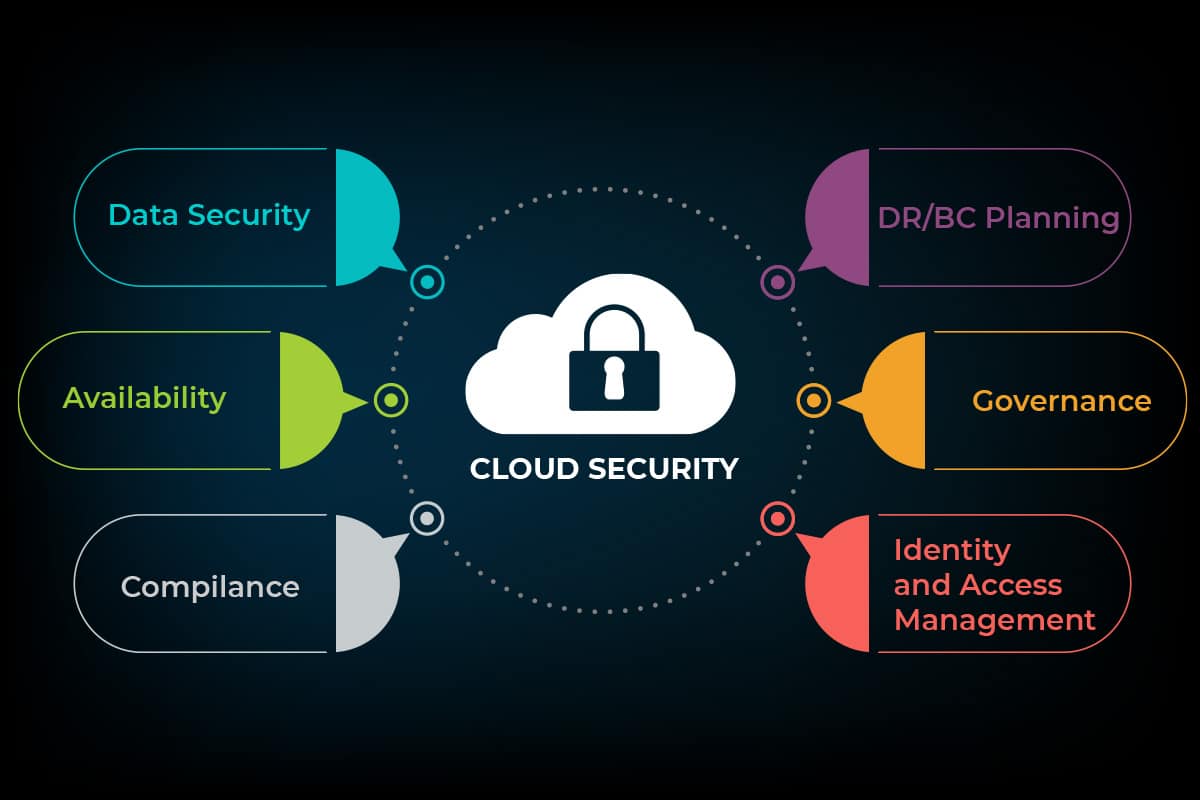
Cloud Storage Security: How Secure is Your Data in The Cloud?
Data is moving to the cloud at a record pace.
Cloud-based solutions are increasingly in demand around the world. These solutions include everything from secure data storage to entire business processes.
A Definition Of Cloud Storage Security
Cloud-based internet security is an outsourced solution for storing data. Instead of saving data onto local hard drives, users store data on Internet-connected servers. Data Centers manage these servers to keep the data safe and secure to access.
Enterprises turn to cloud storage solutions to solve a variety of problems. Small businesses use the cloud to cut costs. IT specialists turn to the cloud as the best way to store sensitive data.
Any time you access files stored remotely, you are accessing a cloud.
Email is a prime example. Most email users don’t bother saving emails to their devices because those devices are connected to the Internet.
Learn about cloud storage security and how to take steps to secure your cloud servers.
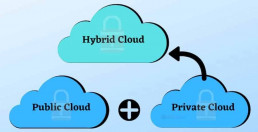
Types of Cloud: Public, Private, Hybrid
There are three types of cloud solutions.
Each of these offers a unique combination of advantages and drawbacks:
Public Cloud: These services offer accessibility and security. This security is best suited for unstructured data, like files in folders. Most users don’t get a great deal of customized attention from public cloud providers. This option is affordable.
Private Cloud: Private cloud hosting services are on-premises solutions. Users assert unlimited control over the system. Private cloud storage is more expensive. This is because the owner manages and maintains the physical hardware.
Hybrid Cloud: Many companies choose to keep high-volume files on the public cloud and sensitive data on a private cloud. This hybrid approach strikes a balance between affordability and customization.
How Secure is Cloud Storage?
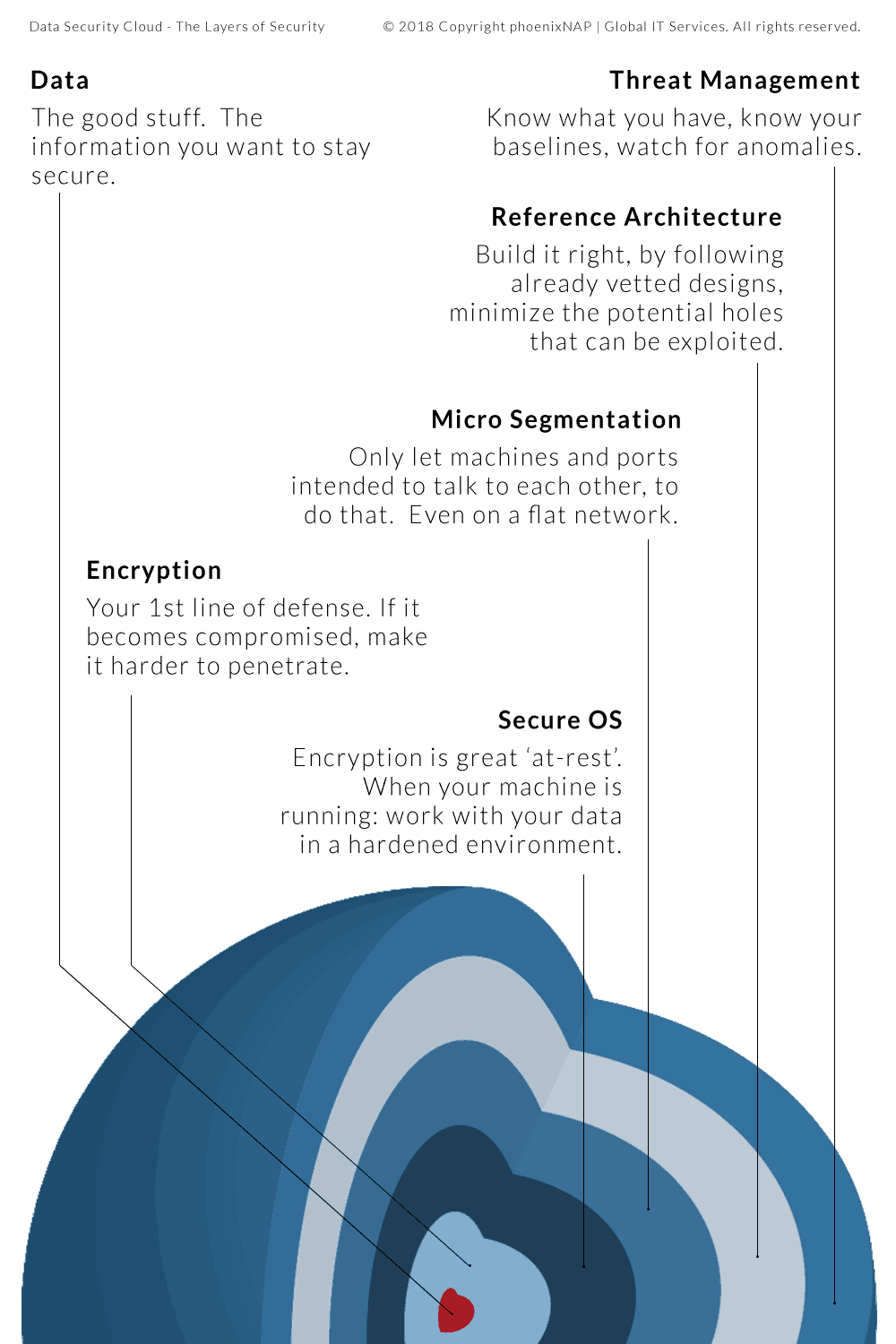
All files stored on secure cloud servers benefit from an enhanced level of security.
The security credential most users are familiar with is the password. Cloud storage security vendors secure data using other means as well.
Some of these include:
Advanced Firewalls: All Firewall types inspect traveling data packets. Simple ones only examine the source and destination data. Advanced ones verify packet content integrity. These programs then map packet contents to known security threats.
Intrusion Detection: Online secure storage can serve many users at the same time. Successful cloud security systems rely on identifying when someone tries to break into the system. Multiple levels of detection ensure cloud vendors can even stop intruders who break past the network’s initial defenses.
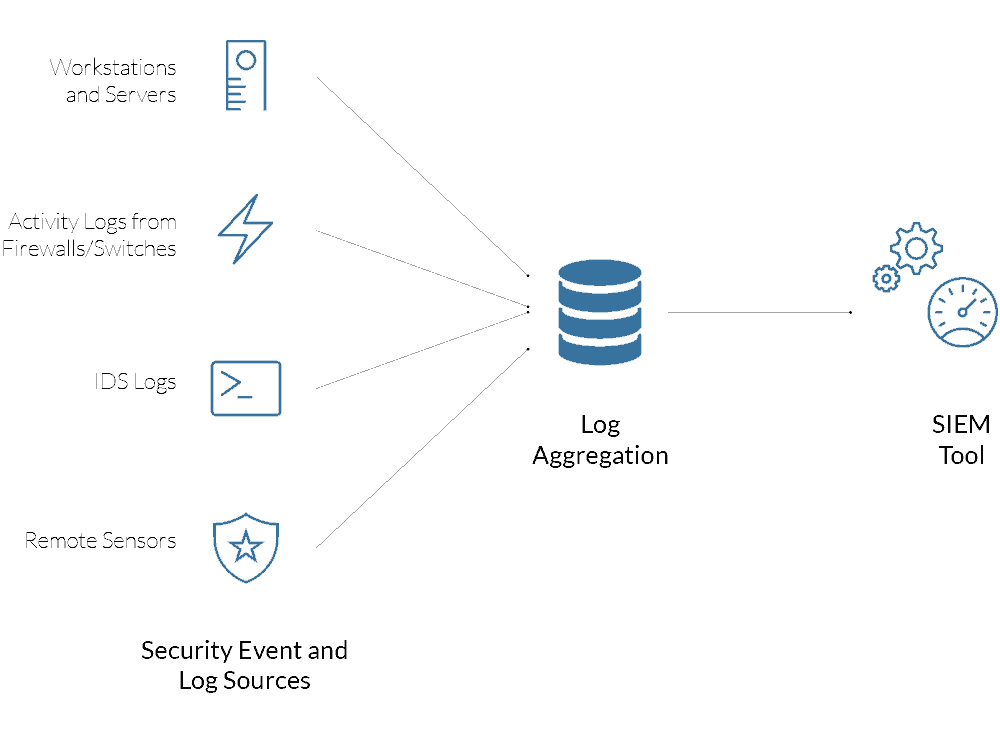
Event Logging: Event logs help security analysts understand threats. These logs record network actions. Analysts use this data to build a narrative concerning network events. This helps them predict and prevent security breaches.
Internal Firewalls: Not all accounts should have complete access to data stored in the cloud. Limiting secure cloud access through internal firewalls boosts security. This ensures that even a compromised account cannot gain full access.
Encryption: Encryption keeps data safe from unauthorized users. If an attacker steals an encrypted file, access is denied without finding a secret key. The data is worthless to anyone who does not have the key.
Physical Security: Cloud data centers are highly secure. Certified data centers have 24-hour monitoring, fingerprint locks, and armed guards. These places are more secure than almost all on-site data centers. Different cloud vendors use different approaches for each of these factors. For instance, some cloud storage systems keep user encryption keys from their users. Others give the encryption keys to their users.
Best-in-class cloud infrastructure relies on giving users the ideal balance between access and security. If you trust users with their own keys, users may accidentally give the keys to an unauthorized person.
There are many different ways to structure a cloud security framework. The user must follow security guidelines when using the cloud.
For a security system to be complete, users must adhere to a security awareness training program. Even the most advanced security system cannot compensate for negligent users.

Cloud Data Security Risks
Security breaches are rarely caused by poor cloud data protection. More than 40% of data security breaches occur due to employee error. Improve user security to make cloud storage more secure.
Many factors contribute to user security in the cloud storage system.
Many of these focus on employee training:
Authentication: Weak passwords are the most common enterprise security vulnerability. Many employees write their passwords down on paper. This defeats the purpose. Multi-factor authentication can solve this problem.
Awareness: In the modern office, every job is a cybersecurity job. Employees must know why security is so important and be trained in security awareness. Users must know how criminals break into enterprise systems. Users must prepare responses to the most common attack vectors.
Phishing Protection: Phishing scams remain the most common cyber attack vector. These attacks attempt to compromise user emails and passwords. Then, attackers can move through business systems to obtain access to more sensitive files.
Breach Drills: Simulating data breaches can help employees identify and prevent phishing attacks. Users can also improve response times when real breaches occur. This establishes protocols for handling suspicious activity and gives feedback to users.
Measurement: The results of data breach drills must inform future performance. Practice only makes perfect if analysts measure the results and find ways to improve upon them. Quantify the results of simulation drills and employee training to maximize the security of cloud storage.
Cloud Storage Security Issues: Educate Employees
Employee education helps enterprises successfully protect cloud data. Employee users often do not know how cloud computing works.
Explain cloud storage security to your employees by answering the following questions:
Where Is the Cloud Located?
Cloud storage data is located in remote data centers. These can be anywhere on the planet. Cloud vendors often store the same data in multiple places. This is called redundancy.
How is Cloud Storage Different from Local Storage?
Cloud vendors use the Internet to transfer data from a secure data center to employee devices. Cloud storage data is available everywhere.
How Much Data Can the Cloud Store?
Storage in the cloud is virtually unlimited. Local drive space is limited. Bandwidth – the amount of data a network can transmit per second – is usually the limiting factor. High-Volume, low-bandwidth cloud service will run too slowly for meaningful work.
Does The Cloud Save Money?
Most companies invest in cloud storage to save money compared to on-site storage. Improved connectivity cuts costs. Cloud services can also save money in disaster recovery situations.
Is the Cloud Secure and Private?
Professional cloud storage comes with state-of-the-art security. Users must follow the vendor’s security guidelines. Negligent use can compromise even the best protection.

Cloud Storage Security Best Practices
Cloud storage providers store files redundantly. This means copying files to different physical servers.
Cloud vendors place these servers far away from one another. A natural disaster could destroy one data center without affecting another one hundreds of miles away.
Consider a fire is breaking out in an office building. If the structure contains paper files, those files will be the first to burn. If the office’s electronic equipment melts, then the file backups will be gone, too.
If the office saves its documents in the cloud, this is not a problem. Copies of every file exist in multiple data centers located throughout the region. The office can move into a building with Internet access and continue working.
Redundancy makes cloud storage security platforms failure-proof. On-site data storage is far riskier. Large cloud vendors use economies of scale to guarantee user data is intact. These vendors measure hard drive failure and compensate for them through redundancy.
Even without redundant files, only a small percentage of cloud vendor hard drives fail. These companies rely on storage for their entire income. These vendors take every precaution to ensure users’ data remains safe.
Cloud vendors invest in new technology. Advances improve security measures in cloud computing. New equipment improves results.
This makes cloud storage an excellent option for securing data against cybercrime. With a properly configured cloud solution in place, even ransomware poses no real threat. You can wipe the affected computers and start fresh. Disaster recovery planning is a critical aspect of cloud storage security.
Invest in Cloud Storage Security
Executives who invest in cloud storage need qualified cloud maintenance and management expertise. This is especially true for cloud security.
Have a reputable managed security services provider evaluate your data storage and security needs today.
Recent Posts
What is Social Engineering? Understanding The Latest Types & Threats
Social engineering has become a malicious tool for hackers to conduct cyber attacks.
Virus protection or your firewall won’t help if you are duped into clicking a malicious link thinking it came from a colleague or social media acquaintance.
Here’s what you need to understand to stay safe and protect your data.
What is Social Engineering?
By definition, social engineering is an attack vector used to gain access to gain access to networks, systems, or physical locations, or for financial gain by using human psychology, rather than using technical hacking methods. It relies on social interaction to manipulate people into circumventing security best practices and protocols.
Social engineering is the new preferred tactic among the hacker community. It is easier to exploit users’ flaws than to discover a vulnerability in networks or systems.
Understanding different types of social engineering attacks is an essential aspect of protection.
TYPES OF SOCIAL ENGINEERING THREATS
Phishing
Phishing is one of the most common types of social engineering.
When a website, article, or online community is presented to a targeted individual as authentic and secure but instead uses a URL that is not official it is called phishing. Hackers and thieves alike utilize phishing attacks to gain false hope and trust from potential victims to receive sensitive information such as usernames, email addresses, and passwords that are linked to social media accounts and bank login websites. Phishing involves the participation of users for the theft of information and data to be completed.
Phishing is most common among users who are not well-versed in browsing the internet or those who are new to using social media and online resources to search for information, content, and media. Many phishing attacks target individuals who are elderly or those who do not work in the tech industry to obtain sensitive information without the risk of being caught.
Preventing phishing starts by ensuring each URL you visit is official and authentic. Phishing attacks often target social media platforms, banking websites, and online service sites to gather crucial information from users who fall for the faked URL.
Phishing attempts increased by 30 million from 2017 to 2018, according to Kaspersky Lab.

Baiting
Baiting is used in both the digital and physical world.
Baiting consists of leaving devices in public areas that are packed with malware, spyware, or other damaging software which is then used to steal and collect the information of users who are tempted to see the contents of the device.
Most commonly, flash USB drives are left in areas such as bathrooms, libraries, subway stations, or even on airplanes in hopes to attract the curiosity of individuals.
Once the user plugs the device into their computer, malware is downloaded onto the hard drive.
Keyloggers and malicious software then send data directly to the hacker, allowing them access to websites and accounts.
Digital baiting is also found in advertisements that showcase enticing deals or free items, only to lead users to websites that immediately trigger a download of malware and spyware software.
In some cases, malware and spyware programs are disguised as traditional software or software updates.
When browsing for software, it is imperative to verify the authenticity of the URL and the provider.
Spear Phishing
Spear phishing is designed to personally attack an individual or organization to appear more authentic and legitimate.
Spear phishing attacks often utilize a user’s personal information or details about an individual to gain the trust and curiosity of the user before stealing information, installing malware, or delivering a keylogger to the individual’s hard drive. Hackers who use spear-phishing tactics are well-versed in scraping data of users from social media sites, official blogs, and even email newsletters or previous online leaks and security breaches.
When a user is presented with a spear phishing attack, they are likely to feel that the attack is a genuine attempt to share information, content, or free products due to the overwhelming personal details provided.
Spear phishing is becoming more popular than traditional phishing attacks as users become aware of checking URLs and verifying the websites they shop and browse on whenever they are online. With a spear phishing attack, it becomes increasingly difficult to determine whether or not the URL or information is malicious, even for those who are seasoned internet users.
Tailgating
Tailgating is a social engineering threat that is purely physical and involves real-world interaction to work. When a hacker is interested in obtaining the information of a specific individual or organization, they may follow them to local cafes or locations where free Wi-Fi is available. Hacking into a public Wi-Fi hotspot provides thieves with the ability to learn more about individuals using the connection while obtaining sensitive and personal data.
Other forms of tailgating may include asking an individual to utilize their access pass while entering a building or going to work in their office by lying about forgetting their pass to quickly steal information. Tailgating is often used by hackers who have a vested interest in an individual or organization believed to have wealth or unsecured banking accounts that are easy to hack and steal from once access is provided.
Tailgating is one of the most personal forms of social engineering and also one of the most threatening in the real world.
Remaining vigilant and secure when accessing Wi-Fi hotspots or internet anywhere outside of the home is essential to prevent the risk of exposing personal information and data that belongs to you. It is also necessary to maintain an encrypted and protected internet connection to keep potential hackers from obtaining access to your data.
Scareware
Scareware is extremely successful in obtaining user information and financial details.
Often presented as popups or programs while prompting users with warnings or threats to receive information such as names, credit card details, and even social security numbers.
An individual is likely to be threatened with contact from the FBI or other areas of the government, prompting quick responses to avoid further action. When users are unfamiliar with this tactic, they are much more likely to fall for a scareware attack.
Scareware does not always include personal or direct threats. Scareware is also commonplace when browsing on unofficial websites or sites that provide free content or programs that are otherwise not free.
In many cases, scareware is used to prompt individuals to download malicious software due to a threat of spyware or malware already infecting the user’s hard drive.
Once the individual downloads the solution presented by the scareware campaign, their computer is compromised and hackers then gain direct access to personal information or the entire hard drive itself.
Pretexting
Pretexting scams are used to collect personal information from individuals by impersonating police, government officials, bank account managers, or even co-workers.
Hackers use pretexting to target unsuspecting individuals who are likely to feel threatened or fearful of retribution if they do not share the requested information. Pretexting is done over the phone, via email, or in some cases, even with the use of social media messenger applications.
Perpetrators who use pretexting often inform individuals that they are in need of highly sensitive information to complete a task or to prevent the individual from legal trouble.
When an individual feels threatened, vulnerable, or scared, they are much more likely to reveal bank account numbers, routing numbers, social security numbers, and other sensitive data.
Quid Pro Quo
Quid pro quo involves hackers requesting information from unsuspecting individuals with the promise of offering something in return.
Individuals presented with a quid pro quo attack are likely to receive offers of compensation, free vacations, or gifts such as new products that are most relevant to the individual’s lifestyle.
Quid pro quo attacks occur over the phone, while using social media, or even through traditional email newsletters that have been hacked, compromised, or impersonated. Users are presented with the promise of money, free travel, or gifts in exchange for login information, credential verification, or other sensitive details such as social security numbers and bank account and routing numbers.
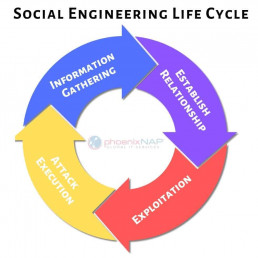
3 Phases of Social Engineering
Research Phase
The first phase of any social engineering attack is research. During this phase, attackers search for information about you. The easiest route to find potential information is through a web or social media search. Social media security best practices are key as people often post personal information that attackers can use against them.
If the target is a business, attackers may be able to collect information about employees or security rules that may aid future attacks. Managers and other high-value targets are at a higher risk because attackers are more likely to do more research for these targets.
Skilled social engineers often research what companies you might work with. They can then use this information to better pretend to be a technician or consultant with the company to gain access to sensitive areas. Through this pretext, they may trick targets into revealing sensitive or secure data.
Contact Phase
After the research phase has finished, attackers will move on to the contact phase. During this phase, attackers will use researched information to look for other weaknesses and gain the target’s trust. This often includes pretending to be someone the target trusts. Once the victim trusts the attackers, the attackers can then leverage this for more information or access.
For example, attackers might use social media to find which employees of a company have left for vacation. They might then contact the company pretending to be a vacationing employee who forgot to give them important information before leaving. Knowing that one employee was out of the office, another person at the company might try to help them by sending attackers the desired information.
Attack Phase
The attack phase builds on the previous two phases. In most cases, this means that attackers have the necessary information and access to you or your company’s systems.
Basic attacks will use this access to steal information from a system, but some hackers go further. Advanced attacks will use this access to aid them in future attacks. They might then leave a backdoor into the system, or copy your credentials.
Understand Social Engineering Threats
Social engineering is not new. However, it is becoming the go-to attack vector of hackers.
With a clear understanding of the definition of social engineering, take control of your online activity while remaining protected.
Recent Posts
2020 Cybersecurity Trends: 31 Experts on Current Issues
This article was updated in December 2019.
According to expert estimates, we are trending for another record-breaking year for data breaches.
Is your company prepared?
Cybersecurity continues to be a hot topic in both media and business. The reasons are evident – the last two years saw consistent growth in cyber breaches with 2018 hitting a new record high. Namely, the recent 2018 Annual Data Breach Year-End Review by Identity Theft Resource Center revealed a 44.7 percent growth in the number of cyber incidents compared to 2016.
Developing at this pace, cybercrime threatens to become even more devastating for businesses in years to follow. For companies across the globe, this strengthens the imperative to implement advanced data security strategies. To do so efficiently, they need to understand what are the most significant threats to your data.
Below are some expert predictions regarding business data security to help you prepare for a new year of cybercrime. Coming from industry experts, these insights will help you protect your data and secure your business long term. Read them through and reconsider your current practices. Is your cybersecurity strategy missing anything?
We are thankful to everyone who participated, and we appreciate the opportunity to collaborate with such great minds. We hope you will find the tips listed below helpful and inspiring to prepare your business for another year of cyber incidents.
1. Privileged account misuse
Csaba Krasznay, a security evangelist, believes that in 2020, privileged account misuse will continue to be the biggest threat to the security industry. He suggests that organizations should start to mitigate the threats using the following strategies:
An increased focus on user behavior analytics over IT assets.
Historically, IT security has mainly been focused on securing IT components, such as data, related processes, IT services, servers, networks, etc. However, if the user is the weakest link in the IT security chain, organizations should place more emphasis on identity and access management.
The implementation of a higher degree of automation through machine learning.
AI-based analysis of behavioral biometric data will be the next major trend in cybersecurity and data protection. Sophisticated machine learning algorithms can build up a profile of a user’s typical behavior, identify unusual patterns of activity and highlight potential threats in real-time before they have a chance to materialize. By automatically detecting suspicious data, the whole security process becomes more efficient, obviating the need for a painstaking manual review of log data.

Csaba Krasznay, Security Evangelist, Balabit
Csaba Krasznay is Balabit’s Security Evangelist and an Assistant Professor at the National University of Public Service in Budapest, Hungary. He is responsible for the vision and strategy of Balabit’s Privileged Access Management solutions.
2. Insider cyber security threats and inadequate security strategies
Assuming that you will be able to stop all breaches.
Too much emphasis and investment are focused on protecting the endpoints and connected devices on the network with the goal of preventing all breaches. It is time to acknowledge that even the most experienced security team cannot possibly keep all cybercriminals out – and insider threats will always be a challenge. Instead, there must be a shift toward active defense. This mindset will give the victims of hackers a pathway towards preventing more damage. The question should not be: “How can I make sure our systems are never penetrated?” Instead, the questions to ask are:
“When a hacker penetrates the network, what will he be able to access? How can we make sure the hacker can’t open, share, print or download any sensitive files?”
Entrusting encryption as your savior.
In 2020, we will see lots of investments in encryption and other data security technologies. Buyer beware. Encryption products, although crucial in many contexts and notoriously hard to use, will fail to stop the problem of data loss. Keys will be lost or stolen, at times by the companies who generate them. Users will be confounded by managing their own keys, which is hard to do when also trying to control one’s passwords.
Bad actors within your company.
Employees are one of the top cybersecurity risks to organizations by merely clicking malicious URLs or bypassing security controls, however unintentional. But the frustration festers into a paternalistic, us-vs-them attitude between security operations center teams and the rest of the organization.
Try googling “there’s no patch for stupidity,” or “people are the weakest link in the cybersecurity chain.” They have become the rallying cries for not knowing how to deal with what the sec pros dub “the human element” as though it were a zoonotic disease. Users will continue to be a weak link in the chain in 2020, but the problem is that experts are pretty bad at figuring out why.

Dr. Salvatore Stolfo, Chief Technology Officer, Allure Security
Dr. Salvatore Stolfo is a professor of Artificial Intelligence at Columbia University. He has been granted over 47 patents and has published over 230 papers and books in the areas of parallel computing, AI knowledge-based systems, data mining, computer security and intrusion detection systems.
3. The use of machine learning for hacking attempts
Stolen customer data almost inevitably leads to increases in the overall volume of chargebacks, so we work closely with partners to help clients mitigate that risk. One of the biggest overall threats I am seeing is that hackers and fraudsters are more and more using our own technology against us.
Take machine learning, for example. With the ability to process mass amounts of data and adjust algorithms on the fly, we can detect suspicious behavior faster, and with increasingly higher accuracy.
However, criminals are doing the same thing. They use machine learning to calculate defenses, feed false information to detection programs, and the like.
I also believe internal threats, disgruntled employees, for example, will continue to grow. Externally, I do not doubt that instances of ransomware will increase, probably dramatically: fraudsters have shown that such attacks WORK—and are profitable—so there is no reason to believe they will decrease.

Monica Eaton-Cardone, Co-founder and COO, Chargebacks911
Monica Eaton-Cardone is an international entrepreneur, speaker, author, and industry thought leader. She is the co-founder and COO of Chargebacks911, a global risk mitigation firm helping online merchants optimize chargeback management globally through offices in North America, Europe, and Asia.
4. Organized hacking efforts
Gregory Morawietz suggests that in 2020, one of the most significant threats will be organized efforts. More attacks from state-backed hackers will take place. Large-scale social attacks, trying to influence political or modern events.
When it comes to his advice on how businesses should prepare, Morawietz suggests:
Buy a firewall, have a security policy, keep strong passwords and treat your employees fairly and with respect.

Gregory Morawietz, IT Security Specialist, Single Point of Contact
Gregory Morawietz is a cloud and IT Security Specialist with over twenty years’ of network and security experience. He has worked with hundreds of firms on improving IT environments, architecting cloud environments, consulting and integrating technology for the enterprise network.
5. Ransomware and zero-day attacks.
Ransomware should be close to the top of everyone’s cybersecurity trends list. Disgruntled employees or former employees will still launch attacks. We will see more zero-day attacks as the market for vulnerabilities heats up.
What should businesses do to prepare?
Busy business leaders need to take these six catchy words to heart:
- Care and share to be prepared.
- Care enough about cyber-security to invest in it, and share what you learn with other good guys.
- Level the playing field because the bad guys already know about your security operations.

