There is a decent chance that anyone who penetrates your email system might manage to steal passwords or any other sensitive data.
Read this post and ensure you take the email security tips onboard and put them into action as soon as possible. The last thing you want is for hackers or the programs they might create to cause issues for your business.
Best email practices for business, Train your employees
The information in this section will offer fundamental security tips while highlighting email security measures you should have in place already. If you are not taking the actions mentioned below, you need to start doing so as soon as possible.
The measures you are going to read make up the very least companies need to do to protect themselves from common threats like hacking.
1. The Best Email Security, Use strong passwords that are unique
There is no getting away from the fact that weak passwords are never going to protect your company from data theft or hacking. You need to take a look at all the passwords and phrases people in your office use right now. You then need to improve them based on the tips mentioned below.
A secure password is almost impossible to guess without some insight. The only way a hacker will break into your system is if they use specialist password-guessing software that will run through millions of combinations.
The more complex the password, the more time it takes for the software to figure it out. The passwords that follow the best practices outlined below would take 200-500 years to break.
Essentials for a strong password:
- Use upper and lower case letters
- Use numbers and special characters
- Use random numbers and letters rather than words
- Never use your birthday, hometown, school, university, or brand name
- Avoid common letter-number substitutions
- Think in terms of phrases rather than words
If you are still not sure why strong passwords matter and how to apply these rules, Edward Snowden sums this up nicely in this video. Your organization needs a solid enterprise password management plan.
2. Using two-tier authentication
It might sound technical, but using two-tier authentication is quite straightforward. Moreover, it is guaranteed to add an extra layer of protection to your emails. There are often options within your email client that will enable you to add that service. You can also download specialized software or use a different cloud email provider if you cannot add two-tier authentication with the system you use at the moment.
The concept is simple. But it is an excellent data loss prevention practice as it makes life much more difficult for hackers and those who wait to sneak a peek at your emails.
Even if a criminal manages to guess or retrieve the passwords to your account, two-tier authentication will mean that the individual will still require a code to get your messages and cause issues. That code is usually sent to your phone via a text message. Do not make the mistake of sending it to your computer because you never know who is watching.
Two-tier authentication is one of the best ways to protect social media or a web application from a data breach. It also works with virtually any cloud storage service you might be using.
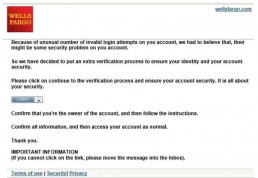
3. Watch out for phishing emails
Before we can help you to keep your eyes peeled for phishing attacks, it is sensible to explain the nature of those domains for people who have not encountered the term in the past. Phishing is a straightforward concept many hackers will use to steal email and account information by tricking individuals into handing over their details.
The process usually works like this:
- The hacker sends emails that contain a link to a site you know.
- The victim clicks the link and finds themselves looking at a familiar website. That is often their bank or something similar, but the site is fake.
- The victim then enters their email address and password to log into their account.
- The fake phishing site steals the email and password before passing it back to the hacker.
When someone at a company falls victim to advanced malware attacks and phishing emails, it can become a disastrous situation.
That is especially the case in instances where the business uses the same passwords for everyone in their office. Hopefully, that should help to highlight how important it can be that you develop strong and unique passwords for all your workers.
A phishing attack is no longer as apparent as it used to be. Hackers are becoming increasingly sophisticated, making it more difficult to identify it unless you pay attention to details.
Just consider this example of a phishing email pretending to be a bank. How long would it take you to figure out it was a scam?
4. Never open unexpected attachments without scanning
Sometimes your business will receive emails that contain file attachments. That is not a problem if you notice the email is from your accountant, and you know you are waiting for them to send information. It is rarely an issue when the emails come from customers or clients either.
However, occasionally, your company will get a phishing email. Such emails come from an unknown source and contain files for you to open.
Of course, you cannot go putting all those messages straight in the trash because many of them might be genuine. For that reason, you need to invest in email threat protection systems. You should consider using antivirus and anti-malware email security software to scan all correspondence, as well as implement advanced spam filters. That should let you know if there is any need for concern when opening the email attachment.
If the program tells you there is a problem, you can delete the message, block the sender, and secure your system. That way, you can prevent a business email compromise and a subsequent data security breach.
5. Do not let employees use company email addresses for private messages
You need to limit the chances of hackers targeting your email system. The best way to achieve this goal is to implement advanced endpoint security solutions and ensure that only work-related messages are hitting your computers.
Discourage all your employees from using company communication systems to talk to friends, shop online or do anything that does not relate to their job roles. It is possible that you could end up attracting cybercriminals if you fail to follow that advice.
You are not awkward when you put measures like that in place. You are just protecting the interests of your operation and everyone it employs.
It is vital to note the same rules will apply to you as the business owner. Never make the mistake of using your professional accounts for anything other than work.
If people in your office need to access their personal accounts for any reason during the working day, tell them to do so using their smartphones and their mobile internet.
Do not allow anyone to connect a smartphone to your office WiFi system if you want to stay under the radar and avoid hackers.
To ensure they understand the reasoning behind this, consider organizing company-wide security awareness training. That can be an excellent way to educate them on the importance of data protection, share email security tips, and raise their awareness of the current cyber threats and technology trends.

6. Scan all emails for viruses and malware
Remember that antivirus malware and software we told you to get a few paragraphs ago?
Well, in most instances, you can use it for far more than just scanning attachments before you open them. Some of the top virus screening solutions on the market will also scan all incoming emails and check them for vulnerabilities as they come into your inbox. The software will present you with an alert if there is any reason for concern. You can usually quarantine the affected email before it has enough time to cause any damage.
Those who use hosted email services will often find their provider follows the same cloud security procedure and lets you know if there is anything dodgy about messages landing in your inbox.
It is your responsibility to check your security settings and enable specific options. Sometimes you have to pay for that service as an extra feature, verify your account now and make sure your provider scans all emails with antivirus solutions.
If you do not have protection, now is the best time to add it.

7. Never access emails from public WiFi
Public WiFi is never secure, and there are many ways in which hackers can steal all the information that passes through a network.
Indeed, criminals only require a laptop and basic software to hack into public WiFi networks and then monitor all the traffic. If you or anyone at your company access emails via a service of that nature, you will make it easy for anyone with the will to steal your passwords and view your sensitive data. That could result in a targeted attack further down the line.
If people need to access their messages outside of the office, there are a couple of options on the table that should not make your operation vulnerable to data theft.
Firstly, if unable to connect to a secure WiFi, your employees could use their smartphone and mobile internet.
That is much more secure than any public WiFi service, and the move should protect your cloud data and your interests.
Secondly, you might consider paying for mobile internet dongles that workers can use with their laptops outside of the office. Both of those options tend to work well, and they should help to protect all your company emails.

8. Use a robust spam filter
One of the best things about cloud-based email services these days is that they tend to come with excellent spam filters.
Indeed, even Google through their service Gmail manages to remove most unwanted messages from your inbox. Make sure you turn your spam filter on or look for a provider who offers better security solutions than those you have right now. Spam filters are an email specialist’s way of attempting to sort the wheat from the chaff and ensure you are not bothered by hundreds of marketing messages and “do you want to lose weight” emails every week.
You can often change the settings on your spam filter to block out any emails that contain specific words or phrases. That can come in handy if you know about some scams going around at the moment because you can block most of the keywords. That should help you to prevent any of your employees from opening a spam email that contains dodgy links or malware by accident.
9. Never click the “unsubscribe” link in spam emails
Let us presume for a moment that an email managed to get through your spam filter and antivirus programs. You open the message and then discover that it looks like a phishing scam or something similar. There is an unsubscribe link at the bottom of the page, and you wonder if it is sensible to click that to prevent further emails from the unwanted source. Whatever happens, make sure you never click that unsubscribe link. Hackers will often place them in emails in an attempt to fool you.
If you decide to click the unsubscribe link or do it by mistake, there is a reasonable chance you will land on a phishing site that will attempt to steal any information it can gather. The link could also provide hackers with a backdoor into your system, and that is why you must never click it. Just mark the message as spam, so your spam filter picks it up next time around, and hit delete.
Remember Safe Email Security Practices
Now you know about email security best practices, nothing should stand in the way of protecting your business.
Combining these with some business data security practices will go a long way regarding your business continuity. You need to make sure all your employees understand this advice too for the best results.
Arrange a meeting or training session where you can hammer the points home and ensure everyone grasps the concept of email data theft and protection.
Whatever you decide, never forget that hackers are everywhere these days. They will stop at nothing to steal your data. Protect yourself with robust email security.
Recent Posts
38 of the Best Information Security Podcasts For IT Professionals
When was the last time you had a chance to hear a world-renowned expert discussing cybersecurity?
If you do not work at a prestigious tech or security company, chances are you have never had an opportunity to talk to an industry thought leader. However, those eager to learn about the subject from pros can always turn to information security podcasts for help.
Information security and cybersecurity podcasts are a favorite way to obtain security news or gain information about the latest security threats.
They are also a great way to learn about some of the most significant incidents, as well as about best practices for staying ahead of the threats. Their central value is the opportunity to learn directly from industry peers and leaders.
Many podcasters bring years of experience, a different spin on things, and valuable insight to those who do not usually have access to such data. In the article below, we made a summary of our favorite security podcasts from industry professionals, analysts, and others who strive to educate, inform, educate, and break down endless hours of reading through extensive government and industry standards and regulations.
Sure you will benefit from reading those documents and articles. Podcasts add to the vast amount of resources available to gain valuable information. It is much easier to absorb several hours of reading material into short and easy-to-understand episodes. In addition to this, you can use these podcasts to gain the latest security news in about half an hour to an hour. Even just getting some highlights on recent security trends and other cybersecurity news will help enhance your understanding of the current trends.
While we will explore various security podcasts, it is important to remember they can be categorized into two main categories. There are those run by individuals giving their experience and opinion on security news and updates, and those run by companies developing security products or services. Both are great resources of knowledge as they present experienced professionals and highly relevant themes.
Security podcasts help you achieve one of the most critical aspects of security, which is staying up to date on the latest trends and best business practices. News feeds, recent articles by industry leaders, blogs, and Tweets are a great way to keep up but do not forget the value a podcast can bring.
. Everything on this list will help you keep in touch with the latest and greatest podcasts to follow for the hottest security and cybersecurity news, events, and trends.
1. Security Now
Hosts: Steve Gibson and Leo Laporte
Security Now is a weekly podcast where the hosts discuss trending issues in computer security. Steve and Leo started the podcast in 2005, which means this is one of the longest running security podcasts.
Their latest 90-minute episode#650 Cryptocurrency Antics talks about the slow progress on the Intel Spectre firmware update front, the unsuspected threat of hovering hacking drones, and much more.

2. OWASP
Host: Mark Miller
Open Web Application Security Project (OWASP) is a series of that highlights projects and people from around the world. The recent HackNYC 2018: Preview with Kevin E. Greene is a talk session with Mr. Greene about the current state of software security and how each of us plays a role in the security of modern software. As a seasoned software architect and security expert, Mr. Greene offers a unique insight into the topic.
3. Risky Business
Host: Patrick Gray
Over 5,000 subscribers cannot be wrong about this information security podcast featuring news and in-depth interviews with industry leaders. Risky Business began in 2007, making it another long-running weekly podcast that features talks by security industry professionals. #487 features guest Katie Mossouris on her recent Senate Subcommittee testimony.
4. Defensive Security Podcast
Hosts: Jerry Bell and Andrew Kalat
This weekly information security podcast features recent high profile cybersecurity breaches, data breaches, malware infections, and the latest intrusions to identify lessons we can learn and apply to in the organizations we strive to protect. Defensive Security episode #211 discusses the malware that wreaked havoc at the Pyeongchang 2018 Winter Olympics, some suggestions on preventing cyber attacks, and much more packed into a 45-minute session.
5. Security Weekly
Host: Paul Asadoorian
Security Weekly covers multiple IT security stories, vulnerabilities, hack threats, security research, and a series of other themes relevant to information security. In their weekly episode #548 that was recorded on 19 February 2018, they featured an interview with Steve Tcherchain, the CISO and Director of Product Management at XYPRO Technology. Steve highlighted various security topics XYPRO is working on such as some of the latest high-level security breaches, layered security, Active Directory, and more.
6. Unsupervised Learning
Host: Daniel Miessler
Daniel focuses on information security, technology, and people in short 15 to 30-minute Unsupervised Learning broadcasts every week. The episode #113 was a particularly interesting one for everyone who wanted to learn more about Parkland tampering, Android Cryptojacking, Spyware Hacking, Password Dating, and much more.

7. Down the Security Rabbithole
Hosts: Rafal Los, James Jardine, and Michael Santacangelo
If you are curious about some industry-specific security issues, Down the Security Rabbithole is quite likely covering them. In their latest episode #284, the hosts discuss Managed Security Service Provider issues, offering constructive feedback for the providers from an enterprise perspective.
8. The Southern Fried Security
Hosts: Andy Willingham, Martin Fisher, Steve Ragan, Joseph Sokoly, and Yvette Johnson
The popular The Southern Fried Security aims to fill the gaps between technical security and Security Now. Their episode #192 on security waste tackles the problems associated with having complexity in our environments and needing more or staff or current staff to stretch themselves thin to support different tools.
9. Data Driven Security
Hosts: Jay Jacobs and Rob Rudis.
Jay and Rob cover all aspects of data analysis and visualization in this monthly podcast. Data Driven Security covers data security with industry leaders in the data science world and professionals in information security.
Episode #30 was an exciting one covering the 2016 Verizon Data Breach Investigations Report focused on data visualizations.
10. Exploring Information Security
Host: Timothy De Block
In his latest release How to become a social engineer – Part 2, Timothy is joined by Chris Hadnagy to discuss various aspects of becoming a social engineer.
Here he also featured resources, college courses, and toastmasters. As you know, social engineering is one of today’s more challenging threats to cybersecurity, but it is only one of the topics Exploring Information Security has covered so far.
11. The Cyber Jungle
Hosts: Ira Victor and Samantha Stone.
The Cyber Jungle‘s Ira is a digital forensic analyst while Samantha is an award-winning journalist.
One of their latest episodes #397 includes an interview with Fred Kaplan, the author of “Dark Territory: The Secret History of Cyberwar.” In addition to the conversation, they also explain how experts were able to fool Windows 10 facial recognition with a photo and South Korea’s Cryptocurrency Exchange.

