Orchestration vs Automation: What You Need to Know
Netflix, Amazon, and Facebook are all pioneers and innovators of Cloud computing and technology.
Orchestration
Orchestration is an integral part of their services and complex business processes. Orchestration is the mechanism that organizes components and multiple tasks to run applications seamlessly.
The greater the workload, the higher the need to efficiently manage these processes and avoid downtime. None of these big industry players can afford to be offline. It’s why orchestration has become central to their IT strategies and applications, which require automatic execution of massive workflows.
Orchestration works by minimizing redundancies and optimizes by streamlining repeating processes. It ensures a quicker and more precise deployment of software and updates. Offering a secure solution that is both flexible and scalable it gives enterprises the freedom to adapt and evolve rapidly.
Shorter turn-around times, from app development to market means more profit and success. It allows businesses to keep pace with evolving technological demands.
Hand in hand with orchestration, enterprises use automation to reduce the degree of manual work required to run an application. Automation refers to single repeatable tasks or processes that can be automated.
Automation
Automation allows enterprises to gain and maintain speed efficiency via software automation tools that regulate functionalities and workloads on the cloud. Orchestration takes advantage of automation and executes large workflows systematically. It does so by managing multiple sophisticated automated processes and coordinating them across separate teams and functions.
In the cloud, orchestration not only deploys an application, but it connects it to the network to enable communication between users and other apps. It ensures auto-scaling to initiate in the right order, implementing the correct permissions and security rules. Automation makes orchestration easier to execute.
To put it simply, automation specifies a single task. Orchestration arranges multiple tasks to optimize a workflow. To understand orchestration vs. automation in more detail, we will take a look at each operation.
What is Cloud Orchestration?
Cloud orchestration refers to the process of creating an automation environment across a particular enterprise. It facilitates the coordination of teams, cloud services, functions, compliance, and security activities. It eliminates the chances of making costly mistakes by creating an entirely automated, repeatable, and end-to-end environment for all processes.
It’s the underlying framework across services and clouds that joins all automation routines. Orchestration, when combined with automation, makes cloud services run more efficiently as all automated routines become perfectly timed and coordinated.
By using software abstractions, cloud orchestration can coordinate among multiple systems located in various sites by using an underlying infrastructure. Modern IT teams that are responsible for managing hundreds of applications and servers require orchestration. It facilitates the delivering of dynamically scaling applications and cloud systems. In doing so, it alleviates the need for staff to run processes manually. Automation is tactical, and orchestration is the strategy.
What is Cloud Automation?
In terms of software development life cycle, the process of cloud automation is best described as a connector or several connectors which provide a data flow when triggered. Automation is typically performed to achieve or complete a task between separate functions or systems, without any manual intervention.
Cloud automation leverages the potential of cloud technology for a system of automation across the entire cloud infrastructure. Results in an automated and frictionless software delivery pipeline eliminate the chances of human error, manual roadblocks. It automates several complex tasks that would otherwise require developers or operations teams to perform them. Automation makes maintaining an operating system efficient by automating simultaneously, multiple repetitive manual processes. It’s like having your workflow run on railways tracks.
By limiting errors in the system, automation prevents setbacks, which minimize the system’s availability and lower the overall negative effects on performance. This lessens the possibility of breaches of sensitive or critical information. In turn, the system is more reliable and transparent. Cloud automation supports the twelve principles of agile development and DevOps methodologies that enable scalability, rapid resource deployment, and continuous integration and delivery.
The most common use cases are workload management to allocate resources, workflow version control to monitor changes. To establish an Infrastructure as Code (IAC) environment, which streamlines system resources. To regulate data back-ups and act as a data loss prevention tool. And can act as an integral part of a Hybrid cloud system, tying together disparate elements cohesively, such as applications on public and private clouds.
Automation is implemented via orchestration tools that manage operations where these tools write down deployment processes and their management routines. Automation tools are then used to execute the procedures listed above.
Importance of Cloud Orchestration Tools
Microservices framework is prevalent in the modern IT landscape, with automation playing an essential part.
Repetitive jobs, which include deploying applications and managing application lifecycles, require tools that can handle complex job dependencies. Cloud orchestration currently facilitates enterprise-level security policies, flexible monitoring, and visualization, among other tasks.
Installing a cloud orchestra at an enterprise-level means that certain conditions have to be met beforehand to ensure success, such as;
- Minimizing human errors by handling the setup and execution of automation tasks, automatically.
- Reducing human intervention when it comes to managing automation tasks by using orchestration tools.
- Ensuring proper permissions are provided to users to prevent unauthorized access to the automation system.
- Simplifying the process of setting up new data integration by managing governing policies around it.
- Providing generalizable infrastructure to remove the need for building any ad hoc tools.
- Providing comprehensive diagnostic support, which results in fast debugging and auditing.
Comparing Cloud Orchestration with Cloud Automation
Both Cloud automation and cloud orchestration are used significantly in modern IT industries. There are some specific fundamental differences between the two, which are explained briefly below.
| Points of Difference | Cloud Automation | Cloud Orchestration |
| Concept | Cloud automation refers to tasks or functions which are accomplished without any human intervention in a cloud environment. | Cloud orchestration relates to the arranging and coordination of tasks that are automated. The main aim is to create a consolidated workflow or process. |
| Nature of Tools | Cloud automation tools and activities related to it occur in a particular order using certain groups or tools. They are also required to be granted permissions and given roles. | Cloud orchestration tools can enumerate the various resources, IAM roles, instance types, etc., configure them and ensure that there is a degree of interoperability between those resources. This is true regardless of the tools native to the LaaS platform or belongs to a third party. |
| Role of Personnel | Engineers are required to complete a myriad of manual tasks to deliver a new environment. | It requires less intervention from personnel. |
| Policy decisions | Cloud automation does not typically implement any policy decisions which fall outside of OS-level ACLs. | Cloud orchestration handles all permissions and security of automation tasks.
|
| Resources Used | It uses minimal resources outside of the assigned specific task. | Ensures that cloud resources are efficiently utilized.
|
| Monitoring and Alerting | Cloud automation can send data to third party reporting services. | Cloud orchestration only involves monitoring and alerting for its workflows. |
Benefits of Orchestration and Automation
Many organizations have shifted towards cloud orchestration tools to simplify the process of deployment and management. The benefits provided by cloud orchestration are many, with the major ones outlined below.
Simplified optimization
Under cloud orchestration, individual tasks are bundled together into a larger, more optimized workflow. This process is different than standard cloud automation, which handles these individual tasks one at a time. For instance, an application that utilizes cloud orchestration includes the automated provisioning of multiple storages, servers, databases, and networking.
Automation is unified
Cloud administrators usually have a portion of their processes automated. It is different from a fully unified automation platform that cloud orchestration provides. Cloud orchestration centralizes the entire automation process under one roof. This, in turn, makes the whole process cost-effective, faster, and easier to change and expand the automated services if required later.
Forces best practices
Cloud orchestration processes cannot be fully implemented without cleaning up any existing processes that do not adhere to best practices. As automation is easier to achieve with properly organized cloud resources, any existing cloud procedures need to be evaluated and cleaned up if necessary. There are several good practices associated with cloud orchestration that are adapted by organizations. These include pre-built templates for deployment, structured IP addressing, and baked-in security.
Self-service portal
Cloud orchestration provides self-service portals that are favored by infrastructure administrators and developers alike. It gives developers the freedom to select the cloud services they desire via an easy to use web portal. This setup eliminates the need for infrastructure admins in the entire deployment process.
Visibility and control are improved
VM sprawl, which refers to a point where the system administrator can no longer effectively manage a high number of virtual machines, is a common occurrence for many organizations. If left unattended, it can cause unnecessary wastage of financial resources and can complicate the management of a particular cloud platform. Cloud orchestration tools can be used to automatically monitor any VM instances that may occur, which reduces the number of staff hours required for managing the cloud.
Long term cost savings
By properly implementing cloud orchestration, an organization can reduce and improve its cloud service footprint, reducing the need for infrastructure staffing significantly.
Automated chargeback calculation
For companies that offer self-service portals for their different departments, cloud orchestration tools such as metering, and chargeback tools could keep close track of the number of cloud resources employed.
Helps facilitate business agility
The shift into a purely digital environment is happening at a much faster pace, and businesses are keen on hopping onboard. IT shops are thus required to design and manage their computer resources, which would allow them to pivot towards any new or emerging opportunity in short notice. This rapid flexibility is facilitated by implementing a robust cloud orchestration system.
A Collaborative Cloud Solution
Both automation and orchestration can take place on an individual level as well as on a companywide level. Employees can take advantage of automation suites that support apps such as emails, Microsoft products, Google products, etc. as they do not need any prior or advanced knowledge about coding. It’s recommended to choose projects which can create significant and measurable business value and not use orchestration for merely speeding up the entire process.
It’s not a debate of orchestration vs automation, but instead, a matter of collaboration and implementing them in the right degree and combination. Doing so allows any company to lower IT costs, increase productivity, and reduce staffing needs. As more organizations start relying on cloud automation, the role of orchestration technology will only increase. The complexity of automation management cannot be performed with only manual intervention, and so, cloud orchestration is considered to be the key to growth, long-term stability, and prosperity.
By streamlining routines automation and its orchestration, free up resources that can be reinvested into further improvement and innovation. Cloud automation and orchestration support more cost-effective business and DevOps/CloudOps pipelines. Whether it’s offsite cloud services, onsite, or a hybrid model, better use of system resources produces better results and can give an organization major advantages over their competition.
Now that you’ve understood the basic differences between orchestration and automation, you can start looking into the variety of orchestration tools available. IT orchestration tools vary in degree, from basic script-based app deployment tools to specialized tools such as Kubernetes’ container orchestration solution.
Are you interested in cloud solutions and using the infrastructure-as-code paradigm? Then speak to a professional today, and find out which tool is the right one for your environment.
Recent Posts
Kubernetes vs OpenStack: How Do They Stack Up?
Cloud interoperability keeps evolving alongside its platforms. Kubernetes and OpenStack are not merely direct competitors but can now also be combined to create cloud-native applications. Kubernetes is the most widely used container orchestration tool to manage/orchestrate Linux containers. It deploys, maintains, and schedules applications efficiently. OpenStack lets businesses run their Infrastructure-as-a-Service (IaaS) and is a powerful software application.
Kubernetes and OpenStack have been regarded as competitors, but in actuality, both these open-source technologies can be combined and are complementary to one other. They both offer solutions to problems that are relatively similar but do so on different layers of the stack. When you combine Kubernetes and OpenStack, it can give you noticeably enhanced scalability and automation.
It’s now possible for Kubernetes to deploy and manage applications on an OpenStack cloud infrastructure. OpenStack as a cloud orchestration tool allows you to run Kubernetes clusters on top of white label hardware more efficiently. Containers can be aligned with this open infrastructure, which enables them to share computer resources in rich environments, such as networking and storage.
Difference between OpenStack and Kubernetes
Kubernetes and OpenStack still do compete for users, despite their overlapping features. Both have their own sets of merits and use cases. It’s why it’s necessary to take a closer look at both options to determine their differences and find out which technology or combination is best for your business.
To present a more precise comparison between the two technologies, let’s start with the basics.
What is Kubernetes?
Kubernetes is an open-source cloud platform for managing containerized workloads and services. Kubernetes is a tool used to manage clusters of containerized applications. In computing, this process is often referred to as orchestration.
The analogy with a music orchestra is, in many ways, fitting. Much as a conductor would, Kubernetes coordinates multiple microservices that together form a useful application. It automatically and perpetually monitors the cluster and makes adjustments to its components. Kubernetes architecture provides a mix of portability, extensibility, and functionality, facilitating both declarative configuration and automation. It handles scheduling by using nodes set up in a compute cluster. Kubernetes also actively manages workloads, ensuring that their state matches with the intentions and desired state set by the user.
Kubernetes is designed to make all its components swappable and thus have modular designs. It is built for use with multiple clouds, whether it is public, private, or a combination of the two. Developers tend to prefer Kubernetes for its lightweight, simple, and accessible nature. It operates using a straightforward model. We input how we would like our system to function – Kubernetes compares the desired state to the current state within a cluster. Its service then works to align the two states and achieve and maintain the desired state.
How is Kubernetes Employed?
Kubernetes is arguably one of the most popular tools employed when it comes to getting the most value out of containers. Its features ensure that it is a near-perfect tool designed to automate scaling, deployment, and operating containerized applications.
Kubernetes is not only an orchestration system. It is a set of independent, interconnected control processes. Its role is to continuously work on the current state and move the processes in the desired direction. Kubernetes is ideal for service consumers, such as developers working in enterprise environments as it provides support for programmable, agile, and rapidly deployable environments.
Kubernetes is used for several different reasons:
- High Availability: Kubernetes includes several high-availability features such as multi-master and cluster federation. The cluster federation feature allows clusters to be linked together. This setup exists so that containers can automatically move to another cluster if one fails or goes down.
- Heterogeneous Clusters: Kubernetes can run on heterogeneous clusters allowing users to build clusters from a mix of virtual machines (VMs) running the cloud, according to user requirements.
- Persistent Storage: Kubernetes has extended support for persistent storage, which is connected to stateless application containers.
- Built-in Service Discovery and Auto-Scaling: Kubernetes supports service discovery, out of the box, by using environment variables and DNS. For increased resource utilization, users can also configure CPU based auto-scaling for containers.
- Resource Bin Packing: Users can declare the maximum and minimum compute resources for both CPU and memory when dealing with containers. It slots the containers into wherever they fit, which increases compute efficiency, which results in lower costs.
- Container Deployments and Rollout Controls: The Deployment feature allows users to describe their containers and specify the required quantity. It keeps those containers running and also handles deploying changes. This enables users to pause, resume, and rollback changes as per requirements.
What is OpenStack?
OpenStack an open-source cloud operating system that is employed to develop public and private cloud environments. Made up of multiple interdependent microservices, it offers an IaaS layer that is production-ready for virtual machines and applications. OpenStack, first developed as a cloud infrastructure in July 2010, was a product of the joint effort of many companies, including NASA and Rackspace.
Their goal since has been to provide an open alternative to the top cloud providers. It’s also considered a cloud operating system that can control large pools of computation, storage, and networking resources through a centralized datacenter. All of this is managed through a user-friendly dashboard, which provides users with increased control by allowing them to provision resources through a simple graphic web interface. OpenStack’s growing in popularity because it offers open-source software to businesses wanting to deploy their own private cloud infrastructure versus using a public cloud platform.
How is OpenStack Used?
It’s known for its complexity, consisting of around sixty components, also called ‘services’, six of them are core components, and they control the most critical aspects of the cloud. These services are for the compute, identity, storage management, and networking of the cloud, including access management.
OpenStack comprises of a series of commands known as scripts, which are bundled together into packages called projects. The projects are responsible for relaying tasks that create cloud environments. OpenStack does not virtualize resources itself; instead, it uses them to build clouds.
When it comes to cloud infrastructure management, OpenStack can be employed for the following.
Containers
OpenStack provides a stable foundation for public and private clouds. Containers are used to speed up the application delivery time while also simplifying application management and deployment. Containers running on OpenStack can thus scale container benefits ranging from single teams to even enterprise-wide interdepartmental operations.
Network Functions Virtualization
OpenStack can be used for network functions virtualization, and many global communications service providers include it on their agenda. OpenStack separates a network’s key functions to distribute it among different environments.
Private Clouds
Private cloud distributions tend to run on OpenStack better than other DIY approaches due to the easy installation and management facilities provided by OpenStack. The most advantageous feature is its vendor-neutral API. Its open API erases the worries of single-vendor lock-in for businesses and offers maximum flexibility in the cloud.
Public Clouds
OpenStack is considered as one of the leading open-source options when it comes to creating public cloud environments. OpenStack can be used to set up public clouds with services that are on the same level as most other major public cloud providers. This makes them useful for small scale startups as well as multibillion-dollar enterprises.
What are the Differences between Kubernetes and OpenStack?
Both OpenStack and Kubernetes provide solutions for cloud computing and networking in very different ways. Some of the notable differences between the two are explained in the table below.
| Points of Difference | Kubernetes | OpenStack |
| Classification | Classified as a Container tool | Classified as an Open Source Cloud tool |
| User Base | It has a large Github community of over 55k users as well as, 19.1 Github forks. | Not much of an organized community behind it |
| Companies that Use them | Google, Slack, Shopify, Digital Ocean, 9GAG, Asana, etc. | PayPal, Hubspot, Wikipedia, Hazeorid, Survey Monkey, etc. |
| Main Functions | Efficient docker container and management solution | A flexible and versatile tool for managing Public and Private Clouds |
| Tools that can be Integrated | Docker, Ansible, Microsoft Azure, Google Compute Engine, Kong, Etc. | Fastly, Stack Storm, Spinnaker, Distelli, Morpheus Etc. |
How Can Kubernetes and OpenStack Work Together?
Can Kubernetes and OpenStack work together? This is a common question among potential users.
One of the most significant obstacles in the path of OpenStack’s widespread adoption is its ongoing life cycle management. For enterprises, using OpenStack and Kubernetes together can radically simplify the management of OpenStack’s many components. In this way, users benefit from a consistent platform for managing workloads.
Kubernetes and OpenStack can be used together to reap the combined benefits of both the tools. By integrating Kubernetes into OpenStack, Kubernetes users can access a much more robust framework for application deployment and management. Kubernetes’s features, scalability, and flexibility make ‘Stackanetes’ an efficient solution for managing OpenStack and makes operating OpenStack as easy as running any application on Kubernetes.
Benefits of Leveraging Both OpenStack and Kubernetes
Faster Development of Apps
Running Kubernetes and OpenStack together can offer on-demand and access-anytime services. It also helps to increase application portability and reduces development time.
Improving OpenStack’s lifecycle management
Kubernetes, along with cloud-native patterns, improve OpenStack lifecycle management through rolling updates and versioning.
Increased Security
Security has always been a critical concern in container technology. OpenStack solves this by providing a high level of security. It supports the verification of trusted container content by integrating tools for image signing, certification, and scanning.
Standardization
By combining Kubernetes and OpenStack, container technology can become more universally applicable. This makes it easier for organizations to set up as well as deploy container technology, using the existing OpenStack infrastructure.
Easier to Manage
OpenStack can be complex to use and has a steep learning curve, which creates a hindrance for any users. The Stackanetes initiative circumvents the complexity by using Kubernetes cluster orchestration to deploy and manage OpenStack.
Speedy Evolution
Both are widely employed by tech industry giants, notwithstanding Amazon, Google, and eBay. This popularity drives software applications to develop and innovate faster. They increase the pace of evolution to offer solutions to issues as they crop up. Evolving and simultaneously integrating, creates rapidly upgraded enterprise-grade infrastructure and application platforms.
Stability
OpenStack on its own lacks the stability to run smoothly. Kubernetes, on the other hand, uses a large-scale distributed system, allowing it to run smoothly. By combining the two, OpenStack can use a more modernized architecture, which also increases its stability.
Kubernetes and OpenStack are Better Together
There has always been competition between OpenStack and Kubernetes, both of whom are giants in the open-source technology landscape. That’s why it can be surprising to some users when we talk about the advantages of using these two complementary tools together. As both of them solve similar problems but on different layers, combining the two is the most practical solution for scalability and automation. Combined, more than ever, DevOps teams would have more freedom to create cloud-native applications. Both Kubernetes and OpenStack have their advantages and use cases, making it very difficult to compare between the two, as both of them are used in different contexts.
OpenStack, together with Kubernetes, can increase the resilience and scale of its control panel, allowing faster delivery of infrastructure innovation. These different yet complementary technologies, widely used by industry leaders, will keep both innovating at an unprecedented pace.
Find out how these solutions can work for you, and get your free quote today.
Recent Posts
Kubernetes vs Mesos: Detailed Comparison
Container orchestration is a fast-evolving technology. There are three current industry giants; Kubernetes, Docker Swarm, and Apache Mesos. They fall into the category of DevOps infrastructure management tools, known as ‘Container Orchestration Engines’. Docker Swarm has won over large customer favor, becoming the lead choice in containerization. Kubernetes and Mesos are the main competition. They have something more to offer in this regard. They provide differing gradients of usability, with many evolving features.
Despite the popularity of Docker Swarm, it has some drawbacks and limited functionalities:
- Docker Swarm is platform-dependent.
- Docker Swarm does not provide efficient storage options.
- Docker Swarm has limited fault tolerance.
- Docker Swarm has inadequate monitoring.
These drawbacks provoke businesses to question: ‘How to choose the right container management and orchestration tool?’ Many companies are now choosing an alternative to Docker Swarm. This is where Kubernetes and Mesos come in. To examine this choice systematically, it’s essential to look at the core competencies both options have. So, one can come to an independently informed conclusion.
Characteristics of Docker Swarm, Kubernetes, and Mesos
| Characteristics | Docker Swarm | Kubernetes | Mesos/Marathon |
| Initial Release Date | Mar 2013, Stable release July 2019 | July 2015, v1.16 in Sept 2019 | July 2016, Stable release August 2019 |
| Deployment | YAML based | YAML based | Unique format |
| Stability | Comparatively new and constantly evolving | Quite mature and stable with continuous updates | Mature |
| Design Philosophy | Docker-based | Pod-based resource-groupings | Cgroups and control groups based in Linux |
| Images Supported | Docker-image format | Supports Docker and rkt, limitedly | Supports mostly Docker |
| Learning Curve | Easy | Steep | Steep |
What is Kubernetes?
First released in June of 2014, Kubernetes, was also known as k8s. It is a container orchestration platform by Google for Cloud-native computing. In terms of features, Kubernetes is one of the most natively integrated options available. It also has a large community behind it. Google makes use of Kubernetes for its Container as a Service offering, renamed as the Google Container Engine. Other platforms that have extended support to Kubernetes include Microsoft Azure and Red Hat OpenShift. It also supports Docker and uses a YAML based deployment model.
Constructed on a modular API core, the architecture of Kubernetes allows vendors to integrate systems around its proprietary technology. It does a great job of empowering application developers with a powerful tool for Docker container orchestration and open-source projects.
What is Apache Mesos?
Apache Mesos’ roots go back to 2009 when Ph.D. students first developed it at UC Berkley. When compared to Kubernetes and Docker Swarm, it takes more of a distributed approach when it comes to managing datacenter and cloud resources.
It takes a modular approach when dealing with container management. It allows users to have flexibility in the types and scalability of applications that they can run. Mesos allows other container management frameworks to run on top of it. This includes Kubernetes, Apache Aurora, Mesosphere Marathon, and Chronos.
Mesos was created to solve many different challenges. One being, to abstract data center resources into a single pool. Another, to collocate diverse workloads and automate day-two operations. And lastly, to provide evergreen extensibility to running tasks and new applications. It has a unique ability to manage a diverse set of workloads individually, including application groups such as Java, stateless micro-services, etc.
Container Management: Explained
Before we decide on how to choose a container management tool, the concept of Container Management must be explained further.
Container Management is the process of adding, organizing, and replacing large numbers of software containers. It utilizes software for automatically creating, deploying, and scaling containers. Container management requires a platform to organize software containers, known as operated-system-level virtualizations. This platform optimizes the efficiency and streamlines container delivery without the use of complex interdependent system architectures.
Containers have become quite popular, as more enterprises are using DevOps for quicker development and for its applications. Container management gives rise to the need for container orchestration, which is a more specialized tool. It automates deployment, management, networking scaling, and availability of container-based applications.
Container Orchestration: Explained
Container Orchestration refers to the automatic process of managing or scheduling of individual containers used for microservices-based applications within multiple clusters. It works with both Kubernetes and Mesos. It also schedules the deployment of containers into the clusters, determining the best host for the container.
Some of the reasons why a container orchestration framework is required include;
- Configuring and scheduling containers
- Container Availability
- Container Provisioning and Deployment
- Container Configuration
- Scaling applications of containers for load balancing
- Health monitoring of containers
- Securing interactions between containers
How to Select Container management and orchestration tool?
There are many variables to consider when deciding on how to implement container management and orchestration efficiently. The final selection will depend on the specific requirements of the user. Some of which are briefly explained below.
- CNI Networking: A good tool should allow trivial network connectivity between services. This is to avoid developers having to spend time on special-purpose codes for finding dependencies.
- Simplicity: The tool in use should be as simple to implement as possible.
- Active Development: The tool chosen should have a development team that provides users with regular updates. This is due to the ever-evolving nature of container orchestration.
- Cloud Vendor: The tool chosen should not be tied to any single cloud provider.
Note: Container orchestration is just one example of a workload that the Mesos Modular Architecture can run. This specialized orchestration framework is called Marathon. It was originally developed to orchestrate app archives in Linux cgroup containers, later extended support to Docker containers in 2014.
What are the differences between Kubernetes and Mesos?
Kubernetes and Mesos have different approaches to the same problem. Kubernetes acts as a container orchestrator, and Apache Mesos works like a cloud operating system. Therefore, there are several fundamental differences between the two, which are highlighted in the table below.
| Points of Difference | Kubernetes | Apache Mesos |
| Application Definition | Kubernetes is a combination of Replica Sets, Replication Controllers, Pods, along with certain Services and Deployments. Here, “Pod” refers to a group of co-located containers, which is considered as the atomic unit of deployment. | The Mesos’ Application Group is modeled as an n-ary tree, with groups as branches and applications as leaves. It’s used to partition multiple applications into manageable sets, where components are deployed in order of dependency. |
| Availability | Pods are distributed among Worker Nodes. | Applications are distributed among Slave nodes. |
| Load Balancing | Pods are exposed via a service that acts as a load balancer. | Applications can be reached through an acting load balancer, which is the Mesos-DNS. |
| Storage | There are two Stage APIs.
The first one provides abstractions for individual storage back-ends such as NFS, AWS, and EBS, etc. The second one provides an abstraction for a storage resource request. This is fulfilled with different storage back-ends. |
A Marathon Container has the capability to use persistent volumes, which are local to the node where they are created. Hence the container always required to run on the said node. The experimental flocker integration is responsible for supporting persistent volumes that are not local to one single node. |
| Networking Model | Kubernetes’ Networking model allows any pod to communicate with any service or with other pods. It requires two separate networks to operate, with neither network requiring connectivity from outside the cluster. This is accomplished by deploying an overlay network on the cluster nodes. | Marathon’s Docker integration allows mapping container ports to hose ports, which are a limited resource. Here, the container will not automatically acquire an IP, that is only possible by integrating with Calico. It should be noted that multiple containers cannot share the same network namespace. |
| Purpose of Use | It is ideal for newcomers to the clustering world, providing a quick, easy, and light way to start begin their journey in cluster-oriented development. It offers a great degree of versatility, portability, and is supported by a few big-name providers such as Microsoft and IBM. | It is ideal for large systems as it is designed for maximum redundancy. For existing workloads such as Hadoop or Kafka, Mesos provides a framework allowing the user to interleave those workloads with each other. It is a much more stable platform while being comparatively complex to use. |
| Vendors and Developers | Kubernetes is used by several companies and developers and is supported by a few other platforms such as Red Hat OpenShift and Microsoft Azure. | Mesos is supported by large organizations such as Twitter, Apple, and Yelp. Its learning curve is steep and quite complex as its core focus is one Big Data and analytics. |
Conclusion
Kubernetes and Mesos employ different tactics to tackle the same problem. In comparing them based on several features, we have found that both solutions are equivalent in terms of features and other advantages when compared to Docker Swarm.
The conclusion we can come to is that they are both viable options for container management and orchestration. Each tool is effective in managing docker containers. They both provide access to container orchestration for the portability and scalability of applications.
The intuitive architectural design of Mesos provides good options when it comes to handling legacy systems and large-scale clustered environments via its DC/OS. It’s also adept at handling more specific technologies such as distributed processing with Hadoop. Kubernetes is preferred more by development teams who want to build a system dedicated exclusively to docker container orchestration.
Our straightforward comparison should provide users with a clear picture of Kubernetes vs Mesos and their core competencies. The goal has been to provide the reader with relevant data and facts to inform their decision.
How to choose between them will depend on finding the right cluster management solution that fits your company’s technical requirements. If you’d like to find out more about which solution would suit you best, contact us today for a free consultation.
Recent Posts
Kubernetes vs Docker Swarm: What are the Differences?
As an increasing number of applications move to the cloud, their architectures and distributions continue to evolve. This evolution requires the right set of tools and skills to manage a distributed topology across the cloud effectively. The management of microservices across virtual machines, each with multiple containers in varied groupings, can quickly become complicated. To reduce this complexity, container orchestration is utilized.
Container orchestration is the automatic managing of work for singular containers. It’s for applications based on microservices within multiple clusters. A single tool for the deployment and management of microservices in virtual machines. Distributing microservices across many machines is complex. Orchestration provides the following solutions:
- A centralized tool for the distribution of applications across many machines.
- Deploys new nodes when one goes down.
- Relays information through a centralized API, communicating to every distributed node.
- Efficient management of resources.
- Distribution based on personalized configuration.
In regards to how modern development and operations teams test and deploy software, microservices have proven to be the best solution. Containers can help companies modernize themselves by allowing them to deploy and scale applications quickly. Containerization is an entirely new infrastructure system. Before discussing the main differences between the Kubernetes and the Docker system, the concept of containerization will be expanded on.
The orchestration tools we will stack up against each other are Kubernetes vs. Docker Swarm. There are several differences between the two. This article will discuss what each tool does, followed by a comparison between them.
What is Kubernetes?
Created by Google in 2014, Kubernetes (also called K8s) is an open-source project for effectively managing application deployment. In 2015, Google also partnered with the Linux Foundation to create the Cloud Native Computing Foundation (CNCF). CNCF now manages the Kubernetes project.
Kubernetes has been gaining in popularity since its creation. A Google Trends search over the last five years shows Kubernetes has surpassed the popularity of Docker Swarm, ending August 2019 with a score of 91 vs. 3 for Docker Swarm.
Kubernetes architecture was designed from the ground up with orchestration in mind. Based on the primary/replica model, where there is a master node that distributes instructions to worker nodes. Worker nodes are the machines that microservices run on. This configuration allows each node to host all of the containers that are running within a container run-time (i.e., Docker). Nodes also contain Kubelets.
Think of Kubelets as the brains for each node. Kubelets take instructions from the API, which is in the master node, and then process them. Kubelets also manage pods, including creating new ones if a pod goes down.
A pod is an abstraction that groups containers. By grouping containers into a pod, those containers can share resources. These resources include processing power, memory, and storage. At a high level, here are some of Kubernetes’ main features:
- Automation
- Deployment
- Scaling
Before discussing Kubernetes any further, let’s take a closer look at Docker Swarm.
Explaining Docker Swarm
Docker Swarm is a tool used for clustering and scheduling Docker containers. With the help of Swarm, IT developers and administrations can easily establish and manage a cluster of Docker nodes under a single virtual system. Clustering is an important component for container technology, allowing administrators to create a cooperative group of systems that provide redundancy.
Docker Swarm failover can be enabled in case of a node outage. With the help of a Docker swarm cluster, administrators, as well as developers, can add or subtract container iterations with the changing computing demand.
For companies that want even more support, there is Docker’s Docker Enterprise-as-a-Service (EaaS). EaaS performs all the necessary upgrades and configurations, removing this burden from the customer. Companies who use AWS or Microsoft Azure can “consume Docker Enterprise 3.0.” Cluster management and orchestration are also known as a swarm. Docker Swarmkit is a tool for creating and managing swarms.
Similar to Kubernetes, Docker Swarm can both deploy across nodes and manage the availability of those nodes. Docker Swarm calls its main node, the manager node. Within the Swarm, the manager nodes communicate with the worker nodes. Docker Swarm also offers load balancing.
What is the Difference Between Kubernetes and Docker Swarm?
Both Kubernetes and Docker Swarm are two of the most used open-source platforms, which provide mostly similar features. However, on closer inspection, several fundamental differences can be noticed between how these two functions. The Table below illustrates the main points of difference between the two:
| Point of Difference | Kubernetes | Docker Swarm |
| Application Deployment | Applications can be deployed in Kubernetes using a myriad of microservices, deployments, and pods. | Applications can be used only as microservices in a swarm cluster. Multi containers are identified by utilizing YAML files. With the help of Docker Compose, the application can also be installed. |
| Scalability | Kubernetes acts like more of an all-in-one framework when working with distributed systems. It is thus significantly more complicated as it provides strong guarantees in terms of the cluster state and a unified set of APIs. Container scaling and deployment are therefore slowed down. | Docker Swarm can deploy containers much faster than Kubernetes, which allows faster reaction times for scaling on demand. |
| Container Setup | By utilizing its own YAML, API, and client definitions, Kubernetes differs from other standard docker equivalents. Thus, Docker Compose or Docker CLI cannot be used to define containers. Also, YAML definitions and commands must be rewritten when switching platforms. | The Docker Swarm API offers much of the familiar functionality from Docker, supporting most of the tools that run with Docker. However, Swarm cannot be utilized if the Docker API is deficient in a particular operation. |
| Networking | Kubernetes has a flat network model, allowing all the pods to communicate with each other. Network policies are in place to define how the pods interact with one another. The network is implemented typically as an overlay, requiring two CIDRS for the services and the pods. | When a node joins a swarm cluster, it creates an overlay network for services for each host in the docker swarm. It also creates a host-only docker bridge network for containers. This gives users a choice while encrypting the container data traffic to create its own overlay network. |
| Availability | Kubernetes offers significantly high availability as it distributes all the pods among the nodes. This is achieved by absorbing the failure of an application. Unhealthy pods are detected by load balancing services, which subsequently deactivate them. | Docker also offers high availability architecture since all the services can be cloned in Swarm nodes. The Swarm manager Nodes manage the worker’s node resources and the whole cluster. |
| Load Balancing | In Kubernetes, pods are exposed via service, allowing them to be implemented as a load balancer inside a cluster. An ingress is generally used for load balancing. | Swarm Mode comes with a DNS element which can be used for distributing incoming requests to a service name. Thus services can be assigned automatically or function on ports that are pre-specified by the user. |
| Logging and Monitoring | It includes built-in tools for managing both processes. | It does not require using any tools for logging and monitoring. |
| GUI | Kubernetes has detailed dashboards to allow even non-technical users to control the clusters effectively. | ocker Swarm, alternatively, requires a third-party tool such as Portainer.io to manage the UI conveniently. |
Our comparison reveals that both Kubernetes and Docker Swarm are comprehensive “de-facto” solutions for intelligently managing containerized applications. Even though they offer similar capabilities, the two are not directly comparable, as they have distinct roots and solve different problems.
Thus, Kubernetes works well as a container orchestration system for Docker containers, utilizing the concept of pods and nodes. Docker is a platform and a tool for building, distributing, and running docker containers, using its native clustering tool to orchestrate and schedule containers on machine clusters.
Which one should you use: Kubernetes or Docker Swarm?
The choice of tool depends on the needs of your organization.
Docker Swarm is a good choice if you need a quick setup and do not have exhaustive configuration requirements. It delivers software and applications with microservice-based architecture effectively. Its main positives are the simplicity of installation and a gradual learning curve. As a standalone application, it’s perfect for software development and testing. Thus, with easy deployment and automated configuration, it also uses fewer hardware resources, it could be the first solution to consider. The downside is that native monitoring tools are lacking, and the Docker API limits functionality. But it still offers overlay networking, load balancing, high availability, and several scalability features. Final verdict: Docker Swarm is ideal for users who want to set up a containerized application and get it up and running without much delay.
Kubernetes would be the best containerization platform to use if the app you’re developing is complex and utilizes hundreds of thousands of containers in the process. It has high availability policies and auto-scaling capabilities. Unfortunately, the learning curve is steep and might hinder some users. The configuration and setup process is also lengthy. Final verdict: Kubernetes is for those users, who are comfortable with customizing their options and need extensive functionalities.
Find out which solution would suit your business best, and contact us today for a free consultation.
Recent Posts
When is Microservice Architecture the Way to Go?
Choosing and designing the correct architecture for a system is critical. One must ensure the quality of service requirements and the handling of non-functional requirements, such as maintainability, extensibility, and testability.
Microservice architecture is quite a recurrent choice in the latest ecosystems after companies adopted Agile and DevOps. While not being a de facto choice, when dealing with systems that are extensively growing and where a monolith architecture is no longer feasible to maintain, it is one of the preferred options. Keeping components service-oriented and loosely coupled allows continuous development and release cycles ongoing. This drives businesses to constantly test and upgrade their software.
The main prerequisites that call for such an architecture are:
- Domain-Driven Design
- Continuous Delivery and DevOps Culture
- Failure Isolation
- Decentralization
It has the following benefits:
- Team ownership
- Frequent releases
- Easier maintenance
- Easier upgrades to newer versions
- Technology agnostic
It has the following cons:
- microservice-to-microservice communication mechanisms
- Increasing the number of services increases the overall system complexity
The more distributed and complex the architecture is, the more challenging it is to ensure that the system can be expanded and maintained while controlling cost and risk. One business transaction might involve multiple combinations of protocols and technologies. It is not just about the use cases but also about its operations. When adopting Agile and DevOps approaches, one should find a balance between flexibility versus functionality aiming to achieve continuous revision and testing.
The Importance of Testing Strategies in Relation to Microservices
Adopting DevOps in an organization aims to eliminate the various isolated departments and move towards one overall team. This move seeks to specifically improve the relationships and processes between the software team and the operations team. Delivering at a faster rate also means ensuring that there is continuous testing as part of the software delivery pipeline. Deploying daily (and in some cases even every couple of hours) is one of the main targets for fast end-to-end business solution delivery. Reliability and security must be kept in mind here, and this is where testing comes in.
The inclusion of test-driven development is the only way to achieve genuine confidence that code is production-ready. Valid test cases add value to the system since they validate and document the system itself. Apart from that, good code coverage encourages improvements and assists during refactoring.
Microservices architecture decentralizes communication channels, which makes testing more complicated. It’s not an insurmountable problem. A team owning a microservice should not be afraid to introduce changes because they might break existing client applications. Manual testing is very inefficient, considering that continuous integration and continuous deployment is the current best practice. DevOps engineers should ensure to include automation tests in their development workflow: write tests, add/refactor code, and run tests.
Common Microservice Testing Methods
The test pyramid is an easy concept that helps us identify the effort required when writing tests, and where the number of tests should decrease if granularity decreases. It also applies when considering continuous testing for microservices.
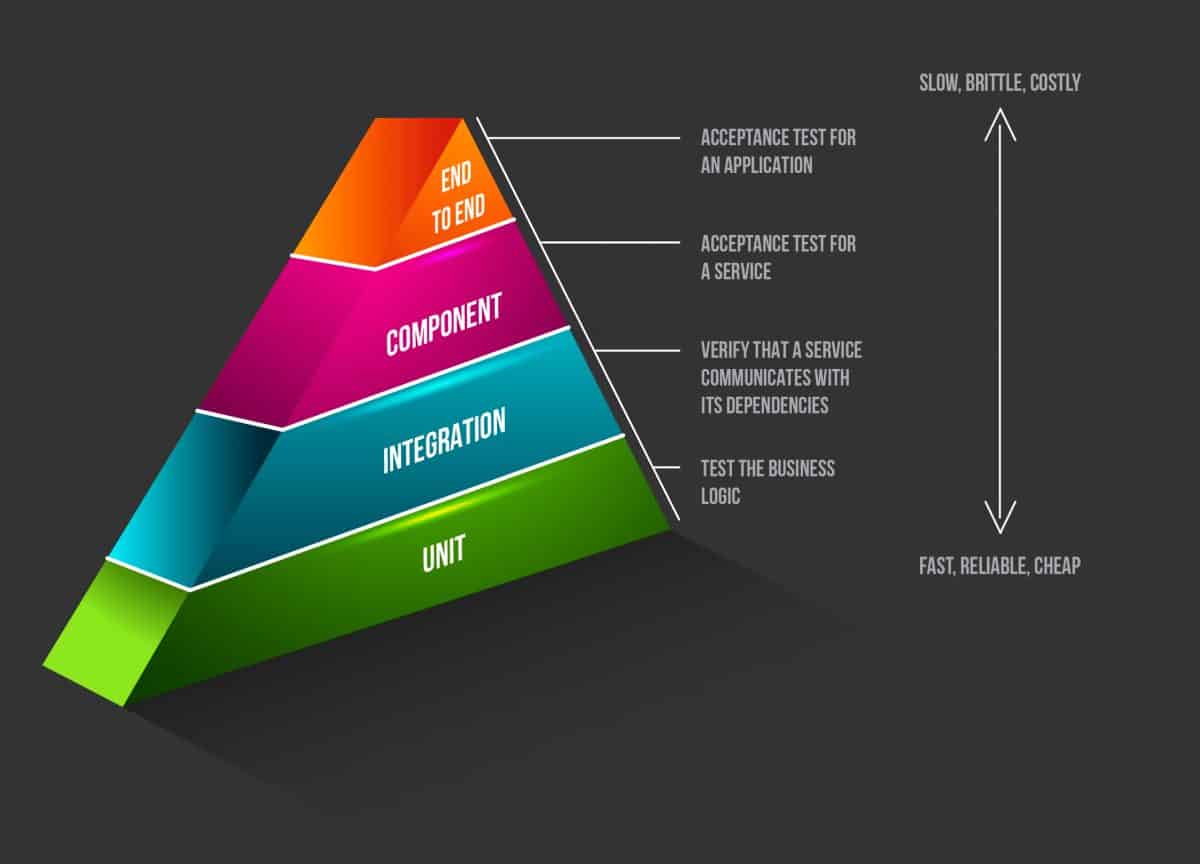
To make the topic more concrete, we will tackle the testing of a sample microservice using Spring Boot and Java. Microservice architectures, by construct, are more complicated than monolithic architecture. Nonetheless, we will keep the focus on the type of tests and not on the architecture. Our snippets are based on a minimal project composed of one API-driven microservice owning a data store using MongoDB.
Unit tests
Unit tests should be the majority of tests since they are fast, reliable, and easy to maintain. These tests are also called white-box tests. The engineer implementing them is familiar with the logic and is writing the test to validate the module specifications and check the quality of code.
The focus of these tests is a small part of the system in isolation, i.e., the Class Under Test (CUT). The Single Responsibility Principle is a good guideline on how to manage code relating to functionality.
The most common form of a unit test is a “solitary unit test.” It does not cross any boundaries and does not need any collaborators apart from the CUT.
As outlined by Bill Caputo, databases, messaging channels, or other systems are the boundaries; any additional class used or required by the CUT is a collaborator. A unit test should never cross a boundary. When making use of collaborators, one is writing a “sociable unit tests.” Using mocks for dependencies used by the CUT is a way to test sociable code with a “solitary unit test.”
In traditional software development models, developer testing was not yet wildly adopted, having to test completely off-sync from development. Achieving a high code coverage rating was considered a key indicator of test suite confidence.
With the introduction of Agile and short iterative cycles, it’s evident now that previous test models no longer work. Frequent changes are expected continuously. It is much more critical to test observable behavior rather than having all code paths covered. Unit tests should be more about assertions than code coverage because the aim is to verify that the logic is working as expected.
It is useless to have a component with loads of tests and a high percentage of code coverage when tests do not have proper assertions. Applying a more Behavior-Driven Development (BDD) approach ensures that tests are verifying the end state and that the behavior matches the requirements set by the business. The advantage of having focused tests with a well-defined scope is that it becomes easier to identify the cause of failure. BDD tests give us higher confidence that failure was a consequence of a change in feature behavior. Tests that otherwise focus more on code coverage cannot offer much confidence since there would be a higher risk that failure is a repercussion for changes done in the tests themselves due to code paths implementation details.
Tests should follow Martin Fowler’s suggestion when he stated the following (in Refactoring: Improving the Design of Existing Code, Second Edition. Kent Beck, and Martin Fowler. Addison-Wesley. 2018):
Another reason to focus less on minor implementation details is refactoring. During refactoring, unit tests should be there to give us confidence and not slow down work. A change in the implementation of the collaborator might result in a test failure, which might make tests harder to maintain. It is highly recommended to keep a minimum of sociable unit tests. This is especially true when such tests might slow down the development life cycle with the possibility that tests end up ignored. An excellent situation to include a sociable unit test is negative testing, especially when dealing with behavior verification.
Integration tests
One of the most significant challenges with microservices is testing their interaction with the rest of the infrastructure services, i.e., the boundaries that the particular CUT depends on, such as databases or other services. The test pyramid clearly shows that integration tests should be less than unit tests but more than component and end-to-end tests. These other types of tests might be slower, harder to write, and maintain, and be quite fragile when compared to unit tests. Crossing boundaries might have an impact on performance and execution time due to network and database access; still, they are indispensable, especially in the DevOps culture.
In a Continuous Deployment scope, narrow integration tests are favored instead of broad integration tests. The latter is very close to end-to-end tests where it requires the actual service running rather than the use of a test double of those services to test the code interactions. The main goal to achieve is to build manageable operative tests in a fast, easy, and resilient fashion. Integration tests focus on the interaction of the CUT to one service at a time. Our focus is on narrow integration tests. Verification of the interaction between a pair of services can be confirmed to be as expected, where services can be either an infrastructure service or any other service.
Persistence tests
A controversial type of test is when testing the persistence layer, with the primary aim to test the queries and the effect on test data. One option is the use of in-memory databases. Some might consider the use of in-memory databases as a sociable unit test since it is a self-contained test, idempotent, and fast. The test runs against the database created with the desired configuration. After the test runs and assertions are verified, the data store is automatically scrubbed once the JVM exits due to its ephemeral nature. Keep in mind that there is still a connection happening to a different service and is considered a narrow integration test. In a Test-Driven Development (TDD) approach, such tests are essential since test suites should run within seconds. In-memory databases are a valid trade-off to ensure that tests are kept as fast as possible and not ignored in the long run.
@Before
public void setup() throws Exception {
try {
// this will download the version of mongo marked as production. One should
// always mention the version that is currently being used by the SUT
String ip = "localhost";
int port = 27017;
IMongodConfig mongodConfig = new MongodConfigBuilder().version(Version.Main. PRODUCTION)
.net(new Net(ip, port, Network.localhostIsIPv6())).build();
MongodStarter starter = MongodStarter.getDefaultInstance();
mongodExecutable = starter.prepare(mongodConfig);
mongodExecutable.start();
} catch (IOException e) {
e.printStackTrace();
}
}Snippet 1: Installation and startup of the In-memory MongoDB
The above is not a full integration test since an in-memory database does not behave exactly as the production database server. Therefore, it is not a replica for the “real” mongo server, which would be the case if one opts for broad integration tests.
Another option for persistence integration tests is to have broad tests running connected to an actual database server or with the use of containers. Containers ease the pain since, on request, one provisions the database, compared to having a fixed server. Keep in mind such tests are time-consuming, and categorizing tests is a possible solution. Since these tests depend on another service running apart from the CUT, it’s considered a system test. These tests are still essential, and by using categories, one can better determine when specific tests should run to get the best balance between cost and value. For example, during the development cycle, one might run only the narrow integration tests using the in-memory database. Nightly builds could also run tests falling under a category such as broad integration tests.
@Category(FastIntegration.class)
@RunWith(SpringRunner.class)
@DataMongoTest
public class DailyTaskRepositoryInMemoryIntegrationTest {
. . .
}
@Category(SlowIntegration.class)
@RunWith(SpringRunner.class)
@DataMongoTest(excludeAutoConfiguration = EmbeddedMongoAutoConfiguration.class)
public class DailyTaskRepositoryIntegrationTest {
...
}Snippet 2: Using categories to differentiate the types of integration tests
Consumer-driven tests
Inter-Process Communication (IPC) mechanisms are one central aspect of distributed systems based on a microservices architecture. This setup raises various complications during the creation of test suites. In addition to that, in an Agile team, changes are continuously in progress, including changes in APIs or events. No matter which IPC mechanism the system is using, there is the presence of a contract between any two services. There are various types of contracts, depending on which mechanism one chooses to use in the system. When using APIs, the contract is the HTTP request and response, while in the case of an event-based system, the contract is the domain event itself.
A primary goal when testing microservices is to ensure those contracts are well defined and stable at any point in time. In a TDD top-down approach, these are the first tests to be covered. A fundamental integration test ensures that the consumer has quick feedback as soon as a client does not match the real state of the producer to whom it is talking.
These tests should be part of the regular deployment pipeline. Their failure would allow the consumers to become aware that a change on the producer side has occurred, and that changes are required to achieve consistency again. Without the need to write intricate end-to-end tests, ‘consumer-driven contract testing’ would target this use case.
The following is a sample of a contract verifier generated by the spring-cloud-contract plugin.
@Test
public void validate_add_New_Task() throws Exception {
// given:
MockMvcRequestSpecification request = given()
.header("Content-Type", "application/json;charset=UTF-8")
.body("{\"taskName\":\"newTask\",\"taskDescription\":\"newDescription\",\"isComplete\":false,\"isUrgent\":true}");
// when:
ResponseOptions response = given().spec(request).post("/tasks");
// then:
assertThat(response.statusCode()).isEqualTo(200);
assertThat(response.header("Content-Type")).isEqualTo("application/json;charset=UTF-8");
// and:
DocumentContext parsedJson = JsonPath.parse(response.getBody().asString());
assertThatJson(parsedJson).field("['taskName']").isEqualTo("newTask");
assertThatJson(parsedJson).field("['isUrgent']").isEqualTo(true);
assertThatJson(parsedJson).field("['isComplete']").isEqualTo(false);
assertThatJson(parsedJson).field("['id']").isEqualTo("3");
assertThatJson(parsedJson).field("['taskDescription']").isEqualTo("newDescription");
}Snippet 3: Contract Verifier auto-generated by the spring-cloud-contract plugin
A BaseClass written in the producer is instructing what kind of response to expect on the various types of requests by using the standalone setup. The packaged collection of stubs is available to all consumers to be able to pull them in their implementation. Complexity arises when multiple consumers make use of the same contract; therefore, the producer needs to have a global view of the service contracts required.
@RunWith(SpringRunner.class)
@SpringBootTest
public class ContractBaseClass {
@Autowired
private DailyTaskController taskController;
@MockBean
private DailyTaskRepository dailyTaskRepository;
@Before
public void before() {
RestAssuredMockMvc.standaloneSetup(this.taskController);
Mockito.when(this.dailyTaskRepository.findById("1")).thenReturn(
Optional.of(new DailyTask("1", "Test", "Description", false, null)));
. . .
Mockito.when(this.dailyTaskRepository.save(
new DailyTask(null, "newTask", "newDescription", false, true))).thenReturn(
new DailyTask("3", "newTask", "newDescription", false, true));
}Snippet 4: The producer’s BaseClass defining the response expected for each request
On the consumer side, with the inclusion of the spring-cloud-starter-contract-stub-runner dependency, we configured the test to use the stubs binary. This test would run using the stubs generated by the producer as per configuration having version specified or always the latest. The stub artifact links the client with the producer to ensure that both are working on the same contract. Any change that occurs would reflect in those tests, and thus, the consumer would identify whether the producer has changed or not.
@SpringBootTest(classes = TodayAskApplication.class)
@RunWith(SpringRunner.class)
@AutoConfigureStubRunner(ids = "com.cwie.arch:today:+:stubs:8080", stubsMode = StubRunnerProperties.StubsMode.LOCAL)
public class TodayClientStubTest {
. . .
@Test
public void addTask_expectNewTaskResponse () {
Task newTask = todayClient.createTask(
new Task(null, "newTask", "newDescription", false, true));
BDDAssertions.then(newTask).isNotNull();
BDDAssertions.then(newTask.getId()).isEqualTo("3");
. . .
}
}Snippet 5: Consumer injecting the stub version defined by the producer
Such integration tests verify that a provider’s API is still in line with the consumers’ expectations. When using mocked unit tests for APIs, we would have stubbed APIs and mocked the behavior. From a consumer point of view, these types of tests will ensure that the client is matching our expectations. It is essential to note that if the producer side changes the API, those tests will not fail. And it is imperative to define what the test is covering.
// the response we expect is represented in the task1.json file
private Resource taskOne = new ClassPathResource("task1.json");
@Autowired
private TodayClient todayClient;
@Test
public void createNewTask_expectTaskIsCreated() {
WireMock.stubFor(WireMock.post(WireMock.urlMatching("/tasks"))
.willReturn(WireMock.aResponse()
.withHeader(HttpHeaders.CONTENT_TYPE, MediaType.APPLICATION_JSON_UTF8_VALUE)
.withStatus(HttpStatus.OK.value())
.withBody(transformResourceJsonToString(taskOne))));
Task tasks = todayClient.createTask(new Task(null, "runUTest", "Run Test", false, true));
BDDAssertions.then(tasks.getId()).isEqualTo("1");Snippet 6: A consumer test doing assertions on its own defined response
Component tests
Microservice architecture can grow fast, and so the component under test might be integrating with multiple other components and multiple infrastructure services. Until now, we have covered white-box testing with unit tests and narrow integration tests to test the CUT crossing the boundary to integrate with another service.
The fastest type of component testing is the in-process approach, where, alongside the use of test doubles and in-memory data stores, testing remains within boundaries. The main disadvantage of this approach is that the deployable production service is not fully tested; on the contrary, the component requires changes to wire the application differently. The preferred method is out-of-process component testing. These are like end-to-end tests, but with all external collaborators changed out with test doubles, by doing so, it exercises the fully deployed artifact making use of real network calls. The test would be responsible for properly configuring any externals services as stubs.
@Ignore
@RunWith(SpringRunner.class)
@SpringBootTest(classes = { TodayConfiguration.class, TodayIntegrationApplication.class,
CloudFoundryClientConfiguration.class })
public class BaseFunctionalitySteps {
@Autowired
private CloudFoundryOperations cf;
private static File manifest = new File(".\\manifest.yml");
@Autowired
private TodayClient client;
// Any stubs required
. . .
public void setup() {
cf.applications().pushManifest(PushApplicationManifestRequest.builder()
.manifest(ApplicationManifestUtils.read(manifest.toPath()).get(0)).build()).block();
}
. . .
// Any calls required by tests
public void requestForAllTasks() {
this.client.getTodoTasks();
}
}Snippet 7: Deployment of the manifest on CloudFoundry and any calls required by tests
Cloud Foundry is one of the options used for container-based testing architectures. “It is an open-source cloud application platform that makes it faster and easier to build, test, deploy, and scale applications.” The following is the manifest.yml, a file that defines the configuration of all applications in the system. This file is used to deploy the actual service in the production-ready format on the Pivotal organization’s space where the MongoDB service is already set up, matching the production version.
---
applications:
- name: today
instances: 1
path: ../today/target/today-0.0.1-SNAPSHOT.jar
memory: 1024M
routes:
- route: today.cfapps.io
services:
- mongo-itSnippet 8: Deployment of one instance of the service depending on mongo service
When opting for the out-of-process approach, keep in mind that actual boundaries are under test, and thus, tests end up being slower since there are network and database interactions. It would be ideal to have those test suites written in a separate module. To be able to run them separately at a different maven stage instead of the usual ‘test’ phase.
Since the emphasis of the tests is on the component itself, tests cover the primary responsibilities of the component while purposefully neglecting any other part of the system.
Cucumber, a software tool that supports Behavior-Driven Development, is an option to define such behavioral tests. With its plain language parser, Gherkin, it ensures that customers can easily understand all tests described. The following Cucumber feature file is ensuring that our component implementation is matching the business requirements for that particular feature.
Feature: Tasks
Scenario: Retrieving one task from list
Given the component is running
And the data consists of one or more tasks
When user requests for task x
Then the correct task x is returned
Scenario: Retrieving all lists
Given the data consists of one or more tasks
When user requests for all tasks
Then all tasks in database are returned
Scenario: Negative Test
Given the component is not running
When user requests for task x it fails with response 404Snippet 9: A feature file defining BDD tests
End-to-end tests
Similar to component tests, the aim of these end-to-end tests is not to perform code coverage but to ensure that the system meets the business scenarios requested. The difference is that in end-to-end testing, all components are up and running during the test.
As per the testing pyramid diagram, the number of end-to-end tests decreases further, taking into consideration the slowness they might cause. The first step is to have the setup running, and for this example, we will be leveraging docker.
version: '3.7'
services:
today-app:
image: today-app:1
container_name: "today-app"
build:
context: ./
dockerfile: DockerFile
environment:
- SPRING_DATA_MONGODB_HOST=mongodb
volumes:
- /data/today-app
ports:
- "8082:8080"
links:
- mongodb
depends_on:
- mongodb
mongodb:
image: mongo:3.2
container_name: "mongodb"
restart: always
environment:
- AUTH=no
- MONGO_DATA_DIR=/data/db
- MONGO_LOG_DIR=/dev/log
volumes:
- ./data:/data
ports:
- 27017:27017
command: mongod --smallfiles --logpath=/dev/null # --quietSnippet 10: The docker.yml definition used to deploy the defined service and the specified version of mongo as containers
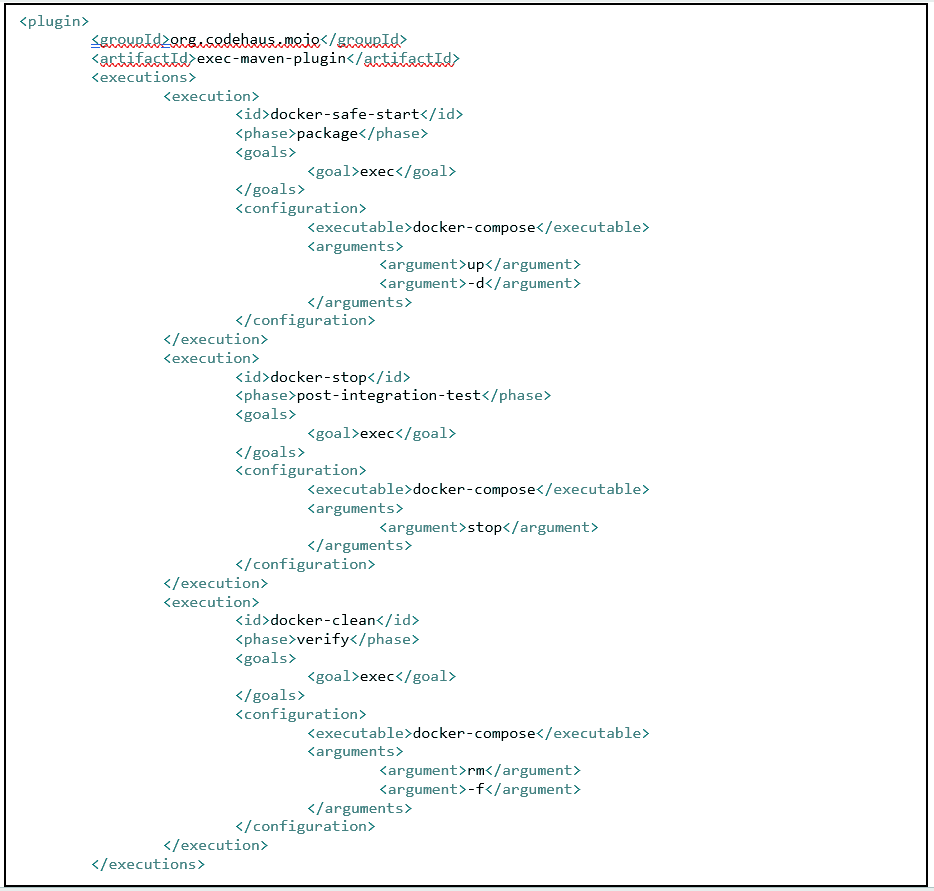
As per component tests, it makes sense to keep end-to-end tests in a separate module and different phases. The exec-maven-plugin was used to deploy all required components, exec our tests, and finally clean and teardown our test environment.
Since this is a broad-stack test, a smaller selection of tests per feature will be executed. Tests are selected based on perceived business risk. The previous types of tests covered low-level details. That means whether a user story matches the Acceptance Criteria. These tests should also immediately stop a release, as a failure here might cause severe business repercussions.
Conclusion
Handoff centric testing often ends up being a very long process, taking up to weeks until all bugs are identified, fixed, and a new deployment readied. Feedback is only received after a release is made, making the lifespan of a version of our quickest possible turnaround time.
The continuous testing approach ensures immediate feedback. Meaning the DevOps engineer is immediately aware of whether the feature implemented is production-ready or not, depending on the outcome of the tests run. From unit tests up to end-to-end tests, they all assist in speeding up the assessment process.
Microservices architecture helps create faster rollouts to production since it is domain-driven. It ensures failure isolation and increases ownership. When multiple teams are working on the same project, it’s another reason to adopt such an architecture: To ensure that teams are independent and do not interfere with each other’s work.
Improve testability by moving toward continuous testing. Each microservice has a well-defined domain, and its scope should be limited to one actor. The test cases applied are specific and more concise, and tests are isolated, facilitating releases and faster deployments.
Following the TDD approach, there is no coding unless a failed test returns. This process increases confidence once an iterative implementation results in a successful trial. This process implies that testing happens in parallel with the actual implementation, and all the tests mentioned above are executed before changes reach a staging environment. Continuous testing keeps evolving until it enters the next release stage, that is, a staging environment, where the focus switches to more exhaustive testing such as load testing.
Agile, DevOps, and continuous delivery require continuous testing. The key benefit is the immediate feedback produced from automated tests. The possible repercussions could influence user experience but also have high-risk business consequences. For more information about continuous testing, Contact phoenixNAP today.
Recent Posts
Cloud-Native Application Architecture: The Future of Development?
Cloud native application architecture allows software and IT to work together in a faster modern environment.
Applications designed around cloud-native structure define the difference between how new technology is built, packaged, and distributed, instead of where it was created and stored. When creating these applications, you retain complete control and have the final say in the process.
Even if you are not currently hosting your application in the cloud, this article will influence how you develop modern applications moving forward. Read on to find out what cloud native is, how it works, and it’s future implications.
What is Cloud-Native? Defined
Cloud native in terms of applications are container-based environments or packaged apps of microservices. Cloud-native technologies build applications that contain several services packaged together which are deployed together and managed on cloud infrastructure using DevOps processes which provide uninterrupted delivery workflows. These microservices create what is called the architectural approach, which is in place to create smaller bundled applications.
What is a Cloud-Native Architecture?
Cloud–native architecture is built specifically to run in the cloud.
Cloud-native apps start as packaged software called containers. Containers are run through a virtual environment and become isolated from their original environments to make them independent and portable. You can run your personalized design through test systems to see where it’s located. Once you’ve tested it, you can edit to add or remove options.
Cloud-native development allows you to build and update applications quickly while improving quality and reducing risk. It’s efficient, run responsive, and scalable. These are fault-tolerant apps which be run anywhere, from public or private environments, or in hybrid clouds. You can test and build your application until it is precisely how you want it to be. For development aspects that you are not an expert in, you can easily outsource them.
The architecture of your system can be built up with the help of microservices. With the help of these services, you can set up the smaller parts of your apps individually, instead of reworking the entire app, all at once. More specifically, with DevOps and containers, applications become easier to update and release. As a collection of loosely connected services, such as microservices are easier to upgrade instead of waiting for one significant release which takes more time and effort.
Lastly, you’ll want to make sure your application has access to the elasticity of the cloud. With this elasticity it allows your developers to push code to production much faster than in traditional server-based models. You can move and scale your app’s resources at any time.
What Are The Characteristics of Cloud Native Applications?
Now that you know the basics about cloud-native apps, here are a few design princicples that you discuss with your developer in the development stages:
Develop With The Best Languages And Frameworks
All services of cloud-native applications are made using the best languages and frameworks. Make sure you can choose what language and framework suites your apps best.
Build With APIs For Collaboration & Interaction
Find out if you’ll be using fine-grained API-driven services for interaction and collaborating your apps, which are based on different protocols for different parts of the app. For example, Google’s open-source remote procedure call, or gRPC, is used for communication inside different services.
Agile DevOps & Automation
Confirm the capability of your app of becoming fully automated, to manage large applications.
How is your application being defined via protocols? Such protocols are CPU and storage quotas and network policies. The difference between you and an IT department when it comes to these protocols is that you are the owner and have access to everything, the department doesn’t.
Managing your app through DevOps will give your app its own independent life. See how different pipelines may work together to send out and manage your application.
Building Cloud-Native Applications
Application development will differ from developer to developer, depending on their skills and capabilities. Common to most cloud-native apps are the following characteristics, which are added in during the development process.
- Updates – Your app will always be available and up to date.
- Multitenancy – The app will work in a virtual space, sharing resources with other applications.
- Downtime – If a cloud provider has an outage, another data center can pick up where it left off.
- Automation – Speed, and agility rely on audited, reliable, and proven processes that are repeated, as needed.
- Languages – Cloud-native apps can be written in HTML, Java, .Net, PHP, Ruby, CSS, JavaScript, Node.js, Python, and Go, never in C/C++, C#, or any virtual studio language.
- Statelessness – With cloud-native apps being loosely coupled, apps aren’t tied to anything. The app stores itself in a database or another external entity, but you can still find them easily.
- Designed modularly – Microservices run the functions of your app, they can be shut off when not needed, or be updated in one section, rather than the entire app being shut down.
The Future of Cloud-Native Technologies
Cloud-native has already proven with its efficiencies that it is the future of developing software. By 2025, 80% of enterprise apps will become cloud-based or be in the process of transferring themselves over to cloud-native apps. IT departments are already switching to developing cloud-native apps to save money and keep their designs secure off-site, safe from competitors.
Adoption now will save yourself the hassle of doing it later, when it’s more expensive.
By switching over to cloud-native apps, you’ll be able to see first-hand what they have to offer and benefit from running them yourself for years to come. Now, that you know how to take advantage of new types of infrastructure, you can continue to improve it by giving your app developers the tools they need. Go cloud-native and get the benefits of flexible, scalable, reusable apps that use the best container and cloud technology available.
What to Look for When Outsourcing Cloud Native Apps
During the planning process, many companies decide to hire a freelancer to help out in developing and executing a cloud-native strategy. It pays off to have a developer experienced in increasing the speed of applications development and organizing compute resources across different environments. It can save you time, money, and a lot of frustration.
When looking for an application developer remember to take these things into consideration,
- Trust – Ensure that they will keep your information safe and secure
- Quality – Have they produced and provided high quality services to other businesses?
- Price – In creating your own apps, you don’t want to overspend Compare process and services to keep prices down
Cloud-native development helps your company derive more value from hybrid cloud architecture. It’s so important to partnerwith a company or contractor that has experience and a great track record.
Go cloud-native and partner with PhoenixNAP Global IT Services. Contact us today for more information.
Recent Posts
What is SDLC? Phases of Software Development, Models, & Best Practices
SDLC, or Software Development Life Cycle, is a set of steps used to create software applications. These steps divide the development process into tasks that can then be assigned, completed, and measured.
What is the Software Development Life Cycle?
Software Development Life Cycle is the application of standard business practices to building software applications. It’s typically divided into six to eight steps: Planning, Requirements, Design, Build, Document, Test, Deploy, Maintain. Some project managers will combine, split, or omit steps, depending on the project’s scope. These are the core components recommended for all software development projects.
SDLC is a way to measure and improve the development process. It allows a fine-grain analysis of each step of the process. This, in turn, helps companies maximize efficiency at each stage. As computing power increases, it places a higher demand on software and developers. Companies must reduce costs, deliver software faster, and meet or exceed their customers’ needs. SDLC helps achieve these goals by identifying inefficiencies and higher costs and fixing them to run smoothly.
How the Software Development Life Cycle Works
The Software Development Life Cycle simply outlines each task required to put together a software application. This helps to reduce waste and increase the efficiency of the development process. Monitoring also ensures the project stays on track, and continues to be a feasible investment for the company.
Many companies will subdivide these steps into smaller units. Planning might be broken into technology research, marketing research, and a cost-benefit analysis. Other steps can merge with each other. The Testing phase can run concurrently with the Development phase, since developers need to fix errors that occur during testing.
The Seven Phases of the SDLC
1. Planning
In the Planning phase, project leaders evaluate the terms of the project. This includes calculating labor and material costs, creating a timetable with target goals, and creating the project’s teams and leadership structure.
Planning can also include feedback from stakeholders. Stakeholders are anyone who stands to benefit from the application. Try to get feedback from potential customers, developers, subject matter experts, and sales reps.
Planning should clearly define the scope and purpose of the application. It plots the course and provisions the team to effectively create the software. It also sets boundaries to help keep the project from expanding or shifting from its original purpose.
2. Define Requirements
Defining requirements is considered part of planning to determine what the application is supposed to do and its requirements. For example, a social media application would require the ability to connect with a friend. An inventory program might require a search feature.
Requirements also include defining the resources needed to build the project. For example, a team might develop software to control a custom manufacturing machine. The machine is a requirement in the process.
3. Design and Prototyping
The Design phase models the way a software application will work. Some aspects of the design include:
Architecture – Specifies programming language, industry practices, overall design, and use of any templates or boilerplate
User Interface – Defines the ways customers interact with the software, and how the software responds to input
Platforms – Defines the platforms on which the software will run, such as Apple, Android, Windows version, Linux, or even gaming consoles
Programming – Not just the programming language, but including methods of solving problems and performing tasks in the application
Communications – Defines the methods that the application can communicate with other assets, such as a central server or other instances of the application
Security – Defines the measures taken to secure the application, and may include SSL traffic encryption, password protection, and secure storage of user credentials
Prototyping can be a part of the Design phase. A prototype is like one of the early versions of software in the Iterative software development model. It demonstrates a basic idea of how the application looks and works. This “hands-on” design can be shown to stakeholders. Use feedback o improve the application. It’s less expensive to change the Prototype phase than to rewrite code to make a change in the Development phase.
4. Software development
This is the actual writing of the program. A small project might be written by a single developer, while a large project might be broken up and worked by several teams. Use an Access Control or Source Code Management application in this phase. These systems help developers track changes to the code. They also help ensure compatibility between different team projects and to make sure target goals are being met.
The coding process includes many other tasks. Many developers need to brush up on skills or work as a team. Finding and fixing errors and glitches is critical. Tasks often hold up the development process, such as waiting for test results or compiling code so an application can run. SDLC can anticipate these delays so that developers can be tasked with other duties.
Software developers appreciate instructions and explanations. Documentation can be a formal process, including wiring a user guide for the application. It can also be informal, like comments in the source code that explain why a developer used a certain procedure. Even companies that strive to create software that’s easy and intuitive benefit from the documentation.
Documentation can be a quick guided tour of the application’s basic features that display on the first launch. It can be video tutorials for complex tasks. Written documentation like user guides, troubleshooting guides, and FAQ’s help users solve problems or technical questions.
5. Testing
It’s critical to test an application before making it available to users. Much of the testing can be automated, like security testing. Other testing can only be done in a specific environment – consider creating a simulated production environment for complex deployments. Testing should ensure that each function works correctly. Different parts of the application should also be tested to work seamlessly together—performance test, to reduce any hangs or lags in processing. The testing phase helps reduce the number of bugs and glitches that users encounter. This leads to a higher user satisfaction and a better usage rate.
6. Deployment
In the deployment phase, the application is made available to users. Many companies prefer to automate the deployment phase. This can be as simple as a payment portal and download link on the company website. It could also be downloading an application on a smartphone.
Deployment can also be complex. Upgrading a company-wide database to a newly-developed application is one example. Because there are several other systems used by the database, integrating the upgrade can take more time and effort.
7. Operations and Maintenance
At this point, the development cycle is almost finished. The application is done and being used in the field. The Operation and Maintenance phase is still important, though. In this phase, users discover bugs that weren’t found during testing. These errors need to be resolved, which can spawn new development cycles.
In addition to bug fixes, models like Iterative development plan additional features in future releases. For each new release, a new Development Cycle can be launched.
SDLC Models & Methodologies Explained
Waterfall
The Waterfall SDLC model is the classic method of development. As each phase completes, the project spills over into the next step. This is a tried-and-tested model, and it works. One advantage of the Waterfall model is each phase can be evaluated for continuity and feasibility before moving on. It’s limited in speed, however, since one phase must finish before another can begin.
Agile
The AGILE model was designed by developers to put customer needs first. This method focuses strongly on user experience and input. This solves much of the problems of older applications that were arcane and cumbersome to use. Plus, it makes the software highly responsive to customer feedback. Agile seeks to release software cycles quickly, to respond to a changing market. This requires a strong team with excellent communication. It can also lead to a project going off-track by relying too heavily on customer feedback.
Iterative
In the Iterative development model, developers create an initial basic version of the software quickly. Then they review and improve on the application in small steps (or iterations). This approach is most often used in very large applications. It can get an application up and functional quickly to meet a business need. However, this process can exceed its scope quickly and risks using unplanned resources.
DevOps
The DevOps security model incorporates operations – the people who use the software – into the development cycle. Like Agile, this seeks to improve the usability and relevance of applications. One significant advantage of this model is the feedback from actual software users on the design and implementation steps. One drawback is that it requires active collaboration and communication. Those additional costs can be offset by automating parts of the development process. Read our detailed comparison of devops vs. agile.
Other models
Many other SDLC models are essentially a variant of these core processes. Organizations use LEAN manufacturing processes for software development. V-shaped development is a type of Waterfall that implements testing, verification, and validation. Spiral development may pick and choose models for each step in the development process.
Best Practices Of Software Development
In addition to the models and stages of software development, there are a few other helpful practices. These can be applied to part or all of the development cycle.
Source Control
Source Control is a security plan to secure your working code. Implement Source Control by keeping the code in a single location, with secure and logged access. This could be a physical location where files are stored and accessed in a single room in the building. It could also be a virtual space where users can log in with an encrypted connection to a cloud-based development environment.
Source Control applications include a change management system to track work done by individuals or teams. As with any storage, use a backup system to record development progress in case of a disaster.
Continuous Integration
Continuous Integration evolved out of a case of what not to do. CI works to make sure each component is compatible through the whole development cycle. Before CI, different teams would build their own projects independently. This created significant challenges at the end when developers stitched the application together. Continuous Integration ensures all teams use similar programming languages and libraries, and helps prevent conflicts and duplicated work.
SDLC Management Systems
A software development cycle management system works to control and manage each step of the development cycle. Management Systems add transparency to each phase and the project as a whole. They also add analytics, bug-tracking, and work management systems. These metrics or KPI’s can be used to improve parts of the cycle that aren’t running efficiently.
Conclusion: The Process for Software Development
SDLC shows you what’s happening, and exactly where your development process can improve.
Like many business processes, SDLC aims to analyze and improve the process of creating software. It creates a scalable view of the project, from day-to-day coding to managing production dates.
Recent Posts
17 Best Security Penetration Testing Tools The Pros Use
Are you seeking the best penetration testing tool for your needs? We have you covered.
Penetration testing tools are software applications used to check for network security threats.
Each application on this list provides unique benefits. Easy comparison helps you determine whether the software is the right choice for your business. Let’s dive in and discover the latest security software options on the market.
What Is Penetration Testing?
Penetration testing, also known as pen testing, means computer securities experts use to detect and take advantage of security vulnerabilities in a computer application. These experts, who are also known as white-hat hackers or ethical hackers, facilitate this by simulating real-world attacks by criminal hackers known as black-hat hackers.
In effect, conducting penetration testing is similar to hiring security consultants to attempt a security attack of a secure facility to find out how real criminals might do it. The results are used by organizations to make their applications more secure.
How Penetration Tests Work
First, penetration testers must learn about the computer systems they will be attempting to breach. Then, they typically use a set of software tools to find vulnerabilities. Penetration testing may also involve social engineering hacking threats. Testers will try to gain access to a system by tricking a member of an organization into providing access.
Penetration testers provide the results of their tests to the organization, which are then responsible for implementing changes that either resolve or mitigate the vulnerabilities.
 Types of Penetration Tests
Types of Penetration Tests
Penetration testing can consist of one or more of the following types of tests:
White Box Tests
A white box test is one in which organizations provide the penetration testers with a variety of security information relating to their systems, to help them better find vulnerabilities.
Blind Tests
A blind test, known as a black-box test, organizations provide penetration testers with no security information about the system being penetrated. The goal is to expose vulnerabilities that would not be detected otherwise.
Double-Blind Tests
A double-blind test, which is also known as a covert test, is one in which not only do organizations not provide penetration testers with security information. They also do not inform their own computer security teams of the tests. Such tests are typically highly controlled by those managing them.
External Tests
An external test is one in which penetration testers attempt to find vulnerabilities remotely. Because of the nature of these types of tests, they are performed on external-facing applications such as websites.
Internal Tests
An internal test is one in which the penetration testing takes place within an organization’s premises. These tests typically focus on security vulnerabilities that someone working from within an organization could take advantage of.
Top Penetration Testing Software & Tools
1. Netsparker
Netsparker Security Scanner is a popular automatic web application for penetration testing. The software can identify everything from cross-site scripting to SQL injection. Developers can use this tool on websites, web services, and web applications.
The system is powerful enough to scan anything between 500 and 1000 web applications at the same time. You will be able to customize your security scan with attack options, authentication, and URL rewrite rules. Netsparker automatically takes advantage of weak spots in a read-only way. Proof of exploitation is produced. The impact of vulnerabilities is instantly viewable.
Benefits:
- Scan 1000+ web applications in less than a day!
- Add multiple team members for collaboration and easy shareability of findings.
- Automatic scanning ensures a limited set up is necessary.
- Searches for exploitable SQL and XSS vulnerabilities in web applications.
- Legal web application and regulatory compliance reports.
- Proof-based scanning Technology guarantees accurate detection.
2. Wireshark
Once known as Ethereal 0.2.0, Wireshark is an award-winning network analyzer with 600 authors. With this software, you can quickly capture and interpret network packets. The tool is open-source and available for various systems, including Windows, Solaris, FreeBSD, and Linux.
Benefits:
- Provides both offline analysis and live-capture options.
- Capturing data packets allows you to explore various traits, including source and destination protocol.
- It offers the ability to investigate the smallest details for activities throughout a network.
- Optional adding of coloring rules to the pack for rapid, intuitive analysis.
3. Metasploit
Metasploit is the most used penetration testing automation framework in the world. Metasploit helps professional teams verify and manage security assessments, improves awareness, and arms and empowers defenders to stay a step ahead in the game.
It is useful for checking security and pinpointing flaws, setting up a defense. An Open source software, this tool will allow a network administrator to break in and identify fatal weak points. Beginner hackers use this tool to build their skills. The tool provides a way to replicates websites for social engineers.
Benefits:
- Easy to use with GUI clickable interface and command line.
- Manual brute-forcing, payloads to evade leading solutions, spear phishing, and awareness, an app for testing OWASP vulnerabilities.
- Collects testing data for over 1,500 exploits.
- MetaModules for network segmentation tests.
- You can use this to explore older vulnerabilities within your infrastructure.
- Available on Mac Os X, Windows and Linux.
- Can be used on servers, networks, and applications.
4. BeEF
This is a pen testing tool and is best suited for checking a web browser. Adapted for combating web-borne attacks and could benefit mobile clients. BeEF stands for Browser Exploitation Framework and uses GitHub to locate issues. BeEF is designed to explore weaknesses beyond the client system and network perimeter. Instead, the framework will look at exploitability within the context of just one source, the web browser.
Benefits:
- You can use client-side attack vectors to check security posture.
- Connects with more than one web browser and then launch directed command modules.
5. John The Ripper Password Cracker
Passwords are one of the most prominent vulnerabilities. Attackers may use passwords to steal credentials and enter sensitive systems. John the Ripper is the essential tool for password cracking and provides a range of systems for this purpose. The pen testing tool is a free open source software.
Benefits:
- Automatically identifies different password hashes.
- Discovers password weaknesses within databases.
- Pro version is available for Linux, Mac OS X, Hash Suite, Hash Suite Droid.
- Includes a customizable cracker.
- Allows users to explore documentation online. This includes a summary of changes between separate versions.
6. Aircrack
Aircrack NG is designed for cracking flaws within wireless connections by capturing data packets for an effective protocol in exporting through text files for analysis. While the software seemed abandoned in 2010, Aircrack was updated again in 2019.
This tool is supported on various OS and platforms with support for WEP dictionary attacks. It offers an improved tracking speed compared to most other penetration tools and supports multiple cards and drivers. After capturing the WPA handshake, the suite is capable of using a password dictionary and statistical techniques to break into WEP.
Benefits:
- Works with Linux, Windows, OS X, FreeBSD, NetBSD, OpenBSD, and Solaris.
- You can use this tool to capture packets and export data.
- It is designed for testing wifi devices as well as driver capabilities.
- Focuses on different areas of security, such as attacking, monitoring, testing, and cracking.
- In terms of attacking, you can perform de-authentication, establish fake access points, and perform replay attacks.
7. Acunetix Scanner
Acutenix is an automated testing tool you can use to complete a penetration test. The tool is capable of auditing complicated management reports and issues with compliance. The software can handle a range of network vulnerabilities. Acunetix is even capable of including out-of-band vulnerabilities.
The advanced tool integrates with the highly enjoyed Issue Trackers and WAFs. With a high-detection rate, Acunetix is one of the industry’s advanced Cross-site scripting and SQLi testing, which includes sophisticated advanced detection of XSS.
Benefits:
- The tool covers over 4500 weaknesses, including SQL injection as well as XSS.
- The Login Sequence Recorder is easy-to-implement and scans password-protected areas.
- The AcuSensor Technology, Manual Penetration tools, and Built-in Vulnerability Management streamline black and white box testing to enhance and enable remediation.
- Can crawl hundreds of thousands of web pages without delay.
- Ability to run locally or through a cloud solution.
8. Burp Suite Pen Tester
There are two different versions of the Burp Suite for developers. The free version provides the necessary and essential tools needed for scanning activities. Or, you can opt for the second version if you need advanced penetration testing. This tool is ideal for checking web-based applications. There are tools to map the tack surface and analyze requests between a browser and destination servers. The framework uses Web Penetration Testing on the Java platform and is an industry-standard tool used by the majority of information security professionals.
Benefits:
- Capable of automatically crawling web-based applications.
- Available on Windows, OS X, Linux, and Windows.
9. Ettercap
The Ettercap suite is designed to prevent man in the middle attacks. Using this application, you will be able to build the packets you want and perform specific tasks. The software can send invalid frames and complete techniques which are more difficult through other options.
Benefits:
- This tool is ideal for deep packet sniffing as well as monitoring and testing LAN.
- Ettercap supports active and passive dissection of protections.
- You can complete content filtering on the fly.
- The tool also provides settings for both network and host analysis.
10. W3af
W3af web application attack and audit frameworks are focused on finding and exploiting vulnerabilities in all web applications. Three types of plugins are provided for attack, audit, and discovery. The software then passes these on to the audit tool to check for flaws in the security.
Benefits:
- Easy to use for amateurs and powerful enough for developers.
- It can complete automated HTTP request generation and raw HTTP requests.
- Capability to be configured to run as a MITM proxy.
11. Nessus
Nessus has been used as a security penetration testing tool for twenty years. 27,000 companies utilize the application worldwide. The software is one of the most powerful testing tools on the market with over 45,000 CEs and 100,000 plugins. Ideally suited for scanning IP addresses, websites and completing sensitive data searches. You will be able to use this to locate ‘weak spots’ in your systems.
The tool is straightforward to use and offers accurate scanning and at the click of a button, providing an overview of your network’s vulnerabilities. The pen test application scans for open ports, weak passwords, and misconfiguration errors.
Benefits:
- Ideal for locating and identify missing patches as well as malware.
- The system only has .32 defects per every 1 million scans.
- You can create customized reports, including types of vulnerabilities by plugin or host.
- In addition to web application, mobile scanning, and cloud environment, the tool offers priority remediation.
12. Kali Linux
Kali Linux advanced penetration testing software is a Linux distribution used for penetration testing. Many experts believe this is the best tool for both injecting and password snipping. However, you will need skills in both TCP/IP protocol to gain the most benefit. An open-source project, Kali Linux, provides tool listings, version tracking, and meta-packages.
Benefits:
- With 64 bit support, you can use this tool for brute force password cracking.
- Kali uses a live image loaded into the RAM to test the security skills of ethical hackers.
- Kali has over 600 ethical hacking tools.
- Various security tools for vulnerability analysis, web applications, information gathering, wireless attacks, reverse engineering, password cracking, forensic tools, web applications, spoofing, sniffing, exploitation tools, and hardware hacking are available.
- Easy integration with other penetration testing tools, including Wireshark and Metasploit.
- The BackTrack provides tools for WLAN and LAN vulnerability assessment scanning, digital forensics, and sniffing.
13. SQLmap
SQLmap is an SQL injection takeover tool for databases. Supported database platforms include MySQL, SQLite, Sybase, DB2, Access, MSSQL, PostgreSQL. SQLmap is open-source and automates the process of exploiting database servers and SQL injection vulnerabilities.
Benefits:
- Detects and maps vulnerabilities.
- Provides support for all injection methods: Union, Time, Stack, Error, Boolean.
- Runs software at the command line and can be downloaded for Linux, Mac OS, and Windows systems
14. (SET) Social Engineer Toolkit
Social engineering is the primary focus of the toolkit. Despite the aim and focus, human beings are not the target of the vulnerability scanner.
Benefits:
- It has been featured at top cybersecurity conferences, including ShmooCon, Defcon, DerbyCon and is an industry-standard for penetration tests.
- SET has been downloaded over 2 million times.
- An open-source testing framework designed for social engineering detection.
15. Zed Attack Proxy
OWASP ZAP (Zed Attack Proxy) is part of the free OWASP community. It is ideal for developers and testers that are new to penetration testing. The project started in 2010 and is improved daily. ZAP runs in a cross-platform environment creating a proxy between the client and your website.
Benefits:
- 4 modes available with customizable options.
- To install ZAP, JAVA 8+ is required on your Windows or Linux system.
- The help section is comprehensive with a Getting Started (PDF), Tutorial, User Guide, User Groups, and StackOverflow.
- Users can learn all about Zap development through Source Code, Wiki, Developer Group, Crowdin, OpenHub, and BountySource.
16. Wapiti
Wapiti is an application security tool that allows black box testing. Black box testing checks web applications for potential liabilities. During the black box testing process, web pages are scanned, and the testing data is injected to check for any lapses in security.
- Experts will find ease-of-usability with the command-line application.
- Wapiti identifies vulnerabilities in file disclosure, XSS Injection, Database injection, XXE injection, Command Execution detection, and easily bypassed compromised .htaccess configurations.
17. Cain & Abel
Cain & Abel is ideal for procurement of network keys and passwords through penetration. The tool makes use of network sniffing to find susceptibilities.
- The Windows-based software can recover passwords using network sniffers, cryptanalysis attacks, and brute force.
- Excellent for recovery of lost passwords.
Get Started with Penetration Testing Software
Finding the right pen testing software doesn’t have to be overwhelming. The tools listed above represent some of the best options for developers.
Remember one of the best techniques to defend your IT structure is to use penetration testing proactively. Assess your IT security by looking for and discovering issues before potential attackers do.
Recent Posts
52 Best DevOps Tools For Automation, Monitoring, & Development (Definitive List)
An essential aspect of software delivery and development is the collaboration and communication that takes place between operations professionals and project management teams.
IT experts, programmers, web application developers, and DevOps experts have worked together to create numerous tools that make this possible. Discover what DevOps tools are, why you need to track KPIs and metrics, and how to choose the right one.
What is DevOps?
In short, the term “DevOps” is a combination of the terms ‘development and operations’.
The term refers to the tools, people, and processes that work together in software development processes. The primary goal is to create a faster, more streamlined delivery.
DevOps use technology and various tools of automation to increase and improve productivity across teams working together. When you are working to scale to your project, the top DevOps tools are going to help you get there faster.
Devops Development Tools
1. Docker
Docker has been a forerunner in containerization. Regarded by many to be as crucial to DevOps as Word to writing or Photoshop to image-editing.
Docker provides agile operations and integrated container security for cloud-native and legacy applications.
Docker automates app deployment and makes distributed development easy. Dependency management isn’t a significant concern with Docker as it can package dependencies.
- Secure and automated supply chain to reduce time to value.
- Google Cloud and AWS both offer built-in support for Docker.
- New and existing applications are supported.
- Turnkey enterprise-ready container platform.
- Docker containers are platform-independent with virtual machine environments.
2. Kubernetes
Kubernetes builds on what Docker started in the containerization field.
Kubernetes was developed by a pair of Google engineers looking to apply Docker’s concepts to scalable projects. The result was a tool that can group containers by logical categorization.
Kubernetes may not be necessary for small teams but have proven vital for large projects.
For large teams, an application like Kubernetes is vital to managing what might otherwise be unwieldy.
- Kubernetes can deploy to multiple computers through automated distribution.
- Kubernetes is primarily useful in streamlining complex projects across large teams.
- Kubernetes is the first container orchestration tool developed for public release.
3. Puppet Enterprise
Puppet Enterprise is a configuration management tool favored among large teams. Puppet Enterprise automates the infrastructure management process to reach a ship date quickly and securely.
Puppet Enterprise is useful for small teams and vital for large projects. It allows for the management of multiple coding and asset teams and many resources.
- Integrates well with most major DevOps tools.
- Puppet features more than five thousand modules.
- Offers real-time reports, node management, and access control delineated by role.
4. Ansible
Ansible is a lightweight option to Puppet.
Ideal for smaller teams in need of a fast, user-friendly configuration management tool. Developers working with dozens or hundreds of team members should use Puppet. Developers in need of a quick, light, and secure management tool should consider Ansible.
- Runs clean and light with no daemons or agents in the background.
- Features several modules.
- Integrates neatly with Jenkins.
5. Gradle
Gradle has been around since 2009 as an alternative to Apache Ant and Maven. A building tool that allows users to code in C++, Python, and Java, among other languages.
Supported by Netbeans, IntelliJ IDEA and Eclipse, and used by Google as Android Studio’s official build tool. Gradle has a learning curve owing to its Groovy-based DSL. Gradle is worth that extra time investment for the time it will save in the long run.
- Gradle is estimated to be 100 times faster than Maven. The increase in speed owes to Gradle’s daemon and build cache.
- The team has released a Kotlin-based DSL for users who would rather skip the learning process for Groovy.
- GWorkspace should be familiar to Maven users.
6. CodePen
CodePen is made with both developers and designers in mind. It is a social development platform meant to showcase websites. Developers can build web projects online and then instantly share them.
CodePen’s influence extends to building test cases and fueling innovation. Coding results are viewable in real-time. CodePen is a place for new ideas, to improve skills, socialize, and showcase talents for an employer.
- The code can be written in a browser.
- A variable editor is suitable for different code levels.
- Focuses on preprocessing syntaxes that associate directly with HTML, CSS, and JavaScript.
- Users have access to a blog, as well as a collection of projects.
7. TypeScript
TypeScript is a popular solution developed on GitHub. It works with any JavaScript host which supports ECMAScript 3 and newer environments. TypeScript is best suited for large apps with robust components and productivity.
Developers use TypeScript to leverage complex code, interfaces, and libraries. It increases efficiency when coordinating JS libraries and workflows. Code refactoring, defining interfaces, static checking, and insights into the behavior of libraries work seamlessly with TypeScript.
- TypeScript is an open-source solution.
- It is especially useful for Angular projects.
- Installable via a Node.js package.
- Works with Visual Studio, Sublime Text, Atom, Eclipse, and more.
- Features include optical static typing, overwriting properties, mock-up spread behavior, and strict checking options.
8. Vue.js
Vue.js is a front-end solution for building web interfaces. It is a JavaScript library that exists as an elaborate framework. Vue owes some of its success to its streamlined design and cutting-edge approach.
Vue is easy to learn. Its scaled solutions appeal to a variety of developers. UIs and single-page applications can be built using Vue.
- Vue is a progressive JavaScript framework existing as an MIT-licensed open source project.
- Several tools are coordinated with the JavaScript core.
- Vue is widely accepted by the developer community and is continuing to grow.
- Designed from the ground up to scale as an overview library to help streamline complex single-page applications.
9. Angular
Angular has been one of the top front-end solutions for years. Its success is owed to being a Google product but amassed a diverse following among the Github developer community. Its latest version is considered a significant improvement in technology.
Angular can build web applications for both mobile and desktop platforms. The structured framework dramatically reduces the redundancies associated with writing code.
- Angular is open-source.
- Created from the input of a team at Google, corporations, and individuals.
- Uses HTML as a template language.
- Angular’s HTML extensions facilitate the wide distribution of web applications.
10. Ionic 3
Ionic is a cross-platform software development kit (SDK). It has applications for front-end and mobile app development. However, it is best known for developing hybrid mobile apps.
In addition to mobile, the dynamic SDK can build web-optimized and desktop apps. It achieves this with a single shared code base for all platforms.
Ionic converts HTML, CSS, and JavaScript to native code. The native features of the UI are top-rated, especially among the fast-paced mobile development community.
- Ionic is built on Angular.
- An established community on Slack and StackOverflow provides substantial support.
- Ionic is entirely open-source.
- There is a high availability of plugins and built-in push notifications.
11. Django
Django is a powerful Python web framework designed for experienced developers. But, it can also be quickly learned. Django emphasizes practicality, security, and efficiency to ease the development of database-driven websites.
Django Supports projects on the back-end of development. Developers can work liberally because Django helps them avoid common mistakes. Apps can be written more efficiently using the flexible framework.
Django is an asset to fast-growing sites. It facilitates dynamic applications and rapid scalability.
- Django is a powerful, fast, and open source.
- Applications quickly move from concept to completion.
- Security is fundamental to the framework.
- It is entirely written in Python.
- Associated languages include HTML, CSS, Bootstrap, JavaScript, jQuery, and Python 3.
Continuous Integration DevOps Tools
12. Bamboo
A CI/CD server solution developed by Atlassian. Bamboo works from the code phase through to deployment, delivery, and continuous integration.
Compatible with Jira Software, Fisheye, Crucible, and hundreds of other tools. Bamboo is available in a variety of languages. It features a plethora of functions, including those for both deployment and searching.
With dedicated agents, you can run fixes and builds instantly to keep production moving. There is a clear visualization of all JIRA software issues so that each team can decipher what they need to do before deploying and throughout production before anything goes live.
For many users, the cost of Bamboo will make it a hard sell compared to Jenkins. For projects and teams with a budget, Bamboo may be preferable for a few reasons. Pre-built functionalities mean that Bamboo’s automation pipeline takes less time to configure than Jenkins.
- Bamboo’s user interface is intuitive and user-friendly.
- Features tools, tips, and auto-completion.
- Bamboo offers easy integration with branching versions through Git and Mercurial.
- For team leaders with expenses in mind, it can save many development hours.
13. TeamCity
TeamCity allows up to 100 different job configurations.
Three builds are capable of running at the same time, with extra agents allowed to be added as you need them. Before you decide to make any changes, you can run a build, check, and complete automated testing.
Whenever you want to run a report on the build, you can. You don’t have to wait for something to finish up before figuring out something is going wrong.
A forum is available that provides access to peer support, or you can file a request to have a feature fixed or repair any bugs.
14. Chrome DevTools
Chrome DevTools is built into the Google Chrome browser allowing for on-the-fly page edits. The objective of Chrome DevTools is to improve UX and performance.
Users are at the center of Chrome DevTools. Its user-friendly interface caters to everyone, from beginners to experienced users.
- Streamlines operations and quick access for users.
- Improves workflows.
- View and change any page.
- Instantly jump to an element to edit.
- Experienced developers can easily optimize website speeds and inspect network activity.
- Debugging incorporates code pauses with breakpoints, workspaces saving changes, dynamic snippets, reference, and local overrides.
15. Sublime Text
Sublime Text is a text editor for coding, markup, and prose. It is a sophisticated cross-platform solution with a Python programming interface. Sublime Text natively supports languages and plugins under free-software licenses.
As a high-level tool, Sublime Text requires time to master. The focus is on performance over functionality. The UI is friendly but comes with remarkable features.
Plugins augment the built-in functionality of the Python API. Its package ecosystem provides easy access to thousands of community-built items.
- Sublime Text is free to evaluate, but is proprietary and requires the purchase of a license.
- The evaluation period currently has no time limit.
- Powered by a customizable UI toolkit.
16. Sumo Logic
The main focus of Sumo Logic is log data. It’s built to help you understand your log data and make more sense of it. To do this, you call upon a variety of features that analyze this data in immense detail.
Sumo Logic can provide your organization with a deep level of security analytics by merging this with integrated threat intelligence.
- Can be scaled infinitely
- Works with Azure Hybrid applications
- Helps reduce your downtime and move to a more proactive monitoring system
17. Postman
Postman is used for performing integration testing on APIs. It delivers speed, efficiency, and improves performance. Postman performs well at both manual and exploratory testing.
The GUI functions can be used as a powerful HTTP client for testing web services. Postman markets itself as the only platform that can satisfy all API needs. It supports all the stages of the API lifecycle.
Developers can automate tests for a variety of environments. These tests can be applied to persistent data, simulations, or other measures of user interaction.
- Developers are onboarded to an API faster.
- Available as a plugin for Google Chrome.
- Built-in-tools are capable of testing, monitoring, automation, debugging, mock servers, and more.
18. Git Extensions
Git Extensions is a standalone GUI for Git used for managing repositories. The shell extension provides context menus for files and directories.
Git Extensions enables the use of Git without the command line. A CLI is unnecessary to control Git.
The ease and extent of its controls make it a top choice among developers. It focuses on intuitive Windows functionality.
- Supports 32bit and 64bit systems.
- Compatible with Linux and Mac OS through Mono.
- Shell extensions integrate with Windows Explorer.
- A Visual Studio extension is available.
Devops Automation Tools
19. Jenkins
A DevOps automation tool, Jenkins is a versatile, customizable open-source CI/CD server.
The Butler-inspired name is fitting. Jenkins can, with proper instruction, perform many of a user’s most tedious and time-consuming tasks for them. Success can be measured at each stage of an automated pipeline, allowing users to isolate specific problem-points.
The pipeline setup can be imposing for first-time users, but it does not take long to learn the interface. Jenkins is a crucial tool for managing difficult and time-consuming projects.
- Jenkins runs on Windows, Linux and Mac OS X.
- Jenkins can be set up with a custom configuration or with plugins.
- Jenkins has been criticized for its UI, which some feel is not user-friendly. Many users take no issue with the interface. This is a concern that seems to come down to personal preference.
20. CA Release Automation
Continuous delivery is possible with CA Release Automation’s deployment that can happen at regulated speeds across your entire enterprise automatically.
What used to take days can be done in just a few minutes so that there is no unexpected work popping up out of nowhere slowing down your productivity. You can be the first one to the market with shorter release cycles that happen up to 20 times faster than before.
Every complicated aspect of applications, environment, and tools are controlled by one program. Your visibility will increase, and you will see your reliability and consistency improve as well. Errors in production have gone down for some as much as 98%. It is both cloud and mainframe ready for quick and easy integration to your existing infrastructures.
21. XebiaLabs
Container, legacy, and cloud environments are all capable of setting up automated deployments with the XebiaLabs software delivery pipeline.
The likelihood of having failed deployments and errors during the process reduces and speeds increase. You stay in control of the deployment with a self-service option.
Visibility improves the status of deployment environments and applications. The DevOps tool can easily be worked in with the current programs and systems that you are already working with so that everything across public and private clouds is completed with ease. Enterprise security and centralized auditing are all capabilities of the XebiaLabs.
Developers can reduce time spent on the administrative side, allowing for much more to be done in a shorter time frame.
22. UrbanCode Deploy
UrbanCode Deploy allows for automated deployments as well as rollbacks of all your applications.
You can update, provision, and de-provision in various cloud environments. Collaborate changes across all your tiers, servers, and components for a more seamless process.
Security differences and configuration can also take place in all different environments. Have a clear visualization of who changed what and what is getting deployed at any given time.
Devops Monitoring Tools
23. Nagios
Nagios is a free tool that is one of the most popular DevOps applications available. Allowing for real-time infrastructure monitoring, Nagios feeds out graphs and reports as you need them, as the data is being produced.
The tool’s reporting provides early detection of outages, security threats, and errors. Plug-ins are a significant draw for Nagios users.
When problems arise, you are made aware of them instantly. Many issues can even be resolved automatically as they are found.
There are thousands of add-ons available for free, as well as many tutorials and how-tos. A large helpful community supports Nagios.
- Free and open-source.
- Available in Nagios Core, Nagios XI, Log Server, and Nagios Fusion. Core is a command-line tool. XI uses a web-based GUI. Log Server searches log data with automatic alerts. Fusion is for simultaneous multiple-network monitoring.
- Nagios demands a lot of set-up time before it is suited to a particular DevOps team’s environment.
24. New Relic
Every change that happens inside of your program can be seen clearly on one platform with New Relic.
Not only do they offer you the opportunity to watch what’s happening, but you can also fix problems, speed up deploy cycles, and take care of other tasks related to DevOps. The team will have the information they need to run everything in a way that works for everyone.
25. Pager Duty
Better customer, business, and employee value is the primary focus of Pager Duty.
They offer over 200 different integrations across multiple tools so that you can ticket, market, and collaborate with what you’ve already established. Some of the other features offered include analytics, on-call management, and modern incident response.
You will have a clear picture of what’s taking place, any disruptions that are occurring, and get patterns in the performance of your builds and productions throughout the delivery. Rapid resolutions, quick collaboration, and business responses are orchestrated and organized for your team.
26. Splunk
Any opportunities that might be available for your company, along with risks, can be visible with the Splunk DevOps product. Splunk uses predictive and actionable insights with artificial intelligence and machine data.
The business analytics can help you in better understand:
- Why you are losing customers,
- How much money you could make in certain situations
- Whether or not the people that are using your programs are accepting of new features and products you introduce.
27. Raygun
Raygun is a monitoring system used to catch errors and crashes.
Raygun recently released an application performance monitoring platform used to diagnose performance issues. Raygun is user-friendly and conducts much of its work with little set-up. Error reports are generated automatically with prioritization letting users know which problems need to be addressed first.
By linking errors to specific points, Raygun can save hours of manual bug fixing work.
- Automatically links errors to specific lines of source code.
- Consolidates both development and operations reporting for all relevant teams.
- Raygun APM can be applied to other DevOps tools like Jenkins to track development at every level.
28. Plutora
Plutora has been dubbed as one of the most complete VSM platforms out there. A VSM (Value Stream Management) tool that’s designed to give you everything you need to scale DevOps throughout your organization. Plutora lets you set up a map to visualize all of your value streams, allowing you to take data from all of your critical systems.
- Plutora includes deployment management, release management, and planning & idea management
- You can manage your ‘Kaizen’ throughout the process at every delivery stage
- vastly improve the speed and quality of your complicated application delivery.
- Contains governance & compliance features that ensure policy adherence for every process
29. Loom Systems
Loom Systems calls upon artificial intelligence and machine learning to help prevent problems in organizations. It does this by predicting what issues may arise, so developers can take steps to stop them from happening.
The core of Loom Systems is ‘Sophie’ – who is essentially your virtual IT assistant. She gives you ideas based on any detected issues as soon as they’re detected. She can also manage your feedback by learning from what went wrong and automatically improving things.
Sophie is currently the only system in the industry that can accurately predict IT issues before they create a negative impact on customers while providing solutions in easy-to-understand terms.
- It’s suggested that around 42% of P1 incidents are predicted using Loom Systems
- Loom can boost business productivity by adding automation
- Provide you with more time to focus on other essential DevOps tasks
30. Vagrant
Vagrant is built around the concept of automation. It can be used in conjunction with other management tools on this list, and it lets you create virtual machine environments all in the same workflow.
By doing this, it gives the entire DevOps team a better environment to continue with development. There’s a shorter set-up time for the development environment, which improves productivity as well.
Many companies have started using Vagrant to help transition into the DevOps culture.
- Vagrant is compatible with various operating systems, including Windows, Mac, and Linux
- Can be used and integrated with Puppet, Ansible, Chef, and more
31. Prometheus
Prometheus is a service monitoring system that helps to power your metrics and alerting. It does this by using a highly dimensional data model, along with powerful queries.
One of the great things about Prometheus is that you can visualize data in a variety of ways. As such, this makes analyzing data far easier for everyone involved.
Plus, you can export data from third-party solutions into Prometheus, which essentially means it works with different DevOps tools, such as Docker.
- Custom libraries that are easy for you to implement
- A very flexible query language
32. Chef
Chef is all about improving your DevOps processes and making life far easier for you. The main focus is on increasing the speed and consistency of tasks, while also enabling you to scale them with relative ease.
The exciting thing about Chef is that it’s a cloud-based system, which means you can access it from any device whenever you want. One of the drawbacks of cloud systems is that they might be unavailable due to server issues. Chef is found to maintain a high level of availability.
With Chef, you can make complicated tasks far easier by calling on automation to carry out different jobs and free up your own time.
- Helps to control your infrastructure
- Is used by big companies like Facebook and Etsy
Devops Collaboration & Planning Tools
33. Git
Remote teams have become standard in software development.
For many software companies, Git is the go-to solution for managing remote teams.
Git is used for tracking a team’s progress on a particular project, saving multiple versions of the source code along the way. Organizations can develop branching versions of the code to experiment without compromising the entire project.
- Git requires a hosted repository. The obvious choice is Github, although competitor Bitbucket has much to offer. Bitbucket offers free unlimited private repos for up to five members of a team.
- Slack can be integrated with either GitHub or Bitbucket.
- Separate branches of source code can be merged through Git.
Source code management tools like Git are necessary for the modern software development field. In that niche, Git stands as the leader.
34. Clarizen
Clarizen is a cloud-based management software DevOps product that makes sure everyone stays involved and engaged in what’s happening with your specific project.
Through aligned communication, you can develop new strategies and share resources. Automated processes can be set with alerts.
Managers can view t in real-time with the 360-degree visualization for the most accurate decisions based on customized data.
35. Slack
Slack enables your team to the opportunity to communicate and collaborate all on one platform.
Valuable information can quickly and easily be shared with everyone involved in a specific project on message boards.
Channels can be set up by topic, team, project, or, however, else you see fit. When information from the conversation is needed, there is a search option that allows for easy access. Slack is compatible with many services and apps you are already using.
36. Basecamp
Basecamp is a way for everyone to stay connected and accountable in an efficient and organized manner. Individual projects can be customized to suit specific requirements.
Each morning, you have the option of getting a summary of the previous day’s activities sent directly to your email. Many functions are available to streamline the process of working within a team:
- Message boards, documents file storage, to-do lists, schedules, check-in questions, and real-time chat.
- Access to clients direct messages
37. Asana
Plan out your team’s projects, assign tasks, set due dates, and stay more organized with Asana. View each stage of the project as it’s happening to ensure things are progressing.
Everyone has a visual representation of the plan and what steps need to be taken to reach the finish line. When something isn’t progressing the way you intended it to, changes can be made shared.
38. NPM
NPM interacts with a remote registry to build JavaScript applications. It focuses on security and collaboration. NPM provides enterprise-grade features while facilitating compliance.
Organizations profit from NPM’s streamlined go-to-market strategies. Zero-configuration functions help to improve team goals by easing collaboration.
NPM assists organizational efforts by simultaneously reducing risk and internal friction. It consolidates resources under a single sign-on to manage user access and permissions. This helps to support operations that depend on structured flows.
- NPM is open-source.
- Interacts with the world’s largest software registry.
- NPM has 100% parity with public registry features, which are in high demand today.
The built-in, zero-friction security design enables greater collaboration and flexibility for on-demand apps.
39. GitKraken
GitKraken incorporates developer experiences to create a cross-platform Git client. It is streamlined for active developers. GitKraken delivers efficiency, reliability, and excellence.
In addition to advanced cross-platform functionality, GitKraken is reportedly a pleasure to use. It is designed with a fast learning curve in mind.
This intuitive GUI client is consistent and reliable. It is a version control system that goes beyond basic software development. Power is merged with ease-of-use through features like quickly viewable information via hovering.
- GitKraken is available on Windows, Mac OS, Ubuntu, and Debian.
- It is built on Electron, an open-source framework.
- A free version is available.
- Among its capabilities are pushing, branching, merging, and rebasing.
- GitKraken is independently developed.
40. Visual Studio
Visual Studio is a Microsoft product. It is an integrated development environment (IDE). Visual Studio has applications for both the web and computer programs.
The broad spectrum of web uses includes websites and associated apps, services, as well as mobile technology. It is considered a go-to, best-in-class solution.
Visual Studio’s Live Share offers benefits beyond Microsoft platforms. It is available for developers and services on any platform and in any language. Both native and managed code can be used.
- Windows availability includes API, Forms, Store, Silverlight, and Presentation Foundation.
- Thirty-six language programs are supported.
- Advanced code editing and debugging for any OS.
- Its app center provides continuous delivery, integration, and learning.
Planning
41. GitLab
GitLab is an internal management solution for git repositories. It offers advantages for the DevOps lifecycle via a web-based engine.
The complete software lifecycle comes under a single application. Starting with project planning and source code management, GitLab extends to the CI/CD pipeline, monitoring, and security. The result is a software lifecycle that is twice as fast.
GitLab established features include planning, creation, management, verification, packaging, release, configuring, monitoring, security, and defense. The defend feature was introduced in 2019. All of the other features have updates and/or expanded functions in the works for 2020.
Available through the GitLab open-source license.
GitLab provides Git repository management, issue tracking, activity feeds, code reviews, and wikis.
42. Trello
Trello is a DevOps collaboration tool that helps improve the organization of your projects. Get more done with Trello by prioritizing projects and improving teamwork.
You can set up different teams and create tasks for everyone to carry out. This ensures that all team members are on the same page and know what they have to do – and what’s essential for them.
Trello allows everyone to interact and communicate with one another on one straightforward and intuitive platform.
- Highly flexible, meaning you can use Trello however you see fit.
- Integrates a range of third-party apps that your team already uses
- Keeps your team in-sync across all devices
Continuous Feedback
43. Mouseflow
Mouseflow focuses on continuous feedback from the customer. It won’t deliver surveys or direct words of feedback, but it does let you see how customers react.
Mouseflow uses heatmaps. You see where all of your visitors are going on your website, and what they’re doing. It’s a genius way of figuring out where the positive and negative aspects of your site lie.
With this tool, you can unlock analytics data that helps you understand why people are possibly leaving your site/application, allowing you to make changes to address this.
- Very easy to use and works on all web browsers
- Contains a Form Analytics feature to see why visitors leave online forms
- Tracks a variety of different funnels
44. SurveyMonkey
There’s no better way to understand what your customers are thinking than asking them.
SurveyMonkey allows you to do that along with providing several other operations, including researching, obtaining new ideas, and analyzing the performance of your business.
Continuous feedback is how to uncover what your clients are expecting from you. Not only can you survey your customers, but you can also use it to find out what your employees are thinking about how things are working within the company.
45. Jira Service Desk
Tracking, obtaining, managing, and addressing customer requests are possible through Jira Service Desk.
It’s where customers can go to ask for help or fill out various forms so that you can get to the bottom of any issues and improve the overall experience of your project so that the people are getting what they want.
Service requests are automatically organized and prioritized by importance with the Jira Service Desk tool.
Your employees can work through the requests quickly to resolve issues more efficiently. When there are critical submissions, an alert will come through, ensuring that you don’t miss anything.
You can also create a resource knowledge base that your clients can use to answer their own questions.
46. SurveyGizmo
This is another feedback tool that works similarly to SurveyMonkey. You can invite people to respond to your surveys and gain a lot of constant information from your customers.
There are many different ways you can construct a survey and select the questions you want to include. With this tool, you’re empowered to make smarter decisions based on the research you generate. There are segmentation and filtering features that help you find out what’s good and bad about your product.
Plus, the surveys look more appealing to potential customers. This could ensure that more people are willing to fill them in.
- Offers quick and easy survey configuration
- Can correlate feedback to positive and negative experiences for a simple overview
Issue Tracking
47. Mantis Bug Tracker
Mantis Bug Tracker provides the ability to work with clients and team members in an efficient, simple, and professional manner.
It’s a practical option for clearing up issues quickly while maintaining a balance of power and simplicity. You have the option of customizing the categories of problems along with workflows and notifications. Get emails sent when there are problems that need to be resolved right away.
You maintain control of your business while allowing specific users access to what you want.
48. WhiteSource Bolt
Security is a critical concern in DevOps.
With WhiteSource Bolt, you have an open-source security tool that helps you zone in on any security issues and fix them right away.
It’s a free tool to use, and you can use it within Azure or GitHub as well. The main aim of the tool is to give you alerts in real-time that show all of your security vulnerabilities. It then gives you some suggested fixes that you can act upon to sure up security and remove the weakness.
- Supports well over 200 different programming languages
- Provides up to 5 scans per day
- Can scan any number of public and private repositories
49. Snort
Snort is another security tool for DevOps that works to protect a system from intruders and attacks.
This is considered one of the most powerful open-source tools around, and you can analyze traffic in real-time. By doing so, it makes intruder detection far more efficient and faster. Snort also can flag up any aggressive attacks against your system.
There are over 600,000 registered users on the Snort platform right now, making it the most widely deployed intrusion prevention system out there.
- Packet logging and analysis provides signature-based attack detection
- Performs protocol analysis and content searching
- Has the ability to detect and flag up a variety of different attacks
50. OverOps
Code breaks are part and parcel of the DevOps life. OverOps is a tool that’s useful at identifying any breaks in your code during the production process.
Not only that, but it gets down to the root cause of an issue and informs you why there was a code issue and exactly when it happened. You’ll be faced with a complete picture of the code when the abnormality was detected, so you can reproduce and fix the code.
- Integrates with Jenkins
- Stops you from promoting bad code
- Uses Artificial Intelligence to spot any new issues in real-time
51. Code Climate
Code Climate is one of the top issue tracking tools for DevOps professionals. With this software, you get a detailed analysis of how healthy your code is. You can see everything from start to finish, which lets you pinpoint any issues.
DevOps professionals can easily see any problems in a line of code and fix them as soon as possible. Therefore, you can start producing better code with fewer errors and bugs – which will only improve the overall customer experience upon launch.
- Very easy to integrate into any workflow
- Let’s you built code that’s easy for everyone to maintain
52. ZenDesk
Zendesk works for companies of all sizes by improving customer service and support.
Choose from hundreds of applications, or use the features as is. Your development team can even build a completely customized tool taking the open APIs offered on the Apps Marketplace.
Zendesk provides benchmark data access across your industry. This is valuable data to improve your customer interactions.
How to Choose the Right DevOps Tool
There is no secret method for choosing proper DevOps tools. You are going to be implementing them across a variety of operational and development teams, so it should be thought of as more of a shift in the existing culture.
No single tool works across all areas of development and delivery. But several tools will work in different areas. You first need to discover your processes, and then you can more easily determine which DevOps security products you will be able to utilize successfully.
A straightforward way to break down your cycle of development is by doing so in phases.
The main phases are:
- Collaboration – deciding which tools everyone can agree on and share across multiple platforms for complete integration.
- Planning – being able to share ideas, brainstorm, comment, and work towards a common goal
- Build -includes the development of software along with coding against any virtual or disposable duplicates to speed up production and get more accomplished.
- Continuous integration – obtaining constant and immediate feedback through the process of merging code. It happens many times a day using automatic testing tools.
- Deploy – deploying predictable, reliable, and frequent applications to keep production running smoothly and risks low through automation.
- Operate – application and server performance monitoring that records and watches data around the clock to ensure it’s working correctly.
- Continuous feedback – user comments, support tickets, Tweets, NPS data, churn surveys, bug reports, and other feedback collected to determine if what’s being built is working.
DevOps Tools Streamline Processes
When you integrate DevOps early in software development, you are streamlining the process. Anyone looking to create and deliver a software program more quickly and efficiently than the more traditional methods can utilize these applications.
Decide which applications above are most useful for your needs and start developing more efficiently today!
Recent Posts
13 Best SIEM Tools for Businesses in 2020 {Open-Source}
Choosing the right Security Information and Event Management software can be overwhelming.
The SIEM market today is nearly a $3 billion industry and growing. Gartner predicts spending on SIEM technologies will rise to almost $2.6 billion in 2020 and $3.4 billion in 2021.
As you consider threat detection systems, find the tools you’ll need to protect your organization against various types of cyberattacks. Examine how you should build out your protection.
Take the time to consider the preparations necessary for successful expansion into the technology. The benefits of a sound, real-time security system are well worth the investment.
What is SIEM?
SIEM or Security information and event management is a set of tools that combines SEM (security event management) and SIM (security information management) Both of these systems are essential and are very closely related to each other.
SIM refers to the way that a company collects data. In most cases, data is combined into a specific format, such as the log file. That format is then placed in a centralized location. Once you have a format and location for your data, it can be analyzed quickly.
SIM does not refer to a complete enterprise security solution, though it is often mistaken for one. SIM relates only to the data collection techniques used to discover problems within a system.
SEM provides real-time system monitoring and notifies network administrators about potential issues. It can also establish correlations between security events.
What are SIEM Software Tools?
SIEM products run directly on the systems they monitor. The software sends log information to a central portal. This is typically a cloud server as they have more robust security monitoring than in-house hardware. They also provide a degree of separation for added protection.
A console provides clients visual aids filtered through local parameters. Cybersecurity incidents can be identified, recreated, and audited through accounting logs.
How Security Information Event Management Works
SIEM works by identifying the correlation between separate log entries. More advanced platforms also include entity and user behavior analysis (UEBA). Other systems may also include SOAR. SOAR stands for “Security Orchestration and Automated Response.” UEBA and SOAR are very helpful in specific instances.
Security Information and Event Management also works by monitoring and logging data. Most security operations experts consider SIEM tools to be more than a simple monitoring and logging solution.
A SIEM security system includes:
- Actively develops lists of global threats based on intelligence.
- Collecting logs from vetted sources of intelligence.
- A SIEM solution consolidates and analyzes log file, including supplemental analytics data to enrich the logs.
- Finds security correlations in your logs and investigates them.
- If a SIEM rule is triggered, the system automatically notifies personnel.
Best Practices for Using a SIEM Solution
Identify Critical Assets To Secure
The first thing organizations must do is identify critical assets thru security risk management. Identification leads to prioritization. No company has the resources to protect everything equally. Prioritizing assets allows an organization to maximize its security within a budget.
Prioritizing assets also help in selecting a SIEM solution
Understanding a companies needs also helps to scale the SIEM platform used. SIEM technology can help with low-level compliance efforts without much customization.
Enterprise visibility is another goal altogether. This requires a much higher level of deployment. This goal does not require as much customization. Does your company know its goals? Take the time to form a detailed strategy before investing.
Train Staff to Understand SIEM Software
The second step is to ensure that in-house staff understands SIEM as a platform.
What system log files will the SIEM technology solution monitor? Does your company use a variety of logs? You may process data differently in various departments. You must normalize these logs before a SIEM security helps you. Different logs do not allow the system to execute to its maximum potential or deliver actionable reports. Why? The data is not consistent.
Create a Scaling Strategy
Some companies duplicate a logging strategy as they expand. The need for servers will eventually increase. As it does, the company reproduces the log rules. The log files will copy themselves as time goes on. This helps preserve records if a company is acquired or merges with another.
Creating a viable strategy becomes more difficult if servers are spread throughout different time zones and locations. Ideally, you would standardize the time zone your organization will use. Unsynchronized time stamps may result from neglecting this step. Finally, configure the triage of potential incidents on the system.
Make Sure the SIEM Solution Meets Your Needs
Each Security Information and Event Management comes with a log gathering requirement. For instance, Syslog logs connect through outsourced agents. Logs from Microsoft deal with locally installed agents. Logs are then collected centrally from a Remote Procedure Call or a Windows Management Instrumentation. Only then are they given to the devices collecting logs.
Executives are responsible for determining the security needs of each prioritized asset. This is essential to produce measurable and actionable results from a SIEM.
Log Only Critical Assets (at First)
Secondary features can roll out after configuring the full log environment. Managing this step by step helps to avoid errors. It also helps to hold back total commitment until the SIEM is tested.