Greg Scott, Senior Technical Account Manager, Infrasupport Corporation
I’m Greg Scott, author of Bullseye Breach, a cybersecurity book disguised as fiction with the story about how elements of the Russian mob penetrated retailer Bullseye Stores and stole 40 million customer credit card numbers.
6. Lack of cybersecurity talent.
One of the top cybersecurity trends in 2020 will be a lack of cyber-security professionals. We are still in a position where almost half of the vacancies go unfilled, and a lack of staff means a lack of solutions to simple problems. Applying basic levels of protection in smaller businesses, or training and awareness in larger companies are all things that require human resources and can make a big difference to the every-day threats.

Karla Jobling, MD, Beecher Madden
Karla Jobling is MD of BeecherMadden. She has recruited for information security positions for over ten years, managing client requirements in the USA, Europe, and the UK.
7. Inadequate cyber hygiene.
In 2017, we saw the widespread impact of the Petya and WannaCry attacks, both of which were a direct result of businesses failing to do the basics of cyber hygiene.
The fact is cyber hygiene was the problem ten years ago. Cyber hygiene was the problem (in flashing lights with horns blaring) this year. I am completely confident it will be a problem again in 2020. This is because enterprises find it incredibly difficult to demonstrate active control over their cyber hygiene and thus efficiently remediate top cybersecurity risks. This is because the larger the organization, the more challenging it is to maintain these ‘basics,’ such as identifying their assets, updating software, patching it, running standard controls and educating the users.
Given that 80% of all cyber security threats could be stopped by addressing the issue of cyber hygiene, it needs to continue to be a key focus for security teams around the globe.

Nik Whitfield, Computer Scientist, Jones Consulting (UK) Ltd
Nik Whitfield is a noted computer scientist and cybersecurity technology entrepreneur. He founded Panaseer in 2014, a cybersecurity software company that gives businesses unparalleled visibility and insight into their cybersecurity weaknesses.
8. Trending types of cyber security threats
Internet Of Things
Using “smart” devices for a malicious activity like mining for bitcoins or DDOS will become more commonplace. These threats are coming from everywhere, but can be avoided!
Corporate Espionage
Undetected hacks that leave things operating as usual, but are actually siphoning off critical data. Again, these threats come from everywhere, including insiders within or closely associated with an organization. This type of risk can be mitigated by going back to the basics and getting a third-party evaluation.
You don’t know what you don’t know
Having a blind trust in cloud companies and assuming that the protections they implement are for you/your company’s best interests. Only YOU are responsible for YOUR security.

Chadd Kappenman, CISO, SMS AZ
Chad Kappenman is Chief Information Security Officer (CISO) at SMS AZ , a local Arizona company that enables small and medium-sized businesses to be proactive about their security efforts.
9. More Advanced hacking technologies
Cybercriminals are incredibly sophisticated and developing ways to “listen in” now, not just to grab credit card numbers shown in text files. Software already exists that can “tap” a voice call and understand it has heard a credit card number, expiration date, or a unique code. It can transpose that data, store it, and sell it within seconds.
With active listening in the gaming space, for example, a cybercriminal could target young people who are completely unaware of the threat. What they are saying can be turned into valuable information, not just to steal identities or money, but to find future human trafficking victims. These technologies will become even more advanced.

Patrick Joggerst, Executive Vice President of Business Development, Ribbon Communications
Patrick Joggerst is the Executive Vice President of Business Development for Ribbon Communications, a secure real-time communications company. Previously, Patrick was EVP of Global Sales & Marketing for GENBAND.
10. Improperly secured cloud data
In 2020, we expect to see “more of the same.” Ransomware is very lucrative for cyber-criminals. It’s perhaps the easiest cybercrime to monetize because the criminals are taking payments directly from the victims. We advise companies to double down on basic security measures. These include a layered defense such as firewall with URL and malicious site blocking, filtered DNS, segmented networks, and security clients (anti-virus and anti-malware). But most of all, employee awareness and training is always the best ROI.
Secondly, expect more data breaches. 2018 was perhaps a record year for publicized data breaches – both in number and in scope. We advise companies to revisit all their stores of information and ensure they have got the proper controls and encryption – encryption at rest, encryption in transit, etc. This is another area where an employee error can overcome the best technology defenses. So employee security training awareness programs are also critical.
Lastly, there were quite a few instances of improperly secured cloud data in 2018. A lot of “MongoDB” databases with default admin credentials and cloud storage buckets were left wide open. This will continue into 2020. Companies need to perform regular SOC audits and reports on their access controls and settings on cloud services. The cloud doesn’t make security issues go away. In some respects, it increases the “attack surface.”

Timothy Platt, VP of IT Business Services, Virtual Operations, LLC
Tim Platt has almost 25 years of experience in multiple areas of technology including programming, networking, databases, cloud computing, security, and project management. He currently works at Virtual Operations, LLC, providing technology consulting in the Orlando, FL area.
11. Weak passwords continue to be a trend in cybersecurity
This year, companies and consumers were plagued with massive cyber attacks and security breaches – from WannaCry to Equifax, companies in 2020 will have to do a lot to win back trust and ensure a safer experience for the customers they serve.
We have all read the tips on how to secure a website, but one misguided argument encourages individuals to create stronger passwords. What if the solution is to rid the world of passwords altogether?

As the former Worldwide Fraud Director of American Express and CEO of Trusona, cybersecurity expert Ori Eisen has dedicated his life to fighting crime online. Working other notable influencers like Frank Abagnale (former conman played by Leonardo DiCaprio in Catch Me If You Can), Eisen is on a mission to protect businesses and consumers across the globe by replacing static usernames and passwords with secure identity authentication, thus eliminating threats of organized cybercrime and rampant malware. Eisen hopes companies will continue to make the jump towards a password-less future.
12. Cyber-Skills Gap: We Are ALL the Problem
Cybersecurity training is everyone’s responsibility. While online training isn’t the golden arrow for the massive, industry-wide skills gap, it does intertwine security in the culture of the organization and raise awareness and culpability at all levels. As an employee, don’t let anyone tell you there’s no budget for continued training. Make your case on how it is beneficial for you and the organization. Here are five diligence practices that organizations can put in place before the ball drops:
- If your business depends on the internet in any way, get a third-party DDoS protection service for business continuity.
- Classify your digital assets immediately, and just as quickly fortify the highest risk areas first.
- Find the hidden threats, get them out, and don’t let them back in. A defensive security approach will only get you so far.
- Programmatic vulnerability scanning software can identify a substantial number of holes in their defenses, and when found, the organization must make plans to continuously and expeditiously patch their systems. Rule of thumb: There are no excuses.
- AI-based malware prevention should be the de facto standard on all endpoints, not traditional signature-based antivirus.
Attacks will happen
Nation-state attackers continue to challenge the stability and safety of our critical infrastructure. Criminals are opportunistic and gladly enter unlocked doors, especially since companies continue to disregard their fiduciary responsibility to invest and protect themselves from cyber attacks. Because of this, we will see an increased number of attacks, they will be successful, and they will be public. Additionally, massive Denial of Service (DoS) attacks will increase and cripple businesses and the internet itself.

Kathie Miley, Chief Operating Officer, Cybrary
As the COO, Kathie Miley brings more than 20 years of experience to help design and implement company business strategies, plans, and procedures, oversee daily operations of the company’s sales and marketing efforts, assist company leadership in strategic ventures, and manage relationships with all business customers, partners, and vendors.
13. Ransomware becoming more sophisticated
With data breaches and leaks on the radar of every industry, leaders are looking to cybersecurity experts for guidance more than ever.
The top IT Security Threats we expect to see include an increasing number of more sophisticated ransomware attacks that are difficult, if not impossible to detect. In response, leading IT professionals will place more emphasis not only on endpoint security but also on corporate data-protection.
For many government-based organizations, tech startups, and research labs, breaches can mean exposed vital and sensitive data. Although the cloud is a looming entity in the enterprise, it is estimated that half of the data lives on endpoint devices. We will see an increase in large-enterprise attacks costing hundreds and millions of dollars in revenue. Additionally, hackers will press for increased ransom due to easier information access.
To top off the evolution of ransomware, we’ll continue to see Petya-grade attacks threaten businesses and evolve into tools for hackers to leverage in 2020. With this in mind, we need to question the ability for an organization or business to protect itself. The only way companies can solve this is by adopting and streamlining evolving technology.

Ian Pratt, President and co-founder, Bromium
Ian Pratt is Co-Founder and President at Bromium, where he is focused on the continued rapid growth of the business through delivering the superb security provided by Bromium’s products to mainstream Enterprises.
14. New technologies will create new loopholes.
With the rise of Bitcoin, Ethereum, and other cryptocurrencies, many businesses and corporations started exploring blockchain technology. It is estimated that more than 50% of corporations currently expecting to integrate with this technology sometime this year.
However, with new technologies comes a valuable opportunity for cybercriminals. We have already started witnessing that as news are coming out every other week of cyber criminals hacking into cryptocurrency exchange companies and hacking corporations using this technology. This is expected to continue heavily in 2020, with more criminals and hackers finding similar opportunities.
Businesses and corporations that choose to adopt such an early-stage technology are also under the threat of attracting similar attacks by hackers. To prepare for such threats, businesses who plan on using blockchain technologies should focus heavily on building the right security infrastructure to protect themselves from hackers who are taking advantage of the vulnerability of the blockchain technology at this stage.

David Kosmayer, CEO and Founder, Bookmark Your Life Inc.
David Kosmayer is CEO and Founder of Bookmark Website Builder, an AI-powered website building disrupting the website design industry. David created his first company at 22 just coming out of college.
15. Smartphone risks
Enterprise
For several years now, cybersecurity has been a top priority for businesses of all sizes and industries. And yet, nearly every month another massive data breach takes place, leaving businesses and their customers highly vulnerable.
Even the most established organizations with ample resources are not safe (take Verizon’s or Chipotle’s recent breaches, for instance), and worse, cybercrime levels are only continuing to rise. The first attack (which is inevitable) of 2020 will set the tone for the year.
Consumer devices
Any individual who owns a smartphone or laptop needs a way to protect themselves against the ramifications of identity fraud should their personal information become compromised. Savvy consumers that are paying attention might agree that relying solely on business to protect one’s personal information is naive, and no longer enough. Given the realities of our increasingly complex, digital world, it behooves consumers to work to protect their privacy on their own.
Establishing company-wide security policies.
All it takes is an employee to click an insecure link, and your server is no longer secure. Implement a policy to keep employees informed of the latest scams and educate them on how to be vigilant and avoid downloading information from emails they do not recognize. Highlight the fact that their participation will boost efforts to keep an eye out for fraud and attacks.
Consumers can get the right cyber insurance.
The loss of sales caused by cybercrime has been reported to cost SMEs nearly $21,000. That could put a business under. Cyber insurance can lessen the financial blow of a cyber attack and give your business the support it needs to get back on track. Some business insurance policies may include limited coverage against cyber attacks compared to a standalone cyber insurance policy. It is imperative to speak with a licensed insurance agent with cyber insurance experience to understand the proper type of coverage your specific business needs.

Keith Moore, CEO, Coverhound
Keith Moore is the CEO of insurance technology leader CoverHound® and the Founder & CEO of CyberPolicy™, both of which are based in San Francisco, California.
16. Black market demand for personal information continues to surge.
Seeing as we’re in the midst of two giant data breaches with Equifax and Uber, I expect us to see much of the same in 2020. A person’s identity, such as their SSN or credit card information, is extremely valuable. As long as people on the black market keep purchasing people’s info and identities, hackers will continue to attack large data stores and take people’s information. Luckily, the implementation of blockchain technology could mitigate much of this issue, but widespread adoption is still ways away. Also, hackers always seem to find ways around the newest data security, anyway.

Evan Tarver, Fit Small Business
Evan Tarver is a staff writer at Fit Small Business, specializing in Small Business Finance. He is also a fiction author and screenwriter.
17. Email phishing
Researchers in the second half of 2017 have been finding more and more flaws in the way email clients deal with fraudulent emails. There have been further weaknesses discovered in email protocols themselves.
Moreover, automated tools that make it nearly impossible to detect fraudulent emails have recently been published. Phishing is already one of the most difficult attack vectors to defend, and this will only become more difficult. Businesses should focus on training their staff to prepare for more fake emails and spot fakes using clues in the email.

Pieter Van Iperen, Founder, Code Defenders
Pieter VanIperen is a Founding Member of Code Defenders, a collective that protects the long tail of the internet, an Adjunct Professor of Code Security at NYU, a Certified Pen Testing Engineer (Ethical Hacker) and a Certified Secure Web Application Engineer.
18. Continued evolution of malware trends
Since 2017 was hallmarked by a record number of hacks to major data records, like Equifax and Verizon, David believes the focus should be put on storing and protecting precious data in a place that can’t be tampered with or altered – an immutable bucket.
According to David, the biggest mistake that IT people make is worrying about making their data hack-proof rather than keeping the focus on storing it someplace safe. Nothing is completely hack-proof, but lost data can certainly kill a business. If you have data that is stored in an immutable bucket, it cannot be altered or deleted. If someone gets a virus that is attempting to take over your data and encrypt it, this will not be possible. It will just produce an error message saying that the data cannot be altered. If all of those people had put their data into an immutable bucket, it would still be there in perfect condition because there’s no way the person or a piece of software could alter the content. If you have sensitive business data, it is worth putting into an immutable bucket and making it immune to ransomware and other threats.

David Friend, Co-founder and CEO, Wasabi
David has been a successful tech entrepreneur for more than 30 years. David co-founded Carbonite, one of the world’s leading cloud backup companies, and five other companies including Computer Pictures Corporation, Pilot Software, Faxnet, and Sonexis.
19. Increased reliance on convenience services
On the edge of another year, the wrath of cybersecurity threats continues. Given the breaches in 2017 such as Equifax, Sonic, FAFSA, and Verizon, we are going to continue feeling the repercussions of identity theft and ransomware. The nation needs to prepare for the when and how this personal information is going to be used against us. And, individuals need to be careful about what they are doing online. The busier our lives get, the more we are relying on convenience services such as Uber, DocuSign, and America’s JobLink, but unfortunately, these come at the cost of potential identity theft.
What should businesses do to prepare?
Businesses need to stop looking for cybersecurity professionals in the wrong places and using outdated ways of hiring employees. We find that many companies lack the understanding of potential cyber threats and also are unfamiliar with the state of the cybersecurity landscape. Therefore, they don’t know better than to rely on a resume than to ask a potential employee to show proof of their skills being validated. This is the main reason the National Cyber League started providing NCL Scouting Reports. Not only does this report reflect personal cybersecurity skills growth, but cybersecurity students are getting jobs as it shows employers their skills are tested and validated.

Dan Manson, National Cyber League Commissioner, Professor in Computer Information Systems (CIS) at California State Polytechnic University, Pomona (Cal Poly Pomona).
Dr. Manson has taught Information Systems Auditing, Internet Security and Computer Forensics in the College of Business Administration Computer Information Systems undergraduate and Master of Science programs. Dr. Manson has also served as the CIS Department Chair and Campus Information Security Officer.
20. Increased Attacks on emerging blockchain solutions
Based on the past two years, 2020 may very well see a ‘next phase’ of attacker activity that should have CISOs on high alert:
- Acceleration of data breaches targeting individual information similar to those we have seen throughout last year – such as Equifax, the 198 million US voter registration breach, the IRS taxpayer information and the ongoing medical information breaches.
- New attacks upon individuals or entire systems as a result of the information mined from these breached records, or the use of it for identity theft or spoofing to access higher-profile assets or objectives
- Increased attacks and attempts upon Bitcoin and emerging blockchain solutions because of the high financial motivation, as well as the assertion that these systems offer stronger security and thus resulting confidence placed on these systems by the organizations that employ them
- Social engineering has become the top-ranked attack vector, along with identity theft as one of the top crimes in the US. The information obtained from these breaches across 2017 will provide attackers substantial insight into how best compromise the employees of organizations in their personal lives, or gain access to government or business assets through them, including those with privileged access.
Organizations should stay vigilant and double-down on employee education and awareness, increase controls on identity and access, and improve audit trails and their frequency. Most importantly, they need to employ tools that implement advanced anomaly detection methods to determine when information and systems are being accessed inappropriately.

Monika Goldberg, Executive Director, ShieldX Networks
Monika Goldberg is a dynamic executive who brings over 25 years of industry experience from leadership roles at infrastructure and security companies such as Intel Security, McAfee, Cisco, HP, and NetApp. She currently serves as Executive Director at ShieldX Networks, a Gartner Cool Vendor that she helped groom.
21. Network endpoints becoming increasingly difficult to secure
Data security failures and cyber attacks such as the Equifax, Yahoo and OPM breaches demonstrate the extent and diversity of security challenges IT professionals are facing around the world.
The increased usage of laptops, smartphones and IoT devices all represent network endpoints that are increasingly difficult to secure, as most employees are always connected via multiple devices. In 2020, with the growing complexities of endpoint security, emphasis will be placed on tracking and managing how users access corporate data across each of their devices. When analyzing the flow of data for threats and vulnerabilities, powerful search and analytic tools can then deliver necessary, actionable intelligence.

Rob Juncker, Senior Vice President, Product Development at Code42
As senior vice president of product development, Rob leads Code42’s software development and delivery teams. He brings more than 20 years of security, cloud, mobile, and IT management experience to Code42.
22. Sophisticated cyber attacks within your infrastructure
No organization is always 100% secure. Detecting and stopping sophisticated cyber attacks that have bypassed traditional perimeter security systems and are now active within your infrastructure should be on your top 3 list of 2020 security priorities.
Security teams will need to factor in a slew of unforeseen threats next year, including those from bad actors scanning the Dark Web in search for the newest attack tools.
Increasingly, security and IT teams are collaborating to address these stealthy attacks before they do real damage. This includes the use of IT infrastructure and security solutions that work together. Leveraging new technologies such as AI-based machine learning, analytics and UEBA can be extremely useful to improve attack discovery and decrease attack dwell times, as well as to send alerts which activate automated or manual enforcement actions that suspend potential attacks until they can be thoroughly investigated.

Larry Lunetta, Vice President of Marketing for Security Solutions, Aruba, a Hewlett Packard Enterprise company
In his current role as Vice President, Security Solutions Marketing for Aruba, a Hewlett Packard Enterprise company, Larry manages the positioning, messaging and product marketing for the portfolio of security products and solutions that Aruba brings to market.
23. Cybersecurity threat: Advanced email phishing attacks like Mailsploit
While it is all but universally accepted that email phishing will remain the primary attack vector in 2020, recently discovered vulnerabilities such as Mailsploit, an exploit designed to spoof an email senders name to bypass DMARC, present substantial challenges for organizations phishing mitigation and email security.
To reduce the risk of spear-phishing, spoofing and impersonation vulnerabilities, organizations should consider implementing the following steps:
- Augmenting the representation of senders inside the email client by learning true sender indicators and score sender reputation through visual cues and metadata associated with every email
- Integrating automatic smart real-time email scanning into multi anti-virus, and sandbox solutions so forensics can be performed on any suspicious emails either detected or reported
- Allowing quick reporting via an augmented email experience, thus helping the user make better decisions

Eyal Benishti, Founder & CEO, IRONSCALES
Eyal Benishti is a veteran malware researcher, co-founder and CEO of IRONSCALES, the world’s first phishing prevention, detection and response provider.
24. Outdated equipment
2017 was a year of technical innovation, and that includes innovative cyber crime as well. We’ve seen ransomware evolve in unexpected ways, becoming a malicious enterprise operation. With vulnerabilities like KRACK infiltrating the standards we once thought secure, it’s more important than ever for businesses to make sure their equipment is up to date. Regular updates and security patches are essential!
What should businesses do to prepare?
Employee security training is equally important, especially when it comes to phishing scams. As with the advances in malware, cybercriminals are getting smarter about sneaking past the safeguards that keep them at bay. The recent cyber attacks attempting to replicate PayPal and Netflix, programs we frequently use in our personal lives, remind us to be aware of any email that hits you or your employees’ inboxes. Employee training and education serve as a critical barrier against these kinds of attacks, protecting from new cyber threats in the coming months. It only takes a single failure due to lack of proper training to take down an entire network.

Amy O. Anderson, Principal, Anderson Technologies
Amy O. Anderson is Principal of Anderson Technologies, a St. Louis IT company that optimizes technology to meet the demands of small and mid-sized businesses. For over 20 years, Anderson Technologies has provided the IT solutions that firms need to be competitive in today’s marketplace.
25. The development of AI and automation
The development of artificial intelligence and automation is the most imminent and dangerous trending threat that we’ll see in 2020. Artificial intelligence has already been weaponized, automating the process of malware dissemination and data retrieval. Machine learning has already been used to combat AI cyber attacks, but companies both large and small will be hit hard if they don’t adapt.

Harrison Brady, Communications Specialist, Frontier Communications
26. Mass growth of digital technologies
Mass adoption of digital technology contributed to a wider dissemination of data. Environments which hold Personally Identifiable Information (PII) are constantly under external attack. If the information is stored online, one can assume it will be compromised.
Businesses will require strong data governance strategy, framework and controls together with the increased corporate use of social media tools and technology to mitigate this risk.
In addition to this, the rise of cloud-based technology platforms such as Amazon and Salesforce with an increased need for continuous delivery will bring new threats of unauthorized access by developers and third parties to production environments. These threats need to be balanced with the increasing demand for continuous delivery in a disruptive technology environment.
The focus of current cyber security issues moves to controlling what matters vs. controlling everything and working out ways to achieve the desired outcomes vs. locking everything down.
Increase in volume and sophistication of ransomware attacks and cyber terrorism is crippling the global economy. Ransomware could severely impact organizations globally where the threat is not mitigated. Businesses need to take this threat seriously if they are to avoid falling victim to ransomware attacks similar to the May 2017 cyber attack by the WannaCry ransomware cryptoworm.

Felicity Cooper, Head of Technology Risk at the Commonwealth Bank of Australia
Felicity Cooper is an expert in risk management solutions – acting as General Manager responsible for Line 1 Technology Risk across Enterprise Services since May 2016, and as Head of Technology Risk, Retail and Wealth, at the Commonwealth Bank (CBA) for the last four years.
27. Crypto-jacking
The crypto-jacking activity has been exploding, and we will undoubtedly see more threats in 2020, particularly as the value of cryptocurrencies escalates. Secondly, the cybercriminal underground will continue to evolve and grow further this year. Apart from that, there is a very strong chance; the state-sponsored attacks will increase immensely.
With cyber attacks on the upsurge, every industry has become a target. However, by becoming proactive towards cyber-security and employing innovative security strategies and tools, along with spreading awareness about the epidemic, organizations can indeed enhance their security against countless threats and avoid expensive data breaches. Many big organizations are improving their IT systems, but we need to do more. We have more devices, more data, more threats, more sophisticated attacks, and more attackers. We must group together as an industry to push in the opposite direction: towards blazing-fast solutions on a majestic scale. That is our only hope. And over the next decade, organizations that assure results without speed or scale will perish, as they should.

Kashif Yaqoob, Brand Strategist, Ivacy
A Digital security and Privacy Enthusiast, working at Ivacy with a focus on developing sustainable brands in an increasingly complex media landscape.
28. Cultural inertia grows as a cybersecurity threat
One of the most significant cybersecurity trends will be cultural inertia. Not moving forward because you are not sure of how to get started or due to having the stance that “security is important, but not a priority” will most likely mean that your company will be the next headline news.
2017 marked yet another year of massive breaches. Yahoo and Equifax topped the charts, but there were, unfortunately, plenty of other incidents that punctuate the fact that security is not yet a top priority for many companies. If security priorities are not first, they are last. Security initiatives need to be embedded into overall programs and objectives, not an afterthought or a periodic exercise.
Unfortunately, I fear that there will continue to be substantial security breaches and issues in 2018, especially as more IoT devices flood the market. This will result in more regulatory discussions, which I hope actually help increase resiliency.

Mike Kail, CTO and co-founder, CYBRIC
Mike previously served as CIO at Yahoo and VP of IT operations at Netflix and has more than 25 years of IT operations and technology leadership experience. He also currently serves as a technical and strategic advisor to a number of technology companies.
29. Advanced persistent threats gaining more AI capability in 2020
One of the biggest cybersecurity trends we will see in 2020 are improvements to technology and services that already exist. For example, social engineering will continue to get better, ransomware will continue to evolve, attacks on exploits will continue to grow faster, and patch scenarios are going to quickly be exploited.
Secondly, we might be seeing more of Artificial Intelligence (AI) Malware, which can think in different ways and is self-aware. Watch out for Advance persistent threats as we might see that go into more of an AI capability in the new year. We will also notice that issues with IoT will grow and continue to be a problem.
What should businesses do to prepare?
Start doing something. Don’t wait until the last minute to take action. Begin following NIST guidelines as a resource for technological advancement and security and implement those guidelines to mitigate control. If you do not understand them, then work with a security expert or partner with someone who does to ensure that you are compliant and have the proper tools in place. You do not need the latest technology, malware or sandbox to prepare for these threats. Instead, figure out where your gaps are in your security posture and learn how you can better monitor, manage, and fill in those gaps.

Matt Corney, Chief Technology Officer, Nuspire Networks
Matt Corney is chief technology officer at Nuspire Networks, bringing over 20 years of data security experience to the company. As CTO, Corney oversees the management of Nuspire’s SIEM solutions as well as the overall creation, maintenance, and updating of the company’s current and future product portfolio.
30. Misconfiguration of permissions on Cloud resources
The most impactful threat to companies will be the misconfiguration of permissions on Cloud resources. As both small companies and large swaths of the Fortune 500 move to the Cloud, security practitioners will need to relearn how to restrict access and permissions to data. This is a model closer to Active Directory. While it’s powerful, it has a steep learning curve until IT staff can confidently monitor and restrict access.
2020 has been dubbed the year of Kubernetes and Container orchestration in production. Expect attackers to start paying attention to Docker and Kubernetes for post exploitation fun. As was presented a few weeks ago at KubeCon by Brad Geesaman, you need to harden your instance of Kubernetes on most public clouds and also monitor it.
We expect attackers to start looking for privileged containers on Docker hub and to start to abuse the Kubernetes and Docker APIs. Expect this will be an issue after containers with Web Applications get exploited while the rest of the Kubernetes world upgrades to the newer and safer versions of Kubernetes.
Expect this year to be the year that someone backdoors favorite container images on a container registry.
The last prediction is not a shocker, but expect that a lot of IoT devices will continue to be the launching point for DDoS attacks and that 2020 will be the year that these attacks do more sustained attacks against infrastructure like GitHub and dyn.

Pete Markowsky, Co-founder and Principal Engineer, Capsule8
Pete Markowsky has been involved with information security and application development since first working with Northeastern University in 2001. He has worked across the security industry from .edu to .mil in roles such as development, security engineer, risk analyst and principal security researcher.
31. State-sponsored attacks and massive IoT device hacks
State-sponsored cyber attacks
The more steps we take towards computerizing our lives, the more room there is for cyber attacks from foreign governments, targeting everything from the economy to national defense. Recently reported Russian interference into the election process perfectly demonstrates how even democracy itself can be affected.
Massive hacks of IoT devices
Internet of things (IoT) is a rapidly growing cybersecurity trend. The number of IoT devices is set to outrank human population by 2020. And most of them are easily hackable! Taking into account how easy it is to hack most of these devices and how devastating IoT-powered DDoS attacks can be, we would see even more significant attacks and breaches in 2020.
Cryptojacking
With Bitcoin and other crypto-currencies becoming a substitute for traditional money and rapidly rising cryptocurrency prices, many malicious actors turned their attention to hacking popular websites to hijack people’s devices to mine cryptocurrency.
Businesses can prepare for revising their data security policies and investing more in cybersecurity protection. 2020 is the right time to start using AI-powered cybersecurity solutions. Although nothing can guarantee 100% protection, using such technologies can dramatically lower the chance of data breach no matter which industry you are in or how big your company is.

George Tatar, Founder and CEO, Akruto, Inc.
George founded Akruto, Inc. in 2010 to help customers keep their private information safe and readily available wherever they go.
32. The lack of urgency and concern around data breaches
The lack of urgency and concern around data breaches continues to increase, with significant incidents only dominating news cycles for a few days or a week at most. Consumers have become entirely numb to security issues and having your credit card information stolen is expected, rather than surprising.
Looking ahead to the cybersecurity trends of 2020, the public will either continue to tune out current cyber threats or something significant will happen to wake people up to the issue and have them take security seriously. In addition to the general public becoming more aware in the wake of a significant event, companies will begin to make consumer education a more substantial part of their business model.