12.Brakeing down Security
Host: Bryan Brake
Bryan is a CISSP certified cyber security professional with a passion for sharing his insights about security, legal matters, compliance, and privacy. His latest Brakeing down Security podcast broadcasted on 13 February 2018 discussed securing mobile devices and CMS against plugin attacks. Bryan started podcasting in 2013 and he loves sharing the latest news and trends about various security topics.
13. Hacker Public Radio
Host: Security community
A new take on podcasts, Hacker Public Radio is crowd-sourced and features news, insights, and views from community members. The latest episode by Nicolas Steenhout discusses various areas of automated and manual testing.
14. Open Source Security Podcast
Hosts: Josh Bressers and Kurt Seifried
The hosts cover multiple information security topics focused on open source software. While this podcast is one of the newest ones on the list, that started in 2016 and over 35 issues have already been released. Episode 81 discusses bug bounties and fixing flaws, market forces in security, future expectations, and how humans perceive threats.
15. PVC Security Podcast
Hosts: Paul R. Jorgensen, Chris Maddalena, Tracy Z. Maleeff, and Edgar Rojas
The hosts of PVC Security Podcast deliver a different perspective and expertise for various matters related to security and leadership. While the hosts decided to end regular broadcasting in August 2017 to move on to other things, 99 sessions are available to listen to. They cover an incredible amount of security news and content. For example, the one on Poutine Security discusses the Canadian Law Librarian Conference and why CyberSecurity is so hard. It also included a view on IT and security professional’s mental health.

16. SANS Internet Storm Center
Hosts: Multiple.
This SANS-hosted podcast brings cybersecurity news from the SANS Internet Storm Center. One of their latest episodes deals with Password Spraying for AD accounts by author Johannes B. Ullrich, Ph.D.
17. Threatpost Digital Underground
Host: Michael Momoso
This podcast is produced by Kaspersky Lab and has been operating for the past decade. Threatpost News Wrap on Nov. 10 is a memorable broadcast where Mike Mimoso and Tom Spring reflect on information security news and Chris Valasek and Charlie Miller’s return to security. It also talks about the fake WhatsApp download and offers a deep dive into the most recent cloud-based storage leaks.
18. The Shared Security Podcast
Hosts: Tom Eston and Scott Wright
This podcast includes debates about the trust in people, apps, and technology. Both hosts include information security, privacy, mobile devices and apps, the Internet of Things, and more.
The episode posted on 19 February 2018 covers topics of Instagram social stalking, crypto jacking, and Equifax breach updates.
19. Crypto-Gram Security Podcast
Hosts: Dan Henage and Bruce Scheier
The Crypto-Gram Security Podcast covers a variety of security-related themes.
The latest episode posted on 15 January 2018 discusses specter and meltdown attacks against microprocessors, Susan Landau’s book “Listening In,” and Daniel Miessler on My Writings about IoT Security.
20. The Cyber Wire
Host: David Bittner
David discusses a variety of security news in small segment summaries to deliver essential detailed information about the security landscape. On Cyberwire, David covers SWIFT phish bait, GRU Hacking looks east, Crypto jacking, and Election cybersecurity.
His interests include a wide array of themes and trends, so each new broadcast offers an exciting view of the threat landscape.
21. Security Current
Host: Multiple
The information produced in this cybersecurity podcast includes collaboration from CISCOs for CISOs. This podcast has multiple hosts and industry leaders who share their expertise on IBM Cloud, SaaS Global security topics, and other security issues that matter to CISCOs.
The session SC 111 deals with the complexity of enterprise networks and the hundreds to thousands of firewall rules, devices, and routers across an on-premises and hybrid cloud environments.

22. Data Breach Today
Hosts: Multiple staff members
This security podcast covers data breach detection and security concerns that have made national headlines. For instance, Tom Field talked about the Russian Indictments in recent political news on 16 February 2018. This discussion covered the significance and impact of the recent announcement that 13 Russian nationals and three Russian entities were indicted for the alleged meddling in the 2016 presidential campaign.
23. The Security Ledger
Hosts: Paul Roberts, Rob Vamosi
This podcast was founded in August 2012 as an independent security news outlet that offers in-depth insights from security thought leaders Paul and Rob. The hosts tackle the latest infosec problems that threaten businesses and individuals. A recent episode #84 discusses jailbreaking voice assistants and features Rapid7’s CEO Corey Thomas on hacking diversity.
24. Hak5
Hosts: Darren Kitchen and Shannon Morse
This podcast focuses on open source software, network infrastructure, pen testing, and more Hak5 is syndicated by Discovery Digital Networks and produces other shows such as ThreatWire, Metasploit Minute, TekThing, and HakTip. The issue #161 discusses a wide variety of trends, including Bitcoin for gaming PCs, Video Gear, and Fingbox Home Network Security.
25. Root Access
Host: Josh Pyorre
Sponsored by Cisco and hosted by Josh Pyorre, an experienced security researcher. The podcast focuses on privacy and security in-depth through different events that change the course of the Internet and how it impacts daily life. One of the recent broadcasts, S2: E5: Analyzes how Quantum computers, networks, and encryption are positioned to change the world. Two of the field’s experts reflect on how quantum technologies will advance society.

26. Naked Security by Sophos
Hosts: Chester Wisniewsi and members of the Sophos team.
Offering different insights on industry news, security breaches, and other stories of interest to privacy and security professionals. The recent episode #267 includes an interview with Claudio Stahnke from Canalys Channel Forums about the viewpoint of security from the channel partner’s perspective. The emphasis is on security as a service (SaaS) and the Internet of Things (IoT).
27. Tripwire Security Slice
Host: Shelley Boose
This podcast aims to offer informative opinions, valuable resources for security professionals, and various security related news. In Inaugural BSidesPhilly Event a Smashing Success, she covers a renowned security event in Philadelphia that had over 200 attendees and 30 presenters who brought engaging talks on multiple Infosec topics. One of the favorite sessions included “Attacker’s Perspective: A Technical Demonstration of an Email Phishing Attack” by Zac Davis.
28. The Social Engineer Podcast
Hosts: Chris “loganWHD” Hadnagy and the Social-Engineer Inc. Team.
Broadcasting on the second Monday of every month, The Social Engineer Podcast is a regular show with a different security theme every time. It focuses on social engineering, ransomware, and other risks and trends of interest to the security community. Recently, Penning the Future with JJ Green offered an interesting overview of what it means to pen the future, how we can help the next generation, and how to stay safe in an increasingly insecure world.
29. SurfWatch Cyber Risk Roundup
Hosts: SurfWatch Labs Team
This podcast delivers cyber risk intelligence solutions to help businesses understand and act on cybersecurity risks. It is delivered weekly by the SurfWatch Labs team focused on how cybercrime impacts modern business. In one of the latest episodes, Talking the Threat Intelligence Mind Map and how it can help organizations, it deals with operational intelligence, tactical intelligence, digital risk monitoring, as well as the people and processes behind them.
30. Silver Bullet Podcast
Host: Gary McGraw
Started in April 2006, Silver Bullet features in-depth conversations with security experts. The guests of Silver Bullet include a mix of academics, business people, authors, government officials, and technologists. Their show #142 features Craig Froelich who discusses the 2018 CISO report.

31. The Virtualization and Cloud Security Podcast
Hosts: Mike Foley and Edward Haletky
This podcast is an open forum to explore all about the bare metal cloud, virtual environments, cloud computing security, and bare metal virtualization benefits.
Episode #191, Grey Market, features Michael White, field product manager for Veeam, talking about how much money there is in cybercrime. White hat hackers, the dark web, and the Grey Market are all components of the attack market and the more businesses know about them, the better they can prepare.
32. Cydefe
Hosts: Raymond Evans and Micheil Fairweather
The goal of Cydefe is to help people understand the cyber landscape. Among their recent debates, the one titled Hacker Methodology 101: Recon Basics offers an insight into about the recon phase of an assessment. The episode covers benefits that can be gained from passive recon in the environment you assess. It also briefly covers some of the tools that could be used in the process, including dig, whois, nslookup, dnsdumpster, and Google dorks, all of which paint a picture of the environment and possible targets for assessment.
33. DevelopSec
Host: James Jardine
The aim of DevelopSec is to deliver awareness of security-related trends and threats. Some of the recent podcasts touch on topics such as steps to securing your database, interviews with various security professionals, Apple Sign-in Bug Take-Aways, vulnerable third-party components, and more. Recently, they covered OWASP Top 10 2017 thoughts to help improve your security program.
34. The Security Orb Show
Host: The Security Orb team
SecurityOrb is a research organization dedicated to information security, incident response, and privacy awareness. The Security Orb Show features interviews with industry professionals whose experience within their realm of information security includes cyber protection, digital privacy, and online safety. Their episode with Marcus J. Carey discussed vThreat and attack-simulation.

35. Cybersecurity Interviews
Host: Douglas A. Brush
Cybersecurity Interviews is a weekly podcast dedicated to picking the minds of security influencers, thought leaders, and individuals in the cybersecurity community. Episode #44 features a talk with James Carder in Automate As Much as You Can. James is the CISO of LogRythm with over 19 years of corporate IT security and consulting experience. On this occasion, he talked about security governance, risk strategies, confidentiality, integrity, and availability of information assets.
36. 2 Minute CyberSecurity Briefing
Host: Scott Schober
This podcast features the latest cybersecurity news, tips, reviews, and interviews with industry experts in short 2-3 minute briefings. If you are interested in understanding the scope of risk that fitness trackers pose to the U.S. Pentagon, listen to this month’s Why Does Pentagon Hate Fitness Trackers?.
37. Recorded Future
Hosts: Multiple
This up-and-coming security podcast includes talks about current events, technical tradecraft, and insights on the big picture of threats in the cybersecurity realm.
Episode #44: Takeaways from the Gartner Threat Intelligence Market Guide gives a close look at the market and a comprehensive overview of relevant findings and use cases.
38. Tenable
Hosts: Paul Asadoorian, Ron Gula, Jack Daniel, and Carlos Perez
Sponsored by Tenable, featuring various security-related topics such as news on latest security vulnerabilities. In their talk about NIST Cybersecurity Frameworks, the discussion covers Gartner’s recent finding that about 30% of all US organizations in both the private and public domains have adopted the NIST Cybersecurity Framework and that an additional 50% will select the framework by 2020.
Get FREE IT security consulting with phoenixNAP’s experts!
Recent Posts
Google SSL Certificate Requirements: How it Affects Your Site
For several years now, Google has been forcing websites to implement SSL certificates. It all started with its 2014 HTTPS Everywhere campaign whose goal was to raise awareness of the value of SSL certificates. SSL later became a Google ranking signal to further encourage its adoption.
Currently, over two-thirds of all websites are unencrypted, and Google is taking the next steps to change that.
As of July 2018, Google SSL requirements were enforced by flagging sites without SSL as unsafe in Chrome.
This update goes beyond adding it to its list of ranking factors only. It fundamentally changes the way web users think about their online security.
SSL certificates are designed to make users feel secure while using the internet. Without them, you could be jeopardizing your business, as well as your customer’s sensitive data. This article will explain what an SSL certificate is, how it works, how to install one, and more.
What is an SSL Certificate?
Put simply, an SSL certificate is a text file with encrypted data that you install on your server. This allows you to secure/encrypt sensitive information and communications between your website and your audience. Many think of it as their electronic passport.
SSL stands for ‘Secure Sockets Layer,’ and when a website owner has one, all data passed between web browsers and servers remains private and encrypted.
Without valid certificates, websites cannot establish a secure connection with web servers, meaning that users will not be digitally connected to a cryptographic key. This puts your company’s and your customers’ information at risk, especially considering current cybercrime trends. As a result, the lack of SSL and HTTPS could potentially damage your brand image.
People will avoid purchasing from you or even signing up to your newsletter through fear of having their details stolen. Your conversions will plummet.
One of the most important things in business is to make customers feel like they are visiting a trusted, reliable website where making purchases is safe. SSL establishes a secure connection which then reassures your visitors using visual cues.
Seeing the lock icon or green bar when visiting a site can automatically make a visitor trust your company and take the next step in making a purchase.
How Does a SSL Certificate Work?
When a browser accesses a secured website, the browser and the web server establish a connection. The process is called an ‘SSL handshake,’ but this handshake cannot be seen by the user and happens within a few seconds. What you can see as a user is a green padlock in the URL address bar of your browser which signifies secure data transfer.
Three keys are used to set up a secure connection: public, private, and session keys. Anything encrypted with the public key can only be decrypted with the private one and vice versa. Encrypting and decrypting using the private and public keys can take a lot of power. Because of this, they are solely used during the SSL Handshake.
When this action takes place, this creates a symmetric session key, which is then used to encrypt all data transmitted from the sites once the secure connection is established.
Here is a better idea of how SSL policies work in simple terms:
- The browser connects to a web server via a secured connection. The browser requests that the server identify itself.
- The server then sends a copy of the SSL Certificate, including the server’s public key.
- The browser checks the root against a list of trusted authorities. It looks to establish that the certificate is unexpired and that the common name is valid for the site it is connecting to.
- If the browser trusts the data it received, it creates, encrypts, and sends back a symmetric session key using the server’s public key.
- The server decrypts the symmetric session key using its private key. It then sends back an acknowledgment encrypted with the session key to begin the encrypted session. This happens instantaneously.
- Both the Server and Browser now encrypt all of the transmitted data using the session key.
The three keys mentioned above work together to establish an encrypted connection. The certificate also contains what is called the “subject,” which is the identity of the website owner. It holds the following information:
- Name of the holder
- Serial number and expiration date
- Copy of the holder’s public key
- Digital signature of the certificate-issuing authority
Knowing how SSL works can further help you understand why they are so important.