Top SIEM Tools and Software Solutions to Consider
The capabilities of each SIEM product listed below vary. Make sure that you vet each system based on your individual needs.
OSSEC
Open source SIEM is quite popular. OSSEC is used most often as a host-based system for intrusion prevention and detection. This system is often abbreviated as an IDS. OSSEC works with Solaris, Mac OS, Linux, and Windows servers and Mac OS. It works well because of its structure. Two components comprise OSSEC: 1. the host agent and 2. the main applications.
OSSEC allows direct monitoring for rootkit detection, file integrity, and log files. It can also connect to mail, FTP, web, firewall, and DNS based IDS platforms. You also can synchronize log analysis from primary commercial network services.
Snort
Snort is a network-based IDS. It lives farther away from the host, allowing it to scan and monitor more traffic. As one of the top SIEM tools, Snort analyzes your network flow in real-time. Its display is quite robust: you can dump packets, perform analysis, or display packets in real-time.
If your network link has a throughput of 100 Gbps or higher, Snort may be the product for your company. The configuration has a high relative learning curve, but the system is worth the wait. Make sure that your staff has a sturdy grip on how to use Snort. It has robust analytical and filtering capabilities alongside its high-performance output plugins. You can use this SIEM tool in many ways.
ELK
ELK may be the most popular solution in the market. The ELK stack is the combination of products from SIEM vendors Elasticsearch, Logstash, and Kibana.
Elasticsearch provides the engine to store data. It is considered a top solution in the marketplace.
Logstash can receive your log data from anywhere. It can also enhance, process, and filter your log data if needed.
Finally, Kibana gives you your visuals. There is no argument in the world of IT about Kibana’s capabilities. It is considered the top open-source analytics visualization system produced in the industry so far.
This stack forms the base of many commercial Security Information and Event Management platforms. Each program specializes, making the entire stack more stable. This is an excellent choice for high performance and a relatively simple learning curve.
Prelude
Are you making use of various open-source tools? Prelude is the platform that combines them all. It fills in certain holes that Snort and OSSEC do not prioritize.
Prelude gives you the ability to store logs from multiple sources in one place. It does this using IDMEF technology (Intrusion Detection Message Exchange Format). You gain the ability to analyze, filter, correlate, alert, and visualize your data. The commercial version is more robust than the open-source version. If you need top performance, go commercial.
OSSIM SIEM Solution
ELK is one of the top SIEM solutions. OSSIM is a close second. OSSIM is the open-source sister to the Unified Security Management package from Alien Vault. It has an automated testing framework that is reminiscent of Prelude. It is considered an excellent tool.
OSSIM is more robust as a commercial offering. The SIEM, open-source version, works well with micro deployments. Get the commercial offering if you need performance at scale.
SolarWinds SIEM Log Manager
You get the event log analyzer and management consolidator for free as a trial. SolarWinds SIEM systems allow you to view logs across more than one Windows system. You can filter your logs and patterns. The Security Events Manager gives you the capacity to assess and store your historical log data.
SolarWinds is one of the most competitive entry-level SIEM security tools on the market. It offers all of the core features you would expect, including extensive log management and other features.
It is an excellent tool for those looking to exploit Windows event logs because of the detailed incident response and is suitable for those who want to manage their network infrastructure against future threats actively.
One nice feature is the detailed and intuitive dashboard design. The user can quickly identify any anomalies because of the attractive and easy to use display.
The company offers 24/7 support as a welcome incentive, so you can contact them for advice if you have issues.
LogFusion SIEM Software
LogFusion is a simple program. It has a simple user portal and a flat learning curve. If you want to handle remote logging, log dumps, and remote event channels from a single screen, this is the platform for you.
Netwrix Event Log Manager
If you do not need all of the features of Auditor, then the Netwrix Event Log Manager may be right up your alley. You get event consolidation from a whole network in a single location. You can create email alerts in real-time. You also have a limited ability to archive and some alert criteria filtering for extra measure.
McAfee Enterprise Security Manager SIEM
McAfee Enterprise Security Manager is one of the best options for analytics. It allows you to collect a variety of logs across a wide range of devices using the Active Directory system.
When it comes to normalization, McAfee’s correlation engine compiles disparate data sources efficiently and effectively. This ensures that it’s easier to detect when a security event needs attention.
With this package, users have access to both McAfee Enterprise Technical Support and McAfee Business Technical Support. The user can choose to have their site visited by a Support Account Manager twice a year if they would like, and this is recommended to make the most of the services.
This choice is Best for mid to large companies looking for a complete security event management solution.
RSA NetWitness
RSA NetWitness offers a complete network analytics solution. For larger organizations, this is one of the most extensive tools available.
However, if you’re looking for something simple, this is not it. The tool is not very easy to use
And can be time-consuming setup. Although comprehensive user documentation can assist you when setting up, the guides don’t help with everything.
LogRhythm Security Intelligence Platform
LogRhythm can help in numerous ways, from behavioral analysis to log correlation and even artificial intelligence. The system is compatible with an extensive range of devices and log types.
When you look at configuring your settings, most activity is managed through the Deployment Manager. For example, you can use the Windows Host Wizard to go through Windows logs. It’s a capable tool that will help you to narrow down on what is happening on your network.
The interface does have a learning curve, but the instruction manual is thorough and does help. The manual provides hyperlinks to features so you can find the links that will help you.
Splunk Enterprise Security
Splunk is one of, if not the most popular SIEM management solution in the world.
The thing that sets Splunk magic quadrant apart from the rest is that it has incorporated analytics into the heart of its SIEM. Network and machine data can be monitored on a real-time basis as the system looks for any vulnerabilities and weaknesses. Display alerts can be defined by you.
The user interface is incredibly simple when it comes to responding to threats, and the asset Investigator does an excellent job of flagging malicious actions.
Papertrail by SolarWinds SIEM Log Management
Papertrail is a cloud-based log management tool that works with any operating system.
Papertrail has SIEM capabilities because the interface for the tool includes record filtering and sorting capabilities, and these things, in turn, allow you to perform data analysis.
Data transfers, storage, and access are all guarded with encryption. Only authorized users are allowed access to your company’s data stored on the server, and setting up unlimited user accounts is simple.
Performance and anomaly alerts are provided and can be set up via the dashboard and are based on the detection and intrusion signatures stored in the Papertrail threat database.
Papertrail will also store your log data, making them available for analysis.
Logstash
Logstash is one of three software solutions that work together to create a full SIEM system. Each application can be used with the other tools as the user sees fit. Each product can be regarded as SIEM software but used together they form a SIEM system.
It is not compulsory to use them together. All of the modules are open source and free for the user.
Logstash collects log data from the network and writes them to file. You can specify in the settings of Logstash which types of records it should manage, so you can ignore specific sources if you wish.
The system has its own record format, and the Logstash file interface can reinterpret the data into other forms for delivery.