Neill Feather, President, Sitelock
Neill Feather is the president of SiteLock, the leading provider of website security solutions for business. At SiteLock, Neill leads the company’s approach to 360-degree domain security by providing industry analysis and utilizing rapidly evolving data sets related to security and hacking trends.
Recent Posts
Network Security Threats, 11 Emerging Trends For 2020
This article was updated in December 2019.
Most experts agree that 2020 will bring a higher sophistication of malicious hacking.
More of these network security threats and attacks will be high profile and reinforce the importance of cybersecurity plan. Hackers will target well-known brands, looking for notoriety as well as money.
As a result, the security response of the business community must rise to the occasion.
Any network with a connection to the Internet is potentially vulnerable. The number one thing you can do to protect your systems is to establish a backup strategy for your data, now.
Types of network threats to be aware of in 2020
Ransomware (and Micro Ransomware)
As the so-called “as a Service” services increase, we can expect a proliferation of ransomware to showcase itself across networks.
Ransomware is an attack vector that focuses on vulnerabilities that are much different from any other form of malware. It is also one of the easier malicious attacks to employ, giving relative newbies the leverage to troll their way into crime.
The more severe users of malware will use ransomware to focus on easily penetrable industries such as healthcare. The proliferation of big data has made sensitive medical information much more valuable than it has ever been. Other industries that traffic in sensitive consumer data will also find themselves targeted by this unique form of malware.
Ransomware can also shutdown POS systems, blocking payments from ever reaching the recipient. Currently, email is the number one delivery method for ransomware and viruses. This will also change as technology becomes more sophisticated.
Although the trend will expand, not all attacks will be massive. Ransomware is one one the fastest growing cybersecurity threats to network security. Experts say that we can also expect ransomware attacks targeting smaller companies.
Long-Term Extortion
An offset of the growing ransomware plague is long-standing extortion techniques. Once a vulnerability has been opened through a ransomware attack, it can be quite challenging to close. This can leave a digital door open for a malicious user to require ongoing payments in order to keep from accessing the vulnerability again.
In this way, ransomware scams can last for much longer than the initial attack, creating an environment of fear for companies that do not have the appropriate technology to ensure closing digital backdoors.
Companies that are looking to expand will find themselves targeted by this kind of extortion. Even if a security network is relatively secure at its base, when it takes on new third-party applications, new security backdoors can be opened because of the interaction between legacy apps and new apps. Companies that rely on automated updates may also face ongoing extortion efforts from hackers who follow the schedule of these updates and plan attacks around the “changing of the guard.”
Malware in the Mobile Device Space
Smartphones are no longer safe. As commerce moves into the mobile space, hackers will move with it. 35% of the general public uses smartphones for banking, and these people will be targeted by hackers. There are many malware families dedicated specifically to mobile device platforms. They are becoming very good at stealing the financial information of online bankers.
Keyloggers, for instance, are no longer a sickness relegated only to desktop and laptop computers. Mobile keyloggers can steal passwords from other apps that are downloaded into a phone. If a user has the same password for that app and a financial app, the hacker now has access to the online banking credentials of that user. Take the time to create ideas for great secure strong passwords.
Hackers may also use creative techniques to get users to download malicious apps. These apps work in the same way as an email phishing campaign or a silent.exe download. Once they open a small hole in the security of the hardware, a hacker can come in and make it much bigger over time.

Exploits Directed at the Windows Subsystem for Linux
The Windows Subsystem for Linux (WSL) will likely be a huge target in 2020. WSL is a new technology that shipped out with Microsoft Windows 10. It was created to allow Windows tend to run alongside a limits environment. However, the many security exploits that have already been found within the Windows 10 environment do not speak well to this premature expansion.
There are many companies that have not upgraded to Windows 10.
As this upgrade is forced into many environments, you can expect that hackers will continue to focus their efforts on it. Microsoft has yet to respond adequately to many of the criticisms leveled its way about forcing implementation of its operating systems before adequately testing for exploits.

IoT Botnets
As people plug into the Internet of Things, hackers will make this new system one of the first locations for significant incidents.
The leaked Mirai code of 2016 that created a very effective legion of bots will expand and grow into IoT, says Bitdefender senior analyst Bogdan Botezatu. The DDoS or denial of service attacks that were created from these bots will seem rather tame in the face of the dual ransomware/botnet attacks that will show themselves in 2020.
Modern botnets even can directly defeat systems with machine learning capabilities. The sheer volume of these botnets makes it possible to attack with brute force some of the weaker infrastructures. GPU based encryption is another advancement that many cybersecurity systems have yet to catch up with.
Polymorphism and Powershell
The proliferation of open-source tools will bring with it an increased level of abuse.
Even network security tools that have a decent reputation in the freeware space may be targeted as Trojans. Commercial actors and APT groups are already beginning to include PowerShell manipulation in their malware toolkits. The more sophisticated these tools become, the more security products they will be able to bypass.
Many types of malware also can change their signatures. This is known as polymorphic malware. Qbot is just one example of incredibly sophisticated polymorphic engines that are currently taking up space in the cloud. The creators of these engines are actually renting them out to other malicious entities, with the two entities splitting the profits of whatever haul they bring in. In short, the creation of malicious software has been crowdsourced. There are simply not enough companies with the in-house staff to handle this kind of teamwork.
Artificial Intelligence Security Tools
It is difficult enough for a company to keep up with and respond to the last major publicized cybersecurity breach. In 2020, hackers will employ AI tools that will consistently scan the environment for new exploits.
Hackers will be able to upgrade and modify their techniques in real time. Most organizations only have access to scanning tools that were based on policy compliance and configuration. These tools are looking to the past, not to the future. They just cannot keep up with AI-based tools that are creating and testing scenarios for the sole purpose of breaking into a system.
There is no in-house DevOps security best practices or team that can keep up with the amount of analysis and data that is necessary to ward off real-time attacks that can consistently change form. It is the equivalent of chasing a fly around a huge room. Companies will need to employee third-party experts that can accurately conduct impact and context analysis.

Cybersecurity Third Party Breach Threat
Breaches do not have to come from a direct attack. In 2018, more breaches were made possible through a third-party source. These nerd parties may have been trusted. However, that third-party does not always have an awareness that it is being used as an open hallway to a target that it is connected to.
Hackers can sanitize their trail so that it cannot be quickly followed. The company that is attacked may believe that it was the direct target of the attacker with no roundabout pathway made to its doorstep through the naïve third-party.
The past few years have seen many security breaches accomplished through third parties. Hackers were able to access the network of major retailer Target through one of its HVAC vendors. A point-of-sale vendor was the gateway for hackers to break into the networks of Home Depot, Inc. and Hilton Hotels. These were not the only companies that suffered a data breach through some aspect of their supply chains.
Companies may also become vulnerable through a third-party connection without a firewall. It is imperative that companies that are doing business with each other in the digital space expand and share their security features with each other. For instance, the app structure of a third-party company may also affect the ability of a targeted company to adequately secure its own borders.
Network Security Risk Management
Companies that haphazardly expand their digital ecosystems will be the most highly targeted. Hackers are continually monitoring these ecosystems, standing just outside the doorway waiting for an expansion that they can exploit.
Governments are attempting to rein in the ability of individual companies to expand their digital real estate too fast. However, there are limitations on what regulations can protect.
The issue of regulatory compliance will come into the spotlight during the implementation of the General Data Protection Regulation (GDPR) across the digital landscape. Experts believe this will cause an outbreak of attacks as companies to adjust their security measures to remain in compliance with GDPR.
It is essential to remember that hackers do not care if you comply with the latest government regulation. They only care about getting your private data.

Business Email Network Security Risks
Email vulnerabilities are the grandfather of all types of threats in network security.
It continues to be a massive problem across industries because it still works with a very high frequency. It is also a relatively easy way to breach a companies systems. Hackers do not need a great deal of technical expertise. All that is necessary is control of a resource that executes when a phish is triggered by an errant employee. Often, the security risks of wireless networks are not taken seriously.
A lack of training on the best practices of email security is the number one culprit in email hacks. Large companies can still be targeted because of the higher probability of an untrained employee opening a phishing email. Many experts believe that the financial industry, ransacked by ransomware and other malware in 2020, will remain a top target of this form of breach.
Criminals looking to break into companies through emails may also use relevant information from employees. Hackers may attend an industry event, gain the contact information of a high-ranking employee, and use that information to break in relatively undetected. It is essential to protect your company from a physical standpoint as well as in the digital space.
Cloud Network Security and Vulnerabilities
The public cloud continues to be a massive target for cybercriminals. Again, large companies continue to rest in the center of the bulls-eye. Companies without a strong tiered program of access are at the most significant risk. All it takes is one untrained employee with access to open up any number of cloud security vulnerabilities across the network.
Hackers can access this information in a number of ways. It is up to the organization to quarantine employee access so that physical hacks will only allow access to a controllable, easily trackable dataset.

The Hijacking of Search Results
Many companies are unaware that the major search engines have personalized search results quite effectively. Depending on the previous searches of a company and its behavior during those searches, it can receive different results from any other entity in the world.
In short, there is no such thing as generalized search results anymore. Hackers are acutely aware of the targeting that search engines employ. If they can hack into the behavioral patterns of an organization, they can also hack into that companies search engine results.
Search tampering involves hijacking one or more of the results on a search engine page. Under the guise of following relevant links, a company can be directed to a malicious site. From here, hackers have a number of options. Once a company has access to this site, a hacker can tap into anything from digital files to security cameras.

Always Be Prepared for the latest network security threats
Knowing about security threats is one thing. Responding to them is another. The tips above should drive you into action.
Take the appropriate steps to protect your data streams. This year will not have mercy on any company without the proper security!
Preparation is the only defense. Start with a network risk management, incident response planning, and evaluating current security protocols.
In most cases, the security industry is functioning in response to attacks from malicious hackers. You must remain proactive and up-to-date on the latest types of network threats. You must also employ the newest protection strategies using AI, machine learning and systems analysis.
Recent Posts
HITRUST Certification vs HIPAA: What are the Differences?
There is more to worry about than just HIPAA Compliance in order to secure media data. That’s where HITRUST comes in.
What is HITRUST Compliance?
How is it different from HIPAA?
How can healthcare organizations leverage this framework?
What is HITRUST?
HITRUST or the Health Information Trust Alliance, in and of itself is not just a framework that allows healthcare providers to meet HIPAA security laws. HITRUST goes far beyond that. They are the entity that created and continues to maintain the CSF, or Common Security Framework. The CSF is a certifiable framework that brings together other compliance frameworks, such as HIPAA, NIST, PSI, and ISO.
Many entities in the healthcare industry think of health information security rules as a burden to deal with before they can do their jobs. HITRUST was made to be the core pillar of the union of different health information systems and exchanges. Today’s technology makes risk management and data protection key for healthcare organizations of all kinds, and HITRUST helps covered entities meet information security regulations easier than ever before.
The HITRUST website describes “a not-for-profit organization whose mission is to champion programs that safeguard sensitive information and manage information risk for organizations across all industries and throughout the third-party supply chain. In collaboration with privacy, information security and risk management leaders from both the public and private sectors, HITRUST develops, maintains and provides broad access to its widely adopted common risk and compliance management and de-identification frameworks; related assessment and assurance methodologies; and initiatives advancing cyber sharing, analysis, and resilience.”

What is HITRUST Compliance Certification?
Part of what makes HITRUST different is the fact that it is certifiable. A health care facility can’t be certified in HIPAA compliance or in how well they follow Federal Trade Commission laws. In the past, healthcare practices just signed agreements that they were, in fact, HIPAA compliant. They signed forms that said they had taken the right measures to put security controls in place.
This could never be confirmed or judged by anyone, making it more of an “I promise” sort of situation. Some medical practices took the first step to conduct a HITRUST readiness assessment or hire a HITRUST CSF assessor. This was to make sure that the practice was properly following the HIPAA security rule and other laws set forth. This was the most any practice could do to “prove” they were HIPAA compliant.
A medical practice can become HITRUST certified.
How to become HITRUST Certified?
As said above, HITRUST compliance requirements include HIPAA, FTC, and many other data security regulations.
HITRUST has the option to allow healthcare practices to do their own self-assessment.
It is highly recommended that medical practices first perform a self-audit.
The HITRUST self assessment tool is also an excellent resource for practices to use on a frequent basis.
Any gaps in regulatory compliance can be addressed and lessened before the final CSF assessment is done. They can make any needed changes before the assessor comes to do the validated assessment.
Or, they can have a CSF assessor perform a validated assessment.
The CSF framework and HITRUST assessment and certification have 19 different domains:
- Healthcare Data Protection & Privacy
- Information Protection
- Wireless Protection
- Transmission Protection
- Network Protection
- Endpoint Protection
- Portable Media Security
- Mobile Device Security
- Third Party Security
- Physical & Environmental Security
- Configuration Management
- Vulnerability Management
- Password Management
- Incident Management
- Risk Management
- Access Control
- Audit Logging & Monitoring
- Education, Training & Awareness
- Business Continuity Management & Disaster Recovery
Many HITUST CSF certification requirements must be met to become certified. These are clearly outlined and can be easily understood and put into practice. HITRUST certifications are good for two years. Then, a healthcare practice will need to go through the assessment, validation, and certification process again.
This may seem like a burden. But with technology and security regulations changing so quickly, certifications require updates
Once a new technology is introduced, or new compliance laws are passed, the certification becomes out of date. When healthcare practices work with HITRUST, they can be sure that every two years the most up-to-date security technology is employed.

HITRUST vs HIPAA Requirements for Certification, The Differences
HIPAA is a law that protects patient medical records. It gives patients some privacy when it comes to who can gain access to the information stored in their file.
Whether or not a health care provider is HIPAA compliant or not is subjective without a certification process. Without being certified, any healthcare practice can say they are HIPAA compliant without following some or all of the laws that HIPAA has set forth.
With growing technology in the healthcare sectors, security compliance can seem strict and at times, unnecessary. Maintaining compliance and IT risk management has been a struggle for many healthcare practices. Costs have increased across the board as practices have had to hire and train more staff to meet the burden of staying compliant with the latest laws in healthcare privacy.
Medical practices in every field have shown a need to simplify how they meet healthcare privacy requirements. Compare HIPAA to HITRUST and learn the differences between the two. Learn how healthcare organizations can use HITRUST to make risk assessment and health care security compliance easy to maintain.
HITRUST
HITRUST is the entity that created and maintains control frameworks that include many different compliance regulations. HITRUST brings together and unifies the various aspects of regulatory compliance. This makes it easy for medical practices to adopt compliant practices and make sure they are using the right security controls to protect sensitive information and patient data.
HIPAA
HIPAA, or the Health Insurance Portability and Accountability Act, are a set of standards and regulations that are meant to protect sensitive information in the healthcare industry. HIPAA compliance involves protecting health information and making sure that only those medical professionals, vendors, and other need-to-know people have access to patient health information.

HITRUST and HIPAA are not interchangeable
HITRUST includes but is not limited to HIPAA. HIPAA is a vital part of data protection and is the baseline for patient information security. However, it does not offer anything beyond guidelines to follow. It doesn’t allow medical practices to engage with complete protection that takes into account the increased threats. These healthcare cybersecurity threats change as technology grows, making it harder to keep up without help.
HITRUST is the organization that formed and updates a comprehensive security platform, or Common Security Framework (CSF). It includes much more than HIPAA regulations. For example, HIPAA includes physical, technical, and administrative safeguards. They outline the policies, procedures, and requirements for organization and documentation that healthcare practices must adhere to.
HITRUST, on the other hand, includes all of the HIPAA safeguards, as well as security guidelines and risk management framework from:
- Control Objectives for Information and Related Technology (COBIT)
- International Organization for Standardization (ISO)
- Federal Trade Commission (FTC)
- Centers for Medicare and Medicaid Services
- National Institute of Standards and Technology (NIST)
- Payment Card Industry Data Security Standard (PCI DSS)
- Other federal and state entities
HITRUST is the framework that allows medical practices to make sure they have all their bases covered. The framework is meant to balance the standards from the different regulatory entities to help healthcare practices simplify.
With HITRUST certification, healthcare facilities can expand their data and patient security coverage.
Planning for Healthcare Security Threats
Data breaches in the healthcare industry can be costly and negatively impact a healthcare practice in many ways.
Sadly, these data breaches are on the rise and are showing no signs of stopping or slowing down. It’s more important than ever to be aware of the risks of technology in a healthcare practice and to adopt controls that minimize those risks. While HIPAA compliance was the first widely adopted set of compliance laws to help keep patient data private and to stop data breaches, it is simply just one piece of an enormous puzzle.
Contrary to popular belief, many entities want to get their hands on private patient data. It may not be relevant to some of them that Joe Smith had a kidney transplant last year. Or, that he was allergic to a particular type of medicine. Remember though that patient data includes much more than just health history.
It includes patient names, addresses, social security numbers, health insurance information, and more. This data can be used to commit different kinds of fraud. With the lack of healthcare available to low income and middle-class people, health insurance fraud is on the rise. Identity theft is also an issue when it comes to patient records. This is because nearly all of an individual’s identifying information is contained within their medical chart.
People who want to get their hands on private patient data don’t have to physically break into a medical office and steal file folders. Technology makes it easy for advanced hackers to get to this information remotely if the right security controls are not in place. Unsecured or unencrypted email can be infiltrated, or hackers can download a wealth of patient data through unprotected cloud services.
Without good cybersecurity framework, a health care facility’s sensitive data is a playground for smart hackers. It’s critical for healthcare practices of all kinds to plan for threats to security. They need to work to adopt controls that keep sensitive information out of any hands it does not belong in.
Next Steps: Protecting Patient Data & Achieving HITRUST Certification
Carefully consider the benefits of becoming HITRUST CSF certified. HITRUST certified medical practices can enjoy the peace of mind that comes with having efficient data security processes and reducing the threat of data breaches.
This certification isn’t one of the business requirements for opening or operating a health care facility of any kind. However, it’s the simplest and most complete way to ensure that your facility is on par with the latest security and regulatory compliance laws.
Get rid of confusion over compliance. Have peace of mind that your practice is protected by a universal cybersecurity framework that accounts for all current industry regulations. Becoming HITRUST certified can also help build the trust between your practice and your patients. Your patients will know their private data and health information is safe.
Recent Posts
HIPAA Compliance Checklist: How Do I Become Compliant?
For healthcare providers, HIPAA compliance is a must. HIPAA guidelines protect patients’ health information, ensuring that it is stored securely, and used correctly.
Sensitive data that can reveal a patient’s identity must be kept confidential to adhere to HIPAA rules. These rules work on multiple levels and require a specific organizational method to implement comprehensive privacy and security policies to achieve compliance.
Most organizations find this to be a daunting task. We have put together a HIPAA compliance checklist to make the process easier.
The first is to understand how HIPAA applies to your organization. The second is to learn how to implement an active process, technology, and training to prevent a HIPAA-related data breach or accidental disclosure. Finally, the third is to put physical and technical safeguards in place to protect patient data.
By the time you’re done with our list, you will know what you need to consider to have a better conversation with your compliance advisors.
What is HIPAA?
Before talking about compliance, let’s recap the basics of HIPAA.
Signed into law by President Bill Clinton in 1996, the Health Insurance Portability and Accountability Act provides rules and regulations for medical data protection.
HIPAA does several important things. It reduces health care abuse and fraud and sets security standards for electronic billing of healthcare. It also does the same for the storage of patients’ healthcare information. The Act mandates the protection and handling of medical data, ensuring that healthcare data is kept private.
The part of HIPAA we are concerned with relates to healthcare cybersecurity. To be compliant, you must protect patients’ confidential records.
HIPAA rules have evolved. When the law was first enacted, it did not mention specific technology. As the HIPAA compliant cloud has become commonplace, it has inspired additional solutions. For example, our Data Security Cloud (DSC) is being developed to create a base infrastructure for a HIPAA compliant solution. Providing a secure infrastructure platform to ride on top of, DSC makes creating a HIPAA-compliant environment easier.
Secure infrastructure handles things at the lowest technical level that creates data, providing the key features to keep data safe. These features include separation/segmentation, encryption at rest, a secure facility at the SOC 2 level of compliance, and strict admin controls among other required security capabilities.

Why Is HIPAA Compliance Important?
HIPAA compliance guidelines are incredibly essential. Failure to comply can put patients’ health information at risk. Breaches can have a disastrous impact on a company’s reputation, and you could be subject to disciplinary action and strict violation fines and penalties by CMS/OCR.
Last year’s Wannacry ransomware attack affected more than 200,000 computers worldwide, including many healthcare organizations. Most notably, it affected Britain’s National Health Service, causing severe disruptions in the delivery of health services across the country.
To gain access to the systems, hackers exploited vulnerabilities in outdated versions of Windows that are still commonly used in many healthcare organizations. With medical software providers offering inadequate support for new OS’s and with medical devices such as MRIs lacking security controls, the attack was easy to carry out.
The attack demonstrated the strength of today’s hackers, highlighting the extent to which outdated technologies can pose a problem in modern organizations. This is precisely why HIPAA also regulates some aspects of technology systems used to store, manage, and transfer healthcare information.
The institutions that fail to implement adequate systems can suffer significant damage. If a breach takes place, the law requires affected organizations to submit various disclosure documents, which can include sending every subject a mailed letter. They may also be required to offer patients a year of identity protection services. This can add up to significant dollars, even before confirming the extent of the breach.

What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule creates national standards. Their goal is to protect medical records and other personally identifiable health information (PHI).
It applies to three types of companies: providers, supply chain (contractors, vendors, etc.) and now service providers (such as data centers and cloud services providers). All health plans and healthcare clearinghouses must be HIPAA compliant.
The rules also apply to healthcare providers who conduct electronic health-related transactions.
The Privacy Rule requires that providers put safeguards in place to protect their patients’ privacy. The safeguards must shield their PHI. The HIPAA Privacy Rule also sets limits on the disclosure of ePHI.
It’s because of the Privacy Rule that patients have legal rights over their health information.
These include three fundamental rights.
-
- First, the right to authorize disclosure of their health information and records.
- Second, the right to request and examine a copy of their health records at any time.
- Third, patients have the right to request corrections to their records as needed.
The HIPAA Privacy Act requires providers to protect patients’ information. It also provides patients with rights regarding their health information.

What Is The HIPAA Security Rule
The HIPAA Security Rule is a subset of the HIPAA Privacy Rule. It applies to electronic protected health information (ePHI), which should be protected if it is created, maintained, received, or used by a covered entity.
The safeguards of the HIPAA Security Rule are broken down into three main sections. These include technical, physical, and administrative safeguards.
Entities affected by HIPAA must adhere to all safeguards to be compliant.
Technical Safeguards
The technical safeguards included in the HIPAA Security Rule break down into four categories.
-
- First is access control. These controls are designed to limit access to ePHI. Only authorized persons may access confidential information.
- Second is audit control. Covered entities must use hardware, software, and procedures to record ePHI. Audit controls also ensure that they are monitoring access and activity in all systems that use ePHI.
- Third are integrity controls. Entities must have procedures in place to make sure that ePHI is not destroyed or altered improperly. These must include electronic measures to confirm compliance.
- Finally, there must be transmission security. Covered entities must protect ePHI whenever they transmit or receive it over an electronic network.
The technical safeguards require HIPAA-compliant entities to put policies and procedures in place to make sure that ePHI is secure. They apply whether the ePHI is being stored, used, or transmitted.
Physical Safeguards
Covered entities must also implement physical safeguards to protect ePHI. The physical safeguards cover the facilities where data is stored, and the devices used to access them.
Facility access must be limited to authorized personnel. Many companies already have security measures in place. If you don’t, you’ll be required to add them. Anybody who is not considered an authorized will be prohibited from entry.
Workstation and device security are also essential. Only authorized personnel should have access to and use of electronic media and workstations.
Security of electronic media must also include policies for the disposal of these items. The removal, transfer, destruction, or re-use of such devices must be processed in a way that protects ePHI.
Administrative Safeguards
The third type of required safeguard is administrative. These include five different specifics.
-
- First, there must be a security management process. The covered entity must identify all potential security risks to ePHI. It must analyze them. Then, it must implement security measures to reduce the risks to an appropriate level.
- Second, there must be security personnel in place. Covered entities must have a designated security official. The official’s job is to develop and implement HIPAA-related security policies and procedures.
- Third, covered entities must have an information access management system. The Privacy Rule limits the uses and disclosures of ePHI. Covered entities must put procedures in place that restrict access to ePHI to when it is appropriate based on the user’s role.
- Fourth, covered entities must provide workforce training and management. They must authorize and supervise any employees who work with ePHI. These employees must get training in the entity’s security policies. Likewise, the entity must sanction employees who violate these policies.
- Fifth, there must be an evaluation system in place. Covered entities must periodically assess their security policies and procedures.

Who Must Be HIPAA complaint?
There are four classes of business that must adhere to HIPAA rules. If your company fits one of them, you must take steps to comply.
The first class is health plans. These include HMOs, employer health plans, and health maintenance companies. This class contains schools who handle PHI for students and teachers. It also covers both Medicare and Medicaid.
The second class is healthcare clearinghouses. These include healthcare billing services and community, health management information systems. Also included are any entities that collect information from healthcare entities and process it into an industry-standard format.
The third class is healthcare providers. That means any individual or organization that treats patients. Examples include doctors, surgeons, dentists, podiatrists, and optometrists. It also includes lab technicians, hospitals, group practices, pharmacies, and clinics.
The final class is for business associates of the other three levels. It covers any company that handles ePHI such as contractors, and infrastructure services providers. Most companies’ HR departments also fall into this category because they handle ePHI of their employees. Additional examples include data processing firms and data transmission providers. This class also includes companies that store or shred documents. Medical equipment companies, transcription services, accountants, and auditors must also comply.
If your entity fits one of these descriptions, then you must take steps to comply with HIPAA rules.
What is the HIPAA Breach Notification Rule?
Even when security measures are in place, it’s possible that a breach may occur. If it does, the HIPAA Breach Notification Rule specifies how covered entities should deal with it.
The first thing you need to know is how to define a breach. A breach is a use or disclosure of PHI forbidden by the Privacy Rule.
The covered entity must assess the risk using these criteria:
-
- The nature of the PHI involved, including identifying information and the likelihood of re-identification;
- The identity of the unauthorized person who received or used the PHI;
- Whether the PHI was viewed or acquired; and
- The extent to which the risk to the PHI has been mitigated.
Sometimes, PHI may be acquired or disclosed without a breach.
The HIPAA rules specify three examples.
-
- The first is when PHI is unintentionally acquired by an employee or person who acted in good faith and within the scope of their authority.
- The second is inadvertent disclosure of PHI by one authorized person to another. The information must not be further disclosed or used in a way not covered by the Privacy Rule.
- The third occurs if the covered entity determines that the unauthorized person who received the disclosure would not be able to retain the PHI.
If there is a breach as defined above, the entity must disclose it. The disclosures advise individuals and HHS that the breach has occurred.
Personal disclosures must be mailed or emailed to those affected by the breach. A media disclosure must be made in some circumstances. If more than 500 people in one area are affected, the media must be notified.
Finally, there must also be a disclosure to the HHS Secretary.
The HIPAA Breach Notification Rule protects PHI by holding covered entities accountable. It also ensures that patients are notified if their personal health information has been compromised.

What Are The HIPAA Requirements for Compliance
The common question is, how to become HIPAA compliant?
The key to HIPAA compliance certification is to take a systematic approach. If your entity is covered by HIPAA rules, you must be compliant. You must also perform regular audits and updates as needed.
With that in mind, we’ve compiled a comprehensive checklist for use in creating your HIPAA compliance policy.
HIPAA Compliance Checklist
These questions cover the components to make you are HIPAA-compliant. You can use the checklist to mark each task as you accomplish it. The list is intended to be used for self-evaluation.
Have you conducted the necessary audits and assessments according to National Institutes of Standards and Technology (NIST) Guidelines?
The audits in question involve security risk assessments, privacy assessments, and administrative assessments.
Have you identified all the deficiencies and issues discovered during the three audits?
There are several things to consider before doing the self-audit checklist. You need to ensure that all security, privacy, and administrative deficiencies and issues are appropriately addressed.
Have you created thorough remediation plans to address the deficiencies you have identified?
After covering the deficiencies and issues mentioned above, you need to provide remediation for each group.
Do you have policies and procedures in place that are relevant to the HIPAA Privacy Rule, the HIPAA Security Rule, and the HIPAA Breach Notification Rule?
You must be aware of these three critical aspects of a HIPAA compliance program and ensure each is adequately addressed.
-
- Have you distributed the policies and procedures specified to all staff members?
- Have all staff members read and attested to the HIPAA policies and procedures you have put in place?
- Have you documented their attestation, so you can prove that you have distributed the rules?
- Do you have documentation for annual reviews of your HIPAA policies and procedures?
- Have all your staff members gone through basic HIPAA compliance training?
- Have all staff members completed HIPAA training for employees?
- Do you have documentation of their training?
- Have you designated a staff member as the HIPAA Compliance, Privacy, or Security Officer as required by law?
- Have you identified all business associates as defined under HIPAA rules?
- Have you identified all associates who may receive, transmit, maintain, process, or have access to ePHI?
- Do you have a Business Associate Agreement (Business Associate Contract) in place with each identify you have identified as a Business Associate?
- Have you audited your Business Associates to make sure they are compliant with HIPAA rules?
- Do you have written reports to prove your due diligence regarding your Business Associates?
- Do you have a management system in place to handle security incidents or breaches?
- Do you have systems in place to allow you to track and manage investigations of any incidents that impact the security of PHI?
- Can you demonstrate that you have investigated each incident?
- Can you provide reporting of all breaches and incidents, whether they are minor or meaningful?
- Is there a system in place so staff members may anonymously report an incident if the need arises?
- Have you distributed the policies and procedures specified to all staff members?
As you work your way through this checklist, remember to be thorough. You must be able to provide proper documentation of your audits, procedures, policies, training, and breaches.
As a final addition to our checklist, here is a review of the general instructions regarding a HIPAA compliance audit.
-
- If a document refers to an entity, it means both the covered entity and all business associates unless otherwise specified
- Management refers to the appropriate officials designated by the covered entity to implement policies, procedures, and standards under HIPAA rules.
- The covered entity must provide all specified documents to the auditor. A compendium of all entity policies is not acceptable. It is not the auditor’s job to search for the requested information.
- Any documents provided must be the versions in use as of the audit notification and document request unless otherwise specified.
- Covered entities or business associates must submit all documents via OCR’s secure online web portal in PDF, MS Word, or MS Excel.
- If the appropriate documentation of implementation is not available, the covered entity must provide examples from “equivalent previous time periods” to complete the sample. If no such documentation is available, a written statement must be provided.
- Workforce members include:
- Entity employees
- On-site contractors
- Students
- Volunteers
- Information systems include:
- Hardware
- Software
- Information
- Data
- Applications
- Communications
- People
Proper adherence to audit rules is necessary. A lack of compliance will impact your ability to do business.
In Closing, HIPAA Questions and Answers
HIPAA rules are designed to ensure that any entity that collects, maintains, or uses confidential patient information handles it appropriately. It may be time-consuming to work your way through this free HIPAA self-audit checklist. However, it is essential that you cover every single aspect of it. Your compliance is mandated by law and is also the right thing to do to ensure that patients can trust you with their personal health information.
One thing to understand is that it is an incredible challenge to try to do this by yourself. You need professional help such as a HIPAA technology consultant. Gone are the days you can have a server in your closet at the office, along with your office supplies. The cleaning personnel seeing a print out of a patient’s file constitutes a ‘disclosable’ event.
Screen servers, privacy screens, and professionally-managed technology solutions are a must. Just because you use a SAS-based MR (Medical Records) solution, does not mean you are no longer responsible for the privacy of that data. If they have lax security, it is still the providers’ responsibility to protect that data. Therefore the burden of due diligence is still on the provider.
Phoenix NAP’s HIPAA compliant hosting solutions have safeguards in place, as audited in its SOC2 certifications. We provide 100% uptime guarantees and compliance-ready platform that you can use to build secure healthcare infrastructure.
Recent Posts
9 Strong Password Ideas For Greater Protection
For your online accounts, passwords are the weakest point in any level in security. If someone accesses your credentials, your content and your vital information are at risk.
Although most websites today offer extra security protection, anyone who retrieves or guesses your password can easily bypass other security measures that most sites have in place.
That person can make any changes to your online accounts, make purchases, or otherwise manipulate your data. Always have your data backed up just in case.
Selecting a secure password is crucial because let’s face it, our entire life is now spent in the digital universe: social media, banking, email, shopping, and more.
Many people have the terrible habit of using the same passwords across multiple accounts. It may be easier to remember, but if there is a security vulnerability on one account, everything could be compromised.