Why is SSL Important To Google?
SSL certificates are important for various reasons, for both business and website visitor. To get an idea of why it could be essential for your site, you can ask yourself the following questions:
- Does your site take text inputs in the form of login panels, contact forms and search bars?
- Is your website on HTTP://?
If yes, then you need SSL to prevent risk. Without one, you stand to put your visitors in danger and eventually lose them.
More reasons why this is important:
Encrypt sensitive information – without an HTTPS connection, the computer in between you and the server will be able to see sensitive information, like credit card numbers and passwords. With an SSL, this information is unreadable except to the server the data is being sent to.
Credit card numbers, social security numbers, and login details can be transmitted securely with HTTPS in place.
Provides data protection from online hackers and criminals – online criminals are great at identifying any weakness in networks. They usually strike gold at the point where information is being transmitted. Without the ability to encrypt traffic, you run the risk of being hacked, having information stolen, and more.
Build more trust with customers – building trust with your customers is one of the most important parts of running a successful company in 2018. With trust comes customer loyalty. SSL security reassures customers that their information is safe with just a few visual cues. You boost your business credibility on top of this.
This is also relevant because:
- HTTPs gives a stronger ranking on Google.
- You will create safer experiences for your customers.
- You will build customer trust and improve conversions over time.
- You will protect both sensitive customer and internal data.
- You will encrypt browser-to-server and server-to-server communication.
- You will increase the security of your mobile and cloud apps.
- You will protect against phishing.
Google said so – There are numerous reasons supporting the fact that this is important, but perhaps the most critical one is ‘because Google said so.’ Nobody wants to experience a drop in search rankings in Google or a negative impact on their business or online reputation. Without SSL, this is likely to happen.

How Does SSL Protect my website?
Establishing SSL can vary depending on your browser and other factors. Your host will likely have options to enable it for you. Some hosts have a one-click option that allows you to auto-generate free SSL certificates and implement one easily.
There are both paid and free certificates. Usually, there are no differences between the two when it comes to the level of encryption offered. However, if you need more support, then a paid one could be beneficial for you. If you do not need support, the free one will do the job.
Here is how to get one:
- Gain administrator access to your web server.
- Make a note of the operating system and server software you use.
- Get the instructions for your server at the CertBot website. Instructions vary from server to server.
- Follow the steps to generate your certificate and ensure you enable auto-renew.
- Pay attention to any mixed content warnings using plugins or manual fixes.
- Verify your HTTPS pages in Google Search Console.
- Submit a new sitemap with your updated URLs.
Once you have all the data, you are ready to install it on your server. Instructions vary depending on the server used. Alongside this, you will install an intermediate certificate that will establish the credibility of your SSL. It does this by incorporating it into your CA’s root certificate.
Implementation and Validation Steps
There are many kinds of SSL certificates, all of which will add credibility to your site and build trust. The one you choose will depend on your needs, so they must be considered first. If you have an E-commerce website, for example, an Extended Validation option is recommended for the best results.
Three different types are as follows:
- Domain Validation or DV
- Organization Validation or OV
- Extended Validation or EV
To download, wait for your SSL certificate to be delivered to your email inbox or download it from your account yourself. Then you can begin installing it on your web server. Bear in mind you will need full access and control of your web server for this to go as smoothly as possible.
You will need information about the following before you can install it:
- IP address
- User password (SSH key authentication)
- Server username (admin or sudo privileges)
- Software (IIS, Apache, Nginx, etc.)
- Operating system and version number (i.e., Debian 7, Ubuntu, CentOs, etc.)
Begin by creating a CSR (Certificate Signing Request), and purchase a certificate if you haven’t already. A certificate authority can validate and process your request once you have done this.
When you have what you need, connect to your server and install a tool to generate the certificate. Send SSH commands once logged in For Mac, use Terminal, an inbuilt application.
For Windows, you can download PuTTY.
When validated, the certificate will be sent over through email, and instructions can be followed based on your server. Ensure you make a backup copy and store it in a secure place, just in case. Below you will find detailed instructions on installing it for various servers:
Install SSL on Apache CentOS 7
Installing SSL Certificate on Internet Explorer 7.0 or later
Installing SSL Certificate for Internet Explorer or Chrome
Install SSL On Microsoft, Mac, and More

Upon downloading the file, will also need to download an intermediate certificate.
This is needed to complete the ‘certificate trust chain.’ The intermediate one must be installed on the server with the primary one for website security purposes.
If the former is not installed to the web server along with the latter, the chain will not be complete, and the site will not be listed as secure.
Remember, registered authorities must provide a known root certificate before their connection can be trusted by SSL-enabled applications. Note that for some servers, like Microsoft, the intermediate certificates are conjoined with SSL. Once you have yours installed, it is a good idea to check that everything is working as it should be.
You can find free SSL installation diagnostic tools online. Utilize them to ensure your installation went as planned.
In addition to this, you may also want to make sure Google knows your website moved from HTTP to HTTPS. To do that, you would need to submit a new sitemap in Google Webmaster Tool and set proper redirects from your HTTP pages. It might also be a good idea to do a comprehensive technical SEO audit at this point to make sure everything is set up correctly. After all, a drop in Google rankings due to improper implementation is the last thing you need.
Conclusion: SSL Certificates are no longer optional with Google
Purchasing and installing SSL is no longer something that online business owners can ignore. Google chrome is set to mark sites as insecure if they do not follow the steps above.
Sites without secure connection will be labeled as ‘Not Secure,’ and perhaps even blacklisted. Those all-important visual cues will not be in a surfer’s address bar to reassure visitors to your site, and you will likely lose them because of this.
Without an up-to-date, validated SSL certificate, you can only damage your position in Google search results. However, there is more to it than making the search engine like you. Without a secured connection, you are putting your whole business and brand reputation at risk.
Recent Posts
Crypto-Mining Malware: Don't Be The Next Victim, Protect Your Systems
The rising popularity of cryptocurrency mining has been profitable not only for those investing in them but also for cybercriminals.
Crypto-mining malware is a serious threat to enterprise CPU power and other resources. In January, Coinjournal.net estimated that 23% of organizations are at risk of having their resources drained by this emerging threat.
The primary targets are media streaming and file sharing services that use extensive CPU and GPU server power that a hacker can exploit.
However, other companies are at risk too. Just recently, the security firm RedLock reported the hack of Tesla’s cloud servers. Redlock found that Tesla was operating under hundreds of open-source systems that could be accessed online without requiring a password. With this, hackers were able to hack Tesla’s Amazon cloud.
While not being a threat to customers’ privacy, cryptocurrency mining malware can cause significant damage to an organization’s IT systems.
The Coinjournal article above points out that the malware can use up to 65% GPU resources. That can mean a significant loss of operational productivity and, consequently, money.
What is Cryptocurrency Mining?
Crypto-mining involves validating transactions and adding encrypted blocks to a blockchain. Cryptocurrency miners solve hashes to establish a valid block connection and then receive rewards, or coins. The more blocks that are mined, the harder it becomes to solve the hash.
The mining process can take years with a basic home computer. To resolve this issue, miners use customized computer hardware to speed the process and form mining pools where several collections of computers work concurrently to calculate the hash.
The more resources in the pool, the better the chance of mining new blocks and collecting more rewards. It is this search for more computing resources that lead miners to exploit networks.

Enterprise security risks Of Crypto Malware
Crypto-mining malware poses a severe threat to enterprise security.
In all cases of mining, software is very processor intense, which means it can slow machines. CPUs running with a high load for an extensive amount of time will raise electrical costs and shorten the life of the processors.
Native mining software can access the operating system in a similar way to how botnet delivered malware exploits a machine. The presence of native mining software could mean a device was compromised.
Organizations, primarily enterprises, need to ensure they are using secure cloud solutions. They should choose secure cloud environments with advanced safety systems and hardware-enhanced security.
Hackers are looking to exploit software vulnerabilities to harness the free source of computing power
Concealed cryptocurrency mining programs are set to operate when CPU cycles aren’t being used, which makes them hard to detect. These programs attempt to disable security software, which leaves your CPUs vulnerable to other attacks. This is why you should take all security steps to block anyone from using your CPU resources.

Protect Your Companies Systems From Crypto-mining Malware
It is hard to tell the precise amount of cryptocurrency is mined through crypto-mining.
Anything over zero is too much for your enterprise to lose. It is only going to get worse as this exploit is still in its infancy. Hackers view crypto-mining as a fast, cheap, and easy way to profit.
There are a few easy ways you can protect your systems:
Malware Protection Starts With Every Network Device
-
Endpoint security – protect your employees’ browsers.
Protection Google Chrome Browser
If your employees primarily use Chrome, you can install Security Chrome extensions to block crypto-mining within the browser.
No Coin is a free extension and can be a safe and reliable method to control how a website interacts with Chrome. The way it works is that as soon as you visit a site, No Coin detects and displays any crypto-mining activity. You will be notified with a red symbol if the extension detects “coin mining malware” on the page.
Another useful extension you can add for Chrome is minerBlock.
Similar to No Coin, minerBlock displays a red notification icon on the upper right-hand side of the browser in the address bar that notifies you of suspicious activity.
Opera Malware Settings With NoCoin
Opera comes with a built-in setting to block crypto-mining activity. Just go to your Settings in Windows or Preferences in macOS > Basic > Block ads and then go to the Recommended lists and check the NoCoin (Cryptocurrency Malware Protection) checkbox.
NoScript in Firefox
For you Mozilla Firefox fans out there, you can add JavaScript-blocking extensions such as NoScript.
Be cautious with this one as it is aggressive and might break connections with websites you try to visit as it will disable all scripts running on the page.
2. Block crypto-mining domains
The manual method of blocking specific domains that is not too intrusive is to edit hosts files and redirect them to 0.0.0.0.
You can do this in both Windows and Linux. For Windows, you will have to go to:
C:\Windows\System32\drivers\….
and edit the host file to include 0.0.0.0 coin-hive.com to the end.
In Linux, open the hosts file by running this command: sudo nano /etc/hosts and add 0.0.0.0 coin-hive.com to the end.
3. Reinforce mobile security policies
With viruses and malware often coming from employees’ mobile devices, you may want to reevaluate your current mobile security policies.
Ensure your employees are using protected devices for accessing company network remotely. Organize security training programs to warn them about the threat and educate them about the best practices.

Conclusion: Crypto-mining Malware
As a relatively new threat, crypto-mining malware is bringing new risks for enterprises. Your systems are vulnerable unless you take preventative measures.
Implement best practices that can minimize the risk of infection.
Protection starts at the workstation level by adding a few browser extensions or making a couple of selections in your browser settings.
Proactive protection of your physical machines and your networks, the less vulnerable you are to security exploits that can cause damage to your data or hardware.
Recent Posts
What is Object Storage? How it Protects Data
Object storage architecture inherently provides an extra security layer for your data. As such, it can be an ideal solution to avoid ransomware threats.
First, let’s start with explaining the differences between traditional storage solutions and object storage.
Object storage vs. Block Storage
With traditional block and file storage, information is typically stored in file systems that allow you to locate each item by following the defined path to that file.
If you need to share data among a group of users through a network, it is best to do so over network-attached storage (NAS). This will work great on a local architecture network (LAN) but might not be so great via wide area network (WAN).
While managing several NAS boxes is not that hard; doing so with hundreds of boxes makes things difficult. When the number of files and users grows substantially, it takes a lot of time and effort to find a particular file. In addition to this, you might even reach your storage file-limit sooner than expected.
Traditional storage was not designed for terabytes of data, so there is a good chance of data loss in the first two years.
Prominent characteristics of traditional storage include:
- Files are shared via NAS or SAN
- Each edit deletes the previous version of that file, and it cannot be restored on the device
- Connecting NAS boxes for scaling
- A file system is located by following its destination path
- Initially, it is straightforward to set up
- Configured with standard file level protocols, like NTFS, NFS, etc.
When talking about cost-considerations, you need to plan your requirements over time carefully. Having too much storage means you will pay for resources you do not need. On the other hand, not having any buffer room might put you in a tight spot when faced with no storage space.
Ransomware was explicitly created to take advantage of the shortcomings of block-and-file storage by encrypting files and locking out users.
Malicious software can even circumvent a volume snapshot service (VSS). That means that you would not be able to recover shadow versions either.
How Object Storage Works
Object storage creates immutable sets of data. It includes versioning and elaborate geo-diverse data replication schemes.
When I say immutable, I mean that data cannot be modified once created. To further clarify, it can be modified, but each edit is saved as a new version.
Object Storage uses flat-file data architecture and stores data in unchangeable containers or so-called buckets. Data, along with its metadata and unique ID, is bundled up in objects.
IT admins gain more control over their objects by assigning a virtually unlimited number of metadata fields. This is an inherent advantage over traditional storage. Thanks to metadata and the unique identifier that lets you locate objects easily, object storage works perfectly for unstructured data such as 4K videos, medical archives, or other large files.
Due to its lack of data hierarchy, object storage features scalability which could not have ever been achieved with block storage.
Advantages of object storage include:
- Continually scalable without any significant performance degradation
- Perfect for high volumes and large files
- Safer thanks to immutable data
- Capable of versioning
- Features replication schemes
- Good at maintaining data integrity
- Cost-effective
- Excellent for dealing with ransomware
- Perfect for file-sharing
- Unparalleled when it comes to metadata
This may sound like object storage is the best thing ever. However, the truth is that this approach is quite specific and not a good fit for every use case.
For example, object storage does not work well for frequently modified data, as there is no guarantee that a GET request will return the most recent version of the object. Furthermore, since objects are accessed via REST API, you may need to do a little bit of coding to make direct REST-based calls.
Even if it is not a one-fits-all solution, object storage does address problems that cannot be solved efficiently with traditional storage.
Object storage is perfect for:

1. Big Data
Big data is a huge (no pun intended) part of 21st century IT. It provides an answer to the ever-growing demand for more storage. In most cases, big data is unstructured and varies in the file type.
Let’s take for example Facebook and the social media phenomenon. This is a relatively new and non-traditional source of data that are being processed by analytics apps. The results are massive amounts of unstructured data. In such conditions, an object storage environment offers the necessary scalability, security, and accessibility.
2. Creating Backup Copies
I cannot stress enough the fact that it is an excellent fit for frequently used, but seldom modified data.
If you are not using a supported backup utility, such as Veeam Cloud Connect of R1Soft, you can leverage object storage for backing up your data. To do this, you would need to use the right cloud backup solution or software, such as Cloudberry Backup.
3. Archives
An archive is not the same as a backup. Backups are files that are very rarely used, and we turn to backups only if something goes wrong. Archives are similar but serve a different purpose.
Compared to backups, archives are accessed more frequently and serve to store and quickly obtain large quantities of data. Businesses with various backgrounds may store medical files in the cloud, engineering documents, videos, and other unstructured data.
After a while, it may become increasingly difficult to find an individual file, not to mention secure all data. However, with object storage IT admins can quickly secure and maintain data integrity, all the while providing easy access.
4. Media & Entertainment
It has never been easier to share information, whether you are on the receiving or giving end. However, nobody seems to think about the resources necessary to store such vast amounts of unstructured data. S3 object storage is especially useful for this use case, as it is easy to build entire front-facing apps based on its API. Perfect for media & entertainment.
5. Hosting a Static Website
Object storage has a suitable architecture for hosting static websites thanks to its virtually infinite scalability. This means it will scale automatically to your traffic needs.
Public users will access your data via the web, just like with any other hosted website. However, it must be noted that no personalized data can be displayed based on cookies and there is no support for server-side scripting. So, there are some limitations.
6. Streaming Services
With the emergence of online video streaming services and the internet becoming globally available, keeping chunks of data in a single location no longer makes much sense. You need fast global access, unlimited storage (a 1h raw 4k video can take as much as 130GB!), scalability, durability, and excellent metadata management.
Object storage technology ticks all the right checkboxes, and it helps that it was built for HTTPS. The best thing is that you can use object storage for several use cases at the same time.
Ransomware, the Role That Object Storage Vendors Can Play
Official statistics claim that ransomware took in $209 million in 2016 alone, while the cost of downtime was even higher. Datto’s report found that 48% of businesses lost critical data when faced with such threats. This is a loss that cannot be easily measured in dollars.
In 2018, ransomware continued to dominate the world of cybersecurity. 6 out of 10 malware payloads in Q1 were ransomware. From WannaCry to NotPetya and BadRabbit, we can safely say that ransomware threats have marked the year behind us. Furthermore, we can safely assume that ransomware has become the biggest security threat any organization or individual may face in the cyber realm.
Recent Posts
Business Data Security: 57 Experts Reveal Their Best Advice
While many businesses are still assessing the odds of being breached, hackers keep improving their data intrusion methods.
The reality is that no company is safe. Even small businesses are targets and increasingly so. Earlier Ponemon Institute research report showed that 50% of surveyed SMBs had been breached in 2017. Only 14% were found to be able to mitigate risks, which is an alarmingly small figure.
In the enterprise ecosystem, millions of dollars are being invested in security systems, staff, and training. Such investments usually pay off, but failures still happen due to simple mistakes and overlooked basic steps.
These trends illustrate the increasingly complex, unpredictable, and confusing cybersecurity landscape.
To help you understand how you can avoid a devastating scenario in your business, we asked entrepreneurs like you to share their best data security tips. They were an incredible help in creating this article, and we are grateful for their time and effort.
Take a look at what they said!
1. Data Protection: the devil in the details
Like any other business, our company wants to keep our data safe. We did it all – advised employees to use different passwords for their different accounts, don’t save them on the PCs, don’t share sensitive information with outside people, (if they are not sure if something fits these criteria, better not discuss it). We did everything to be secure.
Or did we?
Something escaped our attention.
You know how there are different sharing options on Google Drive documents, sheets, etc.? Well, now it appears that people occasionally just copy the shareable link to give it to colleagues. That is not OK. This way, the link can go into the wrong hands.
And while you may think that there isn’t any sensitive information on this document or sheet, why risk it?
It is pretty disturbing when viewing a private document with disclosed information, then some Anonymous Hippo appears and starts highlighting text. There’s no way of tracking who that is. Learn from our mistakes.
Check your sharing settings.
Veronika Adriane, Marketing and Social Media Expert, Fantastic Services Group
Veronika Adriane is a social media specialist and marketing entrepreneur working with Fantastic Services Group. She is passionate about her job, and is always on her quest for improvement.
2. Layer your business data security strategy
Many businesses cannot afford to think outside the box when it comes to data security. They need reliable, cost-efficient solutions with a strong ROI for everything, especially data security. As an IT firm working with SMB, we advise our clients to build data protection in layers because not one single tactic is bulletproof. Three best tactics:
- Double Up Your Firewall. Instead of buying a firewall, rent it (known as Firewall-as-a-Service or FWaaS) because most companies provide two machines for the price of one, so you have instant redundancy without the extra expense. Without that redundancy, your firewall is a single point of failure that can bring down your network or leave it unprotected until your IT person can install and configure a new firewall.
- Use Email Filtering with ATP (Advanced Threat Protection). Email filtering scans inbound emails for potential threats found in both attachments and links, preventing malware from entering your network. (Most viruses enter a network from someone unwittingly opening an attachment with a virus embedded in it.) ATD means your system gets notified of a virus within an hour of being found on the internet to protect your network better. This service costs just $2/month per user.
- Human Firewall. Your employees are your best line of defense and your biggest vulnerability. Train them to look out for suspicious emails and requests, to lock server room doors, use passcodes on their smartphones and workstations, and to report things that look suspicious. We send our clients a monthly simulated phishing email to test them, measure their susceptibility, and to improve our training.

Stephen Tullos, Team Leader,My IT
Stephen Tullos is My IT’s Cybersecurity Team Leader, a retired Army Ranger, active Air Force Reserve in Cybersecurity. He is certified as an Ethical Hacker, Mile 2 CVA for Cybersecurity, CompTIA Security+, and Microsoft Certified Professional (MCP).
3. Plan for the worst-case scenario.
It is not a question if something will go wrong but when. That is why every small business should plan for the worst-case scenario it can think of. For many, that would be a complete loss of all data. To mitigate that risk, develop an appropriate backup plan that involves keeping offsite backups and testing data integrity on a regular basis.
Next, consider the network perimeter. That means reducing the ability for an attacker to penetrate the network by ensuring a firewall is in place, backed up by appropriate data security software and complemented by virtual private network access for all remote employees.
Lastly, given how many successful attacks rely on human error or lack of knowledge, you need a robust employee security training and awareness program. It will ensure that all employees know how to spot common and active attacks, such as ransomware and phishing.
Lee Munson, Security Researcher at Comparitech.com
At Comparitech, Lee writes a wide range of articles, covering security topics of relevance to both SMBs and home users. He is an InfoSec Professional (training, awareness & comms), security researcher, PR, and award-winning blogger.
4. Consider cloud solutions.
Protecting your data as a small business is crucial. One data breach could spell disaster, but there are ways your company can avoid this type of situation.
- Move to some type of cloud service. This helps protect important data from both outside hackers and internal breaches.
- Educate employees on security protocols. Train your staff on appropriate use of the Internet while at the workplace, and the importance of strong passwords.
- Create a strong firewall for your internet connection to prevent perimeter intrusions.
Charlie Trumpess, Marketing Manager at Modern Networks
Over the last decade, Charlie Trumpess has worked for a number of B2B technology companies across EMEA. He’s a Member of the Chartered Institute of Marketing (MCIM), a CIM Chartered Marketer, qualified gamification designer and an experienced channel marketer.
5. Keep your data organized.
Before you rush to a technical solution, sit down and think about what data resides on your systems and where.
Next, create a little spreadsheet that divides the type of data you hold into levels of importance. Customer data such as credit card numbers should sit right at the top of your list, for example. Secure the most critical, sensitive data first.
Less important data will need less security. You will also want to think about policies and user access privileges.
Good security requires in-depth defense. Ensure you have endpoint security on every business computer and mobile device, implement proper patch management and strong passwords policies, establish proper access controls and regular data backups.
If the worst happens, being able to recover your data quickly might make a difference as to whether a hack is a minor inconvenience or a major disaster.
Create containers and even hidden containers using disk encryption software, so you can keep important data encrypted on a laptop or PC even when it is open. Full disk encryption is great if someone steals your PC when it is switched off, but when it is open and running the encryption is also off, providing no protection against a cyber-attack. By using containers, you can isolate sensitive data and keep it encrypted while you work.

Tyler Riddell, Vice President of Marketing, eSUB
Tyler Riddell is the Vice President of Marketing with over 15 years of experience in Marketing, Product Management, Advertising, and Public Relations.
6. Don’t let your employees be the weak links.
- Your weakest security link might not be your networks or infrastructure. It might be your people. A well-meaning employee is a hacker’s best friend. Educate all employees on social engineering prevention. Make regular education an ongoing part of your security plans.
- You would be surprised how many companies spend big bucks on aggressive digital defenses but leave their side door propped open for the delivery guy. Don’t take physical security for granted; pay just as much attention to locked doors and perimeter security as you to firewalls and encryption.
- Never assume you’re too small to be a target for a security breach. Bad actors aren’t always looking for the biggest target to take down. Instead, they prey on the unassuming and unprepared. Have a security strategy in place that matches your organization’s size, industry and specific vulnerabilities.

Jeremiah Talamantes, President and Managing Partner of RedTeam Security
Jeremiah has been in the IT industry for nearly 20 years and is the creator of The PlugBot Research Project, a foray into the concept of a hardware botnet. He is an active security researcher and adjunct professor at Norwich University, College of Graduate Studies in Information Security & Assurance.
7. Deploy the right software-level protection
Cyber attacks against small businesses have been increasing steadily over the past five years.
According to a report by Keeper Security and the Ponemon Institute, 50 percent of small businesses have been breached in the past 12 months.
Small business websites, employee email accounts, and customer data are attractive targets for hackers since they often have more digital assets than an individual consumer, but less security than a large organization. Hackers are very much aware that small businesses are less careful about security,” notes John Swanciger, Manta CEO, adding his top tips for businesses to protect themselves.
- Business owners should deploy antivirus software like Norton or Avira to create a defense against most types of malware. To provide an extra layer of protection, small businesses should look into firewalls to prevent unauthorized data access. Some operating systems like Microsoft Windows come with built-in firewalls. Data backup solutions ensure any information compromised during a breach can be recovered from an alternative location. To protect sensitive data like employee, customer and financial information, business owners should also consider encryption software. And, be sure to perform software and web platform updates regularly. Outdated computers and systems are more prone to crashes and security gaps, so taking the time to check for updates and install them periodically is important, even if it seems like a hassle at the time.
- Educate and train your employees to ensure they are aware of the harmful consequences of cyber attacks. Teach them how to recognize the signs of a data breach, as well as best practices to securely use the company’s network. Along with this, implement company-wide security policies to ensure all of your employees are on the same page when it comes to cybersecurity. For instance, institute a password policy, which would require you and your employees to change their password regularly, as well as avoid sharing passwords, usernames and other sensitive, secure information via email.
- Serve your website over HTTPS, especially for any pages that collect information or passwords. HTTPS encrypts traffic so attackers can’t eavesdrop and intercept passwords and other critical business information. To implement HTTPS, you’ll need to obtain an SSL certificate.
John Swanciger, CEO, Manta
John Swanciger is a seasoned technology executive with vast experience in team building, product marketing, and strategic partner development. As CEO, he leads Manta to strengthen its current offerings, while expanding products and services for small business owners.
9. Know your enemy – assess the threats and implement appropriate data security protection.
Knowing exactly what risks you face can help you choose the right system of protection.
- Be realistic about the threats you face. Don’t waste time protecting data which is, for practical purposes, already public, such as your company’s credit rating or size.
- Don’t gild the lily. You have adequate security already built into your accounting application. You can add passwords to almost any document or spreadsheet without spending a dime on additional software, or create a virtual private network to safeguard data coming in from your road warriors with an old PC and some free open-source software.
- Don’t be afraid to try new things. Your email client already has end-to-end encryption capability built in. All it takes to use it is a couple of encryption certificates that cost less than $50/year. PGP is a reliable alternative, with free applications available for Linux, and free or low-cost Windows/Mac options.
William Horne, Editor, The Telecom Digest
William is the Editor of The Telecom Digest, the oldest e-zine on the Internet. A former telecommunications engineer at Verizon, he currently runs his own consulting business, helping Small Office/Home Office clients to maximize productivity.
10. When in doubt, don’t cheap out on security.
Limit what you put online. Pay someone who knows what they are doing to shut off unnecessary services on your servers/web host. At minimum, set up a Software Firewall/IPS and a Web Application Firewall. Most inexpensive servers and hosts come with many options open by default which should not be left on.
Encrypt, Encrypt and Back Up. Get a trusted and signed SSL certificate and encrypt all traffic to and from your web server end-to-end. Encrypt and/or salt and hash any unique information that is stored, passwords, payment data, even email address. Back up all of your data on your server regularly through a security provider.
It is always too good to be true. – Phishing is one of the most common ways in when hacking small business. Email filters are usually not as effective. Small business owners and entrepreneurs are open to emails they receive as they look for partnerships and other opportunities to grow their business. Host your email on a separate service or set of servers. And scrutinize emails you receive, think twice or three times if it seems to good to be true. It might end up being really bad.
When in doubt, don’t cheap out on Security, pay a service provider that specializes in small business cybersecurity. The investment will be immensely cheaper than the average cost of an incident, which is more than $200 per customer record exposed.