SIEM Tools and Technology: Key Takeaways
Cybersecurity tools and threat detection are a must to secure data and prevent downtime. Vulnerable systems are always a target of hackers, and this is why Security Information and Event Management products have become a crucial aspect in identifying and dealing with cyber attacks.
The top SIEM products provide real-time analysis of security alerts and are essential to identify cyber-attacks.
Recent Posts
What Is Penetration Testing? Types and Techniques
Security should be a multi-layered approach. One of those critical layers is Penetration Testing.
Is your data safe in today’s rapidly changing world of cybersecurity attacks?
The best way to find out if application systems are secure is to attempt to hack them yourself. A tried and tested method is a penetration test, a form of application scanning. Vulnerability detection aims to identify potential weakness before the bad guys do
In this article, we will discuss what pen testing is, different types, and how your organization can benefit from it.
What is Penetration Testing? A Definition
By definition, penetration testing is a method for testing a web application, network, or computer system to identify security vulnerabilities that could be exploited. The primary objective for security as a whole is to prevent unauthorized parties from accessing, changing, or exploiting a network or system. It aims to do what a bad actor would do.
Consider a Pen Test an authorized simulation of a real-world attack on a system, application, or network to evaluate the security of the system. The goal is to figure out whether a target is susceptible to an attack. Testing can determine if the current defense systems are sufficient, and if not, which defenses were defeated.
These tests are designed to target either known vulnerabilities or common patterns which occur across applications — finding not only software defects but also weaknesses in network configurations.
Why Security Penetration Testing is Important
A pen-test attempts to break a security system. If a system has sufficient defenses, alarms will be triggered during the test. If not, the system is considered compromised. Penetration testing tools are used to monitor and improve information security programs.
Though system administrators need to know the difference between a test and an actual threat, it’s important to treat each inspection as a real-world situation. Though unlikely, credible security threats could occur during the test.
Penetration tests are often creative rather than systematic. For example, instead of a brute force attack of a network, a pen-test could be designed to infiltrate a company executive via his/her e-mail. Approaching the problem creatively as an infiltrator is more realistic with what could potentially be a real attack someday.
Once a test is complete, the InfoSec team(s) need to perform detailed triage to eliminate vulnerabilities or defer action where a weakness poses little or no threat.
Typically, penetration testers are external contractors hired by organizations. Many organizations also offer bounty programs. They invite freelance testers to hack their external-facing systems, such as public websites, in a controlled environment with the promise of a fee (or other forms of compensation) to breach an organization’s computer systems.
There is a good reason why organizations prefer to hire external security professionals. Those who do not know how an application was developed may have a better chance of discovering bugs the original developers may never have considered or maybe blind toward.
Penetration testers come from a variety of backgrounds. Sometimes these backgrounds are similar to those of software developers. They can have various forms of computer degrees (including advanced ones), and they can also have specialized training in penetration security testing. Other penetration testers have no relevant formal education, but they have become adept at discovering security vulnerabilities in computer software. Still, other penetration testers were once criminal hackers, who are now using their advanced skills to help organizations instead of hurting them.
Steps of Penetration Testing
Reconnaissance and Intelligence Gathering
Before explaining the different methods for a penetration test, it’s necessary to understand the process of gathering intelligence from systems and networks.
Intelligence gathering, or Open Source Intelligence (OSINT) gathering, is a crucial skill for testers. During this initial phase, ethical hackers or cybersecurity personnel learn how the environment of a system functions, gathering as much information as possible about the system before beginning.
This phase will usually uncover surface-level vulnerabilities.
It includes a scan of:
- The local and wireless network
- Pertinent applications
- Website
- Cloud-based systems
- Employees
- Physical hardware facilities
Threat Modeling
After gathering intelligence, cybersecurity professionals move on to threat modeling.
Threat modeling is a structured representation of the information that affects system security. Security teams use this type of model to treat every application or feature as if it were a direct safety.
Threat modeling captures, organizes, and analyzes the bulk of intelligence gathered in the previous preparation phase for a penetration test. It then makes informed decisions about cybersecurity while prioritizing a comprehensive list of security improvements, including concepts, requirements, design, and rapid implementation.
Threat modeling is a process of its own, and can be summed up by asking the following four questions:
- What are we working on?
- What can go wrong with what we’re working on?
- What can we do to ensure that doesn’t happen?
- Did we completely eradicate the problem?
There is no single, right way to investigate vulnerabilities in a system. But combinations of these questions can go a long way toward finding solutions.
Cybersecurity professionals define and identify vulnerability assessment scope, threat agents, existing countermeasures, exploitable vulnerabilities, prioritized risks, and possible countermeasures during threat modeling.