Passwords are Your Digital Keys
Your sign-on details are the digital keys to all your personal information and the best way to keep your company information safe. You want to make sure to keep your passwords safe from third-parties so that they can stay private.
While many small-time cybercriminals attempt to hack into email accounts and social networks, they often have darker and more malicious goals. They’re usually after information from personal finances such as credit card details and bank account info, or business accounts to either directly line their pockets or attempt to extort an individual or business.
The two significant security risks are insecure password practices and shared accounts. This involves using the same password for personal and business apps, reusing passwords across multiple apps, sharing passwords with other employees, and storing passwords insecurely.
The point here is that a robust and secure password is all that could potentially stand between you and pesky cybercriminals.
How Can Your Password Be Compromised?
Outside of spyware and phishing attacks, there are numerous techniques that hackers use to crack your passwords.
One strategy is to gain access is by straight-up guessing your password. They could do this by looking at your security questions, your social media presence, or any other found information that could be online. That is why it is vital that not to include any personal information in your passwords.
Other tactics that hackers utilize is to try a password cracker. By using brute force, a password cracker employs various combinations continuously until it breaks the password and gains access to the account. We’ve all seen this in the movies, but it’s worth noting that this is not just a Hollywood special effect.
The less complex and shorter your password is, the faster it can be for the tool to produce the correct combination of characters. The more complex and more extended your passwords are, it is less likely the hacker will use a brute force technique. That is due to the extended amount of time it would take for the software to figure it out.
Instead, they will put in place a method called a “dictionary attack.” Here is where a program will cycle through common words people use in passwords.
Strong Password Ideas and Tips with Great Examples
- Make sure you use at minimum ten characters. That is where it can get tricky. As previously noted, you should avoid using personal information or your pet’s information — those are the first choices for hackers to try and exploit. In determining your password strength, pay close attention to two significant details: the complexity and length you choose. Long-tail, complex passwords are tough to crack. To create complex but memorable passwords, use different types of characters, a mixture of lower and uppercase letters, symbols, and number
- Do not use directly identifiable information. The ones trying to hack into your accounts may already know personal details such as your phone number, birthday, address, etc. They will use that information as an aid to more easily guess your password.
- Use a unique password for each separate account. If you use the same password across multiple accounts, you could use the most reliable password possible, and if one account is compromised: all of them are. The recommended best practice is to create a strong password ideas list and use it for all your online accounts. Your unique list of passwords should be kept safe.
- Avoid common dictionary words. This mistake is the toughest one to avoid. The temptation is always there to use ordinary, everyday dictionary words. It is true that the most common password used today is, “password.” Avoid plain dictionary words as well as a combination of words. For instance, “Home” is a bad password. However, adding “Blue Home” isn’t an improvement either. A strong hacker will have a dictionary-based system that cracks this type of password. If you must use a single word, misspell it as best as you can or insert numbers for letters. Use a word or phrase and mix it with shortcuts, nicknames, and acronyms. Using shortcuts, abbreviations, upper and lower case letters provide easy to remember but secure passwords.
For example:
-
- “Pass Go and collect $200”– p@$$GOandCLCt$200
- “Humpty Dumpty sat on a wall” — humTdumt$@t0nAwa11
- “It is raining cats and dogs!”– 1tsrAIn1NGcts&DGS!
Incorporate emoticons, emoticons are the text format of emojis, commonly seen as various “faces.”
You may also find remembering a sentence for your password if it refers to something easy for you, but complex for others, such as; “The first house I ever lived in was 601 Lake Street. Rent was $300 per month.” You could use “TfhIeliw601lS.Rw$3pm.” You took the first letters of each word, and you created a powerful password with 21 digits.
If you want to reuse passwords across numerous accounts, this technique is particularly useful as it makes them easy to remember. Even though, as already mentioned, you really should use separate passwords, you can customize each per account. Utilizing the same phrase as above, “Humpty Dumpty sat on a wall” we created a secure and reliable password, and now you can use it on Amazon, Netflix, or Google accounts:
Here are good password examples using this technique.
-
- AMZn+humTdumt$@t0nAwa11
- humTdumt$@t0nAwa11@gOoGL
- humTdumt$@t0nAwa114netFLX
Weak Passwords to Avoid
Everyone is guilty of creating easy to guess passwords at some point in their digital life. You might feel confident that when you chose “3248575” that no one would figure out is your phone number. The examples below add to what are weak passwords that at first appear strong. However, once you look a little closer, you realize what is missing.
A brief explanation of what makes these bad choices follows each:
-
- 5404464785: Using numbers such as these quickly reveal someone’s phone number. By using this strategy, you are breaking two basic rules, using personal information and all numbers.
- Marchl101977: The birthday password. Even though this password contains a combination of numbers with small and capital letters and is over ten characters long, it is a disaster waiting to happen. It too breaks the rules by starting with a standard dictionary word, use of personal information and it lacks special characters.
- P@ssword234: You may at first feel this password meets the basics. However, it indirectly fails our tests. While it does have over ten characters, contains special characters and numbers, a mix of the letters, and it does not include any personally identifiable information, it is still considered weak. Because of how easy they are to guess, replacing letters for symbols is not a strong recommendation. It also offers the standard “234” sequential pattern.

What is Two-Factor Authentication?
“Multi-factor authentication” in the digital world is simply an extra layer of security. As common as it may seem in the technology industry, if you ask around, you will find that not everyone knows about “Two Factor Authentication”. What’s even more interesting is that many people who don’t understand the term may very well be using it every day.
As mentioned throughout this blog, standard cybersecurity solutions and procedures only require a necessary username and password. With such simplicity, criminals score by the millions.
Two Factor Authentication, also known as 2FA, is two-step verification process, or TFA. It requires more than just a username and password but also something that only that user has on them.
That could be a document or piece of information only they should know or immediately have on hand, like a token of some type. Using this technique makes it difficult for cybercriminals to gain access and steal the identity or personal information of that person.
Many people do not understand this type of security, and they may not recognize it though they use it on a daily basis. When you use hardware tokens, issued by your bank to put to use with your card and PIN when needing to complete internet banking transactions, you’re using 2FA.
They are merely utilizing the benefits of multi-factor authentication by using something they have or what they know. Putting this process to use can indeed help with lowering the number of cases of identity theft on the web, as well as Phishing through email. The reason is that it needs more than supplying the mere name and password details. See our article on preventing ransomware for more information.
There are downsides, however. New hardware tokens which come from the bank in the form of card readers or key fobs that require ordering may slow business down. There can be issues for customers waiting and wanting to gain access to their private data through this authentication procedure.
The tokens get easily lost because they are small, so that too causes problems for everyone when a customer calls in requesting new ones. Tokenless Authentication is the same procedure except there no tokens involved. It is quicker, faster, and less expensive to establish and maintain across numerous networks.

Managing Passwords the Easy Way
Implementing enterprise password management helps small, and large businesses keep their information sound. No matter how many employees you have, they need help protecting the passwords that operate your business and your private life.
A password manager helps you generate strong passwords as well as remembering each one for you. However, if you do choose this route, you will need to at least create a secure password and remember it.
With the masses of websites for which you have accounts, there is no logical way to remember each one easily. Trying to remember every single password, (and where you wrote them down) and not duplicate one or resorting to using an easy-to-read pattern, is where the trouble starts.
Here is where password managers make life more comfortable – as long as you can create a strong master password that is necessary for you to remember. The good news is, that is the last one you will you need to worry about no matter how many accounts you have.
The Truth about Browser-Based Managers
Web browsers – Safari, Firefox, Chrome, and others – each have integrated password managers.
No browser can compete with a dedicated solution. For one, Internet Explorer and Chrome store your passwords in an unencrypted form on your computer.
People can easily access password files and view them unless you encrypt your hard drive. Mozilla Firefox has the feature, “master password” that with one single, “master password” you can encrypt your saved passwords. It then stores them in an encrypted format on your computer.
However, Firefox password manager is not the perfect solution, either. The interface does not help you generate random passwords, and it also lacks various features such as cross-platform syncing.
There are three standout-above-the rest dedicated platforms for password management. Each of these is a reliable option, and the one you choose will rely on what is most important to you.
The important part is remembering that you need to use genuinely random words for a secure password. A great example is “cat in the hat” would make a horrible word because it is a common phrase and makes sense. “My beautiful red car” is another type that is horrible.
However, something such as “correct kid donor housewife” or “Whitehorse staring sugar invisible” are examples of a randomized password. They make no sense together and are in no grammatically correct order, which is fantastic. Managers also allow users to store other data types in a secure form–everything from secure notes to credit card numbers.
In Closing, Stay Secure and Protected
We are experiencing times when passwords that you can remember is not enough to keep yourself and your company safe. If you do suspect criminal mischief with your account, immediately change your passwords.
Doing so only takes a minute, as restoring your personal life and your company financial records and history can often be devastating. Follow the steps listed above for selecting a strong unique password to establish and maintain safe accounts, secure email, and personal information. If your password is easy to remember, it is probably not secure.
Recent Posts
7 Tactics To Prevent DDoS Attacks & Keep Your Website Safe
A massive DDoS attack hits your server. Your basic security systems fail to respond in time.
Suddenly, your business grinds to a halt, and your website is down for hours. You are losing untold amounts of revenue.
You don’t have to look any further than last year’s Dyn incident to see how your business could be reduced to an entity trying to rebuild its reputation and pipeline.
In a single weekend, the worst distributed denial of service attack in history crashed the world’s largest internet services. Twitter, Reddit, The New York Times, and PayPal were just some of the significant sites that went down due to attack.
The reported damage from this malicious attack for Dyn was a loss of 8% of its business. The harshness of the message sent for digital enterprises was immeasurable.
Denial of service attacks are here to stay, and no business can afford to be unprotected.
What are DDoS Attacks? A Definition
DDoS stands for Distributed Denial of Service.
It is a form of cyber attack that targets critical systems to disrupt network service or connectivity that causes a denial of service for users of the targeted resource. A DDoS attack employs the processing power of multiple malware-infected computers to target a single system.
The botmaster, as the lead attacking computer, is called, can act in three primary methods.
Here is a shocking example of a major DDoS attack taking place:
The video opens up a whole new perspective on DDoS data protection, doesn’t it?
It illustrates the possible severity of an attack and also sheds light on the systems that you need to have in place to defend. And the sad reality is the average strength of DDoS attacks continues to grow.
According to Verisign Q1 2018 DDoS Trends Report, the average peak attack size increased by 26% in the reported period. A related study from Neustar suggests that such an attack can cost a company more than $250,000 per hour at risk.
To protect against DDoS, it is essential to understand the most common types of attacks.
Types of DDoS Attacks & How Each Work
Volumetric Attacks
The most common DDoS attack overwhelms a machine’s network bandwidth by flooding it with false data requests on every open port the device has available. Because the bot floods ports with data, the machine continually has to deal with checking the malicious data requests and has no room to accept legitimate traffic. UDP floods and ICMP floods comprise the two primary forms of volumetric attacks.
UDP stands for User Datagram Protocol and refers to the simple transmission of data without checking its integrity. The UDP format lends itself well to fast data transmission, which unfortunately makes it a prime tool for attackers.
ICMP stands for Internet Control Message Protocol, referring to network devices that communicate with one another. An attack focused on ICMP relies on attacking nodes sending false error requests to the target. The target has to deal with these requests and cannot respond to real ones, similar to how a UDP attack works.
Application-Layer Attacks
The application layer is the topmost layer of the OSI network model and the one closest to the user’s interaction with the system. Attacks that make use of the application layer focus primarily on direct Web traffic. Potential avenues include HTTP, HTTPS, DNS, or SMTP.
Application-layer attacks are not as easy to catch because they typically make use of a smaller number of machines, sometimes even a single one. Therefore, the server can be tricked into treating the attack as nothing more than a higher volume of legitimate traffic.
Protocol Attacks
A protocol attack focuses on damaging connection tables in network areas that deal directly with verifying connections. By sending successively slow pings, deliberately malformed pings, and partial packets, the attacking computer can cause memory buffers in the target to overload and potentially crash the system. A protocol attack can also target firewalls. This is why a firewall alone will not stop denial of service attacks.
One of the most common protocol attacks is the SYN flood, which makes use of the three-way handshake process for establishing a TCP/IP connection. Typically, the client sends a SYN (synchronize) packet, receives a SYN-ACK (synchronize-acknowledge), and sends an ACK in return before establishing a connection. During an attack, the client only sends SYN packets, causing the server to send a SYN-ACK and wait for the final phase that never occurs. This, in turn, ties up network resources.
Often, would-be hackers combine these three types of approaches to attack a target on multiple fronts, completely overwhelming its defenses until stronger and more thorough countermeasures can be deployed.

7 Best Practices for Preventing DDoS attacks
The evolution of DDoS attacks shows no signs of slowing. They keep growing in volume and frequency, today most commonly involving a “blended” or “hybrid” approach.
Without early threat detection and traffic profiling systems, it’s impossible to know they’re here. In fact, chances are you know about it only when your website slows to a halt or crashes.
This is especially true for sophisticated attacks, which use a blended approach and target multiple levels simultaneously.
These attacks target data, applications, and infrastructure simultaneously to increase the chances of success. To fight them, you need a battle plan, as well as reliable DDoS prevention and mitigation solutions. You need an integrated security strategy that protects all infrastructure levels.
1. Develop a Denial of Service Response Plan.
Develop a DDoS prevention plan based on a thorough security assessment. Unlike smaller companies, larger businesses may require complex infrastructure and involving multiple teams in DDoS planning.
When DDoS hits, there is no time to think about the best steps to take. They need to be defined in advance to enable prompt reactions and avoid any impacts.
Developing an incident response plan is the critical first step toward comprehensive defense strategy. Depending on the infrastructure, a DDoS response plan can get quite exhaustive. The first step you take when a malicious attack happens can define how it will end. Make sure your data center is prepared, and your team is aware of their responsibilities. That way, you can minimize the impact on your business and save yourself months of recovery.
The key elements remain the same for any company, and they include:
- Systems checklist. Develop a full list of assets you should implement to ensure advanced threat identification, assessment, and filtering tools, as well as security-enhanced hardware and software-level protection, is in place.
- Form a response team. Define responsibilities for key team members to ensure organized reaction to the attack as it happens.
- Define notification and escalation procedures. Make sure your team members know exactly whom to contact in case of the attack.
- Include the list of internal and external contacts that should be informed about the attack. You should also develop communication strategies with your customers, cloud service provider, and any security vendors.
2. Secure Your Network Infrastructure.
Mitigating network security threats can only be achieved with multi-level protection strategies in place.
This includes advanced intrusion prevention and threat management systems, which combine firewalls, VPN, anti-spam, content filtering, load balancing, and other layers of DDoS defense techniques. Together they enable constant and consistent network protection to prevent a DDoS attack from happening. This includes everything from identifying possible traffic inconsistencies with the highest level of precision in blocking the attack.
Most of the standard network equipment comes with limited DDoS mitigation options, so you may want to outsource some of the additional services. With cloud-based solutions, you can access advanced mitigation and protection resources on a pay-per-use basis. This is an excellent option for small and medium-sized businesses that may want to keep their security budgets within projected limits.
In addition to this, you should also make sure your systems are up-to-date. Outdated systems are usually the ones with most loopholes. Denial of Service attackers find holes. By regularly patching your infrastructure and installing new software versions, you can close more doors to the attackers.
Given the complexity of DDoS attacks, there’s hardly a way to defend against them without appropriate systems to identify anomalies in traffic and provide instant response. Backed by secure infrastructure and a battle-plan, such systems can minimize the threat. More than that, they can bring the needed peace of mind and confidence to everyone from a system admin to CEO.
3. Practice Basic Network Security
The most basic countermeasure to preventing DDoS attacks is to allow as little user error as possible.
Engaging in strong security practices can keep business networks from being compromised. Secure practices include complex passwords that change on a regular basis, anti-phishing methods, and secure firewalls that allow little outside traffic. These measures alone will not stop DDoS, but they serve as a critical security foundation.
4. Maintain Strong Network Architecture
Focusing on a secure network architecture is vital to security. Business should create redundant network resources; if one server is attacked, the others can handle the extra network traffic. When possible, servers should be located in different places geographically. Spread-out resources are more difficult for attackers to target.
5. Leverage the Cloud
Outsourcing DDoS prevention to cloud-based service providers offers several advantages. First, the cloud has far more bandwidth, and resources than a private network likely does. With the increased magnitude of DDoS attacks, relying solely on on-premises hardware is likely to fail.
Second, the nature of the cloud means it is a diffuse resource. Cloud-based apps can absorb harmful or malicious traffic before it ever reaches its intended destination. Third, cloud-based services are operated by software engineers whose job consists of monitoring the Web for the latest DDoS tactics.
Deciding on the right environment for data and applications will differ between companies and industries. Hybrid environments can be convenient for achieving the right balance between security and flexibility, especially with vendors providing tailor-made solutions.
6. Understand the Warning Signs
Some symptoms of a DDoS attack include network slowdown, spotty connectivity on a company intranet, or intermittent website shutdowns. No network is perfect, but if a lack of performance seems to be prolonged or more severe than usual, the network likely is experiencing a DDoS and the company should take action.
7. Consider DDoS-as-a-Service.
DDoS-as-a-Service provides improved flexibility for environments that combine in-house and third party resources, or cloud and dedicated server hosting.
At the same time, it ensures that all the security infrastructure components meet the highest security standards and compliance requirements. The key benefit of this model is the ability of tailor-made security architecture for the needs of a particular company, making the high-level DDoS protection available to businesses of any size.

How to Stop a DDoS attack? Monitor for Unusual Activity
Early threat detection is one of the most efficient ways to prevent the attack.
Denial of service can come in multiple forms, and it is critical to recognize its most common telltale. Any dramatic slowdown in network performance or an increase in the number of spam emails can be a sign of an intrusion. These should be addressed as soon as they are noticed, even if deviations do not look that important at first.
Businesses also need to understand their equipment’s capabilities to identify both network-layer and application-layer attacks. If you do not have these resources in-house, you may want to work with your ISP, data center, or security vendor to get advanced protection resources.
With proper systems to detect and react to all types of attacks, you already set your business for a successful defense.
What to Look For In a DDoS Mitigation Service
When possible, it is beneficial to choose a DDoS mitigation service that keeps engineers and network administrators on site continuously monitoring traffic. By doing so, it enables a faster response time than having to do work remotely.
Another factor is whether the service deals with SSL attacks. Sites that provide commercial transactions run on SSL, and a successful attack against this protocol can cost thousands of dollars in lost revenue.
The more comprehensive the mitigation plan, the better off networks are when it comes to protection against DDoS attack. Many different services exist on the market.
Always Be Prepared For Denial of Service Attacks
DDoS attacks are painfully real and are no longer massive corporations problem only. Small and medium-sized companies are increasingly the targets. This trend has sparked even greater demand for multi-layered security solutions that can provide full protection of sensitive workloads.
While the threat landscape continues to develop, so do security technologies. Following that trend, we recently released the fourth phase of DDoS enhancements for all our services. We will be increasing our focus on educated businesses on the most common cyber threats and best security strategies to defend.
Ready to take the next step and ensure business continuity? Contact our cloud security experts to find out more and stop the next DDoS attack from happening to your business.
Recent Posts
What is UPnP or Universal Plug and Play? A Little Known Security Risk
Universal Plug and Play (UPnP) was marked as a significant technological advance.
But, it comes with its share of drawbacks that might leave your systems vulnerable to potential cyber-attacks. In fact, it is enabled by default on millions of routers.
This article will discuss what UPnP is and the risks it poses to your network’s security.
What is Universal Plug and Play (UPnP)?
Universal Plug and Play is a set of networking protocols. It enables network devices such as computers, Internet gateways, printers, media servers, and Wi-Fi access points to discover each other’s presence on the network and create functional network services for data sharing.
UPnP was intended for private networks that do not have enterprise connectivity.
This technology operates under the assumption that a network runs IP (Internet Protocol) after which it leverages SOAP, XML, and HTTP so that it can provide service/device description, data transfers, actions, and eventing. Advertisements and device search requests are enabled by running HTTP in addition to UDP – port 1900 – using HTTPMU (multicast). Search requests’ responses are usually sent over the UDP.
This technology was endorsed by the UPnP forum which is an industry initiative to promote robust and straightforward connectivity to personal computers and stand-alone devices from different vendors. The panel comprised of over 800 vendors who were involved in everything from network computing to consumer electronics. But as from 2016, Universal Plug and Play is managed by the Open Connectivity Foundation.
In concept, Universal Plug and Play is supposed to extend plug and play (a technology that dynamically attaches devices directly to a machine) to zero-configuration networking for SOHO and residential wireless networks.
Thus, UPnP devices are archetypical plug and play. When they are connected to a network, they automatically seek and create working configurations with other hardware.
What Does UPnP Do?
If the above definition seemed a bit complex, then let us use a printer as an example.
In an office setup, the first step would be to connect it physically to the network router – even though you can do it via Wi-Fi today. In the past, you would have to search for the printer manually and then set it up so that other devices within the network can find the printer. Today, however, this process happens automatically thanks to Universal Plug and Play.
Once they are connected, the devices on that network will continue communicating with each other by receiving and sending data. As such, a computer can instruct the printer to print documents; a media center can transmit audio data, while mobile devices can mount themselves onto the computer. The possibilities are endless.
This is why it is called plug and play. You plug in a device and can start playing it right away without having to go through the hassles of setting up and configuring the connection. This makes it one of the most convenient networking technologies that are available to us.
However, UPnP technology has serious security flaws.
For instance, if a computer or some other device connected to the router exploited, the attacker may gain remote control of all devices and security systems. Thus, allowing access to your passwords and access all the other devices that are connected to the network. Additionally, once a device has been compromised, it can be utilized as part of a botnet to issue DDoS (distributed denial of service) campaigns to take down sites while hiding the attacker’s location. It might also provide them with a starting point for other attacks.
Some of the most significant cyber-crimes in recent history have leveraged internet-based devices to launch major DDoS attacks.
With more and more devices utilizing this technology to get connected to the internet, they are the ideal targets for hackers who have to accumulate devices so that they can overwhelm a business network.
Security Risks of Universal Plug and Play
A security survey by Akamai discovered that hackers are actively exploiting the weaknesses of this technology as a starting point for more prominent attacks.
For example malware distribution, DDoS, credit card theft, and phishing attacks.
The evidence found suggested that over four million devices were potentially susceptible to being used in a DDoS attack. This number accounts for approximately 38 percent of the 11 million internet-facing UPnP devices that are being used all over the world. This serves as a big pool for hackers to leverage what would have been small and local attacks into serious threats.
Primarily, these cybercriminals exploit this technology’s weaknesses to reroute the traffic in your business repeatedly until it is untraceable. And in spite of the industry’s knowledge about these vulnerabilities, hackers continue to take advantage of the general apathy towards strengthening the technology.
By default, this technology does not employ authentication.
This means that to ensure security, the devices in the network have to incorporate the additional Device Security Service or the Device Protection Service. There is also a non-standard solution that exists known as Universal Plug and Play – User Profile (UPnP-UP) which proposes an extension to enable user authentication and authorization techniques for UPnP-applications and devices. Sadly, most universal plug and play device implementations do not have authentication methods because they assume that local systems and their users can be trusted.
If authentication techniques are not implemented, firewalls and routers that run the UPnP-protocol become vulnerable to attacks.

Don’t Overlook Securing Your Network
The purpose of Universal Plug and Play technology is to make devices on a specific network to be easily discoverable by other utilities on the same network. Unfortunately, some Universal Plug and play control interfaces can be exposed to the public internet thereby enabling individuals with malicious intent to locate and obtain access to your devices.
A device that is compromised is nothing short of a ticking time bomb for your business network. Because of the complicated nature of these attacks, detecting one as it happens can be very difficult for the user.
In our current world where a fluid work culture is ideal, more and more employees are taking connected devices to and from their workplaces. There is no room for error when it comes to your business’s cybersecurity.
The takeaway here is that you should ensure that your UPnP router settings are disabled.
Recent Posts
What is an MSSP, Managed Security Services Provider?
Every company prioritizes cybersecurity. However, many struggle to prioritize their security needs. Sound familiar?
A managed security service provider (MSSP) can ensure your companies data is safe and secure.
Managed Security Service Provider Definition
A managed security service provider (MSSP) provides outsourced management and monitoring of security devices to protect companies’ digital infrastructures.
IT security services involve some combination of:
- Secure Web Application Firewalls
- Intrusion Detection
- Spam Blocking
- Virtual Private Networks (VPN) System Management
- Virus Protection
- Identity and privileged access management
One consistent benefit is that the managed service model provides clients with peace of mind. So, while some companies may already use advanced firewalls and anti-virus systems, companies that hire an MSSP for their enterprise security services, ensure round-the-clock protection.

6 Benefits of Working with an MSSP
Every year, a growing number of headlines announce the newest company victimized by cybercrime. According to the Identity Resource Center’s 2017 Annual Data Breach Year-End Review, the threat is multiplying, too. Between just 2016 and 2017, incidents grew up 44.7%.
Still, many businesses react to this growing threat by adding new best practices their security operations team. They may initiate new protocols aimed at network security.
Others realize it’s time to find a strategic partner and outsource their company’s protection to the experts.
1. Security Expertise
Most organizations can’t compete with an MSSP when it comes to the expertise they have on staff. Think about your business for a moment: the vast majority of your team dedicates their time to selling products or service offerings.
At managed security companies, their entire staff is dedicated to understanding how to keep companies like yours safe from cybercrime.
While every security partner is different, they all have teams based around specific needs. One team specializes in vulnerability management, while another is in charge of handling cyber security incident responses.
Hiring the same kind of expertise isn’t realistic for most businesses. Just as important, these experts are tasked with staying up-to-date on the evolving threat landscape. The reason criminals victimize many companies is that new threats debut every year. Without experts who continuously monitor this complex field, it’s impossible to defend against them.
2. Affordability
Plenty of companies do have the resources to hire these kinds of specialists and create those kinds of teams. However, they still hire MSSPs.
One reason is that a managed network security service comes at a much lower price. Organizations can protect their budget and their network at the same time. Of course, with the average cost of a successful data breach topping $3.8 million, any price for an MSSP is affordable.
3. Adaptability and Scalability
If your company is like most, it changes regularly. Every year, your technology also needs to update to keep pace.
When you contract Security as a Service (Saas) providers, you’re investing in your company’s ability to change at will. If you want to scale, but realize you’ll need better computer forensics, MSSP companies are there to help.
If you create new web applications, you have a group of dedicated experts who will test it for vulnerabilities.
You can wait until your company can support this move with better technology and expertise. Alternatively, you could scale and hope that a cyber threat doesn’t end up costing you.
A managed security service provider also serves in an advisory role. They’ll let you know where you need to make changes to support specific goals. You don’t need to worry that chasing new goals will leave you vulnerable.

4. Constant Monitoring and Risk Management
Unfortunately for business owners, cybercriminals don’t call it a day when you do. The good news is: neither does an MSSP.
They will keep watch over your company 24/7/365. Knowing experts are protecting your company around the clock should give you priceless peace of mind.
5. Customizable Service Offerings
Relying on a security service vendor doesn’t mean outsourcing all of your needs, either. It certainly can, but it all depends on your organization’s unique needs.
Many organizations need data centers with added security or assistance with managing their private network. Others may need to leverage specific information or security administration services.
Typical examples of these include:
- Provisioning
- Security Updates
- Education and Training
- Privileged access management (PAM)
- Role-Based Access Control Fulfilments
- Cybersecurity Management Reporting
- Security Strategy
- Compliance Reporting
6. Information Security Policy Development and Maintenance
All the hardware and software in the world can’t save you from a network threat if you don’t have the right policies in place.
A company’s employees are usually one of their most significant vulnerabilities. A cyber attack doesn’t necessarily need to be exceptionally advanced to hit its mark.
MSSP’s can help you develop one from scratch. Most importantly, they’ll tailor it to your company’s unique traits. You shouldn’t try to retrofit a “boilerplate” version of something this important.
Managed security services can also monitor to make sure your staff is following this policy. As time goes on, changes and updates will be necessary.
It could be due to scaling, or that new safeguards are necessary to ensure employees don’t leave an organization open to attack. Your security provider will proactively recommend these changes and even implement them on your behalf.