Pieter Van Iperen, Founder, Code Defenders
Pieter Van Iperen is a Founding Member of Code Defenders, a collective that protects the long tail of the internet, an Adjunct Professor of Code Security at NYU, a Certified Penetration Testing Engineer (Ethical Hacker) and a Certified Secure Web Application Engineer. He is a veteran programmer and security expert.
11. Choose security solutions based on your business needs.
- Know how long your business could survive without any of your data before it begins to suffer client loss or service delivery promises. Then build your system recovery plan around that window. Whether it is a ransomware attack that corrupts all of your data or a fire that destroys your computer network, how fast you can recover your business operations is going to be key to your survival. Your recovery system/Disaster Recovery Plan has to focus on your Recovery Threshold, and you have to test it periodically to ensure it will work when you need it the most.
- The #1 vulnerability to your business data privacy and security is your staff falling for a hacker ploy on the web or via e-mail. Ongoing security awareness training for your employees is the best way to reduce risk in your organization. Socially engineered e-mails are the biggest infection delivery method affecting business today. You have to invest in keeping your employees up-to-date on the most current threat types that they will encounter. Spam filters will NOT catch everything, so keeping your employees current on the latest hacker tactics is critical.
- Anti-Virus software isn’t enough to protect your business anymore. There are eight different ways that hackers can exploit your defenses. You need to supplement your defenses with enhanced firewall Gateway protection, off-premises spam scrubbing, and periodic security inspections by professionals that know what to look for. You also need appropriate use policies for people who use your network to reduce risks of infection from outside websites, social media or personal e-mail services.
Jeff Hoffman, President, ACT Network Solutions
Jeff Hoffman is the President and Security Evangelist at ACT Network Solutions in suburban Chicago. ACT has been providing innovative IT Security Solutions to the financial, legal and healthcare industries for over 29 years.
12. Have these three types of security training in place.
Making your employees strong links in the cybersecurity chain requires more than just implementing general security policies. They need different types of training to be able to recognize and deal with different threats. Below are some of the vital ones:
- Security Awareness Training
Get employees to focus on themselves; don’t harp just on security awareness that affects the company. Make workers understand that business security is about *them* too, not only the elusive bigwigs. Talk to them about the most common scams and tricks cybercriminals use, and how to protect themselves at home, with tools such as firewalls and wireless VPNs.
- Phishing Simulation Training
After presenting information about security awareness, come up with a scheme to set up a situation where employees are given the opportunity to open a very alluring link in their email. This is called a “phishing simulation.” This link will take the worker to a safe page, but you must make the page have a message, such as “You Fell For It.” You should also make sure that these emails look like a phishing email, such as adding a misspelling.
- Social Engineering Awareness Training
Consider hiring a professional who will attempt to get your staff to hand over sensitive business information over the phone, in person, and via email. This test could be invaluable, as it will clue you into who is falling for this.

Robert Siciliano, Identity Theft Expert and CEO of IDtheftsecurity.com
Best Selling Author ROBERT SICILIANO is serious about teaching you and your audience fraud prevention and personal security. His programs are cutting edge, easily digestible and provide best practices to keep you, your clients and employees safe and secure.
13. Don’t underestimate the likelihood of an attack.
Small businesses often lack necessary security policies and practices because they underestimate the likelihood of cyber attacks striking their companies.
Manta, an online resource for small businesses, surveyed over 1,400 small business owners and found 87% of owners do not feel they are at risk of a data breach. However, 12% had previously experienced a breach and, what’s even more concerning is that about 1 in 3 small business owners have no controls in place!
Every organization has sensitive data, including customer information, employee records, intellectual property, and medical records that they must protect. Here are three steps to follow:
- Understand the lifecycle of data in your business – How can you prevent an attack if you do not first know where vulnerabilities lie?
- Explore these vulnerabilities — Determine what the data is, how it is being created or collected, how it is maintained, stored and shared while it is being used and how it should be disposed of.
- Implement best practices that will protect these valuable assets — Now that you are better situated to detect potential points of attack, it’s vital that you take all the necessary precautions to prevent future harm.
Success, without security, can easily turn into a catastrophe.
Dana Simberkoff, Chief Risk, Privacy and Information Security Officer of AvePoint
Dana is responsible for AvePoint’s privacy, data protection, and security programs. She manages a global team of subject matter experts that provide executive level consulting, research, and analytical support on industry trends, standards, best practices, concepts, and solutions for risk management and compliance.
14. Go beyond securing your computers.
Data security is not limited to your computers.
Human error or malicious intent is just as much of a threat, if not more so. Therefore, your first and most important step in securing your business’ data is to thoroughly check the backgrounds of any new hires, including references and criminal background checks.
In addition to this, you should make sure to safely and securely shred any old documents before you dispose of them. Hard copies of files that are thrown out or stolen are one of the leading causes of security breaches, particularly identity theft and credit card fraud.
Another important thing is to stay up to date. Many small businesses neglect their software updates, especially if they do not have a dedicated IT team. When a software company pushes out an update, it is often to improve security. Not updating your installation can make you vulnerable to attack as hackers exploit known issues in older versions.
Similarly, only download and install software from known and trusted sources. It may be tempting to save some money by downloading a cracked version of the software you need, but these often have malicious malware embedded that leave your computer wide open to attack.

Gavin Graham, Staff Writer, Fit Small Business
Gavin is a staff writer at Fit Small Business, focusing on creating Buyer’s Guides on a variety of small business topics. Gavin has been at the intersection of content management and creation in the digital marketing world for over ten years.
15. Develop a security culture.
According to Reg Harnish, CEO of GreyCastle Security, the following three tactics are key to maximizing business data safety:
- Get a Risk Assessment. Unlike most large companies, small businesses can be financially wiped out after a cyber attack, so it is critical to understand cyber risks right away. Fortunately, in a small business, there is much less to assess than in larger companies — the surface area is smaller. However, resources are thinner, so it is critical to identify the company’s most valuable assets so as not to exhaust resources protecting worthless data. There are only five critical assets worth protecting: bank accounts, credit cards, identities, intellectual property, and reputation. Once those are identified, focus on protecting them.
- Create a Culture of Security. In all businesses, people are the most critical cybersecurity risk. It is impossible to eliminate human error. However, small business owners can minimize risk by consistently and continuously educating and testing employees regarding desired cybersecurity behaviors. Training should include how to identify phishing emails, how to develop unique passwords for each application or website, and how to implement two-step verification. Business owners working with third-party vendors, such as payroll companies, accounts payable and others, should spell out their position on cybersecurity in all contracts and require regular audits for compliance.
- Prepare for the Worst. For every Fortune 500 company, there are thousands of small businesses, which means cyber attacks on small businesses are much more prevalent. Moreover, smaller businesses’ cyber protections tend to be less established or less mature than those of than big companies, simply because the companies are typically younger, smaller and have less money. This highlights the importance of resilience for small business owners. Resilience is the ability to prepare for and recover rapidly from disruptions. Since it’s easier to play offense than defense, small businesses should aggressively train employees and regularly audit people, networks, and devices.
Reg Harnish, CEO of GreyCastle Security
Reg Harnish is the CEO of GreyCastle Security, a cybersecurity consulting firm dedicated to the management of cybersecurity risks. Harnish is an author, speaker and trusted authority in the cybersecurity world, and was named North America’s Cybersecurity Consultant of the Year by the Cybersecurity Excellence Awards.
16. Follow basic steps for advanced protection.
STEP 1: The first step is easy: Get some. Don’t make the mistake of thinking you are too small to be attacked. Hackers prey on this, making you even more vulnerable to having customer records, employee data, and other privileged information stolen. 62 % of small businesses suffering attacks go out of business within six months; don’t become part of that statistic!
STEP 2. Back up your data. Automate backup so that employees do not have to think about it.
STEP 3. Think about physical security and managing business continuity. The recent hurricanes, floods, and wildfires provide ample evidence that backing up your data to another location is a must. Maybe the cloud, or servers at two securely networked business locations. Or, a dedicated server on the site of your managed services provider or IT consultant. Do not walk around with USB sticks and portable drives that can easily be lost or corrupted.
STEP 4. Keep current with updates and “patches.” Vendors regularly update their devices against the latest ransomware and other exploits. Keeping up with these updates is a simple thing that can avert disaster.
STEP 5. Don’t go it alone. It is not a question of whether you need business security but how much you need. You likely have anti-virus and anti-malware programs running and perhaps basic firewall capabilities. These are a good start, but if you have mobile workers, guests using your Wi-Fi, or need to comply with regulations for protecting data (HIPAA for example), you need more.
Engage a trusted IT consultant to help think through securing networks and data, and educating employees. Sometimes simple, inexpensive measures like whitelisting or blacklisting Internet sites, or defining clear rules for who can access specific resources can make all the difference and cost little or nothing.

Glenn Chagnot, Vice President of Marketing, Uplevel Systems
Glenn Chagnot is VP, Marketing at Uplevel Systems, provider of managed IT services infrastructure solutions to IT consultants serving small business. A prolific writer and speaker, Glenn works with IT consultants and managed services providers (MSPs) to bring affordable, business-class IT to small companies.
17. Ensure security on both provider’s and your end.
There is a tremendous risk to SMBs of significant (if not devastating) financial outcomes caused by the rise of cyber attacks. SMBs typically lack the in-house security expertise to both understand the new types of attacks that occur and protect against them appropriately, and also have limited budgets for enterprise-class solutions. A few tips Arlen suggests include:
- Look to your internet provider to offer robust DNS-based network protection and device security. When protections are built into the ISP network based on DNS query data, attacks can be identified and thwarted before they do harm. DNS security is the broadest layer of protection to have for every device on the network and is the easiest to implement.
- Enforce end-user best practices by requiring highly secure passwords before allowing devices to connect to the network.
- For retail or other businesses that process payments, they should segment their payment processing tablets/machines onto their own VLAN. They should then turn off all internet access to that VLAN, providing it ONLY to the payment processor. This approach would have prevented the Target and other major retail breaches that have occurred in the past.
Arlen Frew, GM of Security & Applications for Nominum
As General Manager for Nominum’s security and applications portfolio business, Arlen oversees the company’s go-to-market strategy including sales, engineering, support, and product management, as well as extending its OEM technology licensing business to the high-growth area of security as a service (SECaaS).
18. Use analytics to develop a tailor-made security program.
Every company’s security program has different threats. There’s no one rule or one guideline to watch out for. There are a few different ways to help reduce data security risks.
- Using security analytics can help you see what threats your business faces and any possible changes in the threat landscape. Any security programs should be updated based on these insights.
- Having your company operate with an extranet (private server) can help reduce these risks as your private documents between your employees and clients are not accessible through the Internet. It is a great added security measure and helps ease communications between your company and clients as well.
- Make sure your deleted files are properly removed from your computers. Overwriting the deleted files is the only way to properly remove any trace of the file from your computer. If a person knows their way around computers, they can easily find deleted information that wasn’t overwritten.

Peter Carson, President of ExtranetUserManager
As the founder and President of ExtranetUserManager, Peter brings over 20 years of technology consulting, certified engineering skills, database design, and application development – combined with strong communication, analytical planning, and business skills.
19. Review your password and information sharing policies.
Even in settings where there are no advanced business security systems, some basic best practices need to be implemented. Gregory Morawietz, an IT Security Specialist, highlights the following:
- Have strong passwords. Have complex and long passwords, change passwords as often as you can. Don’t expose your passwords in files on your desktop, post-it notes on your desks, etc.
- Don’t give out your personal data, information or anything via email, phone or text. Refrain from giving out any other personal data on your Facebook, LinkedIn or otherwise that might compromise your identity.
- Get the information out to your company through a meeting, hand-out, training video, etc. Make an effort to have some training that will disseminate information for security awareness. Communication is the key to success of security awareness.
Gregory Morawietz, VP of Operations, Single Point of Contact
Gregory Morawietz is an IT Security Specialist with over twenty years’ of network and security experience. He has worked with hundreds of firms on improving IT environments, consulting and integrating technology for the enterprise network.
21. Don’t overlook the basics.
As a small business, there are some important steps that need to be taken to ensure the security of your data. The following are the easiest ways to avoid security breaches:
- Keep computers up-to-date: *Keep all computers equipped with the newest in security software, operating systems and web browsers.
- Keep Wi-Fi networks secured: *Make sure your Wi-Fi networks are secure, encrypted and hidden. One way is to set up your wireless access point or router so it will not broadcast the network name, known as the Service Set Identifier (SSID). Also be sure to password-protect access to the router and disable UPnP.
- Train employees on security basics: *Set basic security practices and policies that employees should adhere to such as requiring appropriate internet use, strong passwords, and the detailed penalties for violating those policies. Establish rules for protecting customer information and other internal data.
- Use firewall security for your Internet connection.
Lindsey Havens, Senior Marketing Manager, Phish Labs
Lindsey Havens is a Senior Marketing Manager at PhishLabs, a managed enterprise phishing connection and an Agari partner published in CIO, IT toolbox, and other industry media.
22. Implement encryption on multiple levels
For all of our clients, we recommend measures that match the importance or criticality of the data being protected. However, there are some general best practices that should be applied universally.
For logins, we recommend utilizing “two-factor authentication” whenever possible, especially on cloud systems. Whenever one of your systems requires an additional factor to log in, you have dramatically increased the difficulty for an attacker to use an exposed login and password. It is not infallible and needs to be combined with other authentication best practices, but it is so easy to use in some cases, there is no right excuse not to use it.
Secondly, encryption everywhere. Data on the move should be “encrypted in transit” – this means using HTTPS/SSL for your website and web applications, as well as connections between database servers. Encryption at rest – data on persistent storage (such as server disks, server backups, database backups, etc.) are all to be encrypted where possible.
Lastly, personal data and private data (consumer names, phone numbers, and email addresses, in addition to the traditional items such as credit card numbers) is often the target of a breach attempt should be protected with encryption as well – perhaps as database column encryption.
One final tip – Full Disk Encryption (FDE) on both Windows (via BitLocker) and Mac (via FileVault) – for all workstations and laptops. It’s easy to enable and manage, and it ensures if a machine is lost or stolen (a common occurrence with laptops) that the data will not be retrievable.