Types of Penetration Testing
Following intelligence gathering and threat modeling, a penetration test itself is the next process.
Below are various penetration testing methodologies. It’s important to test for as many potential weaknesses throughout your system and network as possible.
Conducting multiple tests can reveal more vulnerabilities and provide your security and IT teams with more opportunities to address and eliminate security threats.
Network Penetration Testing & Exploitation
This type of test includes both internal and external network exploitation testing through the emulation of hacker techniques that penetrate a system’s network defenses. Once the network has been compromised, the tester can potentially gain access to the internal security credentials of an organization and its operation.
Testing of a network includes identifying:
- Threat Modeling
- Vulnerability Scanning & Analysis
- Firewall bypassing
- Router and proxy server testing
- IPS and DPS evasion
- Open port scanning
- SSH security attacks
Network testing is more in-depth than standard penetration testing and locates vulnerabilities that basic scans may not find, all to create a safer overall network.
Web Application Security Tests
Application security tests search for server-side application vulnerabilities. The penetration test is designed to evaluate the potential risks associated with these vulnerabilities through web applications, web services, mobile applications, and secure code review.
The most commonly reviewed applications are web apps, languages, APIs, connections, frameworks, systems, and mobile apps.
Client Side or Website & Wireless Network
Wireless and website tests inspect relevant devices and infrastructures for vulnerabilities that may compromise and exploit the wireless network.
Recently, Mathy Vanhoef, a security expert at the Belgian University KU Leuven, determined that all WiFi networks are vulnerable to hacking through their WPA2 protocols.
This exploit can reveal all encrypted information, including credit card numbers, passwords, chat messages, emails, and images. Injection and manipulation of data are also possible, leading to the potential for ransomware or malware attacks that could threaten the entire system.
To prevent wireless network hacking, check for the following during pen testing:
- webserver misconfiguration including the use of default passwords
- malware and DDoS attacks
- SQL injections
- MAC address spoofing
- media player or content creation software testing vulnerabilities
- cross-site scripting
- unauthorized hotspots and access points
- wireless network traffic
- encryption protocols
Social Engineering Attacks
Social engineering tests search for vulnerabilities an organization could be exposed to based on its employees directly. In this case, creative testing must be designed to mimic real-world situations that employees could run into without realizing they’re being exploited.
These tests not only help with internal security strategy amongst co-workers but allow security teams to determine necessary next steps in cybersecurity.
Specific topics such as eavesdropping, tailgating, or phishing attacks; posing as employees; posing as vendors/contractors; name-dropping or pretexting; gifts or dumpster diving; bluesnarfing; quid pro quo; or baiting, are common testing practices.
Bad actors typically possess social engineering skills and can influence employees to create access to systems or sensitive customer data. When used in conjunction with other physical tests, social engineering testing can help to develop a culture of security throughout an organization.
Physical Testing
Physical penetration testing prevents hackers from gaining tangible access to systems and servers by ensuring that facilities are impenetrable by unauthorized personnel. IT and cybersecurity professionals focus primarily on system vulnerabilities and may overlook physical security aspects that can result in exploitation. Physical penetration tests focus on attempts to access facilities and hardware through RFID systems, door entry systems and keypads, employee or vendor impersonation, and evasion of motion and light sensors.
Physical tests are used in combination with social engineering such as manipulation and deceit of facility employees to gain system access.
Computer Network Exploitation (CNE) & Computer Network Attacks (CNAs)
In a Computer Network Exploitation (CNE), networks can be used to target other systems directly.
For example, attempting to extract and obtain sensitive information and data such as classified intelligence or government documents. This type of attack is commonly performed within government agencies and military organizations and is considered surveillance, wiretapping, or even cyber-terrorism.
In a Computer Network Attacks (CNAs), the goal is to destroy or corrupt information that exists on a victim’s network through an Electronic Attack (EA). EA’s can use techniques such as an electromagnetic pulse (EMP) designed to incapacitate a network or system.
Types of CNAs can overlap with social engineering and include data modification and IP address spoofing; password-based attacks; DDOS; Man in the middle attacks; or compromised key, sniffer, and application layer attacks.
Cloud Pen Testing
Cloud services are essential for group collaboration, networking, and storage. Large amounts of data are stored within the cloud, which means that it is a hotbed for hackers seeking to exploit this technology.
Cloud deployment is relatively simple. However, cloud providers often have a shared or hands-off approach to cybersecurity, and organizations are responsible for vulnerabilities testing or hacking prevention themselves.
Cloud penetration testing is a complicated test, but one that is necessary and important.
Typical cloud testing areas include:
- Weak passwords
- Network Firewalls
- RDP and SSH remote administration
- Applications and encryption
- API, database, and storage access; VMs; and unpatched operating systems.
Public cloud penetration testing can be among the most complicated to perform.
Utilize a “white box” method of testing by making use of as much information as possible about the target system. This includes the software it runs, and the network architecture, source code.
This will ensure you have the intelligence to accomplish the test. Be aware that public cloud services providers limit your penetration testing abilities due to the resource limitations of shared infrastructures.
For instance, Amazon Web Services (AWS) requires that you fill out the AWS Vulnerability Testing Request Form before testing and forbids certain types of pen tests.
Microsoft Azure lists its Microsoft Cloud Unified Penetration Testing Rules of Engagement on its website.
On-premises subscribers and cybersecurity personnel can scan applications, data, runtime, operating system, virtualization, servers, storage, and networking.
In the cloud, they can test applications, data, runtime, and operating systems for IaaS; applications and data only for PaaS; and no subscriber testing for SaaS.
Assess Your Security With Pen Testing Before a Hacker Does
Cybersecurity is a concern for all businesses. Constant threats to IT systems and networks are non-stop. Identifying weaknesses thru testing can prevent unauthorized parties from accessing data. Ensure that your applications and network systems have an evolving multi-stage security approach.
Designing tests that simulate attacks on hardware, software, networks, and even your employees, you can quickly determine the weaknesses.
Recent Posts
15 DevOps Metrics & KPIs That Enterprises Should Be Tracking
DevOps first made its mark as an option for streamlining software delivery. Today, DevOps is widely regarded as an essential component of the delivery process. Key DevOps processes are involved in everything from securing to maintaining applications.
DevOps practices and principles alone won’t ensure quality and could even cause more issues if not integrated correctly. In the effort to deliver software to the market as quickly as possible, companies risk more defects caught by the end-user.
The modern era of end-to-end DevOps calls for the careful integration of key performance indicators (KPIs). The right metrics can ensure that applications reach their peak potential.
Ideally, DevOps Metrics and KPI’s present relevant information in a way that is clear and easy to understand. Together, they should provide an overview of the deployment and change process — and where improvements can be made.
The following metrics are worth tracking as you strive to improve both efficiency and user experience.
DevOps Metrics and Key Performance Indicators
1. Deployment Frequency
Deployment frequency denotes how often new features or capabilities are launched. Frequency can be measured on a daily or weekly basis. Many organizations prefer to track deployments daily, especially as they improve efficiency.
Ideally, frequency metrics will either remain stable over time or see slight and steady increases. Any sudden decrease in deployment frequency could indicate bottlenecks within the existing workflow.
More deployments are typically better, but only up to a point. If high frequency results in increased deployment time or a higher failure rate, it may be worth holding off on deployment increases until existing issues can be resolved.
2. Change Volume
Deployment frequency means little if the majority of deployments are of little consequence.
The actual value of deployments may be better reflected by change volume. This DevOps KPI determines the extent to which code is changed versus remaining static. Improvements in deployment frequency should not have a significant impact on change volume.
3. Deployment Time
How long does it take to roll out deployments once they’ve been approved?
Naturally, deployments can occur with greater frequency if they’re quick to implement. Dramatic increases in deployment time warrant further investigation, especially if they are accompanied by reduced deployment volume. While short deployment time is essential, it shouldn’t come at the cost of accuracy. Increased error rates may suggest that deployments occur too quickly.
4. Failed Deployment Rate
Sometimes referred to as the mean time to failure, this metric determines how often deployments prompt outages or other issues.
This number should be as low as possible. The failed deployment rate is often referenced alongside the change volume. A low change volume alongside an increasing failed deployment rate may suggest dysfunction somewhere in the workflow.
5. Change Failure Rate
The change failure rate refers to the extent to which releases lead to unexpected outages or other unplanned failures. A low change failure rate suggests that deployments occur quickly and regularly. Conversely, a high change failure rate suggests poor application stability, which can lead to negative end-user outcomes.
6. Time to Detection
A low change failure rate doesn’t always indicate that all is well with your application.
While the ideal solution is to minimize or even eradicate failed changes, it’s essential to catch failures quickly if they do occur. Time to detection KPIs can determine whether current response efforts are adequate. High time to detection could prompt bottlenecks capable of interrupting the entire workflow.
7. Mean Time to Recovery
Once failed deployments or changes are detected, how long does it take actually to address the problem and get back on track?
Mean time to recovery (MTTR) is an essential metric that indicates your ability to respond appropriately to identified issues. Prompt detection means little if it’s not followed by an equally rapid recovery effort. MTTR is one of the best known and commonly cited DevOps key performance indicator metrics.
8. Lead Time
Lead time measures how long it takes for a change to occur.
This metric may be tracked beginning with idea initiation and continuing through deployment and production. Lead time offers valuable insight into the efficiency of the entire development process. It also indicates the current ability to meet the user base’s evolving demands. Long lead times suggest harmful bottlenecks, while short lead times indicate that feedback is addressed promptly.
9. Defect Escape Rate
Every software deployment runs the risk of sparking new defects. These might not be discovered until acceptance testing is completed. Worse yet, they could be found by the end user.
Errors are a natural part of the development process and should be planned for accordingly. The defect escape rate reflects this reality by acknowledging that issues will arise and that they should be discovered as early as possible.
The defect escape rate tracks how often defects are uncovered in pre-production versus during the production process. This figure can provide a valuable gauge of the overarching quality of software releases.
10. Defect Volume
This metric relates to the escape rate highlighted above, but instead focuses on the actual volume of defects. While some defects are to be expected, sudden increases should spark concern. A high volume of defects for a particular application may indicate issues with development or test data management.
11. Availability
Availability highlights the extent of downtime for a given application.
This can be measured as complete (read/write) or partial (read-only) availability. Less downtime is nearly always better. That being said, some lapses in availability may be required for scheduled maintenance. Track both planned downtime and unplanned outages closely, keeping in mind that 100 percent availability might not be realistic.
12. Service Level Agreement Compliance
To increase transparency, most companies operate according to service level agreements. These highlight commitments between providers and clients. SLA compliance KPIs provide the necessary accountability to ensure that SLAs or other expectations are met.
13. Unplanned Work
How much time is dedicated to unexpected efforts? The unplanned work rate (UWR) tracks this in relation to time spent on planned work. Ideally, the unplanned work rate (UWR) will not exceed 25 percent.
A high UWR may reveal efforts wasted on unexpected errors that were likely not detected early in the workflow. The UWR is sometimes examined alongside the rework rate (RWR), which relates to the effort to address issues brought up in tickets.
14. Customer Ticket Volume
As the defect escape rate KPI suggests, not all defects are disastrous. Ideally, however, they will be caught early. This concept is best reflected in customer ticket volume, which indicates how many alerts end users generate. Stable user volume alongside increased ticket volume suggests issues in production or testing.
15. Cycle Time
Cycle time metrics provide a broad overview of application deployment.
This KPI tracks the entirety of the process, beginning with ideation and ending with user feedback. Shorter cycles are generally preferable, but not at the expense of discovering defects or abiding by SLAs.
Start Measuring Devops Success
When tracking key DevOps metrics, focus less on the perceived success or failure according to any one indicator, but rather, on the story these metrics tell when examined together. A result that seems problematic on its own could look completely different when analyzed alongside additional data.
Careful tracking of the KPIs highlighted above can ensure not only greater efficiency in development and production, but more importantly, the best possible end-user experience. Embrace DevOps metrics, and you could see vast improvements in application deployment and feedback.
Recent Posts
How DevOps Security Best Practices Delivers More Secure Software
Agile software development and DevOps Security go hand in hand.
Agile development focuses on changing how software developers and ops engineers think. A DevOps approach focuses on the underlying organizational structure, culture, and practice of software development.
In the past, the two functions were separate. Developers wrote the code. Ops implemented and managed it.
However, a developer’s complex code was sometimes clumsy to implement, causing pushback from operations. DevOps addresses the tension and, in some cases, downright hostility between the two functions.