How to Choose a Managed Security Provider
Given the benefits, it should come as no surprise that managed security service providers are in high demand. If you’re in the market for one, you’ll have no lack of options.
Nonetheless, picking the right one for your company is essential. Here’s what to look for when making your choice.
1. Relevant Service Offerings
Don’t settle for a solution that doesn’t offer every single service your company needs—save for those you wish to keep in-house. This includes the expertise you need for your specific industry.
For example; you may need an MSSP that has experience working with companies that must abide by the GDPR. If you work in healthcare, you would most likely want an MSSP that understands HIPAA compliant hosting.
At the same time, don’t pay for any additional services that your company won’t use. You can always add new services in the future, as they are required.
2. Thorough Assessments
Even if you have your IT team to help, look for a managed security provider who offers assessments.
You want an expert to inspect your company’s digital infrastructure, so they know exactly what’s required to keep it safe.
3. Onsite Security
One of these companies could become a significant liability if they don’t have their own security needs covered.
The best providers have onsite security guards who actively patrol their facility—inside and out. Yours should have a security team staffed by veterans or former police officers. That’s how important the facility’s security is.
Remember, a data center is dedicated to many other clients as well. Even if you are under the assumption that your server is not under security threat, that doesn’t necessarily mean it’s safe.
Onsite network security is an effective deterrent against this worst-case scenario.
4. Disaster Avoidance Solutions
Disaster recovery is a standard service among MSSP security providers.
However, you also want to work with a company that can avoid disaster in the first place.
Ideally, they should be headquartered in a “disaster-free zone,” where threats like earthquakes or flooding are nonexistent. Otherwise, one disaster could be enough to derail your enterprise security services. It could also be a long time before you’re able to get them back.
Your security service provider should also have data center locations worldwide. This is just further protection against the worst possible disasters.
No matter what happens, your company’s Recovery Point Objective (RPO) will remain intact.

Start Your Search for Managed Security Services
Now that you understand what an MSSP does and how to find the right one, it’s time to begin your search. Even if you’re not sure about your company’s specific needs yet, it’s worth consulting with one of our experts. Protection is too critical to wait.
Start today, and you’ll soon enjoy the peace of mind that comes from having managed security solutions defending your company.
Recent Posts
Data Security In Cloud Computing: How Secure Is Your Data?
This article is an expert-level account of our security services by phoenixNAP’s own Anthony Dezilva. Anthony is a 25yr industry veteran, with a background in virtualization and security. He is the Product Manager for Security Services at phoenixNAP.
Leadership and Partnership In Cloud Security
Definitions are critical; essential even. The term “leadership”, for example, is defined simply by Google dictionary, as “The action of leading a group of people or an organization”. At phoenixNAP, leading in our industry is part of our DNA and culture. We define leadership as creating innovative, reliable, cost-optimized, and world-class solutions that our customers can easily consume.
In that vein, the term “Cloud Infrastructure” (or its predecessor “Cloud Computing“) tend to represent multiple different scenarios and solutions, drummed up by overzealous marketing teams. Without a clear definition, clarity around the terms is convoluted at best. “Cloud Security,” however, is more often described as representing concerns around data confidentiality, privacy, regulatory compliance, recovery, disaster recovery, and even vendor viability. We aim to bring clarity, specificity, and trust into this space through our Data Security Cloud solutions.
The Road Ahead: The Security Landscape
According to Heng & Kim (2016) of Gartner, by 2020, 60% of businesses will suffer a failure of some sort, directly attributed to their internal IT team’s inability to manage risk effectively. 87% of nearly 1200 global C-Level executives surveyed by E&Y say they needed 50% more funding to deal with the increased threat landscape. Compound that problem by the fact that we are facing a global skills shortage in technology and security services. These issues directly impact the ability of organizations to maintain and retain their Information Technology and now their Cybersecurity staff.
While the industry prepares for this potential security epidemic, predictions state that a consolidation of the vast number of security services providers is going to take place, along with an increased focus and reliance on automation and machine learning tools. Despite public concern, this may not be such a bad thing. The growing sophistication of these tools, the ability to perform analytics and correlation in many dimensions, and the automation capabilities, could create efficiencies or potentially, advancements in our defensive capabilities.
Industry-leading providers in this space are not standing idly by. As such a provider, phoenixNAP is at the forefront of many initiatives, ranging from local to international. For example, it is critical that we begin to foster knowledge in children as young as grade school to gain an interest in the field. Working with industry organizations, we sponsor events and take leadership roles in organizations to support curriculum development and awareness. We are leading efforts in threat intelligence sharing, and the use of disparate dark web data sources, to create a predictive analysis that can be operationalized for early threat vector identification. Additionally, we have partnered with the United States Armed Forces and U.S. Department of Veteran Affairs to provide pathways for those service members interested, to have a low barrier of entry, and to have a dedicated support system, so that they can successfully transition into cyber roles as civilians.
“Leadership,” we view as our social responsibility and our contribution to enhancing the security posture of our market segment.
Why is this relevant to security in the cloud?
A Gartner study from 2015 predicted a 16% year-over-year annual growth rate. The reality is that as we approach the 2020 mark, we see a 32% increase in IT spending on cloud services. That same study identified that about 40% of IT budgets are now allocating for cloud or SaaS related services.
“These growing statistics are relevant because this is going to influence your existing cloud strategy dramatically, or if you don’t have one, this should alert you that you will soon require one.”
Secure Solutions From Our Unique Perspective
It is safe to assume you are already in the cloud, or you are going there. Our focus is to educate on what we believe are the most significant components of a secure cloud infrastructure, and how these components complement and support the security needs of modern business. Just as the path-goal theory emphasizes the importance of the relationship to the goal achievement, as a technology service provider, we believe in partnering with our customers and going the extra mile to become mutually trusted advisors in product creation and sustenance. The cloud is in your not-too-distant future. Let us keep you safe and secure, and guide you along the way.
At phoenixNAP, we have a unique perspective. As an infrastructure provider, we offer a service portfolio of complementary tools and services to provide organizations with holistic, secure, cloud-based solutions. With that in mind, we identified a gap in the small, and medium-sized business space (SMB), and their barriers to entry, for access to cutting-edge technology such as this. We knew what we had to do: we developed the tools to help these businesses with access to a world-class secure cloud-based solution offering, which met and supported their regulatory needs. We set the bar on performance, recoverability, business continuity, security and now compliance pretty high. Our passion for small to medium-sized businesses and dedication to security is why we built the Data Security Cloud. Our Data Security Cloud is an aspiration to create the world’s most secure cloud offering.
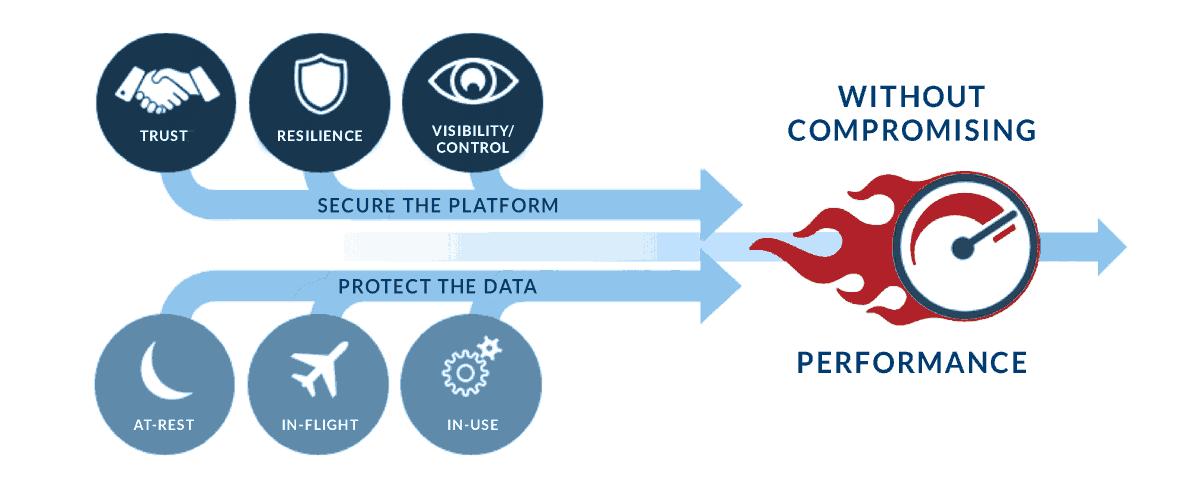
Cloud Security is a Shared Responsibility
The 2017 Cloud Adoption Survey found that 90.5% of respondents believe that Cloud Computing is the future of IT. As many as 50.5% of these respondents still identified security as a concern. Of those concerns, the following areas were of particular interest:
-
- Data and application integration challenges
- Regulatory compliance challenges (54% indicated PCI compliance requirements)
- Worries over “lock-in” due to proprietary public cloud platforms
- Mistrust of large cloud providers
- Cost
We architected our solution from the ground up, with these perspectives in mind. We identified that we needed to monitor, actively defend, and resource a Security Operations Center, to respond to incidents 24×7 globally. We designed a solution where we partner with each of our customers to share in the responsibility of protecting their environment. Ultimately, this strategy contributes to protecting the privacy and confidentiality of their subsequent customers privileged, financial, healthcare, and personal/demographic data. We set out to design a system to empower your goals towards your security posture.
Our challenge, as we saw it, was to commoditize and demystify the types of security in cloud computing. We have invested significant resources in integrating tools and pushed vendors to transition from a traditional CapEx cost model to an OpEx pay-as-you-grow model. Ultimately, this strategy enables pricing structures that are favorable for this market segment and removes any barrier of entry, so that our customers can access the same tools and techniques formerly reserved for the enterprise space.
What are Cloud Services?
When speaking of Cloud Services, we have to define the context of:
Private Cloud
-
- A Private Cloud typically represents the virtualization solution you have in-house or one you or your organization may host in a data center colocation.
- Optimizing the use of idle time on a typical compute workload, by aggregating multiple workloads onto a single host, the Private Cloud will take advantage of the resource overprovisioning inherent of a bare metal hypervisor platform.
- You own your Private Cloud. It is technically in your facility, under your operational control. The confidence in the security controls are therefore high, yet dependent on the skills and competency of the operators and their ability to keep up with proper security hygiene.
- The challenge, however, is that you still have to procure and maintain the hardware, software, licensing, contingency planning (backup and business continuity), and even the human resources described above. Including the organizational overheard to continuously develop and manage these resources (training, HR, medical/dental plans, etc.).

Public Cloud
-
- A public cloud is an environment where a service provider makes a virtualization infrastructure available for resources such as virtual machines, applications, and/or storage. These resources are open to the general public consumption over the internet. The public cloud is typically an environment operated under a pay-per-use model, where the customer pays only for what they have subscribed and/or committed to.
- We can categorize public cloud further as:
- Software-as-a-Service (SaaS). A great example of SaaS is Microsoft’s Office 365. Although you can use a lot of the tools via the internet browser itself, you can also download the client-facing software, while all the real work happens within the cloud environment.
- Platform-as-a-Service (PaaS). A solution where the cloud provider delivers hardware and software tools, typically in an OpEx model.
- Infrastructure as a Service (IaaS). When we refer to the public cloud, this is typically the service most people refer to. A typical scenario is when you visit a website and order a virtual Windows Server; with X amount of processors, Y amounts of RAM, and Z amounts of Storage. At phoenixNAP, we offer this style of service. Once provisioned, you install IIS and Wordpress, you upload your site, and now you have an internet-facing server for your website. Consumers drawn to this model are typically cost-conscious and attempting to create their solution with the least expenditure. Things like an Internet-facing firewall could be overlooked or entirely skipped. Strong system architecture practices such as creating separate workloads for web platforms and database/storage platforms (with an internal firewall) may also suffer. What might be obvious at this point is that this is one of those areas of intense focus when we created our solutions.
- Our value proposition is that this type of cloud platform reduces the need for the organization to invest and maintain its on-premise infrastructure, resources, or even annual service contracts. Although this will reduce resource needs, it will not eliminate them. As most licensing costs are either included via the provider and most likely available at significantly reduced price-points through the provider’s economies of scale, you are also guaranteed to get some of the best pricing possible.
The following table contrasts the shifting cost allocation model:
Traditional IT
Asset Costs
-
- Server Hardware
- Storage Hardware
- Networking Hardware
- Software Licensing
Labor Costs to Maintain Infrastructure
Physical Data Center Costs
-
- Power
- Cooling
- Security
- Insurance
Outsourcing/Consulting Costs
Communications/Network Costs
Public Cloud
Virtual Infrastructure Costs
-
- Server Costs
- vProcs
- vRAM
- vStorage
- Software License Costs
- Professional Services
- Bandwidth Costs
- Managed Services Costs
- Server Costs
Hybrid Cloud
-
- Consider the Hybrid Cloud as a fusion between the Private and Public Cloud. The desired goal is for workloads in both of these environments to communicate with each other, including the ability to move these workloads seamlessly between the two platforms.
- Though this is also possible in the other scenarios, in the case of the Hybrid Cloud, it is typical to see a public cloud environment configured like an on-premise environment. This scenario could have proper North-South traffic segmentation, and in the rare case, proper East-West traffic segmentation facilitated by either virtual firewall appliances or most recently VMware NSX based micro-segmentation technology.
What Role Do Control Frameworks Play?
Control Frameworks are outlines of best practices. A strong and defined set of processes and controls that help the provider adhere to proper security posture. Posture that can be evaluated, audited and reported on, especially when subject to regulatory requirements verified by an audit process. What this means to a consumer is that the provider has built a standards-based solution that’s consistent with the industry. They have not cut corners, they have made the effort to create a quality product that’s reliable and inter-operable should you need to port-in or port-out components of your infrastructure. A standards-based approach by the provider can also be leveraged for your own regulatory compliance needs, as is may address components on your checklist that you can assign to the provider.
Partnering With the Best
Market share numbers are a quantitative measure, although subject to a level of alpha, it is still statistically sound. Intel and VMware are clear leaders and global innovators in this space. Product superiority, a qualitative measure, is a crucial asset when integrating components to create innovative solutions in a highly demanding space. At phoenixNAP, we are proud of our ongoing partnerships and proud to develop products with these partners. We believe in the value of co-branded solutions that innovate yet create stable platforms due to longevity and leadership in the space.
Developing our Data Security Cloud (DSC) product offering, we had the pleasure of working with the latest generation of Intel chipsets and early release VMware product code. We architected and implemented with next-generation tools and techniques, not bound by the legacy of the previous solutions or methodologies.
We incorporated VMware’s vRealize Suite and vCloud Director technologies into a world-class solution. At phoenixNAP, we not only want to empower our customers to manage their operational tasks themselves but by using the industry standard VMware as a platform, we can create hybrid cloud solutions between their on-premise and Data Security Cloud implementations.
Starting Fresh
As we wanted to design a secure cloud service offering, we chose not to be influenced by legacy. Starting with a whole new networking platform based on software-defined-networking, we created and built a flexible, scalable, solution, incorporating micro-segmentation and data isolation best practices. We designed this level of flexibility and control throughout the entire virtualization platform stack and the interconnecting communications fabric.
Design Methodology
We drew upon our extensive background in meeting compliance goals; incorporating a framework approach, using industry best practices, anticipating the needs and limitations inherited with achieving industry and compliance certifications such as PCI, HIPAA Compliance, and ISO 27002 (coming soon). We designed a flexible, yet secure architecture, supplemented by a VMware LogInsight log collection and aggregation platform, that streams security-related incidents to a LogRhythm SIEM, monitored by our 24×7 Security Operations Center (SOC).
We Proved It
What better way to prove that we achieved our goals in a security standard than to have the most respected organizations validate and certify us. We had TrustedSec evaluate our environment, and have them attest that it met their expectations. However, we didn’t stop at just achieving compliance alone. Additionally, as security professionals, we audited our environment, going over and beyond the regulatory standards. We designed our framework to have a “no compromise approach,” and our fundamental philosophy of “do the right thing” from a technical and security perspective. Proved by our PCI certification of this secure cloud platform.
The Launch of our Security Services Offering
After years of extensive testing and feedback from our customers, we built our Security Risk Management and Incident Response capabilities into a service offering, available to our entire customer base. We enhanced our Security Operations through the integration of advanced Security Orchestration and automated testing tools, and through strategic partnerships with public and private Information Sharing and Collaboration (ISACs) organizations. Enhanced by our ability to gather threat vector data globally, in real-time from our own systems, member organizations, and the dark web, we utilize unique enrichment techniques, to do predictive profiling of the social structure of this society; with a goal create, actionable intelligence or early warning systems, to support our defensive posture.
What this means is that we are building advanced tools to detect threats before they impact your business. We are using these tools to take preventative action to protect customer networks under our watch. Actions which could see the latest threat pass you by without including you in its wake.
Layered Approach to Creating a Secure Cloud Infrastructure
Proven Base
phoenixNAP has a long and proven history in designing, developing, and operating innovative infrastructure solutions. With a parent company in the financial transactions sector, we have extensive knowledge and expertise in the secure operations of these critical solutions. As an operator of global data center facilities, we have established a trustworthy reputation and operational process, to support the needs of our diverse and vast client base.
Our certifications in SOC-1, SOC-2, and SOC-3 establish a baseline for physical and logical access control, data security, and business continuity management and procedures. Our Type II designation verifies these capabilities in practice. Our PCI-DSS certification establishes our commitment and credibility to “doing the right thing” to create an environment that exemplifies your concerns for the highest level of security posture.
Redundant Global Communication Fabric
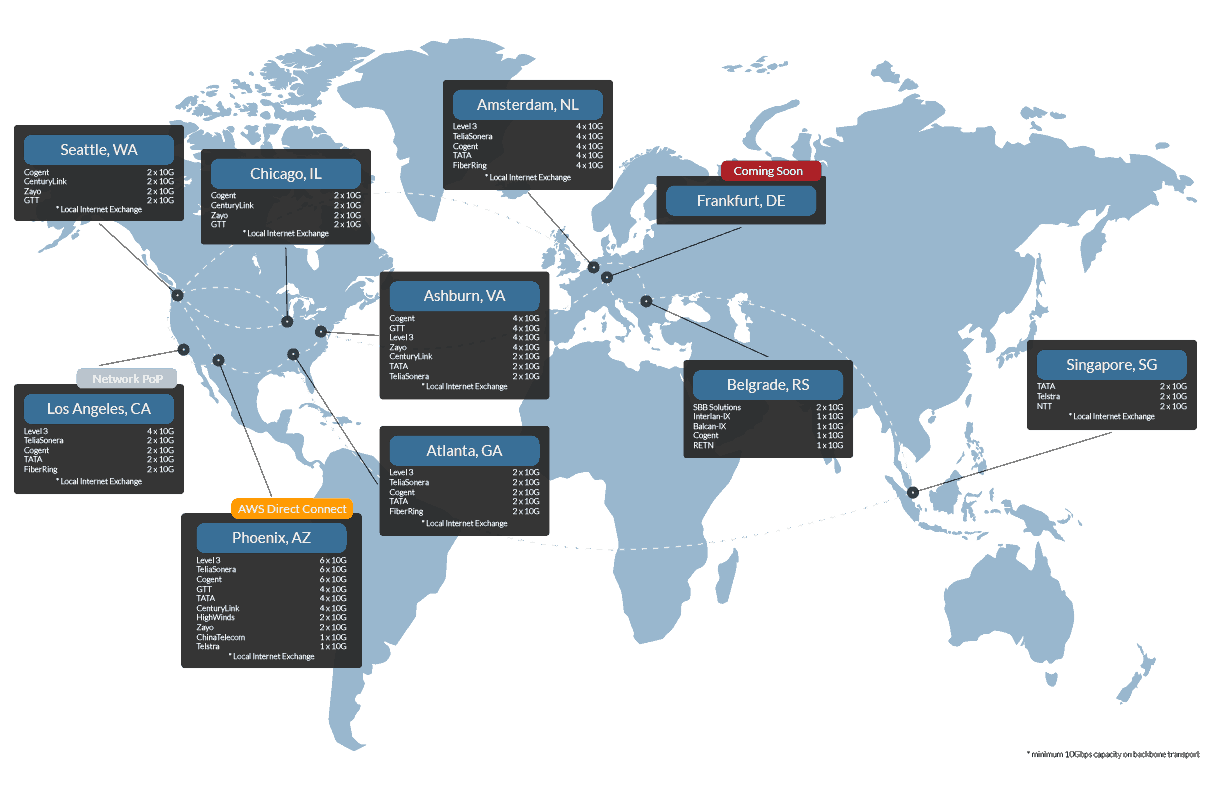
Highly Scalable Hardware Platform
“A new platform that represents the largest Data Center Platform advancement in a decade”
Lisa Spellman – Intel VP/GM of Xeon and Datacenter
Secure at the Foundation
-
- Root of trust module (TPM)
- Built-in instruction sets for verification (Intel TXT)
- Fast, high-quality random number generator (RDSEED)
- Firmware assurance (BIOS Guard)
Built-in Ecosystem
-
- Efficient provisioning and initialization (Intel PTE)
- Scalable management with policy enforcement (Intel CIT)
- Direct integration with HyTrust and VMware, etc.
A New Level of Trust
-
- Secure, Enterprise Key Management
- Trusted connectivity
- Remote attestation fo the secure platform
- Compliance and measurement at the core
Designed around the latest Intel Xeon processor technology alongside our extensive expertise in managing highly scalable workloads in our other cloud offerings, we built a computing platform that achieved 1.59X performance gaines over previous generations. These increases that are passed down into our customer’s workloads, providing them with better performance, and a higher density environment to optimize their existing investment, without any capital outlay; in most cases without any additional OpEx commitments.
Advanced Hypervisor Technology
We build a foundational commitment to VMware, and our commitment to integrate the latest tools and techniques to empower our customers to do what they need, whenever they need it.
Using Hybrid Cloud Extender we can help customers bridge the network gaps to hosted cloud services while maintaining network access and control. Tools like VMWareNSX allow for the creation of logical security policies that can be applied to a Virtual Machine regardless of location (cloud or on-premise). The integration of the latest Intel Cloud Integrity Toolkit allows for platform security with unmatched data protection and compliance capabilities.
Our vRealize Suite and vCloud Director integration is no different. We provide our customers with direct access to the tools they need to manage and protect their hybrid cloud environments effectively. In the event the customer wishes to engage phoenixNAP to perform some of these tasks, we offer Managed Services through our NOC and 3rd party support network.
Segmented Components
Experience has taught us how to identify and prevent repeat mistakes, even those made by strategic or competitive partners in the industry segment. One of those lessons learned is the best practice to section and separate the “Management” compute platform, from the “User compute platform.” Segmentation will significantly minimize the impact of a “support system” crash, or even a heavy operational workload, from impacting the entire computing environment. By creating flexible and innovative opportunities, we train our teams to reflect, communicate and enhance their experiences, creating a knowledgeable and savvy operator who can step onto the batter’s box ready to do what’s asked of them.
Threat Management
We believe that we have created a state-of-the-art infrastructure solution with world-class security and functionality. However, the solution is still dependent on a human operator. One, that based on skill or training, could be the weakest link. We, therefore, engage in continuous education, primarily through our various industry engagements and leadership efforts. This service offering is designed to be a high touch environment, using a zero-trust methodology. A customer, who is unable to deal with the elements of an incident, can see us engage on their behalf and resolve the contention.
If all else fails, and the environment is breached, we rely on 3rd party pre-contracted Incident Responders that deploy in a rapid format. The proper handling of cybersecurity Incident Response requires a Crisis Communication component. One or more individuals trained in handling the details of the situation, interfacing with the public and law enforcement, and based in the concepts of psychology, are trained to be sensitive and supportive to the various victim groups of the situation.
As we bundle backup and recovery as a core service in our offerings, we can make service restoration decisions based on the risk of overwriting data vs. extended downtime. Using the cloud environment to our advantage, we can isolate systems, and deploy parallel systems to restore the service, while preserving the impacted server for further forensic analysis by law enforcement.
It’s All About the Layers
Hierarchy of Virtual Environment Security Technologies
Security solutions are designed to defend through depth. If one layer is compromised, the defense process begins by escalating the tools and techniques to the next tier. We believe that a layered approach as described creates a secure and stable solution that can easily be scaled laterally as the needs and customer base grows.
Why Does This All Matter?
In one of his articles in the CISO Playbook series, Steve Riley challenges IT leaders not to worry that migration to the cloud may require relinquishing total control but encourages them to embrace a new mindset. This mindset is focused on identity management, data protection, and workload performance.
The primary is likely a reference to the cost savings achieved from consolidation, and transfer of responsibility to a service provider.
-
- Converting CapEx expenditure to OpEx ones can surely improve cash flow to those in the SMB market space.
- Reducing technical overhead through the elimination of roles no longer required, can provide far more operating capital, and
by re-focusing core-resources to concentrate on core-competencies, create business advantages in the areas that are important to the organization.
According to Gartner, the benefits of cloud migration include the following:
-
- Shorter project times: Cloud IaaS is a strong approach for trial and error, offering the speed required to test the business model success.
- Broader geographic distribution: The global distribution of cloud IaaS enables applications to be deployed to other regions quickly.
- Agility and scalability: The resource is pay-as-you-go. If an application is designed correctly, then it is simple to scale the capability in a short period.
- Increased application availability: As described, we have demonstrated the highest levels of security and reliability. If you have the right application design, you can develop application availability accordingly.
What’s Fueling the Cloud-First Strategy?
We hear many organizations adopting a cloud-first strategy, where they default to a cloud-based solution, until it proves unable, or not feasible before they consider other options. Factors driving this trend include:
-
- Reduced infrastructure and operational costs. From a reduction in capital expenditures, using the elasticity of cloud services, lower overall software costs and potential reduction of IT staff, organizations report approximately 14% in savings.
- Flexibility and scalability to support business agility. Agility is defined by the ability to bring new solutions to market quickly. The ability to control costs, leverage different types of services, and being flexible to adapt to market conditions.
- Cloud services tend to use the latest in innovation. Being able to leverage the high rate of innovation in this space, an organization can benefit by incorporating it as part of their business strategy.
- A cloud-first strategy can drive business growth through a supportive ecosystem.
Things to Consider
Not every workload is appropriate or destined for cloud-based compute platforms. The scoping part of any cloud migration project should start by identifying and selecting workloads that are easily migrated and implemented in multi-tenant cloud implementation.
The customer needs to understand the profile and characteristics of their workloads. For many years we would have never considered moving database workloads off of physical hardware. This is a similar case where high I/O or hardware timer reliant workloads (such as GPS or real-time event processing) may be sensitive to being in a shared, multi-tenant computer environment.
-
- More importantly, cloud services predominately revolve around x86-based server platforms. Therefore, workloads that are reliant on other processor architecture, or even specialized secondary processing units or even dongles, do not make ideal cloud candidates.
In contrast, cloud-based infrastructure allows for:
-
- Business Agility – for rapid deployment, and even rapid transition from one platform to another, with low transition costs.
- Device Choice – The flexibility to deploy, tear down, and redeploy various device configurations in a matter of clicks.
- Collaboration – Cloud providers typically provide an expert-level helpdesk, with direct access to a community of experts that can support your needs.
There are many reasons to consider a hybrid strategy where you combine workloads. What needs to stay on bare-metal can remain on bare metal servers, either in your facility or a colocation facility such as ours, while staying connected to the cloud platform via a cross-connect, gaining the benefits of both scenarios.
Cloud computing security consists of a broad set of concerns. It is not limited to data confidentiality alone, but concerns for privacy, regulatory compliance, continuity and recovery, and even vendor viability. Staying secure in the cloud is, however, a “shared responsibility.” It requires partnerships, especially between the customer and their infrastructure service provider. Nobody needs to be convinced that data breaches are frequent, and often due to management or operator neglect. Customers are becoming tired of their data being disclosed and then used against them. Most recently, abused via an email-based threat vector, where the bad actor quotes a breached user ID and password, as a way to convince the target recipient to perform an undesired action, behind the mask of perceived authenticity.
Any organization that accepts Personally Identifiable Information (PII) of its customer base establishes with that customer, an implied social contract to protect that information. At phoenixNAP, we have demonstrated leadership in the infrastructure space on a global scale, through partnerships with customers, solution aggregators, and resellers. We have created innovative solutions to meet the unique challenges faced by businesses, going above and beyond to achieve the goals desired by the target organization.
Notes from the Author: Elements of a Strong Security Strategy
Over the years, I have learned many important lessons when it comes to creating solutions that are secure and reliable. Here are some final thoughts to ponder.
-
- There is no substitute for strong architecture. Get it right and you have a stable foundation to build upon. Get it wrong and you will play whack-a-mole for the rest of that life-cycle.
- Have detailed documentation. Implement policies and procedures that make sense. Documentation that supports the business process. Security policy cannot burden the users. If it does, it just becomes a target for shadow IT. It needs to be supportive of the existing process while implementing the control it absolutely needs. A little control is better than no control due to a workaround.
- Plan for a breach, plan to be down, plan for an alien invasion. If you plan for it, you won’t be caught in a state of panic when something undoubtedly happens. The more off-the-beaten-path a scenario seems, the better you can adopt for when real-life scenarios arise.
- You can’t protect what you don’t know you have. Asset management is the best thing you can do for your security posture. If it’s meant to be there: document it. If it’s not meant to be there: make certain that you have a mechanism to detect and isolate it. Even to find out who put it there, why and when.
- Now that you know what you have: monitor it. Get to know what normal behavior is. Get to know its “baseline.”
- Use that baseline as a comparative gauge to detect anomalies. Is this system showing inconsistent behavior?
- Investigate. Have the capability to see the alert triggered by that inconsistent behavior. Are you a 24/7 operation? Can you afford to ignore that indicator until the morning? Will your stakeholders, including your customers accept your ability to detect and respond to the Service Level Agreement (SLA) you extend to them? Can you support the resourcing needed for a 24/7 operation, or do you need to outsource the Threat Management component at least in a coverage extension model? The best SIEM tools are useless without someone actioning the alerts as soon as they pop up. Machine learning helps, however, it cannot yet replace the operator.
- Mitigate the problem or be able to recover the environment. Understand what your Recovery Point Objectives (RPOs) and your Recovery Time Objectives (RTO). Do your current solutions meet those goals? Can those same goals be met if you have to recover into a facility across the country, with no availability from your current staff due to the crisis being faced? How will you communicate with your customers? Do you have a crisis communicator and incident handler as part of the response team?
- Take your lessons learned, improve the process and do it all over again.
No single vendor can provide you with a “silver bullet.” Any vendor that tells you such, is someone you should shy away from. Every customer’s needs are unique. Each situation takes a unique blend of solutions to be effective. Hence your vast network of partner relationships, to provide you with the solutions you need, without trying to make you fit onto one of their offerings.
The offer is always on the table. At phoenixNAP, we will gladly take the call to discuss your concerns in this area, and provide advice on what our thoughts are on the topic of interest. Promoting and supporting properly secured environments is part of our social responsibility. It is part of our DNA and the core philosophy for building products in this segment. Let us be your partner in this journey.
Use of Reference Architectures
One of the benefits of a cloud-based, secure infrastructure such as our Data Security Cloud, is the ability to implement battle tested reference architectures that in some cases go above and beyond the standard capabilities of what’s possible in the physical environment.
In what we would consider an extreme case; an architecture as depicted above creates multiple layers of security with various gateways to get to the prized databases that most bad actors are after. Let’s not ignore the bad actors that want to take control of the web infrastructure to infect visitors with infectious payloads; however, the real prize sits inside those databases in the form of PII, PHI, or PCI data. While the various levels of defensive components are designed to make it difficult for the bad actors to storm the castle, the 24×7 Threat Monitoring will undoubtedly catch the multiple attempts and anomalous behavior, triggering an investigation and response activity.
Through a robust combination of tools, technology, services, and a cost model that’s supportive of the needs of the SMB space, we believe we have demonstrated our leadership, but more importantly, we have created a solution that will benefit you; our SMB customer. We aim to have created a complete security solution that you can take forward as you further define your cloud strategy.
Our Promise
We have assembled a world-class team of highly experienced and skilled leaders, who are passionate about cloud security. As global thought leaders, we design for the world and implement locally. We create sustainable solutions, understanding a customer’s appetite and limited budget. Let us show you how we can benefit your goals through our solutions offerings. Keeping with our promise to “do the right thing” as it involves finding the best solution for you.
Get Started with Data Security in Cloud Computing Today
Contact phoenixNAP today.
Complete the form below and our experts will contact you within 24 hours.
Recent Posts
2020 Disaster Recovery Statistics That Will Shock Business Owners
This article was updated in December 2019.
Data loss can be chilling and has serious financial implications. Downtime can occur at any time. Something as small as an employee opening an infected email, or as significant as a natural disaster.
Yet, 75% of small businesses have no disaster recovery plan objective in place.
We have compiled an interesting mix of disaster recovery statistics from a variety of sources from technology companies to mainstream media. Think of a disaster recovery plan a lifeboat for your business.
Hardware failure is the number one cause of data loss and/or downtime.
According to Dynamic Technologies, hardware failures cause 45% of total unplanned downtime. Followed by the loss of power (35%), software failure (34%), data corruption (24%), external security breaches (23%), and accidental user error (20%).
17 more startling Disaster Recovery Facts & Stats
1. 93% of companies without Disaster Recovery who suffer a major data disaster are out of business within one year.
2. 96% of companies with a trusted backup and disaster recovery plan were able to survive ransomware attacks.
3. More than 50% of companies experienced a downtime event in the past five years that longer than a full workday.
Recovering From A Disaster Is Expensive
When your business experiences downtime, there is a cost associated with that event. This dollar amount can be pretty tough to pin down as it includes direct expenses such as recovery labor and equipment replacement. But, also indirect costs such as lost business opportunity.
The cost can be staggering:
4. Corero Network Security found that organizations spend up to $50,000 dealing with a denial of service attack. Preventing DDoS attacks is critical.
4. Estimate are that unplanned downtime can cost up to $17,244 per minute, with a low-end estimate of $926 per minute.
5. On average, businesses lose over $100,000 per ransomware incident due to downtime and recovery costs. (source: CNN)
6. 40-60% of small businesses who lose access to operational systems and data without a DR plan close their doors forever. Companies that can recover do so at a much higher cost and a more extended timeframe than companies who had a formal backup and disaster recovery (BDR) plan in place.
7. 96% of businesses with a disaster recovery solution in place fully recover operations.