Timothy Platt, Vice President IT Business, Virtual Operations, LLC
Timothy Platt is a VP of IT Business Services at Virtual Operations, LLC – an IT Managed Services Provider.
23. Stop thinking like a small business.
Stop thinking like a small business. You are NOT too small to be a target. If your business data is the core value of your business, protect it.
Don’t run to Best Buy or Staples to buy the cheapest gear, especially Wi-Fi. Again, if your business is how you and your employees feed your families and invest for your future, treat it as such and only deal with skilled professionals who are themselves invested in protecting their business and their clients.
Be afraid, be very afraid. It is a bad new world out there, and the bad guys have tools you would not even believe, and all the time in the world to use them against you.
SMB’s need to have a healthy paranoia about their network and data security.
Art Artiles, Mathe, Inc.
24. Understand the trends – small businesses get hacked too.
- Get rid of the notion that you do not have the data hackers want. No matter how small your business is, you are the modern-day mark hackers are going after. If you connect to the internet in any way, your business is at risk. Hackers are looking to get a hold of your client lists, payroll, financial data, employee information, prospecting lists, and some of them have something even more sinister in mind. SMBs unknowingly harbor malware, which lies dormant until triggered by an unsuspecting employee and is spread to your vendors and contacts, which are often the actual target.
- Implement cybersecurity training for everyone on the payroll. Many breaches are due to negligence such as lost devices, mistakes, and errors, employee theft, or falling for frauds such as phishing and malware from click bait. By providing security training at least twice a year, employees are more likely to make conscious and smart decisions as they come to learn about their role in the cybersecurity plan.
- Staying on top of the latest cyber threats and ensuring your systems are applying patches promptly can be a critical method to help stay ahead of an attack. Many small business owners have neither the technical knowledge nor skills to implement these measures while simultaneously handling the day-to-day routines of managing their business. Fortunately, there are reputable subscription based Security-as-a-Service (SaaS) providers that can monitor and manage these aspects for a nominal monthly fee. In many cases, the provider will also include the necessary security hardware with their monthly rate. By leasing the equipment from the provider, the small business owner can rest easy knowing they have up-to-date protection for their network without the up-front expense of purchasing computer hardware, which will only depreciate.

Kathy Powell, Marketing Manager, Tie National, LLC
Kathy Powell is the Marketing Manager at Tie National, LLC. Kathy has used her talents to both build and manage new departments from the ground up to secure company growth and client satisfaction. Her passions are analysis, design, and volunteer work.
25. Quick wins can make significant differences.
On average, a robbery occurs every 13 seconds, and small businesses are four times more likely to be the target of a break-in compared to a home. As a small business owner, it is important to know your weak spots and safeguard against them.
- Update your security system. While having a security system is great, make sure you have *one that monitors the property 24/7* (as opposed to a system that just makes noise during an intrusion). In case of a break-in, these types of systems will immediately alert you and the police. The faster you can notify the police of a break-in, the more likely you are to recover stolen property and minimize damages and losses.
Most security systems capture video footage that details the time of day the break-in occurred, who it was and where he/she entered from. Make sure to install security cameras, as these alone can deter burglars who like to go unseen.
Most security systems can be controlled from a smartphone or laptop, and you can choose the type of security system that will work best for you and your company. - Perform routine internal safety checks. Unfortunately, 64 percent of small businesses fall victim to internal employee theft. While co-workers are often your office family, not everyone can be trusted. It is important to conduct routine internal safety checks to prevent robbery. Keep and frequently update your inventory of office equipment, IT equipment, office furniture, and products. Also, distribute the workload and financial responsibilities among a team, instead of leaving one employee responsible for the all of the company’s finances.
- Secure doors and safes. Take the time to secure all doors and lock all safes at the close of business each day. It is easy for thieves to kick down doors and pick locks–giving them easy access to files, merchandise, and petty cash. Most burglars are in and out of a location within ten minutes, so they will grab whatever they can access with the most ease. Consider bolting your safe to the ground–as some burglars simply take the safe with them and crack it offsite.
- Regularly update your digital security. Invest in database security or IT team and take all necessary precautions to keep digital information safe.
- Secure your printer. Printers are the second-biggest safety concern for small businesses, according to Eric Montague, CEO of Executech. Multifunction printers (MFPs) have a hard drive that stores every scan ever made. Businesses use printers and scanners daily, leaving private information on the hard drive that could be hacked. When businesses upgrade their printers, it is essential that they wipe the printer hard drive clean or take out the hard drive altogether.
“Hackers can review every scan and get a treasure trove of data,” Montague said.
- Create an emergency and disaster plan. When the unexpected occurs, it is important to be prepared with an disaster recovery plan. Safeguard your small business by having a process in place. Practice routine fire drills, earthquake or storm drills with your employees. Have employees keep snacks and water at their desks in case of an emergency or disaster. Update your office first-aid kit. Make sure your important data is backed up regularly and that the backup is located remotely. Inventory all office items for insurance purposes. This will minimize losses and help secure your business.
Sage Singleton, Security Expert, Safewise
Sage Singleton is a security expert for SafeWise, a comparison engine for home systems.
26. Start with proper “network hygiene.”
In today’s connected world anyone that uses social channels or email is a target for hackers. Small and medium enterprises face the same cybersecurity challenges as large enterprises and government agencies.
The trend of “landing a whale” is rapidly moving to “filling the nets.”
We are seeing greater proportions of successful attacks against the SMB and SME than ever before – one in five SMBs are hacked each year, and 60% of the victims go out of business because of the attack. The rationale for this is pretty simple. All too often, many SMB and SMEs lack the tools, skills and financial resources to detect successful breaches and insider threats. Add to that, the sheer number of prospective victims – close to 6M in the US alone, this target is easy pickings. Damages from one successful targeted attack could cost a small company as much as $84,000.
How to protect:
First, start with proper “network hygiene”. We may no longer see phishing attacks about your dead uncle who left you $10M. However, casting a broad net to snare unsuspecting small business owners is still a viable business model for hackers. Hygiene also includes proper training of your people. Training a person to recognize breach-tactics is imperative for businesses of all sizes. Fortune 100 companies do it and so should SMBs.
The next piece is around network and personnel visibility. Small businesses are often conduits for breaches to larger organizations. The SME hiring and vetting process for all your contractors and employees should be strict. Once the person is in your organization – they are in. Do you want to be the next small business that becomes known as the weak link in the next front-page-headline breach (see HomeDepot and Target)? Also, small and medium enterprises should know what applications are allowed and not allowed to run on their network. There are cost-effective, easy to use, easy to deploy solutions on the market today that enable organizations of all sizes to be situationally aware of what data is coming and what is going.
The next area is protection. Perimeter defenses should be enterprise-class. SMEs should not “settle” for a reduced subset of features just because of their size. If a vendor says, “That is only in our Enterprise Version,” run, not walk away. SMEs are very mobile device dependent. Many times the mobile device is the ONLY computer. Take steps to protect all devices, not just traditional computing platforms such as laptops.
And finally, be prepared for “oh no!” Having an easy to follow remediation plan is a critical step in keeping your business running. Ransomware is only effective if it can hold you for ransom. Have your backups disconnected from the computer? Know who can rebuild a machine quickly.
You will get punched – so be prepared to take one (or more)!

Paul Kraus, Founder & CEO, Eastwind Networks
Paul Kraus is a Founder and CEO of Eastwind Networks, a cloud-based breach detection solution that aims to protect government agencies and enterprise organizations from cyber threats that bypass traditional security measures. He has more than 25 years of experience in security.
27. Do not entrust your data to just any cloud.
- Do not store all data online in a cloud you do not know. It is ok to work with Apple or Microsoft, but for less than $300.00 a company can own their Cloud Service and not be at risk of a massive attack on their systems.
- Do not store all records, banking data, patient or customer ID Data on your server. We recommend our AeigsFS Secure Flash Drive. Pictured below, this is the most efficient manner to keep all computer recordation super secure. They provide up to 480gb, offer SHA 256 Encryption that is Military grade and PIN Access. Kept on your keychain in a solid aircraft aluminum shell, these flash drives are the difference between getting hacked and not. Back up daily.
- Obtain multiple malware and serviceware software. The more power and use require higher levels of cybersecurity malware to protect you from nefarious activities and hacks.
Jim Angelton, CEO, Aegis Finserv Corp
Jim Angelton is a CEO of Aegis Finserv Corp. AegisFS CyberThreat Division provides the full scale of cybersecurity services for small to large businesses.
28. Self-evaluate to keep pace with both risk and compliance.
Your business is small, but risks are enterprise-size
Top cybersecurity threats to small businesses (SMBs) are very similar to the risks all enterprises face. The stakes are much higher for SMBs because they often lack the resources to fight back and prevent data loss. Large firms have teams of data security experts and can afford extensive audits. SMBs can be more vulnerable to security risks and struggle to quickly react to vulnerabilities.
Keep pace with both risks and compliance by self-evaluating
Frequently self-evaluating the company’s cybersecurity practices is the best way to detect and prevent cybersecurity threats. SMBs can use the NIST Cybersecurity Framework (it’s free!) as a blueprint to evaluate current security policies and remodel data protection policies to focus on preventing vulnerabilities and to set goals to improve and maintain security.
Traditional data security standards and protections all attempt to do the same things: protect sensitive data. The NIST Cybersecurity Framework is unique because the Framework combines the best practices of other security standards to focus on outcomes, rather than avoiding liability. SMBs should self-evaluate cybersecurity at least once a year, with participation from all business unit leaders and all of the IT team.
Don’t become a victim of your own success – growth.
As SMBs grow and add employees and partners, they must share access to vital business data and systems. For example, a small company can rely on a single IT person to manage access to data, a server, and the company network. As the SMB grows and adds employees and offices, a “single point of failure” becomes a risk for the company. Security for data and networks should grow with the business, with precautions built into business goals.

Margaret Valtierra, Senior Marketing Specialist, Cohesive Networks
Margaret Valtierra is Senior Marketing Specialist at Cohesive Networks. She is responsible for growing business through digital and written content, public relations, and community events.
29. Stay vigilant about threats
- Complex Passwords. 65% of Americans use memorization to keep track of their online passwords1. This leads to passwords that are easy to remember and even easier for criminals to crack. Since 39% of online adults say they use the same password for many of their accounts, a cracked Gmail password may give a criminal access to your bank account. There are several free password managers available.Let the password manager generate and store your passwords so that they are unique for every site.
- Backup Critical Data. When most people consider a backup and disaster recovery solution, they think about hurricanes, wildfires, and flooding. More often, backup solutions are used to recover employee deleted files or full systems due to a cyber-attack.A small business should not scrimp on a backup system as it may save them thousands of dollars if they become a victim of a cybercrime. A reliable backup solution should include both onsite and offsite storage, backup verification and must protect against Ransomware.
- Email Vigilance. Attackers are using social media to craft emails that are irresistible to their recipients. Most phishing emails contain subject lines or text with rushed language that causes the user to take action immediately. We had a customer whose accounting clerk received a well-worded email from the owner directing her to transfer money instantly to refund an angry customer. A quick phone call to the owner prevented the clerk from moving $35,000 out of their account.Business owners should be using email solutions like Microsoft’s Office 365 or Google’s G Suite, which will filter out most phishing attempts. Recognizing that these emails will reach your employees makes it imperative to train your staff to identify and delete malicious emails.
Terry Barden, President, Forward Systems, LLC
Terry has worked in network and systems engineering for over 20 years at enterprise level operators. He founded Forward Systems in 2015 to help small and medium businesses prepare and defend themselves against cybercriminals. Forward Systems is a security-focused total service provider offering software and hardware solutions for managed security, managed IT, backup and disaster recovery and system virtualization.
30. Understand why you need controls and how you can implement them.
For the owner, manager or executive of a small business, my three tips for data protection would be:
- Know why security controls should be applied. This will allow you to know what your priorities are and save time, effort and money on implementation.
- Make your team understand how a data compromise can affect their lives and how they can protect information. This will give them a sense of commitment and will save you time, effort and money that would be spent with dealing with easily avoidable incidents.
- Ensure that information is backed up and tested regularly and that your organization knows how to act in case of problems. Incidents will happen, and this will save you time, effort and money in recovering your business operations.

Rhand Leal, Information Security Analyst, Advisera
Rhand Leal is one of the lead Advisera’s ISO experts and Information Security Analysts in charge of ISO 27001 compliance and other security standards. He has ten years’ experience in information security, and for the six years he had continuously maintained а certified Information Security Management System based on ISO 27001.
32. Make your systems hacker-proof.
- Small businesses should ensure they have implemented a proper backup and disaster recovery system that is monitored and tested for recovery on a regular basis. Knowing you can recover your data after a breach, such as falling victim to ransomware, will allow you to sleep easier at night!
- Configure your Windows computers and servers to automatically install Microsoft updates as they become available. Occasionally an update from MS breaks a valid 3rd party software or their own software, but dealing with those occasional issues is a far better path then dealing with the results of security vulnerabilities, like the SMB vulnerability exploited by WannaCry and Not Peyta earlier this year.
- Training, training, training! Employee training is paramount to protecting a small business’ data. Training should include how to detect email phishing scams, fraudulent phone calls, bad web sites and dangerous email attachments. Furthermore, training on what information should never be provided on social media posts and to unverified sources is important.