What is DevOps Security?
Combining the words “development” and “operations,” DevOps security breaks down the barriers between software development and IT operations.
Instead of developers coding, then throwing it over the wall to operations, DevOps puts the teams together. Driven by (CI/CD) continuous integration DevOps practices and a continuous deployment philosophy, faster, agile release cycles replace big releases.
This work environment keeps software developers and IT operations in constant communication and tightens collaboration. The combined teams launch software and infrastructure with fewer errors that cause outages, release rollbacks, and operational disruptions. DevOps is a two-pronged approach that addresses cultural change while transforming technology and tools.
Businesses that adopt this approach gain the following benefits:
Consistency
Standardizing infrastructure provisioning and the software release process enforces consistency across the entire DevOps environment.
Provisioning
Code new instances in a few keystrokes using automation tools and runbooks that turn manual processes into pre-packaged, automatic actions.
Speed and Agility
Increase agility, quality, and reliability of new software launches and feature releases.
DevOps Security Challenges
Though DevOps solves many challenges in the software development process, it also introduces new challenges. Less than 46% of IT security professionals are skipping DevOps security in planning and design. These environments end up with a reactive, uncoordinated approach to incident management and mitigation. Often, the lack of coordination isn’t evident until an incident occurs, and systems are breached or attacked.
Aside from just a blip in operations, security breaches can reap long-term havoc. Take the case of the 2017 Uber breach. The root cause was a careless developer who published credentials to GitHub. An all too common error when quickly compiling code to keep up with agile development cycles.
Hackers quickly pounced, attacking Uber in a breach that impacted over 50 million customers and nearly 600,000 drivers. Uber paid off the hackers to keep quiet. However, the data breach was eventually discovered and led to a public relations nightmare.
A secure DevOps environment runs on different tools, processes, and policies to facilitate rapid and secure releases. In the case of Uber, a final security scan to ensure no credentials are left embedded in the code. These pieces come together to provide bulletproof security throughout the application development, release, and management phases.
Organizational Opposition
In the desire to move quickly, security is often seen as just one more thing to slow down the release process. As a result, developers start to resent the time needed pre-release to do security checks, which creates vulnerabilities.
Security Vulnerabilities in the Cloud
Firewalls can’t completely protect you in the cloud. Securing in the cloud revolves more around RBAC and access management. Many of the processes and tools used in securing DevOps rely on cloud-based resources.
Legacy Infrastructure
In that same SANS study referenced above, over 90% reported that they were still supporting legacy resources. That leaves most organizations running hybrid environments using cloud-based elements with traditional, legacy infrastructure. The performance and security requirements of legacy resources create complications when folded into DevOps environments.
Recruiting
As a new discipline, finding experienced DevSecOps engineers is not only difficult, but also pricey. The average salary for DevSecOps engineers is $131,000. The effort to get existing staff up to speed and production-ready potentially impacts attention to critical daily operations.