Numbers Behind Security Breaches and Attacks
9. In a 2017 survey of 580 attendees of the Black Hat security conference in Las Vegas, it was revealed that the more than half of the organizations had been the target of cyber attacks. 20% of those came from ransomware attacks.
10. 2/3 of the individuals responding to the survey believe that a significant security breach will occur at their organization in the next year
11. More than 50% of businesses don’t have the budget to recover from the attack.
The Human Element Of Data Loss
Cybercriminals often utilize a human-based method of bypassing security, such as increasingly-sophisticated phishing attacks.
12. Human error is the number one cause of security and data breaches, responsible for 52 percent of incidents.
13. Cybersecurity training for new employees is critical. Only 52% receive cybersecurity policy training once a year.
14. The painful reality is that malware can successfully bypass anti-spam email filters, and are mostly ineffective against a targeted malware attack. It was reported that in 2018, malware attacks increased by 25 percent.

Evolving Security Threat Matrix
15. By 2021, cybercrimes will cost $6 trillion per year worldwide.
16. Cybersecurity spending is on the rise; reaching $96 billion in 2018.
17. Cryptojacking attacks are increasing by over 8000% as miners exploit the computing power of unsuspecting victims.
Don’t Become a Disaster Recovery Statistic
The good news is that with adequate planning, you can minimize the costs regarding time and lost sales that are associated with disaster recovery.
Backing up and securing your data and systems and having the capability to maintain business as usual in the face of a disaster is no longer a luxury, it is a necessity. Understanding how to put a disaster recovery plan in place is essential. Read our recent article on data breach statistics for 2020.
Recent Posts
Creating a Secure Website: Simple Guide to Website Security
Experts predicted that in 2019, business websites would fall prey to ransomware attacks at the rate of one site every 14 seconds.
In 2018, the damage to websites attacked by cyber criminal exceeded 5 billion dollars.
Every year, these attacks grow in size, and before you know it, it could be your website that is affected.
Why You Need To Keep Your Website Secure
Every website is potentially vulnerable to these attacks.
You need to keep yours safe. An unsecured site can be compromised. Your customer’s data might be stolen. This can lead to lost revenue, costly website coding repairs, and many other problems.
You can protect your website from hackers. We’ll start off with a few basic descriptions of the types of attacks that you might encounter. This is followed by the eleven tips to secure your website.

Potential Web Attacks/What To Prepare For
Whaling / Spear-Phishing
Phishing attacks are used to get people to give away their personal information, such as a social security number or bank account pin number. These attacks aim at broad audiences in hopes of fooling as many people as they can. Typically, phishing is done by email.
For example, a hacker sends out an email that looks like it comes from a bank, causing the recipient to click on the link in panic. That link takes the person to their standard looking banking site. But it is a site only designed to look like the real one. Someone who falls for one of these tricks and fills out the form on that site accidentally gives away their information.
Spear-phishing is similar, but it targets one specific person, not a lot of people in general. Hackers choose a particular target and then try to get them to give away their sensitive information.
Whaling is similar to spear-phishing. Only, in this case, a critical executive, at a company is targeted. That person is called a “whale” due to their influence and power. Hackers try to lure in whales, hoping to gain high-level access to company websites and bank accounts.
Server-Side Ransomware
Ransomware hits everyone from the average computer-user to those who operate websites.
These attacks consist of a hacker taking control of a computer and refusing to allow the user to access even the most basic commands. Server-side ransomware works similarly, except the hacker, gains control of a website server. Access to every website on that server is lost until the hackers are overridden or have their demands met.
IoT Vulnerabilities
IoT stands for Internet of Things. The term refers to the large number of devices that connect to the internet, such as smartphones and tablets that link to the internet and access sites.
The main IoT vulnerabilities are privacy issues, unreliable mobile interfaces, and inadequate mobile security. All of these stem from websites that don’t have the right protective measures installed or those that aren’t optimized for mobile devices. Hackers can take advantage of these issues and use them to gain access to your website.
Securing Your Website, The First Steps
Protecting your website from being hacked can be achieved in a simple 11 step process.
1. Use Secure Passwords
The best website security starts with a secure password. The backend (the developer side) of every website is password protected. Although it’s tempting to use an easy to remember password; don’t.
Instead, pick something that is extremely secure and tough for anyone but you to figure out. A good rule of thumb for passwords is to include a mix of capital letters, punctuation, and numbers, or use a strong password created by a password manager. Never use something that is easy to guess. This goes for everyone in your organization.
2. Be Careful When Opening Emails
Many phishing attacks appear in emails. Hackers also send viruses via email. Every one of your employees (including you) needs to be careful when opening emails from people you don’t know, especially if those emails have an attachment. Spam guards aren’t infallible. A hacker can compromise website security with a virus, wreaking havoc on your website.
Even attachments that are scanned and declared to be “clean” can still contain harmful viruses. Train your employees to use security precautions when opening emails with attachments.
3. Install Software Updates
Manufacturers keep operating systems and software running efficiently with regular updates. It can be tempting to push those updates aside to save time. After all, many of them require a complete system restart and some installation time which eats into productivity. This is a dangerous practice, as those updates contain crucial new security patches. You need to install these updates as they are available to keep your entire system secure.

4. Use a Secure Website Hosting Service
Your web hosting service plays a vital role in the security of every website under their jurisdiction. Choose yours wisely.
Before you build or move your site to a host, ask them about their security platform. The best hosts work with or hires experts in the internet security field. They understand the importance that their customer’s websites aren’t vulnerable to attack.
Make sure they include a backup option. You could lose valuable information due to a hacker. It is easier to rebuild your site from a backup than it is from scratch.
Managed options are also available, such as Security as a Service (Saas).
5. An SSL Certificate Keeps Information Protected
The letters in “https” stand for Hypertext Transfer Protocol Secure. Any webpage that uses this protocol is secure. Those pages exist on a specific server and are protected. Any page that contains a login or asks for payment information needs to be on this secure system. With that said, it is possible to set up your entire website using https.
Google has started marking sites in the Chrome browser as unsecured that do not use SSL Certificates or encrypt data.

6. Secure Folder Permissions
Websites consist of folders and files that contain every piece of information necessary to make your site work properly. All of these live on your web server. Without the right privacy protections and security measures, anyone with the right skills can get in and see this information.
Prevent this from happening by assigning security permissions to those files and folders. Go to your website’s file manager and change the file attributes.
In the section for “numeric values” set the permissions to these options:
- 644 for individual files
- 755 for files and directories
7. Run Regular Website Security Checks
A good security check can identify any potential issues with your website. Use a web monitoring service to automate this. You need to run a test on your site’s programming every week (at minimum). Monitoring services have programs that make this easy to do.
Once you receive the report, pay close attention to the findings. These are all of the vulnerabilities on your site. The report should contain details on them. It may even classify them according to threat level. Start with the most harmful and then fix these issues.
8. Update Website Platforms And Scripts
We already covered the importance of keeping your computer software up to date. The same is true of your web hosting platform, and your plugins and scripts, such as Javascript.
If you use Wordpress, ensure that you are running the most updated version. If you are not, then update your version by clicking on the button on the upper left side of the screen. It is imperative to keep a WordPress site current to avoid any potential threats.
For people who don’t use Wordpress, check your web hosts’ dashboard for updates. Many of them will let you know which version of their software you’re running and keep you informed of any security patches.
You also need to check your plugins and tools.
Most WordPress plugins are created by third-party companies (or individuals.) Although they are safe, for the most part, you are relying on those third parties to keep their security parameters up to date. Set aside time to check for plugin updates at least once a week, and keep an eye out for anything that may seem strange, such as a plugin that ceases to work correctly. This could be a sign that it’s compromised.

9. Install Security Plugins
There are several options here, depending on what type of website you run. For those based on WordPress, there are specific WordPress security plugins that provide additional protection. Examples include Bulletproof Security and iThemes Security. If your site is not on WordPress, protect it with a program like SiteLock.
Security plugins prevent hackers from infiltrating your site. Even the most up to date hosting platforms have some vulnerability. These plugins ensure that no one can take advantage of them.
SiteLock monitors your site continually looking for malware and viruses. It also closes those vulnerable loopholes, providing additional security updates.
10. Watch Out For XSS Attacks
XSS is cross-site scripting. An XSS attack is when a hacker inserts malicious code into your website, which can change its information or even steal user information. How do they get in? It’s as simple as adding some code in a blog comment.
Prevent XSS attacks by inserting a CSP header into your website code. CSP stands for Content Security Policy. It limits the amount of Javascript on your website, keeping foreign, and potentially contaminated scripts from running. Set it so that only the Javascript added to the page by your or your web developer works.
11. Beware of SQL Injection
SQL stands for Structured Query Language. It’s a type of code that manages and allows people to search for information in databases.
Here’s an example of an SQL Attack: if you have a search form on your website, people can enter terms to look for specific new information. Now imagine that someone got into your database files and inserted a code designed to mess them up.
That code can delete information and make it tough for the website to find what it needs to run. Hackers get in through URL parameters and web form fields and wreak havoc. Keep this from happening by setting up parameterized queries and make sure to create secure forms.

Now You Know How To Secure a Website from Hackers
Hopefully, now you understand the importance of creating a secure website. You also understand the eleven necessary steps to follow to prevent hackers from gaining access to its code and elements.
Leaving your website vulnerable to hackers can destroy your livelihood, especially if you run a web-based business. All that it takes is one lapse, and years of years client information can be compromised. This makes your company look bad and creates negative press attention. You’ll lose customers, many of whom may not come back.
Don’t allow this scenario to happen. Instead, focus on website security using the tips presented here.
Recent Posts
What is Cloud Computing in Simple Terms? Definition & Examples
Did you know that the monthly cost of running a basic web application was about $150,000 in 2000?
Cloud computing has brought it down to less than $1000 a month.Read more
What Is Cloud Security & What Are the Benefits?
When adopting cloud technology, security is one of the most critical issues.
Many Organizations still fear that their data is not secure in the cloud environment.
Companies want to apply the same level of security to their cloud systems as their internal resources. It is essential to understand and identify the challenges of outsourcing data protection in the cloud.
What is Cloud Security?
Cloud security is a set of control-based safeguards and technology protection designed to protect resources stored online from leakage, theft, or data loss.
Protection encompasses cloud infrastructure, applications, and data from threats. Security applications operate as software in the cloud using a Software as a Service (SaaS) model.
Topics that fall under the umbrella of security in the cloud include:
- Data center security
- Access control
- Threat prevention
- Threat detection
- Threat mitigation
- Redundancy
- Legal compliance
- Security policy
How Do You Manage Security in the Cloud?
Cloud service providers use a combination of methods to protect your data.
Firewalls are a mainstay of cloud architecture. Firewalls protect the perimeter of your network security and your end-users. Firewalls also safeguard traffic between different apps stored in the cloud.
Access controls protect data by allowing you to set access lists for different assets. For instance, you might allow specific employees application access, while restricting others. A general rule is to provide employees’ access to only the tools they need to do their job. By maintaining strict access control, you can keep critical documents from malicious insiders or hackers with stolen credentials.
Cloud providers take steps to protect data that’s in transit. Data Security methods include virtual private networks, encryption, or masking. Virtual private networks (VPNs) allow remote employees to connect to corporate networks. VPNs accommodate tablets and smartphones for remote access.
Data masking encrypts identifiable information, such as names. This maintains data integrity by keeping important information private. With data masking, a medical company can share data without violating HIPAA laws, for example.
Threat intelligence spots security threats and ranks them in order of importance. This feature helps you protect mission-critical assets from threats.
Disaster recovery is key to security since it helps you recover data that are lost or stolen.
While not a security component per se, your cloud services provider may need to comply with data storage regulations. Some countries require that data must be stored within their country. If your country has this requirement, you need to verify that a cloud provider has data centers in your country.
What are the Benefits of a Cloud Security System?
Now that you understand how cloud computing security operates, explore the ways it benefits your business.
Cloud-based security systems benefit your business through:
- Protecting your business from threats
- Guarding against internal threats
- Preventing data loss
Top threats to systems include malware, ransomware, and DDos.
Malware and Ransomware Breaches
Malware poses a severe threat to businesses.
Over 90 percent of malware comes via email. It is often so convincing that employees download malware without realizing it. Once downloaded, the malicious software installs itself on your network, where it may steal files or damage content.
Ransomware is a form of malware that hijacks your data and demands a financial ransom. Companies wind up paying the ransom because they need their data back.
Data redundancy provided by the cloud offers an alternative to paying ransom for your data. You can get back what was stolen with minimal service interruption.
Many cloud data security solutions identify malware and ransomware. Firewalls, spam filters, and identity management help with this. This keeps malicious email out of employee inboxes.
DDoS Protection
In a DDoS or distributed denial of service attack, your system is flooded with requests. Your website becomes slow to load until it crashes when the number of requests is too much to handle.
DDoS attacks come with serious side effects. Every minute your website is inaccessible, you lose money.
Half of the companies that suffer DDoS attacks lose $10,000 to $100,000. Many businesses suffer from reputation damage when customers lose faith in the brand. If confidential customer data is lost in a DDoS attack, you could face legal challenges.
Given the severity of these side effects, it’s no wonder that some companies close after DDoS attacks. Consider that one recent DDoS attack lasted for 12 days and you sense the importance of protection.
Cloud security services actively monitor the cloud to identify and defend against attacks. By alerting your cloud provider of the attack in real-time, they can take steps to secure your systems.
Threat Detection
Security for cloud computing provides advanced threat detection using endpoint scanning for threats at the device level. Endpoint scanning increases security for devices that access your network.
Computing Security Considerations Require Team Effort
Cloud partners offer clear advantages over in-house data storage. Economies of scale allow a cloud service to invest in the latest security solutions, such as machine learning. As cloud solutions are scalable, your business can purchase what you need with the ability to upgrade at any time.
Now that you know what cloud security is, you have a better understanding of how service providers keep your big data safe.
Remember, a strong security policy should outline what strategies the service uses. You should ask questions to compare and ensure that you are protecting your critical business resources.
Recent Posts
What Is Cloud Monitoring? Benefits and Best Practices
Cloud monitoring is a suite of tools and processes that reviews and monitors cloud computing resources for optimal workflow.
Manual or automated monitoring and management techniques ensure the availability and performance of websites, servers, applications, and other cloud infrastructure. Continually evaluating resources levels, server response times, speed, availability, and predicts potential vulnerability future issues before they arise.
Cloud Monitoring Strategy As An Expansion of Infrastructure
Web servers and networks have continued to become more complicated. Companies found themselves needing a better way to monitor their resources.
Cloud monitoring tools were developed to keep track of things like hard drive usage, switch, and router efficiency, and processor/RAM performance. These are all excellent, and vulnerabilities. But many of these management tools fall short of the needs for cloud computing.
Another similar toolset, often used by network administrators, is configuration management. This includes user controls like group policies and security protocols such as firewalls and/or two-factor authentication. These work based on a preconfigured system, which is built on anticipated use and threats. However, when a problem occurs, these can be slow to respond. The issue must first be detected, the policy adjusted, then the change implemented. A delayed response time of manually logging and reviewing can bog this process down even further.
A cloud monitor uses the advantages of virtualization to overcome many of these challenges. Most cloud functions run as software in a constructed virtual environments. Because of this, monitoring and managing applications can be built into the fabric of that environment; including resource cloud management and security.
The Structure of Cloud Monitoring Solutions
Consider the growing range of SaaS services such as Software, Platform, and Infrastructure. Each of these services runs in a virtual server space in the cloud. For example; Security as a Service lives in a hosted cloud space in a data center. Users remotely connect over the internet. In the case of cloud platform services, an entire virtual server is created in the cloud. A virtual server might span across several real-world servers and hard-drives, but it can host hundreds of individual virtual computers for users to connect to.
As these services exist in a secure environment, there is a layer of insulation between the real-world monitoring and cloud-based monitoring.
Just as a network monitoring application is capable of being installed on a Local Area Network (LAN) to watch network traffic, monitoring software can be deployed within the cloud environment. Instead of examining hard drives or network switches, monitoring apps in the cloud track resources across multiple devices and locations.
One important feature of cloud server monitoring is that it provides more access and reporting ability than traditional infrastructure monitors.
Types of Cloud-Based Monitoring of Servers & Their Benefits
Website: A website is a set of files stored on a computer, which in turn sends those files to other computers over a network.
The host can be a local computer on your network, or remotely hosted by a cloud services provider. Some of the essential metrics for website monitoring include traffic, availability, and resource usage. For managing a website as a business asset, other parameters include user experience, search availability, and time on page. There are several ways this monitoring can be implemented and acted on. A monitoring solution that tracks visitors might indicate that the “time on page” metric is low, suggesting a need for more useful content. A sudden spike in traffic could mean a cyber attack. Having this data available in real-time helps a business adjust its strategy to serve customer needs better.
A virtual machine is a simulation of a computer, within a computer. This is often scaled out in Infrastructure as a Service (IaaS), where a virtual server hosts several virtual desktops for users to connect to. A monitoring application can track users and traffic, as well as infrastructure and the status of each machine. This offers the benefits of traditional IT infrastructure monitoring, with the added benefits of additional cloud monitoring solutions. From a management perspective, tracking employee productivity and resource allocation can be important metrics for virtual machines.
Database Monitoring: Many cloud applications rely on databases, such as the popular SQL server database. In addition to the previous benefits, a database monitor can also track queries and data integrity. It can also help to monitor connections to the database to show real-time usage data. Tracking database access requests can also help improve security. For example, resource usage and responsiveness can show if there’s a need for upgraded equipment. Even a simple uptime detector can be useful if your database has a history of instability. Knowing the precise moment a database goes down can improve resolution response time.
Virtual Network: This technology creates software versions of network tech, such as routers, firewalls, and load balancers. As they are designed with software, integrated tools to monitor can give you a wealth of data about their operation. For example, if one virtual router is continuously overwhelmed with traffic, the network can be adjusted to compensate. Instead of replacing hardware, virtualization infrastructure easily adapts to optimize the flow of data. Also, monitoring tools analyze user behavior to detect and resolve intrusions or inefficiencies.
Cloud Storage: Secure cloud storage combines multiple storage devices into a single virtual storage space.
Cloud computing monitoring track multiple analytics simultaneously. More than that, cloud storage is often used to host SaaS and IaaS solutions. In these applications, it can be configured to track performance metrics, processes, users, databases, and available storage. This data is used to focus on features that users find helpful or to fix bugs that disrupt functionality.

Best Practices For Monitoring
Decide what metrics are most critical. There are many customizable cloud monitoring solutions. Take an inventory of the assets you are using. Then map out the data you would like to collect. This helps to make informed decisions about which cloud monitoring software best fits your needs. It also gives you an advantage when moving to implement a monitoring plan. For example, an application developer might want to know which features are used the most, or the least. As they update, they may scrap features that aren’t popular in favor of features that are. Or, they may use application performance monitoring to make sure they have a good user experience.
Automate the monitoring. One compelling feature is scripting. Monitoring and reporting can be scripted to run automatically. Since cloud functions are virtual, it’s easy to implement software monitoring into the fabric of the cloud application. Even logging and red-flag events can be automated to send a notice when problems are detected. For example, an email notification might be sent if unauthorized access is detected or if resource usage exceeds a threshold.
Consider the security of cloud-based applications. Many users believe that their data is less secure on a remote cloud server than on a local device. While it is true that data centers present a tempting target for hackers, they also have better resources. Modern data centers invest in top-tier security technology and personnel. This offers a significant advantage over end users. With that said, it’s still crucial for cloud users to be mindful of cloud security.
While data centers offer protection for the hardware and infrastructure, it’s important to exercise good end-user security habits. Proper data security protocols like two-factor authentication and strong firewalls are a good start. Monitoring can supplement that first line of defense by tracking usage within the virtual space. This helps detect vulnerabilities by reporting habits that might create security gaps. It also helps by recognizing unusual behavior patterns, which can identify and resolve data breach.

Final Thoughts: Cloud Based Monitoring
With the virtual nature of cloud computing management, infrastructure is already in place for cloud monitoring applications. For a reasonable up-front investment of time and money, monitoring applications can deliver a wealth of actionable data. This data gives businesses insight into which digital strategies are more effective than others. It can identify costly and ineffective services as well.
It is worth looking at application monitoring to report on how your cloud resources are being used. There may be room for improvement.
Recent Posts
Business Continuity vs Disaster Recovery: What’s The Difference?
The terms Business Continuity and Disaster Recovery are not interchangeable though many seem to think otherwise. Disaster Recovery (DR) versus Business Continuity (BC) are two entirely different strategies, each of which plays a significant aspect in safeguarding business operations.
When it comes to protecting your data, it is critical to understand the differences and plan ahead. Those differences arise from both usage and application after a catastrophe strikes.
Business continuity consists of a plan of action. It ensures that regular business will continue even during a disaster.
Disaster recovery is a subset of business continuity planning.
Disaster recovery plans involve restoring vital support systems. Those systems are mostly communications, hardware, and IT assets. Disaster recovery aims to minimize business downtime and focuses on getting technical operations back to normal in the shortest time possible.

Business Continuity Has a Wider Scope
Business Continuity management refers to the processes and procedures that associates take to make sure that regular business operations continue during a disaster.
It can mean the difference between survival and total shutdown. It is based on a relentless analysis and isolation of critical business processes.
One of the key benefits is the focus on business processes. You assess what you must do in the event of a disaster. You articulate benefits versus cost. This is just solid data management, even if catastrophe never occurs.
So, you have already decided which business functions are critical. You have flagged what can be suspended until you fully recover. You have a priority list.
For example, would you concentrate on active customers only? What are your priorities for supply and warehouse management?
Federal and state laws require formal disaster recovery planning.
For example, financial enterprises must have a business continuity plan. The healthcare industry must comply with HIPAA requirements.
With business continuity planning, you have earmarked your resources.
Those resources support your most essential functions. They include any support equipment, software, and stock required to move forward. You manage that stock by keeping your inventory current. You rotate consumable supplies through your emergency stock.
Moreover, you have identified your key staff people. They know what they must do and when they must do it. For every job there is to do, someone must be designated to do it. The designated “doers” must be qualified to carry on the business in the event of a disaster. So, the plan has to include practice and update of the plan as necessary.
The plan must also focus on customers and the supply chain. Suppliers must know that their payment invoices are in the pipeline and ready for payment. Customers must be confident that their orders will be filled or only temporarily delayed, perhaps with a discount premium.
Finally, your BC plan must include a process to replace and recover your IT systems. That contains valuable business data. For example, is your network designed for data backup and recovery?
Failover is where a secondary system kicks in when the first one goes down. How much will it cost you to replace storm-ruined hardware?
Disaster Recovery Plan
Disaster recovery is a subspace of total business continuity planning. A DR plan includes getting systems up and running following a disaster.
IT disasters can range from small hardware failures to massive security breaches.
The statistics on companies that suffer an IT disaster are incredible.
93 percent will file for bankruptcy within one year. Of that 93 percent, 60 percent can expect to shut down within six months. A complete system crash and loss of data is like the aftermath of a burglary. You don’t know what is missing until you go looking for it.
One contributing cause in those business failures is the lack of a written plan. The plan should include a business impact analysis. Many businesses write the plan, but neglect to update it, at least annually. For example, when the natural disaster Hurricane Harvey caused unexpected inland flooding in Houston. Many businesses were quickly inundated as people struggled to evacuate.
Infrastructure technology-related planning failures also include a lack of recovery and business continuity procedural guides. How do you methodically restore each critical application in your IT structure? How long will it take to restore your system by way of backups? What is your restore-point tolerance? A restore point is a time between your last cloud backup and when your system went down.
Finally, if no single person is responsible for data recovery preparedness, how can it occur? That person has to have the authority to work across the organization.