Bob Herman, Co-Founder and President, IT Tropolis Group LLC
Bob Herman has (25) years working experience in the computer security industry after graduating as an engineer from Georgia Tech. His professional interests include computer systems applications to business processes, virtualization technology, cloud computing efficiencies, and cybersecurity.
33. Put the right technologies in place
Every company, every business, and rather every enterprise is facing data security risk. One plausible reason for this is the fact that majority of us intentionally or unintentionally save data on our machines, which, as a matter of fact, are vulnerable to data breach. Businesses going down and getting bankrupt is becoming a norm only because people’s ignorance or lack of knowledge to understand data security risks.
Let’s quickly catch up the biggest and also the most commonly witnessed mistakes companies make with data security protection. These are:
- Failure to understand the threat against their employees, customers, competitors, etc
- Wrongly assuming data security technology to be an information technology problem rather than a business problem
- Relying on cheap cyber products, including anti-virus
- Unable to prioritizing the significance of data and trade secrets
- Failure to detect Insider Threats
- Using unencrypted data on emails
- Saving unencrypted data on backup machines
- Re-using passwords
- Using weak or easy-to-hack passwords
- Lack of sharing data security technologies and policies with employees
These are some issues that businesses, as well as individuals, have been facing over the years. They are not just limited to large companies. Small businesses also face the dangers of getting affected because of the lack of security measures.
But, the good news is that this can be dealt smartly. The following steps might help assist in data security.
- Implementing Security Policies. Set up strong security policies for your company and ensure that every employee is aware, as well as strictly adhere to them. Clarity and understanding of these policies are essential for every worker of the company.
- Putting the right technologies in the right places. Virus and data corruption are not the only threats. Hackers are too! They attack, steal and are capable of misusing your data. You must use a secure internet connection weather LAN or Wireless and protect it by putting a password to access. Also, make sure that your internet security is not on the initial level, which can be breached easily. Hence, use multi-layer security on all the devices that contain your company’s sensitive data. Always try using strong passwords, and try avoiding usage of common or easily ‘guessed’ passwords. Also, try changing your passwords after some time rather than sticking to only one password for long. Using multifactor authentication to access sensitive information is the safest way to go by. Your system’s software must be kept up to date. You must install all the patches and new versions of software because security patches are included in the newly launched versions. Also, use the anti-viruses. Try maintaining backups of all your data because there is a likelihood that certain situations arise where you lose your data. So, make sure of have a backup that is secure in all ways. Use encryption method on your data your all data is stored in encrypted form.
- Conduct a Security Audit. If you are unable to identify the weak part that’s creating a hurdle to fulfill all the security and privacy policies, then a security audit is what you need. You must conduct an audit of all the devices and networks that contain sensitive data/information. It will make your data as well as your business safe from security threats.
Belonging to a company that offers security services, we, at Kualitatem, know how important your data is to you and are cognizant of the significance of keeping it protected.
Kashif Abid, Head of Compliance and Security, Kualitatem Inc.
Kashif Abid MS, LPT, CEH is serving as Head of compliance and security for Kualitatem Inc. He is a researcher, a Certified Ethical Hacker (CEH), EC-Council Certified Security Analyst (ECSA) and a Licensed Penetration Tester (LPT).
34. Set up business data security policies
Outside of the staples (clear company policies/SOP), when it comes to data retention and dissemination along with consistent back-ups, I would say:
- Use group policy settings provided in Windows to prevent the use of USB mass storage devices by users so you can reduce the likelihood that employees can walk out of the office with confidential company data on their flash drive or cell phones.
- Require the use of dual authentication (RSA key, etc.) and meter access to any applications employees are capable of accessing outside of the office. This reduces your exposure should an employee’s credentials ever be compromised and metered access should prevent wholesale raiding of confidential company data (at least remotely).
- Verbose logging. Knowing who and when a file was last accessed, updated, or changes goes a long way in increasing data accountability. When employees know they can’t lie, hide, or blame someone else for the breach or unauthorized transmission of data, they tend to be more prudent and careful.
35. Consider outsourcing qualified IT security staff and systems.
For any business, a data security issue can be ominous. For a small business, it can be catastrophic. The three top tips I can unequivocally recommend are as follows:
- Outsource your IT security for endpoints and servers to a reliable Managed Security Service Provider (MSSP). Their purpose is to provide expert solutions and consulting to their clients, allowing a small business to focus on their business, not information technology.
- Encrypt your data. Data encryption is one of the most effective methods available to reduce the impact of a data breach. Encrypting data also simplifies compliance validation with regulations and mandates such as Sarbanes, Oxley, HIPAA, GDPR Regulation, etc.
- Engage with a Risk Adviser to review your insurance coverage. This is an often overlooked aspect for many organizations, but especially critical for small to medium-sized businesses. Cyber risk and the associated liabilities can be the death knell if not understood and appropriately mitigated.
There are no silver bullets for data security, but by following these tips and proactively engaging with your IT service provider on a monthly basis, any small business will be in an excellent position to understand their exposure, the current cyber environment, and keep their data and business out of harm’s way.
Jeffrey Hornberger, Vice President of Sales, Security First
Jeff Hornberger is the Vice President, Sales and Consulting for Security First Corp, also serving as the lead architect for the Public Sector, including the Intelligence Community and Fortune 100 clients.
37. Set up multi-layered security measures
- Explore all your options. Before you commit to anything, spend the time to research all of the available options for data storage and cloud products. There are thousands of service providers, and it might be easy, especially as a small business with a low IT budget, to go for the cheapest option. When that temptation comes, perhaps it will help to remember that 60 percent of small companies that suffer a cyber attack go out of business within six months. Do a “background check” on several providers and weigh the pros and cons before reaching a decision, because this is one thing your company cannot afford to get wrong.
- Set up multi-layered security measures. When it comes to cybersecurity, passwords are generally the weakest link. 63 percent of hacks occur because of weak passwords, and even though cybersecurity experts constantly address the topic businesses have been slow to learn. You can require employees to regularly change their passwords, but companies would also be wise to implement two-factor authentication. Multi-factor authentication requires multiple pieces of evidence to verify identity, whether that means various passwords, a key-card, facial-recognition or otherwise. It is a fairly simple solution, but according to Symantec 80 percent of breaches could be eliminated by implementing it. Another layer to add is to use data encryption, which is basically taking your data and re-coding it so that it cannot be read or translated without a key.
- Consider purchasing cyber risk insurance. Another solution that isn’t often considered is cyber insurance. To be clear, the insurance should be a last resort. If you have to use it, that means you’ve failed. You’ve risked your clients’ information and your own. At the same time, however, it can be a good safety net for companies who can benefit from secure footing while they’re trying to address the problem. Cyber insurance can help your company avoid the fate of most small businesses that are hit by cyber attacks.
Alec Sears, IT Specialist, Frontier Business
Alec Sears is an Information Technology expert at Frontier Communications.
38. Leverage remote storage and backup solutions.
Tip #1: Store Your Data On An External Hard Drive
It is common nowadays for businesses to store documents on Google Drive and Dropbox. They are convenient, free iCloud storage systems that many use every day. However, they are not the most secure especially for business information and data. To be safe, store your business data on an external hard drive. It may cost a little depending on the size of your small business but will be well worth it in the end. By storing your information this way, it will save you the panic attack if for some reason your data is lost.
Tip #2: Limit The Number Of Employees Who Have Access To Account Passwords
When it comes to data account passwords, it is better to be safe than sorry. Only provide passwords to employees who absolutely need them, and whom you can trust. Issues with account passwords can arise if you have a disgruntled employee or ex-employee. They could steal your business information leading to your business being ruined.
Tip #3: Never Use Public Wi-Fi For Business Work
Public Wi-Fi is a playground for hackers and cybercriminals. When it comes to doing work, never use public Wi-Fi. If a hacker were to gain access to your data, your customer information and business information would be compromised. This type of situation a small business may never recover from.

Holly Zink, Digital Marketing Associate, The Powerline Group
Holly Zink is a Digital Marketing Associate and Cybersecurity Expert for The Powerline Group. For them, she manages multiple technology-related blogs and often writes about data security tips for all people including businesses.
39. Understand and control your data
In May 2018, GDPR (General Data Protection Regulation) will come into force. That’s just five months until the most significant reform in data protection and privacy laws for over 20 years. Things will be very different. GDPR is going to seriously affect data security and how businesses must operate. Whether you’re a multi-national or a small business, all will handle some level of personal data whether it’s on staff, customers or enquirers.
GDPR is the government regulations defining how that personal information is managed, to protect consumers and their privacy from data misuse. GDPR brings stricter guidelines and higher fines than the current data protection legislation. The clock is ticking. How prepared are you?
Here are three data security tips on this topic to get you started:
- Understand and control data – keep a log of all the personal data handled by your business; when and where it came from, who has access, why you have and when you will delete it.
- Only keep the data you need – the more data you have, the harder it is to track and control. Just keep what you need and have a documented purpose of retaining any personal data.
- It’s a company-wide initiative – ensure all staff are aware of data security requirements and sign their adherence. If they’re alert to risks of the data security, breaches are less likely.
Libby Plowman – CRM and Data Director, Intermarketing Agency
Over 20 years’ experience in the marketing data industry, providing consultancy and project management on complex multi-functional data projects. Critical areas of specialism include multi-channel CRM, customer insight, and data strategy, across a variety of industry sectors.
40. Secure your website domain.
Three quick wins for a small business right now would be to:
- Get a security certificate for your site. It is a flag to customers that you care about their security notwithstanding Google penalizing sites without it.
- Ensure that you have SPF set on your domain so that bad actors cannot spoof your domain and trick employees into clicking links in phishing emails.
- If you store data on EU citizens, have a plan to be GDPR compliant. For larger firms consider encrypting data at rest or use services that have this as an option.

Chris Byrne is co-founder and CEO of Sensorpro.
41. Implement email best practices.
Email is essential for all businesses. That necessity is why email is also the number one threat vector for hackers.
That is why it is important to have an email security plan in place. Three things all small businesses can do are:
- Protect yourself from spam, phishing, and malware. Using a strong email filter can help keep most of the threats at bay.
- Don’t click suspicious links, even if it is from someone you know. If someone’s account is compromised, it can send malicious emails without their knowledge. It never hurts to check with the person BEFORE clicking on that link to verify it is legitimate.
- Block large email attachments with macros. Word Docs, Excel and PDF files may be standards in business productivity, but they are also the most common attack files used for malware. There is usually little reason to have attachments larger than 10MB. Attachments with Macros are especially dangerous.

Hoala Greevy, Founder and CEO, Paubox
Hoala has 17 years experience in the email industry and is the architect of the Paubox platform. He graduated from Portland State University with a BS in Geography and a BS in Social Sciences.
43. Ensure your applications are secure-by-design
Cloud data security is frequently thought about in terms of managing existing risk. It’s crucial that organizations ensure that applications are ‘secure by design’ – whether they are developed in-house or purchased from an external provider.
Shifting left and fixing security flaws in the development stage and shifting right to monitor for new vulnerabilities ensures that firms are doing everything they can to stay ahead of the hackers. It helps prevent ransomware locking-down data or from allowing it to be exfiltrated. When purchasing cloud applications, it’s crucial that organizations manage their software supply chain and source solely from providers that can demonstrate proof of security.
Where businesses already have a preferred vendor without such certification, they can be a positive force in supporting their suppliers’ application security processes. A number of firms that CA Veracode works with, for instance, even pay the third-party license fee to
enable their supplier to become compliant with their company’s standards.

Peter Chestna, Director of Developer Engagement, CA Veracode
As Director of Developer Engagement, Pete provides customers with practical advice on how to successfully roll out developer-centric application security programs.
46. Treat security as a process, not an event.
Achieving some level of security requires a specific mindset that every organization needs to understand and then internalize. It doesn’t matter if you’re engaged in “routine” tasks or something more specialized – every organization is more and less secure over time since the nature of cyber attacks constantly evolves. The process of security means adjusting and learning accordingly.
A head-in-the-sand approach ensures that an organization will become less secure.
Also, beware the unwitting perpetrator. Like crimes in the non-virtual world, Distributed Denial of Service (DDoS) attacks and cyber hacks rarely come with calling cards. Those with ill intent find honeypots of oblivious organizations they can commandeer easily, with a single password. In the incident referenced earlier, the mega-provider didn’t even have an abuse team. So, at the very least, businesses need to insist that their hosting company assign a unique password to every server – and have an abuse team at the ready just in case.

Adam Stern, Infinitely Virtual
47. Understand privacy policies of your cloud accounts.
Strong passwords and 2 Factor Authentication are the best things consumers of cloud software services can do themselves to improve the security of their data. The days of swapping letters for numbers and special characters in a password are long gone. So is the advice that they should be changed often.
The recent recommendation is that passwords should be formed of 3 random words. For example, ‘TreeKeyPencil’ is far more difficult to guess than ‘1iv3rp00l’. Adding an extra layer of security with 2 Factor Authentication will further prevent your cloud-stored data from getting into the wrong hands.
Additionally, when choosing a cloud software provider to share your data, it’s essential you read their privacy policy and terms and conditions. This should give you an indication of what the service provider will do in the event of a data breach, as well as what they are doing to prevent one in the first place. For example, ISMS.online undergoes regular penetration testing and has achieved Pan UK Government accreditation and PSN certification.

Sarah James, ISMS.online
The UK-based ISMS.online is a secure cloud software platform used by organizations to describe and demonstrate their information and cybersecurity posture. ISMS.online also allows you to manage regulations like GDPR and certifications like ISO 27001.

48. Take a zero trust approach
The best approach to cybersecurity you can take is to protect everything by default.
This zero trust approach doesn’t require user involvement to keep the data safe and it takes into account the way data is realistically used and shared with organizations.
Keep a watchful eye toward internal breaches, not only external. Even if it’s unintentional, up to 43 percent of data breaches are caused internally. It’s most effective to automate security in a way that is seamless to end-users, so they don’t try to circumvent it.
Understand that there is no longer a perimeter. With multiple entry points into an organization (so many devices), there is no longer a defined and defensible perimeter. In today’s cloud-first environment, companies no longer own or secure the servers where the data is kept.

Lawrence Jones MBE, CEO, UKFast
UKFast is one of the largest independently owned hosting providers with a team of over 400 people in Manchester, London, and Glasgow.
52. There are two critical steps to take for the improved security
The first step to keeping your data secure on the cloud is to ensure that your cloud data is protected by, not just a password, but a two-step authentication process. Creating a strong password (12-15 characters, upper and lowercase, with numbers and symbols) is essential, but even a password like that can be cracked.
Add two-step authentication by sending pin numbers to your phone or adding personal security questions on top of your password.
The second way to keep your data secure is through encryption. Opt for an encrypted cloud service, so your information is always protected. This is especially important for companies in the healthcare and defense industries.