What Does DevSecOps Stand For?
DevSecOps is a philosophy that brings security into the software development process as a shared responsibility.
The fundamental principle is that everyone involved is accounting for security. It also integrates automated security tasks within DevOps (a type of agile relationship between development and IT operations) processes.
The “Sec” in DevSecOps is security. In the past, application security wasn’t a primary concern for developers. Many companies treated security as an afterthought. Sometimes that meant taking on security features at the end of development. Sometimes, it wasn’t considered unless there was a breach.
Before the rise of cybercrime, there weren’t many financial reasons for security. It didn’t add value—or at least it didn’t seem to. Customers were left to look out for themselves. Security companies jumped in to write antivirus programs and firewalls, but this didn’t solve security for individual products or applications.
Data breaches became more frequent, and penalties grew more severe. Customers got frustrated, and companies started seeing higher costs associated with low security. With securing in development, the DevSecOps model creates shared responsibility between Development, Security, and Operations.
How Can You Utilize DevSecOps?
DevSecOps works by protecting against the new type of risks that CI/CD introduces within a DevOps testing framework.
Extensive security checks once saved for the end of the development cycle, become integrated while the code is being built. DevSecOps covers code analysis, post-deployment monitoring, automated security controls, and other security checks. By remaining engaged throughout the process, bugs and other potential issues are uncovered and mitigated before launching.
The result is a more cohesive experience in the development process and a better end-user experience. The improved delivery chain gives users updated features faster, more secure software, and allows users to focus on their jobs instead of lagging technology.
Automated controls and reporting tools help to maintain security, compliance, and privacy to meet stringent compliance and legal regulations. Many of these functions can be automated for reporting and audit purposes. This can often be the tipping point for stakeholders concerned about the risk involved in fast-moving DevOps environments.
DevSecOps best practices include:
- Leaning in over always saying “No”
- Data and security science vs. fear, uncertainty, and doubt
- Open contribution and collaboration over security-only requirements
- Consumable security services with APIs over mandated security controls
- Business-driven security scores over “rubber stamp” security
- ‘Red and Blue Team exploit testing over scans and theoretical vulnerabilities
- 24×7 proactive monitoring versus overreacting after an incident
- Shared threat intelligence over keeping information to silos
- Compliance operations over clipboards and checklists

DevSecOps vs DevOps
DevOps methodology evolved from two industry practices, Lean and Agile.
In the early days of software, engineers wrote most applications. Business leaders set the specifications, and the software engineers would build applications to match. Users, support staff, and security had very little input during development. This led to apps that had lots of features but were harder to learn. It also created long development times and significant waste.
To trim the efficiency of software developers, businesses applied the Lean model. Lean manufacturing sought to reduce waste. By keeping only the parts that add value, companies could make software development more efficient. The Lean model also makes people more critical in the process. The goal with Lean was to get better software by improving the development process.
Lean grew another development philosophy, called Agile. Agile is a set of guidelines created by software engineers but aimed at business leaders. It focuses on communication, working together, and rapid change. These features helped software companies respond more quickly to the market by shortening development cycles. It also helped companies respond better to customer feedback.
The Lean and Agile models helped businesses break out of the old, clunky development model.
To improve software development, a model was needed that focused just on software development. That’s when DevOps was created. “Dev” refers to development, meaning anyone involved in writing software. “Ops” means anyone who operates the software, from users to support agents.
In DevOps, both teams are involved in writing software.
With operations involved, developers don’t need to wait on publication or testing to get feedback. Operations are included and help developers adjust to make better software.
With these two development teams working together, apps can be better, intuitive, and easy to use. It also shortens the development cycle, putting review alongside development. Overall, this process leads to continuous delivery of new software features and updates.
Why The Change In Software Development Model?
Traditionally, a company implemented security after the software was created. It can be an easier way to include security but often works like a retrofit job. When the developers are finished, security reviews the software, and any changes are just tacked on.
Another security model is to compare finished software to an existing security policy. Any areas where the software doesn’t pass policy are kicked back to the developers.
Both of these methods are widely used, and often necessary. Some platforms are used for decades and need to be adjusted as technology moves forward. Usually, the market changes and software has to keep up. Or, an older feature like a database holds critical information, but it may not work with newer servers. Due to the high cost of rebuilding the database, some companies pile on updates and security features. This creates a compromise between cost and security.
A policy of patching at the end of development has its problems. One issue is that it tends to put the focus on reacting to incidents, instead of preventing them. One example of this is modern operating systems. The developer of an operating system publishes regular updates. These updates fix security flaws that are found during testing. This is an important process! However, hackers closely watch that list of updates. Then, they write viruses and scripts that exploit those very weaknesses. And it works, because many companies have a lag between when the patch is released and when it’s installed. Some companies are even stuck using older, unsupported operating systems. With no patches available, a company is stuck with either expensive upgrades or possible security breaches.
With security testing being so complicated, some organizations see it as an obstacle.
The original DevOps model promoted speed and flexibility. Sometimes application security vulnerability is just put on the back burner, or even ignored entirely in the name of speed. This can help companies get an edge in a competitive market. However, with recent, massive data breaches, the “patch later” plan can be a costly gamble.
Advantages of Developing with DevOps Security
DevSecOps promotes a culture of security.
This is useful when developing an application because built-in security features are more effective and more accessible to enhance. The culture of security can also seep into the rest of the business. Operation teams may see the value in security measures, and avoid bypassing them to simplify their work. Developers have a clear view of the finished package they can build to. Security teams become partners and collaborators, instead of reviewers and critics.
One of the critical values of integrating collaboration with a security team is mindfulness. Security practitioners on the development team help everyone to be more aware of security.
That translates into developers making better choices while planning and writing software. It also means operations teams are more likely to promote secure practices and procedures.
Another feature of implementing security into DevOps is that its part of the natural structure. DevOps brings operations into software development. It’s a natural extension to bring Security in. With this in mind, operators are more likely to find ways to misuse apps and fix them, rather than let them slide. They may suggest effectively, but less intrusive, threat protection features.
Implementation earlier in development helps to make security an integral part of the process. That might look like simple, secure authentication. It could also mean less retrofit security. In creating a coherent approach, everything works seamlessly together. Presenting a unified front acts as a strong deterrent against cyber attacks.
Automation of security best practices can be done using scripts or automated testing tools. Use automatic monitoring scans that only read the code that’s been changed. Consider doing regular security audits.
Automated security testing reduces the time spent reviewing an application and overall costs.

How To Implement Best Practices of DevSecOps
Shifting to a DevSecOps model isn’t just a change in technology. It helps to think of it more as a change in philosophy. Adopting integrates security into the fabric of applications and business processes.
One way to implement DevSecOps is to bring security professionals in alongside developer teams and operations teams. Have security teams conduct testing in development, just as they would run tests on IT infrastructure. The details might vary, but the overall process should resemble standard security services.
There are a few more target areas to focus on:
- Use a change management service. These platforms track projects, privileged users, and changes to the code. This helps bring continuous delivery and integration of code changes to everyone involved.
- Analyze code in smaller units. It is easier to scan, and any changes can be corrected more quickly.
- Maintain proper operations and security procedures. If an audit is done regularly (as it should be), your teams are more likely to pass. This also helps promote a culture of good security practices, which in turn lowers overall risk.
- Compare new features and updates against evolving threats. Cyber attacks are becoming more complex. It’s critical always to be aware, and take measures to secure your environment against them.
- When apps are in production, keep evaluating them. Look for new vulnerabilities and fix them. Evaluate and improve how quickly they can be fixed.
- Cross-train developer and operation teams in security, and vice-versa.
If you’re familiar with, implementing security shouldn’t be too challenging.
Consider it as a way of building function, ease-of-use, and security at the same time. DevSecOps training creates coherent software that’s secure and intuitive.
Meeting The Challenges of DevSecOps
There’s often a clash of culture between security and DevOps teams. The disconnect results from developers using agile development methodologies while security teams are holding on to older waterfall methodologies. As developers push to move faster, they often see the advanced security processes as a hindrance.
To keep up with development, DevSecOps integrates automated security controls. Baked into the CI/CD cycle, they require minimum human intervention – and little risk of error. In a DevSecOps survey, 40% reported performing automated security checks throughout the entire software development cycle as opposed to just pre-launch.
Intelligent Automation
Tools like Checkmarx, Splunk, Contrast Security, Sonatype, and Metasploit automate security analysis and testing throughout the software development process.
An embedded static application security testing (SAST) tool scans applications for security issues once a day. To scan an application in real-time, opt for dynamic application security testing (DAST) to find vulnerabilities as they occur.
Open Source Safety
Open source code helps developers quickly implement features, but it also introduces security risks. Recent research shows that 96% of all applications contain open source components. Unfortunately, only 27% of respondents have a plan for identifying and mitigating flaws in open source software.
DevOps tools like OWASP Dependency-Track and GitHub automate the process of checking for flawed open source elements.
Mind Your Alerts
Though these automated tools can shoot out alerts on thousands of different parameters, don’t overwhelm your team. If developers get slowed down with too many alerts, you run the risk of them going around or ignoring warnings.
Start with a few alerts to get them used to it and only apply real-time alerts for critical errors. Set static alerts for a broader set of factors. Balance the need to know with the capacity to respond.
Threat Modeling
Categorizing potential threats, determining the possible outcome, and creating a proactive mitigation strategy results in a solid threat model. By preparing for possible scenarios, you can implement the right tools and processes to reduce the impact of an incident.
To automate the process of threat modeling, use tools like OWASP Threat Dragon and Microsoft Threat Modelling Tool.
Paced Security Transformation
No matter how anxious an organization is to start using secure DevSecOps, remember to focus on small goals. Many DevSecOps security projects fail because the goals exceed capabilities, resources, or talent.
It Is Time To Shift to a DevSecOps Mindset
DevSecOps demands a change in the organizational mindset.
For security teams, it’s a commitment to not being the “no” and to find more ways to say “yes.” This means finding more agile ways to secure assets leveraging automation and machine learning.
For an organization, it means embracing a security-first mindset that incorporates security into the full development lifecycle. This means not sacrificing necessary security measures in the pursuit of CI/CD speed.
Recent Posts
Black Box Testing vs White Box Testing: Know the Differences
Inadequate quality assurance is one of the quickest, surefire ways to ruin a software company’s reputation.
Tiny mistakes hidden in an application’s source code can lead to substantial financial losses. If the errors are severe enough, the company may never recover.
High-profile cases of software being compromised and costing major companies millions make headlines all the time. Starbucks once had to temporarily close more than half of its North American stores due to a POS system failure. Nissan once had to recall more than a million cars due to an airbag sensor fault that turned out to be a software failure.
For a multi-billion-dollar global organization, rebounding from a major software issue is genuinely challenging. For a smaller company, it could simply be a challenge too great to meet.
This is why any organization that releases software needs to be deeply familiar with software testing. Testing identifies errors, gaps, and missing requirements in application code. This gives software development teams the ability to fix the mistakes before release.
Two primary methods for testing software are white box and black box tests. These testing methods have different strengths and weaknesses. Each one is designed to address particular issues and offers quality assurance insight into the causes of software problems.

White Box Testing
White box testing is also called structural testing. Some developers call it transparent box testing or glass box testing.
White box testing techniques focus on systematically inspecting the source code of an application. Developers can automate white box testing in order to efficiently resolve faulty lines of code before the development process advances.
The primary objective of white box testing is to verify the quality of the application code. Since the system’s internal structure is known, developers can pinpoint where errors come from. For instance, poorly defined variables or inaccurate call functions are relatively easy to find in a properly configured white box test.
The white box tester needs to be a software engineer who thoroughly understands the desired outcome of the application being tested. Even with best-in-class automation tools in place, it can still be an exhaustive and time-consuming experience. Automated testing may not work if the application’s code base changes rapidly.
An example of white box testing techniques include:
- Statement Coverage: This testing technique verifies whether every line of code executes at least once.
- Branch Coverage: This testing technique verifies whether every branch executes at least once.
- Path Coverage: This testing technique inspects all of the paths described by the program.
One of the drawbacks to white box testing is that it exposes code. Developers who outsource testing run the risk of having their code stolen. Developers should only trust reputable experts with a long track record of white box testing.