Don’t rely on business insurance
A business insurance policy may only cover loss or damage to your inventory and equipment.
Even if your organization survives a disaster, without effective planning, you will face the following losses:
- Financial: Lost profits, a lower market share, government fines because of data breaches. HIPAA fines, for example, have amounted to multi-millions.
- Damage to your reputation, brand through negative publicity.
- Sanctions: Loss of your business license, or legal liability. You could lose time and money even if you win the lawsuit.
- Breach of contract: Your inability to meet your obligations to clients. Includes a ripple effect up and down your supply chain. This could even drive some of your suppliers and customers out of business.
- Dead in the water: Stalled or frozen business objectives and plans, missed market opportunities.
Bottom Line: Recovery and Business Continuity
The difference between business continuity and disaster recovery is quite specific.
Business continuity planning is a strategy. It ensures continuity of operations with minimal service outage or downtime. A business disaster recovery plan can restore data and critical applications in the event your systems are destroyed when disaster strikes.
Balancing two planning strategies is a matter of priorities. If the majority of your business transactions are online, you need to make data protection your number one concern. Losing all or some of your data could halt your operations. You could not bill customers, pay vendors, or access your inventory information. Your competitive intelligence would disappear.
You need to know how long you can wait to get back to full operation before the pain starts. You also must weigh that delay against the costs of planning and execution. Fortunately, reliable managed services providers and consultants know how to do that. They can address your concerns in a cost-effective and compliant manner.
Looking for a business continuity recovery plan example?
Recent Posts
Start a Cyber Security Awareness Training Program Your Staff Can't Ignore
Corporate cybersecurity is a mindset as much as it is a strategy.
According to Verizon’s 2018 Data Breach Investigations Report, internal actors still account for an alarming number of data breaches. Last year, 28% of attacks involved insiders.
Although adequate security systems are vital, these findings point to the importance of educating employees on cybersecurity best practices. To efficiently protect their data, organizations need to develop a security culture throughout the company. The best way to do so is to introduce relevant, engaging, and regular security training for employees.
For those who tried to do so but failed and for those who are not sure how to start, we asked top cybersecurity experts for their best advice. Take a look at what they said and start implementing their tips today.
- Jef Towle, Intel Corporation
- James Olivier, Shades of Security
- Lisa Parcella, Security Innovation
- Lauren Hilinski, Shred Nations
- Robert Douglas, PlanetMagpie IT Consulting
- Wade Yeaman, Fluid IT services
- Neil Readshaw, Anonyme Labs
- Greg Scott, Author
- Mihai Corbuleac, ComputerSupport
- Sean Spicer, AgileIT
- Derek Anderson, Biztek Solutions, Inc.
- Joshua Crumbaugh, PeopleSec, LLC
- Eyal Benishti, IRONSCALES
- James Goepel, ClearArmor Corporation
- Tom Evans, Ashton Technology Solutions
- Morey Haber, BeyondTrust
- Dean Coclin, DigiCert
- Peter J. Canavan, Safety Expert
- Robert Huber, Eastwind Networks
- Benjamin Dynkin, Atlas Cybersecurity
- Eric Sheridan, WhiteHat Security
- Mike Meikle, SecureHIM
- Bryan Dykstra, Atlantic Data Forensics
- Joshua Feinberg, Data Center Sales & Marketing Institute
- Larry Kahm, Heliotropic Systems, Inc.
- Tom DeSot, Digital Defence, Inc.
- Kevin Gray, EnvisionIT Solutions
- Justin Lavelle, BeenVerified
- John C. Ahlberg, Waident Technology Solutions
- Robert Siciliano, HotSpot Shield
- Amanda Bigley, Hummingbird Networks
- Isaac Kohen, Teramind
Cyber Security Awareness Training, Advice From Industry Experts

Jeff Towle
Sr. Cloud Solution Security Architect, Intel Corporation
Jeff Towle is an industry veteran in the Information Security, Governance, Risk and Compliance industries. At Intel, Mr. Towle specializes in optimizing Intel-based security designs to contend with modern-day threat vectors for Cloud Service Providers.
Mindfulness with safeguarding your Identity
An employees’ Corporate Identity is THE critical component to safeguarding all valuable top secret or highly classified documents, customer records, Intellectual Property, or design secrets. Hackers will go to great lengths to trick employees/end-users to steal their access credentials. This goes way beyond just making sure you update your password with strong alpha-numeric characters regularly per corporate password reset policy. A good rule of thumb is to treat all the files, folders, documents, social media, corporate websites you have been granted access to as would your own bank account. Sharing your corporate ID is never a good idea, even under temporary circumstances. It’s also a good idea from time to time to check with IT to see what exactly you have access to. Especially if you have been at the company for a long time. Do you want access to systems you used 5 years ago? This only creates risk, and it’s OK to ask for a list of things you still may be able to access and request that access be removed.
Attribution of all Business Communications
What is attribution? Simply put, “Do I REALLY know who sent this message to me? It’s important to train yourself to get into the habit of verifying the author or creator of a digital communication to you (via email, text, social media, automated message, website alert/notification, etc.). This is an awareness technique that’s easy to adopt once you start to just ask the question. With email, you can double-click on a name or hover your mouse on the From: field, and it will resolve to the actual email address. SPAM, Phishing attacks and Malicious Ransomware messages often resolve to a string of characters that are easily seen as suspicious. If the email doesn’t end in “companyname.com” you likely are being subjected to some sort of deceptive communication. The same is true of malicious URL’s. Instead of clicking on the link to find out what it resolves to, hover your mouse or right click to see what the whole string looks like. These changes in behavior can really make a difference beyond just updating antivirus, OS patching, and firewall security controls.
Cyber Attitude
You can be your own best anti-hacking expert with these simple tips:
- Don’t leave your laptop or desktop alone with applications open. Make sure to have a password enabled screen saver activated any time you leave your workstation
- Don’t tailgate. Remember your Identity is critical, and this is true of your employee access badge. It’s only meant to let you into the building, parking lot or server room. Make sure you don’t just let people follow you as a matter of courtesy or convenience.
- Hackers love social engineering. They will call and posture as a co-worker or service agent. They can be very crafty about piecing together information to hack into systems or break or sneak into a building. So beware of those asking questions about scheduling and where people will be at what time. Safeguard information around people’s system access just like you do your own.
- Don’t even read it, delete it. And the worst thing you can do is forward it to others.
- Make sure you have a backup of your laptop or workstation’s data. Ask the IT staff if your data is being backed up regularly. This may be the only way to recover from severe ransomware attacks.
- Believe it or not, you can become a frontline defense security expert to assess whether any application or system you access is vulnerable to some attack. Pay attention to irregular content that’s posted, the amount of time it takes to process information on systems or any strange errors reported in a business process flow. Hackers rely on a lack of incident response planning to have their malware spread and escalate access to damage or steal data so the sooner your report something that is not normal, the better.

James Olivier
Principal Cybersecurity Consultant, Shades of Gray Security
James Chad Olivier, author of Trust Me I’m Lying: Banks Pay Me to Rob Them is the owner and Principal Cybersecurity Consultant of Shades of Gray Security.
Make Your Security Training Program More Personal
Training is much more effective following a social engineering test. If you can show them how you tricked them into letting you into the facility, the success statistics of a spear phishing attack, and/or the success of phone call social engineering, it leaves a big impact. Especially on the ones that know they were tricked. I never reveal who was to blame as I explain the test is not a witch hunt, but an awareness exercise.
I use colorful stories from my past exploits to make the lessons more enjoyable. They have just seen one example of a test, so I tell them some other ways an attacker might exploit them. My style is to lighten the mood and tell them from my perspective which makes it more cinematic in their mind. Like a good suspense thriller. Their responses range from amusement to frightened out how easy it is to con people. When I visit them for the next training (often a year later), my clients remember the old tales and tell me how they have seen similar things during that time, and are excited to learn some new stories. This keeps them much more attentive than just a boring statement of policy and procedures.
I don’t make it just about the company. I tell people about how they are tricked personally. How to avoid scams, credit card protection (how to avoid skimmers), and encourage them to share the material with their friends in family. I explain that if we can make ourselves safe, it is better for our employer, our family, and society in general.
If nothing else, no one wants a boring recitation of policy, procedures, and best practices. Liven it up, don’t speak in a monotone voice, and don’t just read bullet points. That applies to any presentation though.
Lisa Parcella
VP of Product Management & Marketing, Security Innovation
Lisa Parcella designs and delivers comprehensive security-focused products and educational solutions for Security Innovation’s diverse client base.
Training Should Engage Staff
Training needs to be engaging to build internal expertise and competency. Here are four ways to keep cybersecurity training exciting for employees:
- Keep it Interactive: Leverage multiple types of interactions to keep learners engaged. Hands-on simulations/real-world training and tabletop exercises are influential in building offensive and defensive cybersecurity skills and help assess an organization’s situational preparedness. This supplemented with computer-based training, and reinforcement assets are effective in reinforcing lessons learned.
- Groom security champions: It’s much easier to get staff to jump on the security bandwagon if one of their own is driving the adoption versus having it come down as a “must-do” from high-level management.
- Motivate with incentives: From simple recognition to formal awards, incentive programs like belts, certificates, spot bonuses, gift cards, etc. help to facilitate progression and motivate employees to want to learn more. Role-Based: Security is a shared organizational responsibility, and there are many stakeholders including general staff, infrastructure, cloud, and development teams, and managers that need to write policy and ensure adherence to compliance and other mandates. Progressive topic-driven modules customized for specific roles are useful in building the required cybersecurity skills.

Lauren Hilinski
Digital Marketing Specialist, Shred Nations
Lauren’s company partners with document shredders across the nation and aim to make it easy to keep private business and personal information safe.
Use Real-Life Scenarios in Awareness Training
- Create consequences. If you are implementing new cybersecurity rules, create consequences for following or not following them. Whether its a reward or special monthly recognition, or if its some kind of punishment for not following your new security rules, give your employees a reason to get engaged.
- Use examples from real life cases. Yahoo, Blue Cross Blue Shield, Equifax and other large organizations have experienced devastating data breaches. Bring these cases to life with numbers and data proving the seriousness of the topic and showing that it can happen to the most sophisticated systems.
- People don’t like change, so if you are implementing new rules make sure to explain *why*, in simple terms that your employees will understand. You know your team better than anyone, explain the information in a way that makes them understand why behavior needs to change, so that even if they don’t like the changes, they understand that they are important.
- Make the information relevant. Too often these types of presentations aren’t industry specific and seem out of touch with what your employees do every day. Bring the information down to their level so that it is at the very least relevant.

Robert Douglas
President, PlanetMagpie IT Consulting
Robert has worked in the IT industry for 30+ years, consulting on everything from network infrastructure to cybersecurity.
Build each training session around a theme
- Basic email security. Never click on an email link or attachment you are not expecting. Email is the #1 delivery method for malware & ransomware. 60% of all successful hacks occur because of one person’s mistaken click.
- Never use personal email for work. Consumer email does not have business-grade security, backup & compliance features, and all of your emails could become discoverable in a lawsuit.
- Use complex passwords! Store your passwords in password management software and not on sticky notes attached to your monitor! (Begging you here.)

Wade Yeaman
Founder and CEO, Fluid IT Services
Founder and CEO of Fluid IT Services has more than twenty years of experience including leadership and operational responsibility for functions related to both business and information technology.
Use Current Events To Resonate
- Make the training engaging by using real-life scenarios. For example, drop a USB drive in the audience before the training and then during the class ask if anyone found it. Once they respond, ask them what they would do with it. The typical answer is ‘plug it into my computer to see what is on it.’ This is a great tool to show how social engineering works on the human gullibility to infect a machine and an organization.
- Make it relevant and use actual examples from recent current events. Technology is already complicated for non-technical employees to understand, the language is foreign, and most technology professionals are not proficient at translating critical technical terms into easy to understand and relevant business terms. Using actual present-day examples not only makes bridging the gap easier, but it also engages the audience in ways relevant to their experiences. One way is to show real examples of malicious emails and point to specific objects and pieces of information within each email that makes them illegitimate. I always include examples from the past 2-3 weeks to demonstrate what is happening now and also to show the importance of always being diligent.
- Make the presentation fun. This is probably one of the most challenging aspects of the training because nothing about cybersecurity is fun, but mixing in more light-hearted material, such as videos (from The Jimmy Kimmel Show in my example), change up the monotony of delivery and make use of humor to get the points across on serious topics.
- Make it collaborative. Many in the audience may be there because they were forced to, but there are always those wanting to learn and participate. Know the industry and business of your audience and ask them questions related to their specific industry, operational area, and even job type. Throughout ask what they have experienced and what they did about it. Include examples of real security incidents, breaches, ransomware and how those companies dealt with it and recovered. Understanding the amount of time, effort and money expended to recover from an incident is often hidden from employees is very eye-opening. Making cybersecurity ‘real’ will leave everyone more aware of the actual risks they will encounter both professionally and personally.
Neil Readshaw
Chief Security Officer, Anonyome Labs
Neil Readshaw is a seasoned security and compliance executive, who spent over 20 years at IBM overseeing technical direction for security architecture, leading the security workstream for the IBM Cloud Computing Reference Architecture, and programming new global data security products.
Context is the most critical aspect of security awareness training
Context means a few things to me:
– Why it matters to our company, not just generic statements about risk management.
– When the message is relevant to the employees.
– For whom the message matters most, i.e., vary the training content or its delivery by job role, as much as is practical.
Here are some examples of how we train employees:
I try and spend some time with each new employee to reinforce our security culture from the beginning. I hope that also helps the new hires see that my team is approachable and helpful. I also get a benefit from this, as I can learn what the security environment was like at their previous company. It is a great way to get new ideas and challenge the ones with which I am currently comfortable. And it is the right way for new hires from the get-go to understand the robust security and data protection culture we have at Anonyome, and thus what will be expected of them.32. Teaching employees how to detect a phishing email is very important, especially as the mailbox is so often the key to password recovery/password reset for other services.
What has been most impactful is showing people real phishing emails that have been received by our employees, as opposed to boilerplate examples. I try and share these examples through our intranet platforms as they happen, to try and capitalize when other employees may be receiving similar phishes.
For the developers in our company, security about our internal assets, but also how we build and operate systems for our products. The unfortunate data breach at Equifax became relevant for our product teams when they understood that the issues at Equifax were due to old, unpatched software. That was a reminder of why we have procedures around patching systems and keeping our use of open source software components up to date.
We keep formal, recurrent security training to a minimum to avoid cyber safety burnout from employees. However, we regularly check in with key account and data owners to ensure compliance and processes are being adhered to and of course answer any questions employees have.

Greg Scott
Author of Bullseye Breach: Anatomy of an Electronic Break-In
Greg Scott is a veteran of the tumultuous IT industry. Greg started Scott Consulting in 1994 and Infrasupport Corporation in 1999. In late summer, 2015, after Bullseye Breach was published, he accepted a job offer with a large, open source software company.
- Keep it simple. Start with care and share to be prepared and expand from there. You have to make the case it is worth their time to care about cyber-security. Once you have made that case, persuade them to share what they learn.
- Make this happen by relating every concept you teach to real-world scenarios, ideally with stories that have protagonists, antagonists, conflict, and high stakes.
- Entertain. Boredom leads to apathy, which is your worst enemy.

Mihai Corbuleac
Senior IT Consultant, ComputerSupport
I am Mihai Corbuleac, Senior IT Consultant at ComputerSupport.com – IT support company providing professional IT support, cloud and information security services.
Start sessions with relevant and scary cybersecurity statistics.
Facts like 46% of entry-level employees don’t know if their company has a cybersecurity policy or the fact that ransomware threats increased by 36% in 2018 or that 1 in 130 emails contains malware etc. It’s important for people to understand the risks of not being informed and educated regarding cybersecurity.
Secondly, always emphasize how destructive lack of knowledge and negligence could be. Finally, don’t forget to mention that most cyber-attacks could have been prevented if specific protocols would have been followed and that due diligence and staying alert represents the state of normality in today’s cybersecurity.

Sean Spicer
Director of Inbound Marketing, AgileIT
Sean Spicer is a 17-year digital marketing veteran who studied Marketing at U.C. Berkeley and earned a computer science certificate from Harvard.
The biggest issue with any security awareness training program is that the people most qualified to teach it are the same ones who are most liable to talk above their audience’s skill level.
While many of the issues in online security are fascinating, it is easy to lose the attention of your team if you get too detailed.
- Keep it fun. Roleplaying phishing scenarios, talking through real work attacks, watching the Pwn videos from Rapid 7 that detail some of the ways they have successfully breached client’s security are all fun ways to engage the audience.
- Keep it actionable. Knowing the dangers of ransomware and identity theft is useless if your team members do not know what to do if they are suspicious of something. Have a point contact or shared email box where they can forward suspicious links.
- Do not victimize, or make examples out of your team. Phishing test exercises are a valuable tool to demonstrate vulnerabilities. However, your most vulnerable employees can feel victimized if they are publicly outed or shamed, which leads to a loss of engagement with the training. Instead of highlighting who failed the assessment, highlight who did the right thing, by forwarding the emails to IT or reporting an unsuccessful penetration testing attempt.
- Be consistent. Complacency is the biggest threat to security, no matter if it is physical security or computer security. Keep your staff up to date on new developments and tools, and make sure to run assessments and micro-training at regular intervals to keep your team vested in the process, and aware of new and emerging threats.

Cyber Security training should be personable and relatable
- Speak to the employees and how they can secure themselves in their personal lives, not just company policies. This gives them more buy-in and reason to pay attention as you are now delivering them value on what they can do to protect themselves and then translate that into how the same principles apply to the organization. I always give my audience a handful of tips they can use personally first, then move on to company policies and then connect the two. It comes back to the old what’s in it for me? If companies just speak about how employees should protect their business, there is less interest, but if you give them personable tools and tips that also relate to the business, you will find greater success.
- Find engaging content. Videos are best in this day in age. I use videos that demonstrate how easy it is for criminals to hack and gain access to personal information. The videos need to be entertaining not lecturing.
- Get out of the classroom/meeting room and get hands-on. We provide a service (and several companies do) that provide real-life employee awareness training that involves sending fake malicious phishing emails to our clients’ staff. The emails do no harm, but replicate what actual bad emails do. When employees fall for our emails, they are kindly told that they failed and need to watch a video on what key points they missed. We provide owners and management reports on their companies phish prone score which gets improved quickly (30 days) with testing and sending these emails and watching the videos. This becomes more random and on-demand training that can be as little as 1 minute to 15 minutes but is consistently ongoing and raising awareness amongst the team.

Joshua Crumbaugh
Chief Hacker at PeopleSec, LLC
Joshua Crumbaugh is one of the world’s leading security awareness experts and internationally-renowned cybersecurity speaker. He is the developer of the Human Security Assurance Maturity Model (HumanSAMM) and Chief Hacker at PeopleSec.
- Shorten the length of training sessions to under 1 minute to accommodate short attention spans.
- Simplify messaging to its bare essentials and do not cover more than one topic in a single security awareness program.
- Phish users on a weekly basis.
- Capitalize on just-in-time training by educating at the moment a mistake is realized.
- Anchor lessons in emotion.

Eyal Benishti
Founder & CEO, IRONSCALES
Eyal Benishti is a veteran malware researcher and founder and CEO of IRONSCALES, the world’s first automatic phishing prevention, detection and response platform.
Most cybersecurity security awareness training conducted for employees is related to email phishing, specifically providing tips and tricks for how business workers can better identify a malicious email. In theory, this is a sound investment. With nine out of ten attacks beginning with phishing, there is a human vulnerability that needs to be addressed.
The challenge is that today’s attacks are so sophisticated and complex that even hyper-phishing aware employees cannot identify them. As an example, 1 in 3 workers in the utility industry in Michigan recently opened a fake phishing email even though those people are mandated to go through security training. In fact, Verizon estimates that only 17 percent of phishing attacks get reported.
So what should companies do?
For starters, if they are going to invest in phishing training, then they should adopt tools that are gamified and tailored to each user’s specific level of awareness. This method is proven to keep people’s attention spans longer and help trigger information retention. Secondly, and most importantly, organizations must realize that humans alone – no matter how much training – can never be relied upon as an actual security safeguard. Instead, companies should look for ways to have humans and machines work together in layers so that when one misses an attack, the other has its back. In this scenario, each time there is an attack, both the human firewall and the machine get a little smarter, further reducing the risk of future phishing emails being successful.

James Goepel
James Goepel, Vice President, General Counsel, and Chief Technology Officer at ClearArmor Corporation
Improving cybersecurity awareness requires cultural changes
Employees need to better appreciate the potential business impacts of their actions, and they need to be held accountable. Until that happens, training is just something employees have to suffer through, rather than being something they understand they need to do. Accountability does not mean the company focuses on punishing those who do not comply. It can also reward those who do.
This can be achieved, for example, through gamification, with employees who do comply receiving positive rewards, such as Starbucks or Panera gift cards if they achieve and maintain certain scores. These kinds of positive reinforcements help move security from being an afterthought to the forefront of employees’ minds, which in turn helps security become part of the culture.

Tom Evans
Over 35 years in IT. Cyber security awareness training for employees is a part-time occupation now that I am retired. End-user support and dealing with security issues occupied most of my working career.
- Actually do training. Even boring training is better than no training. If you do not have the resources in-house, seek outside sources. There are many.
- People enjoy videos these days. There are lots of them out there that help emphasize the severity of the issues. Believe or not NOVA (PBS) has some excellent ones on YouTube. Cisco and others have videos that can be used in training.
- I give out candy when someone answers a question posed to the group. it is not a lot but it gets people involved.
- Once a year is not enough. You cannot train one time and expect people to remember everything. The threat landscape continues to change and training needs to evolve to keep up.

Morey Haber
CTO, BeyondTrust
With more than 20 years of IT industry experience and author of Privileged Attack Vectors, Mr. Haber joined BeyondTrust in 2012 as a part of the eEye Digital Security acquisition. He currently oversees BeyondTrust technology for both vulnerability and privileged access management solutions.
Test The Effectiveness Of Your Staff Training
- Make it interactive. Whether the training is online or in a classroom, it must be interactive and engaging. Watching videos, hours of powerpoint, or even mindless cartoons does not work. Any training, regardless of media, must require the end user to engage the instructor, scenarios on the screen, and provide feedback. Making it fun is important but making it positively interactive is critical.
- Make it real-world. Too often training is based on what-if use cases. If you click on this link, if you open this email, if you share your password, etc. this will happen. While these are informative, good cybersecurity training includes real-world examples from other companies (or from within your own) of people doing bad things and the real-world ramifications. If it included the public details from Uber, Equifax, Ashley Madison, Delta, etc. – then employees can relate better to their own experiences.
- Include role-playing and testing. Employees will learn best if they are placed in actual situations that reinforce what they just learned. While standard role-playing is good, testing and cybersecurity certification are required. There is no reason that security teams should stop there. They should perform a light-hearted pen test after training. This could sample phishing emails; a few loosely dropped USB thumb drives or even fake phone calls. People always remember training best when tested with real-world role-playing and testing.
- Do not do it in isolation. Any staff security awareness and training should not be from a person’s desk. It should have dedicated time and location even if it requires them to use their own laptop. There are too many distractions.
Dean Coclin
Senior Director of Business Development, DigiCert
Dean Coclin has more than 30 years of business development and product management experience in cybersecurity, software, and telecommunications.
More useful than training videos are actual tests or exercises.
For example, a phishing exercise where employees are sent random phishing emails to see if they click on links or attachments provides valuable feedback to both the IT department and the employees. A contest amongst employees to see who can spot the most phishing emails (by forwarding them to an alias) puts some friendly competition into the mix while providing a valuable exercise. Rewards can be simple gift cards or a more complex points program which can be redeemed for prizes. Similar activities can target mobile devices or laptops by asking employees to download unauthorized software.

Peter J. Canavan
- Social engineering attacks are the most insidious. You must educate and train your employees on what phishing attack emails may look like including official-looking logos, a sense of urgency, the need to wire funds or check account or package tracking information immediately. By hovering over the links in a message and noting the URL that appears, many of these phishing attacks can be thwarted. When in doubt, look up the company’s phone number or customer support email on your own and do not rely on the contact information in the email to ascertain validity. However, more and more various websites are hacked, and code installed on them that the site owner is unaware of. Just visiting a compromised site can allow malware to get into your systems.
- A great exercise is to have your employees try to spot fake vs. valid emails and to make a game out of it. Divide employees into teams, and then have them mark which emails are legitimate and which are not. The winning team gets a prize (lunch, leave work early, PTO time, etc.)
- Passwords are one of the easiest places to gain entry into a system. Stress the need for strong password security. Use passwords that are LONGER and not necessarily complex. Any password that is 12 characters or longer is almost uncrackable. It would take too much time for a computer/hacker to crack it. Teach them to use easy to use phrases as passwords such as turning vacation time in Aruba into Vaca710n71m31nAruba! which makes an easy-to-remember phrase into a super strong 20 character password.
- Drill into your employees the need to be vigilant and not complacent. Just because they (or your company) have not been hacked before, does not mean it cannot happen. A recent survey by the National Small Business Association found that 50% of businesses they surveyed had reported being victims of cyber attacks, and 3 out of 4 were small businesses with less than 250 employees. The average cost of a cyber attack is around $21,000, and within six months, 60% of those attacked go out of business. Let your employees know that if they want job security, they need to help contribute to your company’s security!
- The apparent need for a robust and centrally managed antivirus solution on all your servers and workstations is a must. Besides, your router’s firewall must be hardened by an expert who knows exactly what the best practices are. Having a solution that combines the two is an excellent option for small businesses.

Robert Huber
Robert Huber, CSO, Eastwind Networks
Eastwind Networks is a cloud-based breach analytics solution that aims to protect government agencies and enterprise organizations from cyber threats that bypass traditional security measures.
- Ensure cybersecurity is a part of every employee’s performance goals.
- Gamify the security awareness training program, so there are points amassed, a leaderboard or prizes.
- Ensure the situations reflect real-life concerns of the enterprise. Rather than using generic scenarios, show how a loss of control, loss of personal information, loss of client sensitive information, intellectual property or similar related to the business affects the bottom line, company profits, reputation, stock price, etc.

Benjamin Dynkin
Benjamin is a cybersecurity attorney specializing in helping businesses understand, manage, and mitigate their cyber risk. He has published extensively and has been featured in a TEDx on cybersecurity and cyberwarfare.
Information security awareness requires hardening the human element
While there are countless strategies for making a data security program useful, to transform a compliance checkbox into a strong security posture.
- Security Awareness training should be a constant presence in the lives of employees. To be effective, a program cannot merely be a quarterly, semiannual, or annual gathering of employees to be lectured on not clicking a link. Instead, it is essential to create an iterative and dynamic process that tests employee through various types of cybersecurity attack vectors, pair that with general education, and finally, to develop specific interventions for ‘habitual clickers’ and other weak links in the organization.
- In the same spirit as the previous tip, small nuggets of knowledge dolled out regularly are far more effective than drawn out lengthy presentations that are spaced over time. 2-3 minute refreshers or targeted lessons with a specific purpose (risk of phishing, operational security, specific compliance issues, etc.) are far more effective than lumping everything together into a single hour-long (or often longer) session.
- Gamification. The average person is more interested in clicking a link than protecting their company from abstract threats. Thus it is vital for a cybersecurity awareness program to change that dynamic. One of the most useful tools for doing that is gamifying security awareness programs. Gamification refers to the process of turning a mundane task into a game. How to gamify security awareness training is a question that involves creativity and an understanding of the employees of the organization. Depending on the scale of the organization and the resources available, gamification can be something as simple as publicly calling out good acts of security awareness such as reporting a phishing link or completing a training course. For a more intricate and involved solution, an organization can create a public point system that rewards proper conduct and punishes poor practice. The company can give rewards and other benefits to top scorers while hoping that poor performers are encouraged to step up their training.

Eric Sheridan
Chief Scientist, WhiteHat Security
As the Chief Scientist of the Static Code Analysis division at WhiteHat Security, Eric oversees all research and development for Sentinel Source and related products, defining and driving the underlying technology.
The pace of change within and outside of an organization is staggering. Many businesses are in the process of digital transformation where applications and the APIs that connect them are becoming the digital fabric connecting the world. No longer is it taking months or years to build out IT infrastructure and applications. In many businesses today, it might be just a matter of days or hours. We have customers who are pushing application updates multiple times a day.
Cybercriminals are staying on top of this change too, evolving their capabilities at a similar pace. Organizations and individuals must be vigilant when it comes to security education and training, and security vendors need to make it as easy as possible for businesses and consumers to get the training and education they need to stay current on potential cyber threats.
To stay ahead of security risks, here are the top three practices to put in place:
- Enroll in Training Programs: People’s understanding of Security generally falls in two buckets: either the person is uninformed, or the person is informed but their knowledge quickly goes stale. A big part of thwarting attacks is to keep the team trained. There are training programs, some even free such as the WhiteHat Certified Developer Program, that can add to a company’s training and education arsenal and help both security teams and IT/development teams learn valuable secure coding skills and how to secure applications through the entire software development lifecycle.
- Phishing Training: People rely on emails and websites to function on a day-to-day basis, and phishing continues to be an effective means of victimizing users. According to the Verizon Data Breach Investigations Report, 30 percent of phishing messages were opened, and around 12 percent then actually clicked the malicious link or attachment. The best phishing attacks target something that you rely on, whether it be online banking, email or credit cards. Continued education and possibly warnings before executing the links are the best way to combat phishing attacks. Two-factor authentication is a great barrier for anyone attempting to hijack your account. Not only will an attacker need to compromise your username and password, but they will also need to compromise a device as well.
- Security in Context: Covering general security topics will only go so far. Optimal training programs provide curriculums that are tailored to the roles and responsibilities of the individual partaking in the curriculum. By way of example, Software Engineers need to have an understanding of the security implications of clicking an untrusted link, and they must also have an understanding of the security implications of building SQL queries at runtime using user-data.

Mike Meikle
Partner, SecureHIM
Mike Meikle is a Partner at secureHIM, a security consulting and education company that provides cybersecurity training for clients on topics such as data privacy and how to minimize the risk of data breaches.
Companies should include information on general security threats, how hackers compromise systems (social engineering, malware, etc.), top hacker targets (Facebook, Twitter, LinkedIn), defense techniques, an overview of the hacking ecosystem, and the cost of lost data to the organization.
Initially, training should be done in-person with a presenter. A slide presentation with topics that highlight how hackers affect the specific organization’s industry should be included. Live websites and video should be used to keep the audience engaged.
Follow-up security awareness presentation can be via a recorded webinar that is updated to reflect the changing threat landscape. After the recorded session there should be a quiz to measure how effective the presentation was with the target employees.
Also, the Information Security group can send out regular email blasts on threats and create a monthly newsletter or blog to keep security in the forefront of employee’s minds.
The best way for organizations to protect their data and keep their employees from compromising security is to train them on information security best practices. This must be done on a continual basis, in layman’s terms and at a minimum of six-month intervals. Sixty to seventy percent of data breaches are due to social engineering and hardware theft; an issue best addressed by training.
If an organization keeps the issue of information security in front of employees, makes it engaging and keeps the organization informed on how threats are impacting the company, then the employees with have a reference point on how their behavior is or could impact the company.
People love hacker stories. As part of our business we handle data breaches for companies, so we have plenty of stories on how hackers broke into organizations and what they did once inside the network. Many of these stories are relatable and get people interested in the topic. Often we will have 2-3 hacker stories in a briefing to introduce better security practices or ideas.
People like to talk about themselves. I make sure that I provide plenty of time for people to ask questions about their personal cybersecurity concerns related to their email, social media and smartphone use. The concerns that are typically expressed by one person in the group are usually shared by others and always leads to lively discussion and better training.