Keri Lindenmuth, Marketing Manager, KDG
Keri Lindenmuth is the marketing manager and web content writer at KDG, a technology solutions provider located in Allentown, PA.
53. Add enhanced security settings to your public cloud
The most common and publicized data breaches in the past year or so have been due to giving the public read access to AWS S3 storage buckets. The default configuration is indeed private, but people tend to make changes and forget about it, and then put confidential data on those exposed buckets. There’s very little excuse to do so.
In addition to this, you should implement encryption both in traffic and at rest. In the data center, where end users, servers, and application servers might all be in the same building. By contrast, with the Cloud, all traffic goes over the Internet, so you need to encrypt data as it moves around in public. It’s like the difference between mailing a letter in an envelope or sending a postcard which anyone who comes into contact with it can read the contents.

Todd Bernhard, Product Marketing Manager, CloudCheckr, Inc.
55. Be aware of the most common security mistakes
A weak password, or reusing the same password for multiple accounts, is the biggest security risk for cloud-based applications. If one of your accounts is hacked, the rest can easily be hacked using the same credentials. You really shouldn’t be using the same password for your online banking as your email. But since it’s nearly impossible to remember a unique, secure password for every account that you use, I recommend using a password manager like 1Password.
In addition to this, you should run regular backups of data that’s in the cloud.
There’s a big misconception about how cloud-based platforms (ex. Shopify, QuickBooks Online, Mailchimp, Wordpress) are backed up. Typically, cloud-based apps maintain a disaster recovery backup of the entire platform. If something were to happen to their servers, they would try to recover everyone’s data to the last backup. However, as a user, you don’t have access to their backup in order to restore your data. This means that you risk having to manually undo unwanted changes or permanently losing data if:
- A 3rd party app integrated into your account causes problems
- You need to unroll a series of changes
- Your or someone on your team makes a mistake
- A disgruntled employee or contractor deletes data maliciously
Rewind, the company I co-founded, has been backing up Shopify accounts since 2015 and from speaking with hundreds of customers, I can tell you that these four examples are pervasive. I’ve seen everything from entrepreneurs breaking their Shopify site after messing with the code, to 3rd party apps accidentally deleting over 300 products in their store.
Having access to a secondary backup of your cloud accounts gives you greater control and freedom over your own data. If something were to happen to the vendor’s servers, or within your individual account, being able to quickly recover your data could save you thousands of dollars in lost revenue, repair costs, and time.

Mike Potter, CEO and Co-founder, Rewind
Mike is a serial entrepreneur and currently the co-founder and CEO of Rewind, a backup solution for Shopify, BigCommerce, and Quickbooks Online. His second full-time position is Hockey Dad.
56. Get serious about security
Tip 1: Get serious about password security. Storing your data in the cloud means that your password is the key to the only door protecting your data from the world. Follow the advice that you’ve heard so many times, and use a secure password (a password manager such as LastPass or Dashlane can make this easier), and don’t share the password among users. Also, use two-factor authentication if possible to add another layer of protection.
Tip 2: Encrypt the data you store in the cloud. This is easiest if you choose a provider that allows encryption, but there are also services such as SmartCryptor or Boxcryptor. Even if someone is able to get to your cloud service, if you have the files encrypted, it will be more difficult for them to actually access your data.
Tip 3: Keep backups of your data in a separate location. Cloud services are a great way to store data offsite as part of a backup solution, but follow the backup rule of three and have a backup in another location as well, either locally or in a separate service.

Stacy Clements, Owner, Milepost 42
Stacy Clements is the owner of Milepost 42, a technology partner for small business owners who want to focus on their passion and not the techie stuff needed to support the business. She spent 23 years in the Air Force, much of that time in communications/information and cyber operations, and began freelancing as a web technologist in 2008.
57. Maximize cloud security with containers
Containers have been around since the mid-2000s but didn’t experience the surge in popularity until 2013. Now, 56% of all organizations have containerized product applications. Containers simplify software distribution and allow for greater resource sharing through computer systems. Containers also reduce an organization’s vulnerability for a massive cybersecurity breach by isolating data in separate environments.

Carson Sweet, Co-founder and CTO, CloudPassage
Carson Sweet is co-founder and chief technology officer for CloudPassage. Carson’s information security career spans three decades and includes a broad range of entrepreneurial, management and hands-on technology experience.
58. Use specialized software to prevent attacks
Specialized software solutions can significantly improve detection and prevention of cyber attacks, but no system is ever perfect. Even the companies with a good cybersecurity setup can end up as victims too. Make sure your employees are also trained in using cybersecurity software as well as prevention, detection, and incident response.
Detection is king – the longer an attacker is inside your network, the greater the damage they can cause. Intrusion detection systems and a good analytics setup with 24h notifications can go a long way in reacting to the next system intrusion quickly.
Reaction saves the day – make sure you have access to experienced cybersecurity experts who are familiar with your IT infrastructure and setup. If you are a small organization with no IT department, you can outsource this to a range of different IT service providers who can step in when needed.
So what are the solutions available out there? Crozdesk has found that the variety of new IT security software solutions launched onto the market has increased by nearly 350% from June 2016 to June 2017, as compared to the 12 months period before.
Funding for cyber and cloud security software companies has nearly doubled over the last couple of years, and this is resulting in a surge of new cyber technology types. It is good to be updated on the latest network security technologies available and consider adding applicable ones to your cyber security setup. Honeypots (traps for intruders) were in demand last year.

Orion Devries, Researcher at Crozdesk.com
Orion Devries is from Crozdesk.com, a business software discovery and comparison portal featuring more than 100 Cyber and Data Security solutions.
Recent Posts
Benefits of Private Cloud: Protect Your Data Before Its Gone
Definitive 7 Point Disaster Recovery Planning Checklist
The need for a comprehensive disaster recovery plan cannot be felt more than in the aftermath of massive hurricanes that recently ravaged the west coast of the US.
Days-long power knockouts, physical blows, and supply chain breakdowns left thousands of businesses in the dark. Most of them are now facing insurance fights and significant infrastructure rebuilds to get back on track.
These are complex challenges that many will struggle to overcome. The organizations that had disaster recovery and business continuity plans in place now have one less thing to worry about.
Designed to enable businesses to reduce damages of unpredicted outages, a disaster plan is a long-term assurance of business operability. While a disaster of this scale is not an everyday scenario, it can be fatal to business operations.
And it can happen to anyone.
In one form or another, natural disasters and human errors are a constant possibility, and this is why it makes sense to prepare for them. When you add different types of cyber-attacks to the mix, the value of a disaster recovery checklist is even more significant.
This is especially true when you take into account that the average cost of downtime can go up to $5600 per minute in mid-sized businesses and up to $11,000 per minute in enterprises.
With every second of outage counting against your profits, avoiding any impact of downtime is a strategic aim. This is best achieved by preparing your entire infrastructure to resist and stay operational even in the harshest situations.
Why You Need Disaster Recovery Plan: Case Study
While the probability of a disaster may often seem hypothetical, some recent events confirmed that hazards are a real thing. And costly, too.
Hurricanes Irma and Harvey are some of the most striking examples, but a lot of other things can go wrong in business and cause disruptions. One of the cases in point took place earlier in May when British Airways suffered a significant infrastructure technology system collapse. The three-day inoperability left thousands of passengers stuck at airports across the world, while the company worked to identify and fix the error to get their critical systems back online. The entire data disaster reportedly cost 500 million pounds to the company, while its reputation is still on the line.
When it comes to business disruptions, it does not get more real than that.
The BA case is yet another unfortunate confirmation of the fact that unplanned outages can take place anytime and in any company. The ones that have no stable disaster recovery and business continuity plans are bound to suffer extreme financial and reputational losses. This is especially the case with those that have complex and globally dispersed IT infrastructures, where 100% availability is paramount.
Events like these call for a discussion on the disaster recovery best practices that may help companies like this avoid any similar collapses in the future. Below is an overview of the critical items that need to be in the data management plan. What is disaster recovery planning?
1. Risk assessment and business impact analysis (BIA)
The best way to fight the enemy is to get to know the enemy.
The same goes for disaster recovery planning, where the first step is to identify possible threats and their likelihood to impact your businesses. The outcome of this process is a detailed risk analysis with an overview of some common threats in the context of your business.
Start the disaster recovery planning process with a risk assessment. Develop a risk matrix, where you will classify the types of disasters that can occur. The risk matrix is essential to establish priorities and identify the scope of damage that can be devastating for business.
Resource: smartsheet
After you identify and analyze the risks, you can create a business impact analysis (BIA). This document should help you understand the actual effects of any unfortunate event that can hit your business. Whether it is a loss of physical access to premises, system collapse, or inability to access data files, this matrix is a base for planning the next steps.
To get started with BIA, you can use FEMA’s resource with a simple disaster recovery plan template.
2. Recovery Time Objective (RTO) and Recovery Point Objective (RPO)
RTO and RPO are critical concepts in disaster recovery planning, whether your data resides in a dedicated hosting or virtualized environments.
As a reminder, these two refer to the following:
- The amount of time needed to recover all applications (RTO)
- The amount of data loss that you risk losing during disaster recovery, calculated in relation to the amount of time required to complete the process (RPO)
RTO and RPO real-life values will vary between companies. Setting RTO and RPO goals should involve a cross-department conversation to best assess business needs in this respect.
The objectives you define this way are the foundation of an effective disaster recovery plan. They also determine which solutions to deploy. This refers to both hardware and software configurations needed to recover specific workloads.

3. Response strategy guidelines and detailed procedures
Documenting a written DR plan is the only way to ensure that your team will know what to do and where to start when a disaster happens.
Written guidelines and procedures should cover everything from implementing DR solutions and executing recovery activities to infrastructure monitoring and communications. Additionally, all the relevant details about people, contacts, and facilities should be included to make every step of the process transparent and straightforward.
Some of the general process documents and guidelines to develop include:
- Communication procedures, outlining who is responsible for announcing the disaster and communicating with employees, media, or customers about it;
- Data Backup procedures, with a list of all facilities or third-party solutions used for document backups.
- Guidelines for initiating a response strategy (responsible staff members, outline of critical activities, contact persons, etc.)
- Post-disaster activities that should be carried out after critical apps and services are reestablished (contacting customers, vendors, etc.).
The key to developing effective procedures is to include as many details as possible about every activity. The essential ones are a) name of a responsible person with contact details, b) action items, c) activity timeline, and e) how it should be done. This way, you can achieve full transparency for every critical process in the overall DRP.
4. Disaster recovery sites
Putting the plan to work also involves choosing the disaster recovery site where all vital data, applications, and physical assets can be moved in case of a disaster. Such a site needs to support active communications, meaning that they should have both critical hardware and software in place.
Traditionally, three types of sites are used for disaster recovery:
- A hot site, which is defined as a site that allows a “functional data center with hardware and software, personnel and customer data;”
- A warm site that would allow access to all critical applications excluding customer data;
- A cold site, where you can store IT systems and data, but that has no technology until the IT disaster recovery checklist is put into motion.
Most DR solutions automatically backup and replicate critical workloads at multiple sites to strengthen and speed up the recovery process. With the advances in virtualization and replication technologies, DR capabilities that are at the disposal of modern companies are many. Choosing the right one involves finding the balance between price, technology, and a provider’s ability to cater to your own needs.

5. Incident Response Team
When a disaster strikes, all teams get involved. To efficiently carry out a disaster recovery plan, you should name specific people to handle different recovery activities. This is key to ensuring that all the tasks will be completed as efficiently as possible.
The activities of the incident response team will vary, and they should be defined within DR guidelines and procedure documents. Some of these include communicating with employees and external media, monitoring the systems, system setup and recovery operations.
Like with all the other guidelines and procedures, details about incident response team should include:
- The action to complete
- The job role of a person responsible for completing the work
- Name/contact details of a person responsible
- The timeframe in which the activity should be completed
- Steps that more closely describe the operation
The Incident response team will involve multiple departments – from technicians to senior management – each of which may have an essential role in minimizing the effects of a disaster.
6. IT Disaster Recovery Services
Recovering complex IT systems may require massive manpower, hardware resources, and technical knowledge. Many of these can be supplemented by third-party resources and cloud computing solutions. Cloud-based resources are particularly handy to optimize costs and shift parts of the infrastructure to remote servers, which brings higher security and better use of costs.
In companies where not all workloads are suitable for public cloud backup, a balanced distribution between on-site and cloud servers is a cost-effective way to configure infrastructure. Similarly, a hybrid approach to an IT disaster recovery plan is ideal for companies with advanced recovery needs.
A particularly convenient option for businesses of any size is Disaster-Recover-as-a-Service (DRaaS), which offers greater flexibility to teams operating within a limited DR budget. DRaaS allows access to critical infrastructure and backup resources at an affordable price point. It can also be used in both virtualized and dedicated environments, which makes it suitable for companies of any size and any infrastructure need.

7. Maintenance and testing activities
Once created, a disaster recovery plan needs to be reviewed and tested regularly. This is the only way to ensure that it is efficient long-term and that it can be applied in any scenario.
While most modern businesses now have recovery strategies in place, many of them are outdated and not aligned with a company’s current needs. This is why the plan needs to be updated to reflect any organizational or staff changes, especially in companies that grow rapidly.
All the critical applications and procedures should be regularly tested and monitored to ensure they are disaster-ready. This is best achieved by assigning a specific task to the defined disaster recovery teams and training employees on disaster recovery best practices.
Closing Thoughts: IT Disaster Recovery Planning & Procedures
Given the dynamics of today’s business, occasional disruptions seem inevitable, no matter the company size. The significant disasters we have seen recently only enhance the sense of uncertainty and the need to protect critical data and applications.
While a disaster recovery checklist may have many goals, one of its most significant values is its ability to reassure company staff that they can handle any scenario and restore normal business operations. The suggestions given above are intended to guide your company up to this path.
Need more details about DR? Follow the link below to download our FREE guide!