Black Box Testing
Black box testing is also called functional testing or data-driven testing. The object of this approach is to check program functionality.
Programming knowledge is not needed to conduct black box testing. Software esters are human users who navigate the application interface. The application passes or fails the test based on its usability, not on the quality of its code.
Since black box testers do not know how the program works, their concerns reflect those of regular users. This testing method is based on trial and error.
Programmers may not predict the particular path a black box tester may choose, which will result in errors. The programmer will then need to inspect the code to find the cause of the failure.
Black box testing is well-suited for large code segments that have clear-cut functionality. It is ideal for outsourced testing because it allows low-skilled testers to complete valuable work. Since the code is not exposed, there is no risk of intellectual property theft.
There are multiple black box testing methods, and most of them focus on testing inputs:
- Equivalence Partitioning reduces huge sets of potential inputs to small, representative test cases. It is ideal for creating test cases.
- Boundary Value Analysis looks for extreme input values that generate errors. Testers look for the boundaries of input values and report them.
- Cause-Effect Graphing uses a graph to identify input values that generate errors. It is ideal for multivariate input types.
When to Use White Box vs. Black Box Testing
White box testing does not require a complete user interface. This makes it preferable when programmers wish to test early application builds. It offers a fast, thorough way to test every path in a program. This ensures the code is good – but doesn’t guarantee it does what users want it to do.
White box testing does not separate the program and the testing environment. Sometimes updates can break source code. This can be an additional strain on developer time.
This makes white box testing a good choice during development. When small parts of a program need to be verified, white box testing makes it an easy in-house task. As the release date nears, white box testing gives way to black box testing.
Black box testing is best-suited to completed programs. A large team testing a program right before release can identify user experience problems at the last minute. Test cases are easy to make, and programmers can respond quickly to them.
It is important to carefully organize black box testing scenarios. Test outcomes may be difficult to reproduce. Tests can become redundant. Even in the best situations, testing rarely covers all software paths.
Since black box testers do not need to be highly skilled, programmers can scale up testing as the release date nears. This gives software companies the best chance of enhancing the end user experience while releasing a robust final product.
In Summary
Ultimately, each type of testing is best-suited to particular situations. Test engineers often use a combination of white box and black box testing to address different errors. And, testing may occur at different phases in the development cycle.
Whatever version or combination you choose to run, a proper testing process is crucial for software quality assurance.
All these tests may feel like a lot now, but in the long run, it will save you both time and money.
One day, it may protect your company from an embarrassing public incident.
Recent Posts
5 Types of Automation Testing Frameworks: How to Choose
Every business runs on software, and all software needs to be vetted before it is released to users. Beta testing and other crowd-sourcing methods have their uses, but they aren’t available for every step of the process.
Automated security testing is vital to developing good tools, resources, and products. For that, you need test automation frameworks.
Insufficiently tested software releases lead to unhappy customers. Conversely, comprehensive testing is expensive.
Frameworks supply resources and a streamlined process to test designers. This cuts labor costs, overall time investments in testing and other resources tied to deploying any software or computerized service. Much like a programming language saves programmers time by circumventing work in machine code, an automation framework helps testers by skipping some of the raw programming steps in the process.
In this article, we will discuss the types of frameworks and the benefits of each.
What is a Test Automation Framework?
A set of guidelines or standards that can help create quality assurance tests is commonly referred to as a test automation framework. The principle is that following a framework will improve the efficiency of both designing and executing automated tests that generate meaningful results.
These solutions provide the primary features of automated testing out of the box. Test platforms include a selection of features and the ability to script customized, repeatable tests. Often, automated testing solutions will work with existing technologies, APIs, and plug-ins, developing a robust feature set. This creates an environment through which testers can run and analyze their automated testing.
Types of Automation Testing Frameworks
The journey from knowing what a framework begins by understanding the different mainstream formats and their advantages and disadvantages.
Module Based Testing Framework
A modular automation framework breaks the overall test into smaller pieces. Each of those pieces is entirely independent of the others. This allows the test to assess different segments of the process in question to find areas of opportunity for improvement. The independent modular test results are then recombined for an overall quality assurance rating.
Modular testing has some definite advantages. The largest is the ability to reuse code. Each tested component might need to be assessed individually, but that does not require it to have unique scripts or parameters to run those tests. Any common actions among different modules can be operated with the same scripts. This saves time in both developing and performing the tests.
Conversely, modular testing comes with an inherent disadvantage. The framework is one that requires data sets to be embedded into the individual tests. If a function needs to be tested across a wide range of inputs, a modular framework will prove cumbersome.
Library Architecture Testing
Test automation framework design takes the concept of modular testing and tries to organize it more efficiently. Rather than testing the different components of the code in question, a library architecture framework groups similar functions. That enables a single module to test multiple interactions within the overall software and compare the results.
Library architecture might better be understood through an example. Consider a service that requires a user to log in. That action might appear at a number of different points within the service, so the library architecture finds and catalogs every such occurrence to test them with a single module. Interactions that require a user input variable data (such as financial statements for balancing a ledger) might be grouped in a different module.
This architecture adds layers of efficiency to traditional modular testing, but it still requires the same data embedding. In that, the library shares the fundamental weakness of modular frameworks.
Data-Driven Frameworks
A data-driven framework takes a substantially different approach to test design. The fundamental difference is that input data is stored separately from testing scripts. This eliminates the embedded-data issue that exists with modular frameworks. It also makes data-driven frameworks ideal for rapid-fire tests that simply rotate input data.
An additional advantage of this design philosophy is that it can simultaneously compare expectation values with actual test results. It can then tabulate that comparison across a range of parameters. This makes data-driven frameworks an obvious choice for tests that need such variable data, but there is a con. These tests require a higher understanding of the systems involved during the design stage. That can lead to non-trivial increases in test-design costs.
Keyword Driven Framework
Keyword-driven frameworks take the data-driven philosophy and run with it. In addition to storing data tables separately, they also save blocks of code on separate files. Entire scripts and more can be listed in external tables to be drawn as needed.
A keyword-driven framework streamlines test design. Since any given test function can be quickly identified and accessed by its keyword (hence the name), variable test scenarios can be mapped and executed in short order. Many keywords can be taken from open sources and grafted into the desired test. It’s a preferred methodology for testers who are not necessarily experts within the application field that is under scrutiny (e.g., a computer science specialist testing a fast food kiosk).
The drawback is that they can quickly complicate the testing system. An abundance of keywords can sometimes damage efficiency; this is an important trap to avoid.
Hybrid Testing
With the fundamental frameworks explained, it’s possible to cover hybrid frameworks using automated testing tools.
As the name implies, this includes any framework that combines any of the fundamental principles already covered. A keyword framework can potentially be used to rapidly build modular tests. Such a combination is ideal for anticipating user-friendliness and intuitive design. There is no real limit on how a hybrid automation framework can be combined. Real-world applications include hybridization more often than not.
Finding The Right Automated Testing Framework
By now it is clear that there is no single framework that is perfect for every test scenario.
The open-source frameworks listed above are also only a fraction of the total available. For their purpose, they are the best of the best, and if your test falls under their strengths, you are all set. They also cover the majority of mainstream testing needs. If you have an obscure niche, then additional research is necessary. Regardless, learning about test automation frameworks is only a single step in the journey.
Recent Posts
Vulnerability Scanning vs. Penetration Testing: Learn the Difference
Software security is vital. Allow that software access to the internet, and the requirement for security is increased by unimaginable orders of magnitude.
Successful protection of software and its assets requires a multifaceted approach, including (but not limited to) vulnerability scanning and penetration testing. These terms are often confused within the IT industry, and for a good reason.
Penetration tests and vulnerability scans are confused for each other.
Vulnerability assessments and scans search systems and profiles for what you would expect: vulnerabilities. Where-as penetration testing tests for threats actively attempting to weaken an environment. A critical difference between the two is that vulnerability scanning can be automated, where a penetration test requires various levels of expertise.
All networks, regardless of scale, are potentially at risk to threats. Thoroughly monitoring and testing a network for security problems allows you to eliminate threats and lower overall risk. Believing your network is safe based on assumptions rather than data-driven testing will always provide a false sense of security and could lead to disastrous results.
What is Vulnerability Scanning?
Vulnerability scanning is a term for software designed to assess other software, network operations, or applications. This software will scan for potential weaknesses in code or structure. In the same fashion that a manufacturing engineer monitors his/her product for structural integrity, vulnerability testing does the same, searching for weak points or poor construction. The scans identify areas where a system may be open to attack.
There are two types of scans: authenticated and unauthenticated. The difference is that authenticated scans allow for direct network access using remote protocols such as secure shell (SSH) or remote desktop protocol (RDP). An unauthenticated scan can examine only publicly visible information and are unable to provide detailed information about assets. This type of scan is typically used by security analysts attempting to determine the security posture of a network.
Modern scanning software is often available as Software-as-a-Service (SaaS) by specific providers that build web-based interface applications. These applications have the capabilities to scan installed software, open ports, validate certificates, and much more.
Scanners rely on published and regularly updated lists of known vulnerabilities, which are available for widely used software. Vulnerabilities don’t make it onto the list until there is a notable fix (which can pose difficulties for zero-day style attacks). When the software detects an anomaly, a patch is delivered. The software is designed to detect issues by querying the software for version information and observing the responses the software provides to specific requests.
Vulnerabilities are classified by priority. Critical vulnerabilities indicate a high likelihood that an attacker could exploit weaknesses and enact damage. Lower-priority threats may help intruders to gather information but don’t directly allow breaches.
The Center for Internet Security (CIS) considers continuous vulnerability scanning as a critical requirement for effective cyber defense.
What is Penetration Testing?
In contrast to vulnerability scanning, penetration testing (also known as a “pen test”), is an authorized attack, simulated on a computer system, designed to evaluate the security of the system. Tests are run to identify weaknesses (vulnerabilities), such as abilities to gain access to a system’s features or data. It also compiles a risk assessment of the entire system.
A penetration test can aid in determining whether a system is vulnerable to an attack, if the current defense systems are sufficient, and if not, which defenses were defeated.
Penetration tests can target either known vulnerabilities in applications or common patterns that occur across many applications. It can find not only software defects but weaknesses in an application and network configuration.
There are typically five stages of penetration testing:
- Reconnaissance – Gathering information on the system to be targeted.
- Scanning – Penetration testing tools used to further the attacker’s knowledge of the system.
- Gaining Access – Using previously collected data, the attacker can target an exploit in the system.
- Maintaining Access – Taking steps to remain within the target environment to collect as much data as possible.
- Covering Tracks – The attacker must wipe all trace of the attack from the system including any type of data collected, or events logged, to remain anonymous.
“Fuzzed” packets are a popular technique. These are legitimate requests to applications with one or a few characters randomly changed. They exercise the system’s ability to handle erroneous input cleanly.
As with vulnerability scans, the tests can either be authenticated or unauthenticated. An authenticated test runs as a registered and logged-in user on the internal network, whereas unauthenticated would be from an external source with no network privileges.
In some cases, testing goes beyond sending and receiving data and examines an organization’s business processes. If it’s in their assigned scope, testers may send phishing messages to test users’ ability to catch fraudulent requests. They may even try to sneak into the facilities to test physical security.
Security experts classify pen tests as “white box” or “black box.” A white box test makes use of as much information as possible about the target system. This includes the software it runs, the network architecture, and sometimes even source code. A black box test uses only publicly available information.
A white box test should, in principle, find more problems, since it has more information to go on. However, it’s easy for a penetration tester to become dependent on what they know about the system and not use their imagination as much. Black box testers start from the same position as an outside intruder and have to find weaknesses without help. They may devise approaches that white box testers don’t think of. Both methods have their pros and cons.
Pen tests are not a singular security solution, but a component of a full security audit. For example, to remain PCI-Compliant, the Payment Card Industry Data Security Standard requires regularly scheduled security penetration testing, and especially after system changes.
Understanding Security Testing Reports
The deliverable for both types of testing is a detailed report on any problems found. Vulnerability reports are long but straightforward. For each issue, the report lists a source, a severity rating, a description, and a remedial action. The typical remedy is to install a patch. If the software has weaknesses and its publisher no longer maintains it, replacing it with something more secure can be necessary. The InfoSec staff need to perform detailed triage on the list, eliminating or deferring action where the vulnerability poses little or no risk.
The report from a penetration test will list fewer items, but they aren’t as straightforward to explain and remedy. It will describe the attack technique, which is often ambiguous. It will explain the potential effects. The remedy could be a simple one, such as restricting access. In other cases, coming up with a fix may require serious analysis. A strong report will put the results into context and provide detailed recommendations for remediation.
Difference between penetration testing and vulnerability scanning process
Running a penetration test is considered to be more challenging or at least involved than a vulnerability scan.
A penetration test attempts to break into a security system. If the system has adequate defenses, this will trigger alarms. Though administrators need to know the difference between a test and a real threat, they can’t let their guard down against credible attacks that could be happening at the same time.
Ideally, a penetration test should be run once a year, whereas vulnerability testing should be run continuously.
A penetration test requires more creativity than a vulnerability scan since it is looking for ways to exploit the ordinary course of business. For example, a CEO could transmit his or her password to their webmail, using the same password as an internal LDAP. To come up with fresh strategies in testing, you’ll want to work with people who are creative but also technically capable of executing the attack.
Vulnerability scanning is an essential process of maintaining information and network security. Every newly added piece of equipment or software that is deployed should have a vulnerability scan run against it and within a month after that. It’s essential to establish a baseline of essential equipment that’s updated and maintained regularly. Any open ports or changes found after a scan should be investigated and considered severe.
Vulnerability Scanning & Penetration Tests Are Essential
To ensure a detailed and well-protected level of security for a network, there must be detailed steps taken to conduct both vulnerability scans and penetration tests. Probing for vulnerabilities finds unpatched and poorly maintained software. It prompts IT staff to upgrade software that has encountered issues or potential weaknesses. If that’s not possible, the team needs to find a workaround or replace the software.
Scanning won’t find all the problems. The surest way to decide whether a system is secure is to try to break it. That will find not just software defects but insecure connections, configuration weaknesses, and exposed data.
Together, vulnerability scanning and penetration testing are powerful network security tools used to monitor and improve information security programs.
Recent Posts
19 Best Automated Testing Tools For 2020
This article was updated in December 2019.
Before you begin introducing test automation into your software development process, you need a solution. A successful test automation strategy depends on identifying the proper tool.
This post compiles the best test automation tools.
The Benefits of Automated Testing Over Manual
Automated software testing solutions do a significant portion of the work otherwise done by manual testing. Thus, reducing labor overhead costs and improving accuracy. Automated testing is, well, not manual. Rather than having to program everything from the ground up, developers and testers use sets of pre-established tools.
This improves the speed of software testing and also increases reliability and consistency. Testers do not need to worry about the strength of their product, nor do they need to worry about maintaining it and managing it. They need only to test their own application.
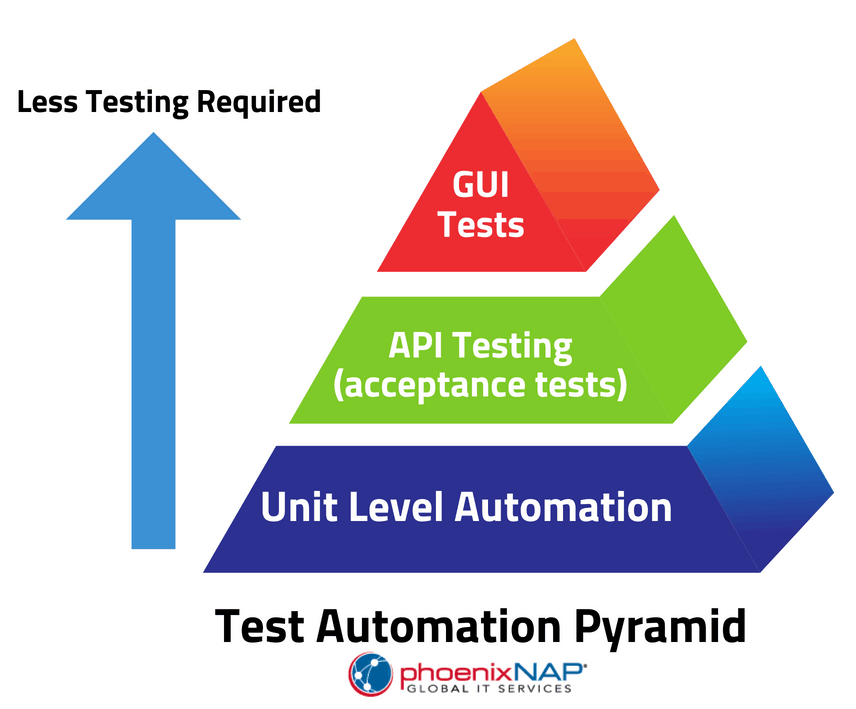
When it comes to automating these tests, being both thorough and accurate is a necessity. Developers have already tested these automated solutions for thoroughness and accuracy. Solutions often come with detailed reporting and analysis that can be used to further improve upon applications.
Even when custom scripted, an automated testing platform is going to provide stability and reliability. Essentially, it creates a foundation on which the testing environment can be built. Depending on how sophisticated the program is, the automated solution may already provide all of the tools that the testers need.
Types of Automated Software Testing Tools
There are a few things to consider when choosing an automated testing platform:
Open-source or commercial?
Though commercial products may have better customer service, open-source products are often more easily customized and (of course) more affordable. Many of the most popular automated platforms are either open source or built on open-source software.
Which platform?
Developers create frameworks for mobile testing applications, web-based applications, desktop applications, or some mix of different environments. They may also run on different platforms; some may run through a browser while others may run as a standalone product.
What language?
Many programming environments favor one language over another, such as Java or C#. Some frameworks will accept scripting in multiple languages. Others have a single, proprietary language that scripters will need to learn.
For testers or developers?
Testers will approach automated testing best practices substantially differently from developers. While developers are more likely to program their automated tests, testers will need tools that let them create scenarios without having to develop custom scripting. Some of the best test automation frameworks are specifically designed for one audience or another, while others have features available for both.
Keyword-driven or data-driven?
Different performance testing formats may have a data-based approach or a keyword-driven approach, with the former being better for developers and the latter being better for testers. Either way, it depends on how your current software testing processes run.
A test automation framework may have more or less features, or provide more robust or less robust scripting options.
Open Source DevOps Automation Testing Tools
Citrus
Citrus is an automated testing tool with messaging protocols and data formats. HTTP, REST, JMS, and SOAP can all be tested within Citrus, outside of broader scope, functional automated testing tools such as Selenium. Citrus will identify whether the program is appropriately dispatching communications and whether the results are as expected. It can also be integrated with Selenium if another front-end functionality testing has to be automated. Thus, this is a specific tool that is designed to automate and repeat tests that will validate exchanged messages.
Citrus appeals to those who prefer tried and true. Citrus is designed to test messaging protocol. It contains support for HTTP, REST, SOAP, and JMS.
When applications need to communicate across platforms or protocols, there isn’t a more robust choice. It integrates well with other staple frameworks (like Selenium) and streamlines tests that compare user interfaces with back-end processes (such as verifying that the send button works when clicked). This enables an increased number of checks in a single test and an increase in test confidence.
Galen
Unique on this list, the Galen is designed for those who want to automate their user experience testing. Galen is a niche, specific tool that can be used to verify that your product is going to appear as it should on most platforms. Once testing has been completed, Galen can create detailed reports, including screenshots, and can help developers and designers analyze the appearance of their application over a multitude of environments. Galen can perform additional automated tasks using JavaScript, Java, or the Galen Syntax.
Karate-DSL
Built on the Cucumber-JVM. Karate-DSL is an API tool with REST API support. Karate includes many of the features and functionality of Cucumber-JVM, which includes the ability to automate tests and view reports. This solution is best left for developers, as it does require advanced knowledge to set up and use.
Robot Framework
Robot is a keyword-driven framework available for use with Python, Java, or .NET. It is not just for web-based applications; it can also test products ranging from Android to MongoDB. With numerous APIs available, the Robot Framework can easily be extended and customized depending on your development environment. A keyword-based approach makes the Robot framework more tester-focused than developer-focused, as compared to some of the other products on this list. Robot Framework relies heavily upon the Selenium WebDriver library but has some significant functionality in addition to this.
Robot Framework is particularly useful for developers who require Android and iOS test automation. It’s a secure platform with a low barrier to entry, suited to environments where testers may not have substantial development or programming skills.
Robot is a keyword-driven framework that excels in generating easy, useful, and manageable testing reports and logs. The extensive, pre-existing libraries streamline most test designing.
This enables Robot to empower test designers with less specialty and more general knowledge. It drives down costs for the entire process — especially when it comes to presenting test results to non-experts.
It functions best when the range of test applications is broad. It can handle website testing, FTP, Android, and many other ecosystems. For diverse testing and absolute freedom in development, it’s one of the best.
Well suited to environments where testers may not have substantial development or programming skills.
Selenium
You may have noticed that many of these solutions are either built on top of or compatible with Selenium testing. Selenium is undoubtedly the most popular automated security testing option for web applications. However, it has been extended quite often to add functionality to its core. Selenium is used in everything from Katalon Studio to Robot, but alone, it is primarily a browser automation product.
Those who believe they will be actively customizing their automated test environments may want to start with Selenium and customize it from there. In contrast, those who wish to begin in a more structured test environment may be better off with one of the systems that are built on top of Selenium. Selenium can be scripted in a multitude of languages, including Java, Python, PHP, C#, and Perl.
Selenium is not as user-friendly as many of the other tools on this list; it is designed for advanced programmers and developers. The other tools that are built on top of it tend to be easier to use.
Selenium can be described as a framework for a framework.
Many of the most modern and specialized frameworks draw design elements from Selenium. They are also often made to work in concert with Selenium.
Its original purpose was testing web applications, but over the years it has grown considerably. Selenium supports C#, Python, Java, PHP, Ruby, and virtually any other language and protocol needed for web applications.
Selenium comprises one of the largest communities and support networks in automation testing. Even tests that aren’t designed initially on Selenium will often draw upon this framework for at least some elements.
Watir
A light and straightforward automated software testing tool, Watir can be used for cross-browser testing and data-driven testing. Watir can be integrated with Cucumber, Test/Unit, and RSpec, and is free and open source. This is a solid product for companies that want to automate their web testing as well as for a business that works in a Ruby environment.
Gauge
Gauge is produced by the same company that developed Selenium. With Gauge, developers can use C#, Ruby, or Java to create automated tests Gauge itself is an extensible program that has plug-in support, but it is still in beta; use this only if you want to adopt cutting-edge technology now. Gauge is a promising product, and when it is complete will likely become a standard, both for developers and testers, as it has quite a lot of technology behind it.
Gauge aims to be a universal testing framework. Gauge is built around being lightweight. It uses a plugin architecture that can be work with every primary language, ecosystem, and IDE in existence today.
It is primarily a data-driven architecture, but the emphasis on simplicity is its real strength. Gauge tests can be written in a business language and still function. This makes it an ideal automated testing tool for projects that span workgroups. It is also a favorite for business experts who might be less advanced in scripting and coding. It is genuinely difficult to find a system that cannot be tested with Gauge.
Commercial Automation Tools
IBM Rational Functional Tester
A data-driven performance testing tool, IBM is a commercial solution that operates in Java, .Net, AJAX, and more. The IBM Rational Functional Tester provides unique functionality in the form of its “Storyboard” feature, whereby user actions can be captured and then visualized through application screenshots. IBM RFT will give an organization information about how users are using their product, in addition to how users are potentially breaking their product. RFT is integrated with lifecycle management systems, including the Rational Quality Manager and the Rational Team Concert. Consequently, it’s best used in a robust IBM environment.
Katalon Studio
Katalon Studio is a unique tool that is designed to be run both by automation testers and programmers and developers. There are different levels of testing skill set available, and the testing processes include the ability to automate tests across mobile applications, web services, and web applications. Katalon Studio is built on top of Appium and Selenium, and consequently offers much of the functionality of these solutions.
Katalon Studio is an excellent choice for larger development teams that may require multiple levels of testing. It can be integrated into other QA testing processes such as JIRA, Jenkins, qTest, and Git, and its internal analytics system tracks DevOps metrics, graphs, and charts.
Ranorex
Ranorex is a commercial automation tool designed for desktop and mobile testing. It also works well for web-based software testing. Ranorex has the advantages of a comparatively low pricing scale and Selenium integration. When it comes to tools, it has reusable test scripts, recording and playback, and GUI recognition. It’s a sufficient all-around tool, especially for developers who are needing to test on both web and mobile apps. It boasts that it is an “all in one” solution, and there is a free trial available for teams that want to test it.
Sahi Pro
Available in both open source and commercial versions, Sahi is centered around web-based application testing. Sahi is used inside of a browser and can record testing processes that are done against web-based applications. The browser creates an easy-to-use environment in which elements of the application can be selected and tested, and tests can be recorded and repeated for automation. Playback functionality further makes it easy to pare down to errors.
Sahi is a well-constructed testing tool for smaller parts of an application. Still, it may not be feasible to use for more wide-scale automated test production, as it relies primarily on recording and playback. Recording and playback is generally an inconsistent method of product testing.
TestComplete
Both keyword-driven and data-driven, TestComplete is a well-designed and highly functional commercial automated testing tool. TestComplete can be used for mobile, desktop, and web software testing, and offers some advanced features such as the ability to recognize objects, detect and update UI objects, and record and playback tasks. TestComplete can be integrated with Jenkins.
TestPlant eggPlant
TestPlant eggPlant is a niche tool that is designed to model the user’s POV and activity rather than simply scripting their actions. Testers can interact with the testing product as the end users would, making it easier for testers who may not have a development or programming background. TestPlant eggPlant can be used to create test cases and scenarios without any programming and can be integrated into lab management and CI solutions.
Tricentis Tosca
A model-based test automation solution, Tricentis Tosca offers analytics, dashboards, and multiple integrations that are intended to support agile test automation. Tricentis Tosca can be used for distributed execution, risk analysis, integrated project management, and can support applications, including mobile, web, and API.
Unified Functional Testing
Though it is expensive, Unified Functional Testing is one of the most popular tools for large enterprises. UFT offers everything that developers need for the process of load testing and test automation, which includes API, web services, and GUI testing for mobile apps, web, and desktop applications. A multi-platform test suite, UFT can perform advanced tasks such as producing documentation and providing image-based object recognition. UFT can also be integrated with tools such as Jenkins.
Cypress
Designed for developers, Cypress is an end-to-end solution “for anything that runs inside the browser.” By running inside of the browser itself, Cypress can provide for more consistent results when compared to other products such as Selenium. As Cypress runs, it can alert developers of the actions that are being taken within the browser, giving them more information regarding the behaviors of their applications.
Debuggers can be quickly introduced directly to applications to streamline the development process. Overall, Cypress is a reliable tool that is designed to be used for end-to-end during project management development.
Serenity
Serenity BDD (also known as Thucydides) is a Java-based framework that is designed to take advantage of behavior-driven development tools. Compatible with JBehave and Cucumber, Serenity makes it easier to create acceptance and regression testing. Serenity works on top of behavior-driven development tools and the Selenium WebDriver, essentially creating a secure access framework that can be used to create robust and complex products. Functionality in Serenity includes state management, WebDriver management, Jira integration, screenshot access, and parallel testing.
Through this built-in functionality, Serenity can make the process of performance testing much faster. It comes with a selection of detailed reporting options out-of-the-box, and a unique method of annotation called @Step. @Step is designed to make it easier to both maintain and reuse your tests, therefore streamlining and improving your test processes. Recent additions to Serenity have brought in RESTful API testing, which works through integration with REST assured. As an all-around testing platform, Serenity is one of the most feature-complete.
RedwoodHQ
RedwoodHQ is an Open Source test automation framework that works with any tool.
It uses a web-based interface that is designed to run tests on an application with multiple testers. Tests can be scripted in C#, Python, or Java/Groovy, and web-based applications can be tested through APIs, Selenium, and their web IDE. Creating test scripts can be completed on a drag-and-drop basis, and keyword-friendly searches make it easier for testers to develop their test cases and actions.
Though it may not be suitable for more in-depth testing, RedwoodHQ is a superb starting place and an excellent choice for those who operate in a primarily tester-driven environment. For developers, this performance testing tool may prove to be too shallow. That being said, it is a complete automation tool suite and has many necessary features built-in.
Appium
Appium has one purpose: testing mobile apps.
That does not mean to imply that it has a limited range of testing options. It works natively with iOS, Android, and other mobile operating systems. It supports simulators and emulators, and it is a darling for test designers who are also app developers. Perhaps the most notable perk of Appium is that it enables testing environments that do not require any changes to the original app code. That means apps are tested in their ready-to-ship state and produces test results that are as reliable as possible.
Apache JMeter
JMeter is made for load testing. It works with static and dynamic resources, and these tests are critical to all web applications.
It can simulate loads on servers, server groups, objects, and networks to ensure integrity on every level of the network. Like Citrus, it works across communication protocols and platforms for a universal look at communication. Unlike Citrus, it’s emphasis is not on basic functionality but in assessing high-stress activity.
A popular function among testers is JMeter’s ability to perform offline tests and replay test results. It enables far more scrutiny without keeping servers and networks busy during heavy traffic hours.