Joshua Feinberg
President, Data Center Sales & Marketing Institute
Joshua Feinberg is a digital strategist and revenue growth consultant, specializing in the data center, mission-critical, and cloud services industries. He is also a president of the Data Center Sales & Marketing Institute.
- Avoid cyber security courses where IT teams are scolding employees for being careless about their use of IT assets. While the 1990’s SNL skit with Jimmy Fallon (Nick Burns, Your company’s computer guy) is sure to be an excellent icebreaker for what your IT team shouldn’t be acting like, it’s far better to infuse a tip or two into other company meetings that employees want to attend.
- Use stories/videos to drive home the point. A few minutes on YouTube, looking for current events about breaches should yield plenty of 2-5 minute videos worth watching. For example, it’s widely known that a very high-ranking 2016 U.S. presidential campaign manager was compromised over essentially not having two-factor authentication turned on. (which brings me to my next point)
- Accept that shadow IT exists and provide department/application-specific advice. For example, show what should be done in settings to protect against the basics: turning on two-factor authentication, enforcing strong passwords, and forcing SSL usage in webapps. A tech-savvy power user in finance or marketing can often be a great person for your IT team to partner with on these efforts.
- Point out the dangers of public WiFi and why VPN software is so critical. Anyone with young kids, or who remembers being a kid, can relate to the telephone game, where you whispered in your friend’s ear to reveal a secret. This is an excellent analogy for this topic.

Larry Kahm
President, Heliotropic Systems, Inc.
Larry Kahm is president and owner of Heliotropic Systems, an IT provider for small businesses and entrepreneurs, located in Fort Lee, NJ. He has clients throughout eastern Bergen County, New York City, and Long Island.
Some general “rules of thumb” about emails that ask you to pay for invoices or to send out financial or client data:
- The same rule as you would use for a phishing email: Be very skeptical.
- If you have an admin handling your mail, make sure they ASK directly, or by phone or text, before they take any action.
- If the email is from someone you know, call them to double-check.
- If the email is from someone you do not know – do NOT call them. It is likely that they will try to use social engineering to convince you to send it.
- Do NOT send attachments if you do not know who requested them
- If you are at all uncertain about the email’s legitimacy, delete it. If someone really and truly needs something – they will get back to you!
I realize that this last one flies in the face of all social contracts. But each of you has to weigh how much you value your businesses’ security program over some possibly ruffled feathers.

Tom DeSot
EVP and CIO, Digital Defense, Inc.
As chief information officer, Tom is charged with key industry and market regulator relationships, public speaking initiatives, key integration and service partnerships, and regulatory compliance matters. Additionally, Tom serves as the company’s internal auditor on security-related matters.
Build A Powerful In House Defense Against Cybercrime
- Arm employees with the required knowledge to thwart information security intrusions designed to help train, educate and reinforce a security-aware employee base.
- Use All Tools Available to Fight Hackers – Kick off a new way of training and create maximum excitement and support by leveraging a fun and enjoyable staff security awareness program.
- Improve Your Team’s Security IQ – Easily deploy fun and engaging animated videos to all employees regardless of keeping security awareness top of mind. Easy and convenient, these videos will be accessible from multiple platforms (PC, laptop, iPad/tablet or mobile device).

- Employees need to be educated on what a phishing email looks like and why they are BAD. We do this by sending out test phishing emails and track which employees click on the link in the test email, and then we can educate that employee on a personal level.
- Another great tip is to not use or connect your devices to public WIFI. (i.e., hotels, airports, Starbucks, etc.) use your phone’s hotspot, so you are not allowing other devices to view your network access.
- Sessions are often boring wastes of time, both for employees and the IT teams responsible for them. How do you avoid this? – Whether we are educating our clients or presenting at a cyber security conference, we always do 2 things to make the event not a boring waste of time 1.) FOOD – we always have food and provide catering at our events and 2.) Giveaway gift cards throughout the presentation and at the end. Ask questions to get audience participation and give away $$. The bottom line on cybersecurity and reducing your risk is TRAINING/EDUCATION. You have to make it a priority to educate your employees.
Justin Lavelle
Chief Communications Officer, BeenVerified
BeenVerified is a leading source of online background checks and contact information. It allows individuals to find more information about people, phone numbers, email addresses, property records, and criminal records in a way that’s fast, easy, and affordable.
Start an Employee Security Awareness Program ASAP
The secret sauce for cybersecurity is focusing on two simple things – Talk about it and think about it. The reality is that dealing with security is a business issue (not an IT issue) and it involves hundreds of little things (usually not expensive or time-consuming) and not just the several big things you think you need to be doing (which can be costly and time-consuming).
Talk about it. We have found great success just getting people in the same room and telling stories. Call it a lunch and learn or do it in the afternoon and call it a snack and learn. The company buys some food, and everyone has to show up. Takes an hour or less and have someone come prepared with some best practices and stories of how people have made poor security decisions (we play this part for our clients). It is amazingly powerful seeing one employee explain how they got a phishing email and how they fell for it and say how they avoid it in the future and then hearing weeks later that someone else in the room saw the same thing but were not a victim because they listened to that story. It is super simple and really works. Just talk about it.
Think about it. Most people do not want to bother thinking about security. It is easier to turn a blind eye and think nothing bad will ever happen to you. All the business person needs to do is to make a conscious effort to think about security. Ask their IT for information about their business applications and such – manage who has access with privileged access management, what rights do users have, what is the password policy (complex and expire after X months), should you be using MFA (Multifactor Authentication), reports for antivirus and software updates, etc. Also think about if there are any concerns with other business areas – physical access control, third parties like banks, etc. Think about it and you will be more secure.

Robert Siciliano
Identity Theft Expert with HotSpot Shield
Train your staff and test your employees
- After presenting information about security awareness, come up with a scheme to set up a situation where employees are given the opportunity to open a very alluring link in their email. This is called a “phishing simulation.” This link will actually take the worker to a safe page, but you must make the page have a message, such as “You Fell For It.” You should also make sure that these emails look like a phishing email, such as adding a misspelling. The people who fall for this trick should be tested again in a few days or weeks. This way, you will know if they got the message or not.
- Do not make it predictable as to when you are giving out these tests. Offer them at different times of day and make sure that the email type changes.
- Consider hiring a professional who will attempt to get your staff to hand over sensitive business information over the phone, in person, and via email. This test could be invaluable, as it will clue you into who is falling for this.
- Quiz your staff throughout the year, to allow you to see who is paying attention. You want to focus on educating your staff, not disciplining them. They should not feel bad about themselves, but they should be made aware of these mistakes.
- Make sure your staff knows any data breach could result in legal, financial or criminal repercussions.
- Schedule workstation checks to see if employees are doing things that might compromise your business’ data, such as leaving sensitive information on the screen and walking away. Explain how important security is to your business and encourage staff to report any suspicious activity.
Amanda Bigley
Marketing Associate, Hummingbird Networks
Amanda Bigley is a marketing associate for Hummingbird Networks. She enjoys researching and writing about all things cybersecurity.
- Make a game out of it. Provide your employees with security basics of identifying social engineering through a quick read or cheat sheet and then incentivize them to put their knowledge to the test. Consider something like a department-wide game of Jeopardy. This method eliminates the boring lecture and boosts employee morale.
- Train employees as they come. Create material for training employees as they join the company. This will eventually cancel out the need for a large group training and ensure employees are properly vetted from day one. A quarterly quiz could help ensure their cybersecurity knowledge stays fresh and relevant.
- Create entertaining literature. Using the good old ambient marketing method, consider printing bathroom literature that provides employees with some easily consumable content. Taking a humorous tone, inform employees of current cybersecurity risks and tips, or company security news with a weekly, bi-monthly or monthly print which is then displayed on the back of stall doors. Create a simple template that requires little time to update with new info.

Isaac Kohen
Founder and CEO, Teramind
Isaac Kohen is the founder and CEO of Teramind, an employee monitoring, insider threat prevention platform that detects, records, and prevents malicious user behavior.
Cybersecurity awareness sessions for employees can often be boring wastes of time.
Combat the snooze fest of employee education sessions by making them engaging. This can be done by making the courses relatable. Create cybersecurity scenarios that employees can easily understand.
Utilize games, trends, gifs, memes, etc. whatever you need to convey your cybersecurity message. Understand your environment and hone in on whatever applies to your employees. You can easily incorporate funny and relatable scenarios to keep your employees attention all while helping them understand why cybersecurity is vital.
Recent Posts
PCI DSS 3.2 Compliance Requirements Guide: Updated For 2020
Every day we are becoming more and more a cashless society.
Plastic is the preferred method of payment for most North American businesses, and we even see a significant shift into virtual payment systems and direct-to-consumer banking.
In the modern world of digital currency, e-commerce, and fast-moving transactions, how can your business make sure that it is safely handling customer data?
Do you want to end up as the next headline splashed across the news as another company that has mishandled thousands of sensitive customer records?
If your business is accepting credit card payments and either stores, processes, or transmits cardholder data, then you are required to adhere to Payment Card Industry Data Security Standard compliance standards, otherwise known as PCI DSS.
The latest iteration of the standards is PCI DSS 3.2, as published by the Payment Card Industry Security Standards Council, with version 3.1 was entirely replaced as of October 2016.
This guide is a strong starting point for companies looking to maintain a strong security infrastructure. It also sets a clear and specific standardization of what is expected of companies that handle cardholder data.

What is PCI DSS Compliance?
PCI stands for “payment card industry” and refers to the Payment Card Industry Security Standards Council (PCI SSC).
The Counsel is a compromise between five proprietary data security and operations programs from major credit card companies: Visa, MasterCard, American Express, Discover, and JCB.
These companies aligned their policies to form the PCI DSS standard. This standard means that your company can pass validation of compliance from a Quality Security Assessor (QSA) from a firm-specific Draft Internal Security Assessor.
PCI validation methods culminate in an audit of PCI security standards controls. If the controls are found to be valid, a Report of Compliance (ROC) is issued. When a QSA conducts the audit, an Attestation of Compliance (AOC) is also issued. These are the accepted processes set by the PCI Security Standards Council.
TL:DR – Identify the 6 Most Prevalent Risk Factors in Data Security
Who do PCI DSS 3.2 Requirements Apply To?
Any company or private entity that can process, transmit or store consumer information from any of the five major credit card companies are subject to DSS compliance.
Credit card companies maintain merchant compliance levels depending on the number of annual transactions that a company completes:
-
- Level 1 – Merchants with more than 6 million yearly sales added across all channels. However, global merchants that identify as Level 1 in any region maintain that distinction in all areas.
- Level 2 – Merchants that conduct between 1 and 6 million transactions on an annual basis across all channels.
- Level 3 – Online Merchants that conduct e-commerce between 20K and 1 million transactions on an annual basis across all channels.
- Level 4 – Online Merchants that conduct e-commerce of fewer than 20K transactions on an annual basis across all channels, and merchants processing no more than 1 million yearly transactions across all channels.
Transactions may not be included in the merchant total if they are processed through local merchant locations instead of through the corporate entity.
The credit card companies also state that they maintain the sole right to define a Level 1 Merchant.
What Is the Timeline for the PCI DSS 3.2 Update?
As stated directly from the PCI Council:
“PCI DSS 3.1 will retire on October 31st, 2016, and after this time all assessments will need to use version 3.2. Between now and 31 October 2016, either PCI DSS 3.1 or 3.2 may be used for PCI DSS assessments. The new requirements introduced in PCI DSS v3.2 are considered best practices until January 31st, 2018. Starting February 1st, 2018 they are effective as requirements and must be used.”

What To Expect from the PCI 3.2 requirements Update?
The most critical changes that companies can expect from the update to the 3.2 standards are as follows.
Multi-factor authentication – This is different from two-factor authentication, or 2FA. Multi-factor authentication includes all processes that have at least two authentication factors. Every employee who has administrative access control to the cardholder data environment (CDE) must process through multifactor authentication. Previous PCI DSS standards only required 2FA and just remote administrators that were considered “untrusted” were required to verify themselves this way. This is one of the most significant expansions of the authentication requirement standards in the history of published PCI DSS.
SAQ Changes – All Self Assessment Questionnaires (SAQs) added many requirements outside of SAQ B and SAQ P2PE. SAQ B stayed the same as its previous iteration. SAQ P2PE took away two of its obligations. These requirements had to do with emailing and masking PAN data that was not encrypted.
Network segmentation and scoping – Systems outside of the CDE may now be included within the scope of PCI compliance. Many systems that connect to the CDE may also need to be added due to lack of segmentation.
Service providers – There are multiple changes for merchants and service providers including changes in penetration testing and the establishment of responsibilities for data and annual PCI compliance. There are also changes to the personal reviews performed on a quarterly basis, timeliness of reporting and detection of problems and cryptographic architecture.
Deprecation of SSL and Early TLS – All uses of SSL and TLS 1.0 within your CHE must be removed by June 30, 2018. However, TLS 1.1 is allowed though it is highly recommended to upgrade to TLS 1.2.
How Do The Updated Requirements Affect Your Organization?
The change from 3.1 to 3.2 is considered a non-major release and should not impact organizations significantly.
The depreciation of SSL and early TLS will be a challenge for many organizations but is a much-needed rule. SSL and TLS 1.0 have been exploitable for a significant amount of time and businesses are doing themselves a favor by upgrading. Many TLS and SSL exploits have caused many companies problems, including the exploits known as BEAST and POODLE. The National Institute of Standards and Technology (NIST) report that there are currently no patches that can provide a full repair for these TLS and SSL exploits.
How Can You Prepare for Your Next PCI DSS 3.2 Assessment?
Ordering Compliance Efforts Through the 6 Step Prioritized Approach
PCI DSS has identified six security measures that are most important in assessing and protecting against the most prevalent risk factors in business data security. These steps are meant to provide a company with a roadmap that can help to prioritize time and resources towards a fully compliant organization. The process is also intended to improve morale towards an environment of full compliance by creating a pragmatic approach that creates ultimate successes.
This prioritized approach also helps to promote consistency in compliance assessments along with operational and financial planning. Following the steps in order will also help a company to protect its cardholder data environment more quickly than haphazardly applying compliance standards. The approach was cultivated through an assessment of past breaches and feedback from forensic investigators and QSAs.
The six steps are as follows:
-
- The removal of authentication data that may be sensitive and the limitation of data retention – in short, companies should delete all data that they do not need. This is especially true of authentication data and other personal and financial information that may be sensitive. If this data is deleted from the system, its ability to be used to compromise the system is greatly reduced.
- The protection of networks and systems through constant vigilance in preparation for a breach – Companies should identify the most common point(s) of access for a breach or security compromise(s). The company should then identify and begin to prep the processes by which it will respond to these challenges.
- Securing all applications of payment card information – Weaknesses in application processes, servers, and controls for applications are straightforward ways for hackers to compromise company systems. This event should be considered on its own because of the importance of securing payment card applications.
- Monitoring who has physical access to company systems and controlling data access – Companies should implement a tiered system that limits the access of administrators to information that is outside of their jurisdiction. This system should be monitored, and all processes for the security of the system fully documented.
- The protection of cardholder data that is stored within the system – First, companies must determine whether they need to store highly sensitive information such as Primary Account Numbers. If a company has made this determination through a complete assessment of its internal processes, then it must create protection measures for that data.
- Ensuring that all protection controls are fully operational and finalizing any extra compliance efforts – By the time that milestone six is completed, all PCI DSS 3.2 requirements should be fulfilled. Additionally, any related processes, policies, and procedures that relate in any way to PCI DSS compliance should be fully operational as well.

Here are 10 best practices to prepare for your next PCI assessment.
Consistent Monitoring of Security Controls
Because of the speed with which malicious hackers improve their techniques, companies must continuously monitor their security controls. Part of being compliant with PCI DSS v3.2 is determining if a company can protect itself between assessments. If it cannot, then the assessment itself may not serve as an adequate deterrent for hackers looking for a weak target. It is also a requirement to review your PCI controls on a quarterly basis (if not monthly).
Timely Identification and Response to Failures of Security Controls
If a security control fails, then specific processes must be invoked within a timely manner to remain compliant. These processes include identification of why the control failed, identifying security issues that occurred during failure, full restoration of the control, the creation of procedures to ensure the failure doesn’t happen again, and the implementation of a monitoring strategy to verify operation of the control.
Determination of Changes Made before Upgrades Can be Completed
If any system is to be added into a PCI DSS environment, the impact of that system must be assessed. This system can be entirely new or modified from an existing system. Any part of a company’s infrastructure that connects to the addition must be evaluated for its compliance with PCI DSS 3.2. The company is responsible for identifying that new compliance requirements are met for all systems and networks modified by the change. The scope of the PCI DSS must be updated, and all new security controls required must be implemented and penetration tested.
Changes to the Organizational Structure Must be Reviewed
All employees must have privileged security access management controls that are relevant to his or her responsibilities and job description within the company. This structure should be reviewed from multiple scopes, including the individual and group levels.
Companies Should Initiate Consistent Reviews
A company should perform a regular review of its compliance measures to ensure that all requirements are implemented and up-to-date. These reviews must be conducted, at a minimum, quarterly to remain compliant. A company should also check to make sure that its processes have been properly updated as suggested by PCI 3.2. These internal reviews should include all company locations and all system components. A company has some leeway to determine how often these reviews should be completed, based upon the size and complexity of its infrastructure.
A main focus of these reviews should be to verify that appropriate records are being kept to maintain and prove PCI DSS v3.2 compliance efforts.
Regular Documentation of Both Software and Hardware Technologies
The vendor must fully support all equipment that is used within the company. All equipment must also meet the PCI DSS version 3.2 security requirements of the client. The company should immediately take action if any hardware is not vendor supported or the requirements are not met.
The same level of scrutiny should be applied to all software that the company is using. Software that is out of compliance accounted for 44% of data breaches in 2018.

Ensuring Accountability for Security Notifications
Five new requirements are introduced with 3.2 dealing specifically with the need for companies to notify customers of problems promptly.
The changes deal with detection of critical security systems and control mechanisms as well as cryptographic architecture. The amendments also require that a company perform quarterly reviews to vet all internal security personnel. The timely notification of severe issues to customers was found to be one of the aspects of security most lacking in companies, even those compliant with past iterations of the PCI DSS.
Ensuring the Proper Masking of Primary Account Numbers
To remain compliant with PCI DSS 3.2, a company must mask all instances of primary account numbers. At a maximum, only the last four digits or the first six digits may be shown. Any employee who is allowed to see more than this maximum must be accounted for. A company must create a list of these employees, including their roles within the company and the reasoning behind allowing them to see more than the masked primary account number.

Going Over the Designated Entities Supplemental Validation (DESV)
Because payment brands have the power to require service providers to fulfill additional DESV validations, companies should go over these requirements from the beginning of the compliance process. These requirements are covered in Appendix 3 and only will be penetration tested when instructed by an acquirer or a payment brand. PCI DSS 3.2 has the Designated Entities Supplemental Validation process as an appendix, including all new requirements that service providers will be expected to follow. These updated requirements include interviewing personnel to ensure documentation of cryptographic architecture. Additionally, companies are expected to implement a full change management process that keeps up with all system changes that may impact any system that is within the auspices of the PCI DSS.
Properly Scoping the Affected Environment
Evaluating the company environment is one of the most critical steps that you can take towards compliance and implementation of PCI DSS version 3.2.
To begin the process of scoping, a company should identify every component of the system that is either connected to or located within the CDE. The PCI SSC has given suggestions for compliance. Currently, there is a process to assess, report and remediate all data within the scope of the PCI DSS.
The Future Importance Of PCI Compliance
No one is quite sure exactly how malicious hackers will attack ecommerce in the coming years. There is a consensus, however, when you discuss data breaches in general. The problem is not going away.
Unprotected companies can almost expect to be targeted. Having a data security standard is essential to protecting your company and the information of the people who trust you. Take the above PCI compliance guide into account, consider PCI Compliant Web Hosting to bolster your security controls.
Recent Posts
What is High Availability Architecture? Why is it Important?
Achieving business continuity is a primary concern for modern organizations. Downtime can cause significant financial impact and, in some cases, irrecoverable data loss.
The solution to avoiding service disruption and unplanned downtime is employing a high availability architecture.
Because every business is highly dependent on the Internet, every minute counts. That is why company computers and servers must stay operational at all times.
Whether you choose to house your own IT infrastructure or opt for a hosted solution in a data center, high availability must be the first thing to consider when setting up your IT environment.
High Availability Definition
A highly available architecture involves multiple components working together to ensure uninterrupted service during a specific period. This also includes the response time to users’ requests. Namely, available systems have to be not only online, but also responsive.
Implementing a cloud computing architecture that enables this is key to ensuring the continuous operation of critical applications and services. They stay online and responsive even when various component failures occur or when a system is under high stress.
Highly available systems include the capability to recover from unexpected events in the shortest time possible. By moving the processes to backup components, these systems minimize downtime or eliminate it. This usually requires constant maintenance, monitoring, and initial in-depth tests to confirm that there are no weak points.
High availability environments include complex server clusters with system software for continuous monitoring of the system’s performance. The top priority is to avoid unplanned equipment downtime. If a piece of hardware fails, it must not cause a complete halt of service during the production time.
Staying operational without interruptions is especially crucial for large organizations. In such settings, a few minutes lost can lead to a loss of reputation, customers, and thousands of dollars. Highly available computer systems allow glitches as long as the level of usability does not impact business operations.
A highly available infrastructure has the following traits:
- Hardware redundancy
- Software and application redundancy
- Data redundancy
- The single points of failure eliminated
How To Calculate High Availability Uptime Percentage?
Availability is measured by how much time a specific system stays fully operational during a particular period, usually a year.
It is expressed as a percentage. Note that uptime does not necessarily have to mean the same as availability. A system may be up and running, but not available to the users. The reasons for this may be network or load balancing issues.
The uptime is usually expressed by using the grading with five 9’s of availability.
If you decide to go for a hosted solution, this will be defined in the Service Level Agreement (SLA). A grade of “one nine” means that the guaranteed availability is 90%. Today, most organizations and businesses require having at least “three nines,” i.e., 99.9% of availability.
Businesses have different availability needs. Those that need to remain operational around the clock throughout the year will aim for “five nines,” 99.999% of uptime. It may seem like 0.1% does not make that much of a difference. However, when you convert this to hours and minutes, the numbers are significant.
Refer to the table of nines to see the maximum downtime per year every grade involves:
| Availability Level | Maximum Downtime per Year | Downtime per Day |
| One Nine: 90% | 36.5 days | 2.4 hours |
| Two Nines: 99% | 3.65 days | 14 minutes |
| Three Nines: 99.9% | 8.76 hours | 86 seconds |
| Four Nines: 99.99% | 52.6 minutes | 8.6 seconds |
| Five Nines: 99.999% | 5.25 minutes | 0.86 seconds |
| Six Nines: 99.9999% | 31.5 seconds | 8.6 milliseconds |
As the table shows, the difference between 99% and 99.9% is substantial.
Note that it is measured in days per year, not hours or minutes. The higher you go on the scale of availability, the cost of the service will increase as well.
How to calculate downtime? It is essential to measure downtime for every component that may affect the proper functioning of a part of the system, or the entire system. Scheduled system maintenance must be a part of the availability measurements. Such planned downtimes also cause a halt to your business, so you should pay attention to that as well when setting up your IT environment.
As you can tell, 100% availability level does not appear in the table.
Simply put, no system is entirely failsafe. Additionally, the switch to backup components will take some period, be that milliseconds, minutes, or hours.
How to Achieve High Availability
Businesses looking to implement high availability solutions need to understand multiple components and requirements necessary for a system to qualify as highly available. To ensure business continuity and operability, critical applications and services need to be running around the clock. Best practices for achieving high availability involve certain conditions that need to be met. Here are 4 Steps to Achieving 99.999% Reliability and Uptime.
1. Eliminate Single Points of Failure High Availability vs. Redundancy
The critical element of high availability systems is eliminating single points of failure by achieving redundancy on all levels. No matter if there is a natural disaster, a hardware or power failure, IT infrastructures must have backup components to replace the failed system.
There are different levels of component redundancy. The most common of them are:
- The N+1 model includes the amount of the equipment (referred to as ‘N’) needed to keep the system up. It is operational with one independent backup component for each of the components in case a failure occurs. An example would be using an additional power supply for an application server, but this can be any other IT component. This model is usually active/passive. Backup components are on standby, waiting to take over when a failure happens. N+1 redundancy can also be active/active. In that case, backup components are working even when primary components function correctly. Note that the N+1 model is not an entirely redundant system.
- The N+2 model is similar to N+1. The difference is that the system would be able to withstand the failure of two same components. This should be enough to keep most organizations up and running in the high nines.
- The 2N model contains double the amount of every individual component necessary to run the system. The advantage of this model is that you do not have to take into consideration whether there was a failure of a single component or the whole system. You can move the operations entirely to the backup components.
- The 2N+1 model provides the same level of availability and redundancy as 2N with the addition of another component for improved protection.
The ultimate redundancy is achieved through geographic redundancy.
That is the only mechanism against natural disasters and other events of a complete outage. In this case, servers are distributed over multiple locations in different areas.
The sites should be placed in separate cities, countries, or even continents. That way, they are entirely independent. If a catastrophic failure happens in one location, another would be able to pick up and keep the business running.
This type of redundancy tends to be extremely costly. The wisest decision is to go for a hosted solution from one of the providers with data centers located around the globe.
Next to power outages, network failures represent one of the most common causes of business downtime.
For that reason, the network must be designed in such a way that it stays up 24/7/365. To achieve 100% network service uptime, there have to be alternate network paths. Each of them should have redundant enterprise-grade switches and routers.
2. Data Backup and recovery
Data safety is one of the biggest concerns for every business. A high availability system must have sound data protection and disaster recovery plans.
An absolute must is to have proper backups. Another critical thing is the ability to recover in case of a data loss quickly, corruption, or complete storage failure. If your business requires low RTOs and RPOs and you cannot afford to lose data, the best option to consider is using data replication. There are many backup plans to choose from, depending on your business size, requirements, and budget.
Data backup and replication go hand in hand with IT high availability. Both should be carefully planned. Creating full backups on a redundant infrastructure is vital for ensuring data resilience and must not be overlooked.
3. Automatic failover with Failure Detection
In a highly available, redundant IT infrastructure, the system needs to instantly redirect requests to a backup system in case of a failure. This is called failover. Early failure detections are essential for improving failover times and ensuring maximum systems availability.
One of the software solutions we recommend for high availability is Carbonite Availability. It is suitable for any infrastructure, whether it is virtual or physical.
For fast and flexible cloud-based infrastructure failover and failback, you can turn to Cloud Replication for Veeam. The failover process applies to either a whole system or any of its parts that may fail. Whenever a component fails or a web server stops responding, failover must be seamless and occur in real-time.
The process looks like this:
- There is Machine 1 with its clone Machine 2, usually referred to as Hot Spare.
- Machine 2 continually monitors the status of Machine 1 for any issues.
- Machine 1 encounters an issue. It fails or shuts down due to any number of reasons.
- Machine 2 automatically comes online. Every request is now routed to Machine 2 instead of Machine 1. This happens without any impact to end users. They are not even aware there are any issues with Machine 1.
- When the issue with the failed component is fixed, Machine 1 and Machine 2 resume their initial roles
The duration of the failover process depends on how complicated the system is. In many cases, it will take a couple of minutes. However, it can also take several hours.
Planning for high availability must be based on all these considerations to deliver the best results. Each system component needs to be in line with the ultimate goal of achieving 99.999 percent availability and improve failover times.
4. Load Balancing
A load balancer can be a hardware device or a software solution. Its purpose is to distribute applications or network traffic across multiple servers and components. The goal is to improve overall operational performance and reliability.
It optimizes the use of computing and network resources by efficiently managing loads and continuously monitoring the health of the backend servers.
How does a load balancer decide which server to select?
Many different methods can be used to distribute load across a server pool. Choosing the one for your workloads will depend on multiple factors. Some of them include the type of application that is served, the status of the network, and the status of the backend servers. A load balancer decides which algorithm to use according to the current amount of incoming requests.
Some of the most common load balancing algorithms are:
- Round Robin. With Round Robin, the load balancer directs requests to the first server in line. It will move down the list to the last one and then start from the beginning. This method is easy to implement, and it is widely used. However, it does not take into consideration if servers have different hardware configurations and if they can overload faster.
- Least Connection. In this case, the load balancer will select the server with the least number of active connections. When a request comes in, the load balancer will not assign a connection to the next server on the list, as is the case with Round Robin. Instead, it will look for one with the least current connections. Least connection method is especially useful to avoid overloading your web servers in cases where sessions last for a long time.
- Source IP hash. This algorithm will determine which server to select according to the source IP address of the request. The load balancer creates a unique hash key using the source and destination IP address. Such a key enables it always to direct a user’s request to the same server.
Load balancers indeed play a prominent role in achieving a highly available infrastructure. However, merely having a load balancer does not mean that you have a high system availability.
If a configuration with a load balancer only routes the traffic to decrease the load on a single machine, that does not make a system highly available.
By implementing redundancy for the load balancer itself, you can eliminate it as a single point of failure.

In Closing: Implement High Availability Architecture
No matter what size and type of business you run, any kind of service downtime can be costly without a cloud disaster recovery solution.
Even worse, it can bring permanent damage to your reputation. By applying a series of best practices listed above, you can reduce the risk of losing your data. You also minimize the possibilities of having production environment issues.
Your chances of being offline are higher without a high availability system.
From that perspective, the cost of downtime dramatically surpasses the costs of a well-designed IT infrastructure. In recent years, hosted and cloud computing solutions have become more popular than in-house solutions support. The main reason for this is the fact it reduces IT costs and adds more flexibility.
No matter which solution you go for, the benefits of a high availability system are numerous:
- You save money and time as there is no need to rebuild lost data due to storage or other system failures. In some cases, it is impossible to recover your data after an outage. That can have a disastrous impact on your business.
- Less downtime means less impact on users and clients. If your availability is measured in five nines, that means almost no service disruption. This leads to better productivity of your employees and guarantees customer satisfaction.
- The performance of your applications and services will be improved.
- You will avoid fines and penalties if you do not meet the contract SLAs due to a server issue.