Find the Right Automated Testing Software
Ultimately, choosing the right test solution is going to mean paring down to the test results, test cases, and test scripts that you need. Automated tools make it easier to complete specific tasks. It is up to your organization to first model the data it has and identify the results that it needs before it can determine which automated testing tool will yield the best results.
Many companies may need to use multiple automated products, with some being used for user experience, others for data validation. Others are used as an all-purpose repetitive testing tool. There are free trials available for many of the products listed above. Testee each solution and see how it fits into its existing workflow and development pipeline.
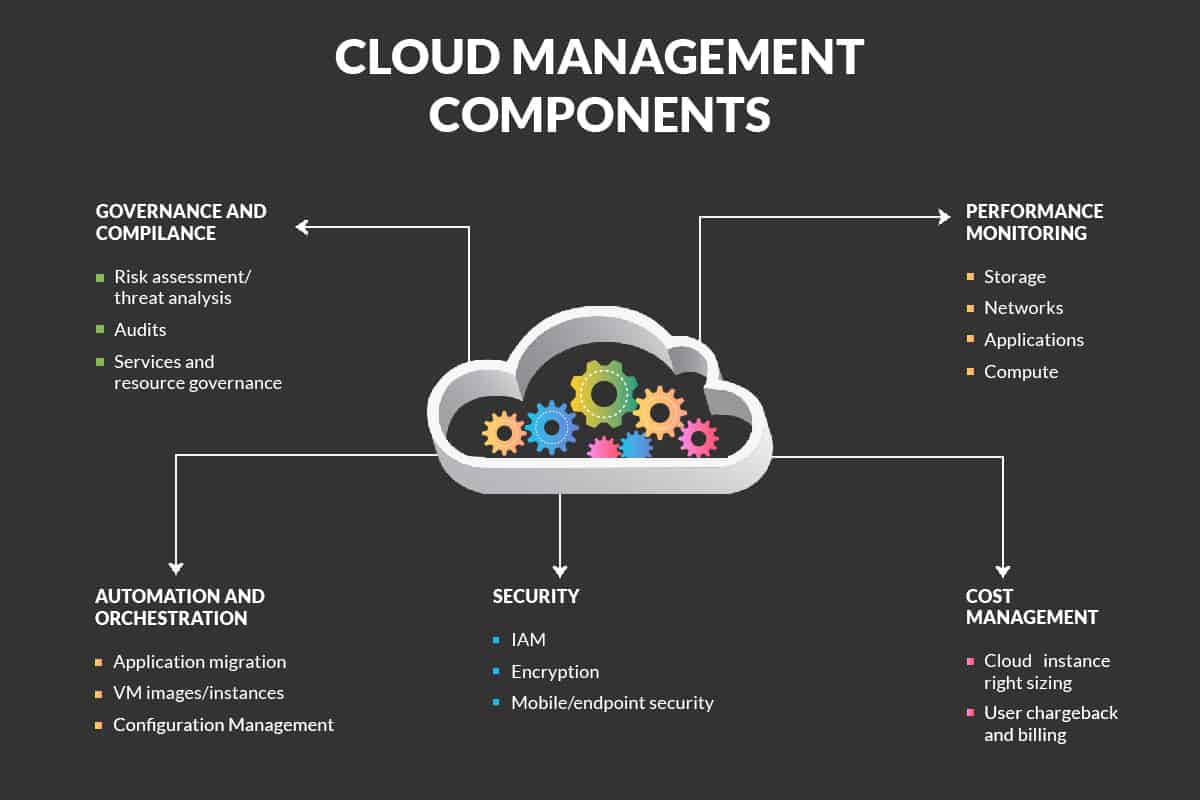
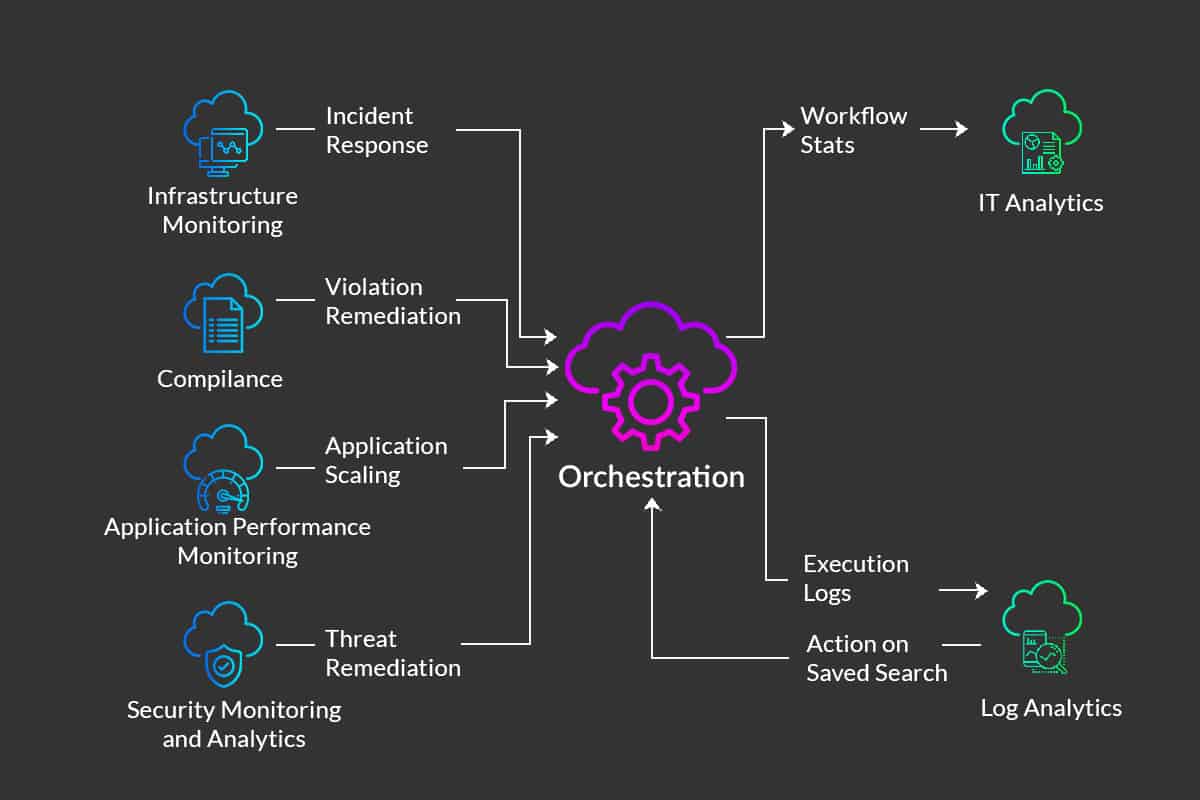

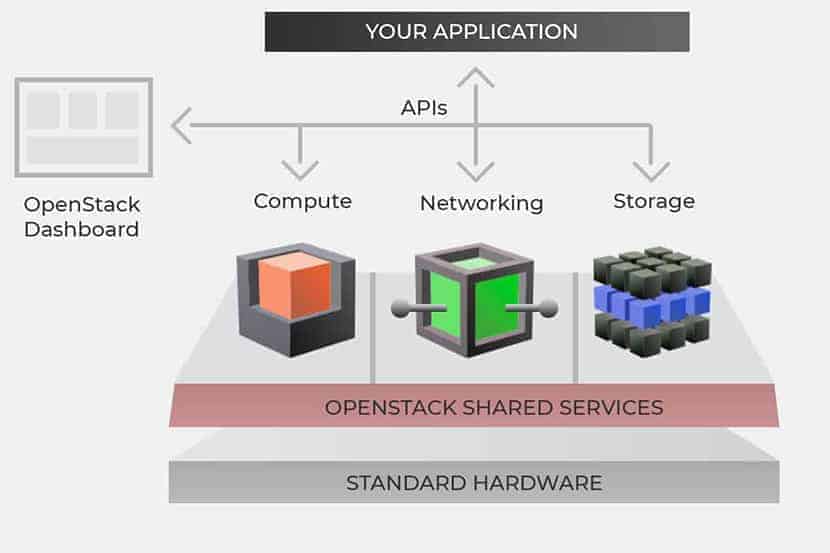

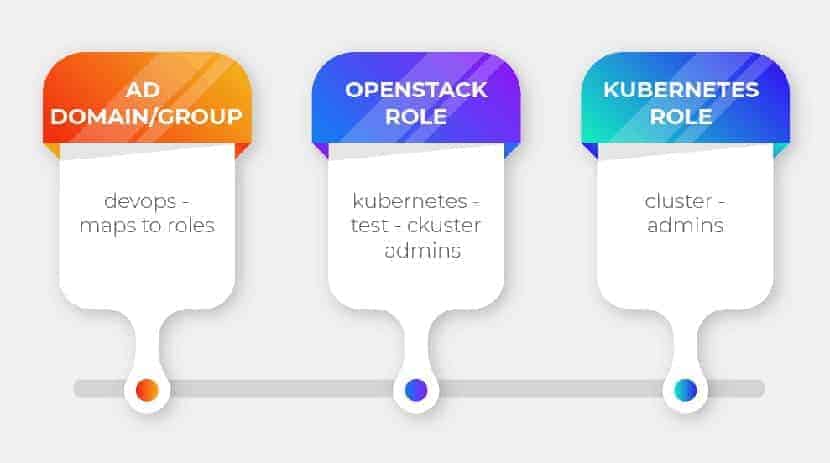

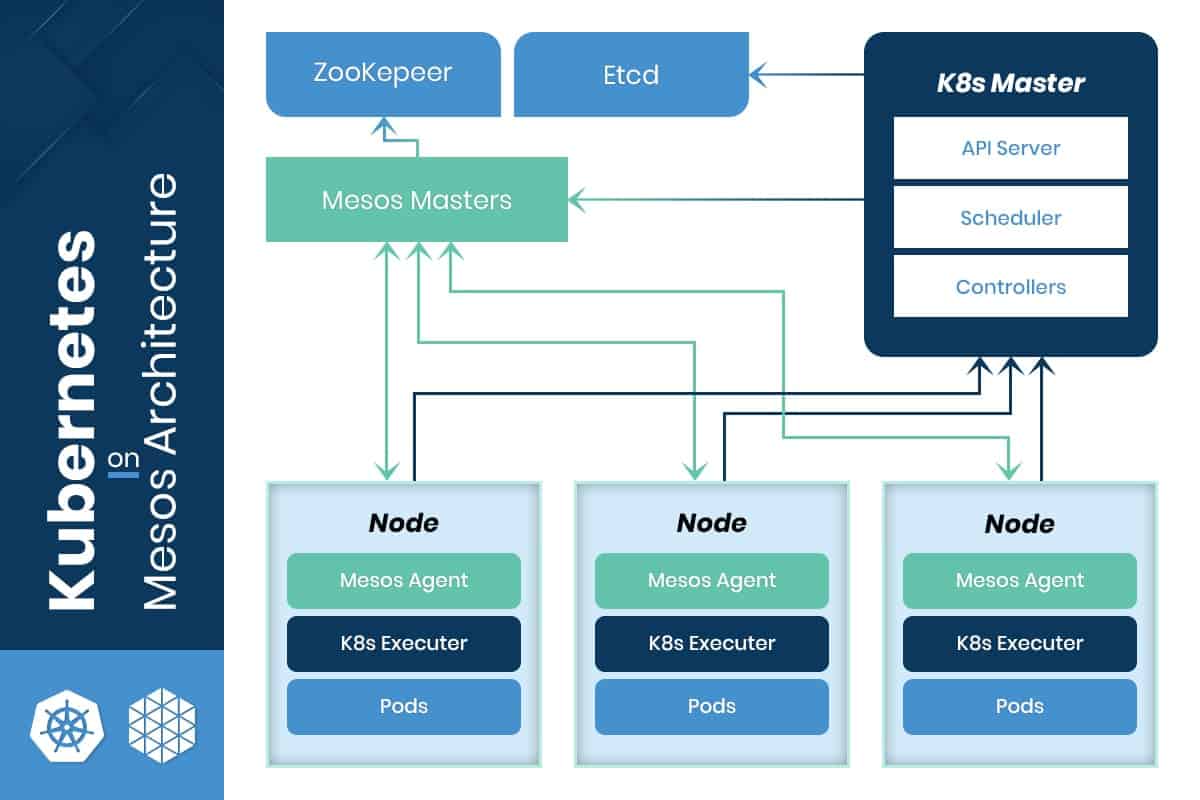
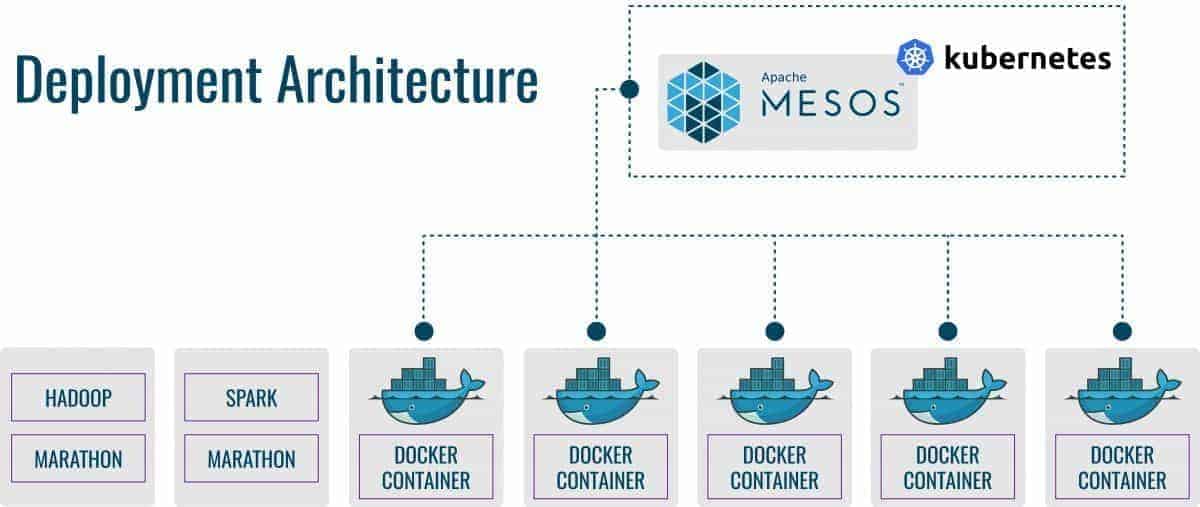


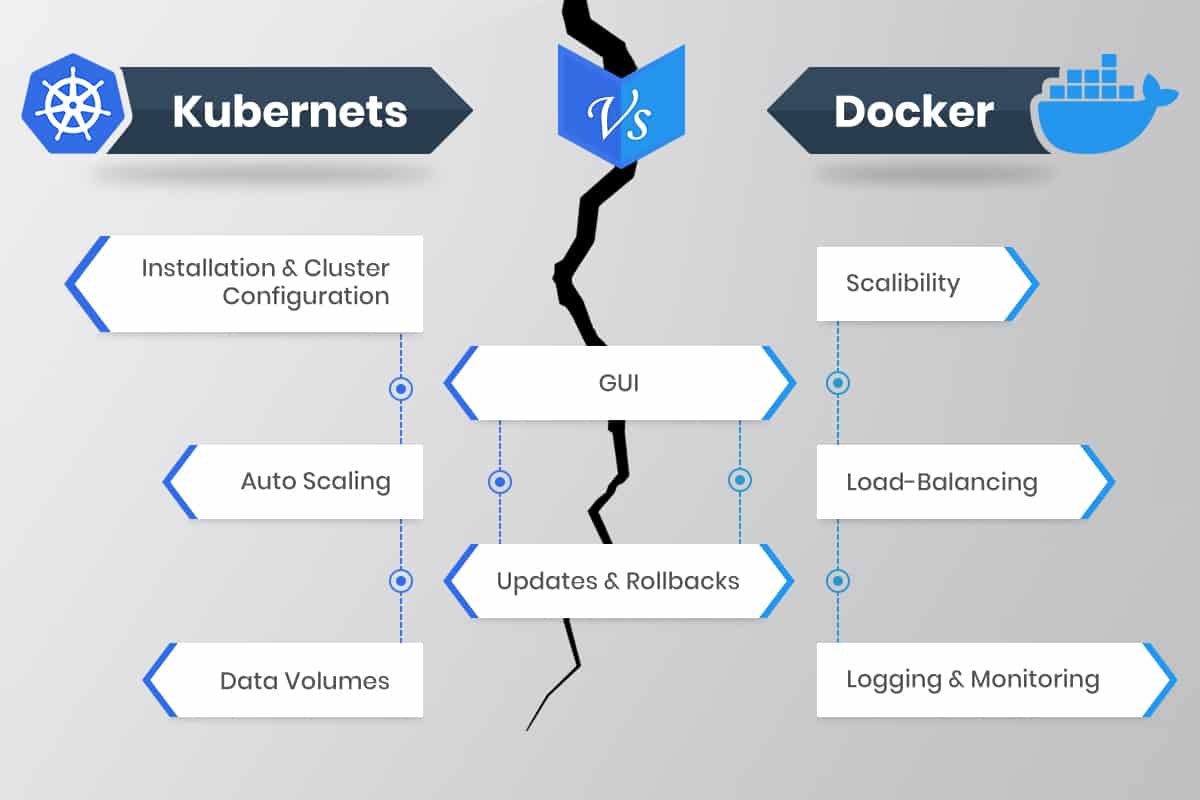
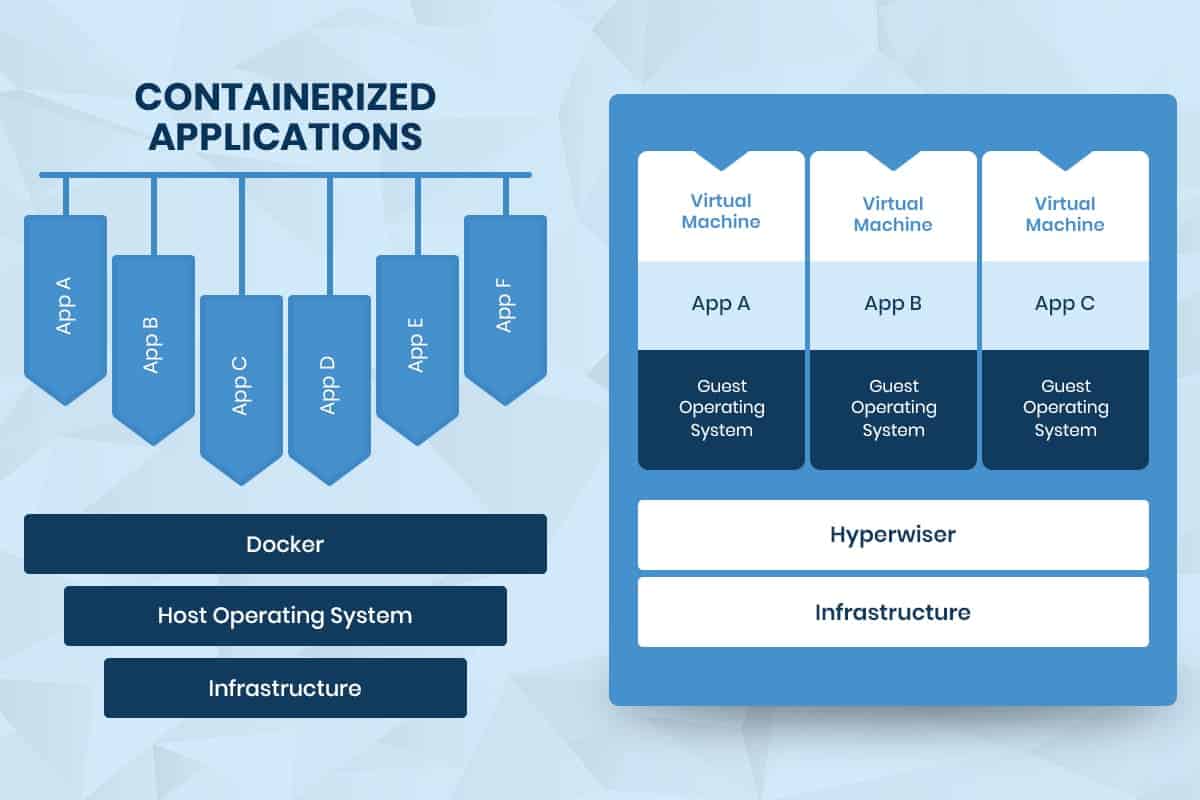
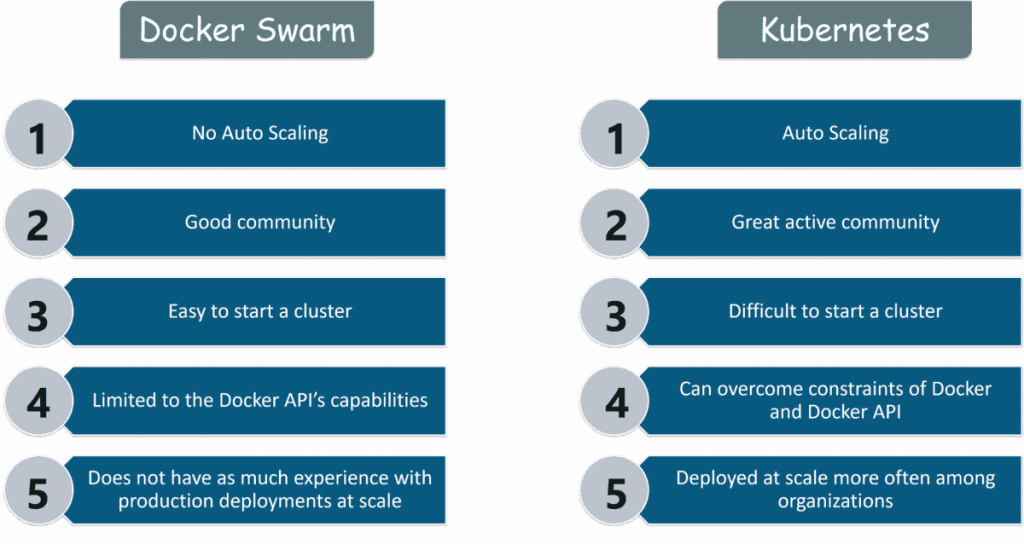

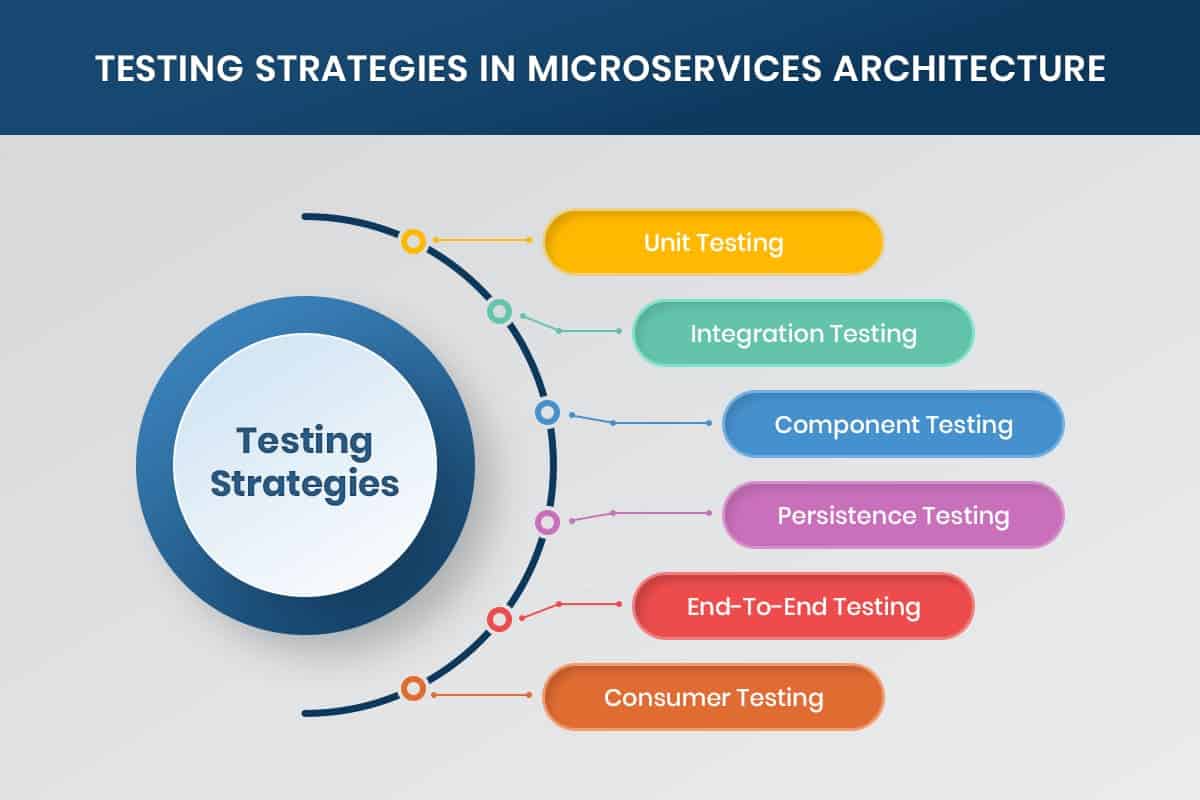


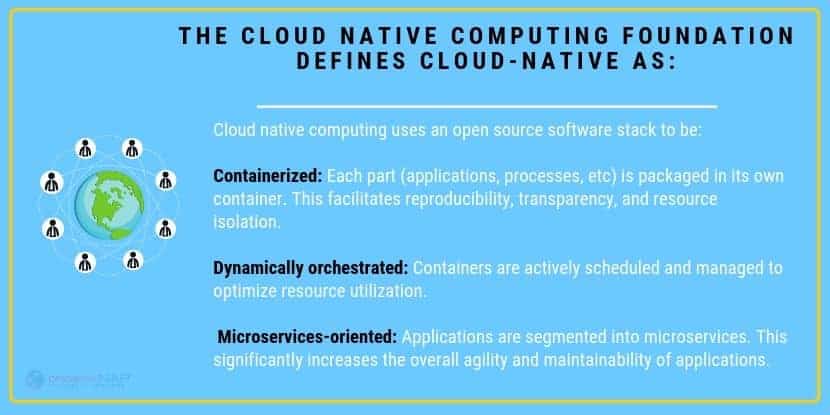


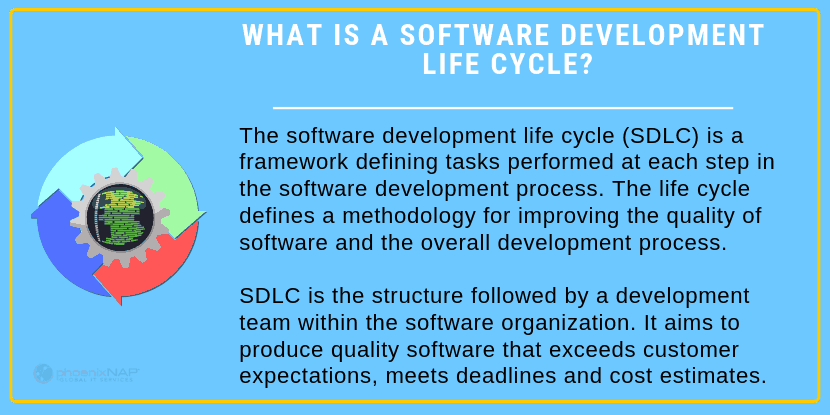
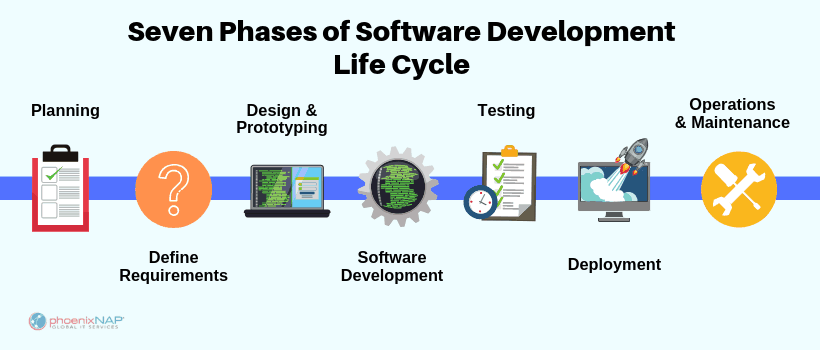


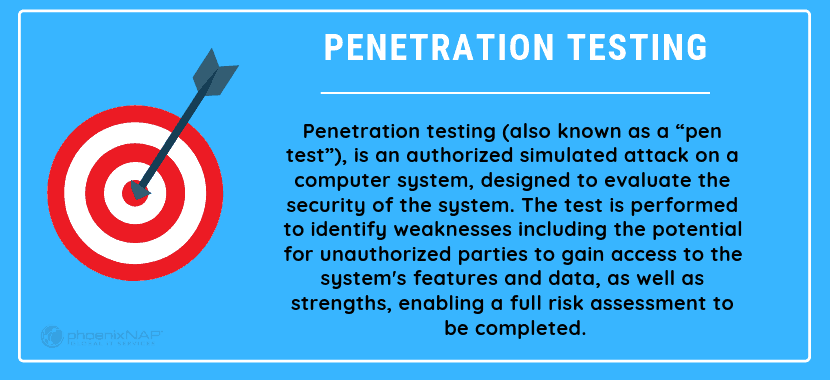
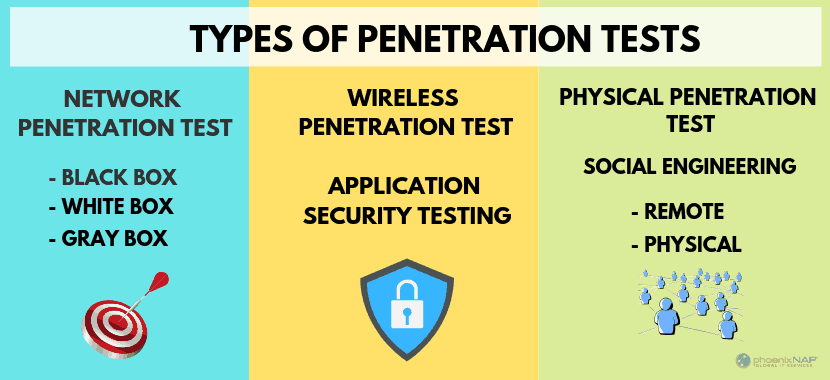 Types of Penetration Tests
Types of Penetration Tests